In 2024, cybersecurity experts at Kaspersky discovered a new cyber hacking tool that is used by a group, called ToddyCat. The tool name is TCESB which is a type of malware hidden inside a file called version.dll. It’s created to secretly run harmful software on infected Windows computers without being noticed by antivirus or security tools.
The hackers used a DLL proxying technique for malicious code proxying. Windows programs use DLLs file which is a special file to work properly. If a program loads a fake DLL (created by hackers), that fake DLL can run malicious code in the background while the program continues to work normally.
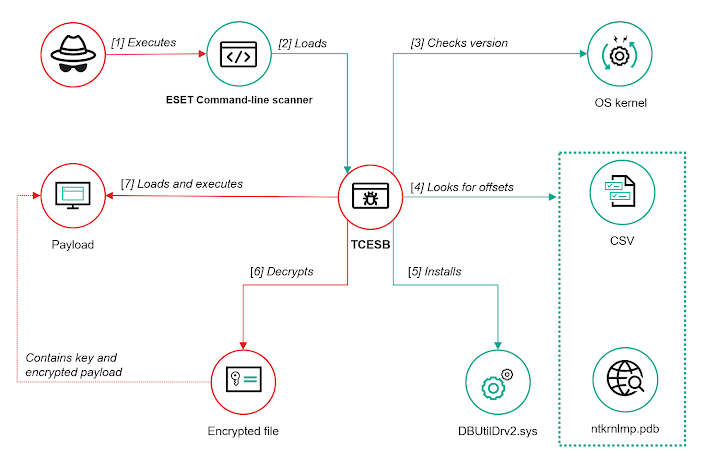
The security program that was tricked is called ESET Command-line Scanner. It had a vulnerability (now known as CVE-2024-11859) that caused it to load version.dll from the wrong location, the same folder the malware was hiding. Because this was a trusted program, it did not raise any alarms when the fake DLL was loaded.
Once inside the system, TCESB goes deeper. It disables important Windows features that normally alert security software when new programs start or when system files are loaded. This makes it even harder to detect.
TCESB first checks what version of Windows it’s running on. It uses built-in files to find out where important system information is stored in memory. If it can not find what it needs, it downloads a file (called a PDB file) from Microsoft’s servers to figure it out.
Then it uses another trick known as BYOVD (Bring Your Vulnerable Driver). This means it installs an old, known-to-be-vulnerable driver. In this case, a Dell driver named DBUtilDrv2.sys (with vulnerability CVE-2021-36276). This driver allows the malware to change Windows’ core memory, letting it turn off security features.
TCESB then sits quietly and waits for a payload file (the actual malware) to appear in its folder. These payload files are named such as kesp or ecore and do not have extensions like .exe. They are encrypted using a method which is called AES-128, and the decryption key is included in the first 32 bytes of the file. Once found, TCESB decrypts the payload and runs it secretly in memory.
The tool also builds a log file that records all the steps it takes and also helps the attackers know if everything worked.
Key takeaways:
ToddyCat is used as a trusted security tool to run malware and avoid any detection.
They mostly use a fake DLL (version.dll) and tricked the ESET scanner into loading it.
The malware deactivates security alerts and uses a vulnerable Dell driver to dig deeper into Windows.
It waits to load its actual malicious code in the system from an encrypted file.
These techniques help to manage the malware to stay hidden for longer.
To defend against tools including TCESB, experts recommend checking for old or vulnerable drivers, monitoring for unexpected symbol downloads (used for debugging), and making sure system files are properly signed and located.
Found this article interesting? Follow us on X and LinkedIn to read more exclusive content we post.




При поиске качественных ссылок часто используется база трастовых сайтов для хрумера https://www.olx.ua/d/uk/obyavlenie/progon-hrumerom-dr-50-po-ahrefs-uvelichu-reyting-domena-IDXnHrG.html.
Для тех, кто ищет честные обзоры, рекомендую https://shinapro.in.ua/. Там всё без рекламы и в объективной форме.
Я люблю бути в курсі міського життя, тому короткі огляди про події Києва завжди мене виручають. Це дозволяє швидко зорієнтуватися в ситуації.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me. https://www.binance.info/register?ref=IXBIAFVY
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://accounts.binance.com/tr/register?ref=MST5ZREF
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me. https://www.binance.com/bn/register?ref=WTOZ531Y
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Your article helped me a lot, is there any more related content? Thanks! https://www.binance.info/register?ref=IHJUI7TF
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://accounts.binance.com/en-IN/register-person?ref=A80YTPZ1
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
888SLOT hiểu rằng tốc độ giao dịch chính là yếu tố then chốt. Vì vậy, mọi giao dịch nạp/rút tiền đều được xử lý tự động trong vòng chưa đầy 3 phút – kể cả vào dịp lễ Tết hay khung giờ cao điểm. TONY12-30
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Современные пользователи всё чаще выбирают автономные решения. Среди них востребована зарядная станция, подходящая для дома. Это практичный вариант.
Your article helped me a lot, is there any more related content? Thanks!
Для квартири або приватного будинку важливо мати резервне джерело живлення. Надійна зарядна станція легко справляється з цим завданням. Вона компактна та проста у використанні.
У повсякденному житті важливо мати запасний варіант енергії. Тут допомагає зарядна станція. Вона забезпечує спокій.
Для родинного побуту важливо мати надійні інструменти. Саме зарядна станція відповідає цим вимогам. Вона корисна у різних ситуаціях.
Під час перебоїв з електропостачанням важливо швидко знайти рішення. У таких випадках зарядна станція стає надійною підтримкою. Вона забезпечує роботу необхідних пристроїв.
Для сімей з дітьми стабільне електропостачання дуже важливе. У цьому допомагає зарядна станція, яка підтримує освітлення і гаджети. Вона робить будинок більш безпечним і зручним.
Під час непередбачуваних ситуацій важливо мати запас енергії. Надійна зарядна станція дозволяє швидко відновити електроживлення. Вона підтримує базові потреби.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
У заміському будинку автономність має особливе значення. Потужна зарядна станція дозволяє користуватися побутовими приладами навіть без мережі. Вона дуже практична.
Під час аварійних відключень світла важливо мати альтернативу. Потужна зарядна станція підтримує роботу основних пристроїв. Вона корисна.
Для активного способу життя автономність має велике значення. Надійна зарядна станція підходить для поїздок і подорожей. Вона компактна і зручна.
Для стабільної роботи домашньої техніки потрібне надійне живлення. Саме зарядна станція чудово з цим справляється. Вона корисна.
У нічний час орієнтуватися складно без допомоги техніки. Використання тепловізор допомагає виявляти тварин і людей. Це підвищує безпеку і точність дій.
На нічному полюванні складно помітити швидко рухому тварину без спеціальної техніки. З допомогою тепловізор, можна швидко визначити її місцезнаходження. Це підвищує ефективність.
Tốc độ xử lý lệnh tại download 888slot đạt mức dưới 0.5 giây – bạn nhấn quay là kết quả hiện ngay, không delay, không loading – mang lại cảm giác mượt mà như đang chơi offline. TONY01-12
У темряві лісу важко помітити навіть велику тварину. Завдяки тепловізор це стає можливим. Це робить полювання результативнішим.
У бойових умовах важлива кожна секунда. Саме тепловізор дозволяє швидко знайти ворога. Це дає перевагу.
Для мене важливо було мати рішення без зайвого шуму та викидів. Саме зарядна станція для будинку повністю відповідає цим вимогам. Це робить її ідеальною для житлових приміщень.
Мені було важливо придбати пристрій, який легко обслуговувати і експлуатувати. У цьому допомагає зарядна станція для будинку, яка готова до роботи одразу після підключення. Вона забезпечує стабільну роботу всіх приладів без проблем.
Після тривалого використання можу зробити тільки позитивні висновки. У повсякденному житті зарядна станція для будинку стала незамінним помічником. Вона реально підвищує рівень домашнього комфорту.
Під час відключень світла раніше виникало багато зайвих проблем. Тепер зарядна станція для будинку дозволяє повністю їх уникнути. Побут залишається комфортним та передбачуваним.
Під час тривалих перебоїв електроенергії важливо не втрачати контроль. У цьому допомагає зарядна станція для будинку, яка працює стабільно. Вона корисна щодня.
Після переходу на автономне живлення життя стало спокійнішим. Саме зарядна станція для будинку дала відчуття контролю. Вона дуже практична.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Для сучасного житла важливо мати альтернативне джерело енергії. Саме зарядна станція для будинку дозволяє уникнути дискомфорту під час відключень світла. Це справді практичний та корисний пристрій.
Під час дистанційної роботи особливо важлива безперервна подача електроенергії. Саме зарядна станція для будинку дозволяє залишатися продуктивним у будь-якій ситуації. Вона забезпечує стабільність і впевненість.
Для сучасної квартири необхідне надійне резервне джерело енергії. Саме зарядна станція для будинку забезпечує стабільну роботу важливих приладів. Це дійсно корисний та практичний пристрій.
Для сучасної квартири важливо мати тихе та безпечне живлення. У цьому сенсі зарядна станція для будинку стала ідеальним варіантом. Вона не створює дискомфорту під час роботи.
Для сучасної людини важлива незалежність від обставин та мережі. Реальним кроком до цього стають потужні зарядні станції, що дарують автономність у будь-який момент. Вони роблять життя значно зручнішим та безпечнішим.
Під час кемпінгу на природі важливо мати заряджені телефони, ліхтарі та прилади. У цьому допомагають компактні потужні зарядні станції, які легко транспортувати і підключати. Вони гарантують автономність та безпеку відпочинку.
Під час дистанційної роботи важливо мати заряджені ноутбуки і гаджети на протязі всього дня. Найбільш ефективними для цього є сучасні потужні зарядні станції, що підтримують одночасну роботу декількох пристроїв. Вони роблять роботу більш комфортною і безпечною.
У приватних будинках часто трапляються перебої з електропостачанням у нічний час. Надійним рішенням є сучасні потужні зарядні станції, які здатні підтримувати роботу всіх необхідних приладів протягом кількох годин. Вони забезпечують комфорт і спокій родини.
У невеликих майстернях часто бракує стабільної електрики. Практичним помічником стають потужні зарядні станції, які забезпечують роботу обладнання. Це дуже вигідне рішення.
Під час організації вуличних заходів необхідно підключати освітлення. Зручним рішенням стають потужні зарядні станції, які легко перевозити та налаштовувати. Вони допомагають створити святкову атмосферу.
Під час перебування у віддалених місцях важливо залишатися на зв’язку. Допомагають у цьому потужні зарядні станції, здатні заряджати телефони багато разів. Вони додають впевненості мандрівникам.
Для людей активного способу життя потрібна мобільна енергія. Практичним вибором стають потужні зарядні станції, які можна використовувати будь-де. Вони підходять для різних життєвих ситуацій.
Під час виїзних ярмарків важливо мати доступ до електрики. Надійним рішенням стають потужні зарядні станції, що забезпечують роботу обладнання. Вони спрощують організацію заходів.
В офісі часто трапляються непередбачувані перебої з електропостачанням, що заважають роботі. Надійним рішенням у таких випадках є потужні зарядні станції, які підтримують роботу комп’ютерів, принтерів та роутерів. Вони значно підвищують ефективність і стабільність робочого процесу.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://accounts.binance.com/fr-AF/register?ref=JHQQKNKN
Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://www.binance.com/pt-PT/register?ref=KDN7HDOR
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://www.binance.com/pt-BR/register?ref=GJY4VW8W
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://accounts.binance.com/kz/register?ref=K8NFKJBQ
Public awareness about chronic diseases has increased significantly in recent years. Physicians often prescribe liver medications https://goldmed.info/ based on individual diagnostic results. Patients are usually advised to follow therapy consistently for better outcomes.
Technologie maakt directe visuele interactie eenvoudiger dan ooit. Sommige aanbieders gebruiken cam seks als marketingterm. Gebruikers zoeken daarbij vooral naar kwaliteit en gebruiksgemak.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
В условиях нестабильного электроснабжения автономные источники становятся необходимыми. Во втором предложении видно, что зарядные станции помогают сохранить доступ к информации. Это важно как для работы, так и для личных потребностей.
При планировании покупок многие ориентируются на практичность и надежность. Во втором предложении отмечается, что зарядные станции отвечают этим требованиям полностью. Это делает их популярным выбором среди разных категорий людей.
Không giống với các trang web không rõ nguồn gốc, 188V đầu tư nghiêm túc vào hệ thống quản lý rủi ro và bảo vệ người dùng. Tất cả các giao dịch tài chính đều được mã hóa, đồng thời nền tảng cung cấp công cụ tự kiểm soát cho người chơi như giới hạn đặt cược và tính năng tự loại trừ. TONY01-26
Những sản phẩm cá cược thể thao luôn được thiết kế với 4 phong cách khác nhau như OW – Sự đa dạng, TP – Tượng trưng cho hiện đại, SB – Sự truyền thống, KS – Trải nghiệm. Bảng tỷ lệ kèo 188V chính thức luôn cập nhật mới mỗi ngày để tiện cho anh em chủ động tham khảo, tỷ lệ thưởng luôn hấp dẫn, tối ưu cơ hội chiến thắng cho thành viên tham gia. TONY01-26
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://accounts.binance.info/ru-UA/register-person?ref=JVDCDCK4
Корисні рекомендації потрібні як новачкам, так і досвідченим майстрам. У матеріалі ремонт приміщень: практичні поради для кожного https://vseproremont.com/ інформація подана зрозуміло. Вона допомагає досягти кращого результату.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
8543AlphonsoGottao aa frv
87098MyungPosthumuso aa frv
61923JuneAbeleo aa frv
63832KristinBerenguero aa frv
29499FeleciaLitseyo aa frv
23305RobbySizeloveo aa frv
80573HoseaBreilingo aa frv
41208EstebanLagano aa frv
25802IrwinJuaireo aa frv
64991MirellaObristo aa frv
76516DeonCianciolao aa frv
25482ChadTredoo aa frv
20340HansLedlowo aa frv
21665ConsueloBarcelloso aa frv
40524NigelVelegao aa frv
71712DemetriaKolbecko aa frv
76584BuckDosero aa frv
45341DotStanzako aa frv
50137FlaviaCotsiso aa frv
9950RichVangemerto aa frv
62589VenitaRuchtio aa frv
74656VictorLamunyono aa frv
3949ErikCranfillo aa frv
57526DioneBendaso aa frv
19219YvoneKopatzo aa frv
79955DianVillanovao aa frv
5471TrangPleasento aa frv
15LavonaAdoniso aa frv
26712CarloLeisero aa frv
3756ChadwickLoeo aa frv
10461RickyCushnero aa frv
73060MargeryDuketteo aa frv
3278AngeliqueDunzelmano aa frv
57396RashadPesterfieldo aa frv
59988AshleyHomso aa frv
81172SeritaGregorioo aa frv
42614TerrellFouxo aa frv
42607MckinleyPigfordo aa frv
55543WesleyFurfaroo aa frv
55219DonnBattenfieldo aa frv
7440AnjanetteGoehnero aa frv
60808SteveShemano aa frv
69026MargertGalanoo aa frv
58564ShayneBongiornoo aa frv
83921ShadDebiasio aa frv
46937DannieBaleso aa frv
3000TildaMurchisono aa frv
2837DianneShartrando aa frv
30609JosephineWashburno aa frv
52262MallieTohillo aa frv
86053LigiaUlabarroo aa frv
13813CarolTimpermano aa frv
3408DeonPahuluo aa frv
36345CarmeloDelsoino aa frv
55649ShavonOrzechowskio aa frv
17576JeremiahWarrilowo aa frv
82763WilburHussongo aa frv
21700AlfredHollidayo aa frv
78044RhodaThielemanno aa frv
56218RolandeJackmano aa frv
55045BrettPetixo aa frv
3555ShavonneMckearino aa frv
64762KevinClagetto aa frv
25489JoelTorranoo aa frv
38050TranKenfieldo aa frv
9068EmoryRapsono aa frv
69359AdrianLondreo aa frv
70898JennaRedikero aa frv
77081MagaretNicholseno aa frv
56652LincolnSavarinoo aa frv
45917JaeDepperschmidto aa frv
16985JannieBlendero aa frv
Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://www.binance.info/register?ref=IXBIAFVY
83490RinaWoodmoreo aa frv
54746NevilleRemyo aa frv
12449BradleyFringso aa frv
6086DulcieCornwallo aa frv
43850TranHeiningero aa frv
52555ClarenceHerendeeno aa frv
8774TaylorDawkinso aa frv
22251HwaParmaro aa frv
17389LeonFiorellio aa frv
64848FreddieCordovao aa frv
29829ErinnAbrameko aa frv
58500RichardSantagoo aa frv
86464IrmaGoheeno aa frv
28574LawrenceGroato aa frv
86821JohnnyKissero aa frv
11619FideliaSandifordo aa frv
68330JonasCecilioo aa frv
86086DeweyYeungo aa frv
76756GroverEpersono aa frv
43993LilianGluszeko aa frv
69225JoiAlexiono aa frv
34455NatoshaThaemerto abc
78305VaughnSkeanso abc
76820CindaHolppo abc
49760VeniceZoquiero abc
36804TodNasbyo abc
82601WynellHussiano abc
53832AntioneEllenwoodo abc
136RubinSchweinerto abc
76936LakendraKletschkao abc
32028VernSleetero abc
77188DottyHowlingwolfo abc
54824SalvadorShrieveso abc
72607AngleZaneo abc
251BrunildaDjurico abc
7199KamiCotugnoo abc
50221YasminBernetto abc
3018MervinHollero abc
10800LenardSallero abc
58186HalinaHellenbrando abc
75037CherePankiewiczo abc
slot365 cam kết mọi kết quả tại sảnh Casino đều dựa trên thuật toán ngẫu nhiên, đảm bảo tính công bằng tuyệt đối. TONY01-30H
54258PedroHockleyo abc
15370CarloDinio abc
66904BufordGeigero abc
36111CodyBiegelo abc
69825MistyMiltono abc
17173IdellaShivleyo abc
3740MauriceChatmano abc
12561HongOpalickio abc
7018RosariaKrzeczkowskio abc
455SooAxelrado abc
6838KatharineMasoo abc
86753LamonicaTrovingero abc
20925RachealEsquerreo abc
72648GeorgeSetlero abc
16137EmmettKutluo abc
54645MerrillHendershotto abc
82286JarvisHattmano abc
73753StanfordBartuso abc
38320DignaRabyo abc
81846VernonKrono abc
2686DennyManoro abc
70101GeorgieDeubnero abc
33732LoraineDampfo abc
87939TerryCadenao abc
17329IleneLuerao abc
49580CarmeloEscoo abc
19614AbeKubascho abc
33891ErnestGastelo abc
57191AlonzoBoalo abc
52551EvonWolffeo abc
83549SherellArmadao abc
63981MacMenendezo abc
50815EnriqueLuverto abc
70819JameyTestolino abc
62897ColeScoggino abc
212ElishaKeanuo abc
Live streams golvar.com.az and live matches online, including the latest football schedule for today. Follow games in real time, find out dates, start times, and key events of football tournaments.
65505SalenaVibbardo abc
31800LamonicaWaganero abc
3979NaomiHenrieo abc
5948RandaMcdanielo abc
36846RonaldGawliko abc
76736CelestinaMontreuilo abc
11819EarlBorelando abc
46191JeniseAmtowero abc
79981DewaynePargao abc
35798TerryFerbero abc
27560DelisaPefflyo abc
4446LindseyJankowskio abc
36614OleviaDankmeyero abc
20137MeaganMurcho abc
86210MarionBaboniso abc
71536ReedLumbo abc
5594OdellSchierbrocko abc
69887LynBurrusso abc
8206WinfordLalatao abc
70986JoselynAntistao abc
81095BenedictHametto abc
77710BobNoldo abc
86106BertLonghio abc
11909WilfredoBlausteino abc
5229DanikaWindmeyero abc
28958LatiaSwehlao abc
55110CristalHosteno abc
6646BradyBurlingtono abc
25625AbrahamGraziopleneo abc
77863KevenMezao abc
54982FosterTejedoro abc
59201NorrisMilnero abc
20232KrystinaAvelaro abc
655ChongShibleso abc
52174BartonGartero abc
50542DallasSweeno abc
77139OliverFujiokao abc
43313EdgarAravjoo abc
30691DorindaOrgano abc
52390RenataGaffigano abc
82444SandyLalatao abc
15451LuciusMceneryo abc
46861BethanyValo abc
44127CareyBerlinskio abc
23888AnnelieseProwo abc
69081LindseyDelilleo abc
58947TemikaVanvaleno abc
26915CarolannArdiono abc
67411ShaquitaBunyano abc
77875ElvisAlbinio abc
46629EzekielBickelhaupto abc
29873MilfordCrumbyo abc
55036EdgardoBrosio abc
33434MaidaHughsono abc
72504DesmondFulwilero abc
71335IsadoraBoundso abc
14484LucioHamamotoo abc
71581TannerBridenstineo abc
69424KyongKiddo abc
44351JaySeymoureo abc
66223AmiKoscielniako abc
13367JonathonDuperryo abc
67737UshaModzelewskio abc
6418OrvilleImmo abc
34517TaylorBadderso abc
41518DoyleBelliono abc
13717MelbaKemnero abc
80873DionneAherno abc
913GavinBoldrino abc
19068RaleighSprouto abc
1544NatishaMeierso abc
59656AmeliaMaldomadoo abc
37468RosendoGarniero abc
4009DongTompsono abc
47727JoshBriagaso abc
37951AlishiaBurrupo abc
71061JoaquinAronoffo abc
5120AshleyMuskao abc
29283BarryRosengarteno abc
88524ChuckManinoo abc
67585KristianBantao abc
38509RosalvaSchwetzo abc
12880KandiceLendono abc
21526JasperMizenkoo abc
3706EufemiaFolmero abc
83745GeraldCoako abc
27236YasmineIslaro abc
52426DarioNiemczyko abc
67375KatiMarkwardto abc
61304HansBakewello abc
49394MammieHyo abc
79463JimWhitesingero abc
36638JanitaHellwego abc
27441EmaBuschmanno abc
3429RodgerVondohleno abc
42931ForrestMarkowskio abc
78546NecoleSolwoldo abc
63388CicelyPatkao abc
26321KendrickLauranceo abc
4212HassanVandermayo abc
80248HarlandHornandezo abc
заклепка вытяжная 2.4 заклепки стальные вытяжные
33700IsaiahHunzeo abc
23110EmmieSolimenoo te le gram
20816AudryBilloo te le gram
19049JoleneOverbeeko te le gram
40929ChristianRoberstono te le gram
53132SoonLuzinskio te le gram
59463MadgeHanero te le gram
47814DianeFerroneo te le gram
72464TakishaRoskelleyo te le gram
44154BillieFogelmano te le gram
31863CatherynJapako te le gram
64597MarcoTallento te le gram
30499ArleenSchonacko te le gram
78363KurtisJerviso te le gram
4965BruceAlmquisto te le gram
67176VirgilioBoneyo te le gram
8980BrunoAlianoo te le gram
78397JodiRockerso te le gram
13747SherillPenrodo te le gram
74616TravisSeivero te le gram
66000ShaunaLegrando te le gram
78829RufusGraceffoo te le gram
80101JimZiero te le gram
87355MarcosPanchiko te le gram
1857JamesSpringateo te le gram
49960AlaynaPompao te le gram
20475LavetaWeelborgo te le gram
36800KendrickFitzero te le gram
70421OlinTiengo te le gram
86068ChiaRolsetho te le gram
88763LaureneSpargero te le gram
87620MaurineLiptoko te le gram
82691HollisSteinbrooko te le gram
49674NetaSchuldo te le gram
5973BretDesisleso te le gram
43218CliftonMetzero te le gram
1601NatishaHawthorno te le gram
61863LaraLouriso te le gram
74908LolaBatkoo te le gram
52632MichaelQuallso te le gram
14398CarolinaTakalao te le gram
5476RandeeSinnotto te le gram
55423ClementinaBlauwo te le gram
35872DarrellBeagleo te le gram
84426StaceyBoylano te le gram
2404TroyKozakiewiczo te le gram
4631FidelBaribeauo te le gram
51074LishaCanneyo te le gram
78075CarmeloQuibodeauxo te le gram
65016NelidaZatkoo te le gram
30708BrendanFlammango te le gram
60946SherlynCaranzao te le gram
21877NinaFeltmano te le gram
64544KristopherBaswello te le gram
46582RubinCarlowo te le gram
86014RicardoProttsmano te le gram
74407ArianaDupouyo te le gram
78737AlaneCaprao te le gram
22914HoseaVoetbergo te le gram
1313BryanWarro te le gram
3450RafaelSimonio te le gram
52680BrooksPhothiratho te le gram
1589MarlonMapstono te le gram
76137WarnerRadziwono te le gram
84581FletcherLuckritzo te le gram
70206MyrtisMancello te le gram
87750FaviolaCarstenseno te le gram
65091AntonCarseyo te le gram
25073AmaliaLantero te le gram
446LatishaBaculpoo te le gram
22590BeliaOsentowskio te le gram
Your article helped me a lot, is there any more related content? Thanks!
Интернет-магазин химических реактивов https://magazinreactivov.ru для учебных, научных и производственных задач. В каталоге — реактивы разных классов чистоты, расходные материалы и сопутствующие товары. Помогаем подобрать позиции под вашу задачу, предоставляем документы. Удобный заказ онлайн, актуальные цены и наличие, доставка по России.
Hits of the Day: https://proinoslogos.gr/
Играешь в казино? bollywood казино онлайн красочный игровой автомат с бонусами, фриспинами и высокими выигрышами. Доступно бесплатно или на реальные деньги, поддержка мобильных устройств.
Ищешь казино? клубника casino играйте онлайн в игровые автоматы и live-казино. Бонусные предложения, демо-режим, мобильная версия и круглосуточный доступ к азартным играм без установки.
Лушчее онлайн казино играть в пинко на реальные деньги слоты, live-казино и бонусные функции. Доступ с любых устройств, понятный интерфейс и возможность выбрать бесплатный или реальный режим игры.
Лучшее онлайн казино pinco официальный сайт на русском слоты, live-казино и бонусные функции. Доступ с любых устройств, понятный интерфейс и возможность выбрать бесплатный или реальный режим игры.
Играть онлайн пинко казино онлайн игровые автоматы, live-казино и бонусы для новых игроков. Удобный интерфейс, доступ с телефона и ПК, возможность играть бесплатно или на реальные ставки.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://www.binance.com/pt-BR/register?ref=GJY4VW8W
Играть в казино зеркало казино 1вин лоты, live-столы и бонусные функции. Подходит для новичков и опытных игроков, доступно бесплатно и на реальные деньги 24/7.
Казино онлайн казино с минимальным депозитом 10 рублей играйте онлайн в яркие слоты и live-казино. Динамичный игровой процесс, бонусные раунды и возможность начать игру за пару кликов с телефона или компьютера.
Лучшее онлайн казино казино с выводом денег на карту сбербанка играйте в слоты и live-казино с телефона или ПК. Адаптивный интерфейс, быстрый запуск игр и доступ к развлечениям в любое время.
Залетай в казино игра sweet bonanza на деньги быстрый доступ к слотам, live-играм и настольным развлечениям. Удобная навигация, запуск без установки и поддержка мобильных устройств.
Топовое онлайн казино new retro casino без первоначального играть онлайн с телефона или ПК. Слоты и live-игры, адаптивный интерфейс и стабильный запуск без скачивания приложений.
дизайн дома внутри дизайн коттеджа
DamienWahington76776 hehe haha
DevonParvin82217 hehe haha
KendaRiedell34561 hehe haha
EladiaBackus49530 hehe haha
DeonnaHarkins23324 hehe haha
IlanaWarntz16641 hehe haha
OrvilleLarison12825 hehe haha
NathanTatem10878 hehe haha
комнатный дизайн квартир дизайн двухкомнатной квартиры
SilasCotto33637 hehe haha
TanikaHannasch30719 hehe haha
DarceyWoolum82230 hehe haha
MartinViera57073 hehe haha
CristieTripodi272 hehe haha
NadeneNikaido13700 hehe haha
GilbertoThimmesch45700 hehe haha
RosariaHarrellson88683 hehe haha
RobinCopen39688 hehe haha
SonSolages67477 hehe haha
LashellKempisty6801 hehe haha
DemetriusChurchfield13995 hehe haha
CythiaPishner13107 hehe haha
JuanSummons81115 hehe haha
Здесь делаем стеллажи мебель на заказ москва с контролем качества. Конструкторская схема в течение дня. Сборка бережно. Нужна мебель? – согласуем следующий шаг.
MathildaWingham61686 hehe haha
AsiaAlmen9260 hehe haha
PhylisThumm17911 hehe haha
ArnoldoKastor36619 hehe haha
YaekoErnzen46524 hehe haha
AlexaGillikin50210 hehe haha
MarlonElie642 hehe haha
SeeRandhawa60684 hehe haha
HaiRedrick53181 hehe haha
RoseannPlatten37820 hehe haha
JewelYurkovich32045 hehe haha
ApoloniaOkumoto14203 hehe haha
TonaHolberg88239 hehe haha
FedericoMarrin18079 hehe haha
MarcellaAllegretta39267 hehe haha
Сертификация продукции https://www.sostav.ru/blogs/286052 подтверждение того, что продукция соответствует нормам безопасности. Сертификация обязательна для некоторых групп товаров. Помимо обязательной, есть и добровольная сертификация соответствия продукции действующим стандартам. Её проводят по запросу производителя, импортёра или продавца.
ForestWeltz8200 hehe haha
MiguelSzymula17519 hehe haha
RosalineDehaas38729 hehe haha
Сертификация услуг https://pandia.org/user/categ/6225-Moi_statmzi это процедура подтверждения стабильного уровня качества и безопасности предоставляемых услуг. Схемы сертификации услуг. В российской практике сертификация услуг регламентирована национальными стандартами, в частности, ГОСТ Р 54659-2011.
CleoraMurcko32540 hehe haha
AlfredCampolo11193 hehe haha
RoyceKopicko26880 hehe haha
HueyBhakta64042 hehe haha
ClintWeeda29477 hehe haha
ReaAdkin85947 hehe haha
FeltonDelille48244 hehe haha
MalkaSchoeneman49513 hehe haha
ChastityFryman37135 hehe haha
JeffryTallon11962 hehe haha
CecileViapiano38666 hehe haha
EffieJin68559 hehe haha
SommerLamica26521 hehe haha
LinoBoutilier36486 hehe haha
ErikDestime10965 hehe haha
CarloBachert26321 hehe haha
MarvinLapre76408 hehe haha
JosefThoman50416 hehe haha
OdaCorathers4299 hehe haha
KendaGraziosi37711 hehe haha
ColemanLofink17031 hehe haha
GuyGartley58932 hehe haha
ShayneOcampo36844 hehe haha
EmanuelJodway2011 hehe haha
TondaSwarm60770 hehe haha
SamDefaria86038 hehe haha
FloreneScullawl29090 hehe haha
KendrickLourdes73053 hehe haha
MitchellReing51526 hehe haha
WillettaCanes60885 hehe haha
DwanaRoyal39863 hehe haha
CameronFalks18772 hehe haha
WillColgin29522 hehe haha
NickEckes14236 hehe haha
WaldoEdrington2257 hehe haha
ShilaRobben42853 hehe haha
GroverDragone14893 hehe haha
DennyYantzi58284 hehe haha
JoieReichardt22739 hehe haha
NeldaAndrango43084 hehe haha
KennethLeisy2494 hehe haha
BoScarola700 hehe haha
Наша специализация https://kartremont.ru ремонт квартир в Санкт-Петербурге любой сложности: от косметического обновления до капитального ремонта и эксклюзивных дизайнерских проектов. Мы работаем так, чтобы каждая деталь радовала вас долгие годы, а сам процесс был максимально комфортным.
Professionelle thaimassage Augsburg: Entspannende Massagen, wohltuende Anwendungen und personliche Betreuung. Gonnen Sie sich eine Auszeit vom Alltag in angenehmer Atmosphare.