On April 10, 2024, Volexity uncovered the zero-day exploitation of a vulnerability in Palo Alto Networks PAN-OS GlobalProtect feature at one of its network security monitoring (NSM) clients. Suspicious network traffic alerts prompted an investigation, revealing a compromised device. The next day, April 11, 2024, Volexity detected similar exploitation at another NSM client, indicating a recurring threat actor.
The security vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.0) Volexity, monitoring threat actor UTA0218, witnessed remote exploitation of firewall devices. The attacker established a reverse shell, loaded additional tools, and targeted configuration data extraction for lateral movement within victim organizations.
During its investigation, Volexity found that UTA0218 tried to install a custom Python backdoor, UPSTYLE, on the firewall. This backdoor allows for executing commands via network requests. Volexity also discovered successful exploitation at other organizations dating back to March 26, 2024, with attempts to validate exploitability. On April 7, 2024, failed backdoor deployment was observed, followed by successful exploitation on April 10 and 11, 2024.
After exploiting devices, UTA0218 downloaded additional tools from their remote servers to ease access to victims’ internal networks. They swiftly moved laterally, extracting sensitive credentials and files. The attacker’s speed and tactics suggest a highly skilled actor with specific objectives. Volexity cannot estimate the extent of exploitation but suggests affected organizations review the advisory for mitigation steps. This post details the added malware, lateral movement attempts, and methods to detect network compromise.
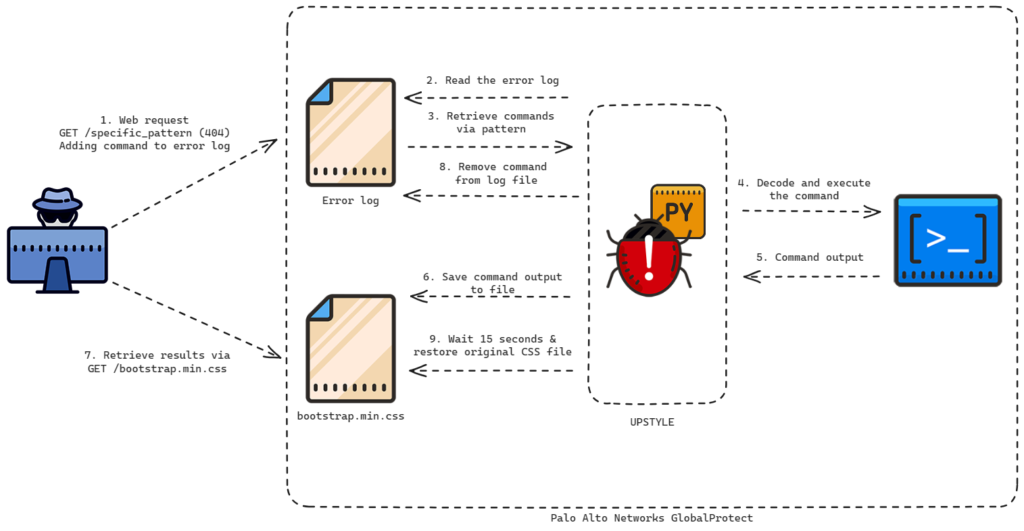
There are two ways to detect compromise on a firewall device. Volexity is working with Palo Alto Networks on one method, details pending. The following section outlines detection methods. If compromise is found, refer to the “Responding to Compromise” section.
Targeting edge devices is a favored tactic among skilled threat actors. Robust detection measures are crucial for spotting exploit-related activity, including network monitoring and EDR capabilities to catch lateral movement. Early detection minimizes mitigation scope and costs.
Volexity tracks activity by UTA0218, likely a state-backed actor due to resource investment and targeted victims. A spike in exploitation is expected, prompting swift mitigation deployment by organizations.
It’s crucial for organizations to act promptly, deploying recommended mitigations and conducting device compromise reviews.
The blog post offers advice on prevention and detection, and you can find related indicators for download on the Volexity GitHub page.
Found this article interesting? Follow us on X and LinkedIn to read more exclusive content we post.


