Cybersecurity researchers have uncovered a new Android banking trojan called BlankBot which targets Turkish users in an attempt to steal financial data.
Summary:
Researchers at Intel 471 Malware Intelligence discovered BlankBot in July 2024. It is a new Android banking Trojan that most likely targets Turkish users. Malicious features of BlankBot involve injections, keylogging, screen recording, and WebSocket connection with a control server. Antivirus software misses the majority of samples, yet the existence of logs and different codes implies the malware is still under development. In a report released last week, Intel 471 said.
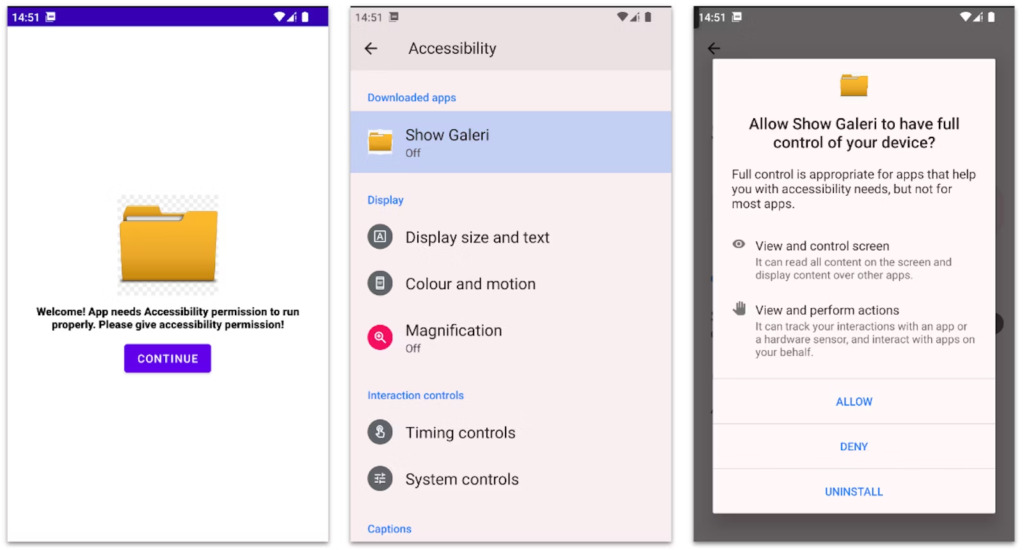
BlankBot incorporates many of the features found in other banking Trojans but takes them a step further. Some key distinctions include:
- Advanced Screen Recording: Unlike its predecessors, BlankBot can capture real-time video of the device’s screen, potentially exposing sensitive information beyond just keystrokes.
- Sophisticated Remote Control: BlankBot offers attackers unprecedented control over infected devices, allowing for more complex and targeted attacks.
- Enhanced Anti-detection: BlankBot employs advanced techniques to evade detection by antivirus software and security researchers, making it more persistent and difficult to remove.
- Comprehensive Cryptocurrency Theft: While some Trojans have limited capabilities in this area, BlankBot is designed to target a wide range of cryptocurrency wallets.
Below is a list of some of the malicious APK files that include BlankBot. –
app-release.apk (com.abcdefg.w568b)
app-release.apk (com.abcdef.w568b)
app-release-signed (14).apk (com.whatsapp.chma14)
app.apk (com.whatsapp.chma14p)
app.apk (com.whatsapp.w568bp)
showcuu.apk (com.whatsapp.w568b)
IOC:
BlankBot APK SHA-256:
7d5b6bcc9b93aedc540e76059ee27841a96acb9ea74a51545dfef18b0fcf5b57
6fc672288e68146930b86c7a3d490f551c8d7a7e8ba3229d64a6280118095bea
ad9044d9762453e2813be8ab96b9011efb2f42ab72a0cb26d7f98b9bd1d65965
b4b4b195e14e9fda5a6d890ddb57f93ef81d6d9a976078354450ee45d18c89e3
8d6ca64e4c3c19587405e19d53d0e2f4d52b77f927621d4178a3f7c2bf50c2ea
d163cc15a39fb36391bd67f6eaada6691f0c7bc75fc80282a4a258244163e12a
6681b0613fc6d5a3e1132f7499380eb9db52b03ab429f0c2109a641c9a2ea4d3
11751c6aa3e5c44c92765876bc9cd46da90f466b9924b9b1993fa1c91157681d
fc5099e5be818f8268327aaf190cd07b4b4ebb04e9d63eefa5a04ea504f93d62
BlankBot control servers:
79.133.41.52
185.255.92.185
Found this article interesting? Follow us on X(Twitter) and LinkedIn to read more exclusive content we post.


Mini Nina Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Gina Savage X Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
its Brklyn X Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Soriyah Sann Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lorena VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Miss Des Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Molly The Worker Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Zara Patel XX Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Haleigh Cox Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lemon Drop it Like its Hot Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jus a Teasee – Naomi Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Mini Nina Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Coco Fantasia Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Crystal Sunshine Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lorena VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Coco Star Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jade x Jamal Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Fire Violet Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lexi Soriya Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Dab of Kya Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Gina Savage X Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Curvy Mommy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
YouDreamofShayy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Kara J Lee Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Cinnabus Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
OTM Dee Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Livv A Little Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Natalie Turner Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
I Am Queen Jaii FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jessyy Renn Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Scandinavian Anna – FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Envy Kells x Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jasminca David Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
T_O_Princess XOXO Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jacqueline Valentine Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Sunnyy Tha Goat Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jolene Canada Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Thee Princess Nat Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lolita Aliya – u Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Wuta Booty Fulashh Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
NamiSwanBB – NamiBBSwan Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Rosa Acosta Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Elixserr Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Legit Alexa Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Kayla Dene Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Pyteee Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Bossy Brazilian xXx Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Mara Santiago Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Valeriaaa Belen Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Officially Seni Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Empress Elfiie – Little Elfiie Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Thick n Lite Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Steph Murves VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Nikki Stone Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Baddies Galleryy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Krissy Taylor VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
JasmineeRoseeXX FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
uDream of Jordan VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
SweetGirl Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Defiant Panda Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lina Bina Baby Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
BBY Anni Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
XOXO Melia Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Biscuit Wit Da Fanss Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lil Milky Bun – FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Tasty Tracey VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Love Bug Chanel Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Kayla G Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
YogaBlondie Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Paradis Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Crystal Sunshine Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Rosa Acosta Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Russian Creammmmmm – TheySayyPassionnx Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Bebe Da Brattttt Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
XOXO Melia Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
The Official Phat Butt Veda Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Paradis Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
SweetGirl Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Slavic Caramel FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Mikayla D VIP – Mikayla Demaiter Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lolita Aliya – u Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Yo Fav Thickiee Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Caramel Kitten Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Blondie Sofia Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Real Princess Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Fine Ass Shanice Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
That Honey Dip Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Kayla Dene Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
XO Leeza Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
xx Reeses Pieces Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
NaturalLuvsBeauty – The Comfy Princess – LiaMirandaLinzy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
K Zaye Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Aurorita Marie Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Love Bug Chanel Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
NyyJjaae – FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Dab of Kya Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Only Boddy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Gabriella_ Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Wavy Ting Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Elixserr Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
SweetGirl Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Miss Des Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Amber Jay Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Ivy Vix Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Haleigh Cox Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Vinny Ballerina Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Baileyy Rose Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Officially Seni Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Symone Skye Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Erzabel X Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
The Throat Bully Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Defiant Panda Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Violet Got Cake – BaddGalSteph Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Professor Gaia Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Fine Ass Mercedes Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Hazey Haley Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Mythiccal Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Cherri Cali Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Jade x Jamal Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
SlimAssTink – SlimGoesRounds Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Cinnabus Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Ms Thick Overload Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
Lil Milky Bun – FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
There’s a certain magic in the way you make even the most abstract ideas feel personal and real.
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
My partner and I absolutely love your blog and find many of your post’s to be what precisely I’m looking for. Would you offer guest writers to write content for you personally? I wouldn’t mind producing a post or elaborating on a few of the subjects you write related to here. Again, awesome site!
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
Great post. I was checking constantly this blog and I’m impressed! Extremely useful info specially the last part 🙂 I care for such information a lot. I was seeking this certain information for a long time. Thank you and best of luck.
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB FANSLY MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
Thanks for the strategies presented. One thing I should also believe is credit cards presenting a 0 rate of interest often bait consumers in zero rate, instant approval and easy on-line balance transfers, nonetheless beware of the most recognized factor that will void your 0 easy street annual percentage rate and as well as throw one out into the very poor house rapid.
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
I am really impressed with your writing skills and also with the layout on your weblog. Is this a paid theme or did you modify it yourself? Either way keep up the nice quality writing, it抯 rare to see a great blog like this one today..
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
6TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
ONLY FANS LEAKS TRADING ( https://urbancrocspot.org/ucs-leaks-archive/ )
10TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY FANSLY LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY ONLYFANS MEGA FOLDERS ( https://urbancrocspot.org/ucs-leaks-archive/ )
12TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
BUY LEAKED ONLYFANS ( https://urbancrocspot.org/ucs-leaks-archive/ )
11TB ONLY FANS MEGA LINK ( https://urbancrocspot.org/ucs-leaks-archive/ )
TRADE ONLYFANS MEGA LINKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
PURCHASE ONLY FANS LEAKS ( https://urbancrocspot.org/ucs-leaks-archive/ )
8TB ONLYFANS MEGA FOLDER ( https://urbancrocspot.org/ucs-leaks-archive/ )
Please tell me more about this. May I ask you a question? http://www.hairstylesvip.com
Thank you for your articles. I find them very helpful. Could you help me with something? http://www.ifashionstyles.com
Good web site! I truly love how it is easy on my eyes and the data are well written. http://www.hairstylesvip.com I am wondering how I could be notified whenever a new post has been made. I’ve subscribed to your RSS which must do the trick! Have a nice day!
Great content! Super high-quality! Keep it up! http://www.kayswell.com
Thank you for your help and this post. It’s been great. http://www.kayswell.com
Thanks for the interesting things you have exposed in your short article. One thing I would really like to discuss is that FSBO human relationships are built over time. By introducing yourself to the owners the first weekend break their FSBO can be announced, prior to the masses start calling on Wednesday, you generate a good association. By sending them instruments, educational materials, free accounts, and forms, you become a great ally. By subtracting a personal interest in them in addition to their problem, you develop a solid relationship that, oftentimes, pays off once the owners opt with an agent they know as well as trust – preferably you actually.
Thanks for posting. I really enjoyed reading it, especially because it addressed my problem. http://www.kayswell.com It helped me a lot and I hope it will help others too.
Incredible! This blog looks exactly like my old one! It’s on a entirely different subject but it has pretty much the same layout and design. Excellent choice of colors!
Thank you for writing this post. I like the subject too. http://www.kayswell.com
I want to thank you for your assistance and this post. It’s been great. http://www.kayswell.com
Thank you for your help and this post. It’s been great. http://www.hairstylesvip.com
I want to thank you for your assistance and this post. It’s been great. http://www.kayswell.com
Wow, marvelous blog structure! How lengthy have you ever been running a blog for? you make blogging glance easy. The full glance of your website is fantastic, as smartly as the content material!
Thank you for writing this post! http://www.hairstylesvip.com
Thanks for your help and for writing this post. It’s been great. http://www.ifashionstyles.com
Thanks for posting. I really enjoyed reading it, especially because it addressed my problem. http://www.ifashionstyles.com It helped me a lot and I hope it will help others too.
Hi to every body, it’s my first pay a visit of this weblog; this weblog contains remarkable and genuinely excellent material designed for readers.
Hello, I enjoy reading all of your post. I wanted to write a little comment to support you.
constantly i used to read smaller articles or reviews that also clear their motive,and that is also happening with this piece of writing which I am reading here. http://www.kayswell.com
Good write-up. I certainly appreciate this website. Keep it up! http://www.kayswell.com
You’re so interesting! I don’t suppose I have read something like this before. So nice to discover another person with a few genuine thoughts on this subject. Seriously.. many thanks for starting this up. This web site is something that’s needed on the web, someone with a little originality! http://www.kayswell.com
If some one needs to be updated with latest technologies therefore he must be go to see this web site and be up to date every day. http://www.kayswell.com
Spot on with this write-up, I really believe this site needs much more attention. I’ll probably be returning to read through more, thanks for the info! http://www.kayswell.com
Hi there to all, for the reason that I am truly keen of reading this website’s post to be updated daily. It carries fastidious data. http://www.kayswell.com
Hi to every body, it’s my first pay a visit of this weblog; this weblog contains remarkable and genuinely excellent material designed for readers. http://www.kayswell.com
It’s enormous that you are getting ideas from this paragraph as well as from our dialogue made at this time. http://www.kayswell.com
Thank you for the auspicious writeup. It in fact was a amusement account it. Look advanced to far added agreeable from you! By the way, how could we communicate? http://www.kayswell.com
When someone writes an piece of writing he/she keeps the thought of a user in his/her brain that how a user can know it. So that’s why this paragraph is outstdanding. http://www.kayswell.com
Sweet blog! I found it while searching on Yahoo News. Do you have any tips on how to get listed in Yahoo News?I’ve been trying for a while but I never seem to get there! Many thanks http://www.kayswell.com
Very nice post. I just stumbled upon your weblog and wished to say that I’ve truly enjoyed surfing around your blog posts. After all I will be subscribing to your feed and I hope you write again very soon! http://www.kayswell.com
Hello there! I could have sworn I’ve been to this blog before but after checking through some of the post I realized it’s new to me.Anyways, I’m definitely glad I found it and I’ll be bookmarking and checking back frequently! http://www.kayswell.com
Somebody essentially assist to make critically posts I would state. That is the first time I frequented your website page and to this point? I amazed with the research you made to make this actual put up amazing. Magnificent task! http://www.kayswell.com
Really when someone doesn’t be aware of afterward its up to other viewers that they will help, so here it occurs. http://www.ifashionstyles.com
Thanks for your write-up on the travel industry. I will also like to include that if you are a senior considering traveling, it can be absolutely crucial to buy travel cover for golden-agers. When traveling, seniors are at biggest risk of experiencing a medical emergency. Getting the right insurance plan package for one’s age group can safeguard your health and provide you with peace of mind.
First off I would like to say superb blog! I had a quick question which I’d like to ask if you don’t mind. I was interested to find out how you center yourself and clear your thoughts before writing. http://www.kayswell.com I have had a difficult time clearing my mind in getting my ideas out there.I truly do take pleasure in writing but it just seems like the first 10 to 15 minutes are
Hi there, everything is going sound here and ofcourse every one is sharing data, that’s really good, keep up writing. http://www.hairstylesvip.com
Thanks for your publication. What I want to comment on is that when evaluating a good online electronics store, look for a web site with total information on critical indicators such as the personal privacy statement, safety measures details, payment guidelines, along with terms and policies. Often take time to look into the help as well as FAQ areas to get a greater idea of how a shop performs, what they are capable of doing for you, and the way you can make best use of the features.
One thing is that when you find yourself searching for a education loan you may find that you will want a cosigner. There are many scenarios where this is correct because you will find that you do not employ a past credit standing so the loan provider will require that you’ve got someone cosign the financing for you. Thanks for your post.
Do you mind if I quote a few of your articles as long as I provide credit and sources back to your website? My website is in the exact same area of interest as yours and my visitors would definitely benefit from some of the information you provide here. http://www.hairstylesvip.com
Hello mates, nice article and fastidious urging commented here, I am actually enjoying by these. http://www.kayswell.com
Oh my goodness! Incredible article dude! Many thanks, However I am experiencing problems with your RSS. I don’t understand the reason why I cannot join it. Is there anybody having the same RSS issues? Anyone that knows the solution will you kindly respond? Thanx!! http://www.kayswell.com
Aw, this was a very nice post. Taking the time and actual effort to create a great article… but what can I say… I hesitate a whole lot and never seem to get nearly anything done. http://www.kayswell.com
Pretty great post. I just stumbled upon your weblog and wanted to say that I have really loved browsing your weblog posts. After all I’ll be subscribing on your feed and I hope you write once more very soon! http://www.kayswell.com
Very nice post. I just stumbled upon your weblog and wished to say that I’ve really enjoyed browsing your blog posts. After all I’ll be subscribing to your feed and I hope you write again soon!
Hi there! This is kind of off topic but I need some guidance from an established blog. Is it difficult to set up your own blog? I’m not very techincal but I can figure things out pretty fast. I’m thinking about creating my own but I’m not sure where to begin. Do you have any points or suggestions? Many thanks
Hello mates, nice article and fastidious urging commented here, I am actually enjoying by these.
Wow, incredible blog layout! How long have you been blogging for? you made blogging look easy. The overall look of your web site is excellent, let alone the content!
Hi, Neat post. There is a problem with your site in web explorer, might test this? IE still is the market chief and a large component of other people will leave out your wonderful writing because of this problem.
I haven’t checked in here for a while because I thought it was getting boring, but the last few posts are good quality so I guess I’ll add you back to my daily bloglist. You deserve it my friend 🙂
You are a very bright person!
I’m not that much of a internet reader to be honest but your blogs really nice, keep it up! I’ll go ahead and bookmark your website to come back in the future.
Hello there, You’ve done a great job. I will certainly digg it and personally recommend to my friends. I’m sure they will be benefited from this site.
If some one desires expert view concerning blogging afterward i advise him/her to pay a visit this weblog, Keep up the good work.
Very nice post. I just stumbled upon your weblog and wished to say that I’ve truly enjoyed surfing around your blog posts. After all I will be subscribing to your feed and I hope you write again very soon!
It’s enormous that you are getting ideas from this paragraph as well as from our dialogue made at this time.
I’m not that much of a internet reader to be honest but your blogs really nice, keep it up! I’ll go ahead and bookmark your site to come back down the road. Many thanks
It’s impressive that you are getting thoughts from this piece of writing as well as from our argument made at this time. http://www.kayswell.com
Somebody essentially assist to make critically posts I would state. That is the first time I frequented your website page and to this point? I amazed with the research you made to make this actual put up amazing. Magnificent task!
I’m extremely impressed with your writing skills as well as with the layout on your weblog. Is this a paid theme or did you customize it yourself? Anyway keep up the excellent quality writing,it is rare to see a nice blog like this one today. http://www.kayswell.com
Pretty great post. I just stumbled upon your weblog and wanted to say that I have really loved browsing your weblog posts. After all I’ll be subscribing on your feed and I hope you write once more very soon! http://www.kayswell.com
You actually make it seem so easy with your presentation but I find this matter to be actually something that I think I would never understand. It seems too complex and very broad for me. I’m looking forward for your next post, I will try to get the hang of it! http://www.kayswell.com
If you would like to obtain a great deal from this paragraph then you have to apply these methods to your won website.
We’re a group of volunteers and starting a new scheme in our community. Your website offered us with helpful information to work on. You’ve done a formidable task and our whole community will be thankful to you. http://www.kayswell.com
What’s up, after reading this awesome post i am too happy to share my familiarity here with colleagues. http://www.kayswell.com
I’m really enjoying the design and layout of your website.It’s a very easy on the eyes which makes it much more pleasant for me to come here and visit more often. Did you hire out a developer to create your theme? http://www.kayswell.com
Pretty great post. I just stumbled upon your weblog and wanted to say that I have really loved browsing your weblog posts. After all I’ll be subscribing on your feed and I hope you write once more very soon!
Hello there! I could have sworn I’ve been to this blog before but after checking through some of the post I realized it’s new to me.Anyways, I’m definitely glad I found it and I’ll be bookmarking and checking back frequently!
Hi there, just became alert to your blog through Google,and found that it is truly informative. I am gonna watch outfor brussels. I’ll be grateful if you continue this in future.Lots of people will be benefited from your writing.Cheers!
What’s up, after reading this awesome post i am too happy to share my familiarity here with colleagues. http://www.kayswell.com
Greetings! Very helpful advice in this particular article! It’s the little changes that will make the most significant changes. Thanks a lot for sharing!
Greate article. Keep posting such kind of info on your site. Im really impressed by your site. Hi there, You have done an excellent job. I’ll definitely digg it and individually suggest to my friends. I am sure they will be benefited from this web site.
Interesting article. It is unfortunate that over the last decade, the travel industry has had to deal with terrorism, SARS, tsunamis, bird flu, swine flu, plus the first ever entire global recession. Through it all the industry has proven to be powerful, resilient as well as dynamic, getting new approaches to deal with adversity. There are constantly fresh issues and opportunity to which the sector must once again adapt and respond.
Pretty nice post. I just stumbled upon your weblog and wanted to say that I’ve truly enjoyed surfing around your blog posts. After all I’ll be subscribing to your rss feed and I hope you write again very soon!
Right here is the perfect blog for everyone who hopes to find out about this topic. http://www.ifashionstyles.com You understand so much its almost hard to argue with you (not that I actually will need to…HaHa). You definitely put a freshspin on a topic that has been written about for decades.Excellent stuff, just great!
Nice post. I learn something new and challenging on sites I stumbleupon everyday. It’s always exciting to read through content from other authors and practice a little something from other web sites.
Your mode of explaining everything in this piece of writing is genuinely pleasant, every one be capable of simply be aware of it, Thanks a lot.
Great blog you’ve got here.. It’s difficult to find excellent writing like yours these days. I seriously appreciate individuals like you! Take care!!
I am regular reader, how are you everybody? This post posted at this web page is genuinely pleasant.
These are actually great ideas in about blogging. You have touched some pleasant things here. Any way keep up wrinting. http://www.ifashionstyles.com
I used to be able to find good advice from your blog articles.
Nice answers in return of this matter with firm arguments and telling everything concerning that.
I’m not sure where you’re getting your info, but great topic. I needs to spend some time learning more or understanding more. Thanks for great info I was looking for this information for my mission.
This is very attention-grabbing, You are an excessively professional blogger.I’ve joined your feed and stay up for in quest of extra of your fantastic post. Also, I have shared your web site in my social networks。
Oh my goodness! Incredible article dude! Many thanks, However I am experiencing problems with your RSS. I don’t understand the reason why I cannot join it. Is there anybody having the same RSS issues? Anyone that knows the solution will you kindly respond? Thanx!! http://www.ifashionstyles.com
Hey very nice web site!! Man .. Beautiful .. Amazing .. I will bookmark your site and take the feeds also…I am happy to find a lot of useful information here in the post, we need develop more strategies in this regard, thanks for sharing. . . . . .
Another issue is that video games are typically serious as the name indicated with the primary focus on knowing things rather than amusement. Although, it comes with an entertainment factor to keep your children engaged, each and every game is usually designed to work with a specific group of skills or program, such as mathematics or scientific discipline. Thanks for your posting.
You’re so interesting! I don’t suppose I have read something like this before. So nice to discover another person with a few genuine thoughts on this subject. Seriously.. many thanks for starting this up. This web site is something that’s needed on the web, someone with a little originality!
It’s in point of fact a great and useful piece of info.I am glad that you just shared this useful info with us.Please keep us informed like this. Thanks for sharing.
Hi, Neat post. There’s an issue together with your site in internet explorer, could test this? IE still is the market leader and a large section of other folks will miss your great writing due to this problem. http://www.ifashionstyles.com
I used to be able to find good advice from your blog articles. http://www.hairstylesvip.com
Great post. I was checking continuously this blog and I’m impressed! Extremely useful information specifically the last part 🙂 I care for such info much. I was seeking this certain information for a long time. Thank you and good luck.
I think the admin of this website is in fact working hard in support of his website, as here every stuff is quality based stuff.
Your mode of explaining everything in this piece of writing is genuinely pleasant, every one be capable of simply be aware of it, Thanks a lot.
It is really a nice and useful piece of information. I am glad that you shared this helpful information with us. Please keep us informed like this. Thank you for sharing.
I do agree with all of the concepts you’ve introducedon your post. They’re really convincing and will definitely work.Nonetheless, the posts are very brief for newbies.May just you please extend them a bit from subsequent time?Thanks for the post. http://www.kayswell.com
Good day! Would you mind if I share your blog with my zynga group?There’s a lot of folks that I think would really enjoy your content. Please let me know. Cheers
I do agree with all of the ideas you have presented in your post. They are very convincing and will definitely work. Still, the posts are very short for newbies. Could you please extend them a bit from next time? Thanks for the post.
Admiring the time and effort you put into your site and detailed information you offer. It’s good to come across a blog every once in a while that isn’t the same unwanted rehashed information. Wonderful read! I’ve bookmarked your site and I’m adding your RSS feeds to my Google account.
Hello! I just wanted to ask if you ever have any problems with hackers? My last blog (wordpress) was hacked and I ended up losing months of hard work due to no back up. Do you have any methods to prevent hackers?
Buy OnlyFans Accounts – https://urbancrocspot.org/product-tag/only-fans-account/
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts For Sale – https://urbancrocspot.org/accounts/
OnlyFans Accounts With Balance
OnlyFans Account With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Accounts – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts For Sale
OnlyFans Account Seller
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OF Creator Account Fully Verified – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Accounts
Buy OnlyFans Accounts
Hello my loved one! I wish to say that this post is amazing, great written and include approximately all significant infos. I would like to peer extra posts like this .
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account With Balance
Buy OnlyFans Creator Account
OnlyFans Accounts For Sale – https://urbancrocspot.org/accounts/
Buy OnlyFans Accounts
OnlyFans Accounts With Balance
I’d like to thank you for the efforts you have put in writing this blog.I’m hoping to check out the same high-grade content from you later on as well. In truth, http://www.hairstylesvip.com your creative writing abilities has motivated me to get my very own website now 😉
Buy OnlyFans Creator Account
Buy Hacked OnlyFans
OF Creator Account Fully Verified – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Accounts
OF Creator Account Fully Verified
I’m really enjoying the design and layout of your website.It’s a very easy on the eyes which makes it much more pleasant for me to come here and visit more often. Did you hire out a developer to create your theme? http://www.hairstylesvip.com
OnlyFans Account Seller – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts For Sale – https://urbancrocspot.org/accounts/
Greetings! Very helpful advice in this particular post! It is the little changes that produce the biggest changes. Thanks a lot for sharing!
OnlyFans Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account With Balance
OF Creator Account Fully Verified
OnlyFans Account Seller – https://urbancrocspot.org/product-tag/only-fans-account/
OF Creator Account Fully Verified – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts For Sale
Buy OnlyFans Accounts
OnlyFans Account With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Accounts
Buy OnlyFans Creator Account – https://urbancrocspot.org/accounts/
OF Accounts With Balance
OF Accounts With Balance
Cracked OnlyFans Accounts
OnlyFans Account With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Accounts – https://urbancrocspot.org/product-tag/only-fans-account/
Buy Hacked OnlyFans
Buy OnlyFans Accounts – https://urbancrocspot.org/accounts/
Hiya! Quick question that’s totally off topic. Do you know how to make your site mobile friendly? My site looks weird when browsing from my apple iphone. I’m trying to find a template or plugin that might be able to correct this issue. If you have any suggestions, please share.
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Creator Account – https://urbancrocspot.org/accounts/
Buy OnlyFans Creator Account – https://urbancrocspot.org/accounts/
OnlyFans Account Seller – https://urbancrocspot.org/product-tag/only-fans-account/
OF Accounts With Balance
Buy OnlyFans Accounts – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Accounts
OnlyFans Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account Seller
Buy OnlyFans Accounts
OnlyFans Account With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account Seller – https://urbancrocspot.org/product-tag/only-fans-account/
OF Creator Account Fully Verified
OnlyFans Account Seller – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Creator Account – https://urbancrocspot.org/accounts/
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
Cracked OnlyFans Accounts – https://urbancrocspot.org/accounts/
OF Accounts With Balance
OF Creator Account Fully Verified
OnlyFans Account With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account With Balance
OF Creator Account Fully Verified
OF Creator Account Fully Verified – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Accounts – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Accounts – https://urbancrocspot.org/accounts/
Buy OnlyFans Accounts – https://urbancrocspot.org/product-tag/only-fans-account/
OF Creator Account Fully Verified – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts With Balance
OnlyFans Account Seller – https://urbancrocspot.org/product-tag/only-fans-account/
OF Creator Account Fully Verified – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts For Sale
Buy OnlyFans Accounts – https://urbancrocspot.org/accounts/
Buy Hacked OnlyFans
Buy OnlyFans Accounts
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account With Balance
OnlyFans Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account Seller – https://urbancrocspot.org/product-tag/only-fans-account/
OF Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OF Creator Account Fully Verified
Cracked OnlyFans Accounts
Buy Hacked OnlyFans
Buy OnlyFans Creator Account
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OF Creator Account Fully Verified – https://urbancrocspot.org/product-tag/only-fans-account/
OF Creator Account Fully Verified
OF Creator Account Fully Verified
OnlyFans Accounts For Sale
OnlyFans Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
Buy OnlyFans Accounts
OnlyFans Accounts For Sale – https://urbancrocspot.org/accounts/
Cracked OnlyFans Accounts
Cracked OnlyFans Accounts
Buy OnlyFans Accounts
OnlyFans Account Seller – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account Seller
Cracked OnlyFans Accounts
OnlyFans Accounts For Sale
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account Seller
Buy OnlyFans Accounts – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OF Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Account With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts For Sale – https://urbancrocspot.org/accounts/
OF Accounts With Balance – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts For Sale
Buy OnlyFans Accounts – https://urbancrocspot.org/product-tag/only-fans-account/
Buy Hacked OnlyFans
Buy OnlyFans Creator Account – https://urbancrocspot.org/accounts/
Your article helped me a lot, is there any more related content? Thanks!
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://accounts.binance.info/vi/register?ref=MFN0EVO1
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://accounts.binance.info/fr/register-person?ref=T7KCZASX
OnlyFans Accounts For Sale – https://urbancrocspot.org/accounts/
OnlyFans Accounts For Sale – https://urbancrocspot.org/accounts/
Buy OnlyFans Accounts – https://urbancrocspot.org/accounts/
Buy Hacked OnlyFans
OnlyFans Account Seller
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Buy OnlyFans Creator Account – https://urbancrocspot.org/accounts/
OnlyFans Accounts With Balance
Buy Hacked OnlyFans – https://urbancrocspot.org/product-tag/only-fans-account/
OnlyFans Accounts For Sale
OF Creator Account Fully Verified
I’m not sure where you’re getting your info, but great topic. I needs to spend some time learning more or understanding more. Thanks for great info I was looking for this information for my mission.
Haleigh Cox Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
That Honey Dip Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
LotusBombb Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Your article helped me a lot, is there any more related content? Thanks!
The Real Slim Cadi Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Miss Dominican Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Delly The Dream Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Scandinavian Anna – FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
xx Reeses Pieces Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Nebraska Wut Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jasminca David Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Real Princess Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lillianette Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
xx Reeses Pieces Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lil Booty Plug Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
May Murcielaga Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Biscuit Wit Da Fanss Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lena Paul – Lena is A Peach Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Tiahnie Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Flower Bombbbb Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Korina Kova Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
BabyGirl Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Tamekia Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Nasty GILF – YoFavShyFreak – Taveleigh Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Scarlett Jasminn – FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Curvvyy B – SimplyBella Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Nadia Palik Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
SlimAssTink – SlimGoesRounds Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://www.binance.com/en-NG/register?ref=YY80CKRN
Red Rose La Cubana Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
ElvaSnaps FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Janie Fit Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Shez a Druq Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
YogaBlondie Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Mrs Katty Cakes Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Paradis Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
SweetGirl Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Livv A Little Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Pooh BBeearr Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Minx Millz Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Sugarr Spiceee FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Fine Ass Shanice Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Miaa Diorr Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Thick n Lite Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Gabriella_ Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Sophie Raiin Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Shez a Druq Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Nadia Palik Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Nebraska Wut Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Semaj Media FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lillianette Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lunita Skye Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Anelisa Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Tamekia Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jojo Uncut Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
LotusBombb Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Waifu Flare Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Princess So Seductive Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Destiny Next Door Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Karla James Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Juicyyyyy E – Ebony Mariaaaa Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Minx xXx Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Bebe Da Brattttt Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Pyteee Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Myah Janes VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Vinny Ballerina Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
JasmineeRoseeXX FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lolita Aliya – u Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Ivory Offical Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Janie Fit Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Baileyy Rose Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Thick Lana Love Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Fiit Jazz Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Coca Buttaaaa Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Zara Patel XX Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Afro Sunshine Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Minx xXx Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Yasmin Estrada_ Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Shiroktsne FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
CuteFruit Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Baddiee Babe Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Hi, Neat post. There’s a problem with your web site in internet explorer, would test this?IE still is the market leader and a large portion of people will miss your fantastic writing due to this problem.
Baddiee Babe Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Krissy Kummins VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
ArkansasBabe Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Mikayla D VIP – Mikayla Demaiter Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
FoxyBrown FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Fiit Jazz Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Coco Fantasia Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Baddiee Babe Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Thique Ashhhh Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Pooh BBeearr Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Persian Doll Gia – Whos Madison – Gia Khavari Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lee Lee Zilla Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Hazey Haley Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Ken Brazy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
ThicckAsia – Thick Lauryn Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Hannah Bandz Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Haleigh Cox Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Juliana x Ferrara Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Astr Girll Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Ny Ny Irene Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Tiffy Monroe X Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Wuta Booty Fulashh Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Juicyyyyy E – Ebony Mariaaaa Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Wavy Ting Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Princess So Seductive Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Ms LyLy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Kendra Karter Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Slavic Caramel FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Fiit Jazz Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Hell Bunny k Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Legit Alexa Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Pimpsation Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Brunette Dulce Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
BBY Anni Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Bossy Brazilian xXx Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
All Charged Up Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Hannah Bandz Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lil Lunita Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
I Am Queen Jaii FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
VivaLaKipp Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Naomi Gets Nasty Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
TylerUncensored Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Missus Blu Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Bebe Da Brattttt Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
The Juicy Goddess Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Cherri Cali Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
G Cup Baby Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Nany Palacio Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Ken Brazy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
xXx KJayyyyy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Red Rose La Cubana Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lorena VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Scarlett Jasminn – FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Kendra Karter Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Ms Biddies Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Empress Elfiie – Little Elfiie Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Foxy Roxie Vaught Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
The Official Phat Butt Veda Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Love Bug Chanel Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Your article helped me a lot, is there any more related content? Thanks! https://accounts.binance.com/es/register?ref=RQUR4BEO
iWant Judyyy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Cubana Redd Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Scandinavian Anna – FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lillianette Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Alexis Texas Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://accounts.binance.info/el/register?ref=DB40ITMB
Lil Lunita Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Miss Dominican Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
The Juicy Goddess Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jiggy Mama FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Shy Thickie VIP Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Sarita Natividad Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Mythiccal Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Cinnabus Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Brown Bodii Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
SlimAssTink – SlimGoesRounds Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Envy Kells x Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Curvy Mommy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Josseline Garcia – u Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Slot tại xn88 win có tính năng “tạm dừng” – nếu có việc đột xuất, bạn có thể pause ván chơi và quay lại sau mà không mất tiền cược hay vòng quay đang diễn ra. TONY12-30
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Ms Biddies Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Juicyyyyy E – Ebony Mariaaaa Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Nicole Aniston XO Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
All Charged Up Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Miss Dominican Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Kall Me Katrina Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Ivy Vix Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Thick n Lite Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
The Real Britt Fitt Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Symone Skye Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Jacqueline Valentine Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Nebraska Wut Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lemon Drop it Like its Hot Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Sarah Mariee FANSLY Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
its Brklyn X Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Marie Temara Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Sunnyy Tha Goat Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Lovely Adriana Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Elixserr Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Fiit Jazz Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
The Real Muvad Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Paris Senpai Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Mara Santiago Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
EDM Flower Fairy Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Jus a Teasee – Naomi Only Fans Leaked Fansly Leaks Mega Folder Download Link ( https://UrbanCrocSpot.org )
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your article helped me a lot, is there any more related content? Thanks!
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://www.binance.info/cs/register?ref=OMM3XK51
188v có lừa đảo không có tính năng “theo dõi bạn bè” – xem ai đang chơi gì, thắng bao nhiêu (với sự đồng ý). TONY01-26
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Avia Masters de BGaming es un juego crash con RTP del 97% donde apuestas desde 0,10€ hasta 1.000€, controlas la velocidad de vuelo de un avion que recoge multiplicadores (hasta x250) mientras evita cohetes que reducen ganancias a la mitad, con el objetivo de aterrizar exitosamente en un portaaviones para cobrar el premio acumulado
feg.org.es
Avia Masters de BGaming es un juego crash con RTP del 97% donde apuestas desde 0,10€ hasta 1.000€, controlas la velocidad de vuelo de un avion que recoge multiplicadores (hasta x250) mientras evita cohetes que reducen ganancias a la mitad, con el objetivo de aterrizar exitosamente en un portaaviones para cobrar el premio acumulado
https://share.google/cZmrtPSiGY5DgiFrZ
Hi I am so delighted I found your blog page, I really found you by accident, while I was browsing on Aol for something else, Regardless I am here now and would just like to say cheers for a fantastic post and a all round interesting blog (I also love the theme/design), I don’t have time to read it all at the moment but I have saved it and also included your RSS feeds, so when I have time I will be back to read much more, Please do keep up the great job.
casino zumospin
купить букет москва недорого Цветочный сервис день в день
Bạn có thể đặt giới hạn thua/ngày tại bắn cá 188v – hệ thống sẽ tự động khóa cược khi đạt ngưỡng, giúp bạn kiểm soát cảm xúc và tránh rủi ro tài chính. TONY01-30H
La esencia fundamental de AviaMasters es su revolucionario gameplay aГ©reo. Contrario a otros crash games, aquГ mГЎs allГЎ de ver, sino que tambiГ©n sientes la tensiГіn de cada decisiГіn.
aviamasters.nom.es
Hệ thống khuyến mãi tại game 66b không chỉ hấp dẫn mà còn rất thực tế: từ tiền cược miễn phí không cần nạp, hoàn trả tuần lên tới 2%, đến quà sinh nhật và ưu đãi VIP theo cấp bậc – chơi càng nhiều, lợi càng lớn. TONY02-02O
Good post but I was wondering if you could write a litte more on this topic? I’d be very grateful if you could elaborate a little bit more. Thanks!
https://share.google/fvCDyQF8wAymGVXcz
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://www.binance.info/en-NG/register?ref=YY80CKRN